Design method of active defense system based on white list technology and system
A technology of active defense and design method, applied in the field of security, can solve the problems of difficult to deal with zero-day attacks, specific attacks, very large number of software resources, insufficient security, etc., to ensure effectiveness and identification efficiency, non-limited design implementation method, the effect of ensuring the speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0043] Embodiment 1 (a design method of an active defense system based on whitelist technology)
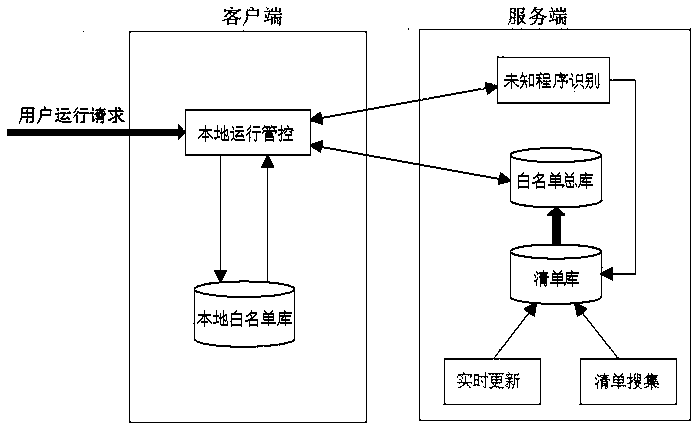
[0044] as attached figure 1 As shown, a kind of design method of the active defense system based on white list technology of the present invention, its specific implementation steps are as follows:
[0045] 1) list collection : The server software collects the executable files in the OS installation image downloaded from the official website of the operating system, obtains the detailed information of the executable files, such as file name, operating system version, file modification time, file Hash value, etc., and trusts them The level is set to white (allow execution), and MySQL is used to generate the manifest library.
[0046] [Design intent: collect the OS installation image downloaded from the official website of the operating system through the server software, and obtain the hash value of the built-in program of the operating system from it, ensuring the reliability o...
Embodiment 2
[0066] Embodiment 2 (a design system of an active defense system based on whitelist technology)
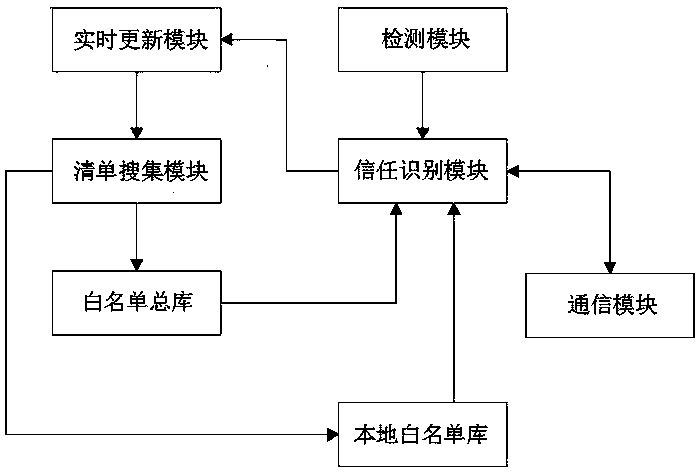
[0067] as attached figure 2 As shown, the present invention also provides a design system of an active defense system based on whitelist technology, wherein,
[0068] Server equipment includes:
[0069] The list collection module is used to collect the OS installation image downloaded from the official website of the operating system, obtain the hash value of the built-in program of the operating system from it, and generate a list library;
[0070] The white list total library generated by the list library on the server side;
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com