White list based realization method for active defense of cloud host
An implementation method and active defense technology, applied in computer security devices, instruments, electrical digital data processing, etc., can solve problems such as not being able to meet the security requirements of cloud data centers, prevent unknown malware and zero-day attacks, and have strong practicability , protection against application and code effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0036] The present invention will be further described below in conjunction with the accompanying drawings and specific embodiments.
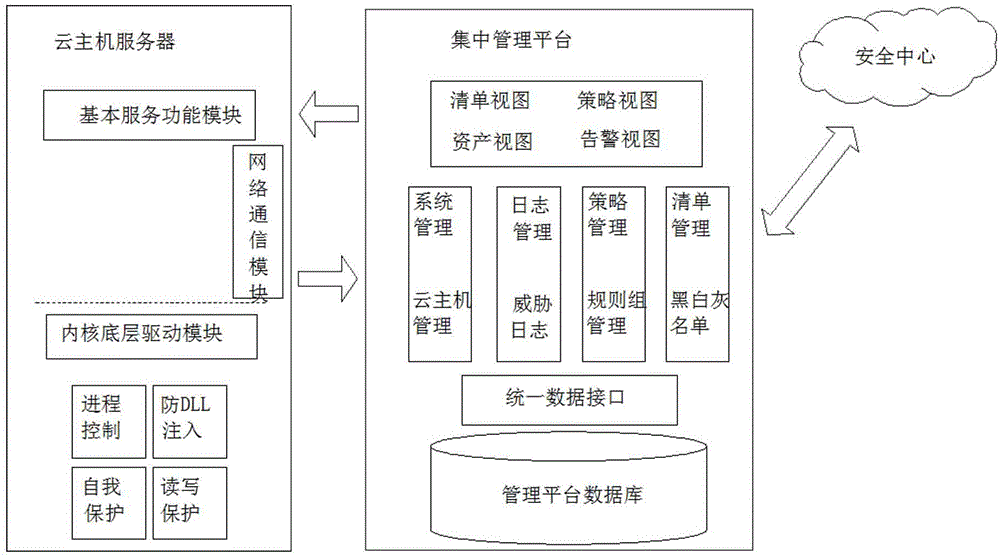
[0037] The present invention provides a whitelist-based cloud host active defense implementation method, as shown in the attached figure 1 As shown, it includes the centralized management platform and client of the server, and the client is installed on each cloud host that needs to be protected. The specific implementation process is as follows:
[0038] 1. First, scan all binary files on the protected cloud host through the server software;
[0039] 2. The cloud security center identifies the trust level of the above-mentioned scanned files, and adds the classified file list library to the white list library, black list library and gray list library respectively, wherein the white list contains known trusted applications; black list The list includes known malicious applications; the gray list includes all unknown applications whose trust le...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com