Network security vulnerability defense system based on dynamic camouflage
A network security and defense system technology, applied in transmission systems, electrical components, etc., can solve problems such as powerlessness, and achieve the effect of improving security and stability and reducing utilization value
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
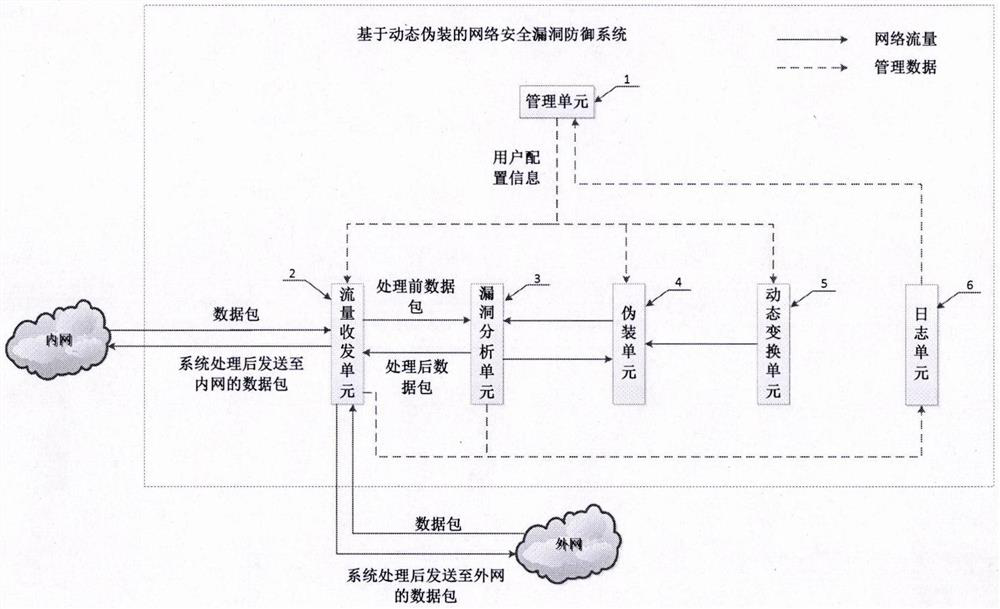
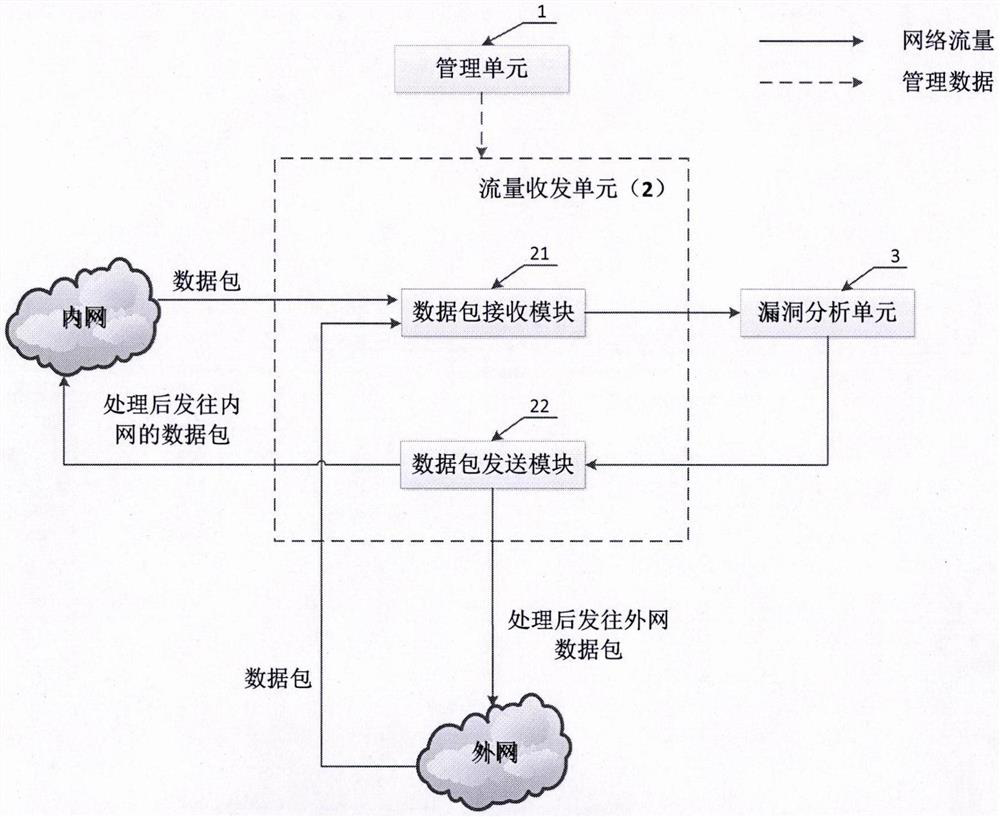
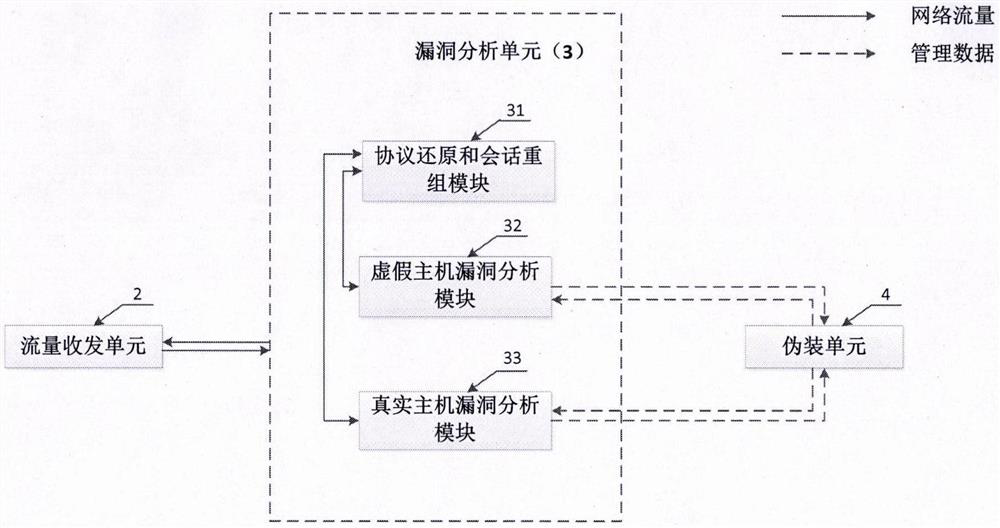
[0054] The network security loophole defense system based on dynamic camouflage described in the second preferred embodiment of the present invention is different from the above-mentioned first preferred embodiment in that when the defense system finds that an attacker accesses a real loophole on a real host, It can be falsely responded to or redirected to a honeypot, thereby effectively preventing attackers from exploiting real vulnerabilities on real hosts. Control network, etc., has important practical value. In the network security loophole defense system based on dynamic camouflage described in the second preferred embodiment of the present invention, the management unit (1) can issue the following configuration information to the camouflage unit (4): real host IP, loopholes that actually exist on the real host The feature field and the content of the corresponding fake response, and / or the IP address and port of the redirect honeypot.
[0055] The present invention prop...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com