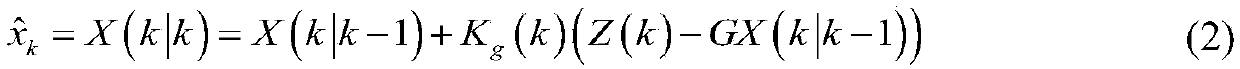A two-layer defense method against spurious data injection attack in power system
A false data injection attack technology, applied in transmission systems, information technology support systems, electrical components, etc., can solve the problem of no FDI attack defense and achieve the effect of defending against FDI injection attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] The accompanying drawings are for illustrative purposes only and cannot be construed as limiting the patent;
[0036] In order to better illustrate this embodiment, some parts in the drawings will be omitted, enlarged or reduced, and do not represent the size of the actual product;
[0037] For those skilled in the art, it is understandable that some well-known structures and descriptions thereof may be omitted in the drawings.
[0038] The technical solutions of the present invention will be further described below in conjunction with the accompanying drawings and embodiments.
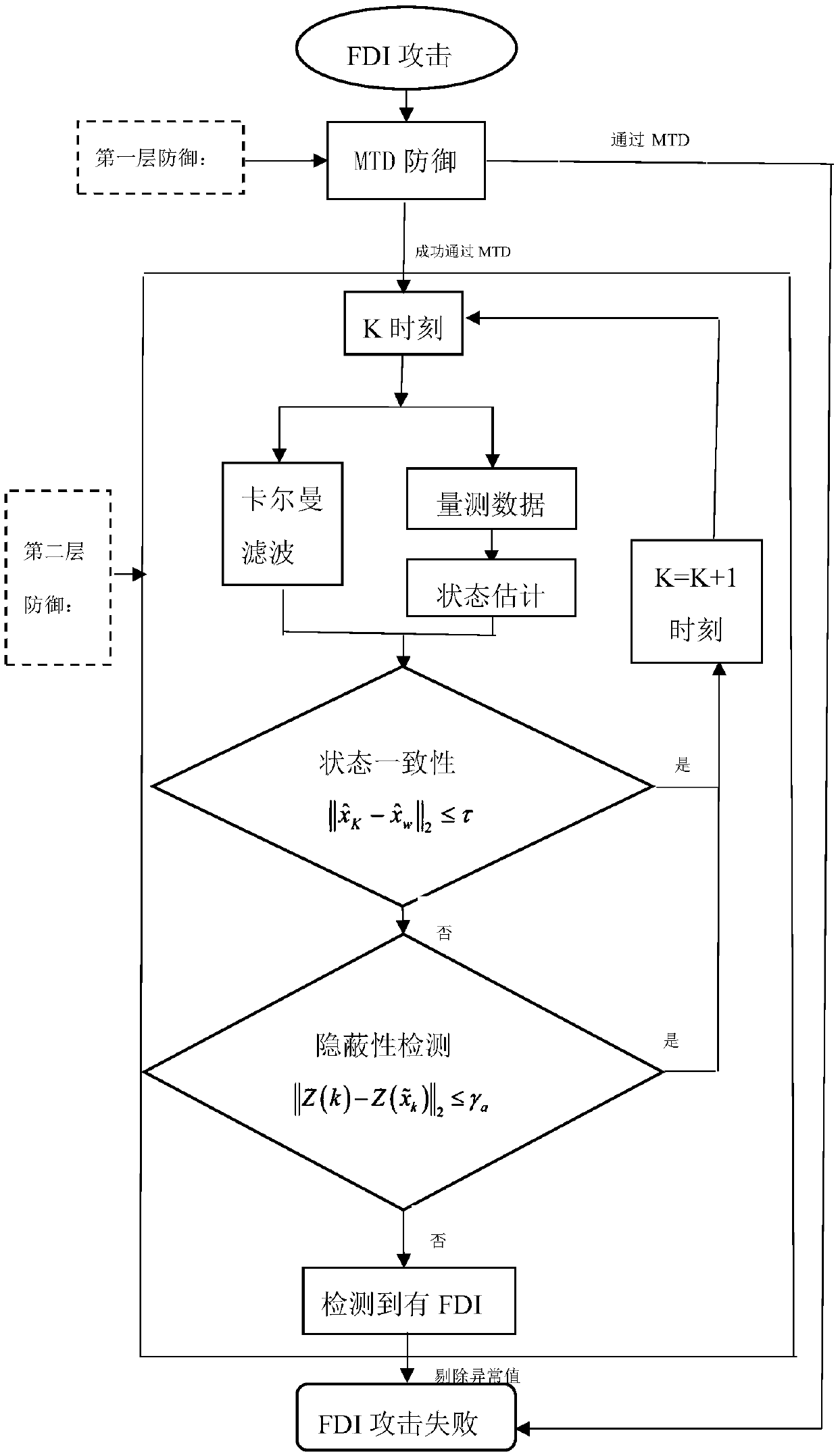
[0039] refer to figure 1 , the specific implementation steps of the present invention are as follows:
[0040] S1: For the FDI attack launched by the attacker at time k, the defender first uses the MTD method to defend. The defender arranges a flexible AC transmission system (D-FACTS) device on the transmission line, and transfers the transmission line between the transmission line i and the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com