A protection method for access security of IP multimedia subsystem
A multimedia subsystem and security technology, applied in the direction of synchronous sending/receiving encryption equipment, data exchange through path configuration, etc., can solve the problems that the user terminal does not support the use of certificates, cannot authenticate UE identity, etc., and overcomes the problem of weak two-way authentication Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
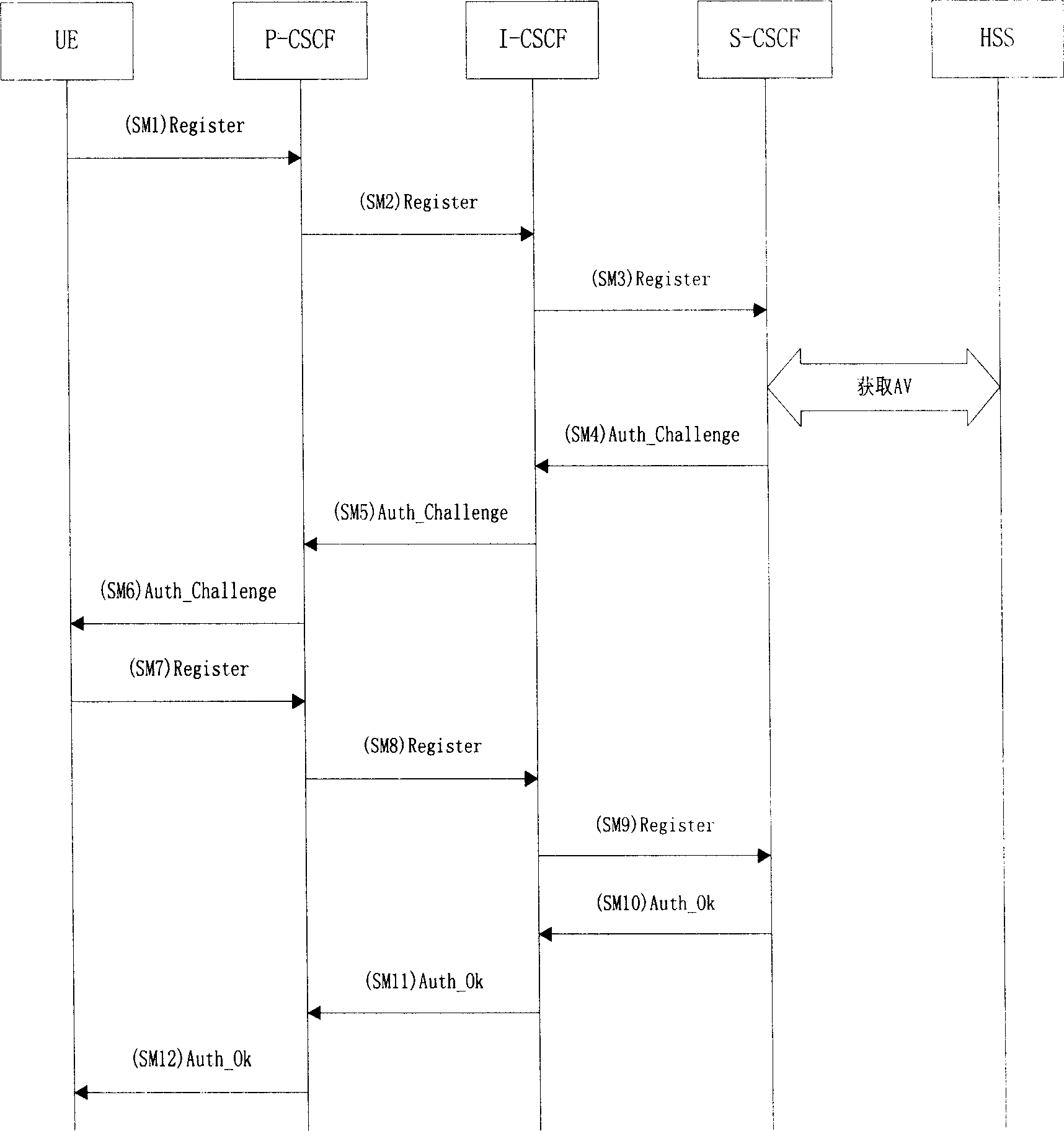
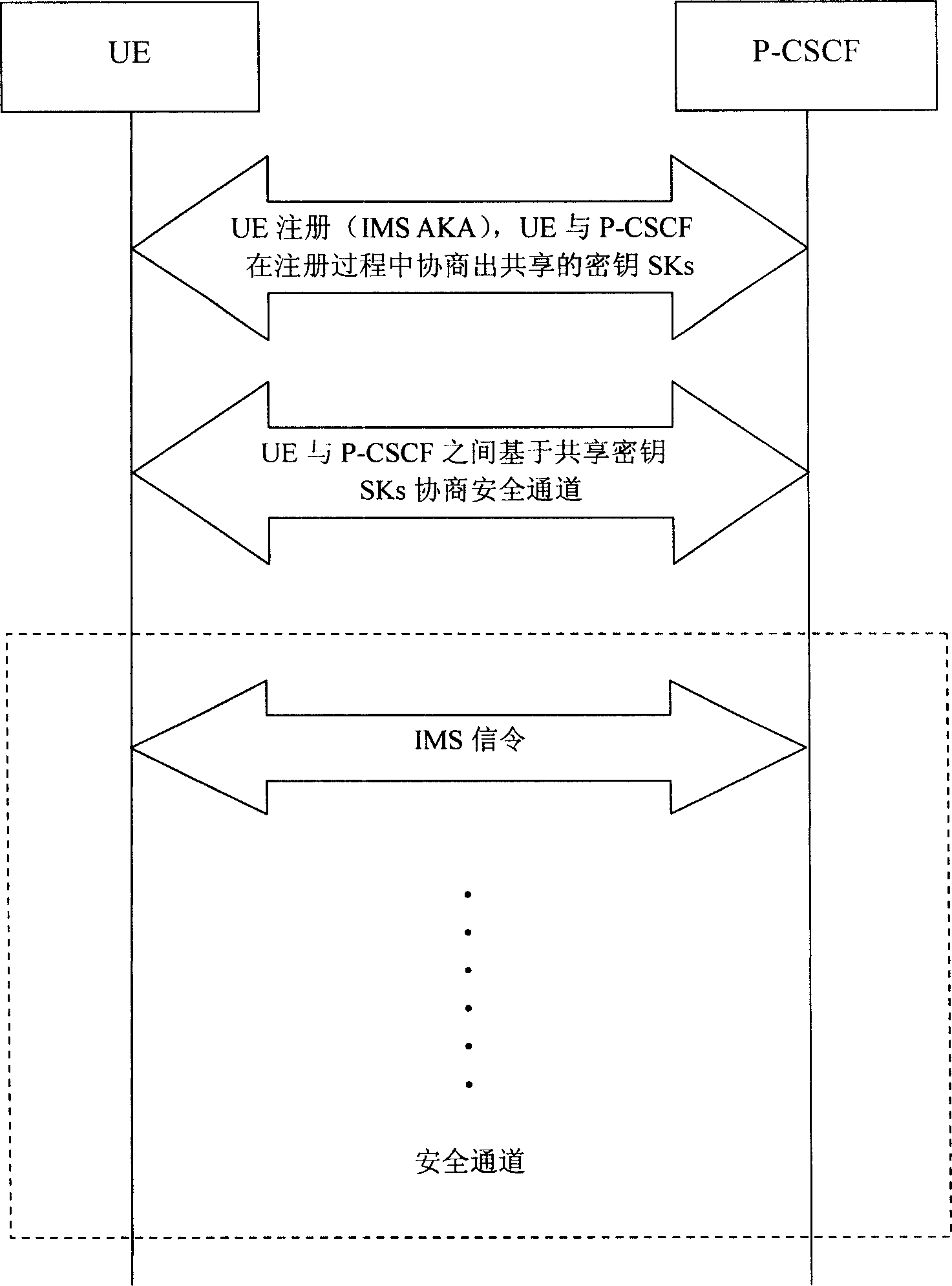
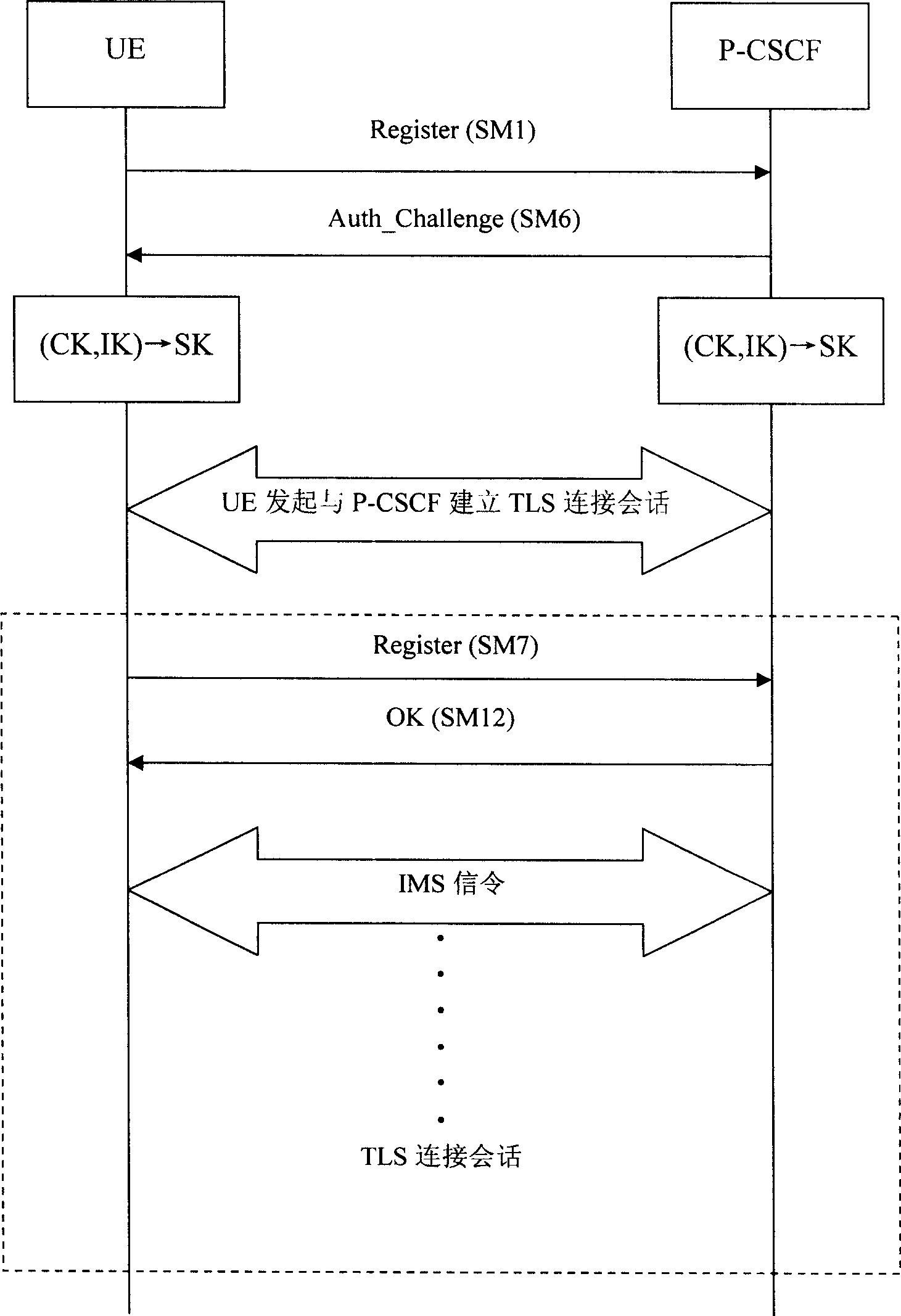
[0051] This embodiment combines image 3 , Describes the method for protecting IMS access security with TLS protocol in the present invention. In this embodiment, both the UE and the P-CSCF support three security mechanisms: TLS, IPSec / IKEv2, and IPSec / IMS AKA. The P-CSCF has a higher priority for TLS support. The UE's IMS access process is as follows:
[0052] 1. The UE sends an initial registration message (Register) SM1 to the P-CSCF, which contains the message headers of require, proxy-require, and security-client. The headers of the require and proxy-require messages contain the tag "sec-agree" option, which indicates that the P-CSCF must support the UE's security mechanism. The Security-client message header contains a list of security mechanisms supported by the UE and its parameters. The content is "TLS; IPSec / IKEv2; IPSec / IMS_AKA, SPI_U, Port_U, cipher suite list". The security-client message header contains three Security mechanism: TLS, IPSec / IKEv2 and IPSec / IMSAKA, whe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com