Patents
Literature
625 results about "Non critical" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Selectively applying resolution enhancement techniques to improve performance and manufacturing cost of integrated circuits
InactiveUS6928635B2Reduce delaysReduction of gate lengthSemiconductor/solid-state device testing/measurementSemiconductor/solid-state device manufacturingResolution enhancement technologiesImage resolution
One embodiment of the present invention provides a system that applies resolution enhancement techniques (RETs) selectively to a layout of an integrated circuit. Upon receiving the layout of the integrated circuit, the system identifies a plurality of critical regions within the layout based on an analysis of one or more of, timing, dynamic power, and off-state leakage current. The system then performs a first set of aggressive RET operations on the plurality of critical regions. The system also performs a second set of less aggressive RET operations on other non-critical regions of the layout.
Owner:SYNOPSYS INC
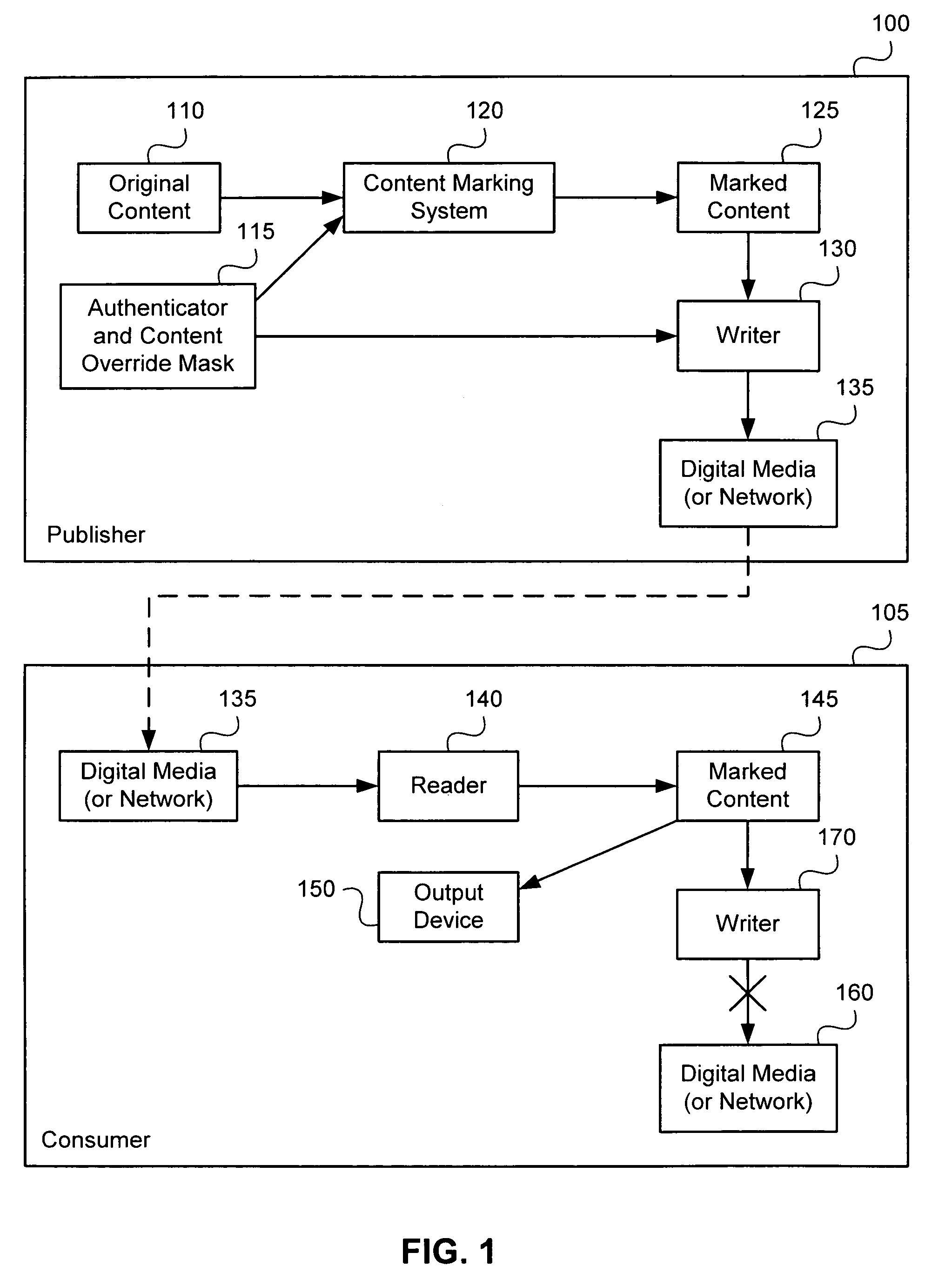
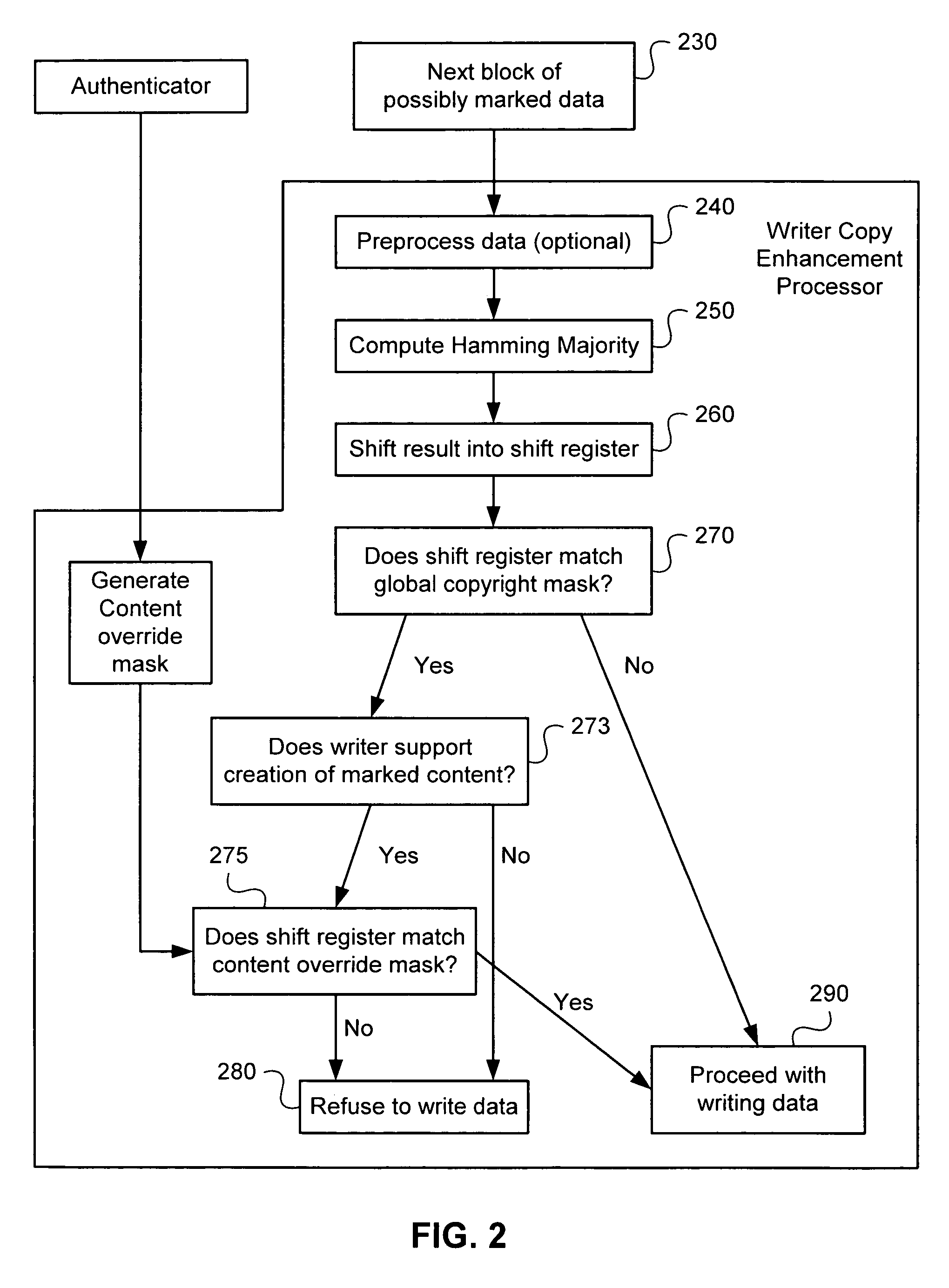
Method and system for copy-prevention of digital copyright works
InactiveUS6978370B1Obstruction is producedHighly effective copy-preventionUser identity/authority verificationTelevision systemsShift registerCoverage function
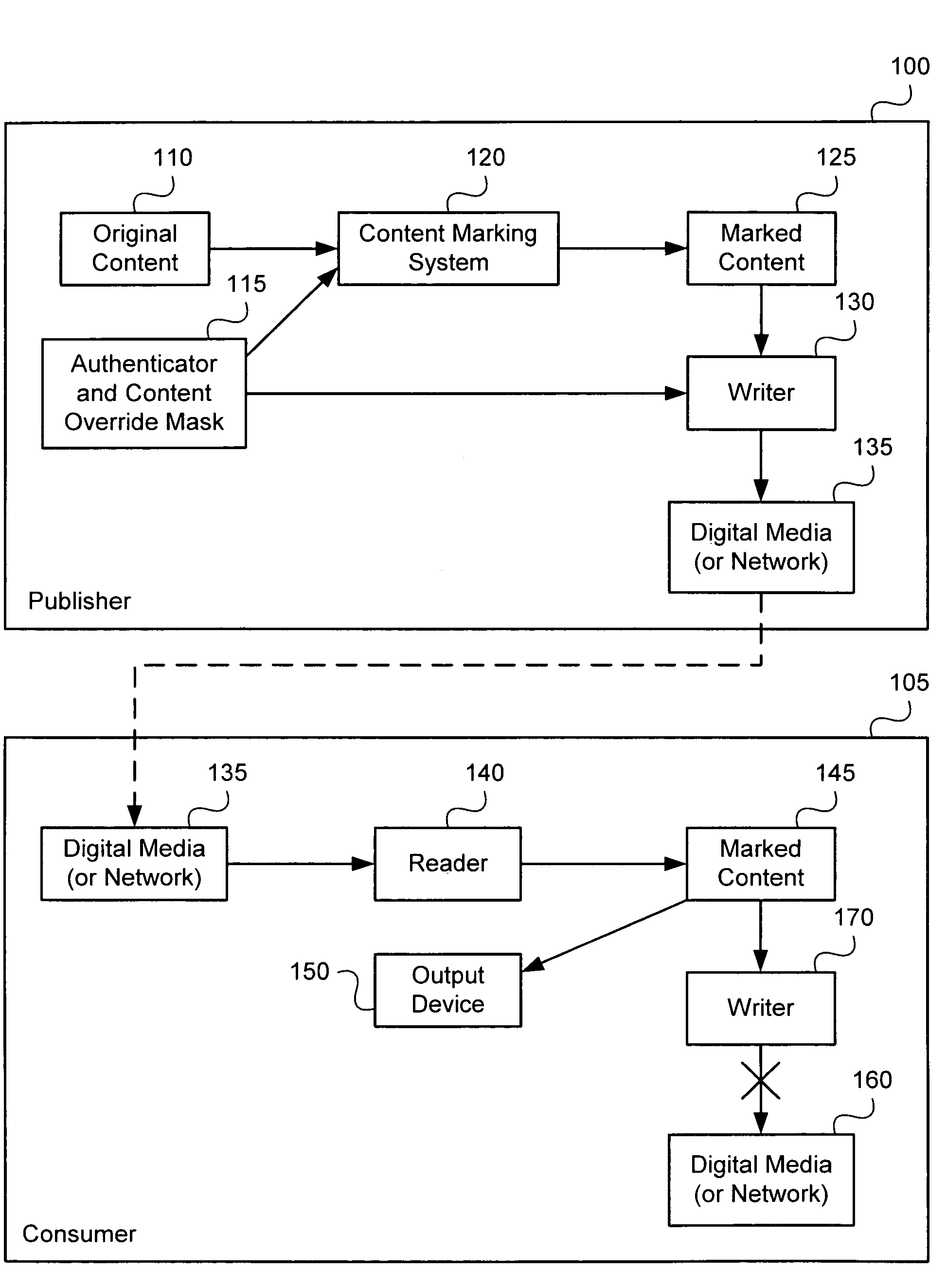
Methods and apparati for marking digital material and for detecting marks therein. For mark detection, the material is divided into a plurality of blocks, to which a non-collision resistant compression function is applied. Compression outputs are placed in a shift register, whose value is tested for predetermined values or patterns. Mark embedding may be performed by modifying the data (for example by altering low-order bits and other non-critical regions) such that the outputs of the compression operation, when used as an input to the shift register, yield a predetermined value or pattern. A Hamming Majority operation, computed as the most common bit in a block, may be used as the compression operation, enabling marking and mark detection with material of virtually all types and formats. Mark detection technology may be implemented in media writers and other devices to determine whether the digital material is copyrighted or otherwise protected. An override capability is provided to allow authorized parties to bypass the protection.
Owner:IRDETO USA
Processing sensor data
ActiveUS20140266684A1Convenient and reliable serviceConvenient and reliable and functionalityDigital data processing detailsAlarmsCritical functionNon critical
Methods, systems, computer-readable media, and apparatuses for processing sensor data are presented. In some embodiments, a security server may receive sensor data from one or more sensors that are located at a premises. Subsequently, the security server may classify a first portion of the received sensor data as critical sensor data, (e.g., based on the first portion of the received sensor data being associated with a critical function). In addition, the security server may classify a second portion of the received sensor data as non-critical sensor data (e.g., based on the second portion of the received sensor data being associated with a non-critical function). Thereafter, the security server may process the critical sensor data, and further may provide the non-critical sensor data to a network server for processing.
Owner:COMCAST CABLE COMM LLC
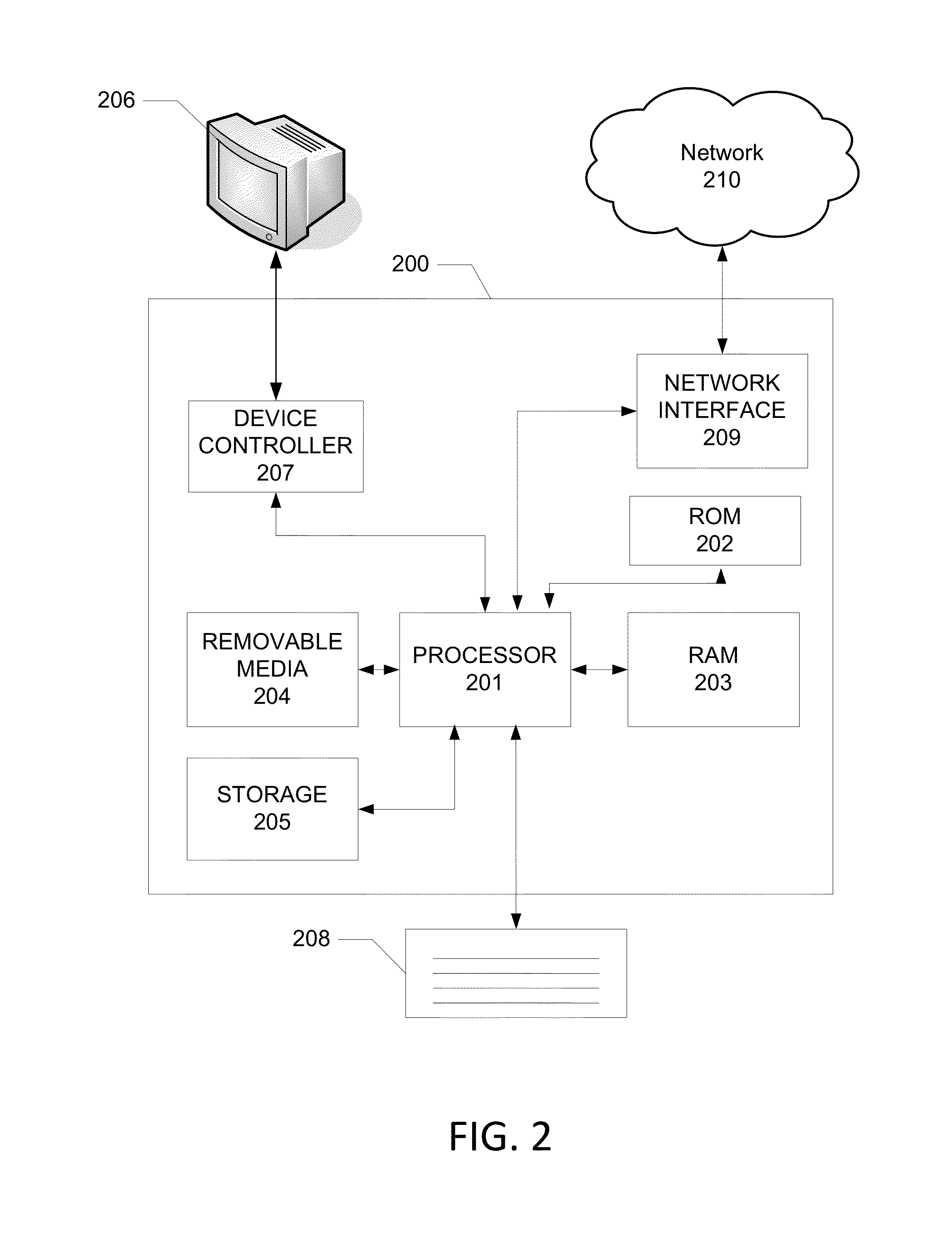
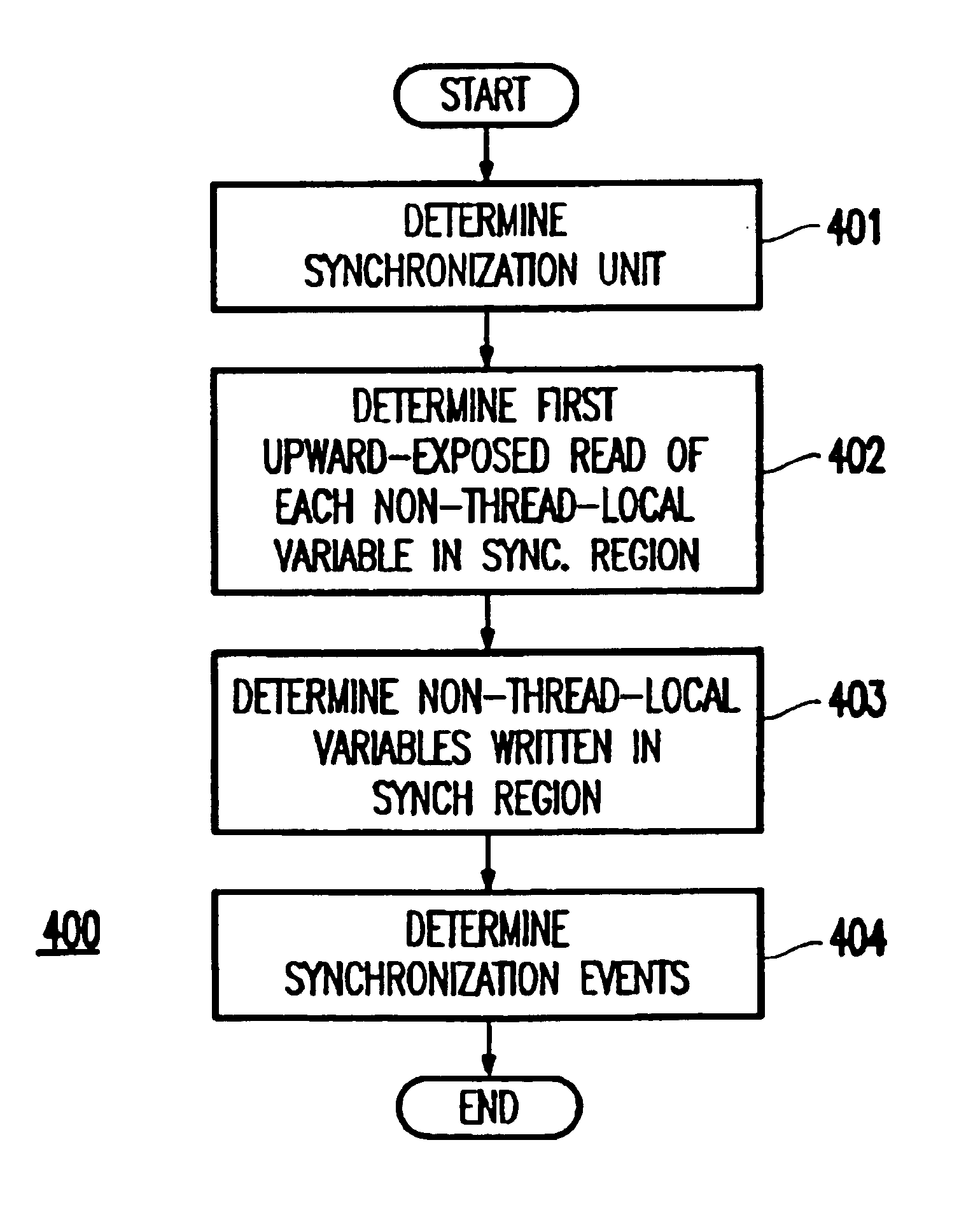
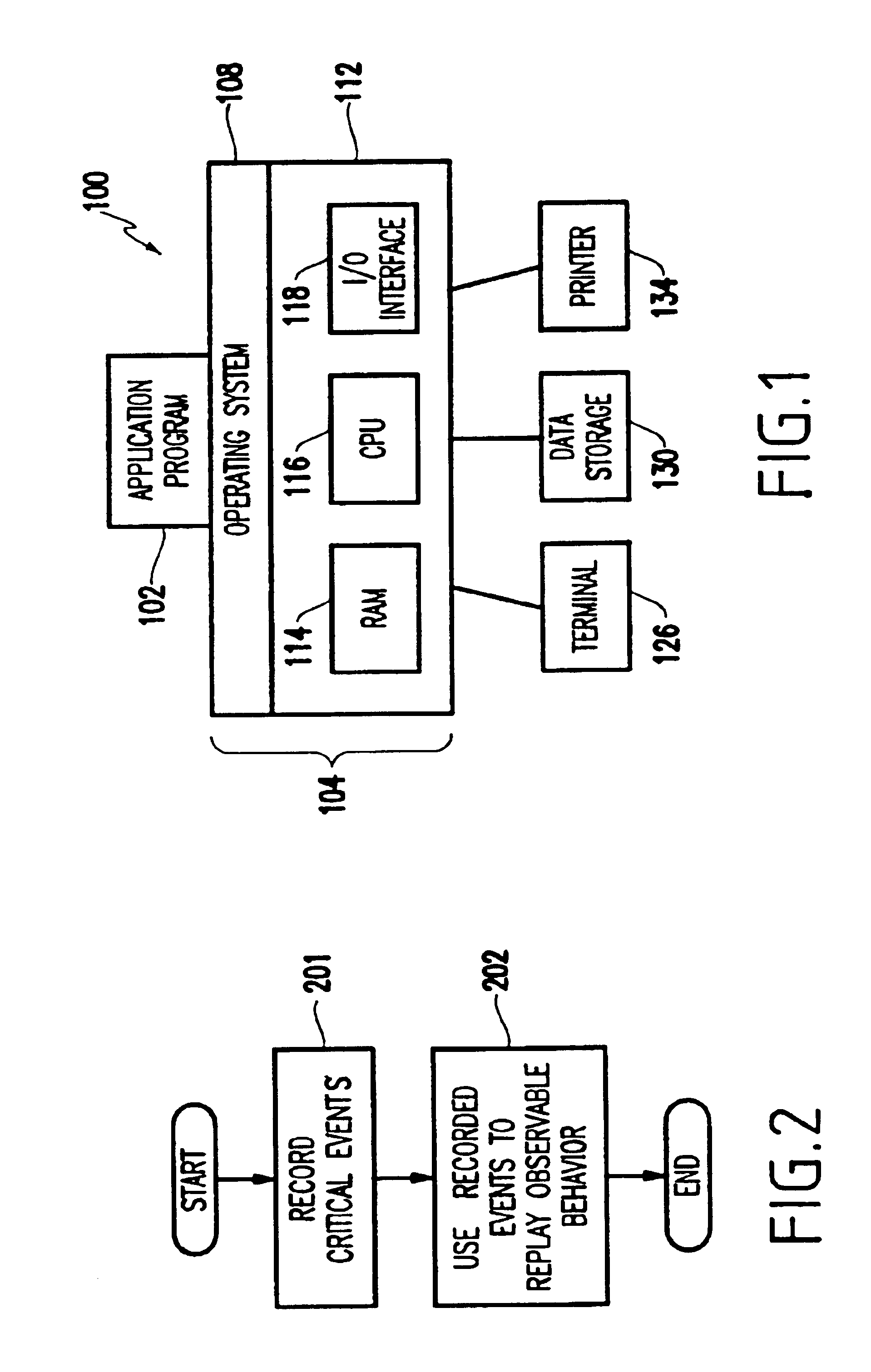
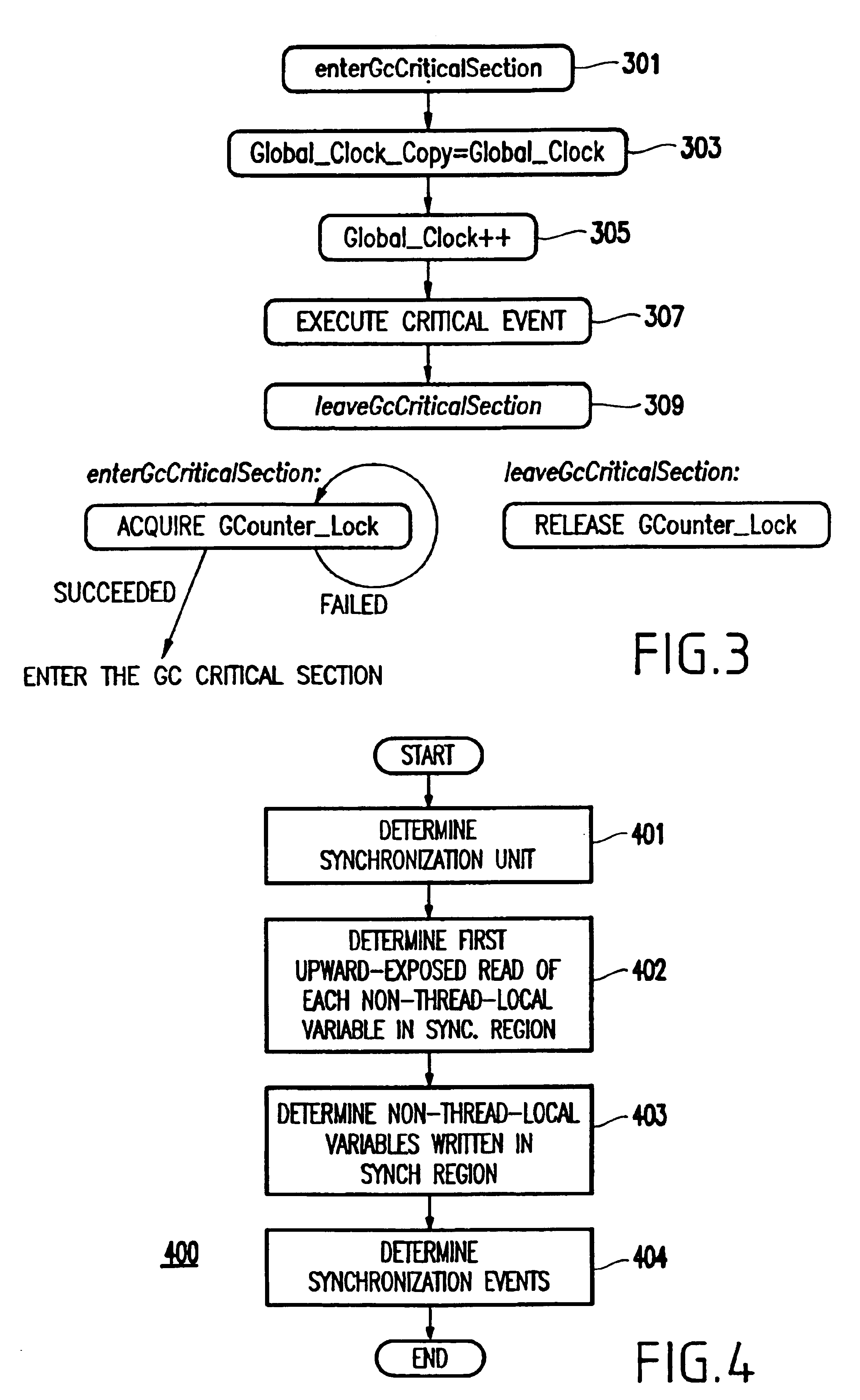
Method and apparatus for deterministic replay of java multithreaded programs on multiprocessors
InactiveUS6854108B1Reduce in quantityGood runtime performanceSoftware testing/debuggingSpecific program execution arrangementsMulti processorThread scheduling
A method (and apparatus) of determinstically replaying an observable run-time behavior of distributed multi-threaded programs on multiprocessors in a shared-memory multiprocessor environment, wherein a run-time behavior of the programs includes sequences of events, each sequence being associated with one of a plurality of execution threads, includes identifying an execution order of critical events of the program, wherein the program includes critical events and non-critical events, generating groups of critical events of the program, generating, for each given execution thread, a logical thread schedule that identifies a sequence of the groups associated with the given execution thread, and storing the logical thread schedule for subsequent reuse.
Owner:IBM CORP
Resistance memory with tungsten compound and manufacturing
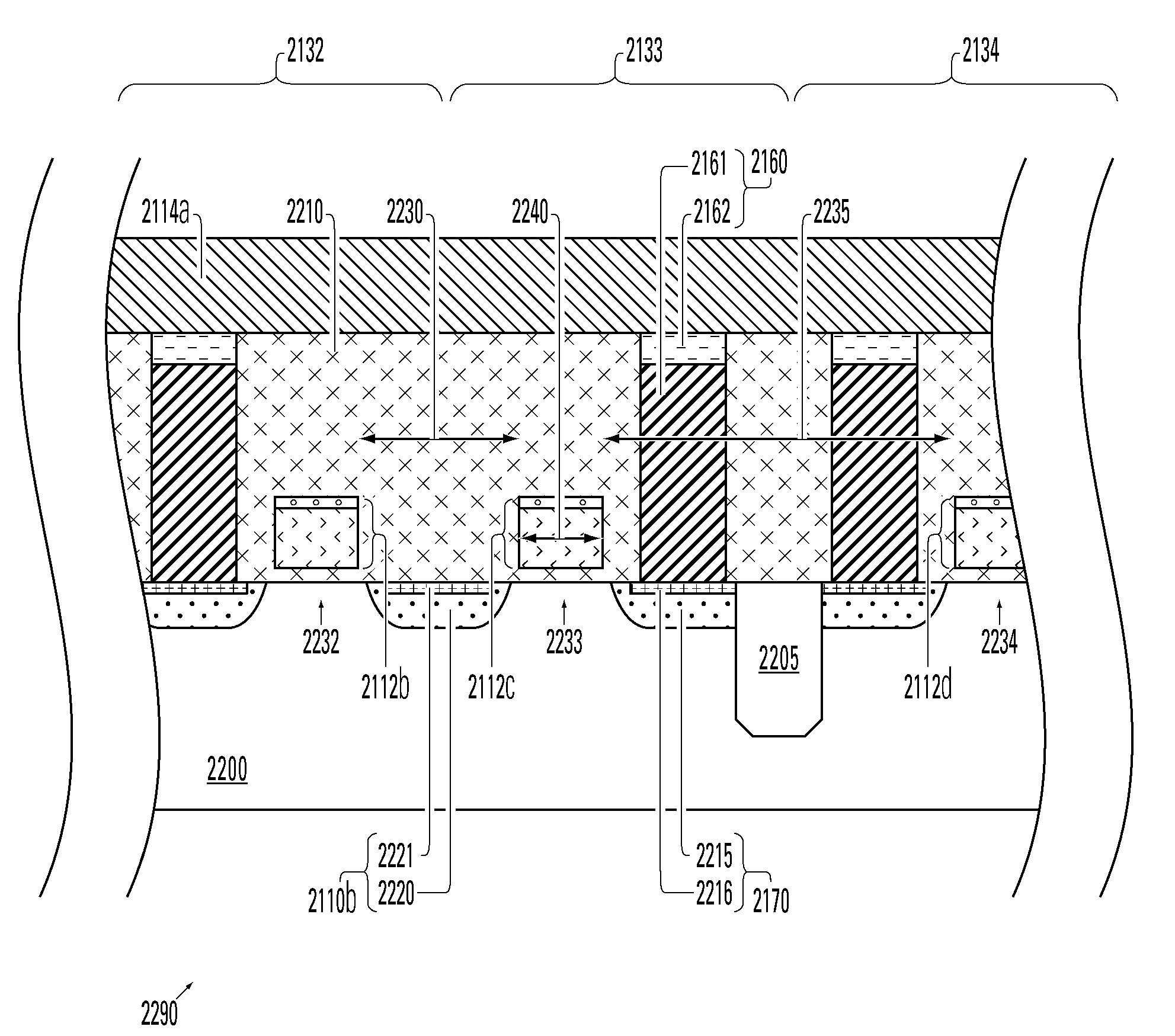
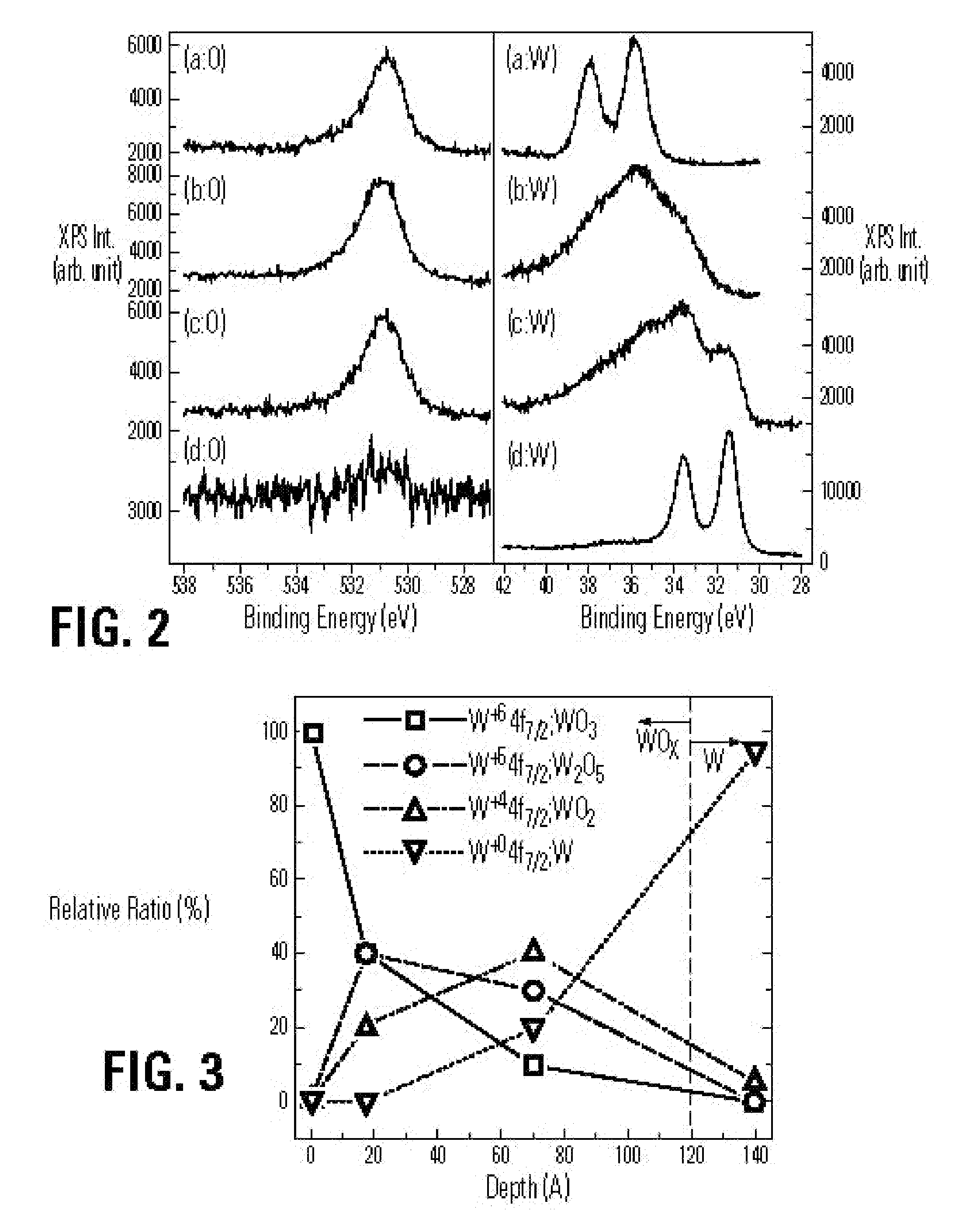
Memory devices based on tungsten-oxide memory regions are described, along with methods for manufacturing and methods for programming such devices. The tungsten-oxide memory region can be formed by oxidation of tungsten material using a non-critical mask, or even no mask at all in some embodiments. A memory device described herein includes a bottom electrode and a memory element on the bottom electrode. The memory element comprises at least one tungsten-oxygen compound and is programmable to at least two resistance states. A top electrode comprising a barrier material is on the memory element, the barrier material preventing movement of metal-ions from the top electrode into the memory element.
Owner:MACRONIX INT CO LTD
Osteogenic devices and methods of use thereof for repair of endochondral bone and osteochondral defects
InactiveUS7041641B2Avoid undesirable formationOvercome problemsPowder deliveryImpression capsRepair tissueNon union
Disclosed herein are improved osteogenic devices and methods of use thereof for repair of bone and cartilage defects. The devices and methods promote accelerated formation of repair tissue with enhanced stability using less osteogenic protein than devices in the art. Defects susceptible to repair with the instant invention include, but are not limited to: critical size defects, non-critical size defects, non-union fractures, fractures, osteochondral defects, subchondral defects, and defects resulting from degenerative diseases such as osteochondritis dessicans.
Owner:MARIEL THERAPEUTICS
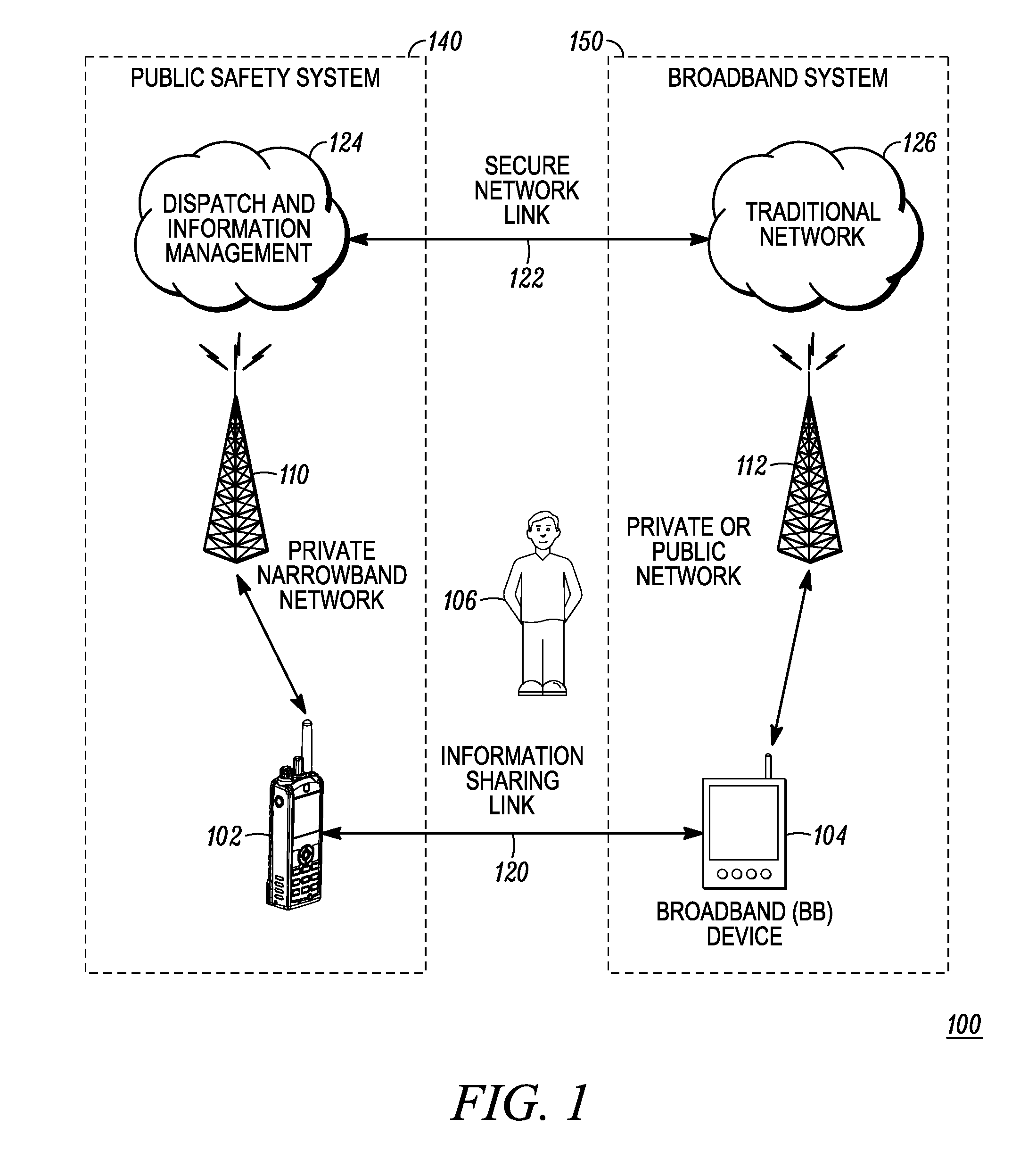
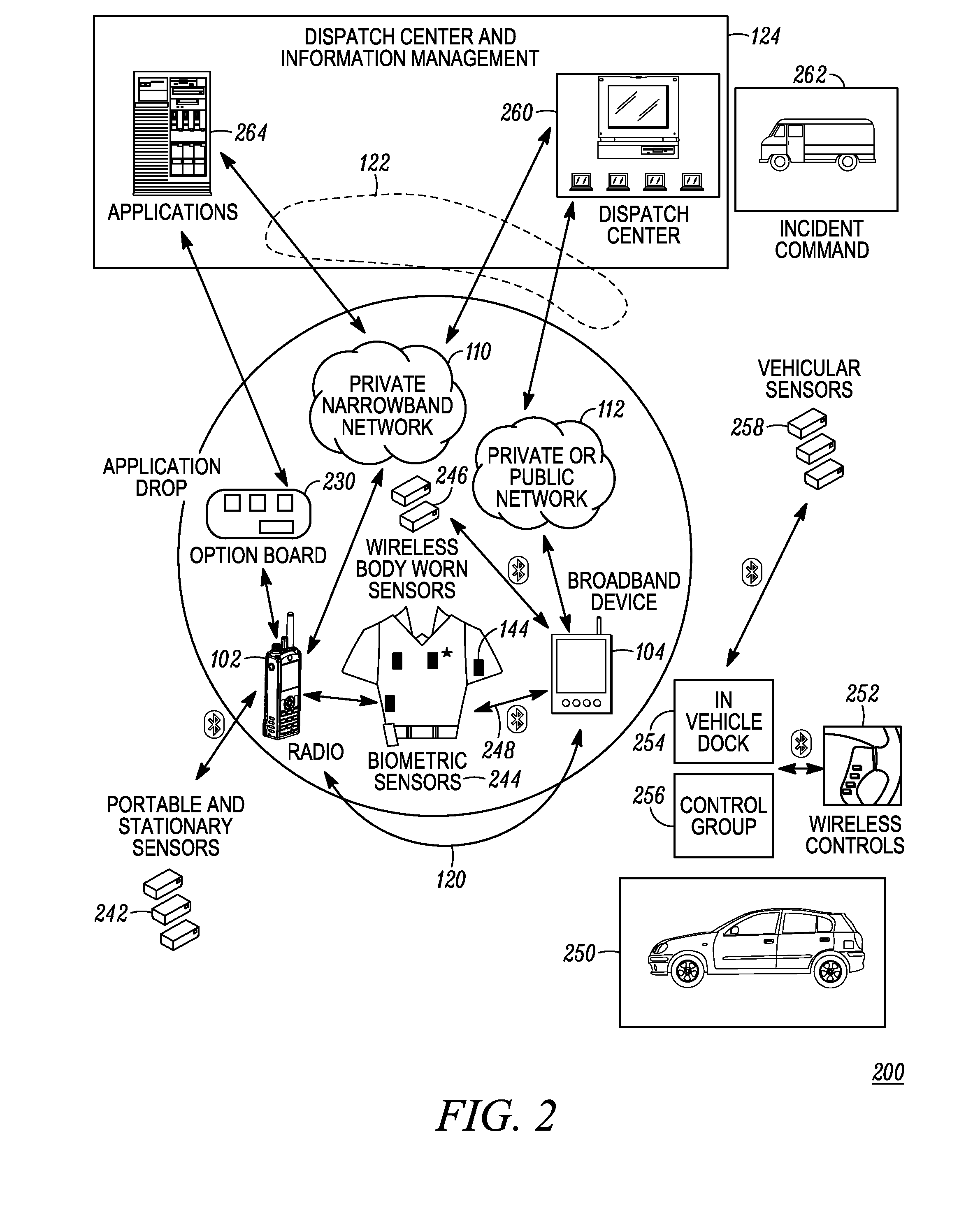
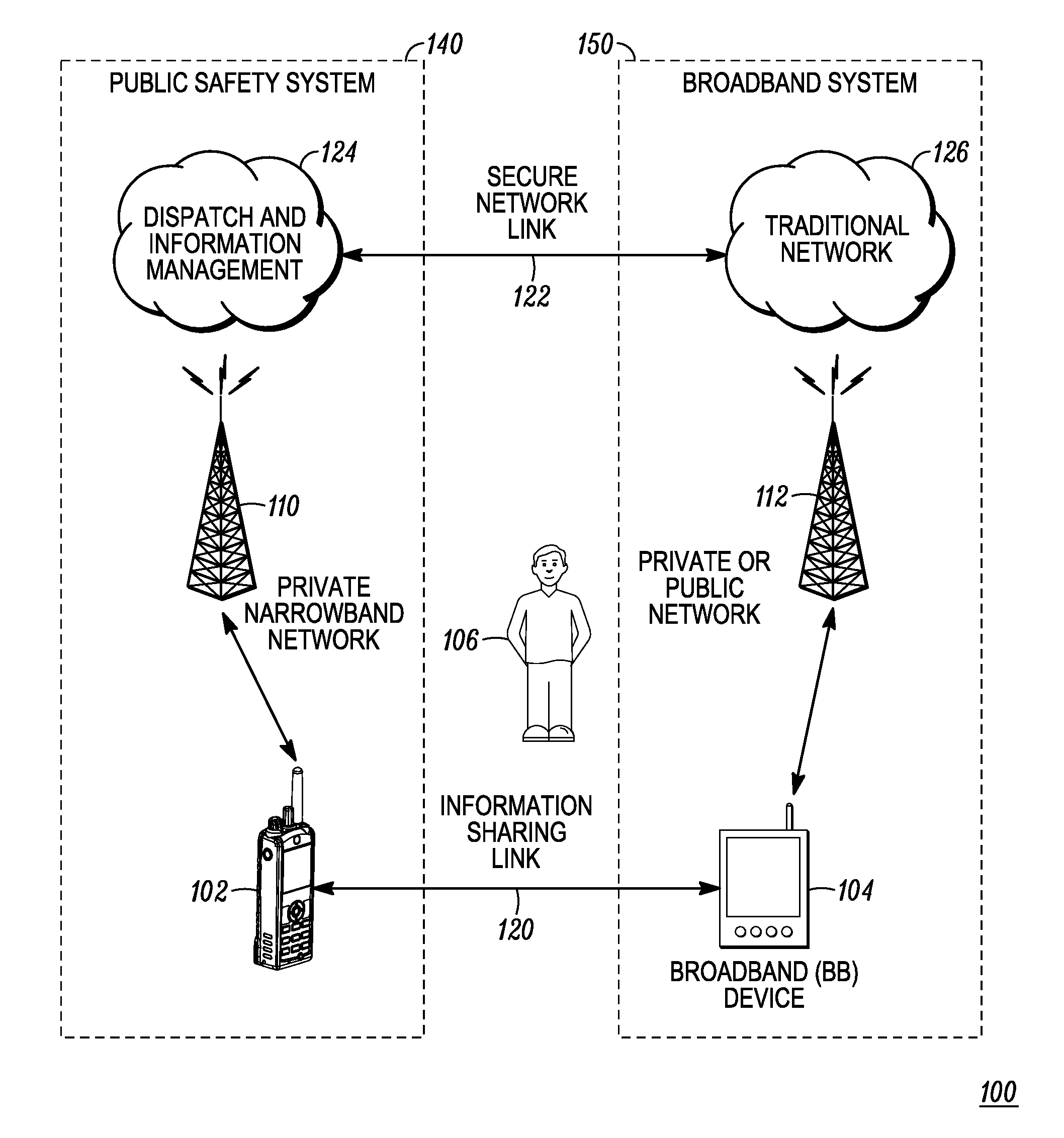
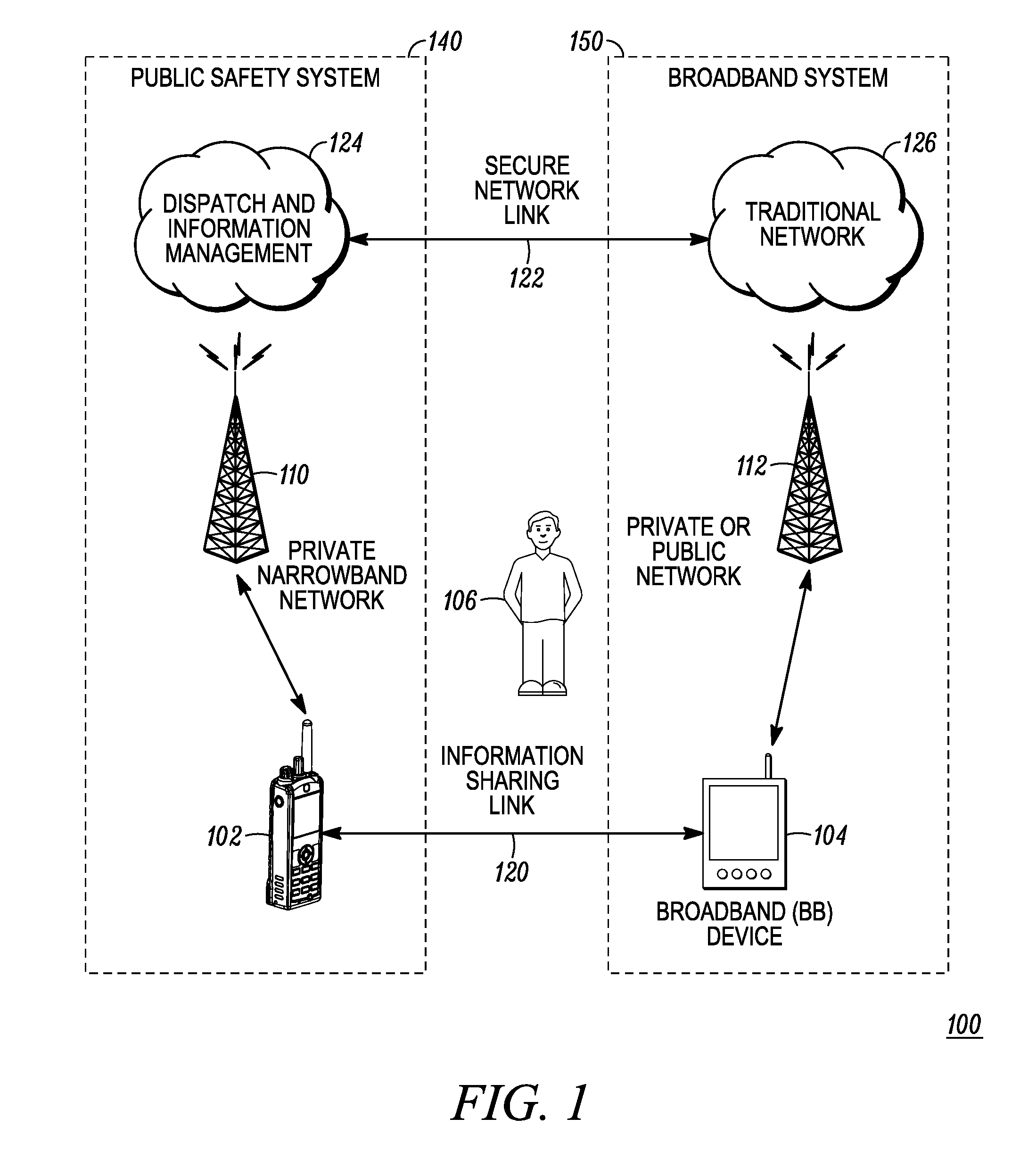
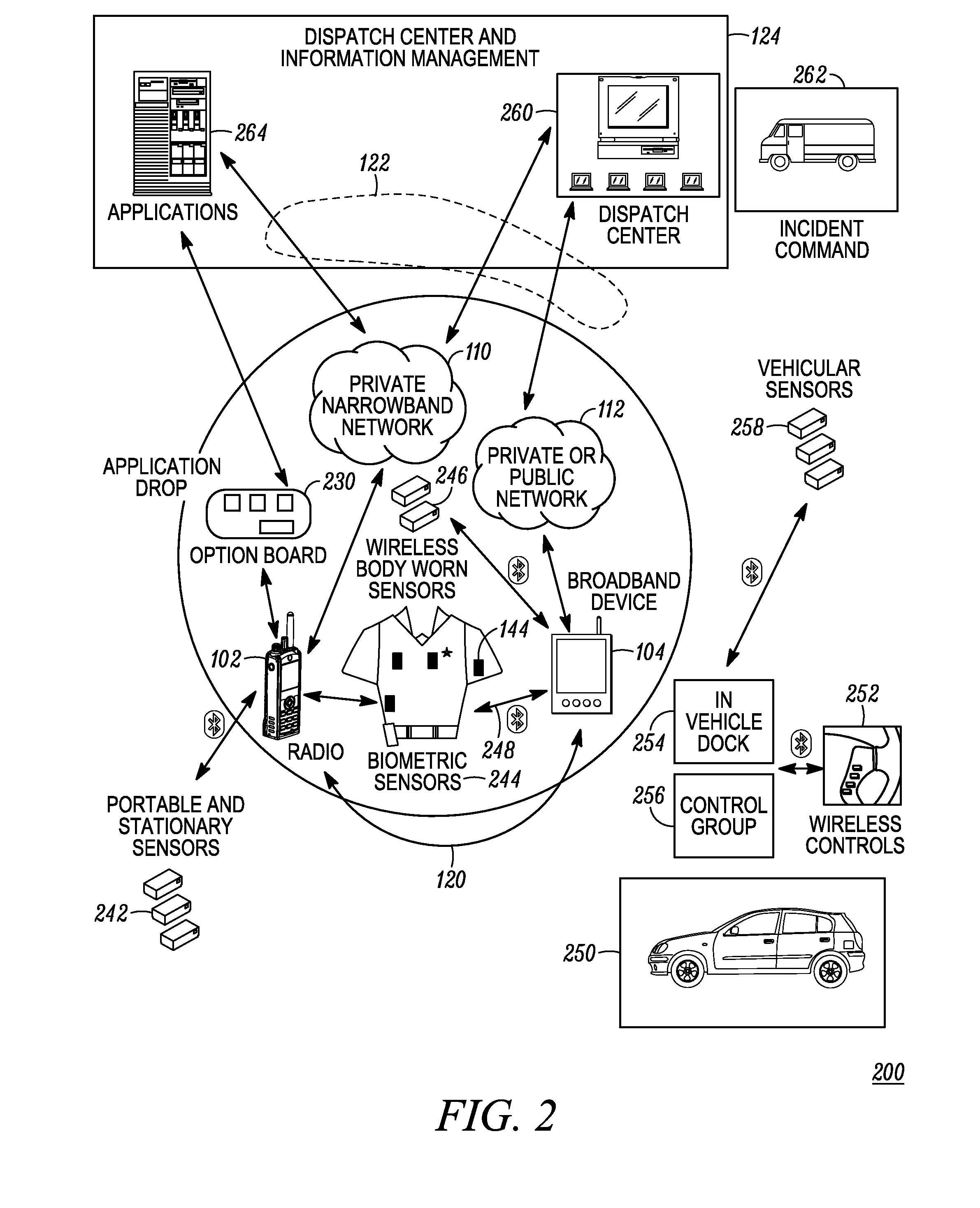
Enhanced public safety communication system
ActiveUS20110237287A1Emergency connection handlingNetwork topologiesCommunication deviceBroadband communication
A communication system (100) provides collaboration between narrowband communication devices (102) and broadband communication devices (104) operating over different networks. The communication devices (102, 104) are linked to provide peer-to-peer communication that supports the dissemination of public safety information to a public safety personnel user utilizing the devices. Applications within the devices (102, 104) automatically control features amongst the plurality of devices for redundancy of critical information, removal of non-critical information and power management. Context information can also be examined and shared between amongst the devices.
Owner:MOTOROLA SOLUTIONS INC
Flexible cable for high-speed interconnect
InactiveUS20060067066A1Coupling device connectionsLine/current collector detailsElectric power transmissionHigh velocity
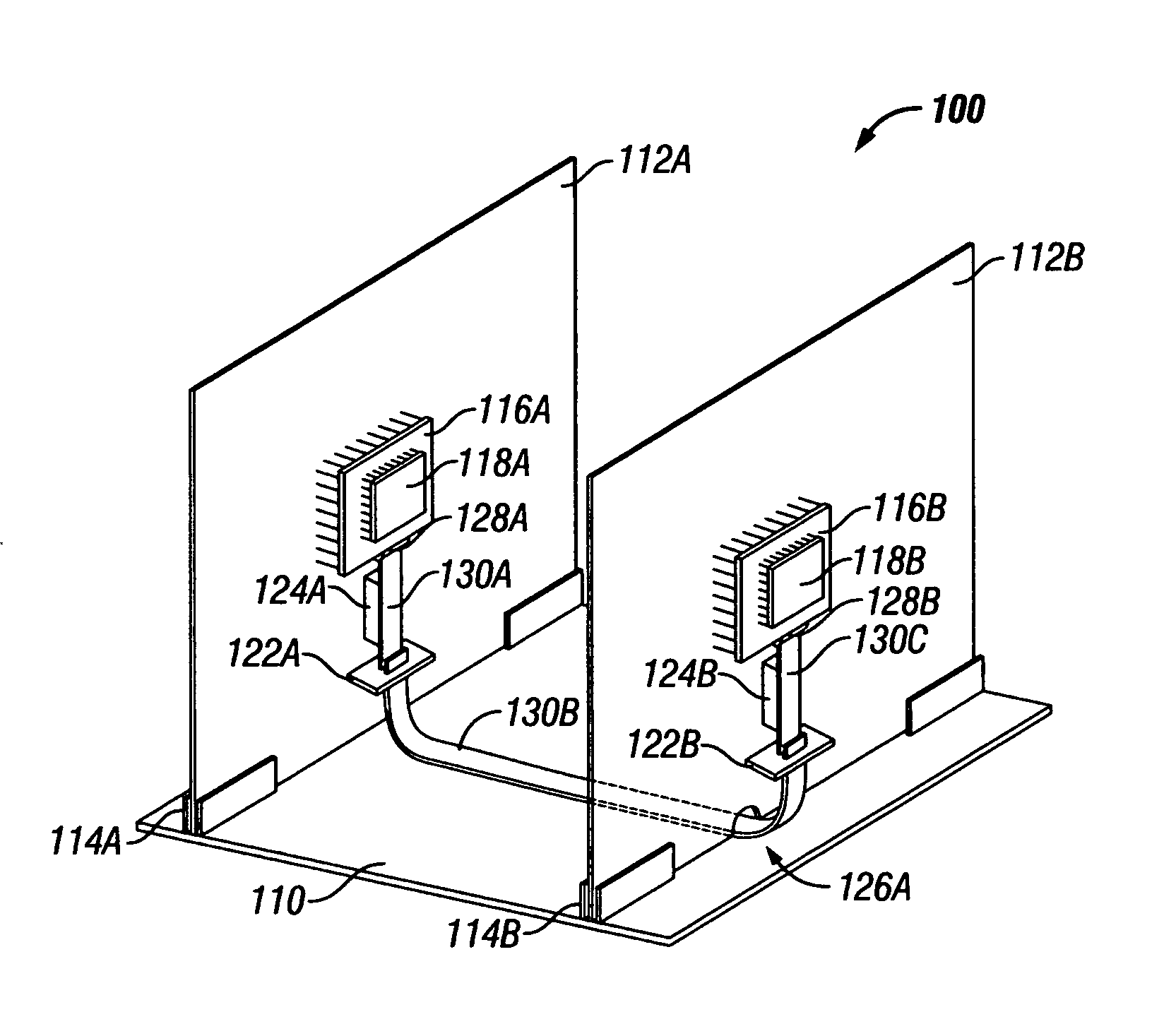
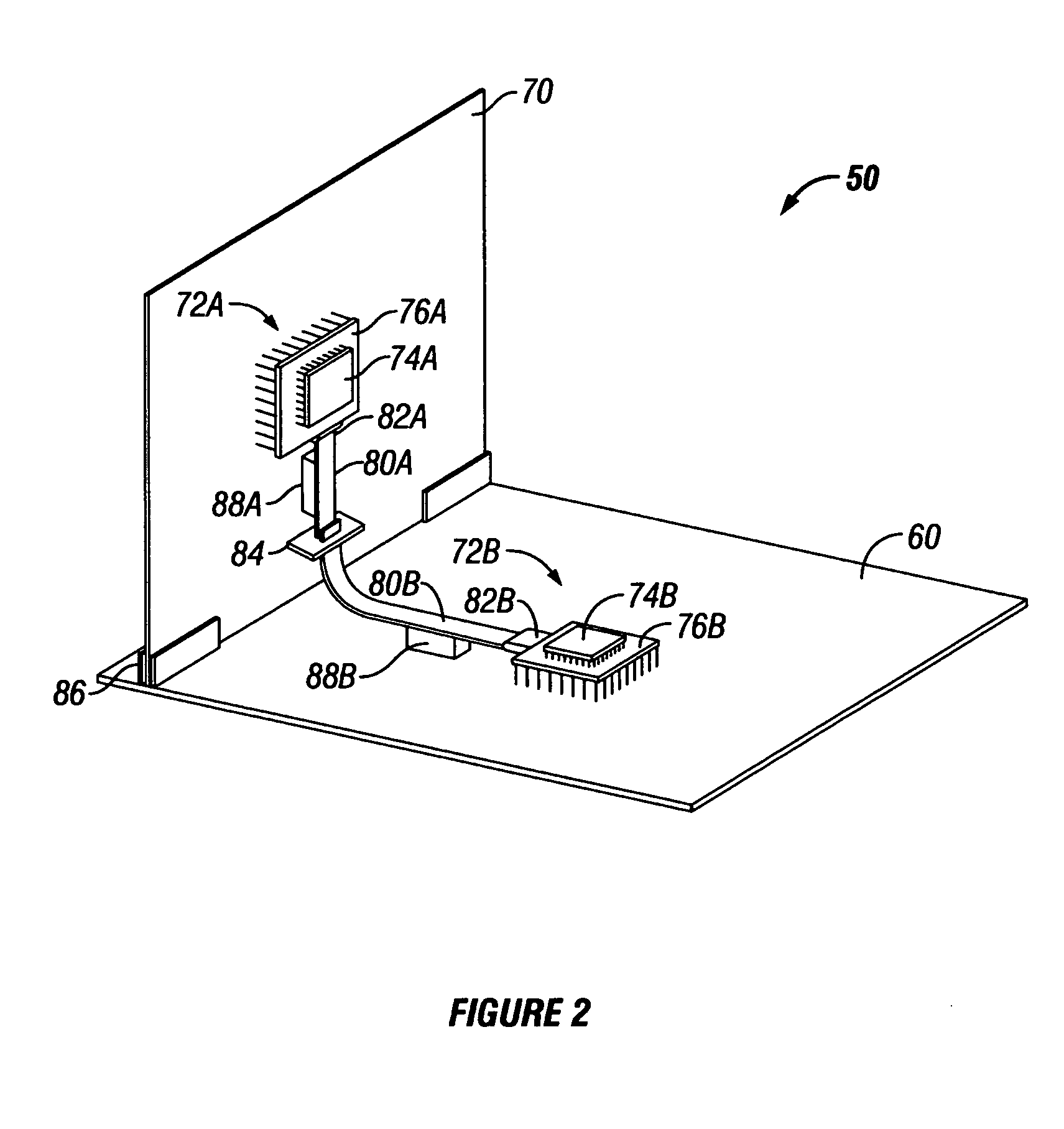
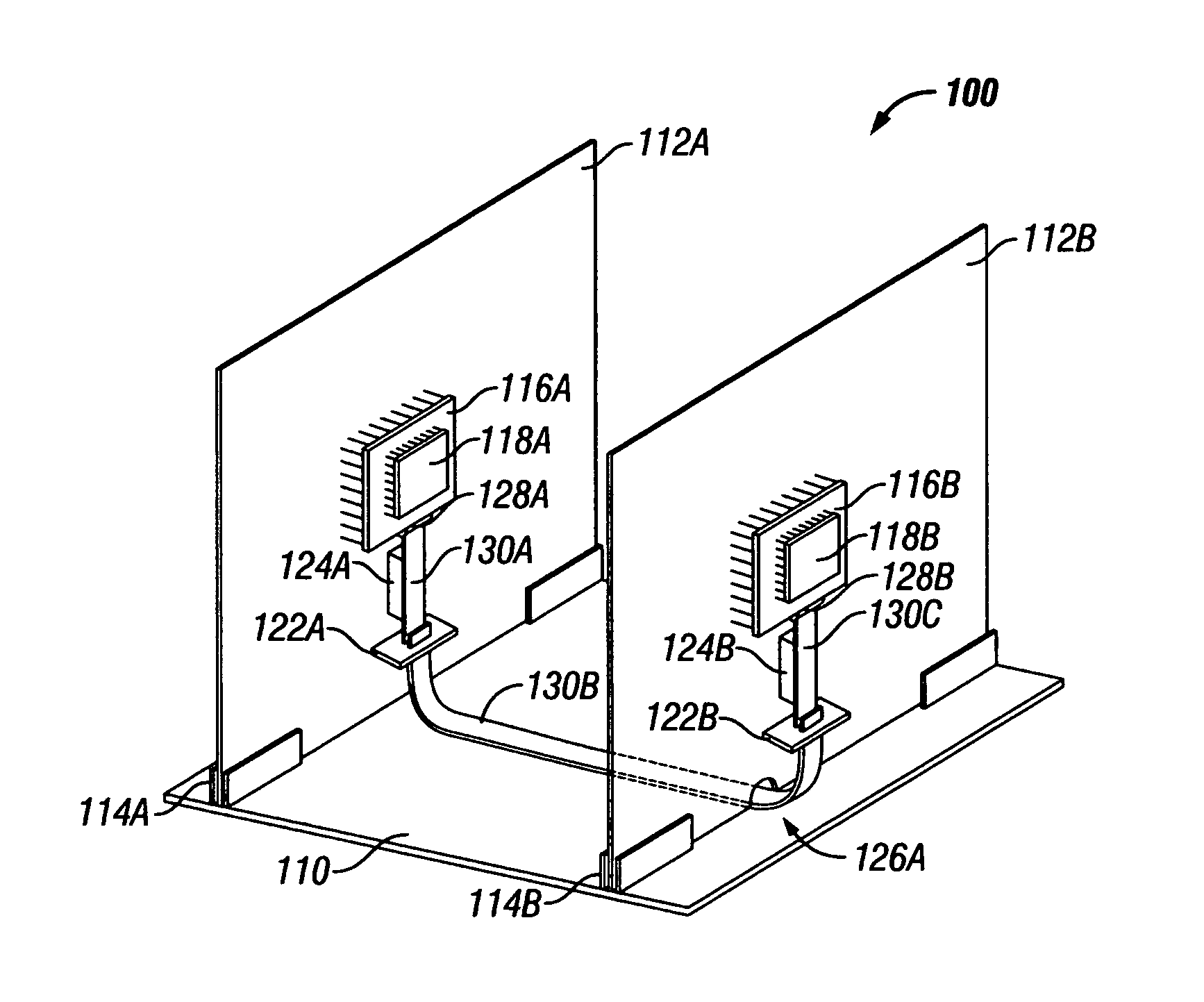
A system and method are disclosed in which flex cables are affixed to PCBs, for providing high-speed signaling paths between ICs disposed upon the PCBs. The flex cables are fixably attached to the PCBs so as to substantially mimic their structural orientation. Where the configuration includes more than one PCB, the flex cables include multiple portions which are temporarily separable from one another and from the die, using flex-to-flex and flex-to-package connectors, allowing field maintenance of the configuration. By routing the high-speed signals between ICs onto the flex cable, single-layer PCBs can be used for non-critical and power delivery signals, at substantial cost savings. By disposing the flex cables onto the PCB rather than allowing the cables to float freely, the configuration is thermally managed as if the signals were on the PCB and cable routing problems are avoided.
Owner:INTEL CORP
Flexible cable for high-speed interconnect
InactiveUS7148428B2Coupling device connectionsLine/current collector detailsElectric power transmissionEngineering
A system and method are disclosed in which flex cables are affixed to PCBs, for providing high-speed signaling paths between ICs disposed upon the PCBs. The flex cables are fixably attached to the PCBs so as to substantially mimic their structural orientation. Where the configuration includes more than one PCB, the flex cables include multiple portions which are temporarily separable from one another and from the die, using flex-to-flex and flex-to-package connectors, allowing field maintenance of the configuration. By routing the high-speed signals between ICs onto the flex cable, single-layer PCBs can be used for non-critical and power delivery signals, at substantial cost savings. By disposing the flex cables onto the PCB rather than allowing the cables to float freely, the configuration is thermally managed as if the signals were on the PCB and cable routing problems are avoided.
Owner:INTEL CORP
Planning method and planning device for knee implants
ActiveUS20050251065A1Overcome disadvantagesSurgical navigation systemsPerson identificationTibiaKnee Joint
A planning method and device for knee implants, wherein spatial data on the configuration of a patient's genicular anatomy, in particular of at least a part of the femur and / or the patella and / or the tibia, are captured in order to be inputted into a computer-assisted planning station; the movement of the parts of the genicular anatomy is recorded using a tracking and / or motion capturing method; the captured anatomical and movement data are made available to the computer-assisted planning station; a part of the patient's genicular anatomy is virtually replaced in the planning station by a sample implant and movements of the knee together with the sample implant are simulated; contact and impingement between the non-replaced parts of the genicular anatomy and the implant during the virtual movement is ascertained according to its magnitude; and wherein an adjustment of the positioning, shape or orientation of the implant or of a number of these parameters is determined until the contact and impingement become non-critical and the adjustment thus determined is defined as a suitable adjustment.
Owner:BRAINLAB
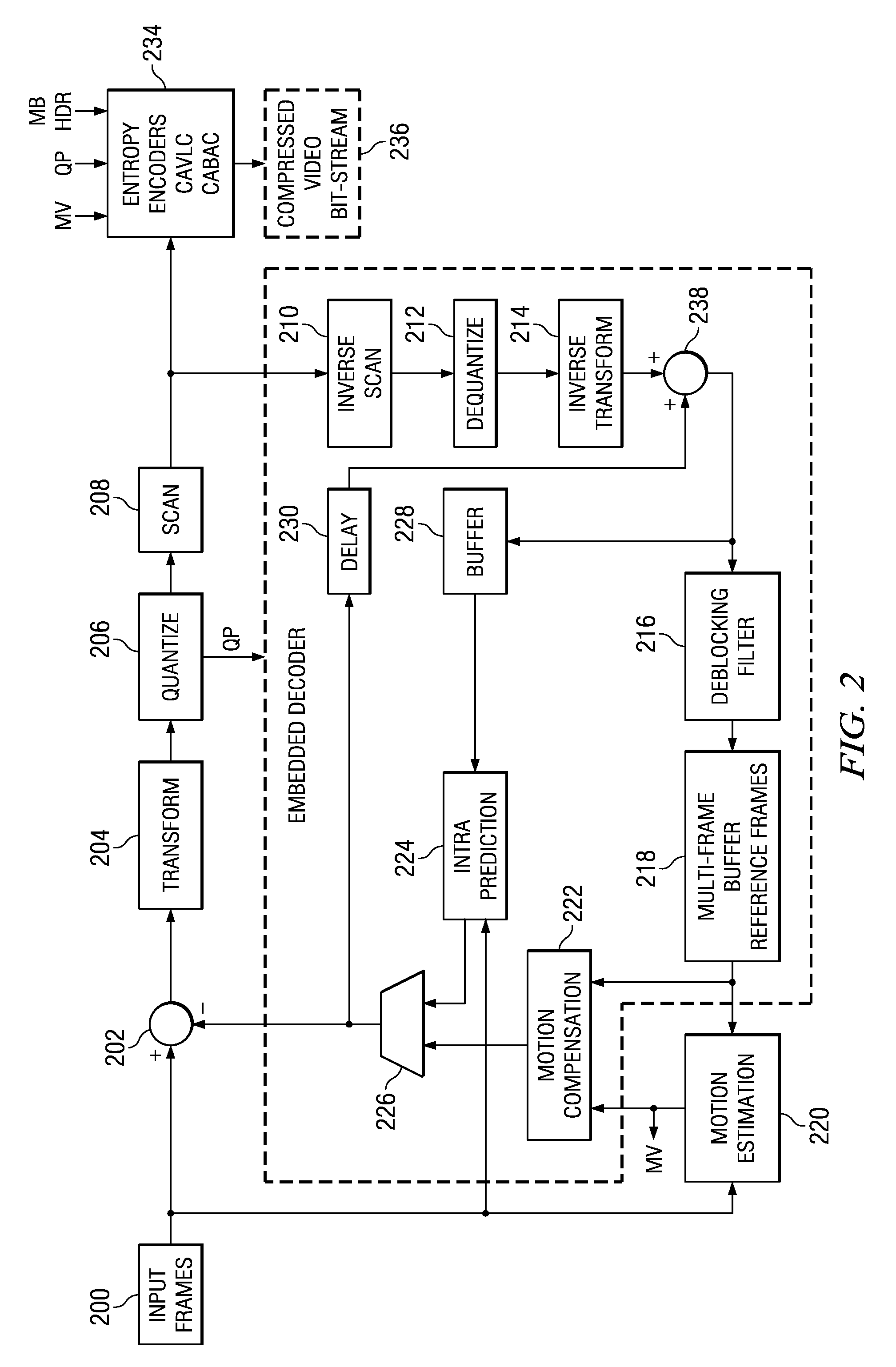
Error Resilience in Video Decoding
InactiveUS20100246683A1Color television with pulse code modulationColor television with bandwidth reductionPattern recognitionImage resolution
A method for decoding an encoded video stream is provided that includes when a sequence parameter set in the encoded video stream is lost, wherein the sequence parameter set includes a frame number parameter, a picture order count parameter, a picture height parameter, a picture width parameter, and a plurality of non-critical parameters, assigning default values to the plurality of non-critical parameters, setting the picture height parameter and the picture width parameter based on a common pixel resolution, when a slice header of an instantaneous decoding refresh picture is available, determining the frame number parameter from the slice header, and determining the picture order count parameter using the frame number parameter, the default values, the pixel height parameter, and the picture width parameter, and using the parameters to decode a slice in the encoded video stream.
Owner:TEXAS INSTR INC
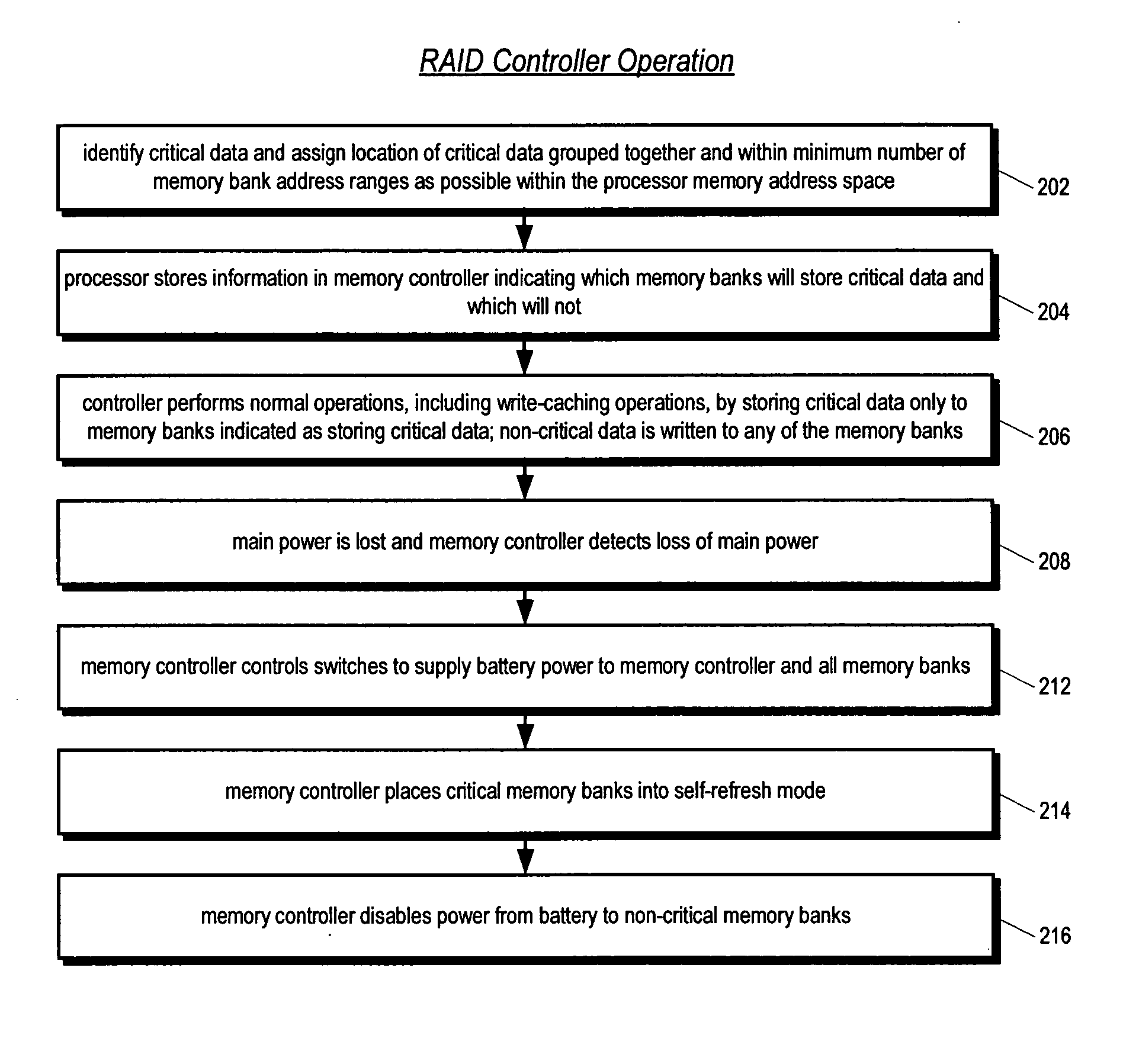
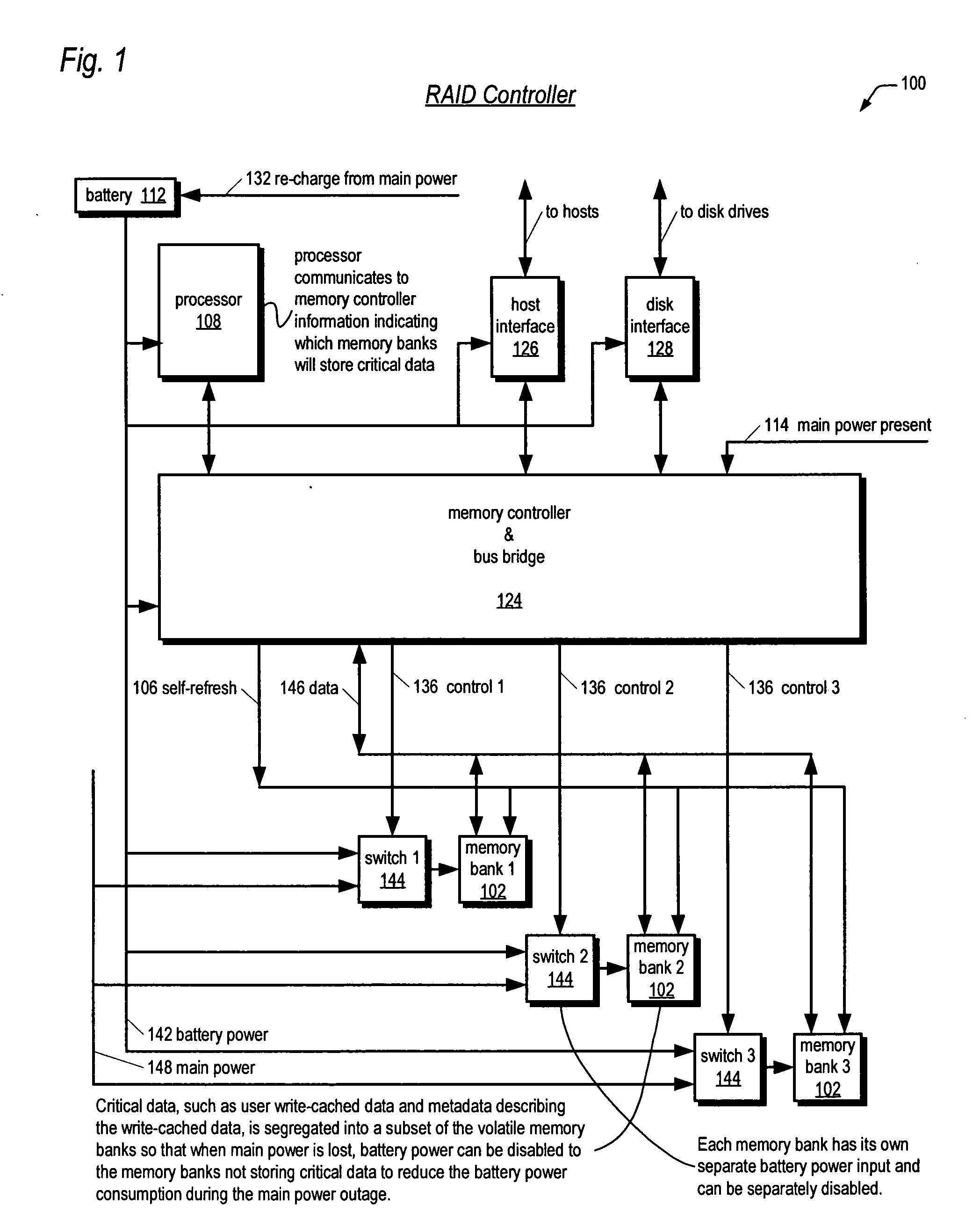
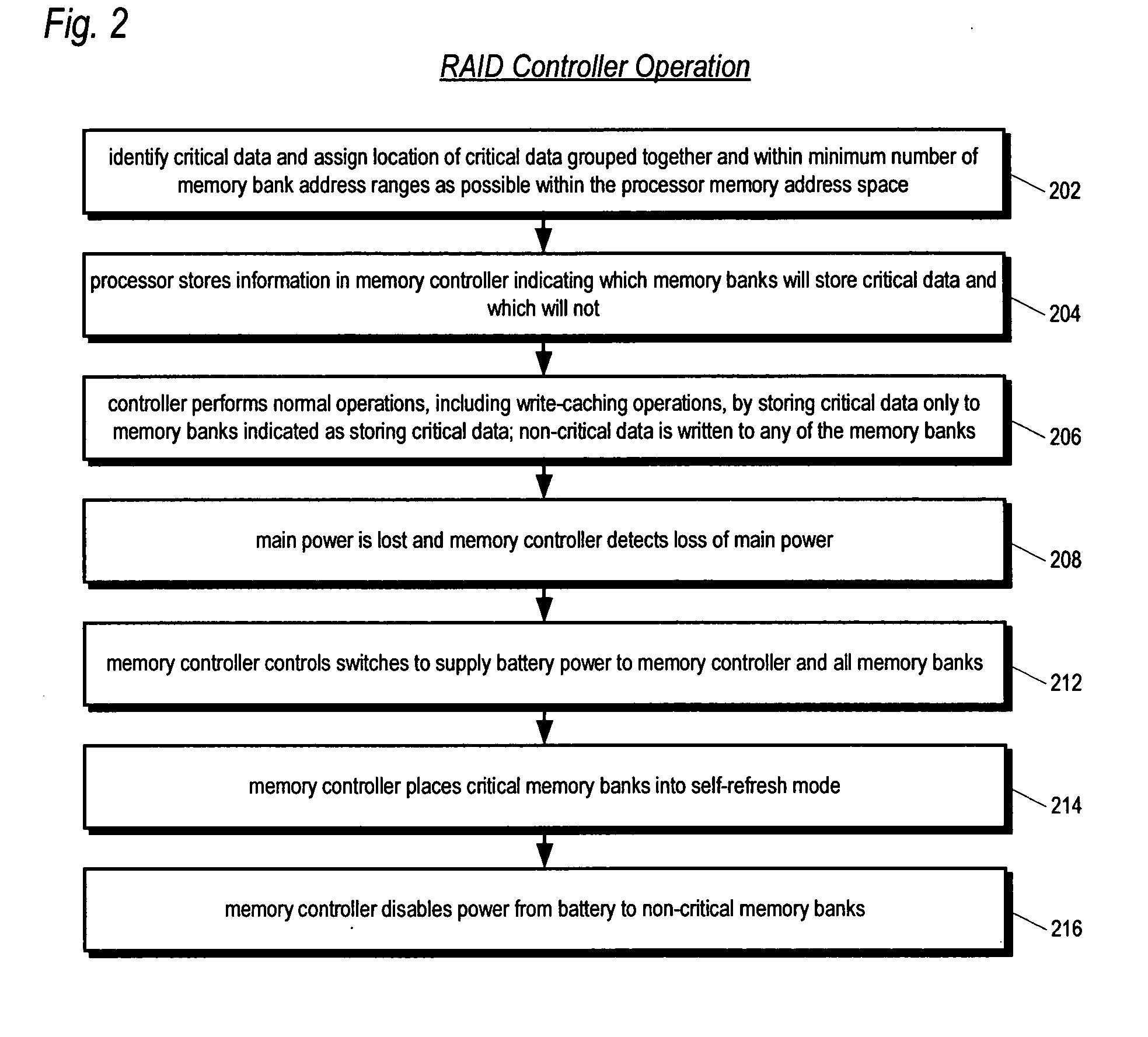
Mass storage controller with apparatus and method for extending battery backup time by selectively providing battery power to volatile memory banks not storing critical data
ActiveUS20060212651A1Reduce the amount requiredExtension of timeMemory architecture accessing/allocationEnergy efficient ICTMass storageMemory bank
A battery-backed write-caching mass storage controller is disclosed. The controller includes a plurality of volatile memory banks for caching write data prior to being written to disk drives. Critical data is stored into a first subset of the memory banks, leaving a second subset of memory banks storing only non-critical data. Critical data is data that must be retained during a main power loss to avoid loss of write-cached user data. Critical data includes the write-cached user data itself, as well as metadata describing the write-cached user data. When the controller detects a loss of main power, the controller causes the critical memory banks to receive battery power, but disables battery power to the non-critical memory banks in order to extend the length of time the critical memory banks can continue to receive battery power to reduce the likelihood of user data loss.
Owner:DOT HILL SYST
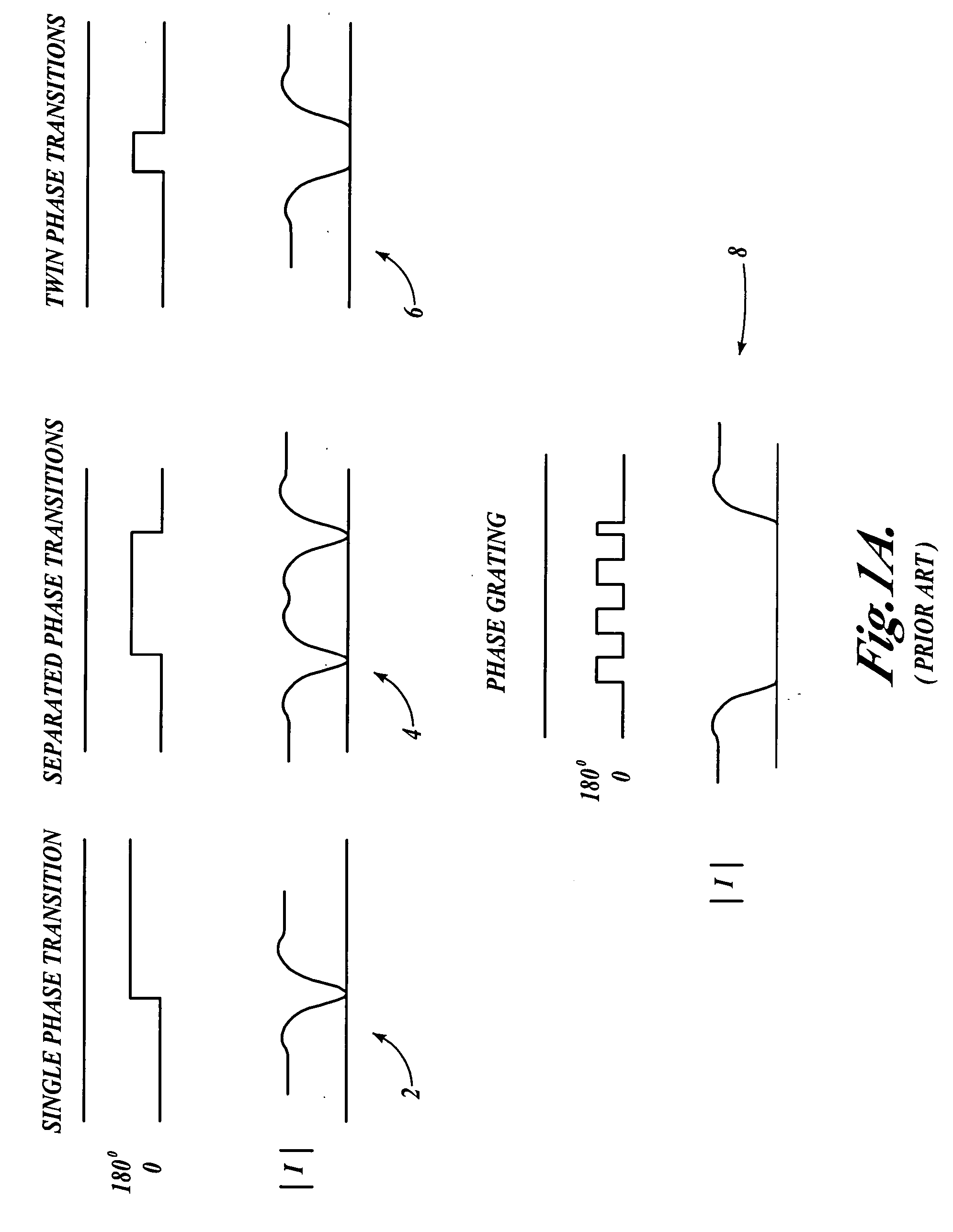
Method, program product and apparatus for performing double exposure lithography
InactiveUS20060277521A1Photomechanical apparatusSemiconductor/solid-state device manufacturingLithographic artistPhase shifted
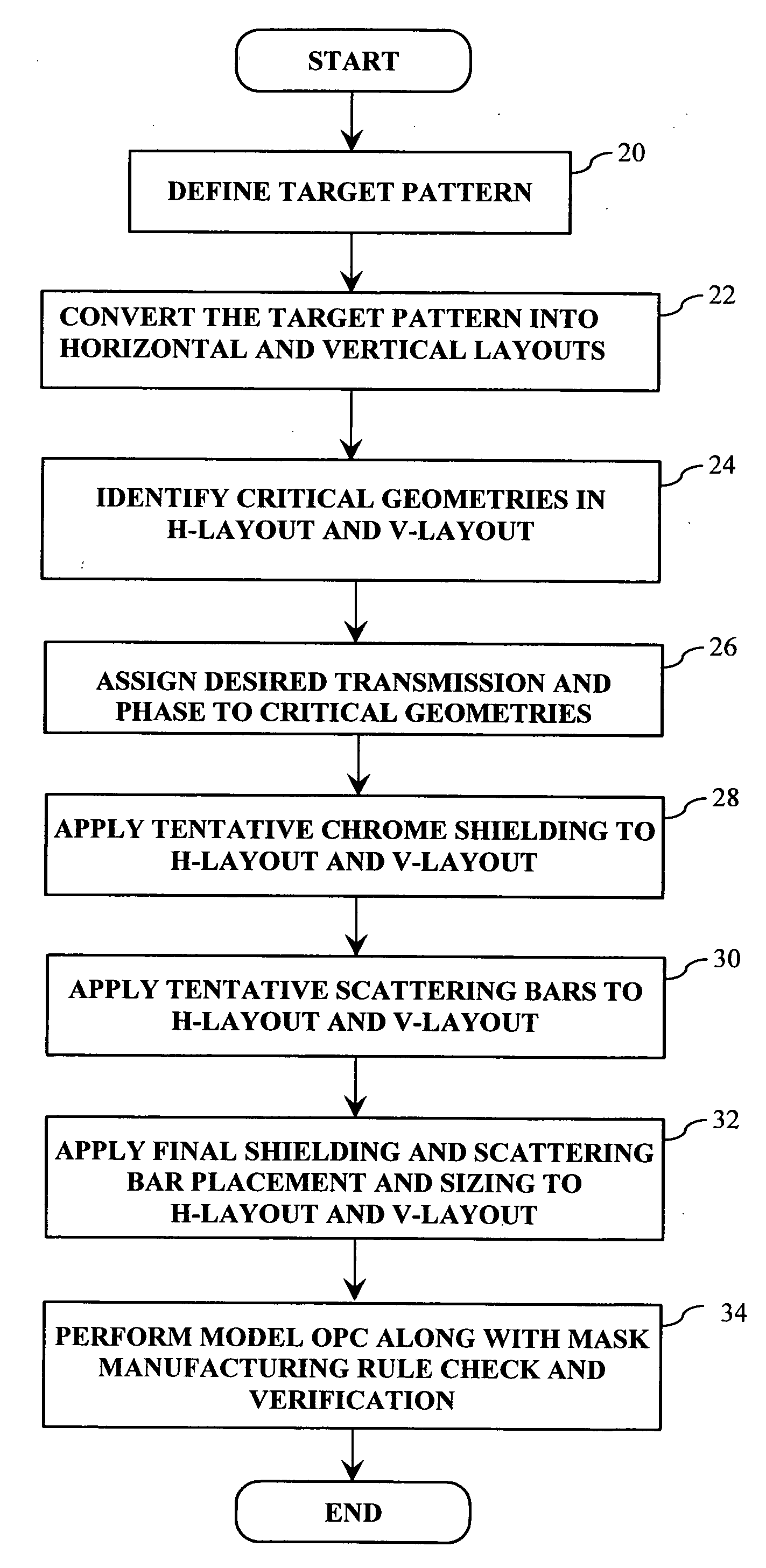
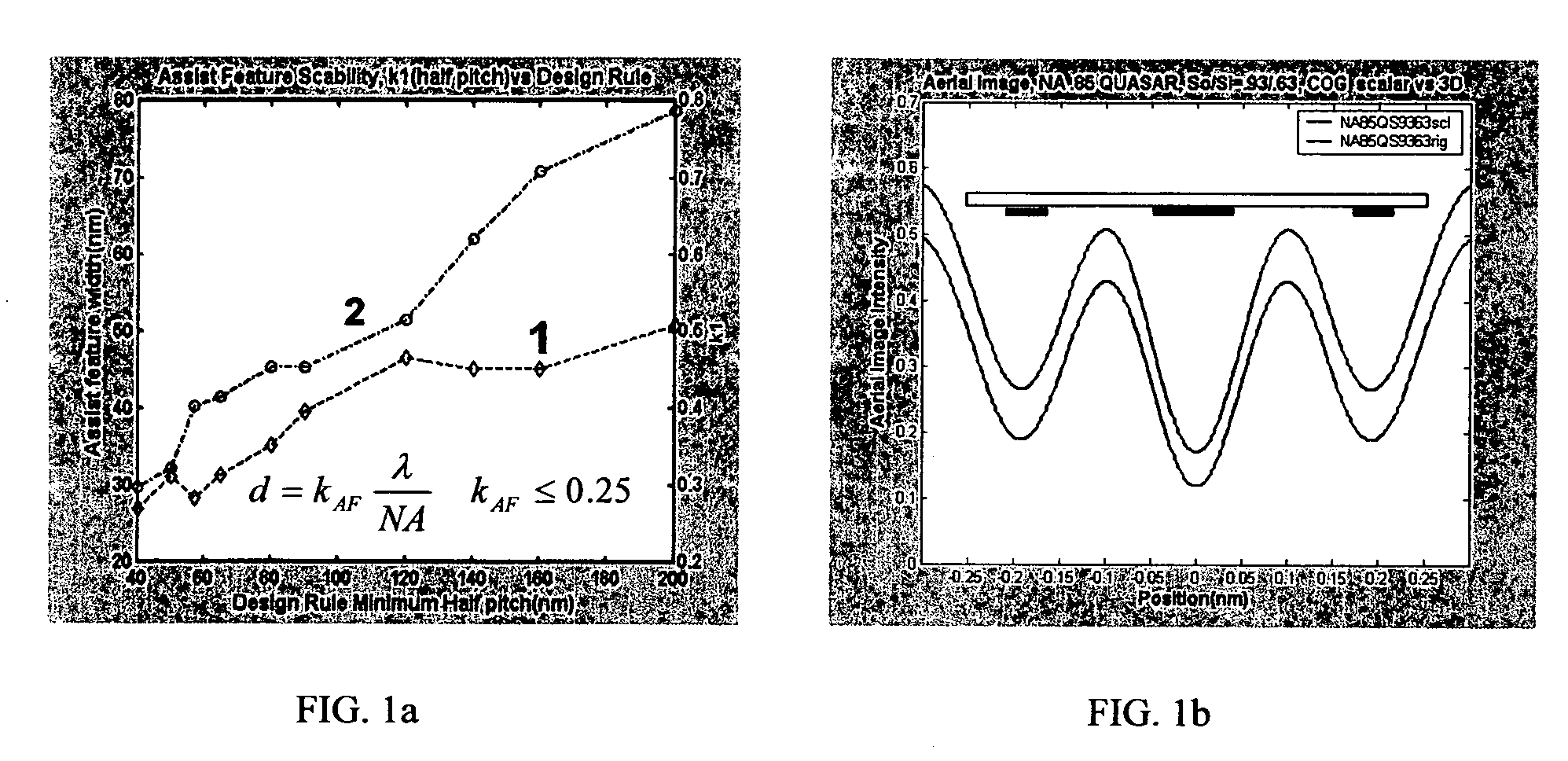
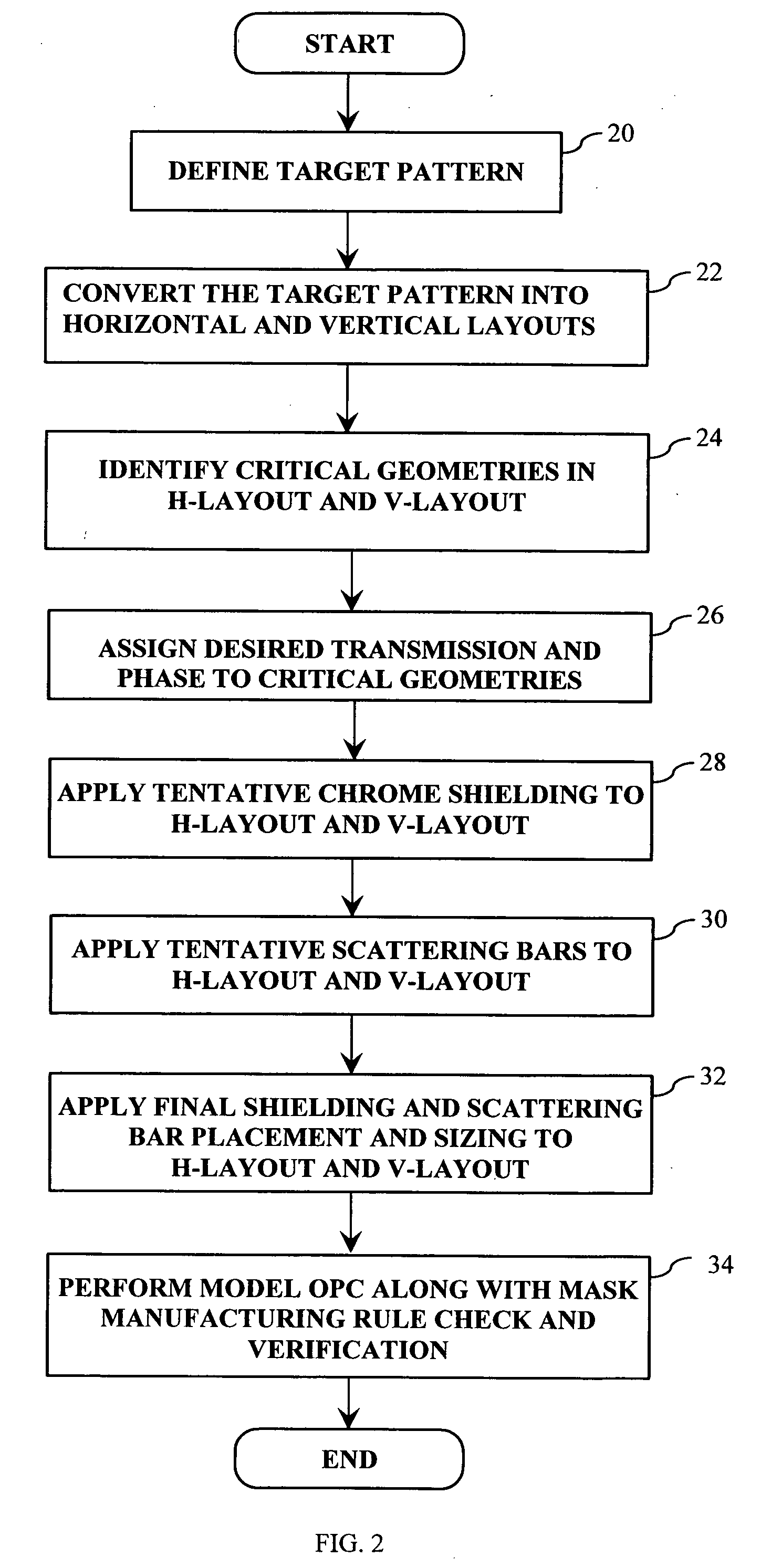
A method of generating complementary masks based on a target pattern having features to be imaged on a substrate for use in a multiple-exposure lithographic imaging process. The method includes the steps of: defining an initial H-mask corresponding to the target pattern; defining an initial V-mask corresponding to the target pattern; identifying horizontal critical features in the H-mask having a width which is less than a predetermined critical width; identifying vertical critical features in the V-mask having a width which is less than a predetermined critical width; assigning a first phase shift and a first percentage transmission to the horizontal critical features, which are to be formed in the H-mask; and assigning a second phase shift and a second percentage transmission to the vertical critical features, which are to be formed in the V-mask. The method further includes the step of assigning chrome to all non-critical features in the H-mask and the V-mask. The non-critical features are those features having a width which is greater than or equal to the predetermined critical width. The non-critical features are formed in the H-mask and the V-mask utilizing chrome. The target pattern is then imaged on the substrate by imaging both the H-mask and V-mask.
Owner:ASML NETHERLANDS BV
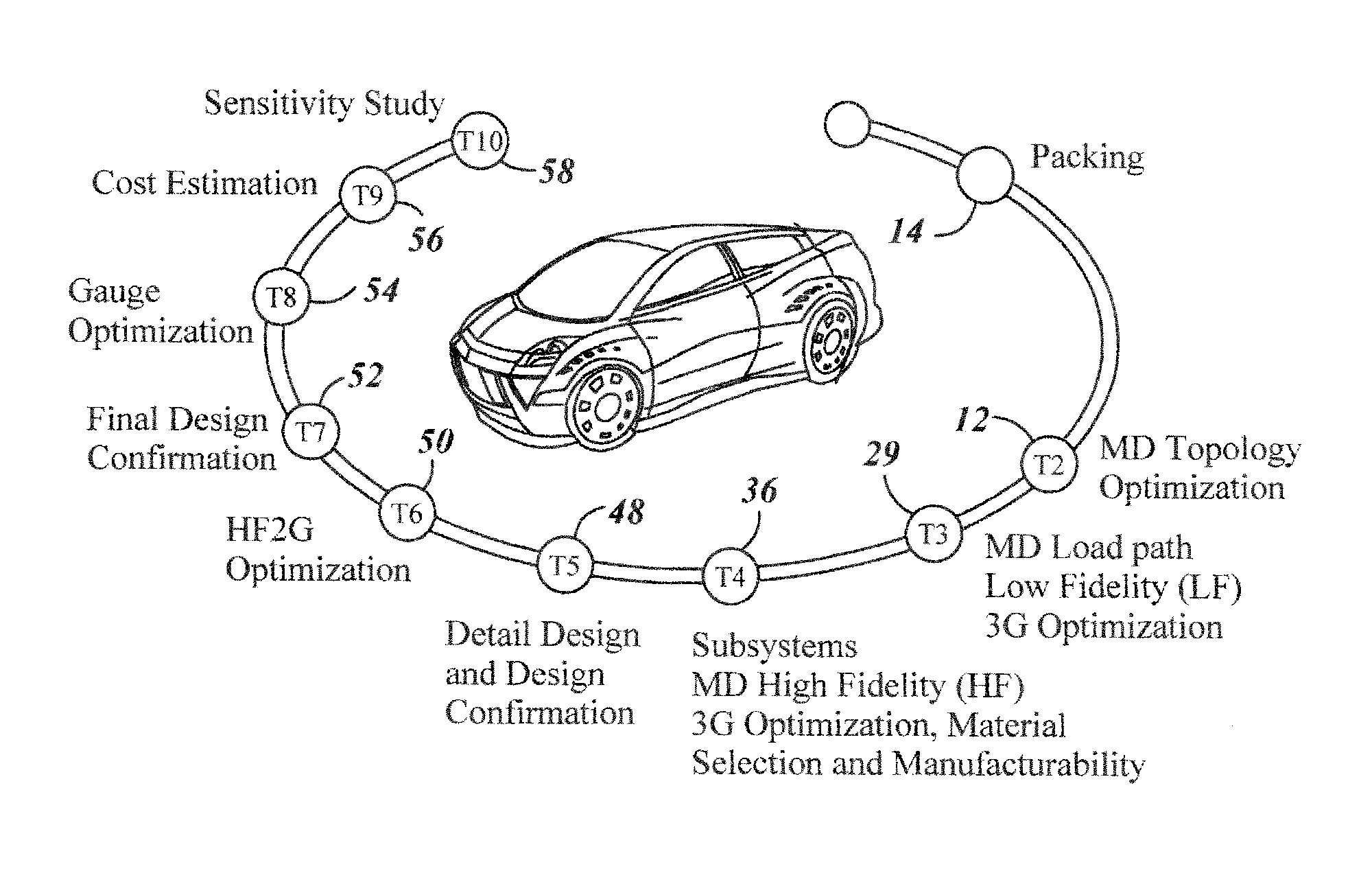
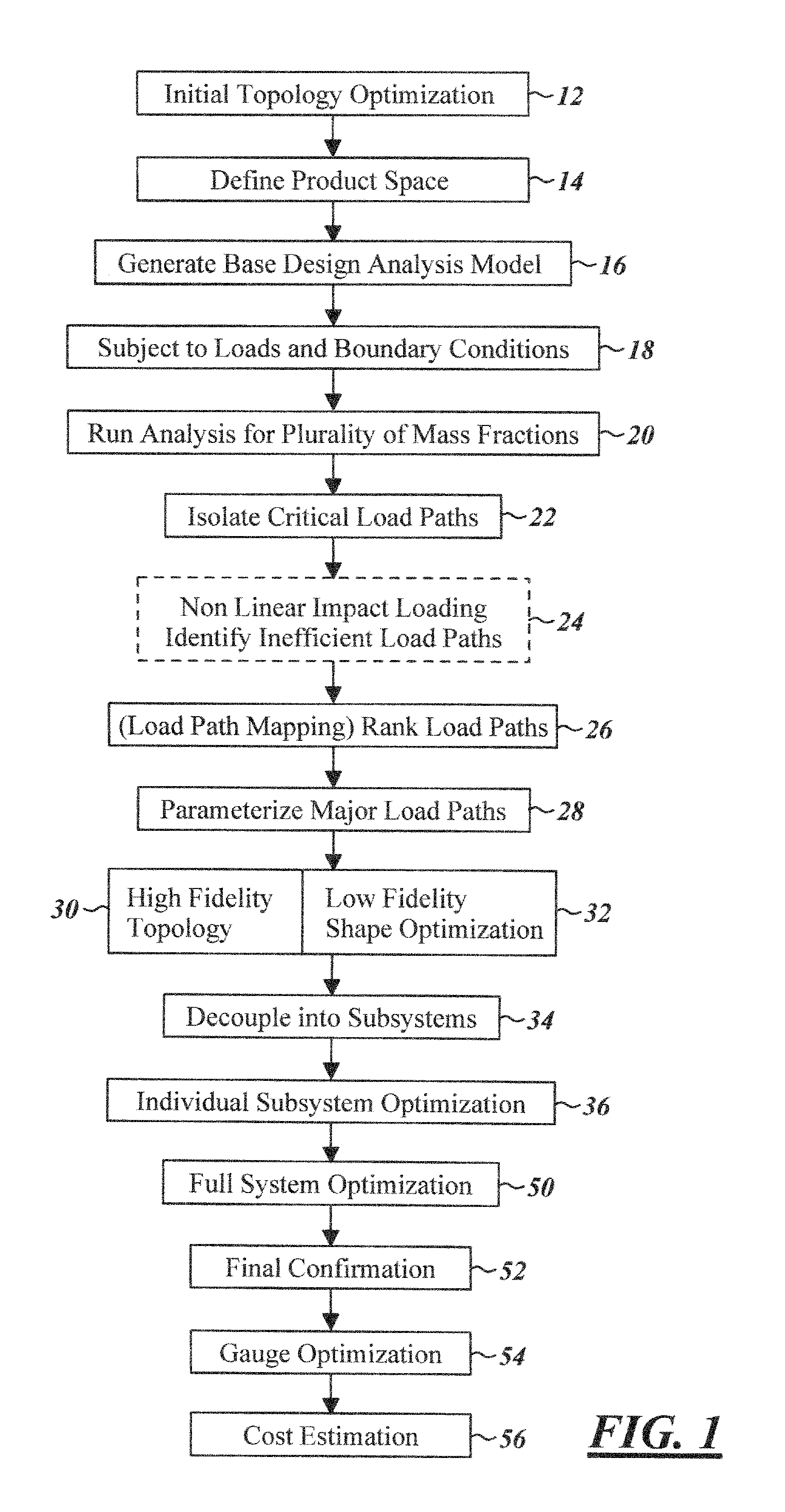
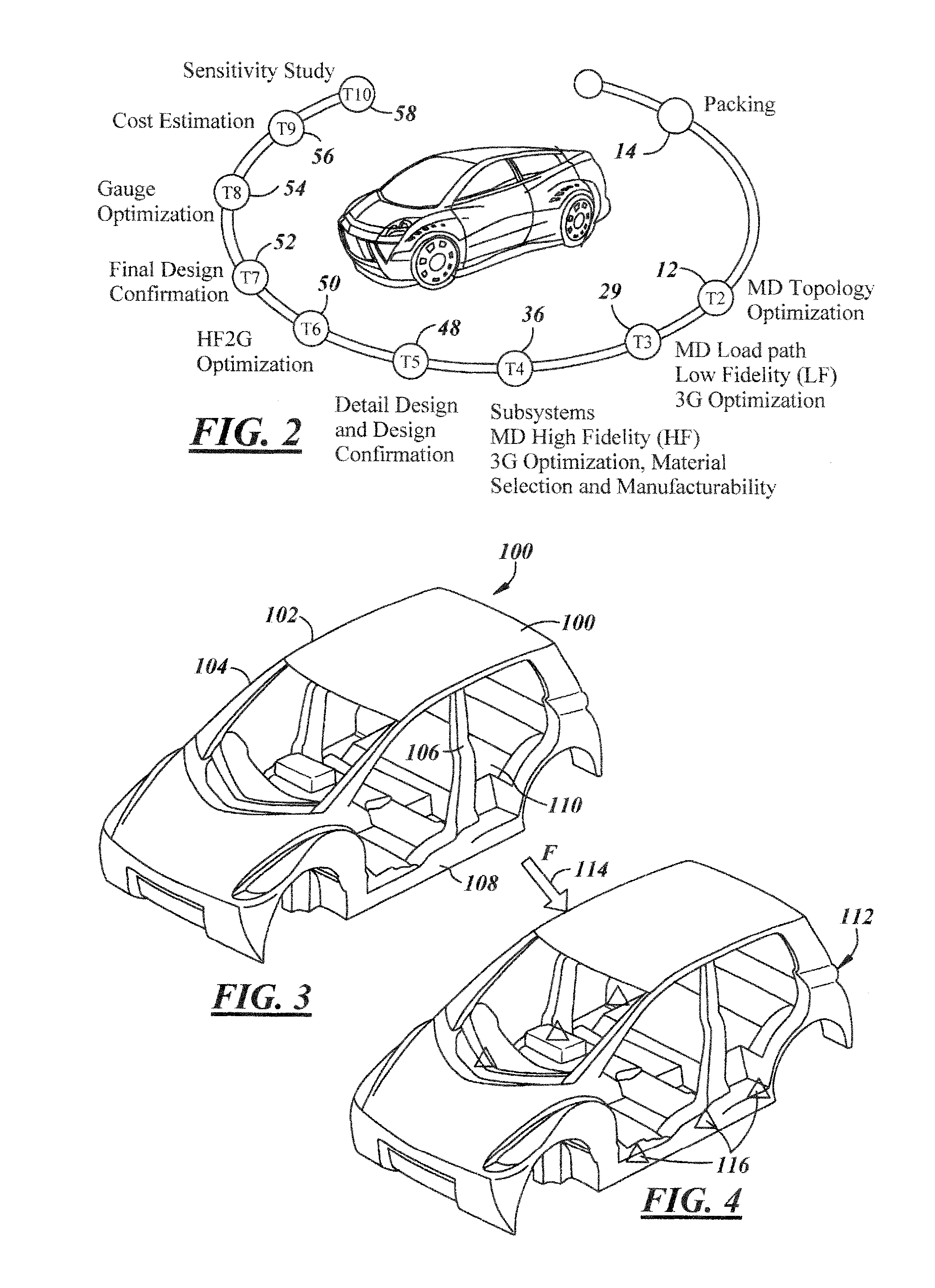
Optimization system
A method for generating an optimized body structure is provided. A first topology optimization of a first body configuration is performed to generate a second body configuration. A subset of critical body components are identified based on load path values for the second body component and are parameterized. A second optimization is performed. The second optimization includes a low fidelity optimization for the geometry, the gauge and the grade of the critical body components, and a high fidelity optimization for the mass of each of the critical body components to generate an optimized set of critical body components. The optimized set of critical body components are combined with non-critical body components from the second body configuration to generate a final body configuration which is optimized for performance and weight.
Owner:NITED STATES STEEL CORP +1
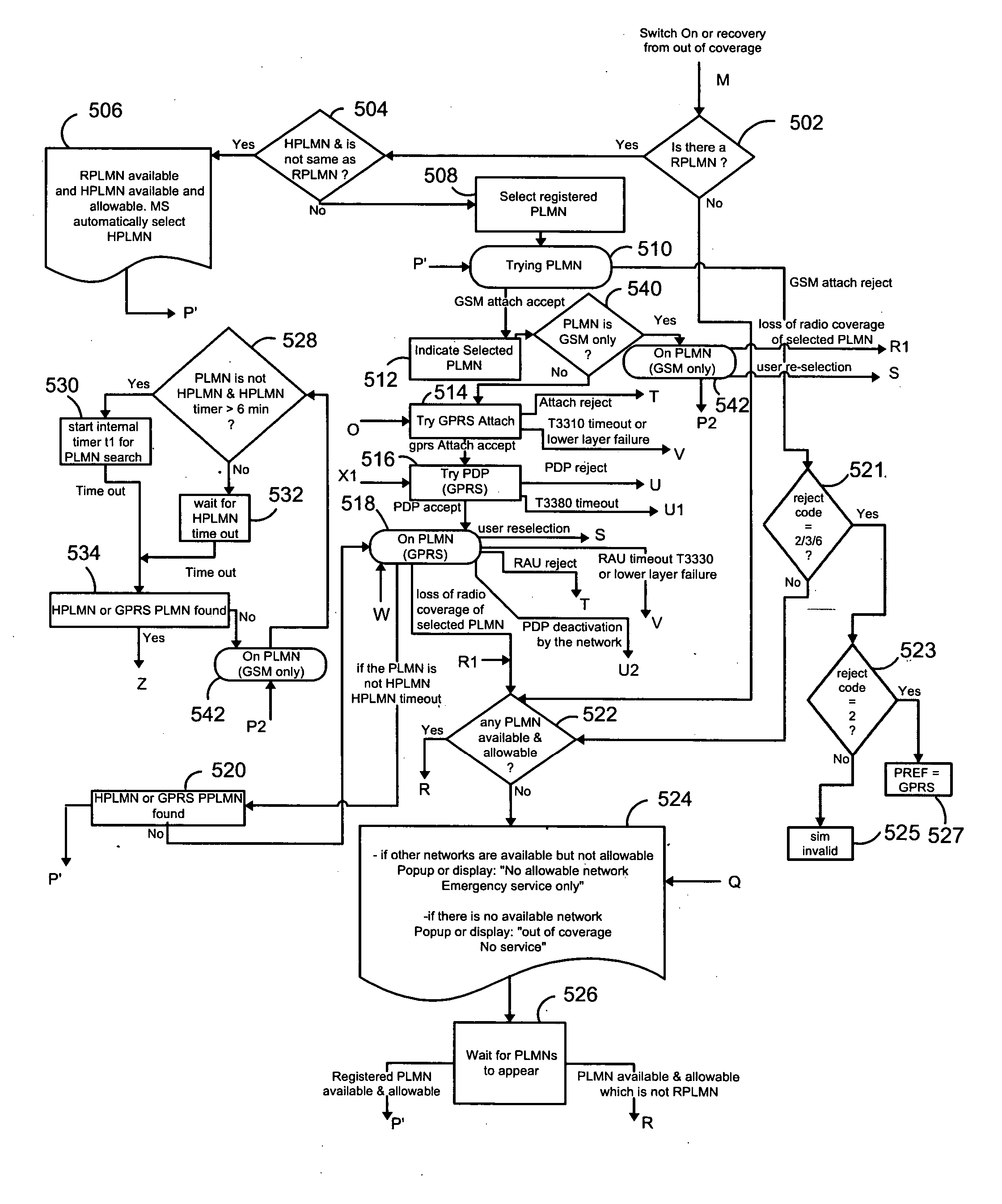
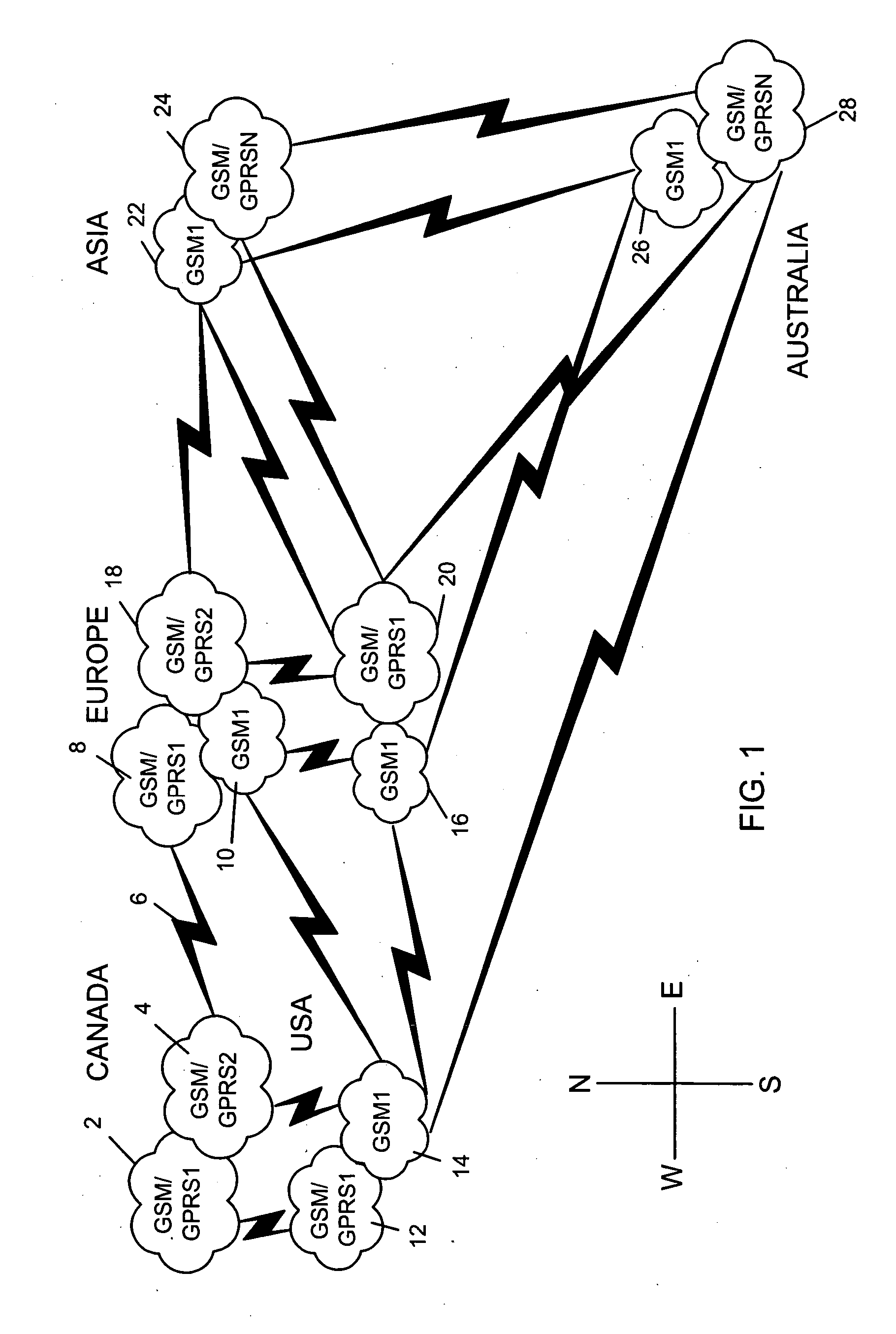
Data-capable network prioritization with reject code handling
ActiveUS20050227720A1Network traffic/resource managementAssess restrictionTime efficientNon critical
Reject code handling is utilized for a more time-efficient selection of data-capable networks. One illustrative method for use in selecting a wireless communication network for communications involves the steps of causing a request for data connectivity to be transmitted through a first wireless network; reattempting the request for data connectivity through the first wireless network one or more times if a reject code comprising a non-critical error is received in response to the request for data connectivity through the first wireless network; and attempting to select a second wireless network for communications without reattempting the request for data connectivity through the first wireless network one or more times if a reject code comprising a critical error is received in response to the request for data connectivity through the first wireless network.
Owner:MALIKIE INNOVATIONS LTD
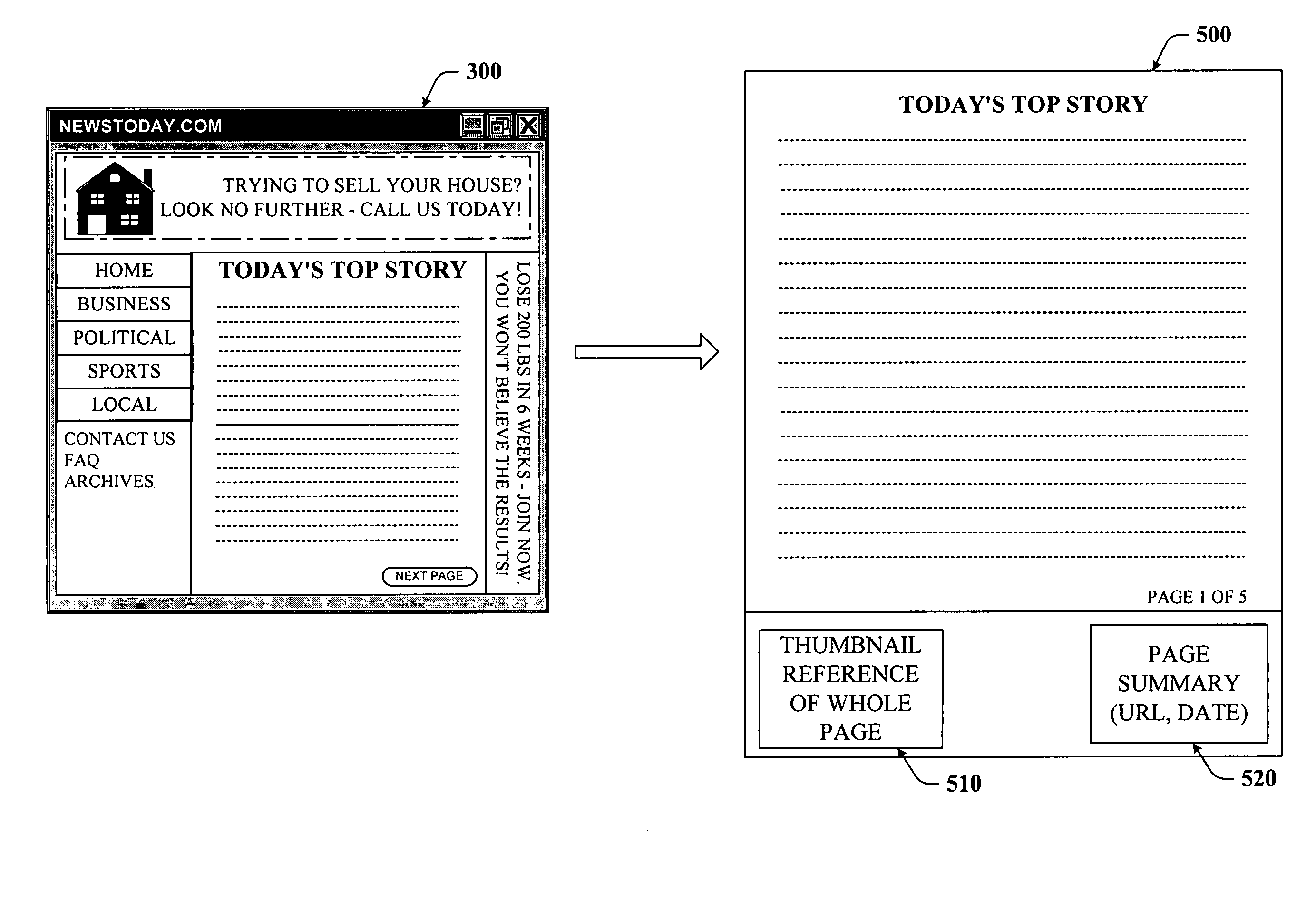
Smartly formatted print in toolbar
InactiveUS7249319B1Easy to distinguishEasily and readily printCathode-ray tube indicatorsNatural language data processingFrustrationThe Internet
The subject invention provides for systems and methods that allow a web user to more easily and readily print what they actually want to print and at the same time, mitigates user frustration that often ensues from poor web page printing. More specifically, the subject invention involves deciphering a structure or layout of any web page on the Internet. When a user employs the present print feature, the invention can be invoked to analyze the structure of a current web page to automatically generate a print preview page of the current web page. After analyzing the current web page, extraneous content of the page that is deemed to be non-critical or non-essential to that web page can be removed for printing purposes. Furthermore, previous knowledge learned regarding web page structure can be applied to determine the page and / or content structure of the current page to facilitate generating the print preview page.
Owner:MICROSOFT TECH LICENSING LLC
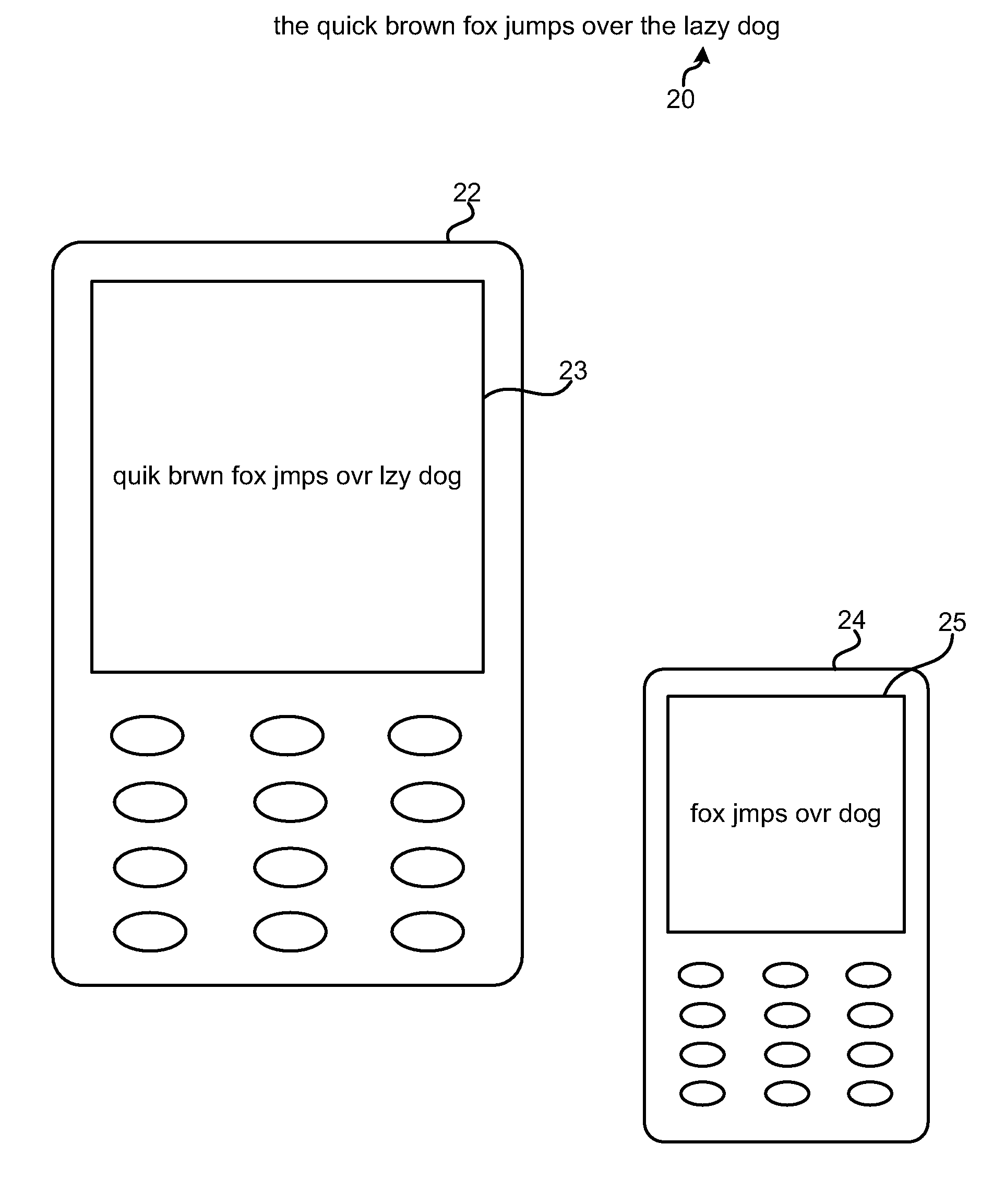
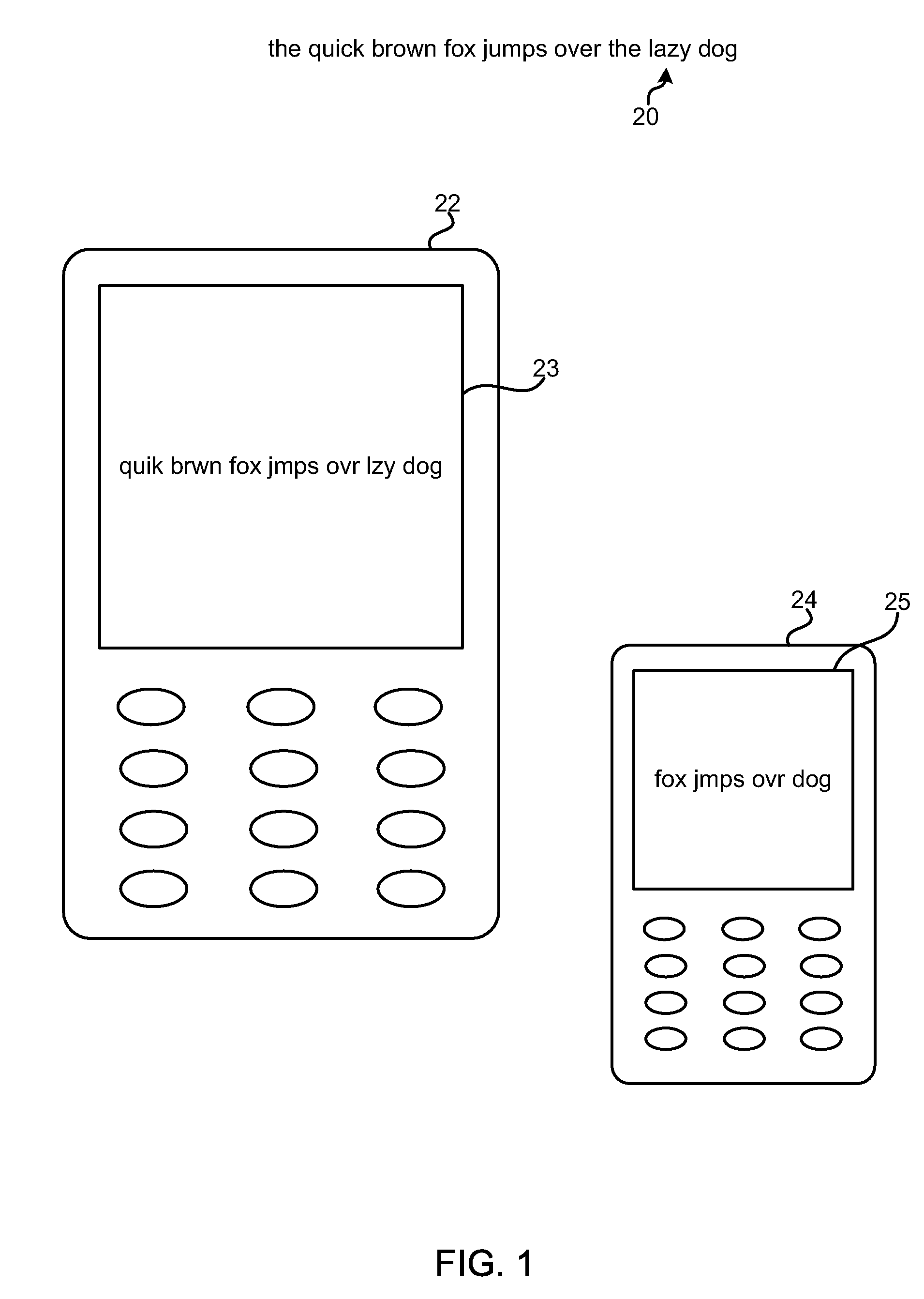
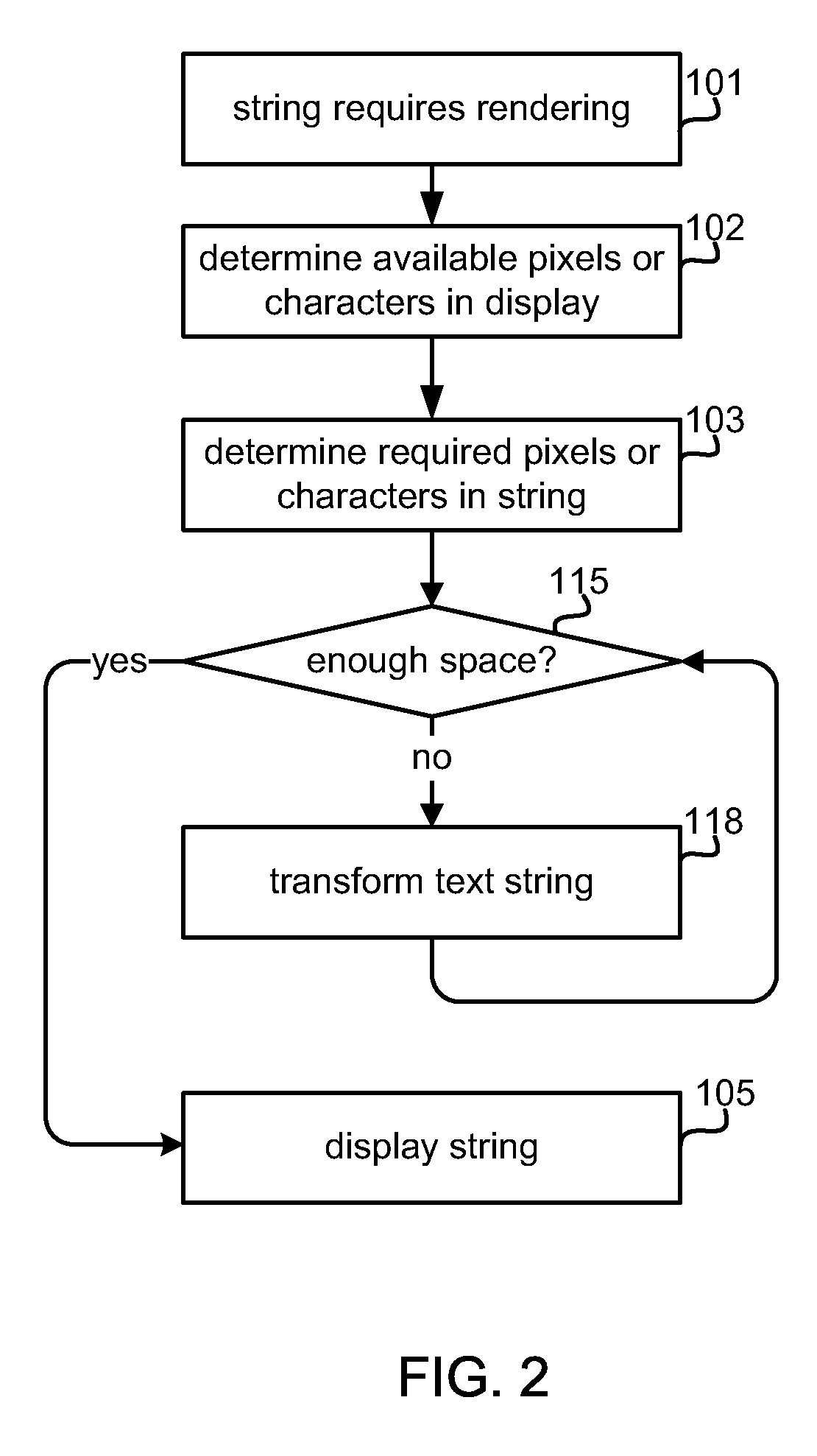
Method and apparatus for adjusting the length of text strings to fit display sizes
InactiveUS20100145676A1Digital data information retrievalNatural language data processingAlgorithmTheoretical computer science
The various aspects provide methods and devices which can reduce the length of a text string to fit dimensions of a display by identifying and deleting elements of the string that are not essential to its meaning. In the various aspects, handheld devices may be configured with software configured to analyze and modify text strings to shorten their length by adjusting font size, changing fonts, deleting unnecessary words, such as articles, abbreviating some words, deleting letters (e.g., vowels) from some words, and deleting non-critical words. The order in which transformations are affected may vary depending upon the text string according to a priority of transformations. Such transformation operations may be applied incrementally until the text string fits within the display size requirements. Similar methods may be implemented to increase the length of text strings by adding words in a manner that does not substantially change the meaning of the text string.
Owner:QUALCOMM INC
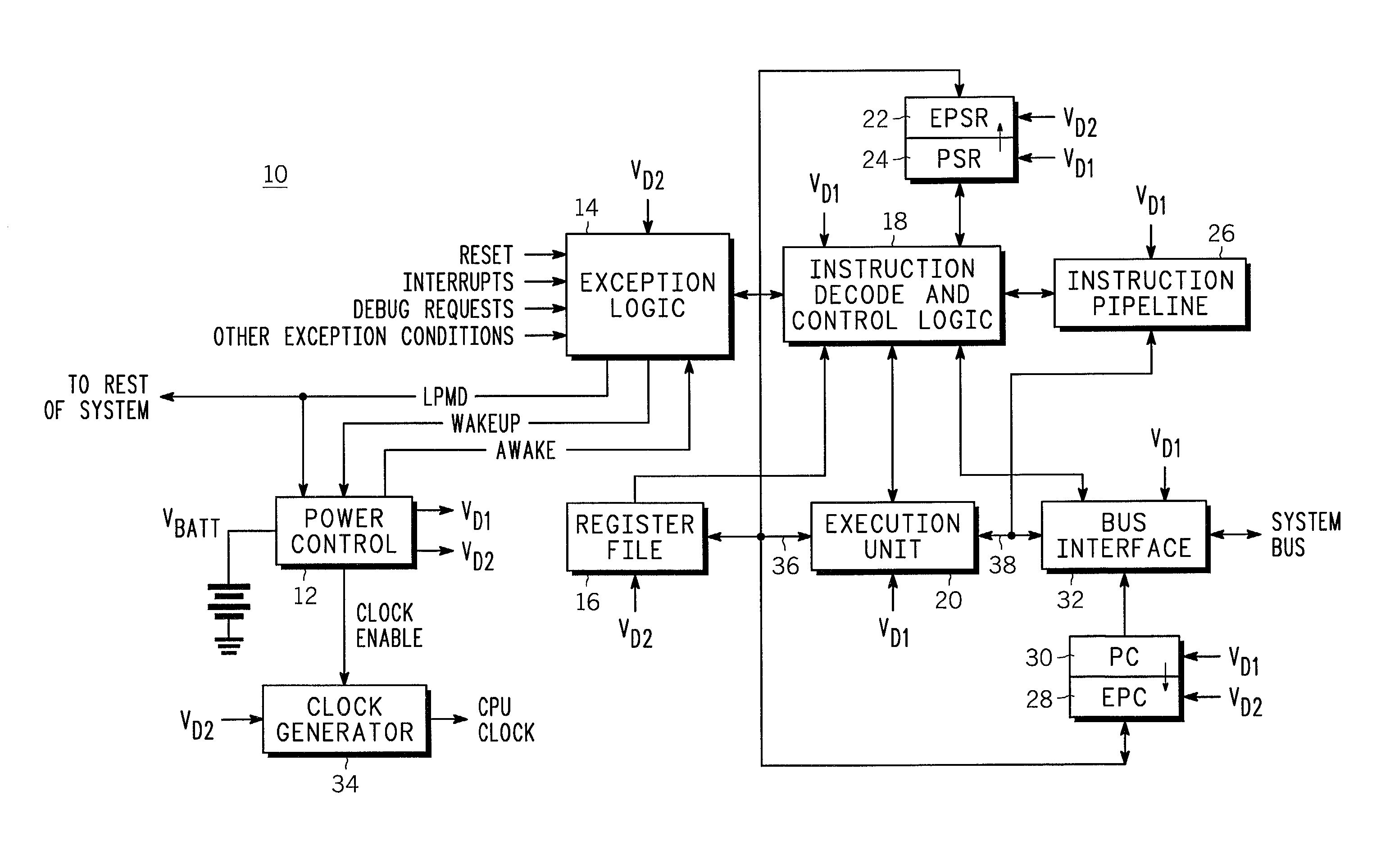
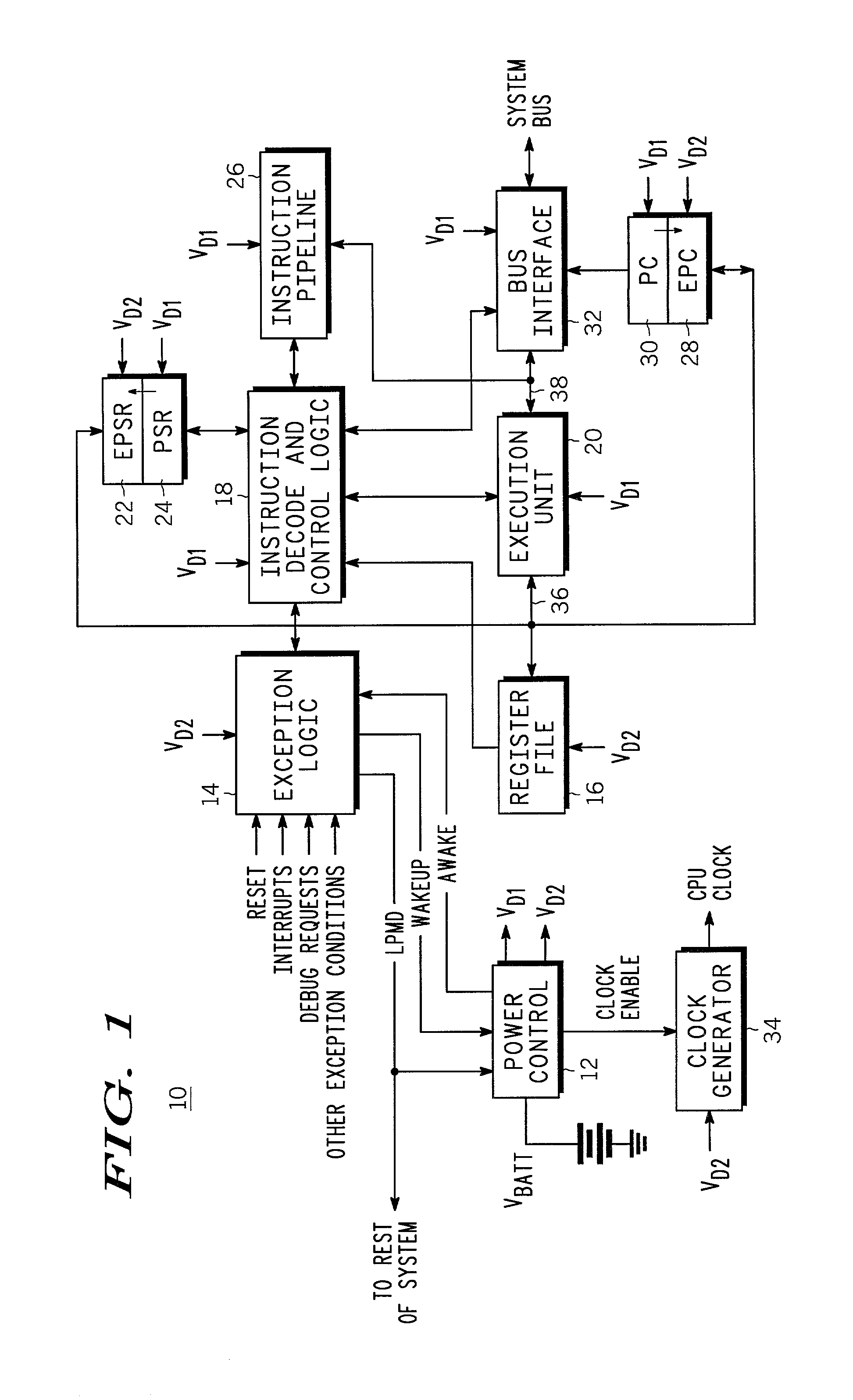
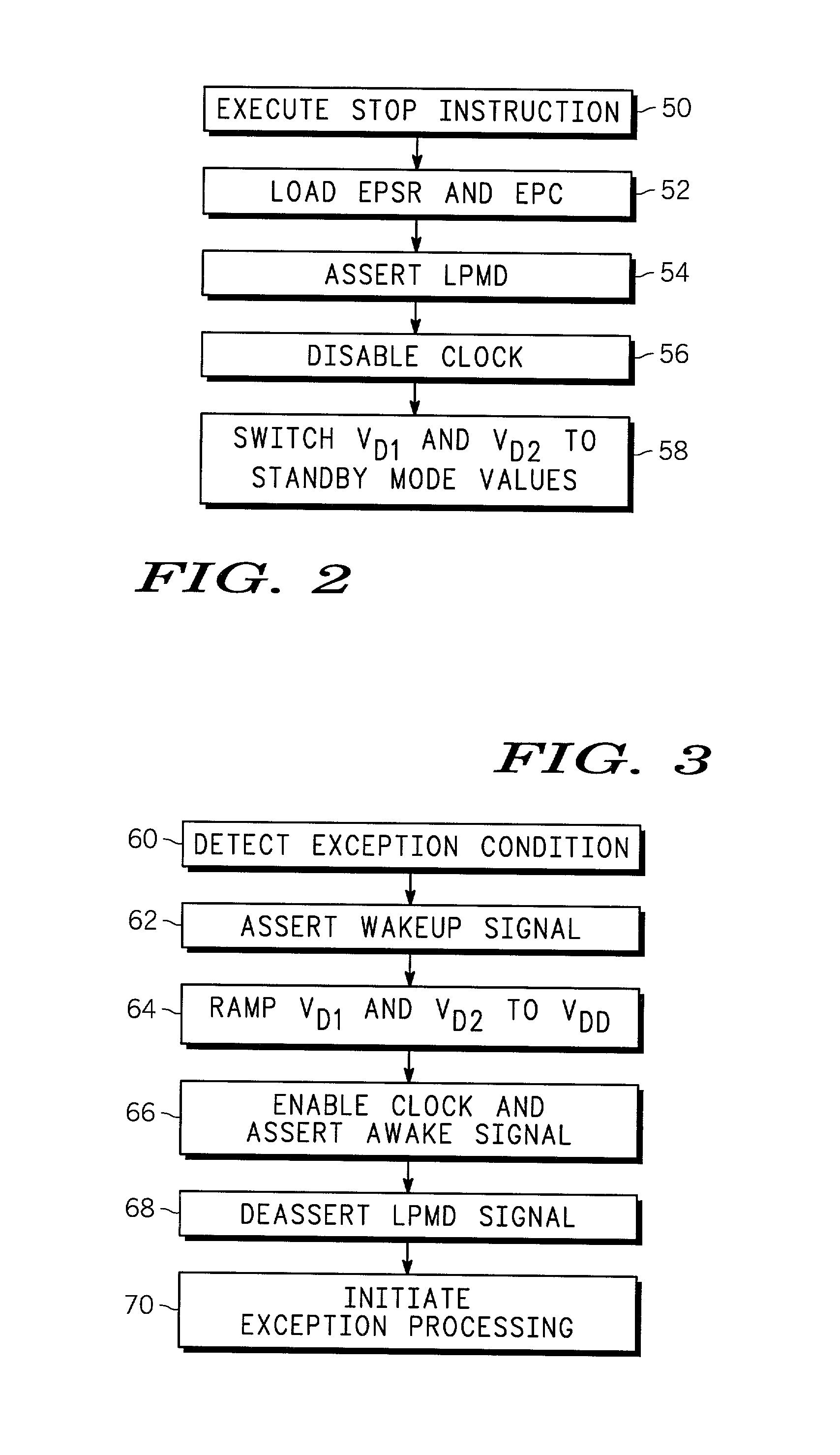
CPU powerdown method and apparatus therefor
A CPU has a powerdown mode in which most of the circuitry does not receive power. Power-up, coming out of powerdown, is achieved in response to receiving an exception. Because most of the state information that is present in the CPU is not needed in response to an exception, there is no problem in removing power to most of the CPU during powerdown. The programmer's model register file and a few other circuits in the CPU are maintained in powerdown, but the vast majority of the circuits that make up the CPU: the execution unit, the instruction decode and control logic, instruction pipeline and bus interface, do not need to receive power. Removing power from these non-critical circuits results in significant power savings during powerdown. The powered circuits are provided with a reduced power supply voltage to provide additional power savings.
Owner:APPLE INC
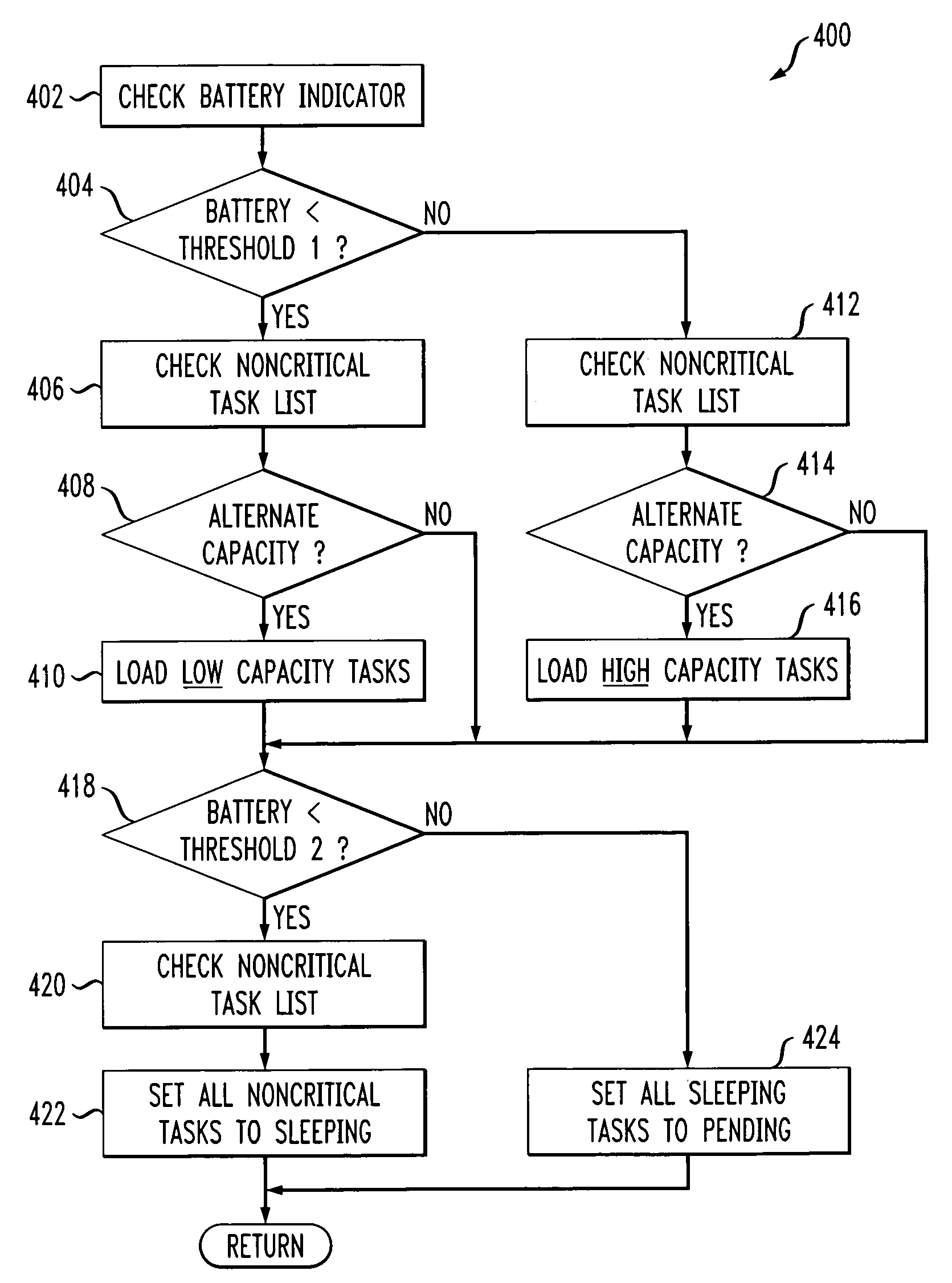
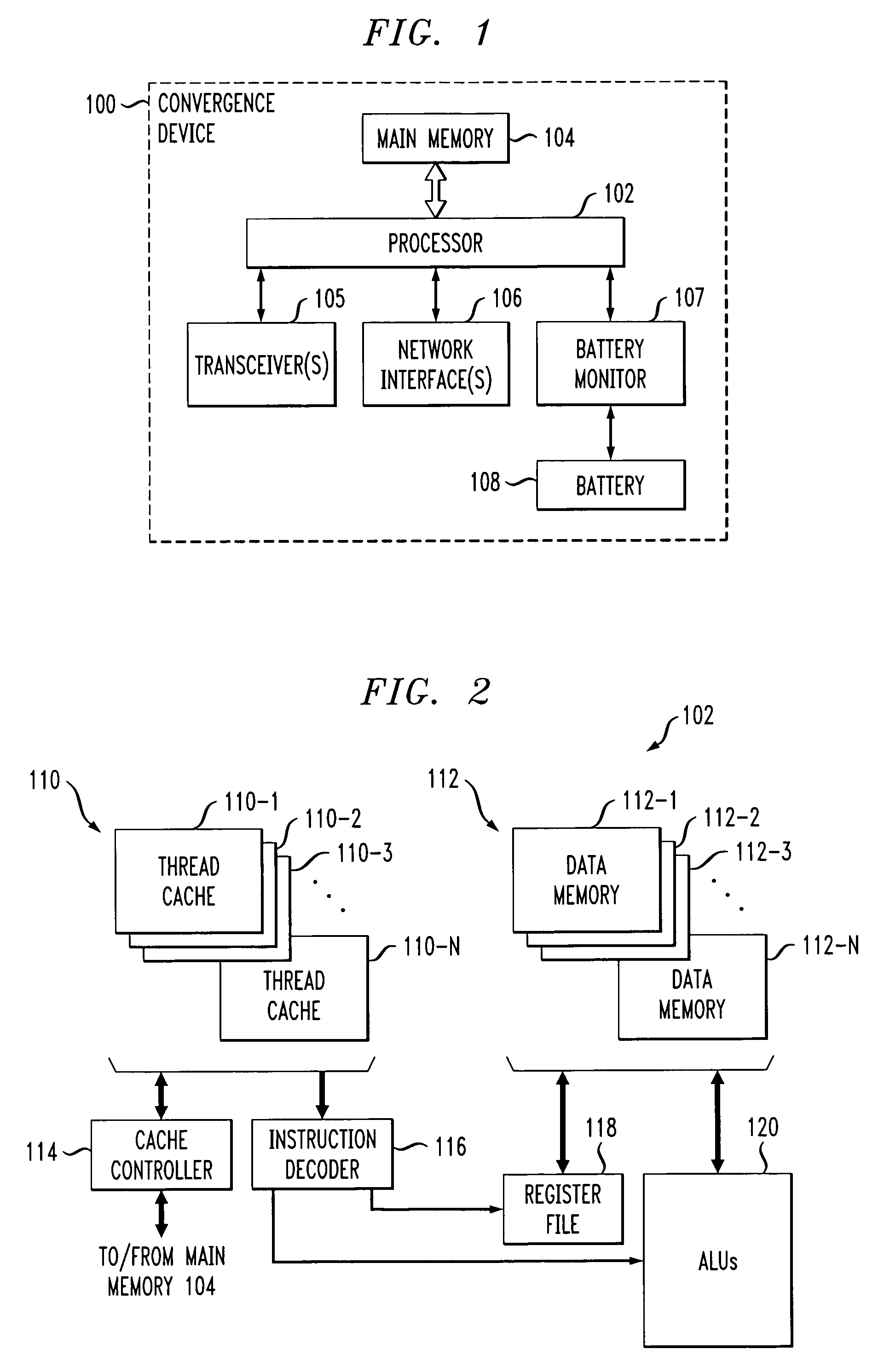
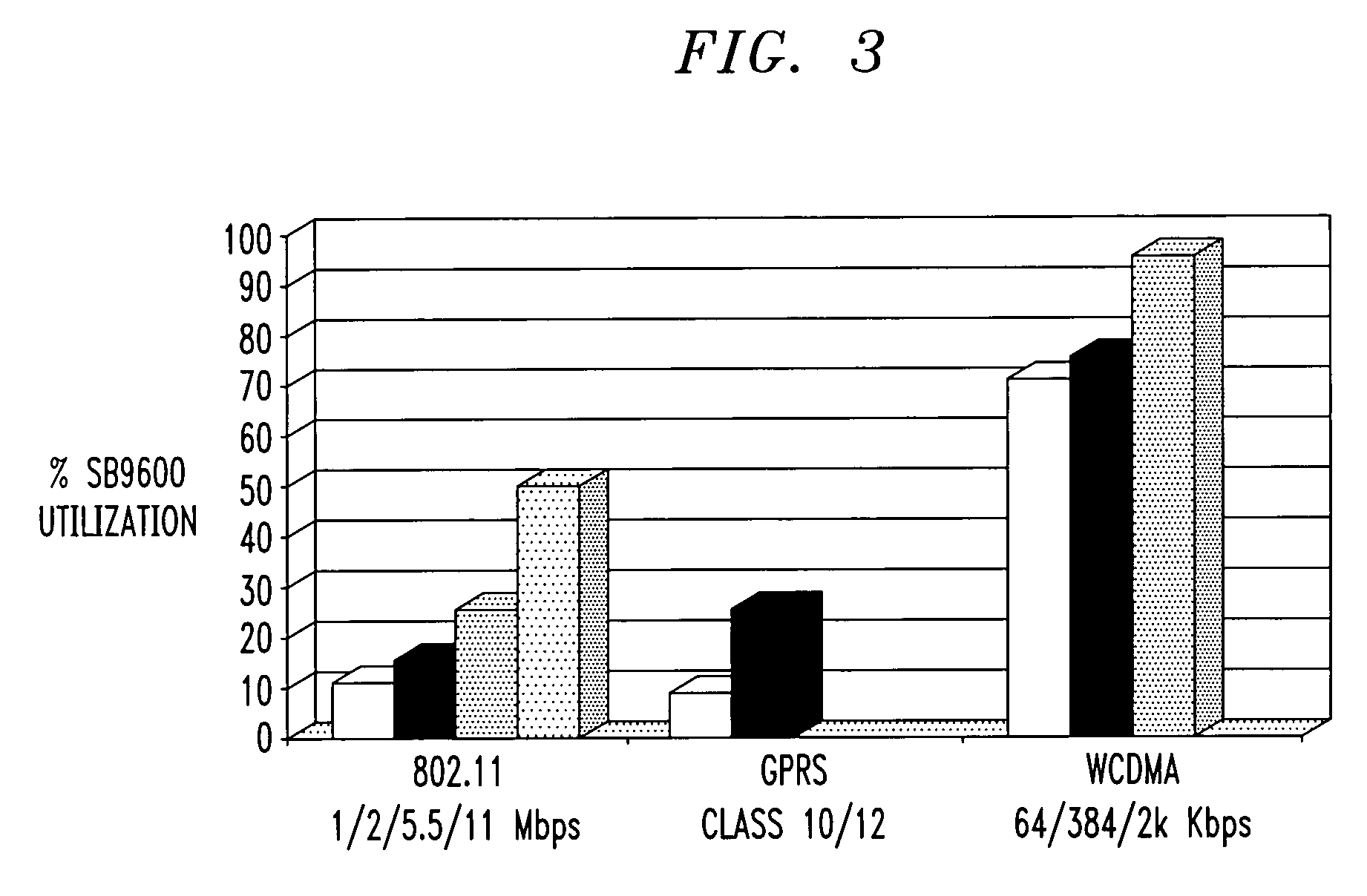
Convergence device with dynamic program throttling that replaces noncritical programs with alternate capacity programs based on power indicator
ActiveUS7251737B2Extension of timeEnergy efficient ICTVolume/mass flow measurementComputer hardwareSpeech sound
Techniques for conserving power by controlling program execution in a convergence device comprising a battery or other power source and at least one processor. The processor is configured to perform processing operations associated with voice call communication functions and to perform processing operations associated with data communication functions, and is operative to execute critical programs and noncritical programs. The convergence device stores, for at least a given one of a plurality of noncritical programs associated with the data communication functions, an identifier of at least one alternate capacity program capable of performing substantially the same function as the given program but having a different power source capacity associated therewith. Based at least in part on a power indicator representative of remaining capacity or another characteristic of the power source, execution of the given program may be replaced with execution of the alternate capacity program, such that an amount of power source capacity utilizable for the voice call communication functions is increased.
Owner:QUALCOMM INC
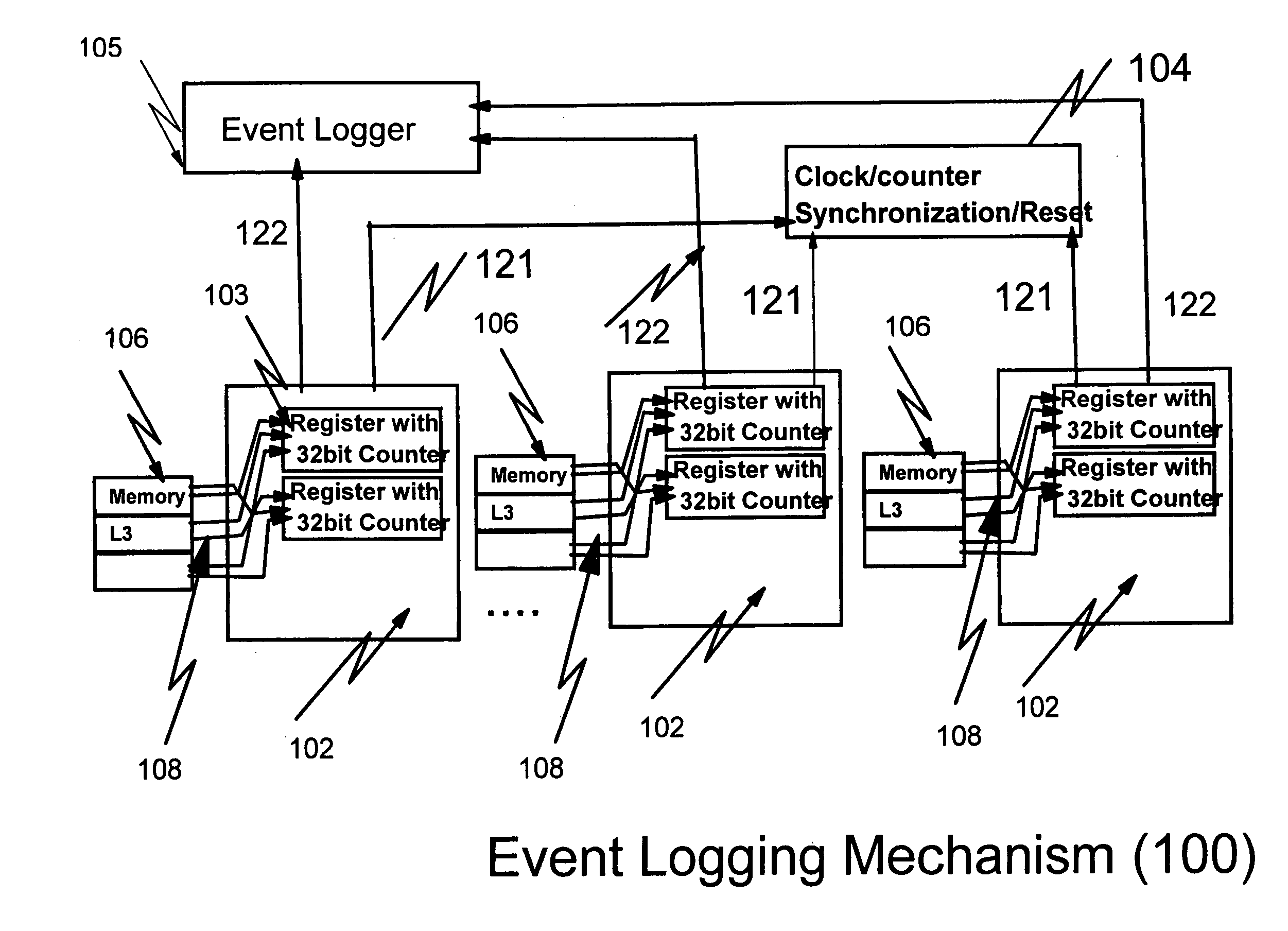
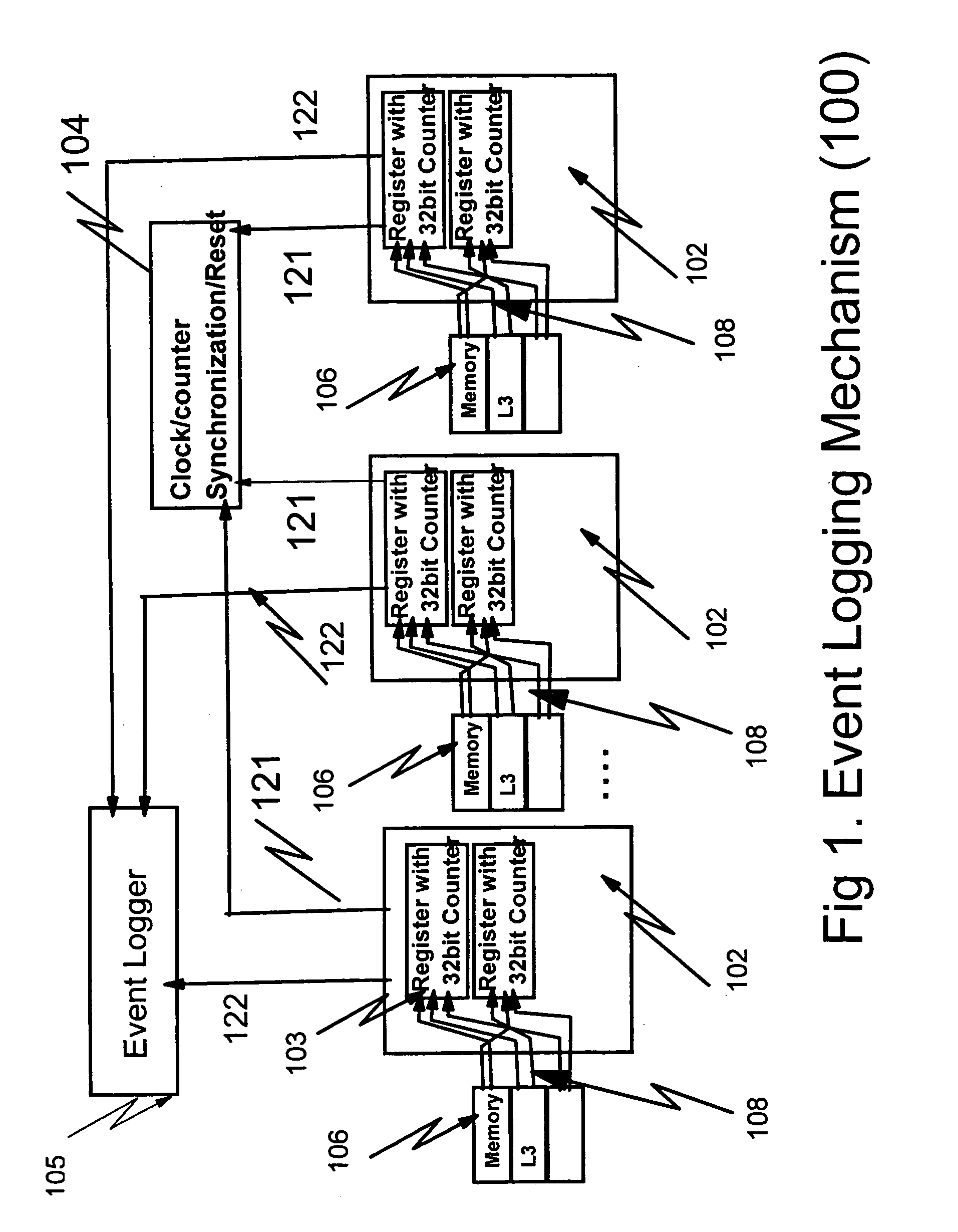
Hardware/software based indirect time stamping methodology for proactive hardware/software event detection and control
InactiveUS20050144532A1Error detection/correctionDigital computer detailsEvent triggerRemedial action
An improved method and apparatus for time stamping events occurring on a large scale distributed network uses a local counter associated with each processor of the distributed network. Each counter resets at the same time globally so that all events are recorded with respect to a particular time. The counter is stopped when a critical event is detected. The events are masked or filtered in an online or offline fashion to eliminate non-critical events from triggering a collection by the system monitor or service / host processor. The masking can be done dynamically through the use of an event history logger. The central system may poll the remote processor periodically to receive the accurate counter value from the local counter and device control register. Remedial action can be taken when conditional probability calculations performed on the historical information indicate that a critical event is about to occur.
Owner:IBM CORP
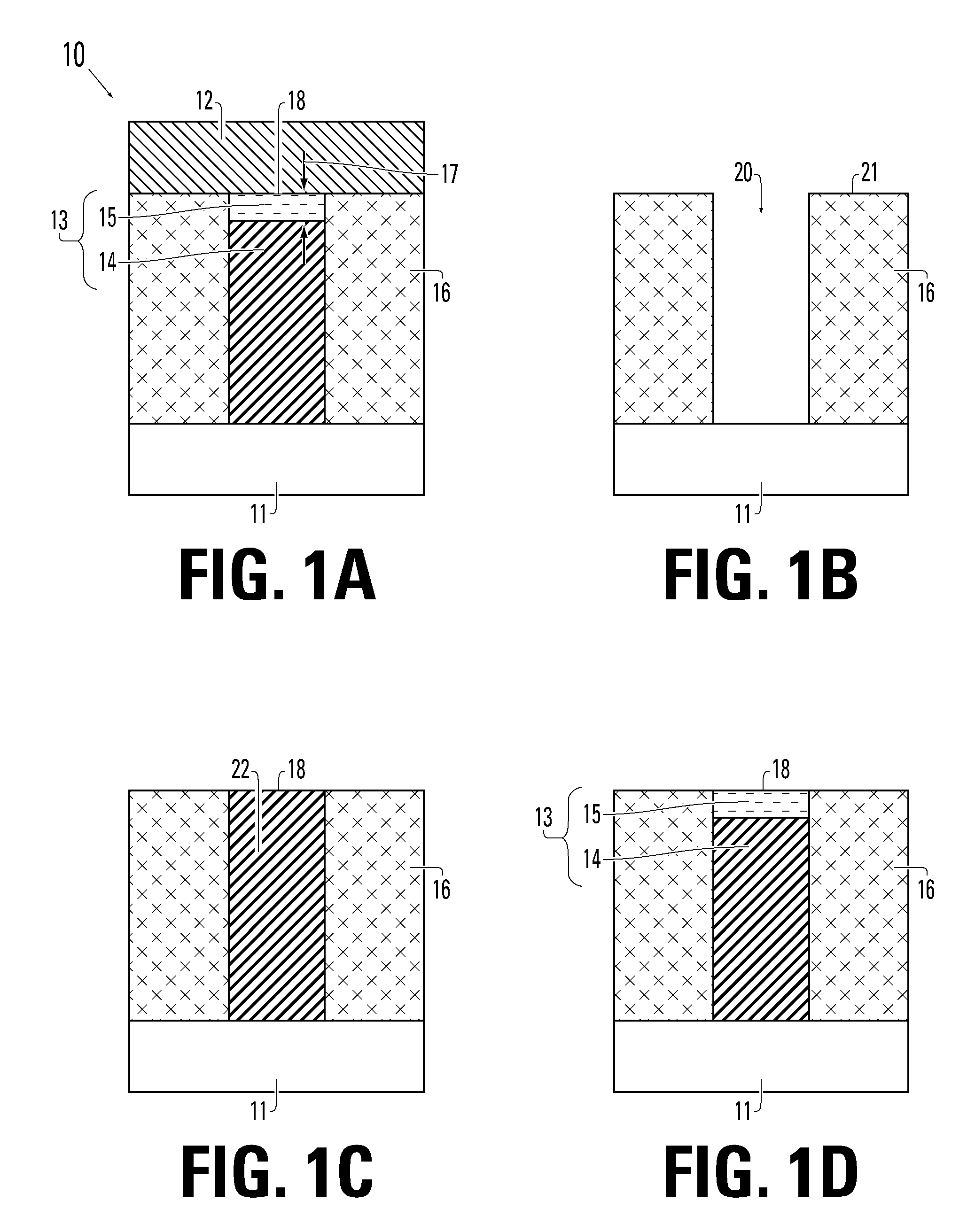
Method to perform selective drain engineering with a non-critical mask
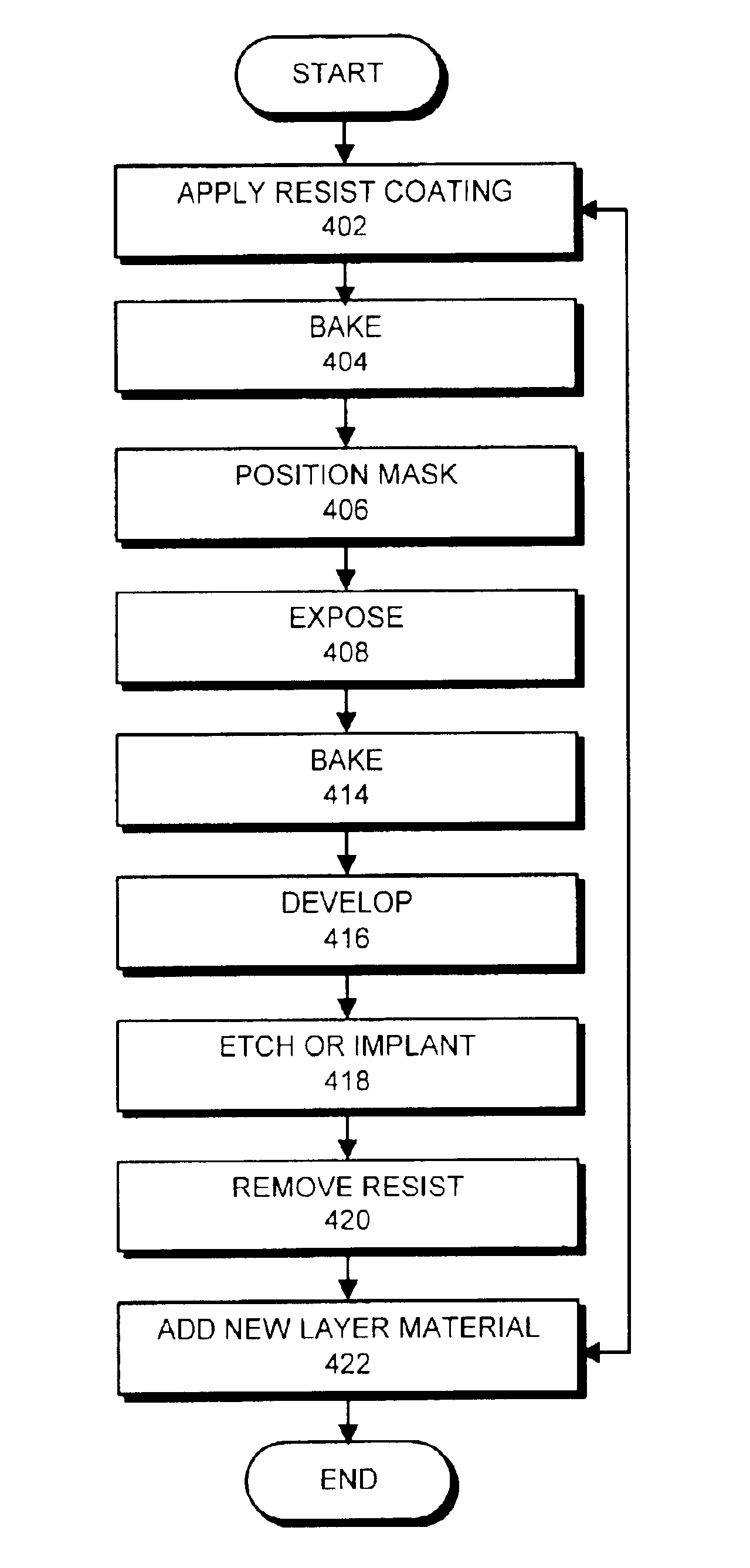
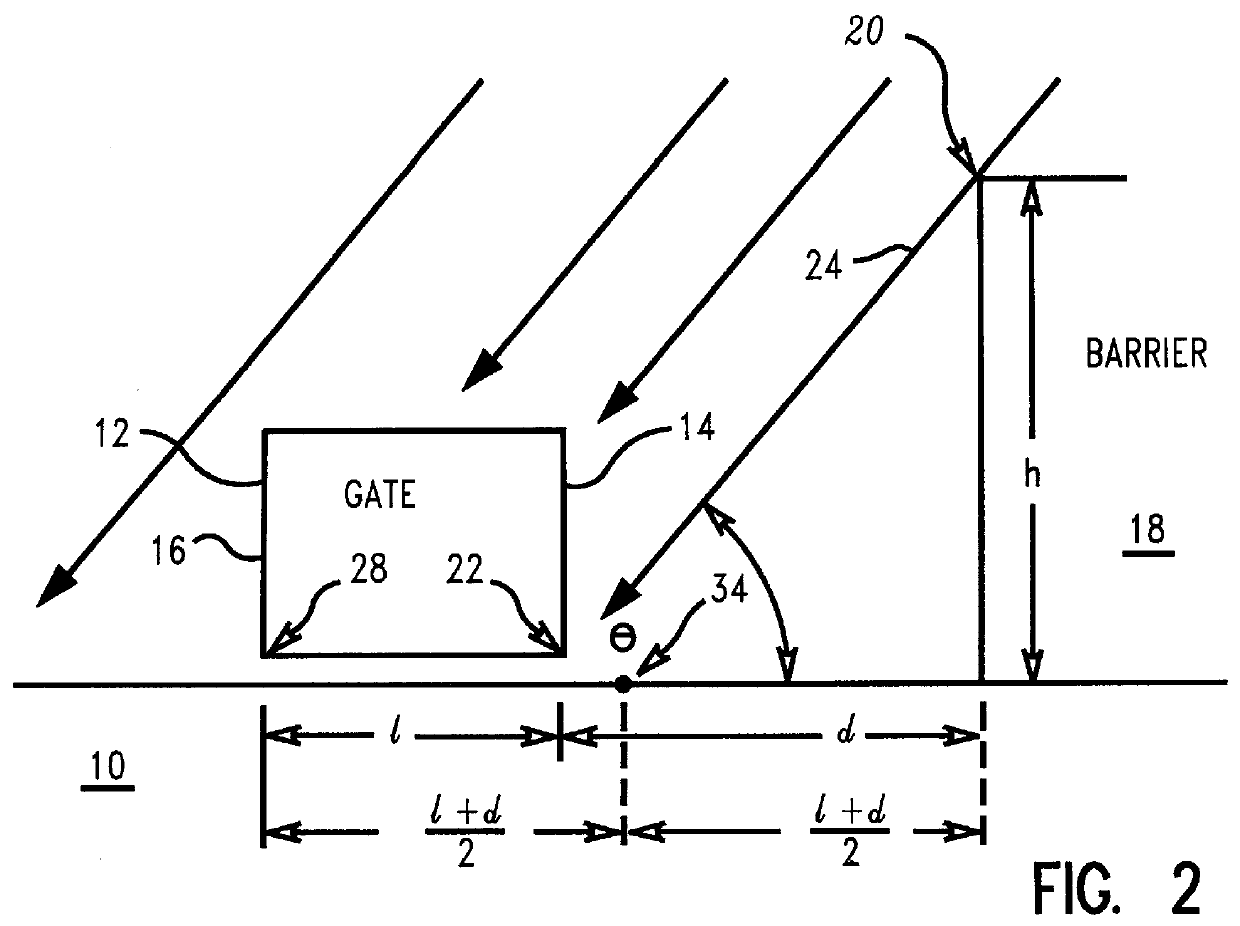
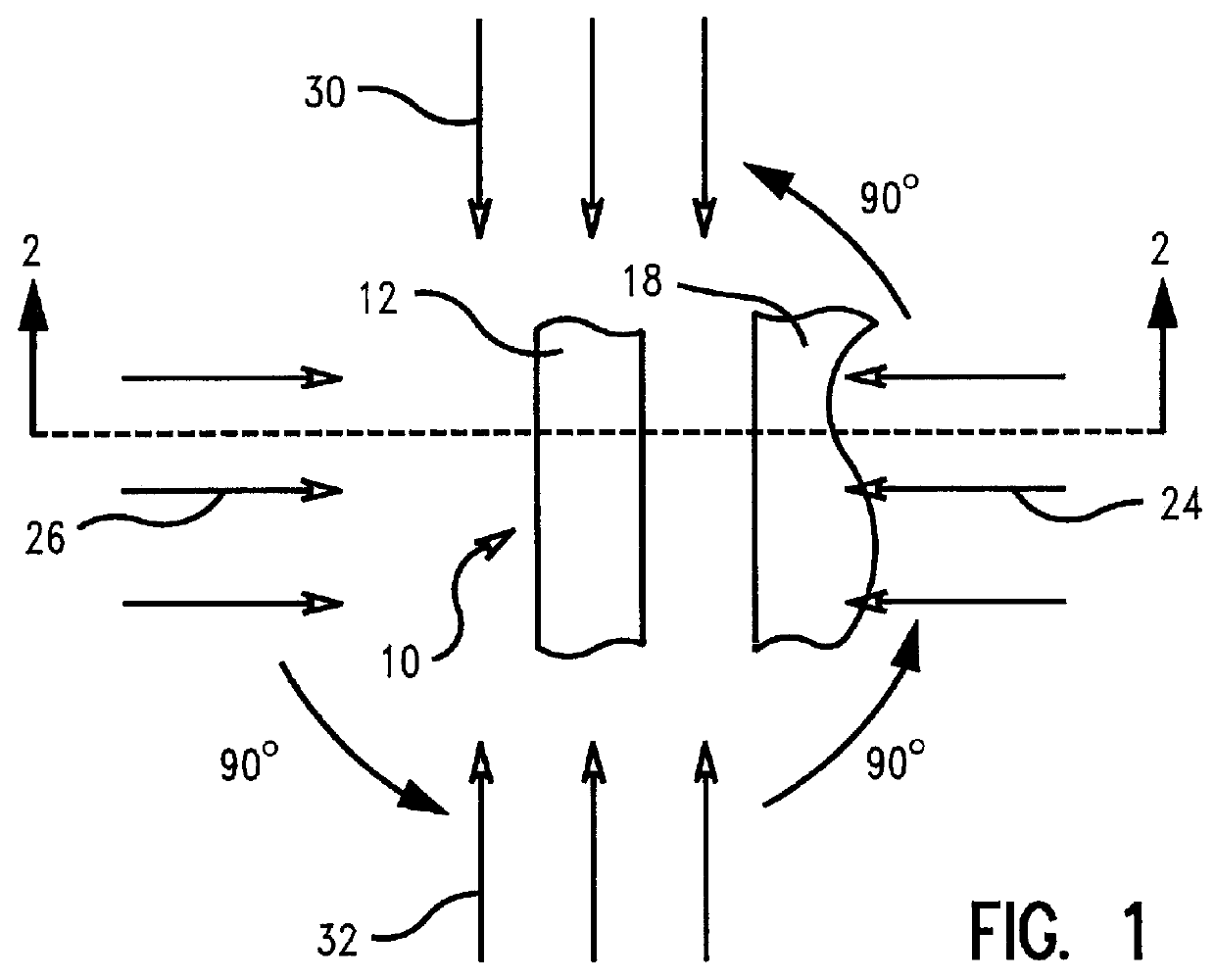
InactiveUS6083794ALow implementation costTransistorSemiconductor/solid-state device manufacturingSemiconductorIon implantation
A method of producing an asymmetrical semiconductor device with ion implantation techniques and semiconductor devices constructed according to this method in which a barrier of ion absorbing material of height h is positioned beside a structure on a semiconductor surface. The barrier is located at a maximum distance d from one side of the structure, and an angled ion implant is directed at the side of the structure. The maximum distance d of the barrier from the side of the structure is equal to the height of the barrier h divided by the tangent of the angle of the ion implant so that the side of the structure is shadowed from the ion implant. A second ion implant is directed to the opposite side of the structure on the semiconductor surface, thereby forming a desired implant and producing the asymmetrical semiconductor device.
Owner:IBM CORP
Routing shipments according to criticality
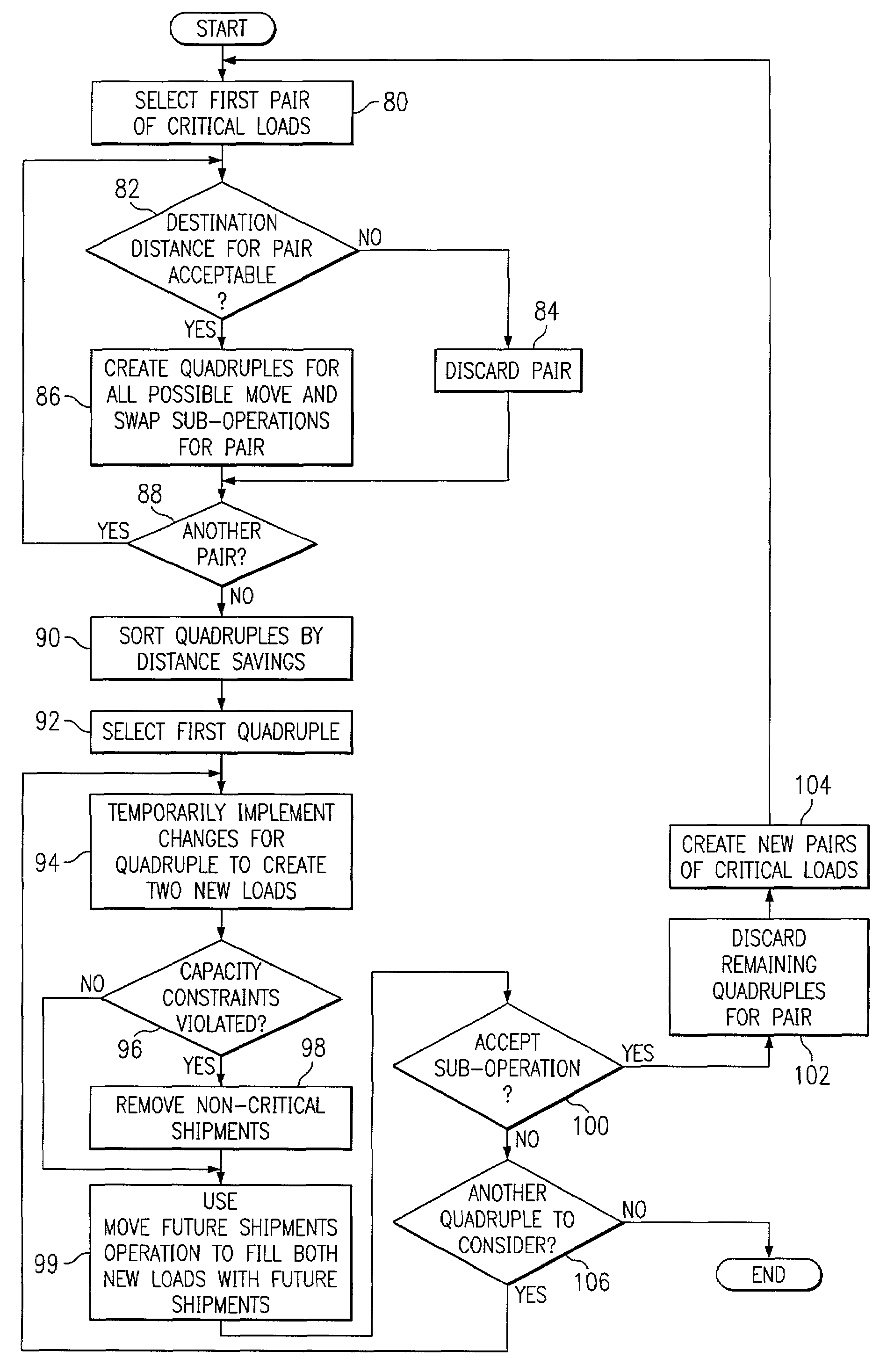
InactiveUS6980885B2Disadvantages can be reduced eliminatedSimple and flexible and effectiveAcutation objectsDigital data processing detailsCritical loadParallel computing
A computer-implemented method for routing shipments according to criticality includes accessing an initial solution to an optimization problem of routing multiple shipments to multiple locations using multiple vehicles, the initial solution including multiple loads such that each shipment is routed within exactly one load and a global cost across all loads is minimized, the initial solution being generated independent of the criticality of the shipments. Into each of one or more critical loads in a current solution, one or more non-critical shipments are inserted that are within a neighborhood of the critical load, a critical load being a load containing at least one critical shipment. One or more local search operations are executed to improve the initial solution, the operations including at least one of: (a) splitting each of one or more selected critical loads in a current solution into two new critical loads; (b) for each of one or more selected critical load pairs in a current solution, move a sequence of stops from one critical load in the pair to the other critical load in the pair and / or swap two sequences of stops between the critical loads in the pair; and (c) for each of one or more selected critical loads in a current solution that are indirect critical loads having at least one in-transit stop, break up the indirect critical load into a plurality of new direct critical loads having no in-transit stops and execute operation (b) on each of one or more selected critical load pairs, each selected critical load pair including at least one new direct critical load.
Owner:BLUE YONDER GRP INC
Chromeless phase shifting mask for integrated circuits
ActiveUS20060199084A1Originals for photomechanical treatmentSpecial data processing applicationsSemiconductorIntegrated circuit
Owner:SIEMENS PROD LIFECYCLE MANAGEMENT SOFTWARE INC
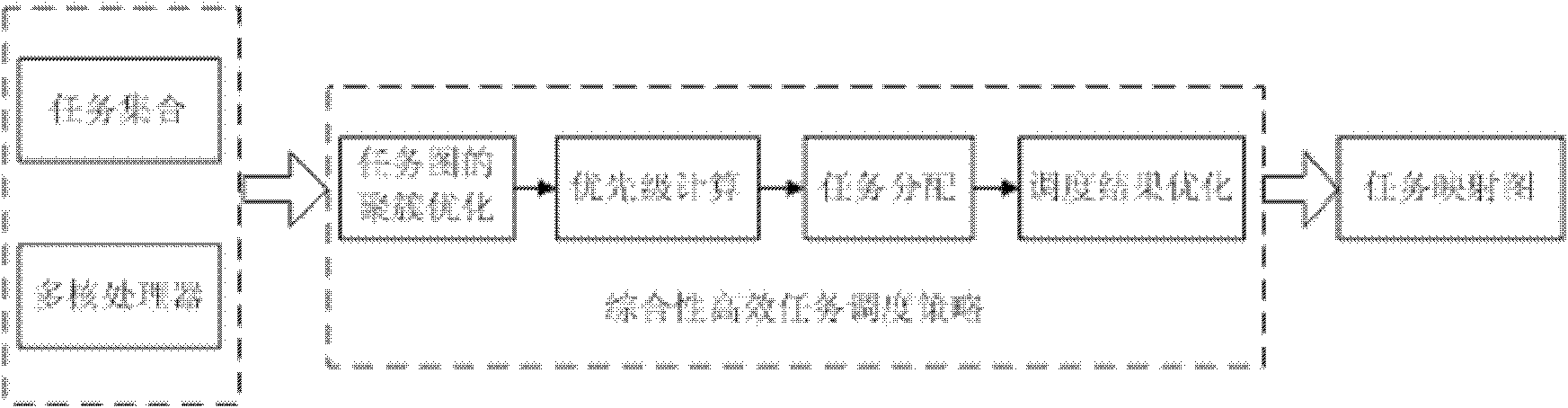
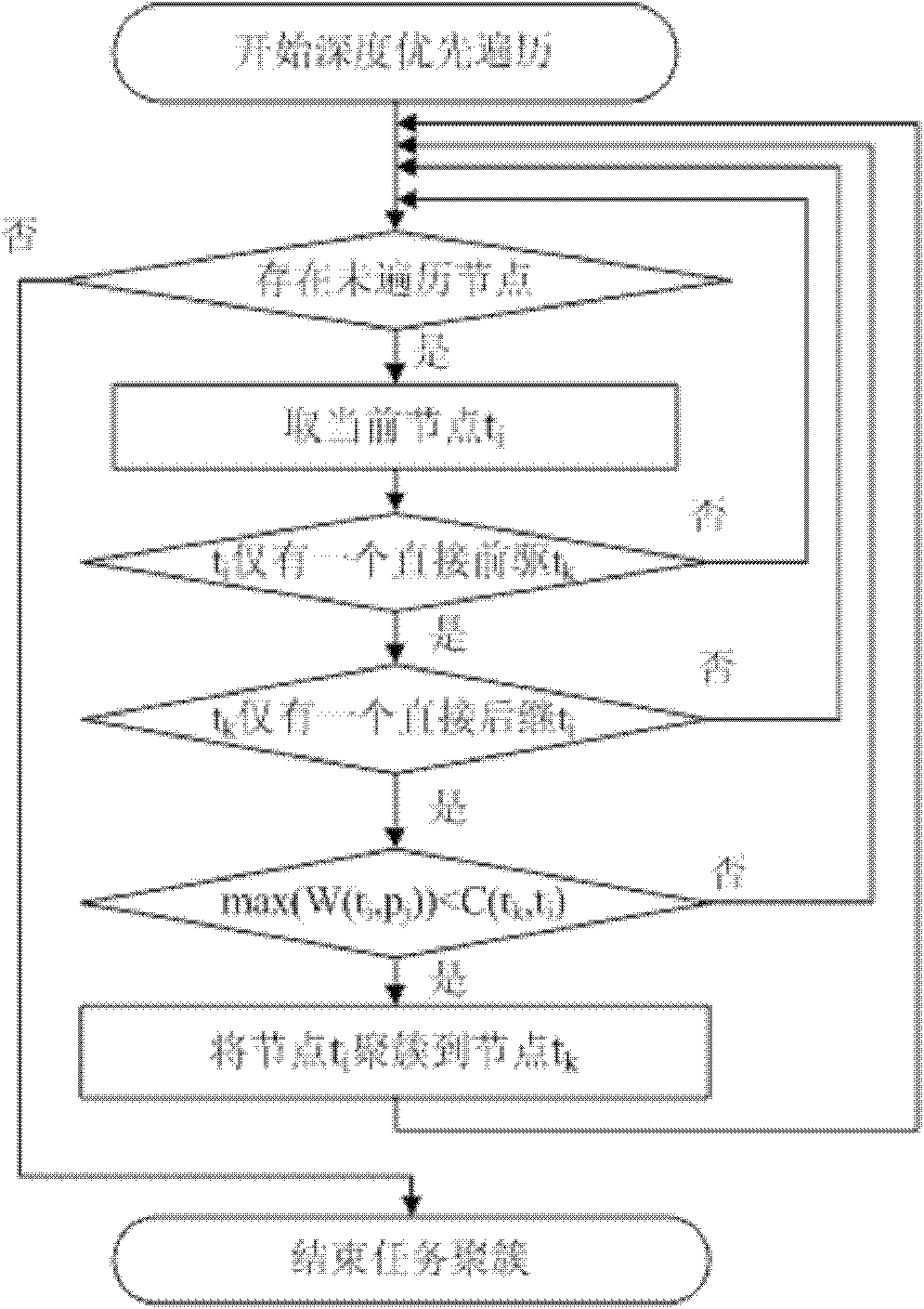
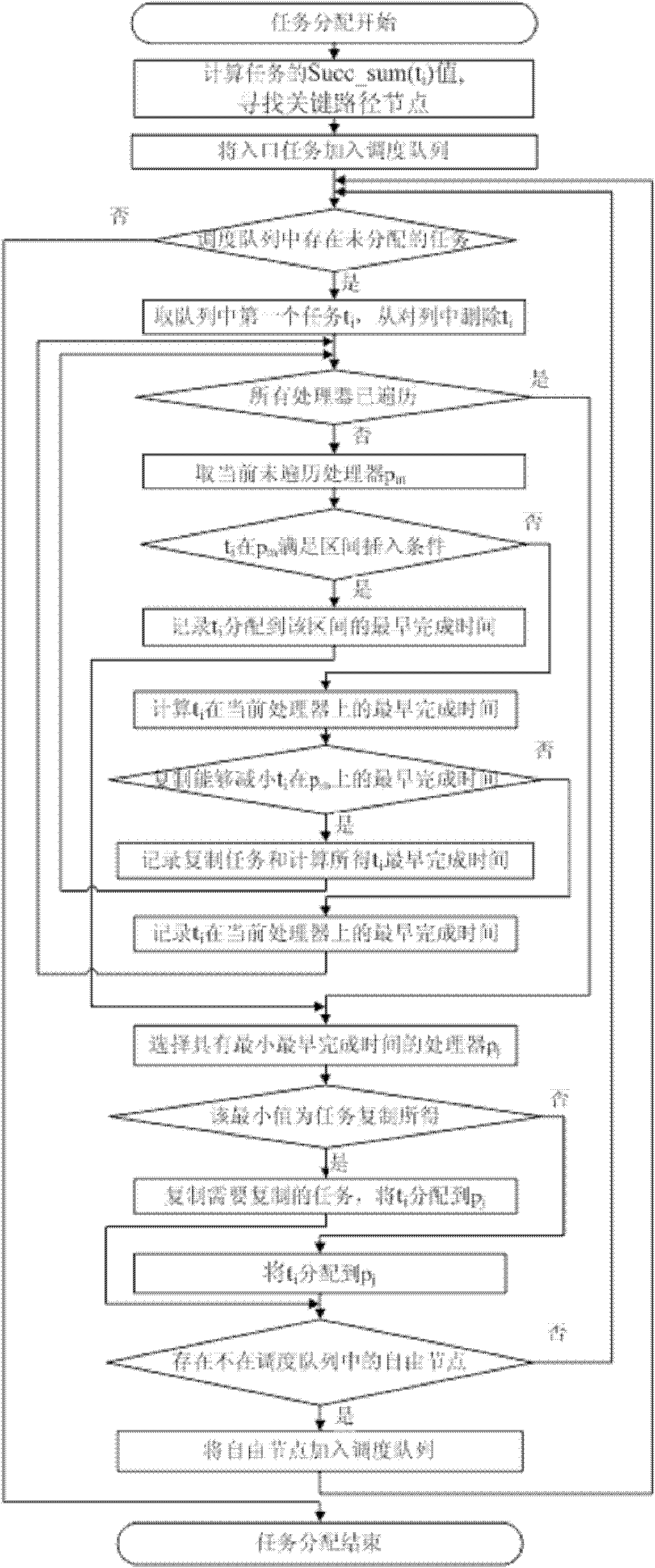
Method for high-efficiency task scheduling of heterogeneous multi-core processor
InactiveCN102193826ARaise priorityOptimize calculation resultsEnergy efficient ICTResource allocationEarliest finish timeCritical path method
The invention provides a method for high-efficiency task scheduling of a heterogeneous multi-core processor. The method comprises the following steps of: clustering certain special tasks which are large in communication overhead and easy to cluster in a task image to a precursor node of the tasks by adopting a linear task clustering method; starting from a topological structure of the whole task image, selecting parameters capable of comprehensively reflecting the importance of the task in the whole task image as priority weights; selecting a free critical path node to perform allocation first, and if multiple free critical path nodes exist, allocating the free critical path nodes in a sequence from high to low according to the node priority weights, and allocating all non-critical path free nodes in a sequence from high to low according to the priority weights; performing redundancy judgment, and deleting redundant tasks in a scheduling result; and performing adjustment according to the scheduling result after deleting the redundant tasks, and recalculating the earliest finish time of each task. According to the method, the efficiency of the task scheduling of the heterogeneous multi-core processor is improved, the power consumption of the processor is reduced, and the performance of the multi-core processor is promoted.
Owner:HARBIN ENG UNIV
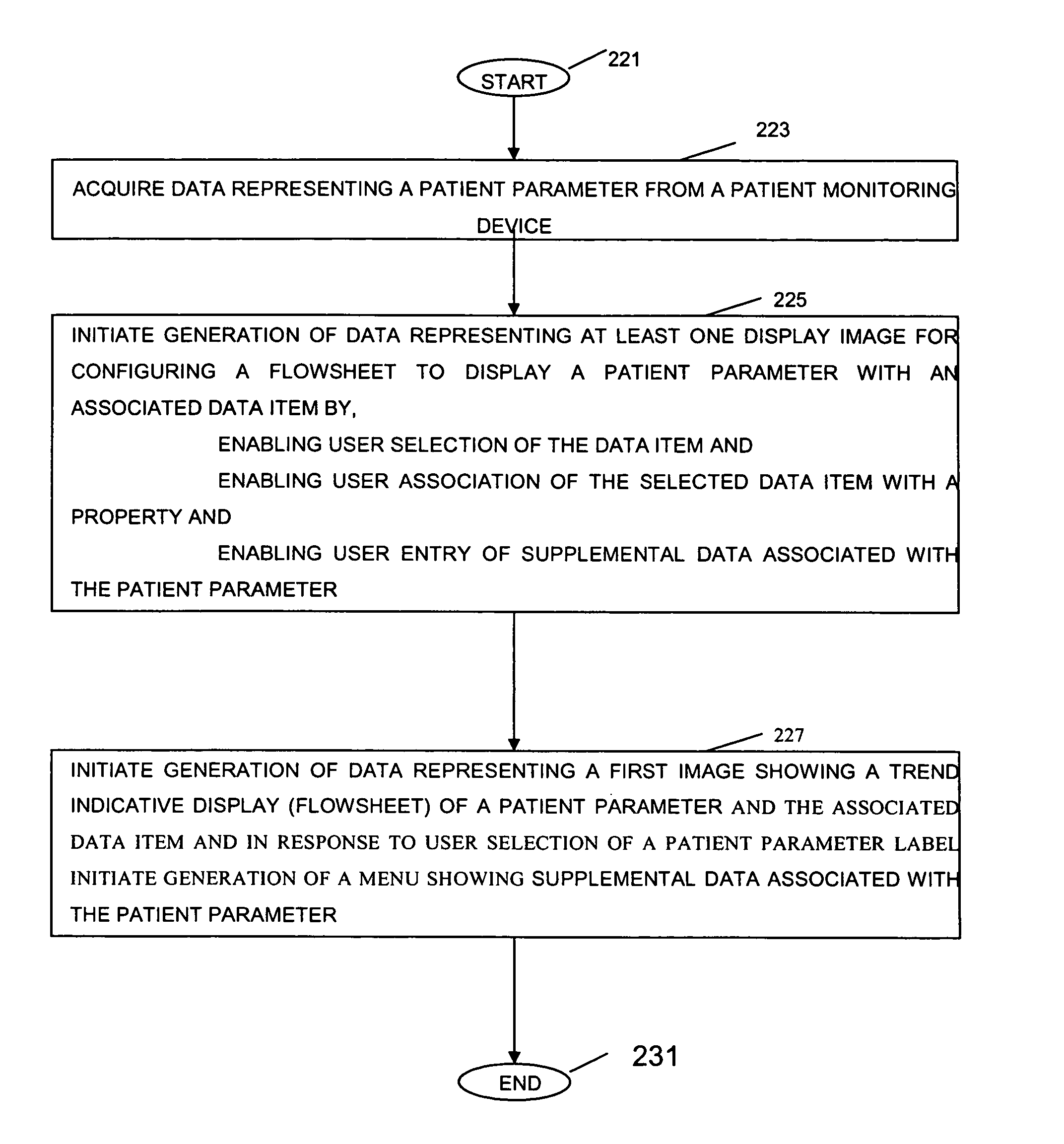
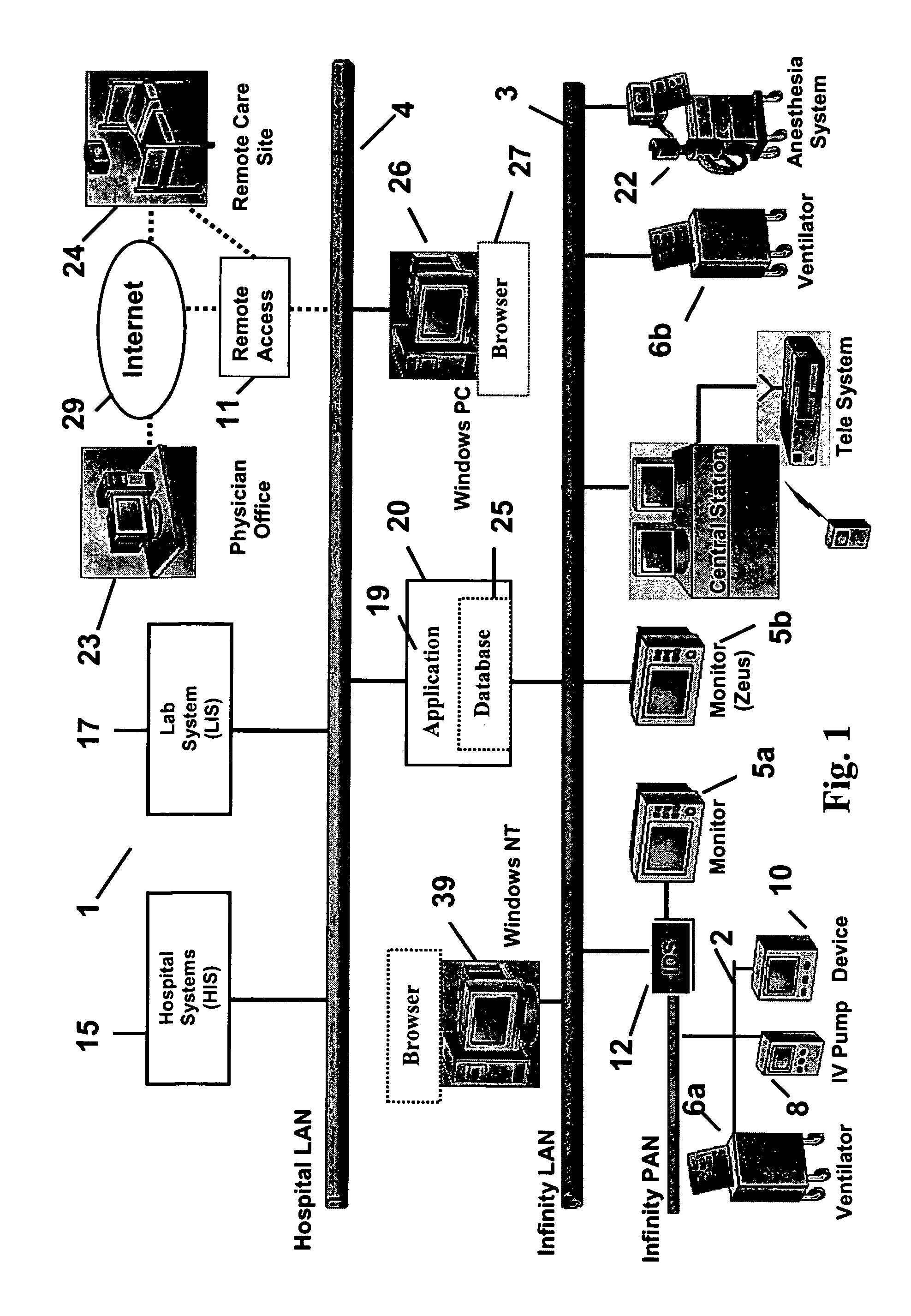
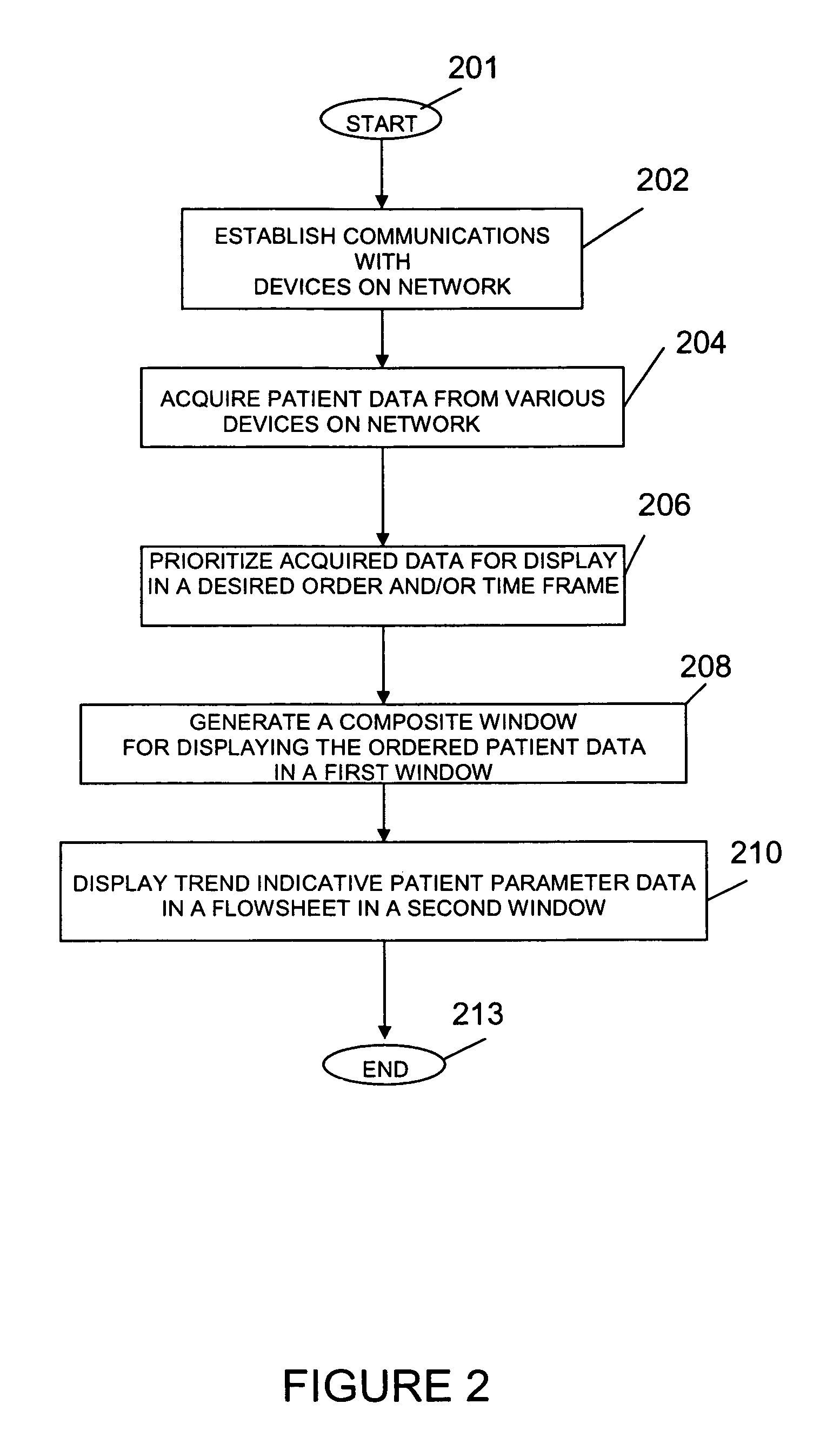
System and user interface for configuring and presenting a trend indicative display of patient medical parameters
ActiveUS7904822B2Increase flexibilityEnabling user configurabilityDrug and medicationsDiagnostic recording/measuringFluid infusionAcquisition time
A system provides an electronic patient parameter Flowsheet offering the flexible features of a paper chart by enabling user configurability of a Flowsheet trend indicative display to incorporate and locate desired patient parameters and associated data items and properties and to hide non-critical supplementary data. A system configures a user interface presenting patient medical parameter data in a trend indicative display indicating a time period comprising user selectable acquisition time intervals. An acquisition processor acquires, from a patient monitoring device, data representing a patient parameter. A processor initiates generation of data representing at least one display image for use in configuring a trend indicative display of a patient parameter and an associated data item by enabling user selection of the data item for trend indicative display and by enabling user association of the data item with a property indicating at least one of, (a) the data item represents volume data to be used in patient fluid infusion or output calculation, (b) the data item represents a rate for use in calculation of volume of patient fluid infusion or output and (c) the data item value is to be used in multiple acquisition time intervals of the trend indicative display.
Owner:DRAGERWERK AG
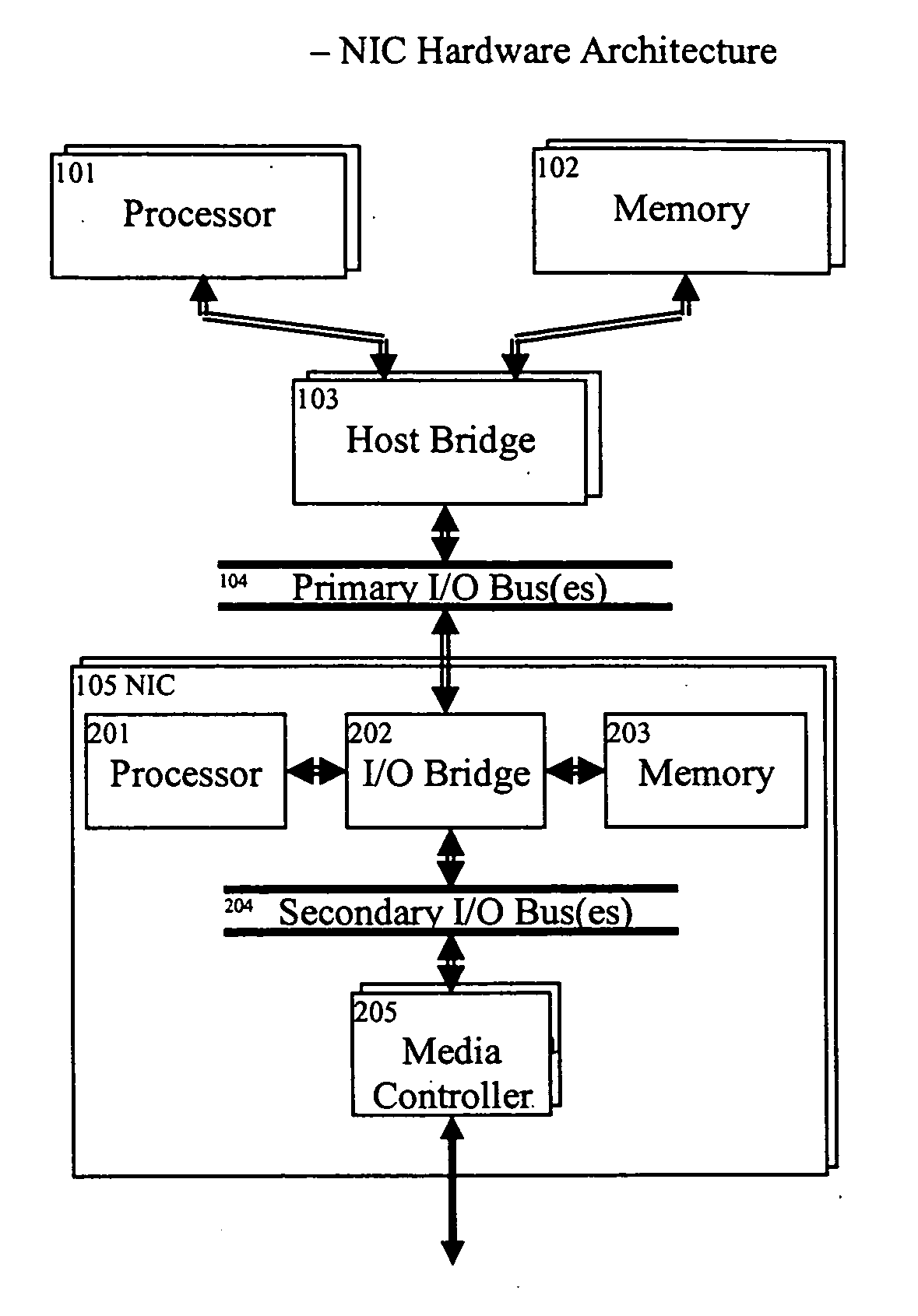
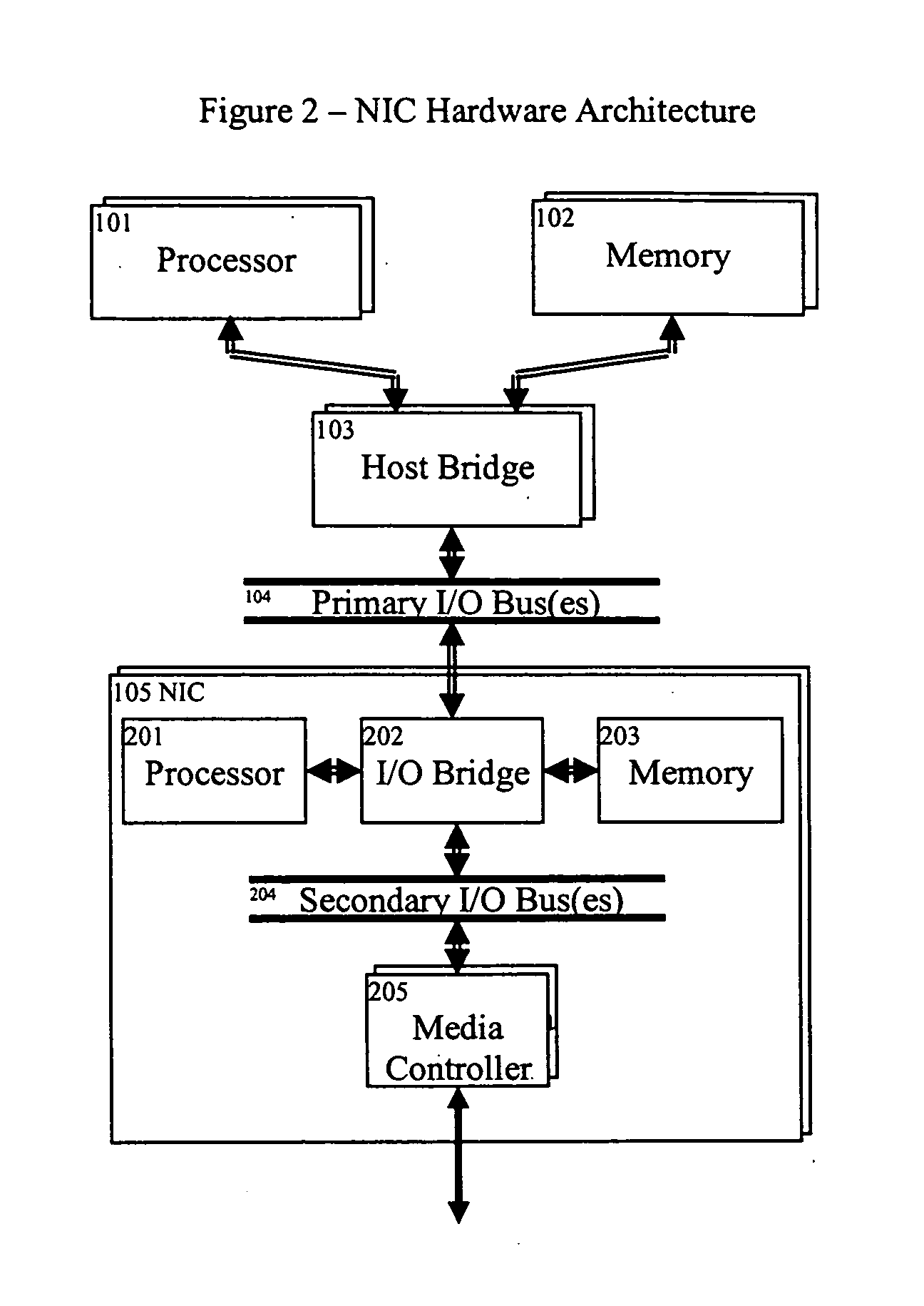
Intelligent network interface card (NIC) optimizations
InactiveUS20090172301A1High rateLow utilizationMultiprogramming arrangementsMultiple digital computer combinationsBusy timeNon critical
Intelligent NIC optimizations includes system and methods for Token Table Posting, use of a Master Completion Queue, Notification Request Area (NRA) associated with completion queues, preferably in the Network Interface Card (NIC) for providing notification of request completions, and what we call Lazy Memory Deregistration which allows non-critical memory deregistration processing to occur during non-busy times. These intelligent NIC optimizations which can be applied outside the scope of VIA (e.g. iWARP and the like), but also support VIA.
Owner:UNISYS CORP
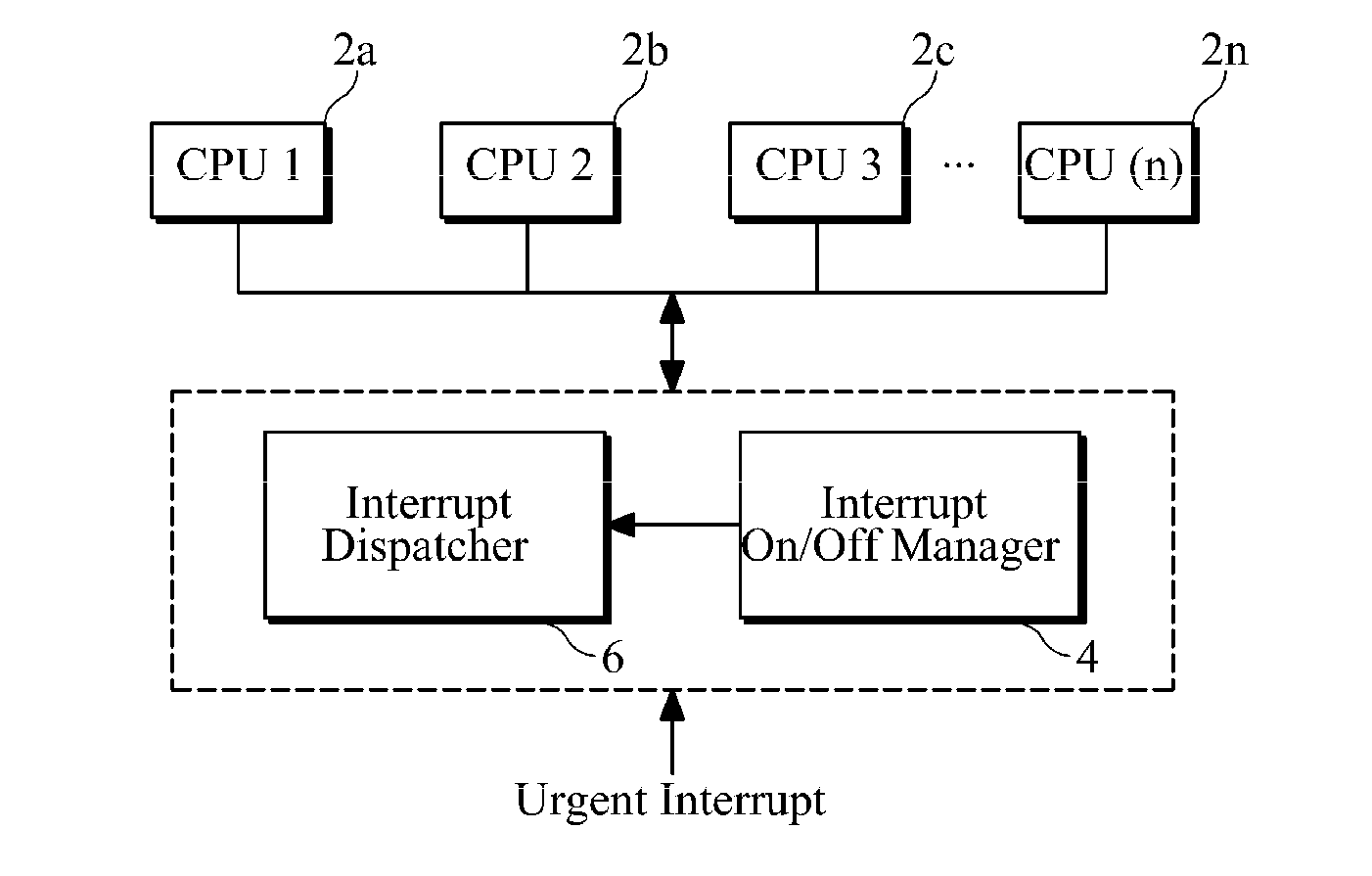
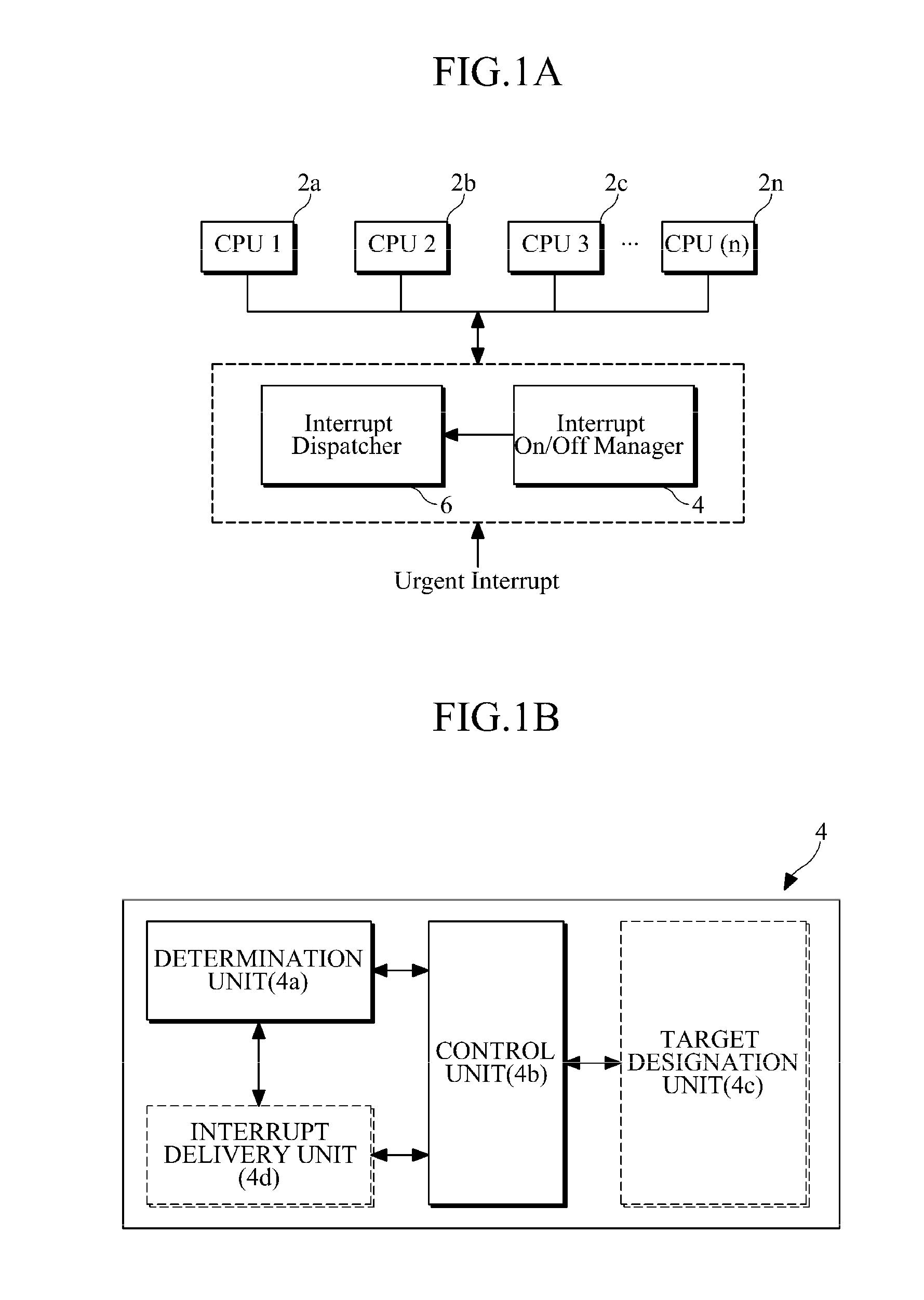
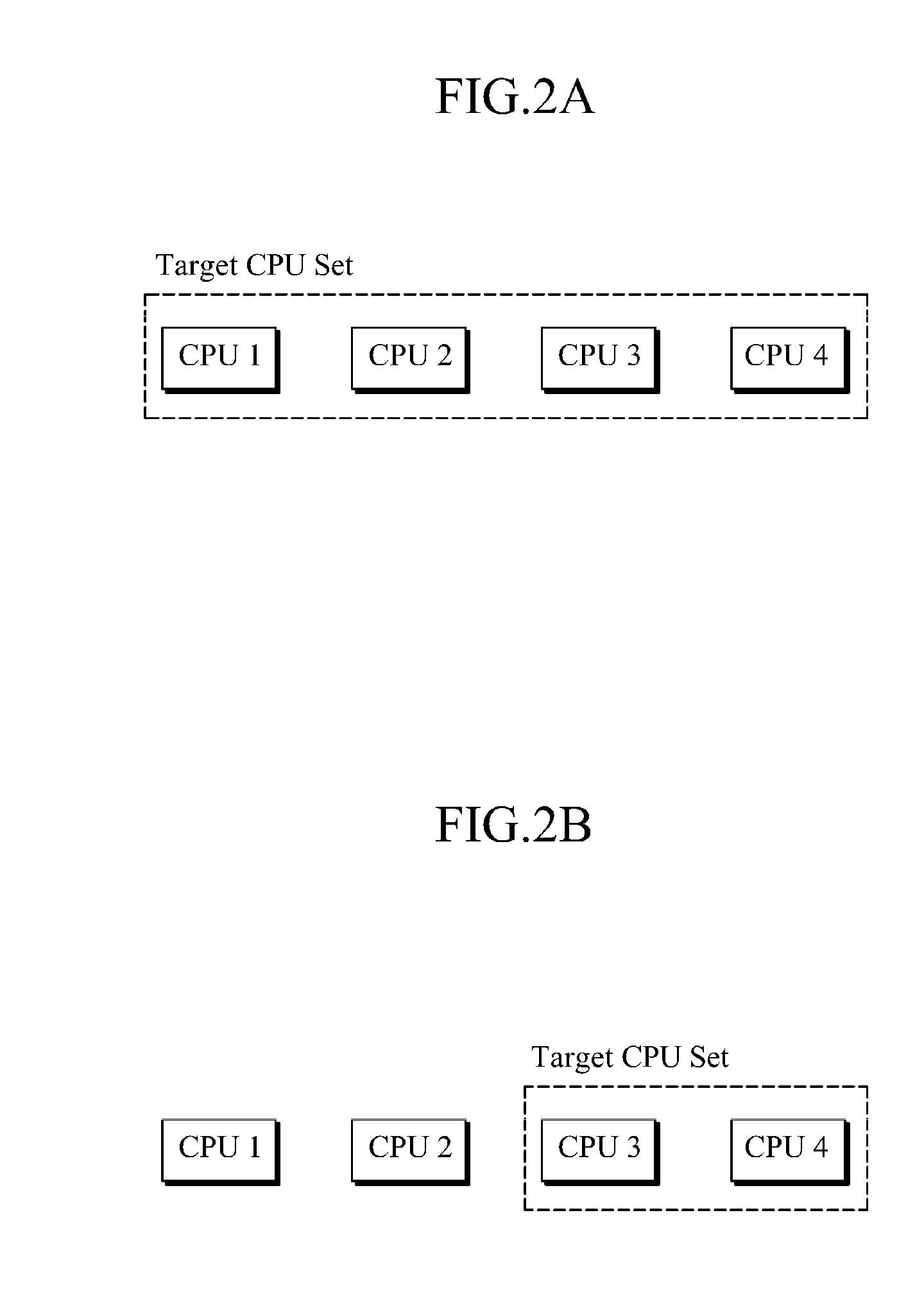
Interrupt on/off management apparatus and method for multi-core processor
InactiveUS20110072180A1Minimize and reduce delayImprove real-time performanceElectric digital data processingCritical sectionCritical zone
Provided are an interrupt on / off management apparatus and method for a multi-core processor having a plurality of central processing unit (CPU) cores. The interrupt on / off management apparatus manages the multi-core processor such that at least one of two or more CPU cores included in a target CPU set can execute an urgent interrupt. For example, the interrupt on / off management apparatus controls the movement of each CPU core from a critical section to a non-critical section such that at least one of the CPU cores is located in the non-critical section. The critical section may include an interrupt-disabled section or a kernel non-preemptible section, and the non-critical section may include an interrupt-enabled section or include both of the interrupt-enabled section and a kernel preemptible section.
Owner:SAMSUNG ELECTRONICS CO LTD
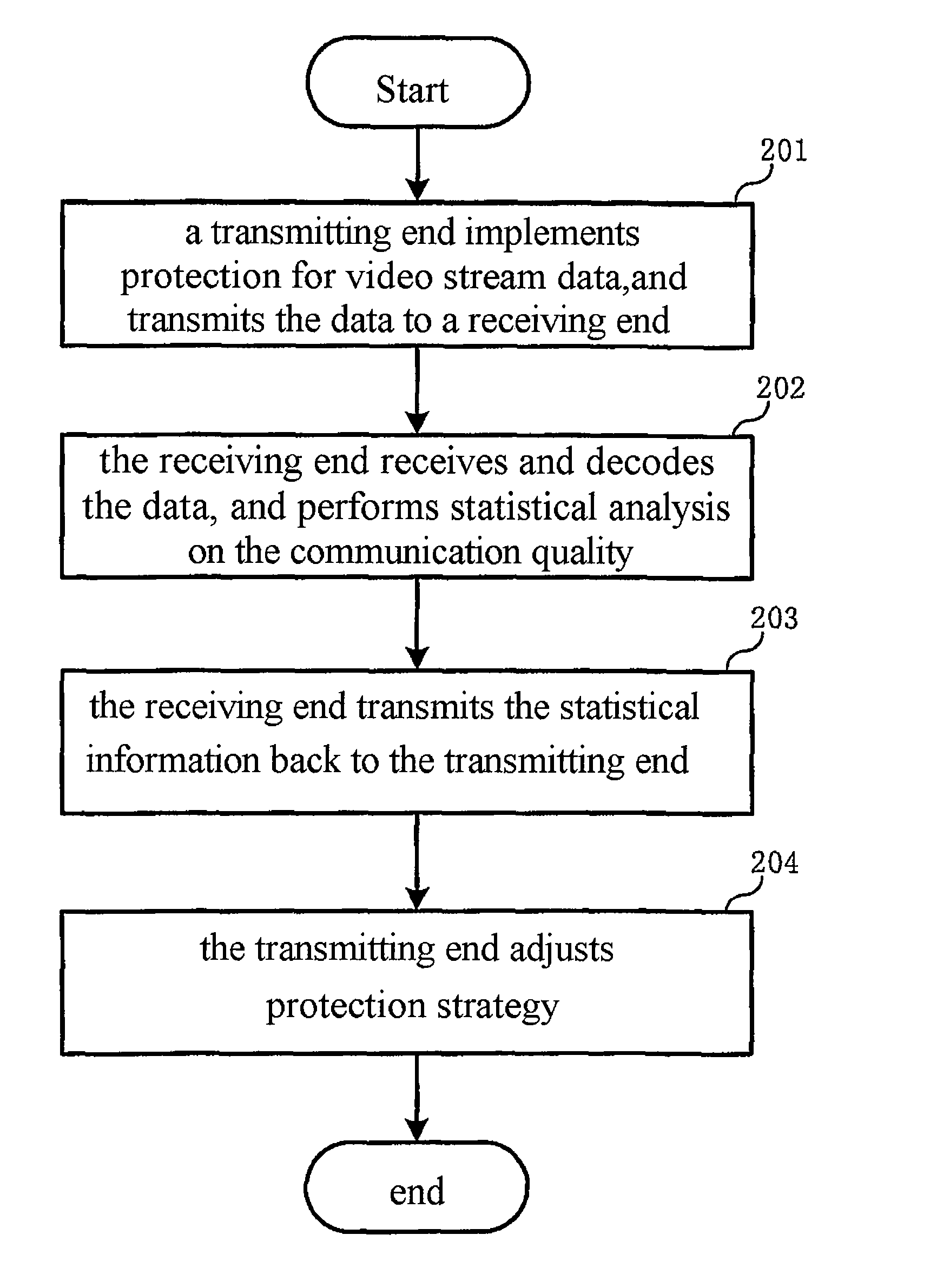
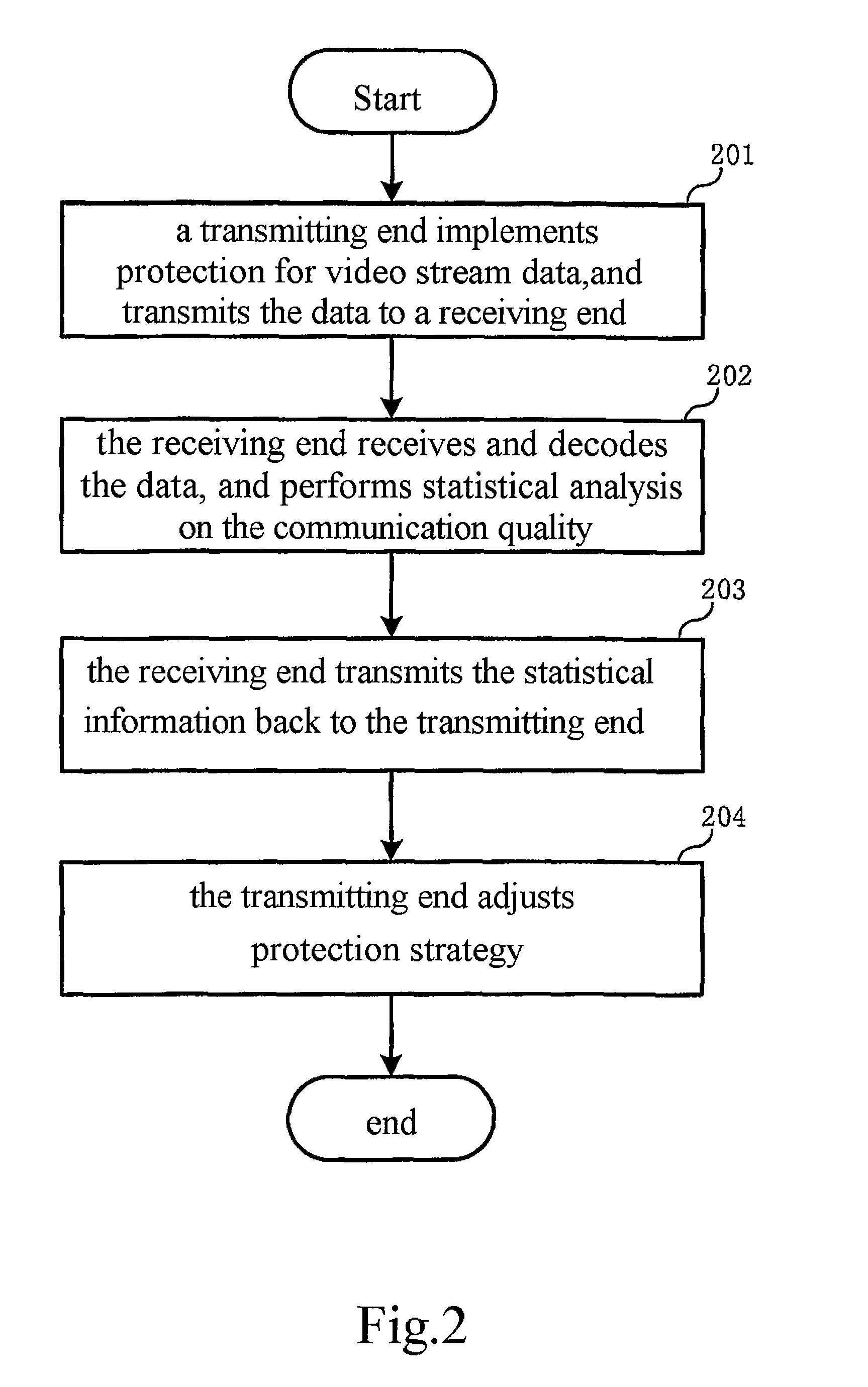
Method for protecting video transmission based on h.264
InactiveUS20080144724A1Statistical information is preciseSave system resourcesPulse modulation television signal transmissionPicture reproducers using cathode ray tubesCommunication qualityVideo transmission
A method for protecting video transmission based on H.264 is disclosed, In the invention, a receiving end performs statistical analysis on the communication quality and the result is fed back to a transmitting end, the transmitting end adjusts the protection strategy self adaptively; the receiving end performs statistical analysis on the accumulated lost slice rate and position information about lost data based on the discontinuous situation of NALU sequence numbers; the receiving end feeds the statistical information back to the transmitting end with extended SEI message; the transmitting end configures two sets of protection strategy systems to separately protect critical data and non critical data, and selects the protection strategy of appropriate level according to the accumulated lost slice rate that is fed back; the receiving end transmits position information about lost data back to the transmitting end; the transmitting end resends the lost data.
Owner:HUAWEI TECH CO LTD
Enhanced public safety communication system
ActiveUS8504090B2Emergency connection handlingTransmission systemsDisseminationBroadband communication
A communication system (100) provides collaboration between narrowband communication devices (102) and broadband communication devices (104) operating over different networks. The communication devices (102, 104) are linked to provide peer-to-peer communication that supports the dissemination of public safety information to a public safety personnel user utilizing the devices. Applications within the devices (102, 104) automatically control features amongst the plurality of devices for redundancy of critical information, removal of non-critical information and power management. Context information can also be examined and shared between amongst the devices.
Owner:MOTOROLA SOLUTIONS INC
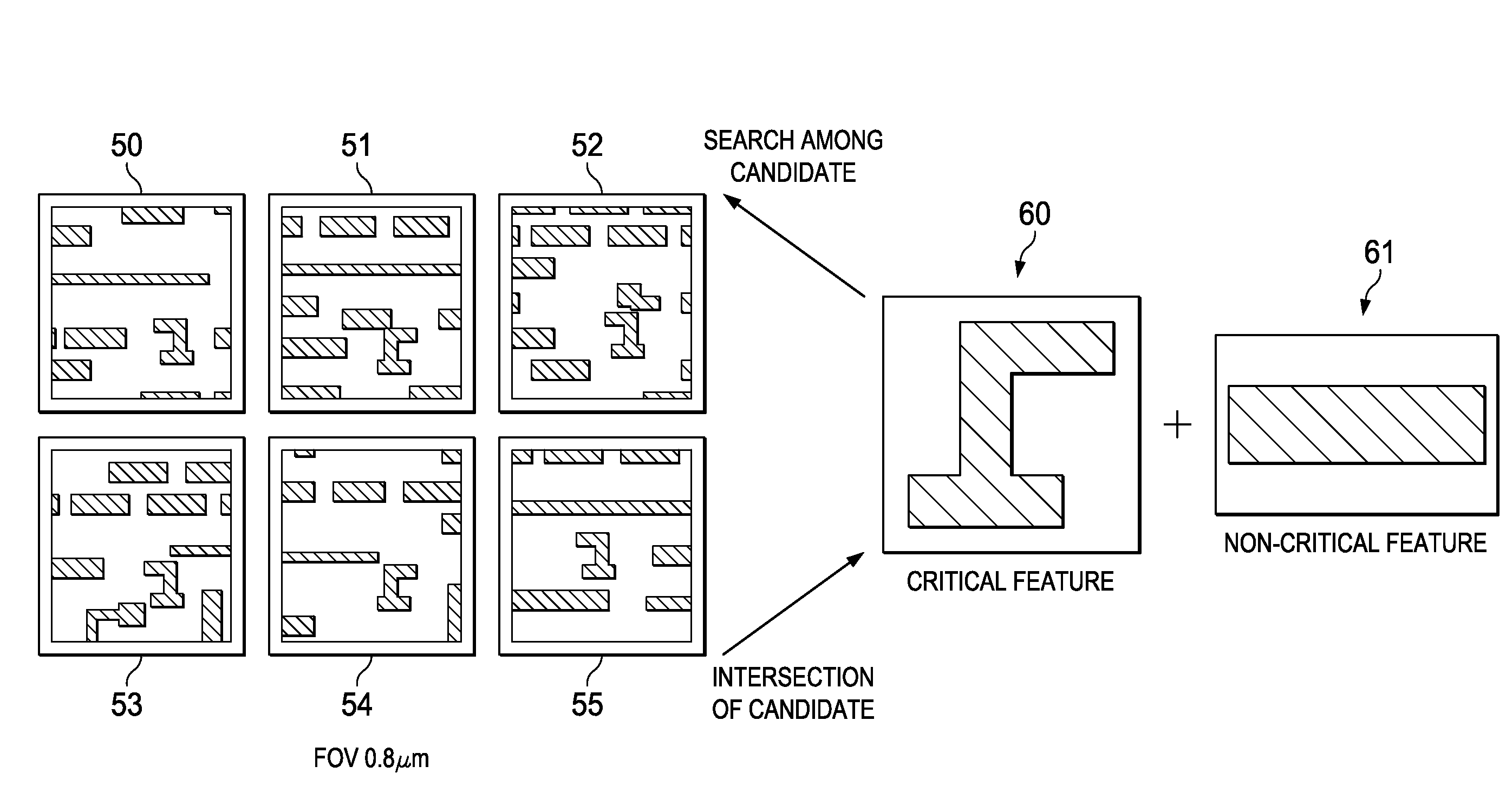
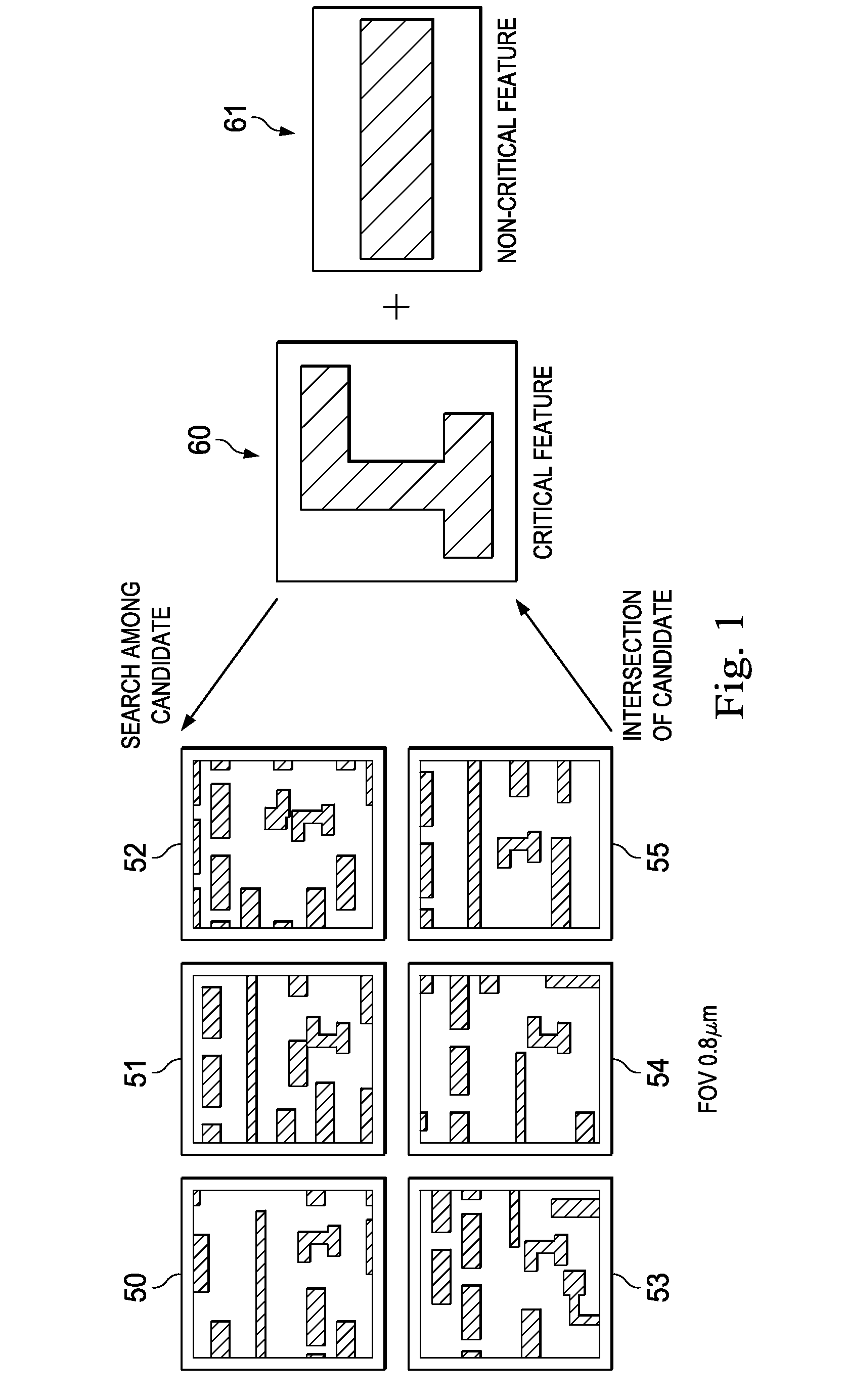
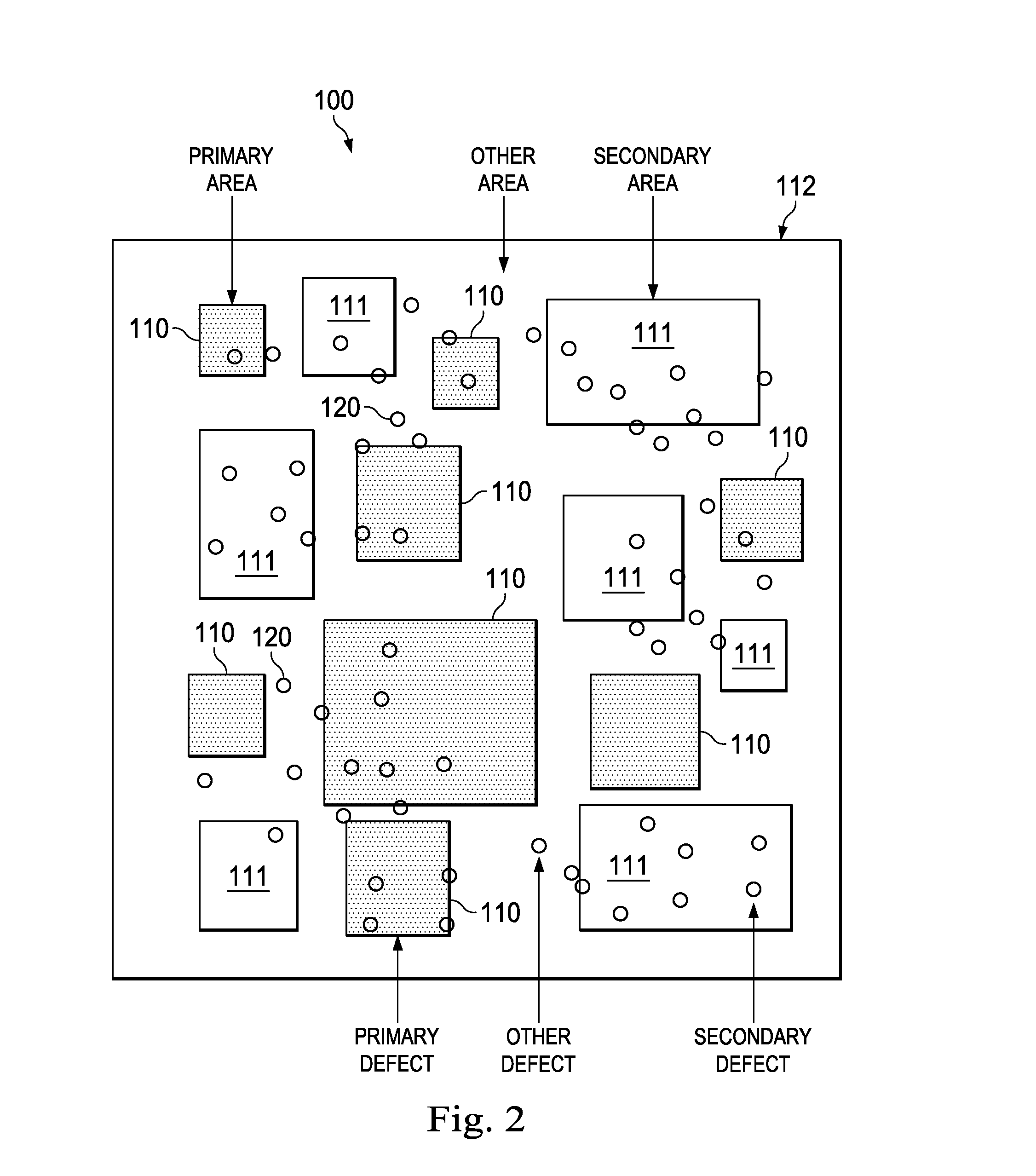
Method and Apparatus for Extracting Systematic Defects
The present disclosure provides a method of systematic defect extraction. Primary and secondary areas are defined in a wafer layout. A plurality of defects is identified by a first wafer inspection for an outside-process-window wafer. Defects located in the secondary area are removed. Defects associated with non-critical semiconductor features are also removed via a grouping process. Sensitive regions are defined around defects associated with critical semiconductor features. A second inspection is then performed on the sensitive regions for an inside-process-window wafer, thereby identifying a plurality of potentially systematic defects. Thereafter, a Scanning Electron Microscopy (SEM) process is performed to determine whether the defects in the sensitive regions of the inside-process-window wafer are true systematic defects.
Owner:TAIWAN SEMICON MFG CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com