Mobile-terminal ultra-low power consumption and high safety communication method
A mobile terminal, high security technology, applied in the field of data communication, can solve the problems of user loss, need a long time, high power consumption, etc., to achieve the effect of improving security, avoiding theft, and low power consumption
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
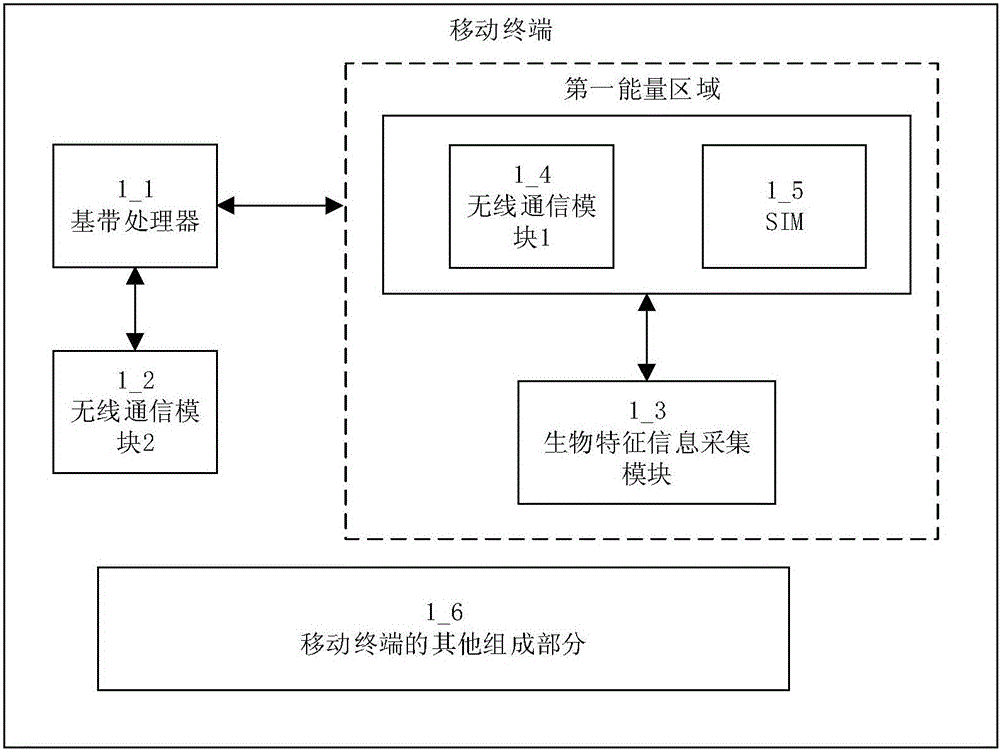
[0051] like Figure 13 As shown, a mobile terminal ultra-low power consumption communication method, the SIM unit forms a judgment result output according to identity information and standard verification information when the mobile terminal is in standby mode, and the standby mode is when the screen of the mobile terminal is in Off state, no information is displayed, and the screen is in a power-off state, but not limited to the above-mentioned states; specifically include:
[0052] Step A1, the standard verification information of the user is prefabricated in the SIM unit;
[0053] Step A2, when the first communication module in the mobile terminal receives an identity verification request, the identity information collection module of the mobile terminal acquires the identity information of the current user;
[0054] Step A3, judging whether the identity information matches the standard verification information, and outputting a judging result.
[0055] It should be noted...
Embodiment 2
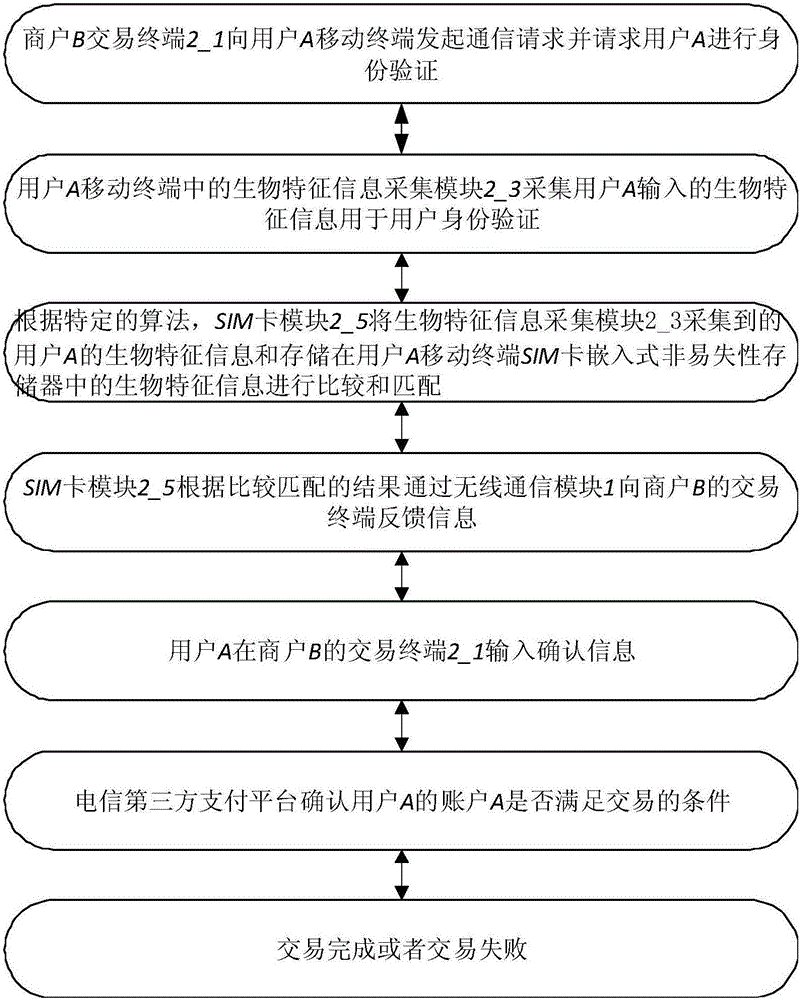
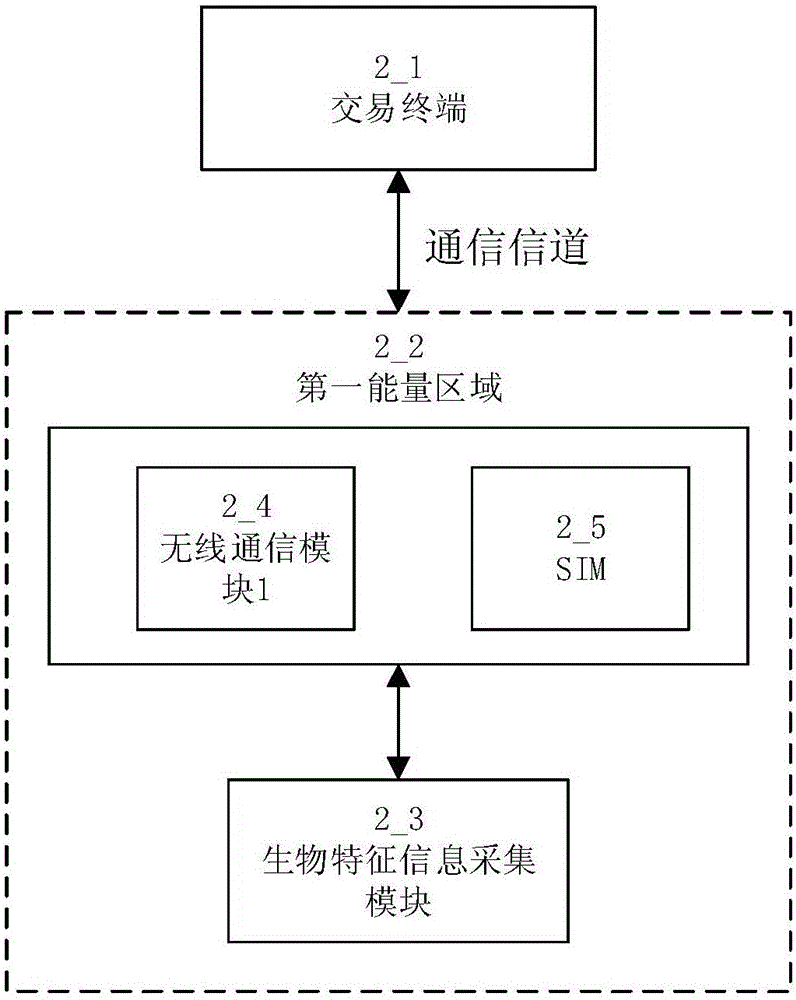
[0057] This embodiment proposes a method for completing micropayment without starting the application processor or / and baseband processor of the mobile terminal and with high security and ultra-low power consumption, by storing the biometric information in the SIM card (SIM Unit) in the embedded non-volatile memory, so as to ensure the absolute security of the standard verification information (the biometric information is used as an example below), by adding a first communication module, the mobile terminal communicates with the external identity authentication terminal through the first communication module (transaction terminal) to communicate, the communication protocol that the first communication module communicates with the external identity authentication terminal is a short-distance wireless communication protocol, such as NFC, RF, BLE and ZigBee, etc., the absolute security of fingerprint information is guaranteed by this embodiment, At the same time, micropayment can...
Embodiment 3
[0069] Compared with the ultra-low power consumption offline transaction mode proposed in the second embodiment, this embodiment also proposes two online transaction modes, which are the first online transaction mode and the second online transaction mode. The online transaction mode is explained.
[0070] The first online transaction mode is the situation where users use terminals other than mobile terminals, such as computers, to purchase commodities. The specific structure is as follows: Figure 4 shown, with Figure 4 Among them, 4_1 is the terminal used by the user to purchase goods, and the terminal is a terminal other than a mobile terminal, such as a computer, etc. 4_2 is a third-party trading platform for telecommunications, and 4_3 is a merchant. In a traditional situation, a user needs to enter a password for authentication when purchasing goods for payment, but since the password may be stolen and cracked, the security of using a password for authentication in a t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com