Method for generating security file system of smart card
A security file and smart card technology, applied in response to error generation, internal/peripheral computer component protection, instruments, etc., can solve the problems of poor file system security, poor scalability and controllability, and high file system management overhead
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
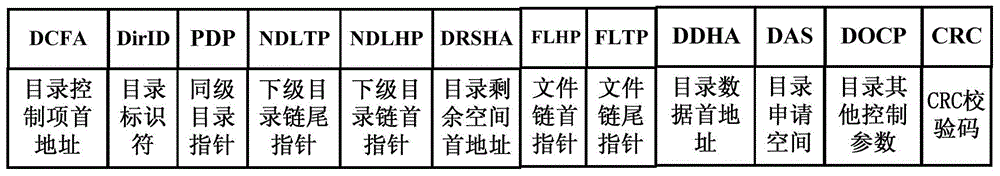
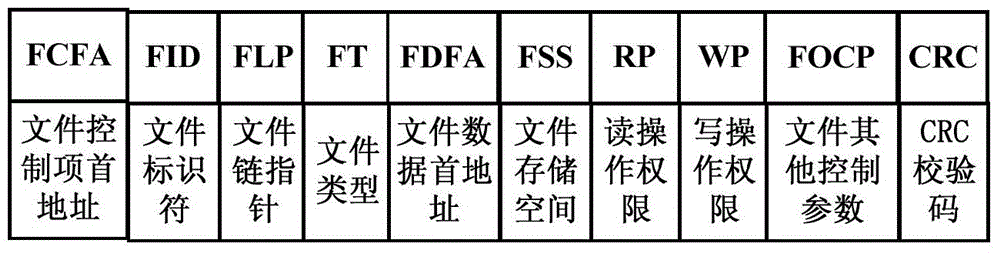
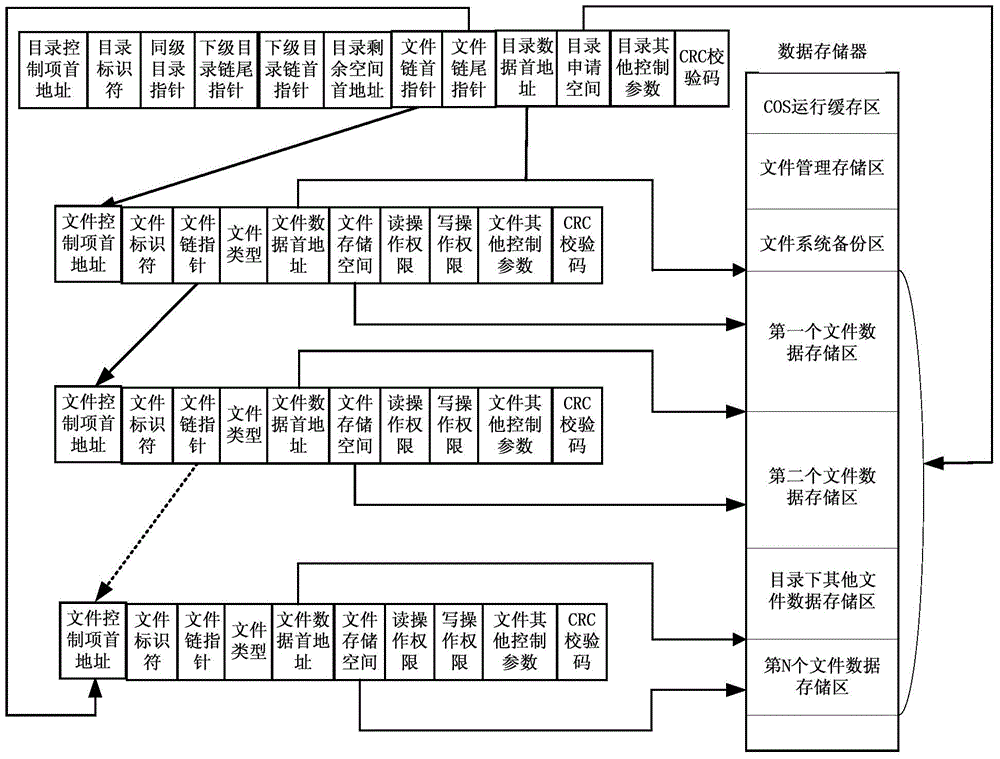
[0055] Such as figure 1 As shown, the directory control item consists of the directory control item header address (DCFA), directory identifier (DirID), peer directory pointer (PDP), lower-level directory chain head pointer (NDLHP), lower-level directory chain tail pointer (NDLTP), directory Remaining space head address (DRSHA), file chain head pointer (FLHP), file chain tail pointer (FLTP), directory data head address (DDHA), directory application space (DAS), directory other control parameters (DOCP) and CRC check code composition.
[0056] The directory identifier consists of 2 bytes. The root directory identifier is specified as 3F00. The directory identifier is one of the parameters to find out whether the directory exists. Each directory must have a directory identifier, and the directory identifiers of the same-level directories cannot be the same . The same-level directory pointer points to the directory control item of the same-level directory. When the pointer is e...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com