Smart card safety protection circuit and smart card safety protection method
A security protection, smart card technology, applied in computer security devices, electrical digital data processing, internal/peripheral computer component protection, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] The method and its specific implementation will be described in detail below in conjunction with the accompanying drawings.
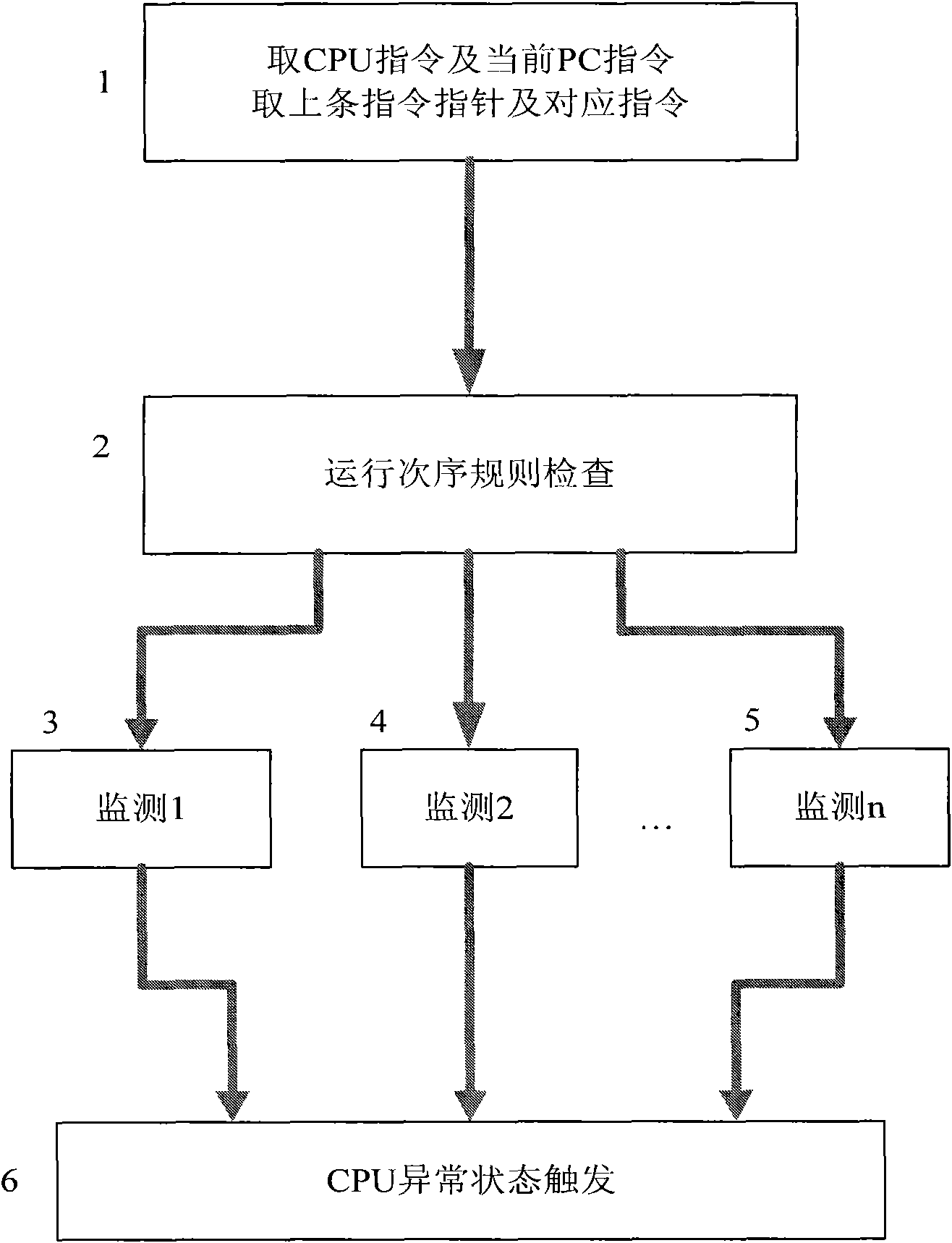
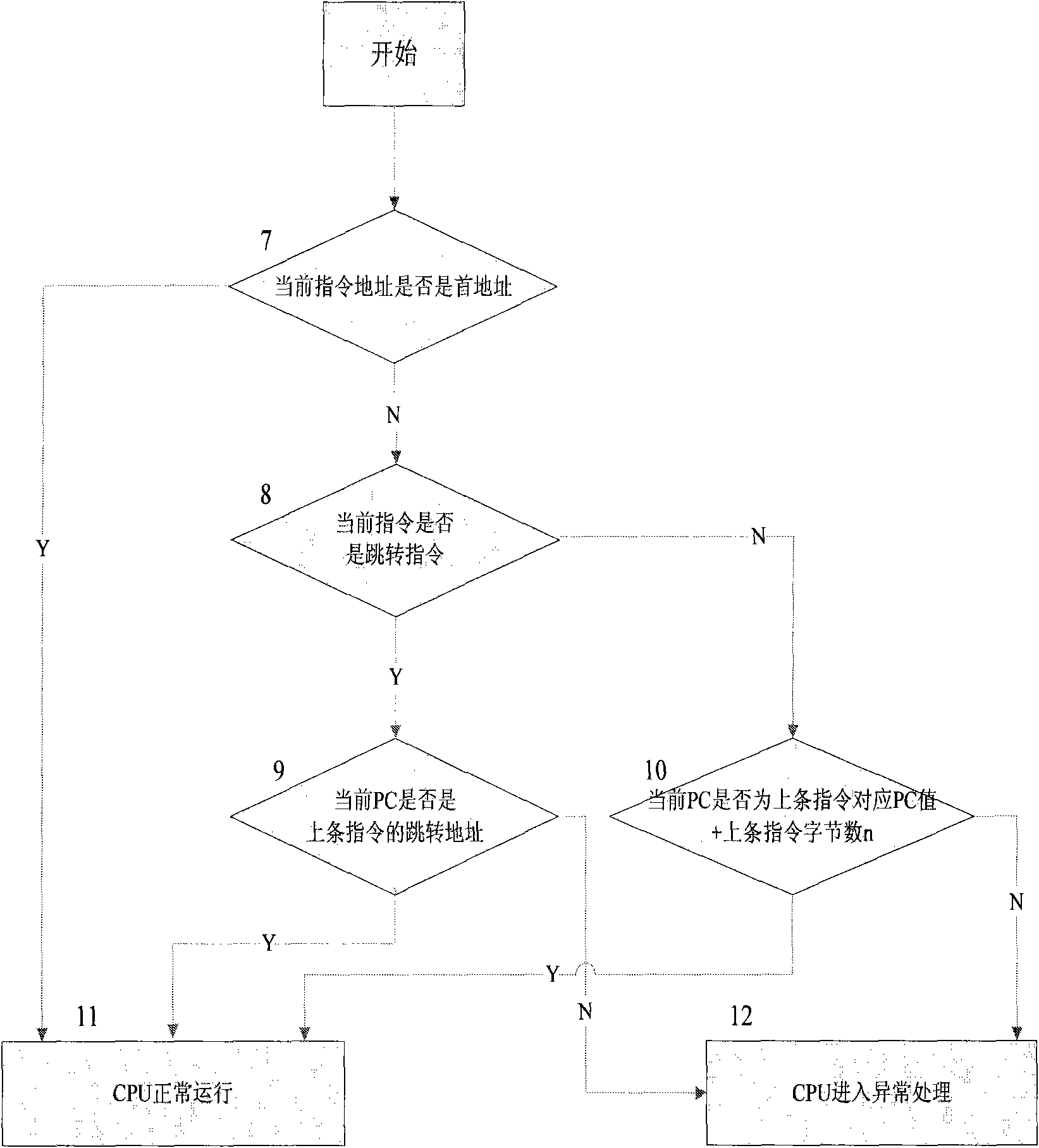
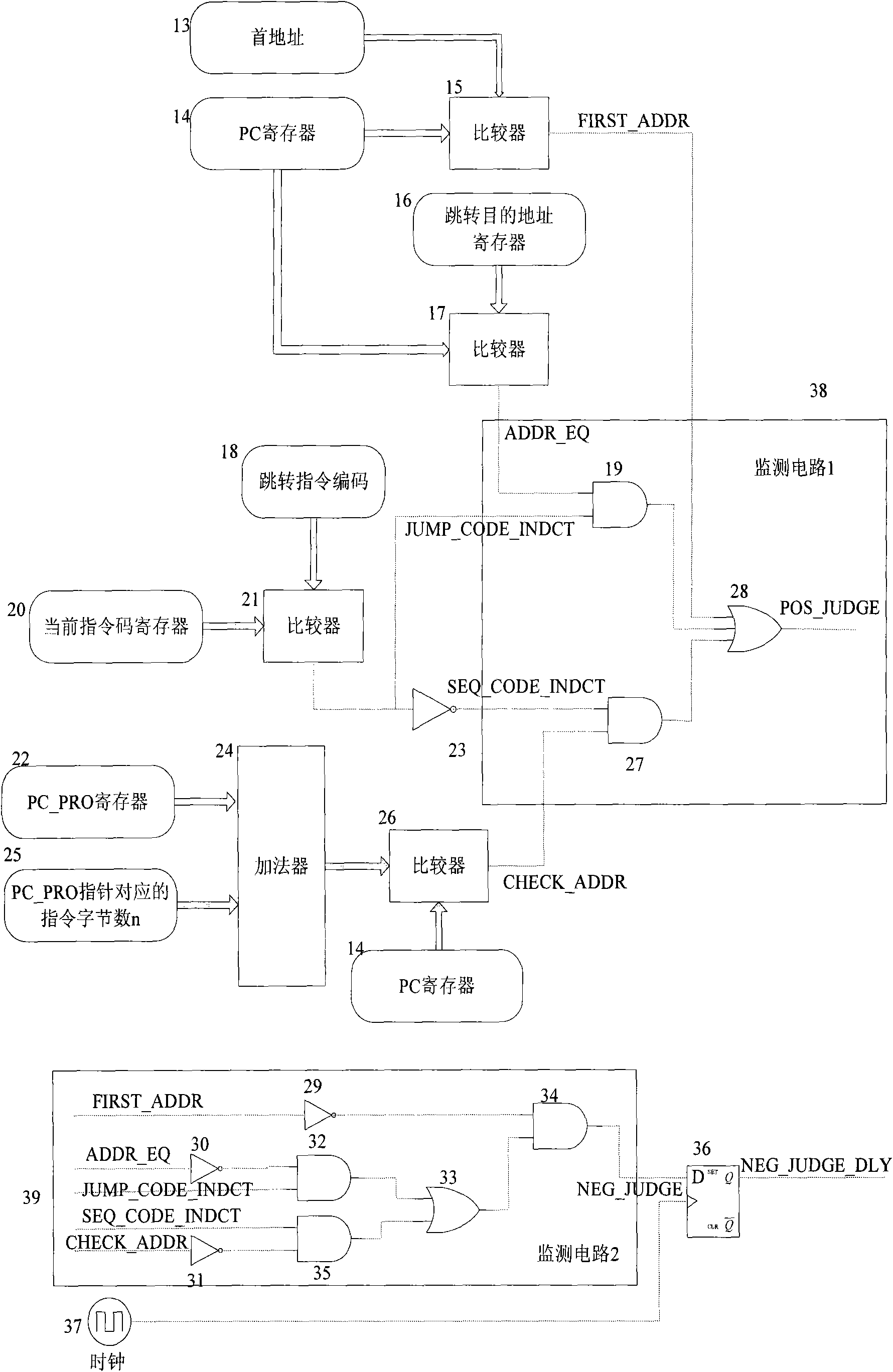
[0026] figure 1 For overall block diagram of the present invention, at first take out this bar instruction code and program pointer PC (abbreviation PC pointer) and last instruction code and PC pointer (1) (do not take out last instruction code and PC pointer when running the first instruction ); check in real time whether the operation of the CPU conforms to the operation order rule (2), and monitor the output signal of the inspection. The monitoring method has the characteristics of time-sharing and distribution, that is, two or more monitoring circuits ((3) , (4),...(5))) Monitor whether the operation of the CPU conforms to the operation sequence rules, and output two or more monitoring signals including high and low logic levels. Once an abnormality occurs, these monitoring signals Trigger the smart card chip to enter abnormal processing (6...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com