Smart card security session system
A technology for secure sessions and smart cards, applied in computer security devices, public keys for secure communications, user identity/authority verification, etc., and can solve problems such as smart card security issues
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
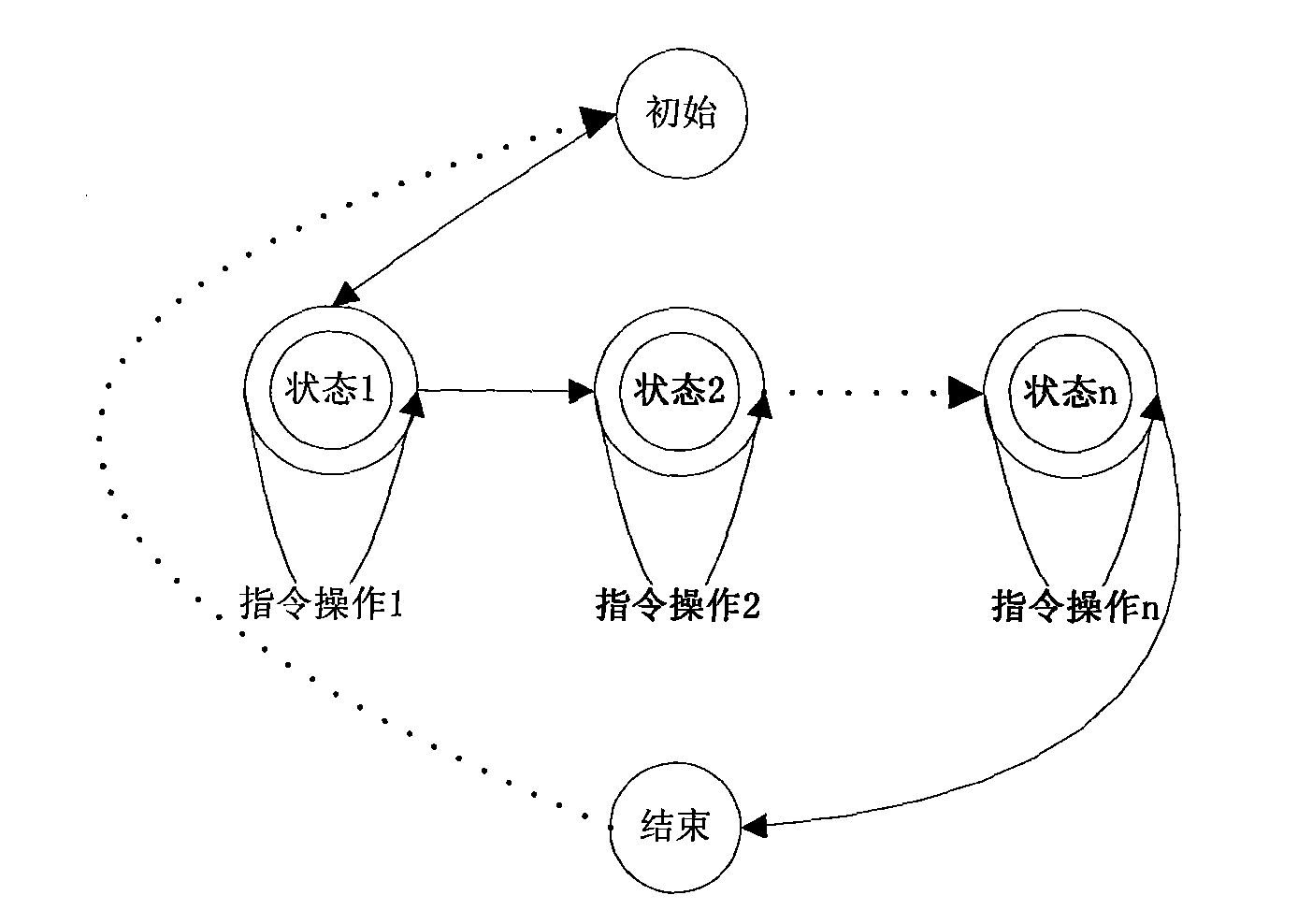
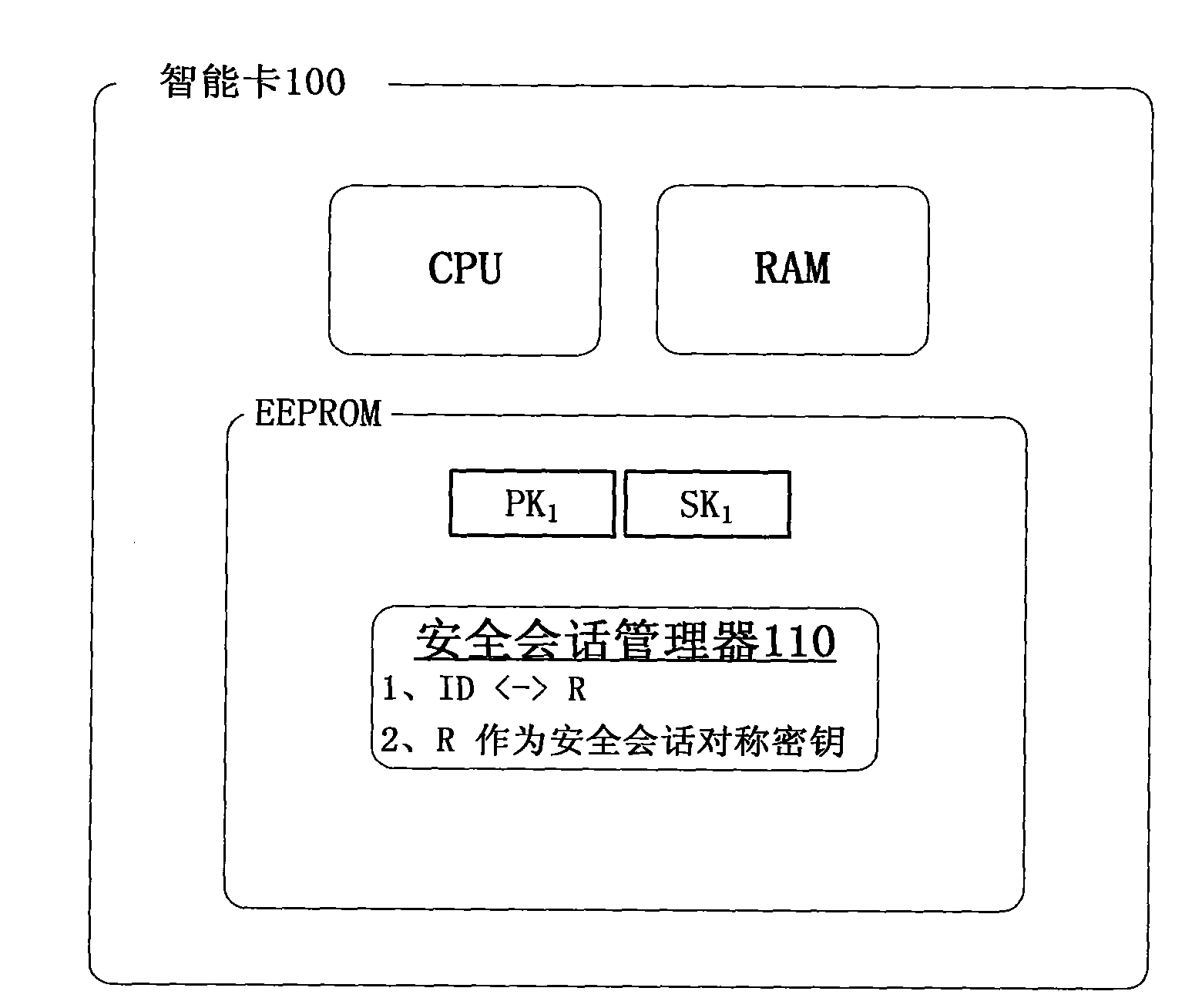
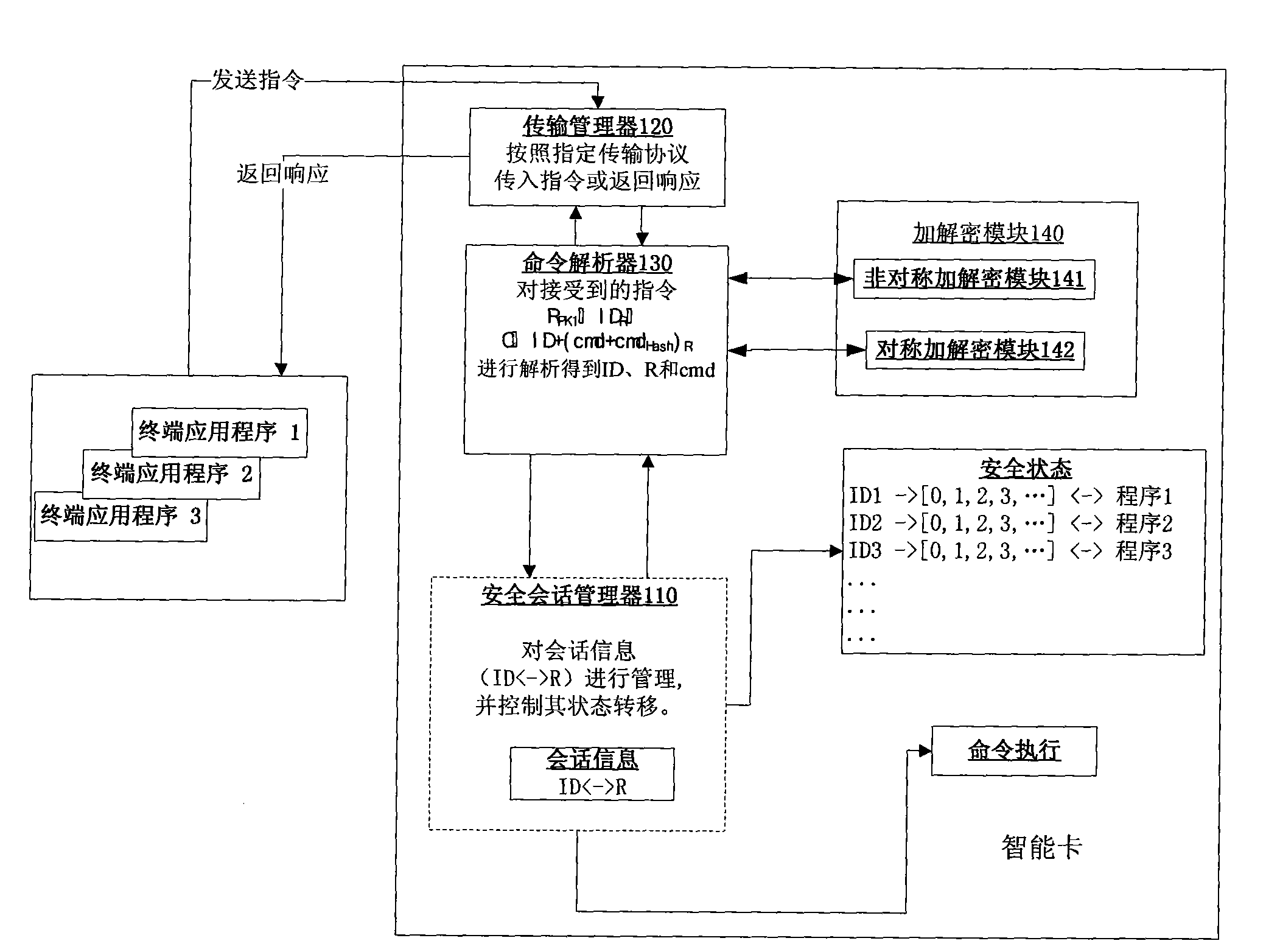
[0051] Based on the above smart card system design, the present invention takes asymmetric encryption and decryption RSA algorithm and symmetric encryption 3DES algorithm as examples, assuming that there is a public-private key pair PK for encryption and decryption hosted by CA on the smart card 1 and SK 1 , using this key pair as the public-private key pair of the secure session, the following smart card secure session communication workflow is proposed: (see image 3 )
[0052] 1) The terminal application reads the public key on the smart card as the secure session public key PK 1 ;
[0053] 2) The terminal application generates a random number R and uses the secure session public key PK 1 Encrypt the random number R to get R PK1 and send it to the smart card;
[0054] 3) Secure session private key SK for smart card 1 Decrypt R PK1 Get the random number R, then generate the security session identification ID of the current application program, and the security session...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com