Method for identifying communication object of smart card
A technology of communication object and smart card, which is applied in the direction of cooperative devices, instruments, electrical components, etc., and can solve the problems of smart card security and other issues
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
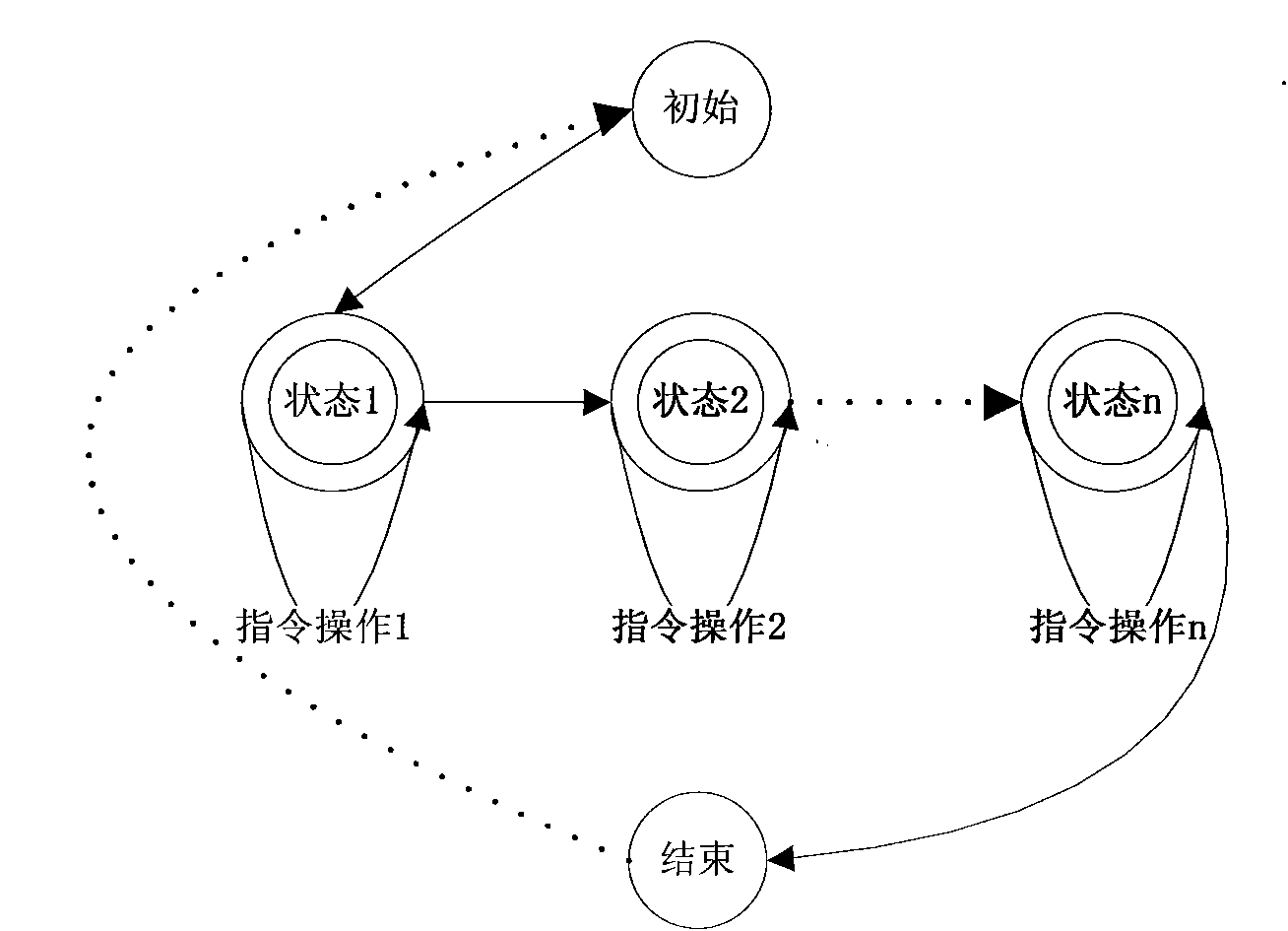
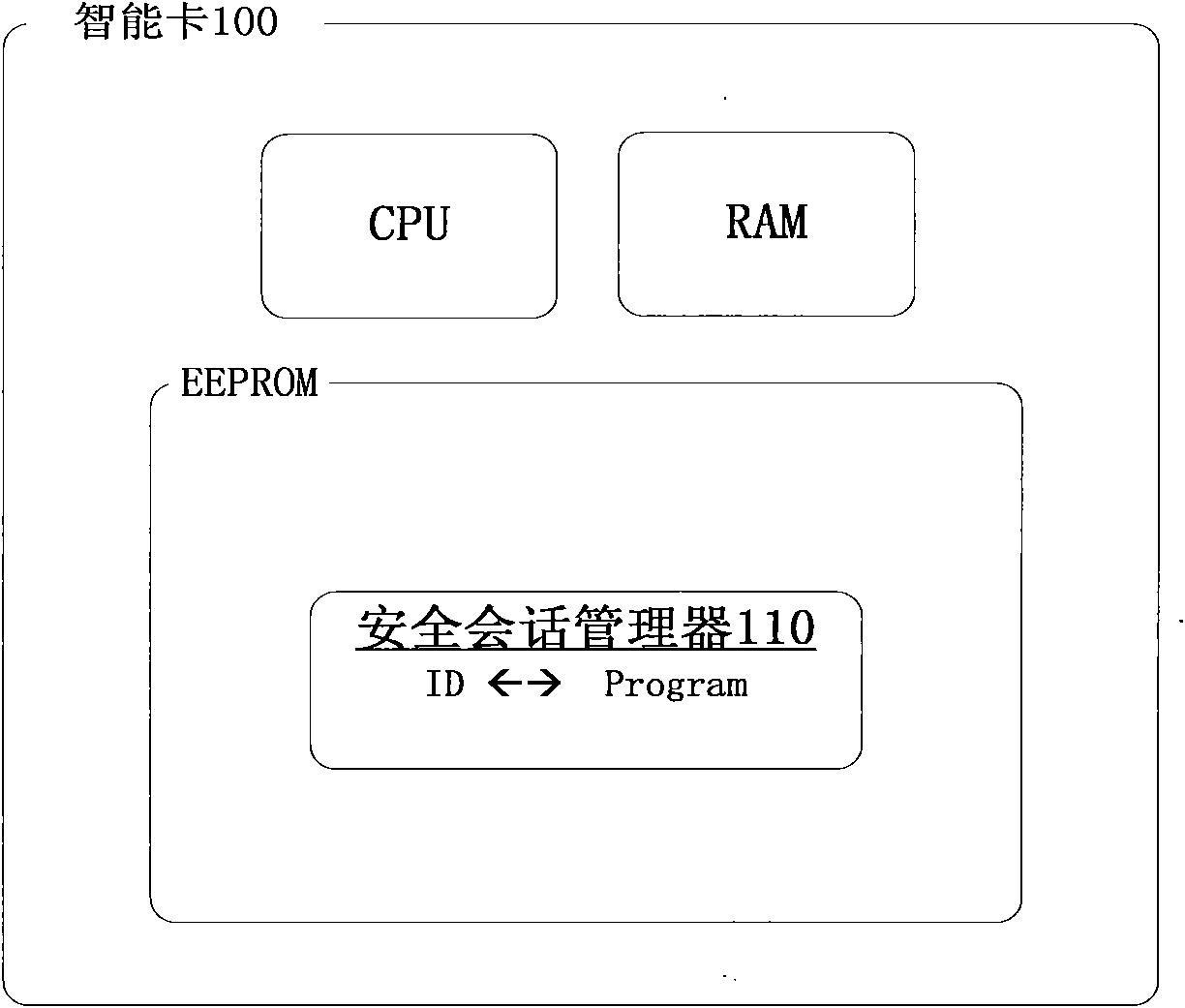
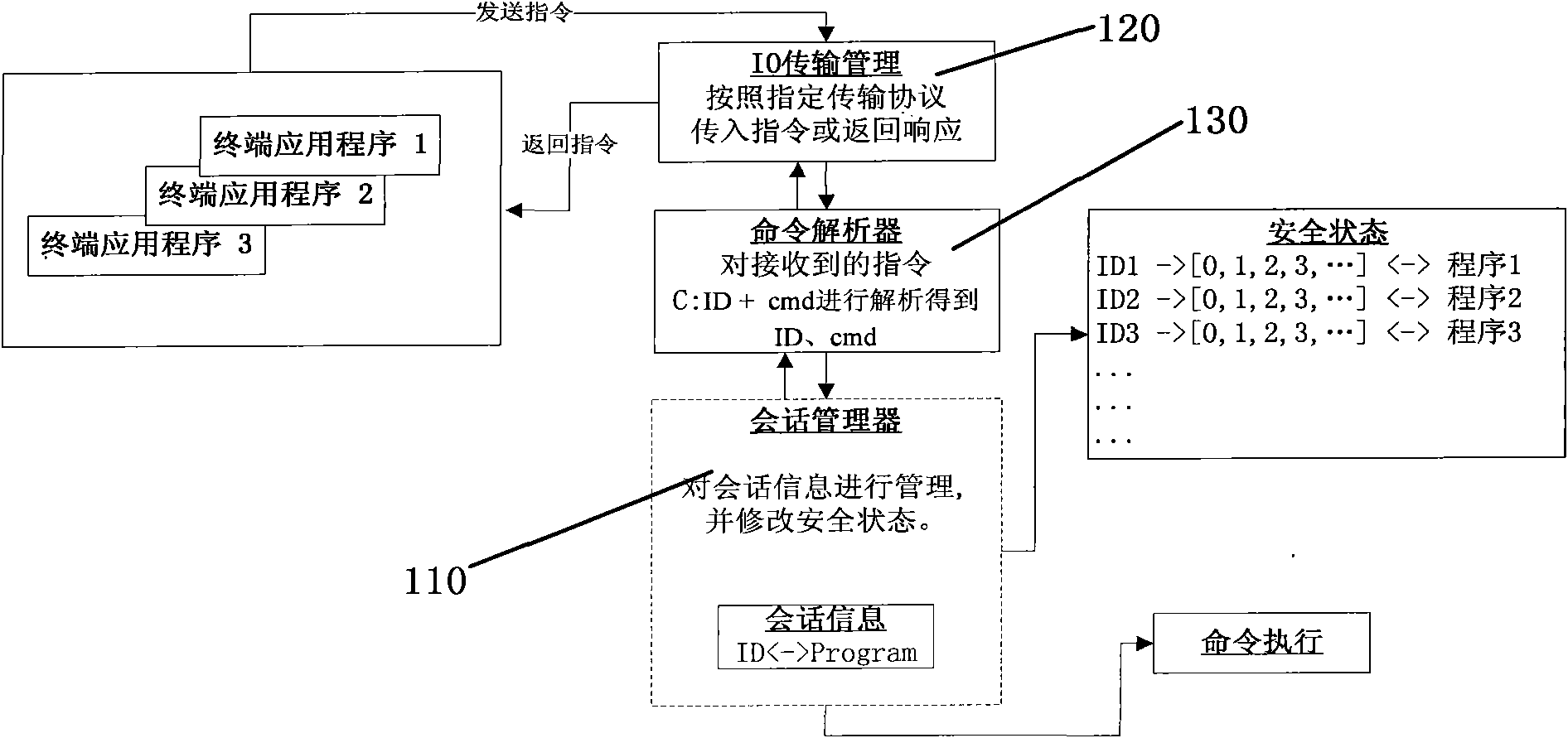
[0042] Such as figure 2 , image 3 As shown, a method for identifying a smart card communication object of the present invention comprises the following steps:
[0043] (1) The terminal application initiates a secure session and generates a random number as a secure session identifier;
[0044] (2) Mapping the generated security session ID, and then returning the security session ID to the terminal application;
[0045] (3) When the terminal application program accesses the smart card, it is necessary to send the command and the security session identifier to the smart card, and the smart card parses the command to obtain the command;
[0046] (4) The smart card decides whether to allow the terminal application to access according to the received information.
[0047] In the present invention, the smart card 100 is composed of a secure session manager 110, a transmission manager 120 and a command parser 130, and the secure session manager 110, the transport manager 120 and...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com