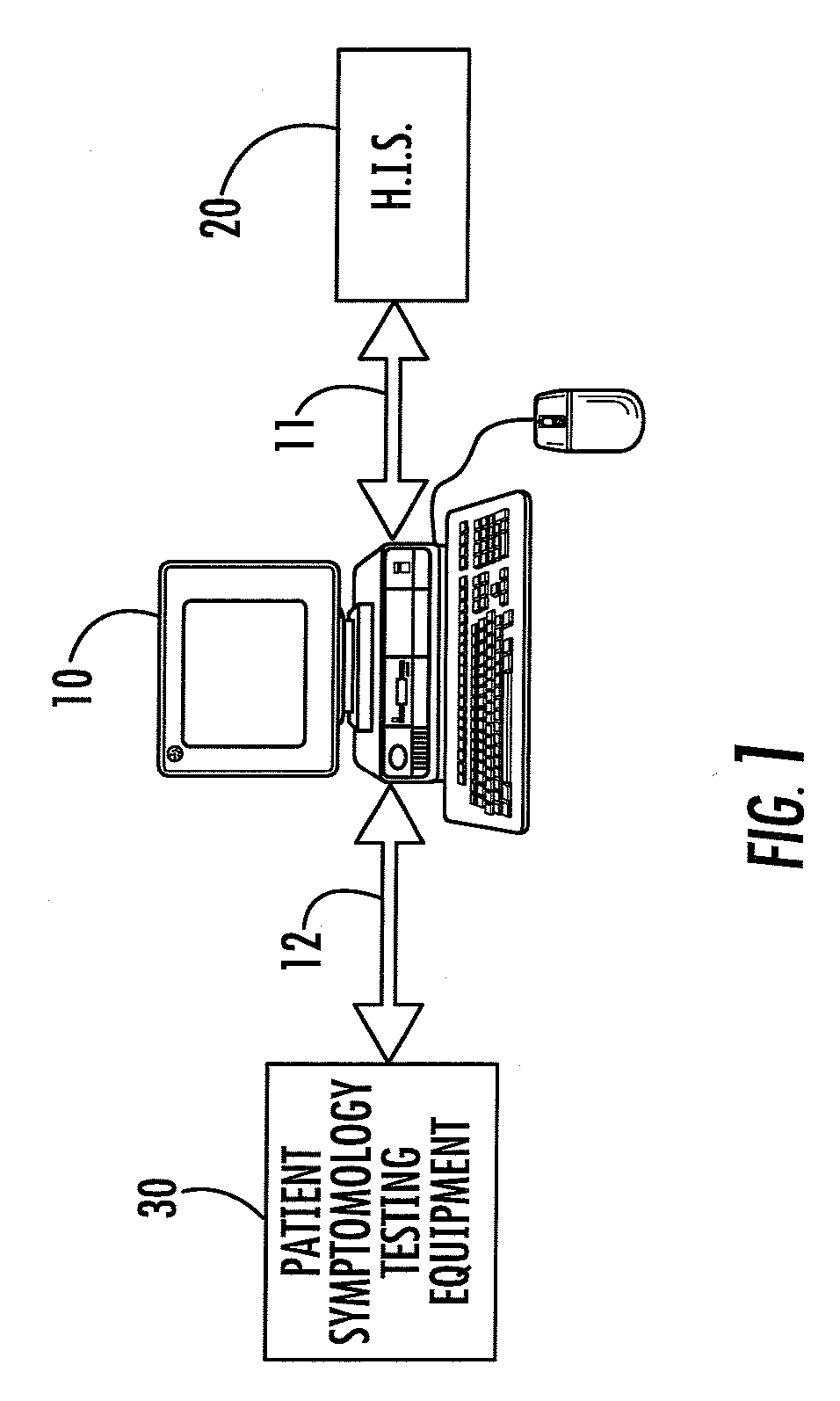
Patents
Literature
130 results about "Verified procedure" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
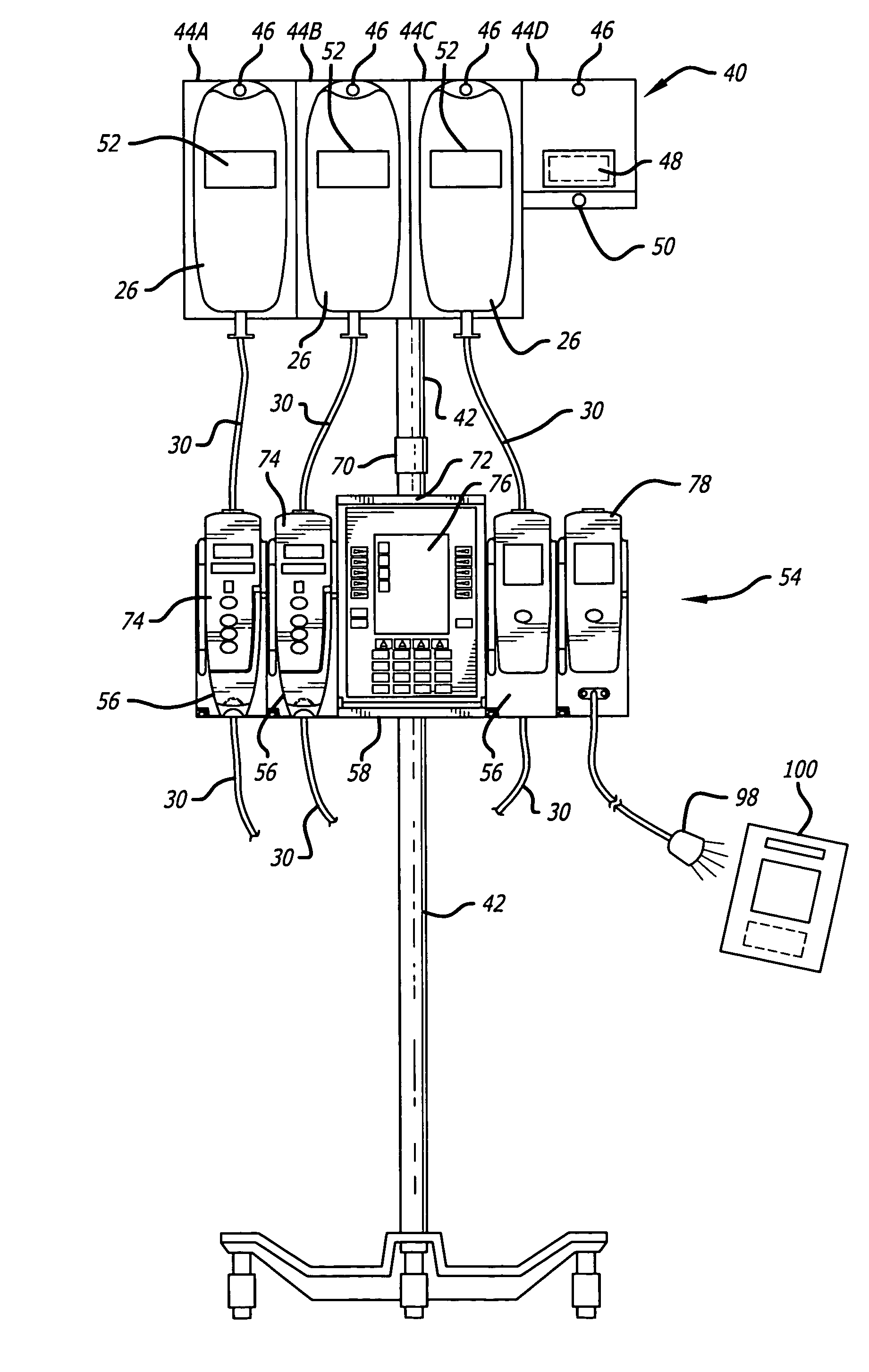
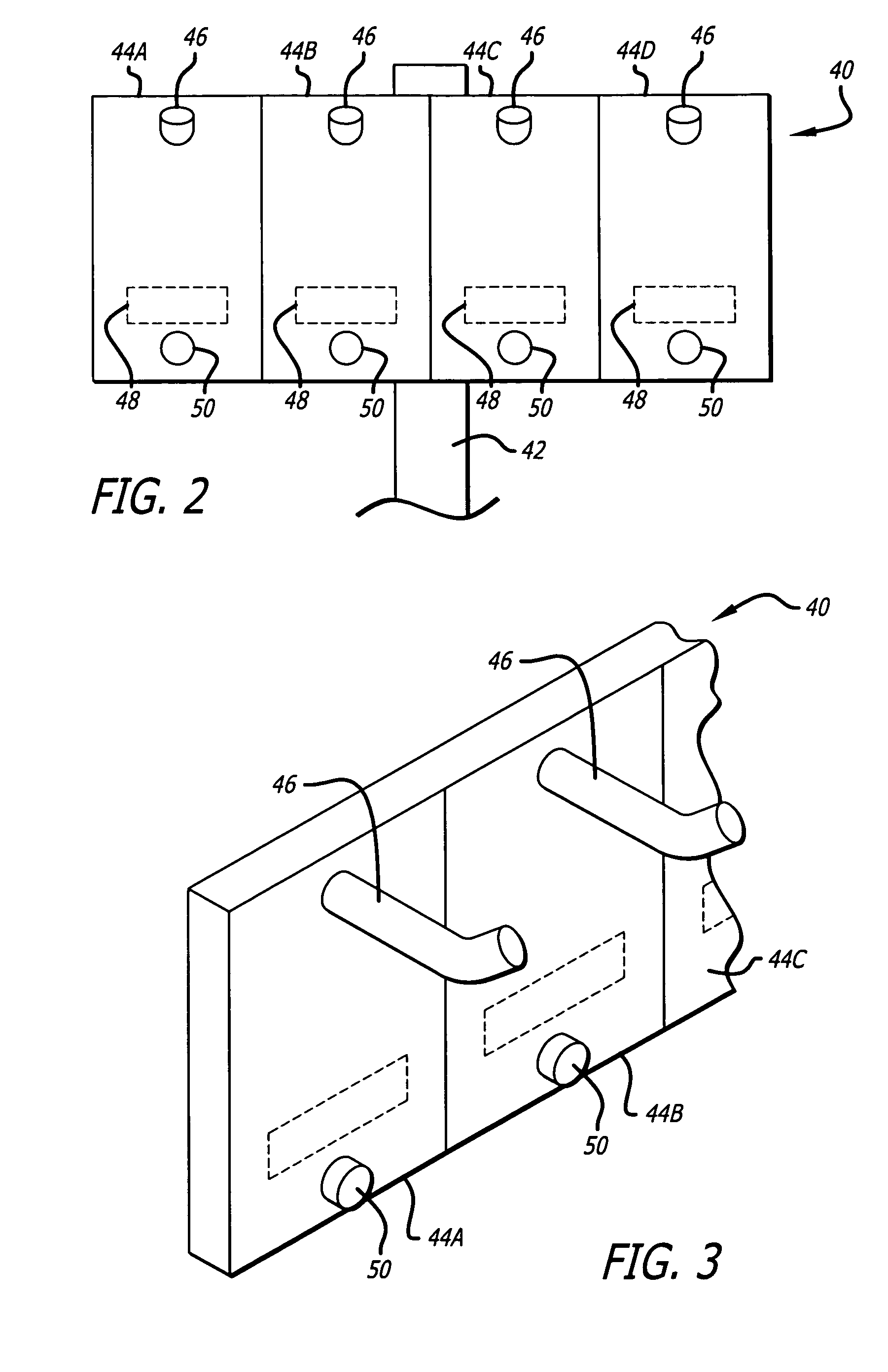
Medication safety system featuring a multiplexed RFID interrogator panel
A medication safety system includes a panel mounted to an IV pole above a multi-channel infusion pump also mounted to the IV pole. The panel includes multiple RFID readers for reading the RFID tags placed on each of the medication containers mounted to the panel. The pump includes a controller that communicates with the RFID readers at the panel to receive the information read by the RFID readers and automatically program the respective pump channel. A verification program verifies that the medication delivery information from the containers matches the patient identified for the pump and the programming parameters of the pump fall within acceptable ranges. In another aspect, the panel contains multiple vibration devices to impart vibrations to the medication of each of the containers mounted to the panel. Those vibrations are sensed by the particular pumping channel to confirm that the correct channel has been programmed for that medication. When the clinician opens the door of the pumping channel, the pump may request information from the RFID reader at the panel for that medication and may wait for receipt of the vibrations in the medication of the tubing mounted into the channel.
Owner:CAREFUSION 303 INC
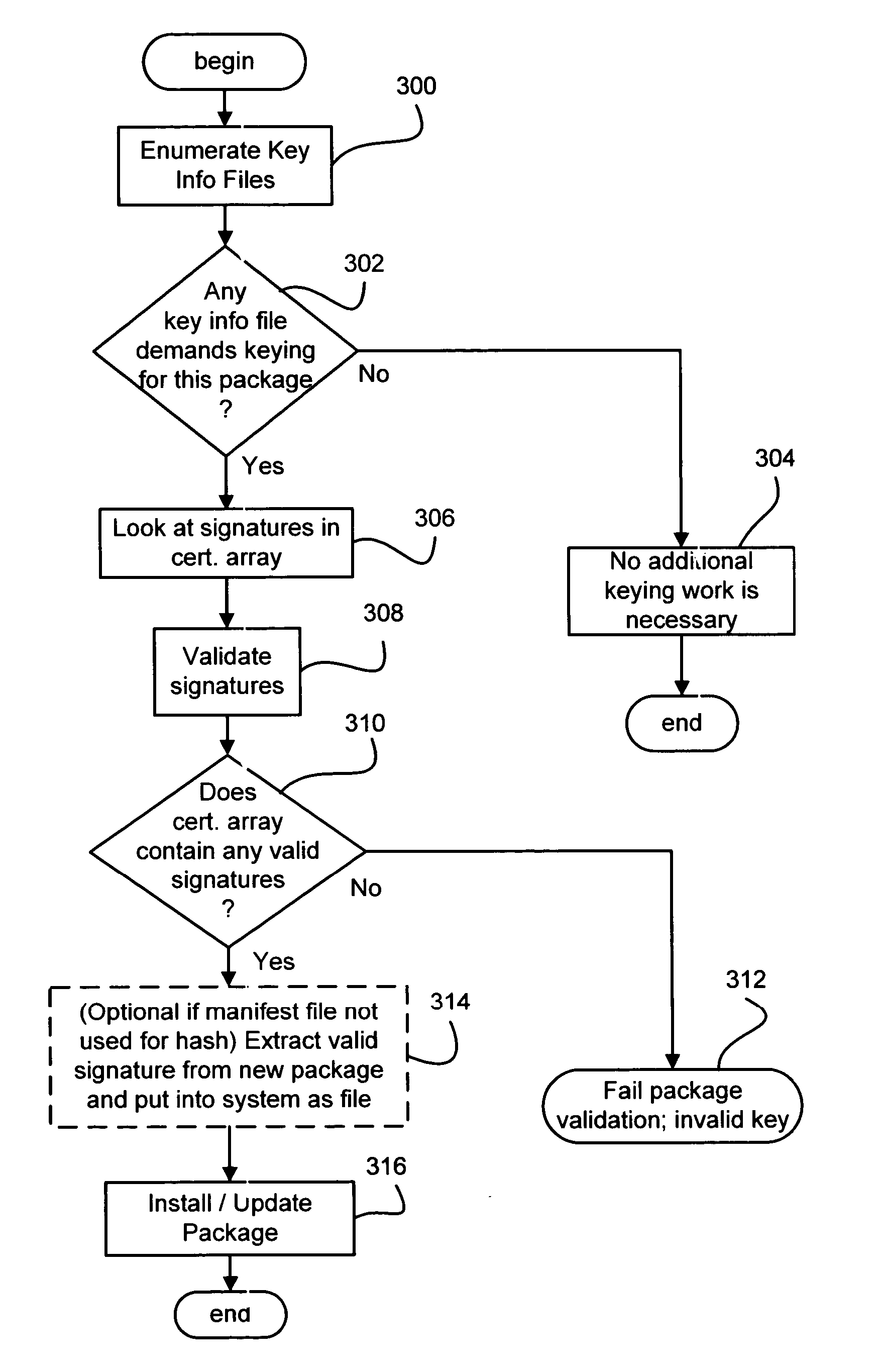
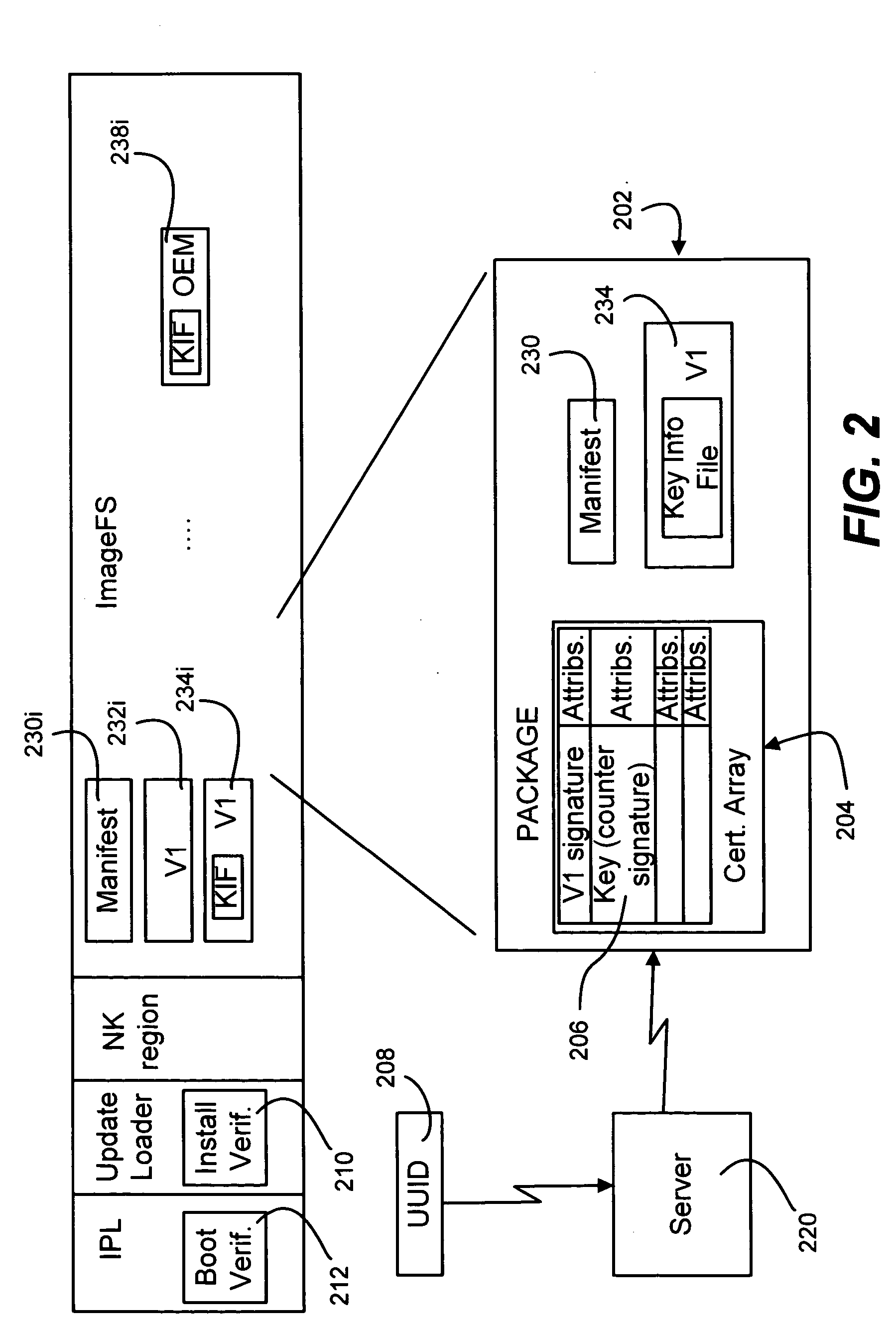
Ensuring that a software update may be installed or run only on a specific device or class of devices
InactiveUS20050132357A1Digital computer detailsComputer security arrangementsSoftware updateVerified procedure
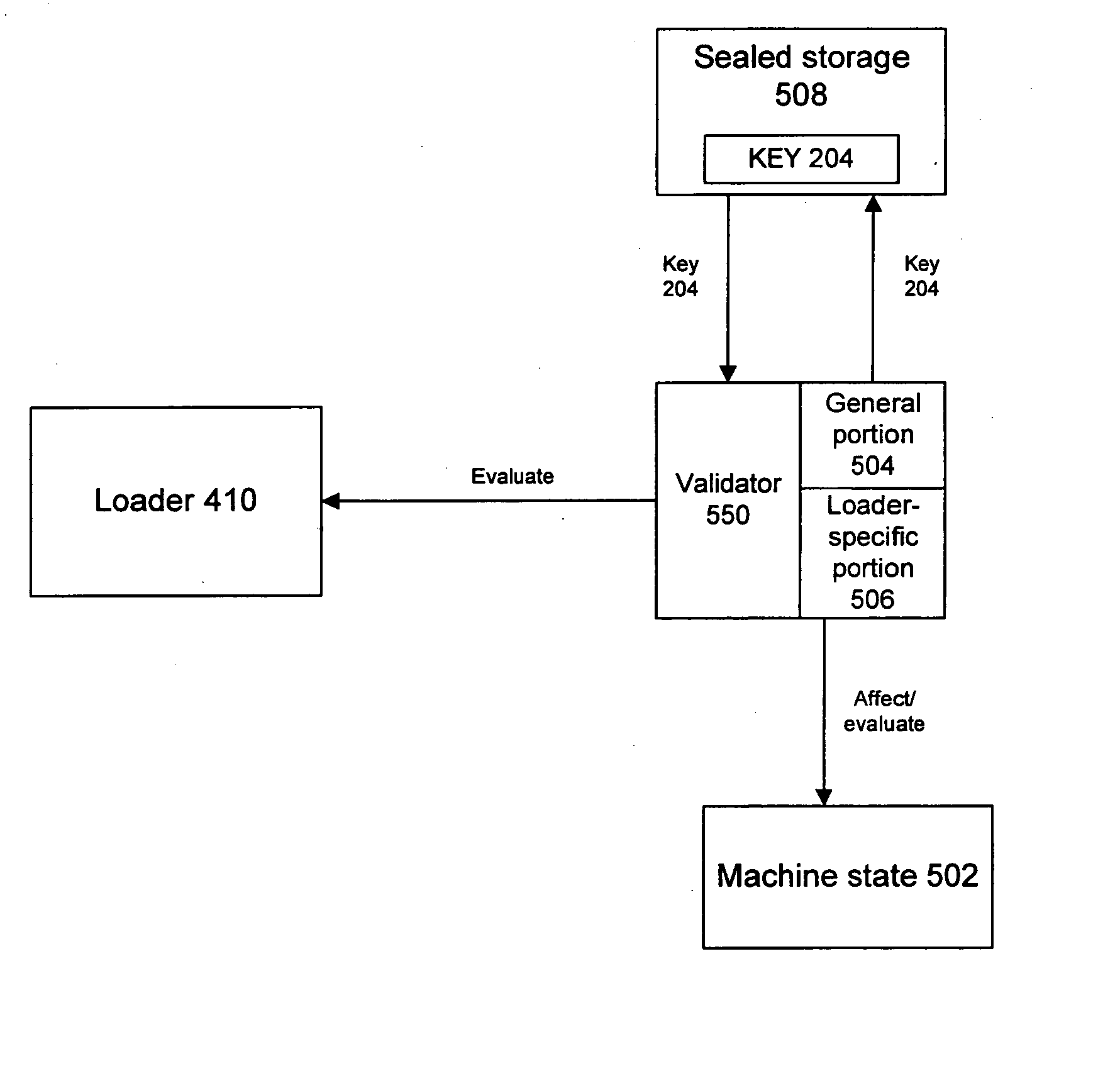
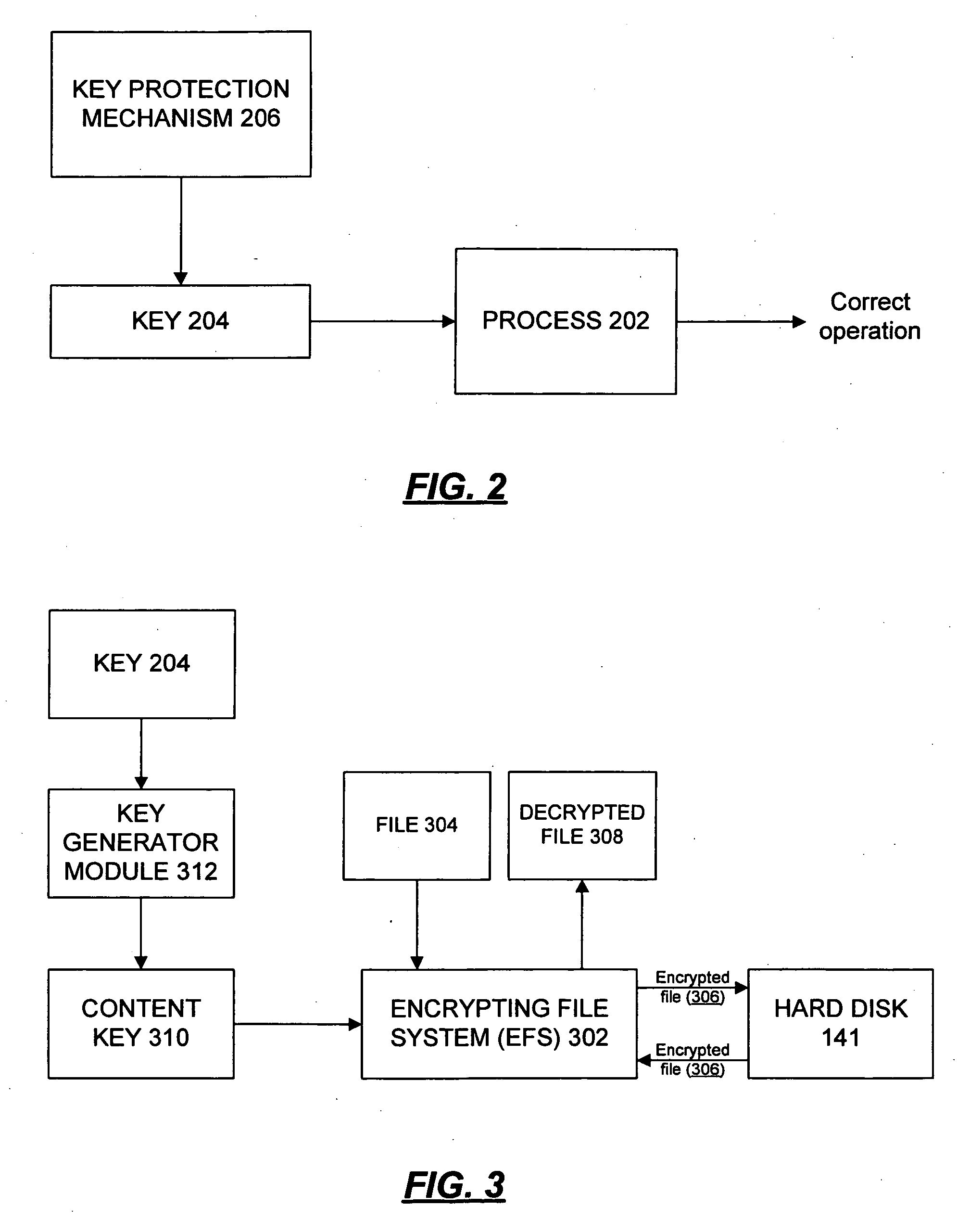
Described is a system and method in which a system and method in which a device manufacturer or software image provider controls which devices are allowed to install or to run a software image. An image keying mechanism uses package data and UUID associated with the device or class of devices to key an image. Because the UUID is used in the key, an installer verifier and / or boot-time verifier can ensure that the device is authorized to install and / or run the image. Any package, including existing device packages or the package for which installation is requested can demand that keying be enforced. An installer mechanism checks whether the device is allowed to install the image. A boot-time enforcement mechanism prevents an improperly installed image from operating by halting the boot process if a demanded key is invalid or missing.
Owner:MICROSOFT TECH LICENSING LLC
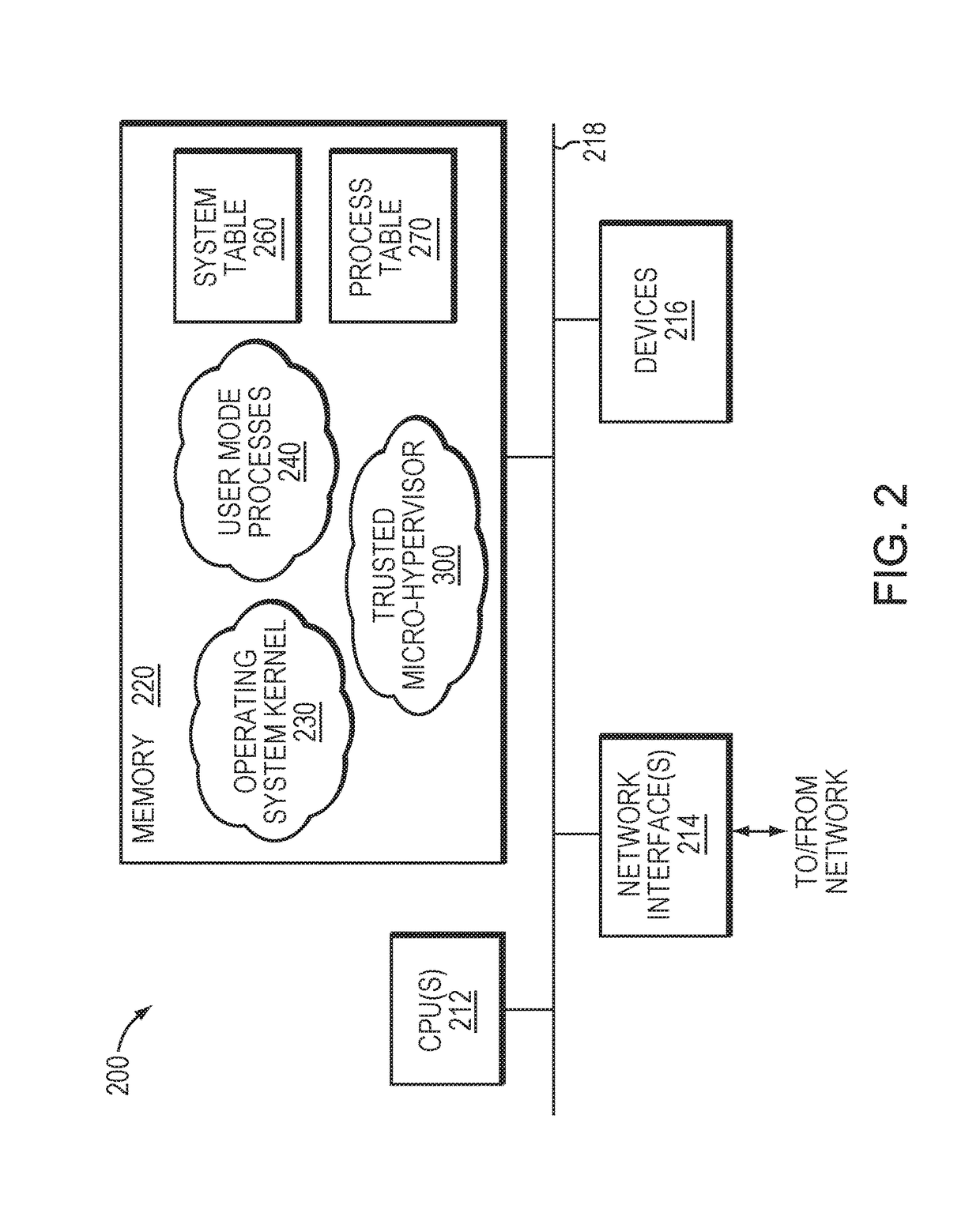
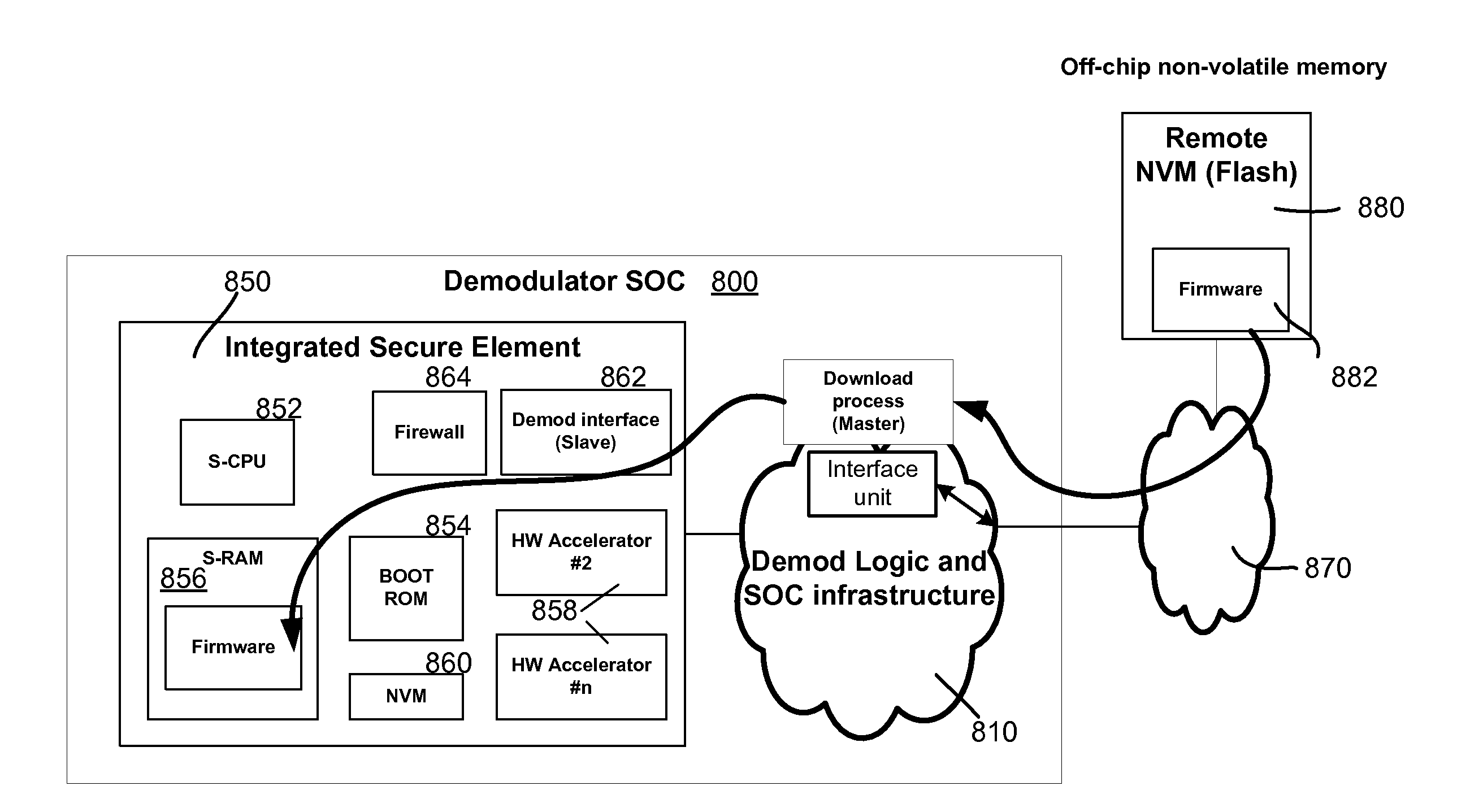
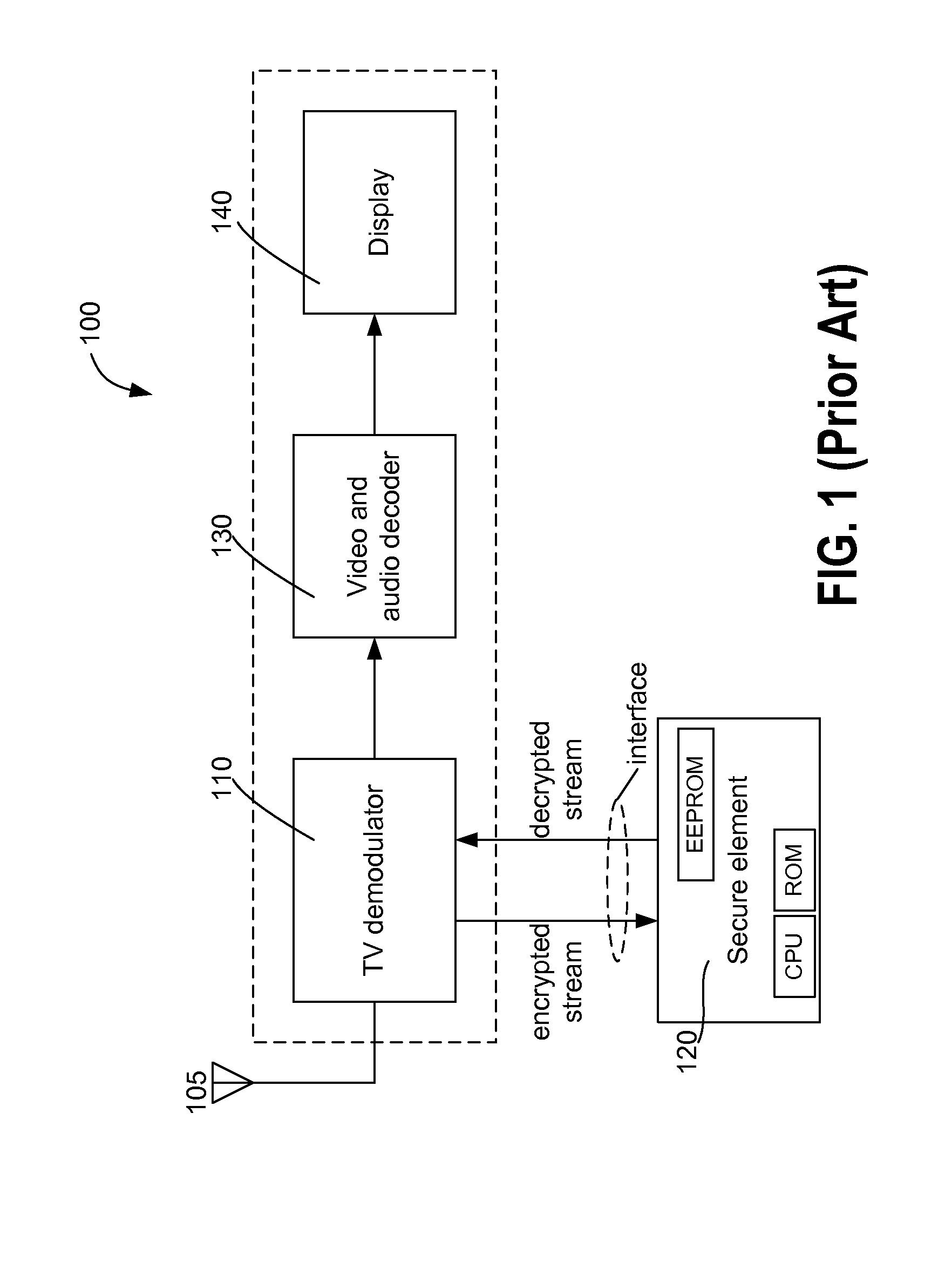
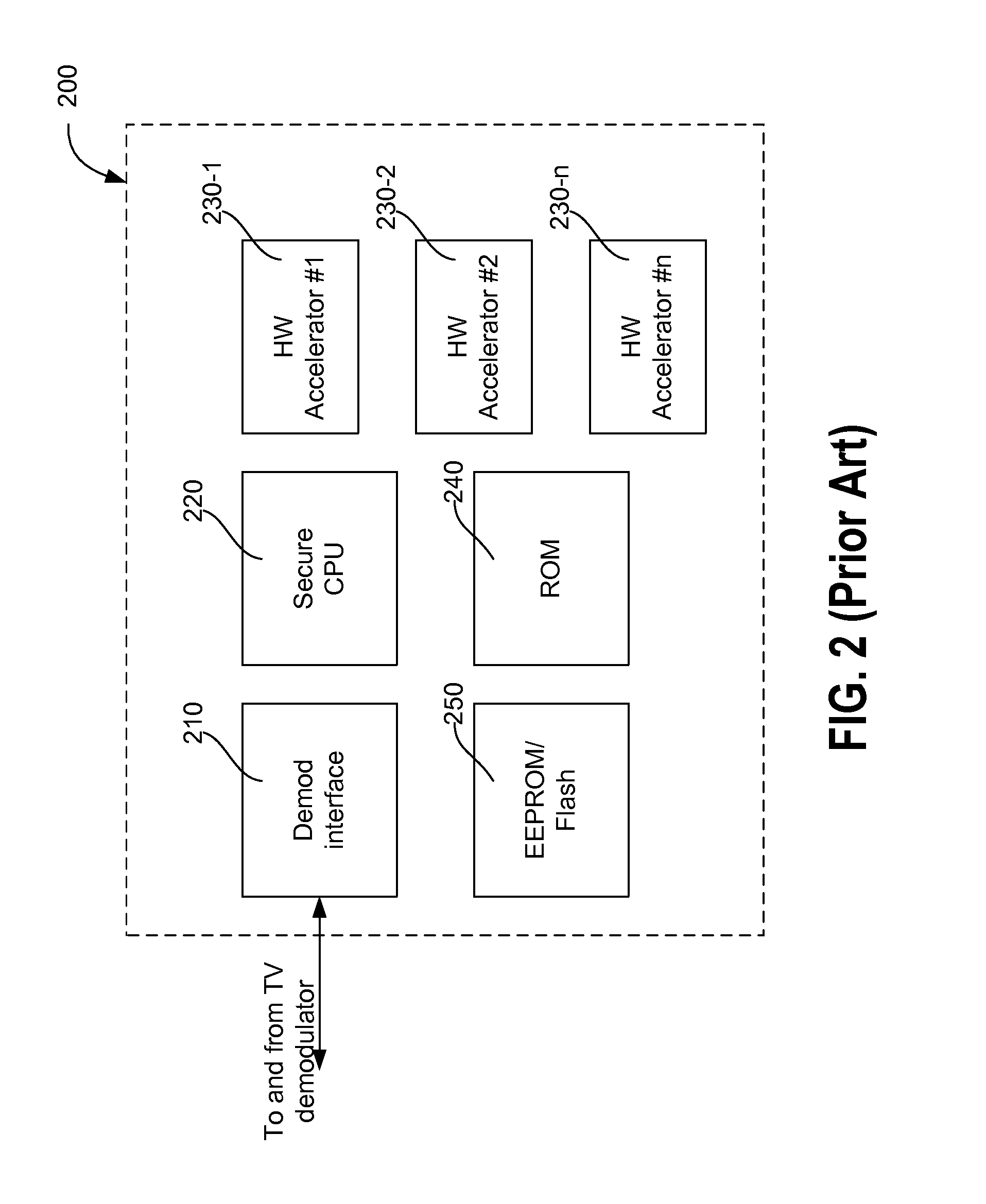
Firmware Authentication and Deciphering for Secure TV Receiver
InactiveUS20120079287A1Unauthorized memory use protectionHardware monitoringStatic random-access memoryTelevision receivers
A method for authenticating and deciphering an encrypted program file for execution by a secure element includes receiving the program file and a digital certificate that is associated with the program file from an external device. The method stores the program file and the associated certificate in a secure random access memory disposed in the secure element and hashes the program file to obtain a hash. The method authenticates the program file by comparing the obtained hash with a checksum that is stored in the certificate. Additionally, the method writes runtime configuration information stored in the certificate to corresponding configuration registers disposed in the secure element. The method further generates an encryption key using a seed value stored in the certificate and a unique identifier disposed in the secure element and deciphers the program file using the generated encryption key.
Owner:RADIOXIO LLC
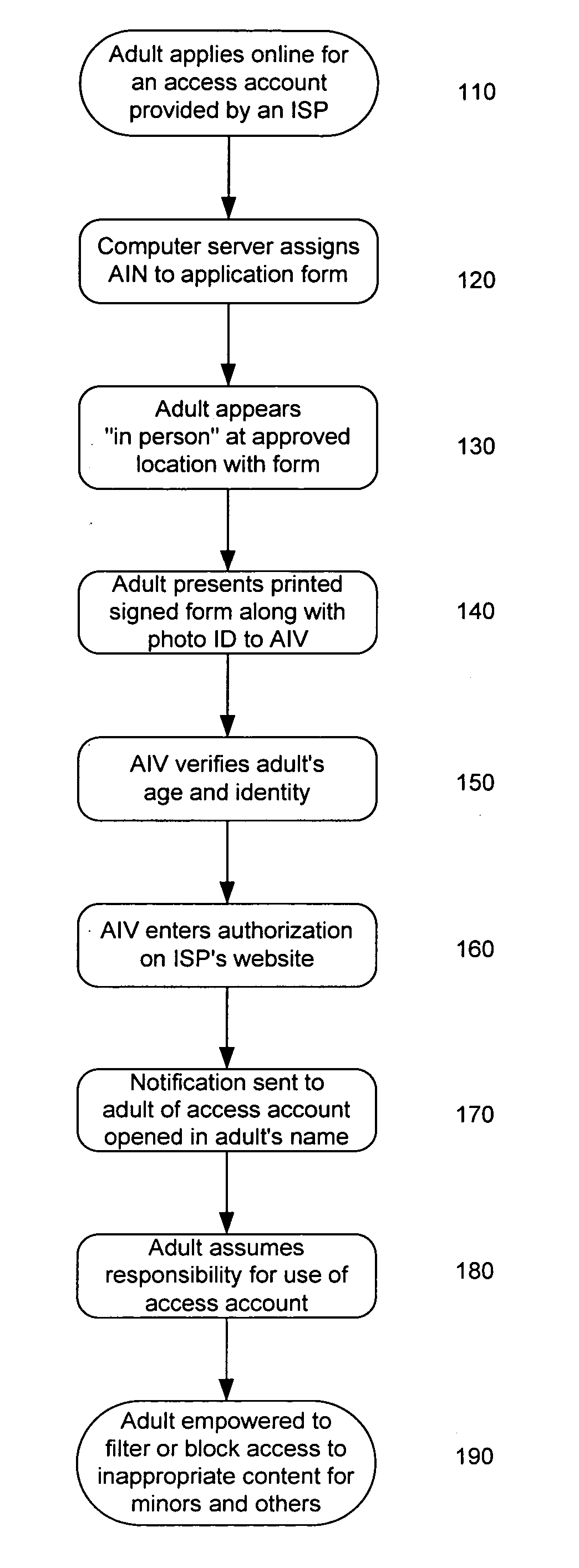
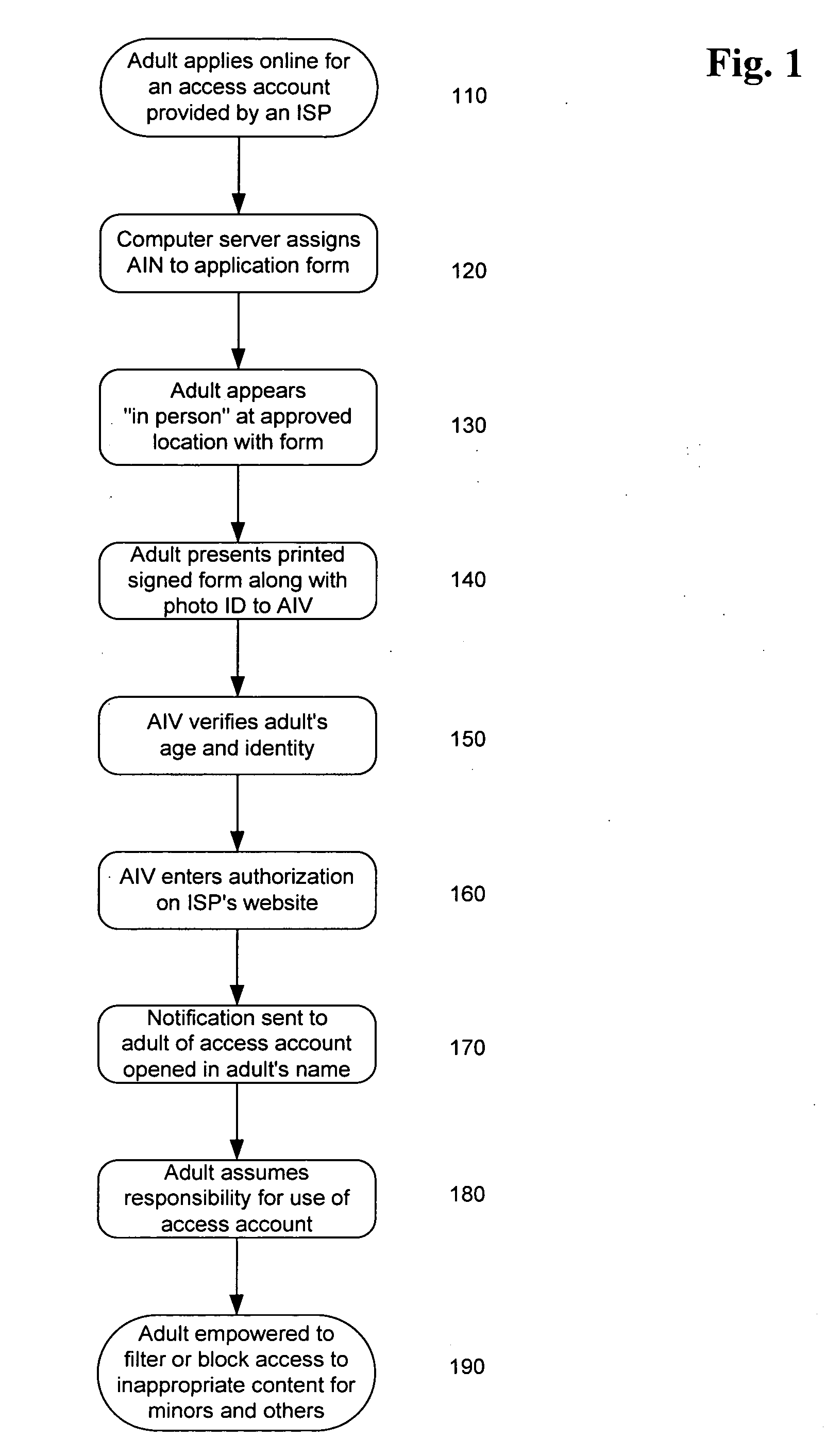
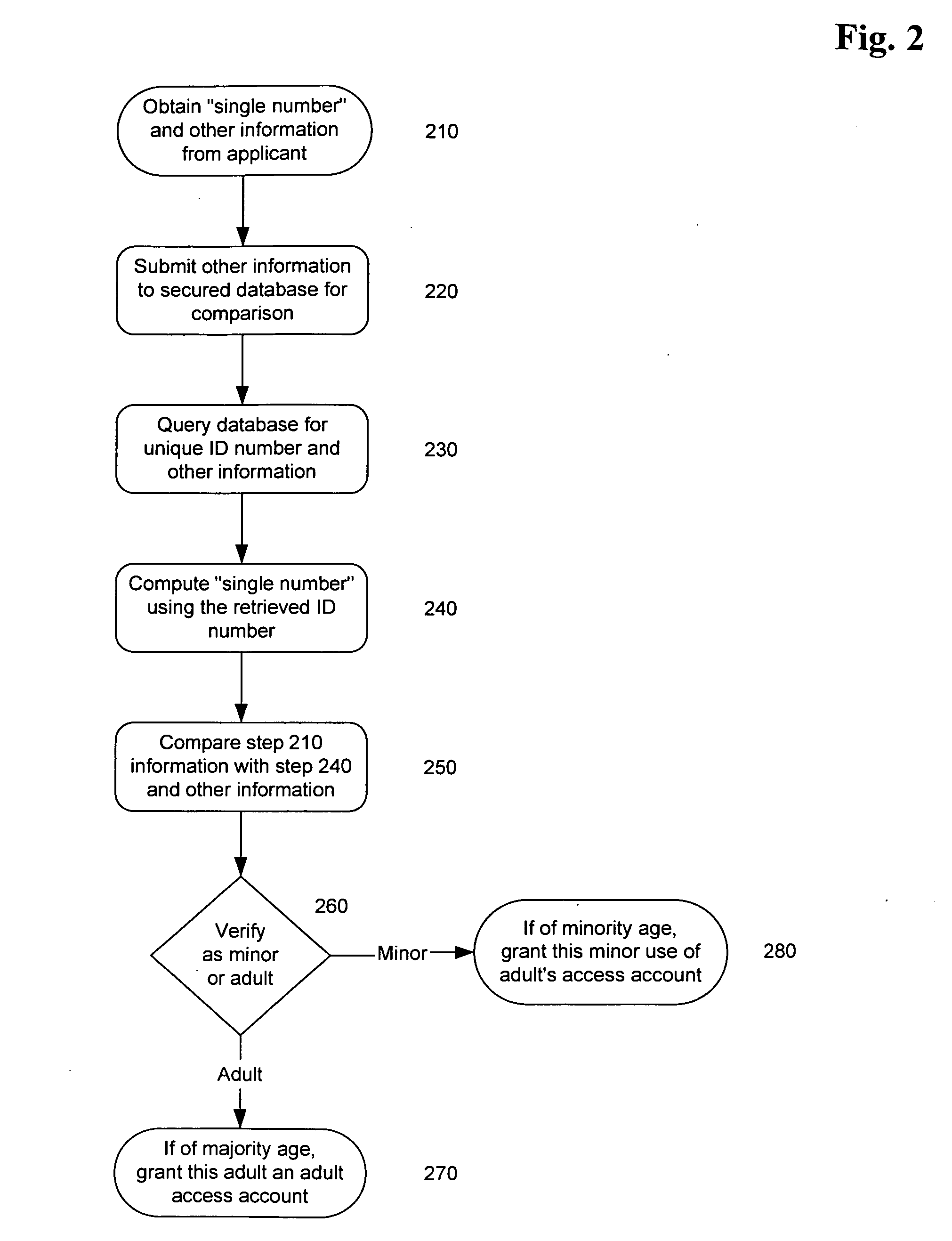
System and method for verifying the age and identity of individuals and limiting their access to appropriate material and situations
InactiveUS20060173793A1Overcome deficienciesPayment architectureSecret communicationVerified procedureComputer science
Limiting access to the Internet, intranets, computers, appliances, websites, individuals and / or other venues, for example, by providing an access account, to an “in person” and / or otherwise verified “adult” who assumes responsibility for such account's use for accessing appropriate material, websites and / or individuals, while empowered by control of a “single access account” that filters inappropriate material, websites and / or individuals based on (1) profiles created by such adults and stored on provider's “access server,” and / or elsewhere, and / or (2) “mandatory” provider imposed filtering. Further, helping “producers” comply with 18 U.S.C. 2257 by adopting the “verification process” to protect children.
Owner:GLASS PAUL H
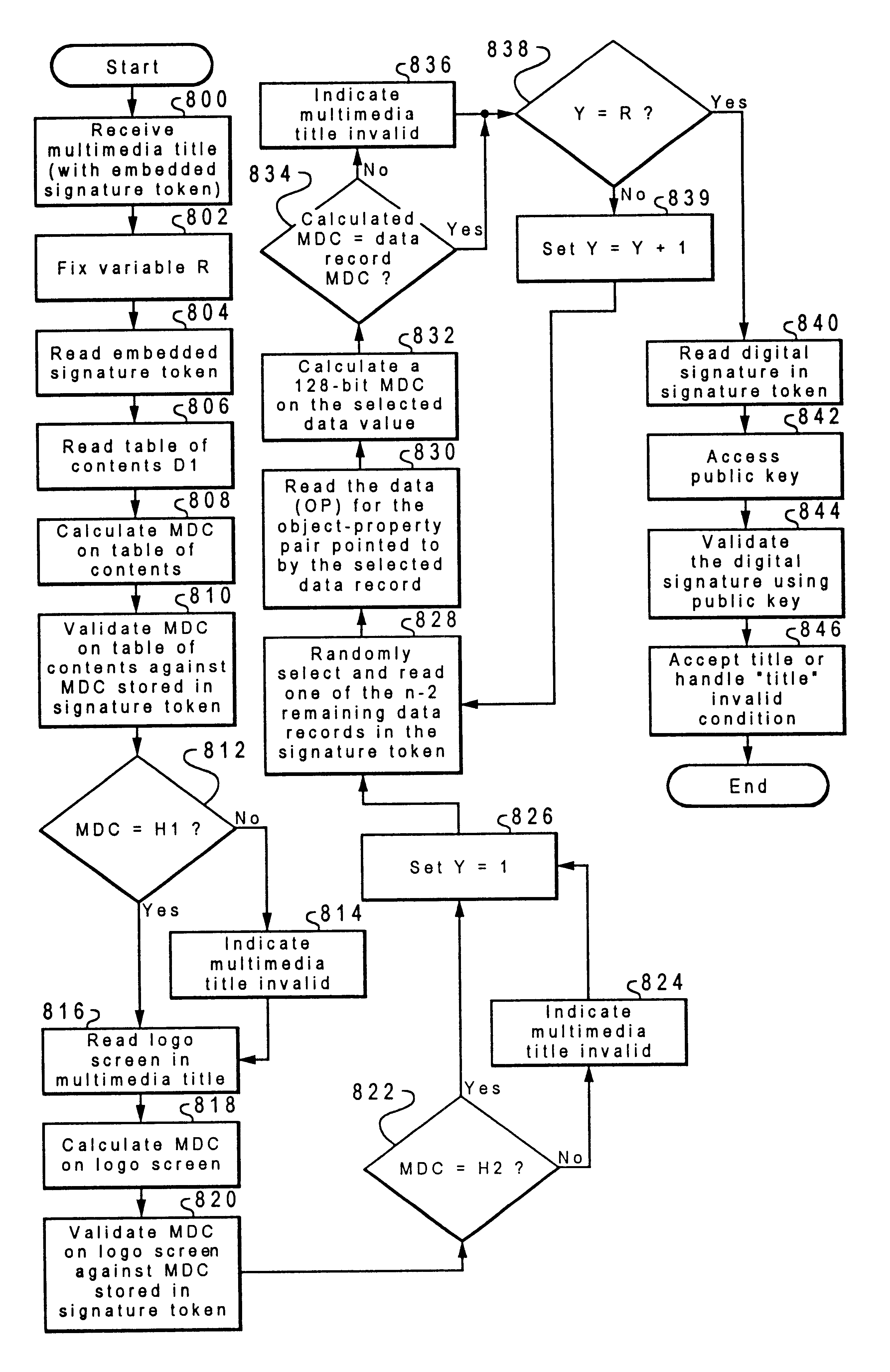
Method and system for the secured distribution of multimedia titles
InactiveUSRE38375E1Memory loss protectionDigital data processing detailsData processing systemProgramming language
A method and system for detecting authorized programs within a data processing system. The present invention creates a validation structure for validating a program. The validation structure is embedded in the program and in response to an initiation of the program, a determination is made as to whether the program is an authorized program. The determination is made using the validation structure.
Owner:ACTIVISION PUBLISHING
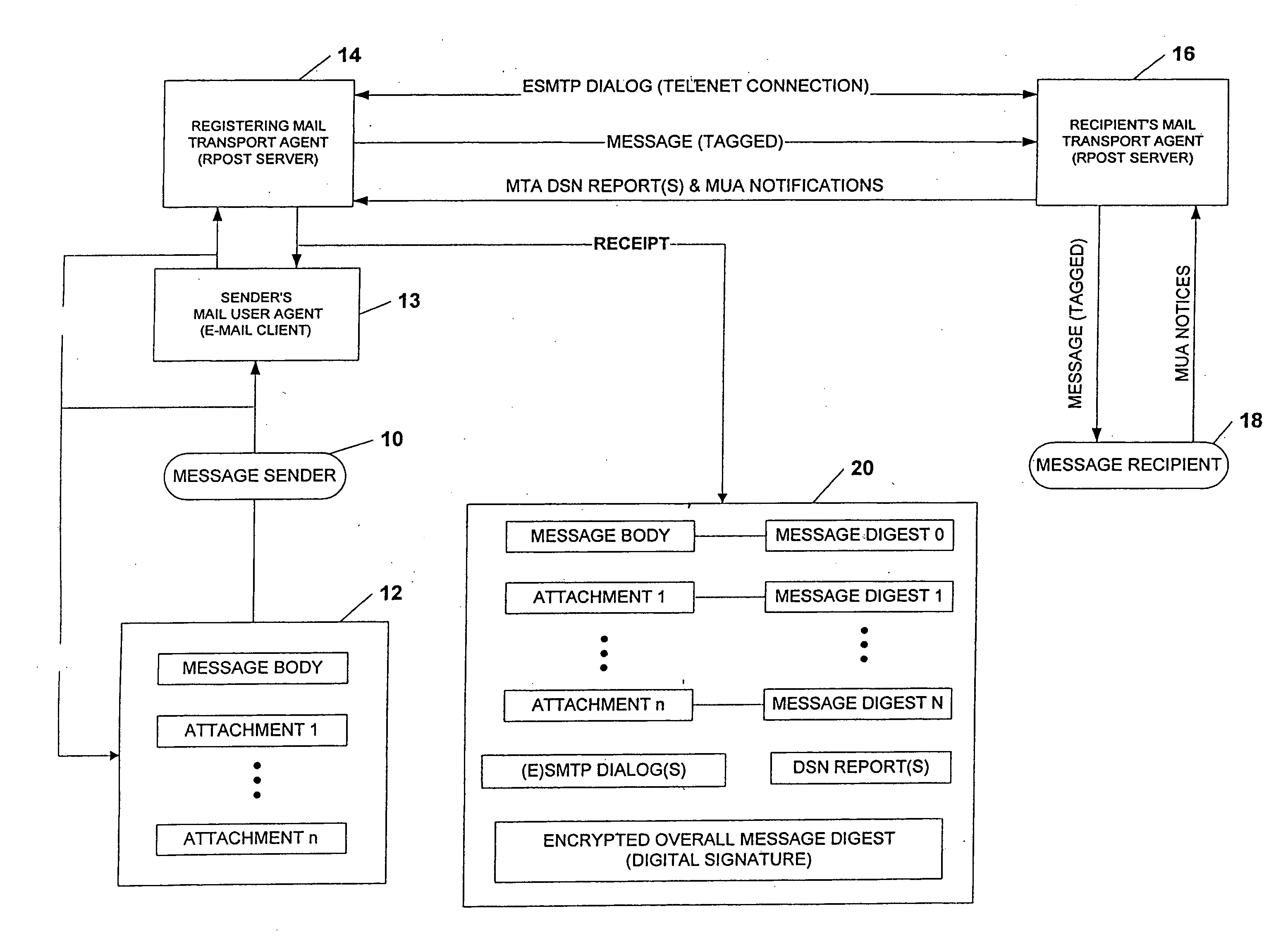
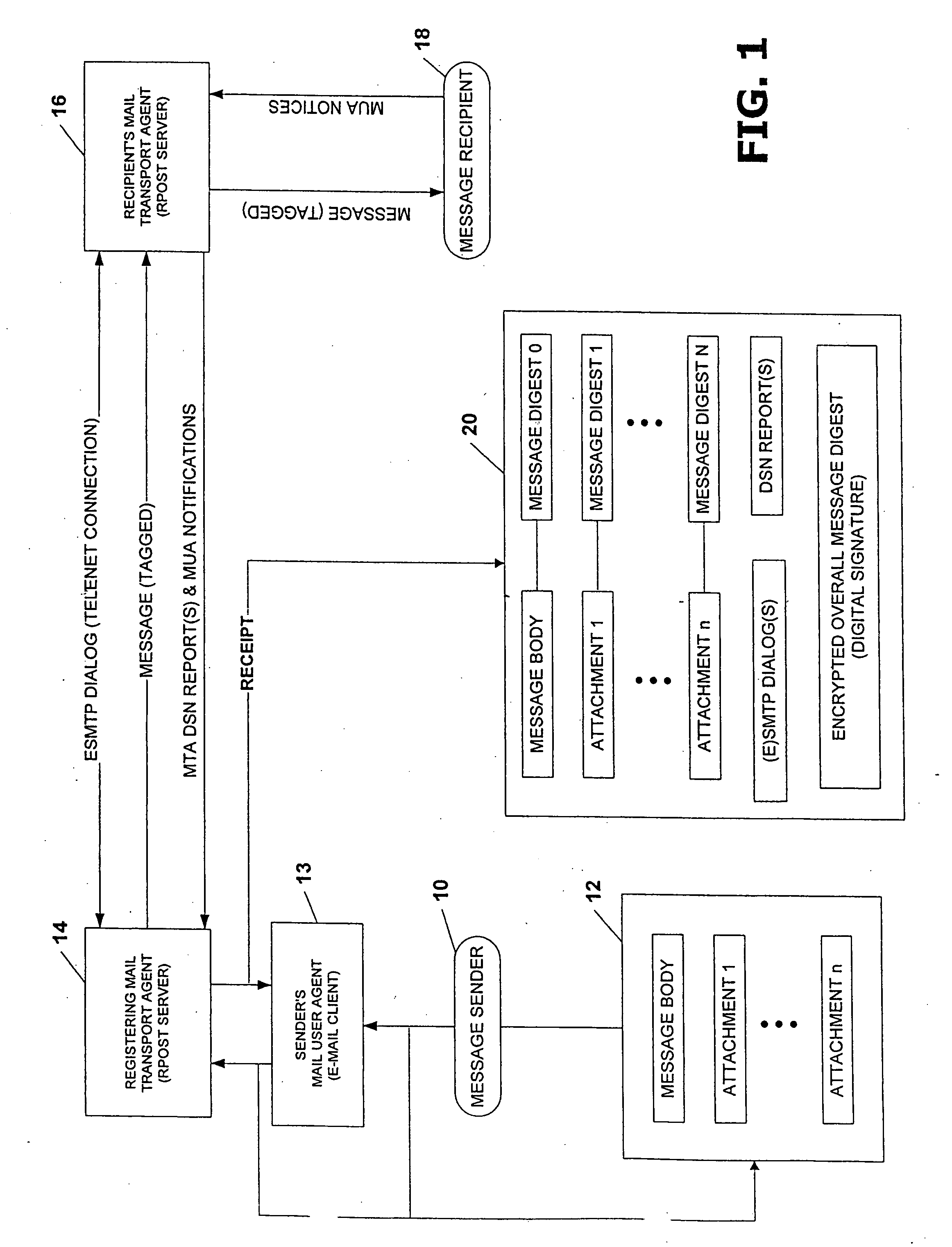
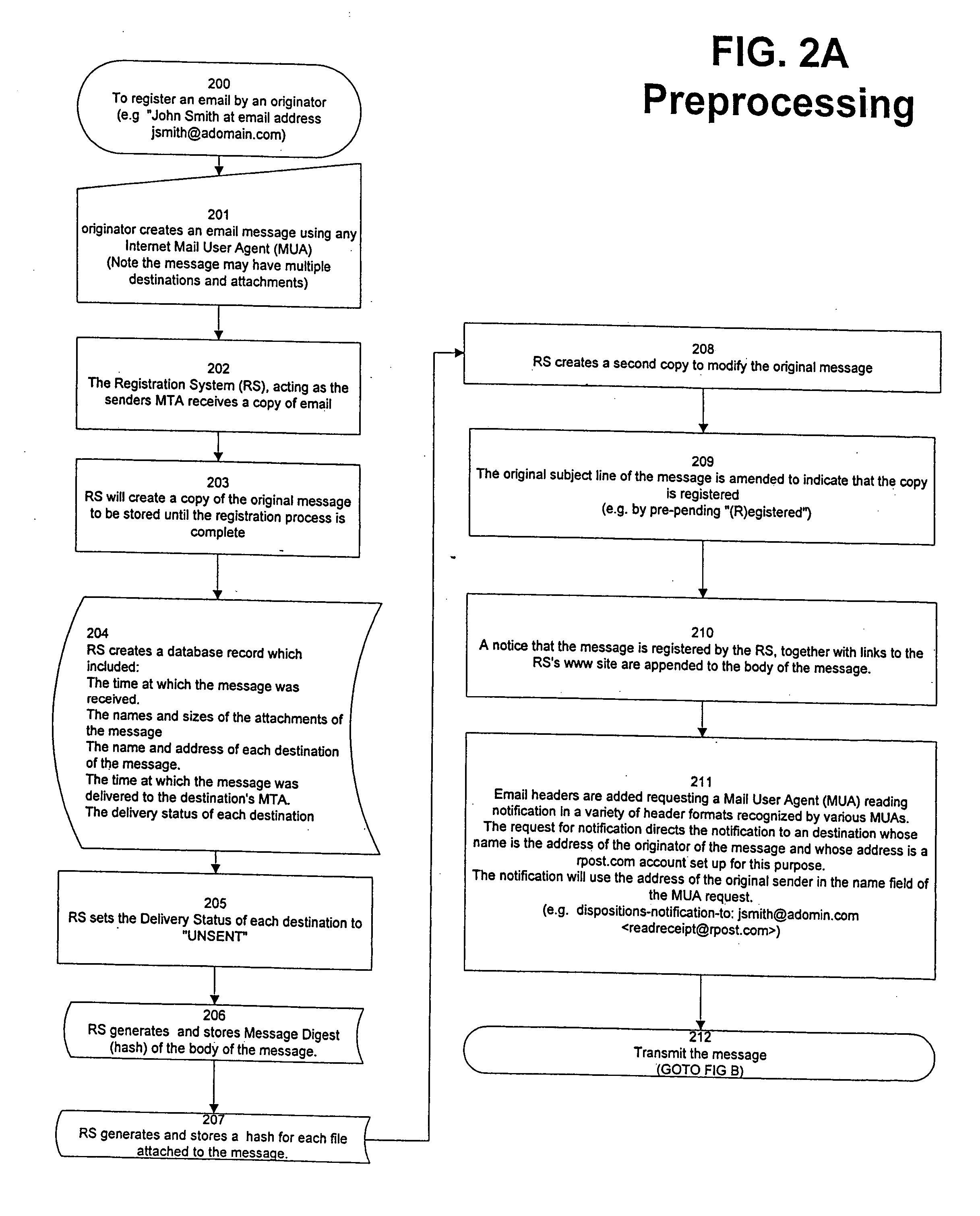
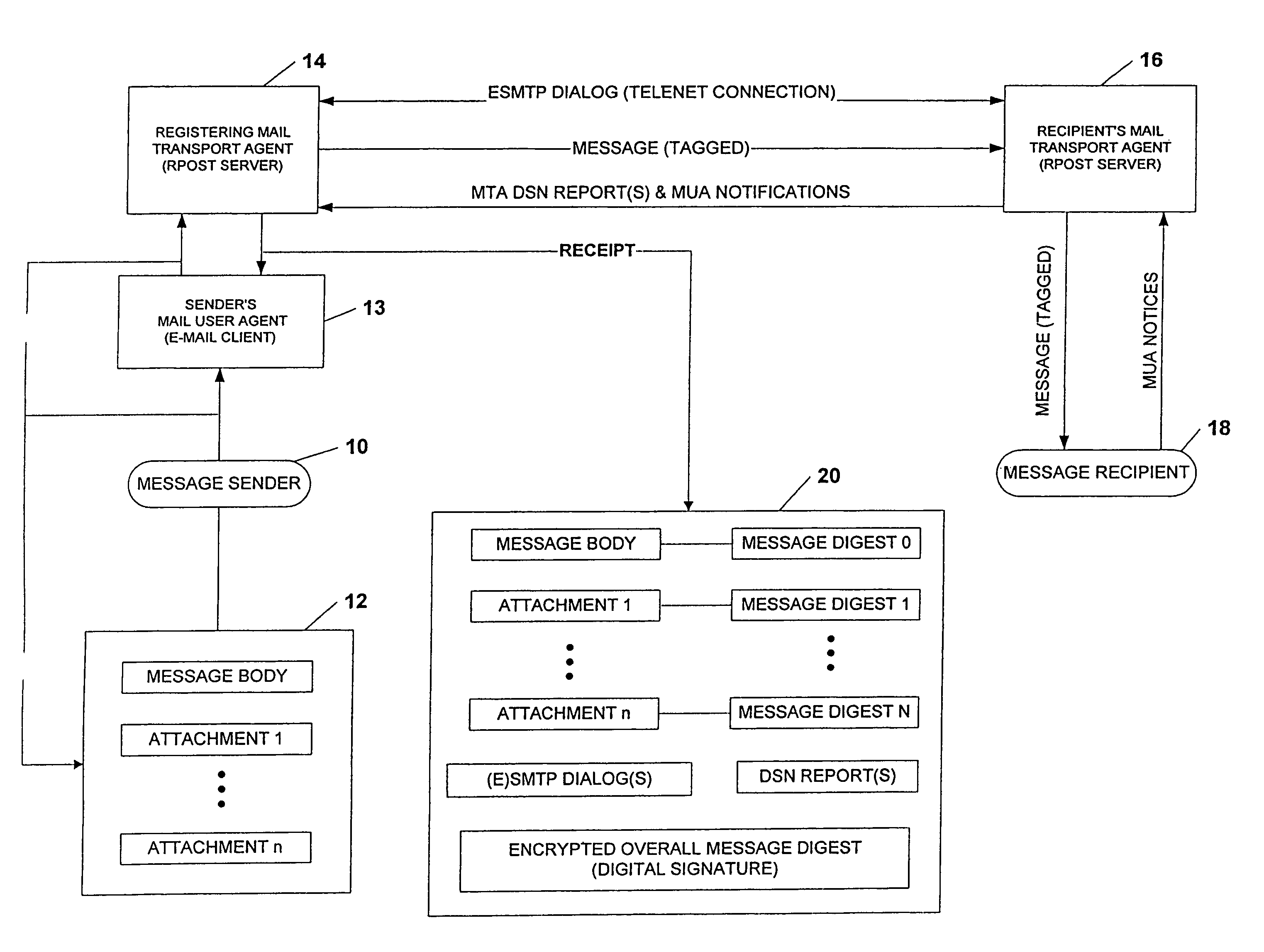
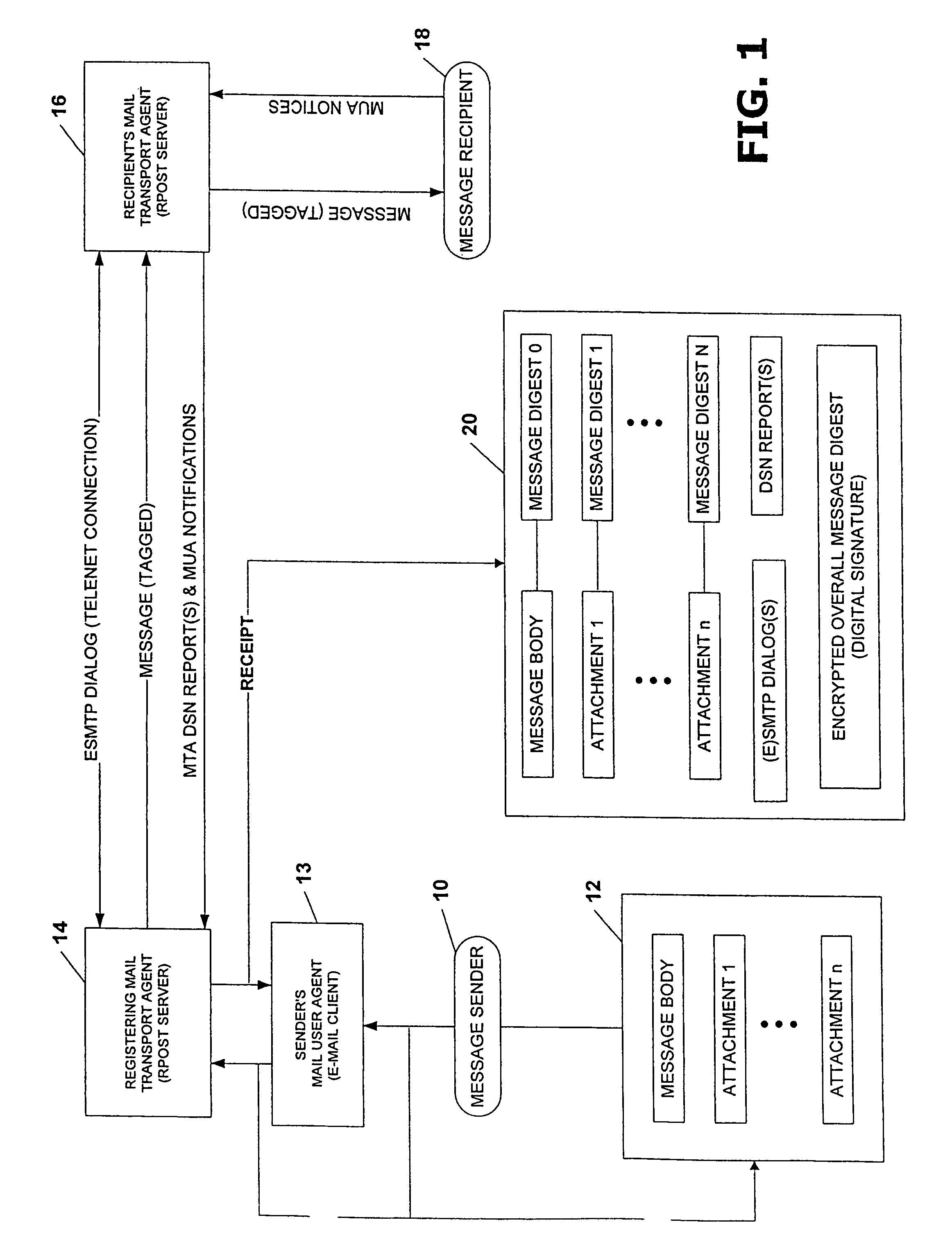
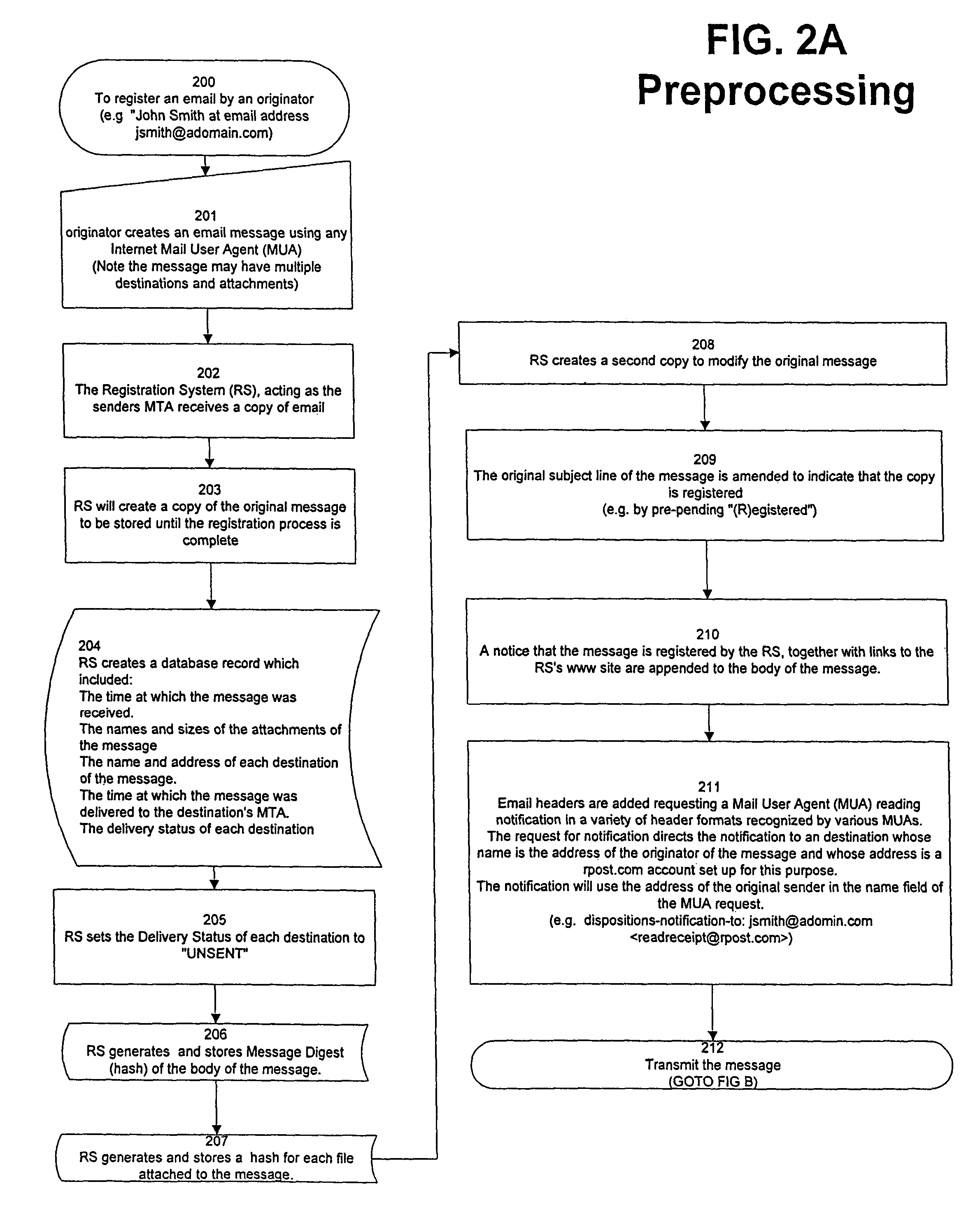
System and method for verifying delivery and integrity of electronic messages
InactiveUS20070174402A1Verify reliabilityUser identity/authority verificationMultiple digital computer combinationsVerified procedureAuthentication
A server transmits a message from a sender to a destination address. During transmission, the server and the destination address have a dialog constituting an attachment, via a particular one of SMTP and ESMTP protocols, concerning the message, the server and the destination address. The message passes through servers between the server and the destination address. This passage is included in the attachment. Verifiers are provided for the message and for the attachments. The verifiers may constitute encrypted hashes of the message and of the attachment. The sender receives the message, the attachments and the verifications from the server before authentication and transmits the message, the attachments and the verifiers to the server to obtain authentication by the server. The server operates on the message and the message verifier to authenticate the message and operates on the attachments and the attachments' verifier to verify the attachments.
Owner:RPOST COMM
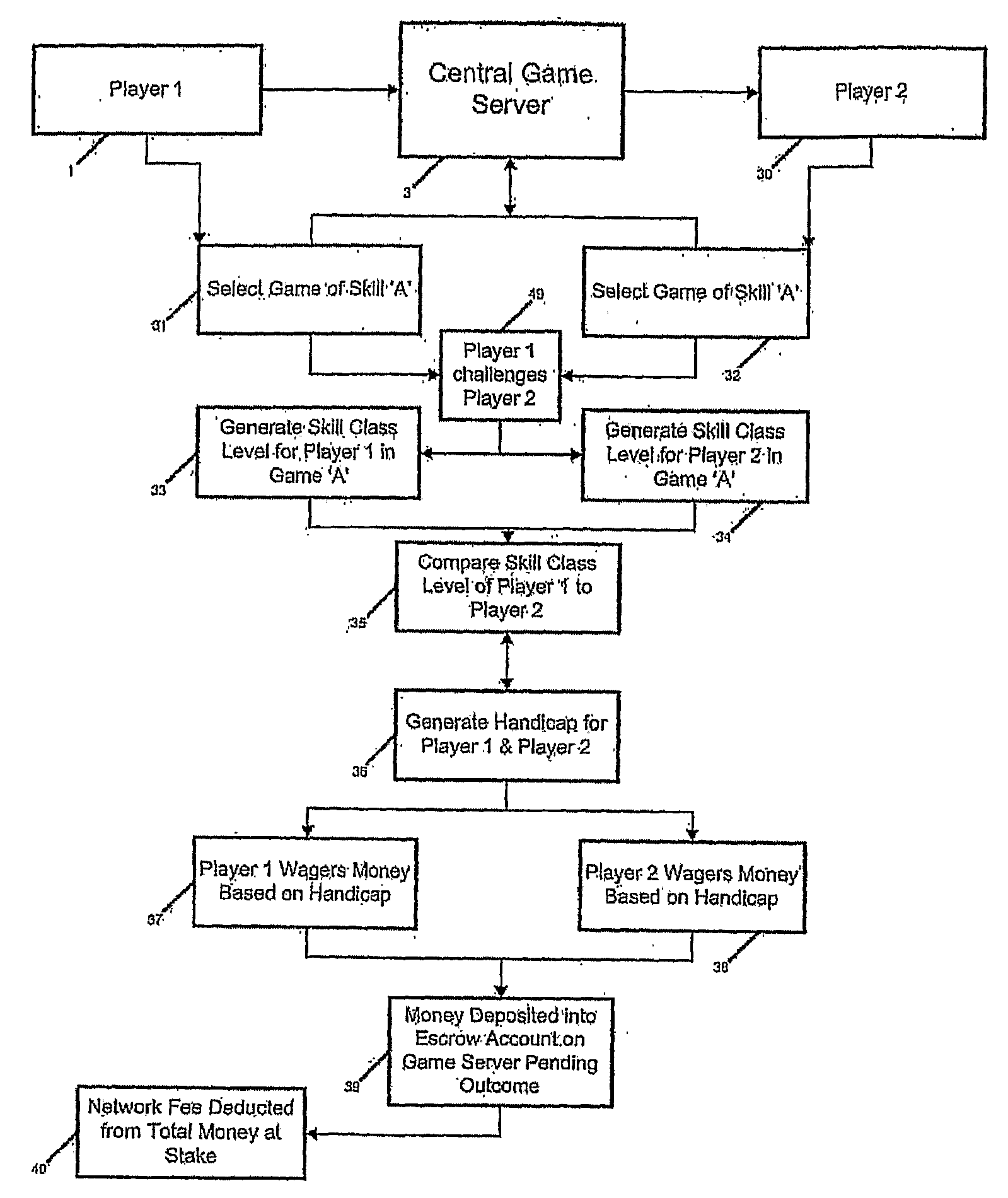
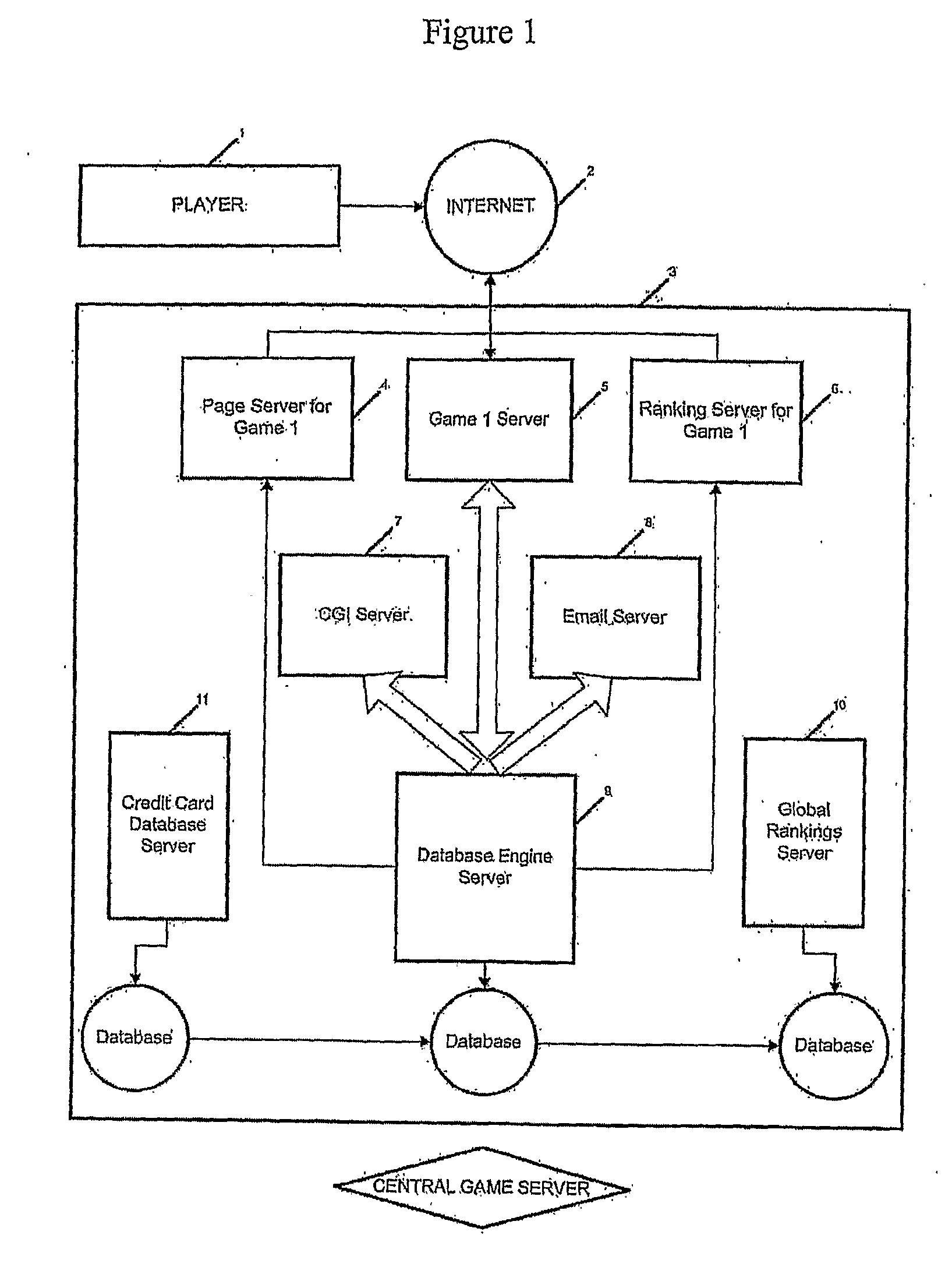
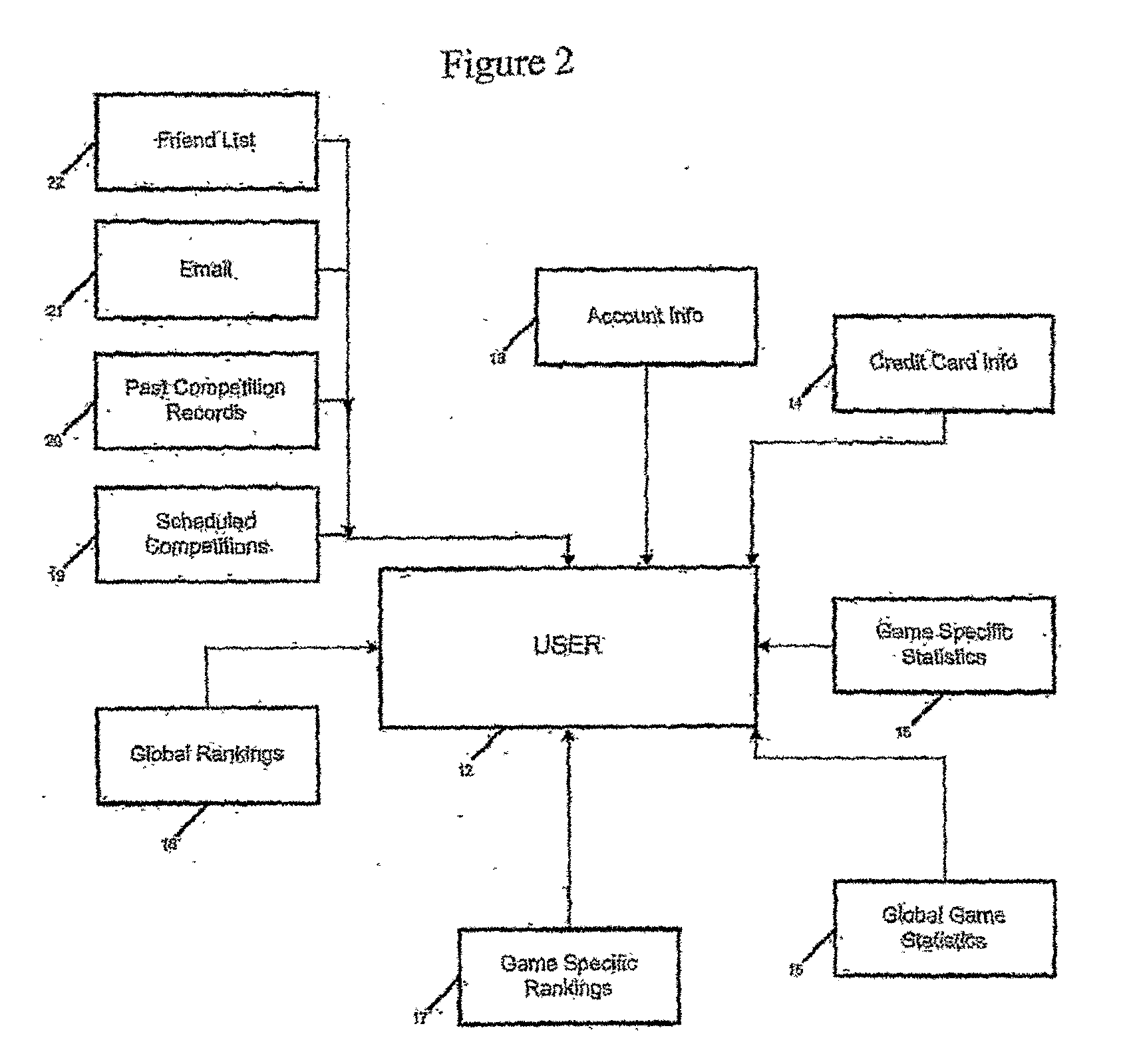
Method of software distribution via the internet
InactiveUS20090049542A1Digital data processing detailsUser identity/authority verificationUser profileVerified procedure
In one general aspect there is provided a method for distributing software. The method comprising (a) a software user creating a user profile which includes one or more types of biometric data; (b) providing the biometric data to a software distributor; (c) obtaining the software; and (d) utilizing the software on the user's computer having a biometric sensing device that senses or measures a biometric parameter of the user useful for creating biometric data, wherein utilizing the software causes the activation of a verification program or function that compares the sensed or measured biometric data to the biometric data in the user profile. In another aspect, the invention relates to a method of handicapping two or more players of a game of skill, wherein the players are of varying skill levels. Also provided are methods of ranking players according to skill level and generating a professional gaming league based on skill level. Also provided is a system and an apparatus for verifying the identity of a user in a game of skill.
Owner:DEYONKER JAMES JOSEPH +1
Secure digital certificate storing scheme for flash memory and electronic apparatus
ActiveUS20070130439A1Improve featuresImprove data securityUser identity/authority verificationRead-only memoriesData memoryVerified procedure
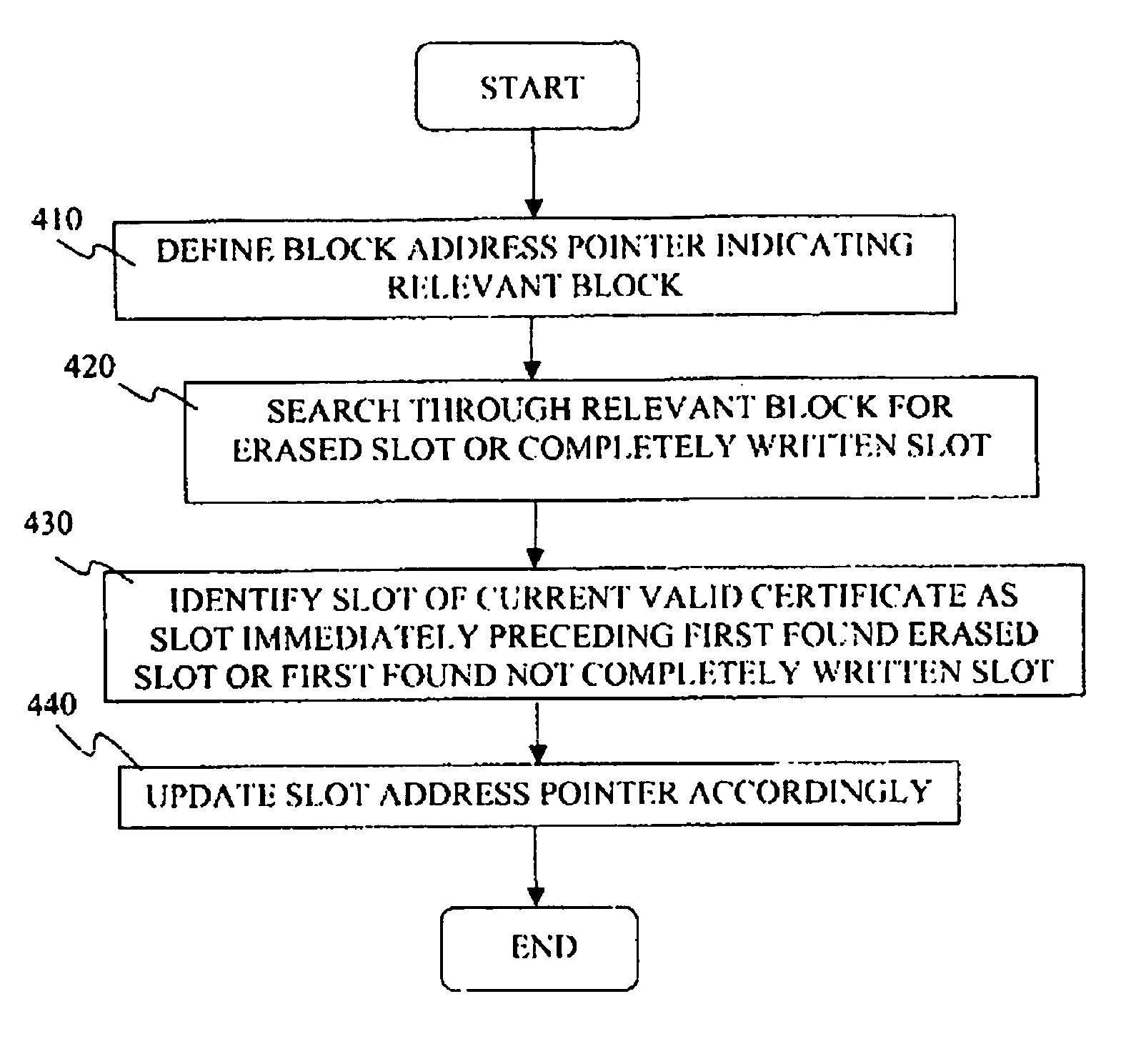
The invention relates generally to data security and to data memory technologies, and more specifically provides a method for storing and updating digital certificates in a flash memory, and provides further a flash memory and an electronic apparatus exploiting said method. The method according to the invention is applicable for a flash memory (110) having predefined erase-write blocks and write-read blocks, for enhancing the tampering proof characteristics of said flash memory (110), said certificates authenticating a computer program and being verified by a verification program associated with the computer program, said method comprising the steps of: (230) defining a plurality of memory slots within said at least one erased erase-write block wherein each memory slot have a commencing address comprising a binary “0”- or a binary “1” bit pattern, (240) writing a first and second digital certificate in a first and second one of said memory slots, (250) defining a certificate slot address pointer, (260) updating said certificate slot address pointer by replacing said “0”- or “1”-bit pattern of said pointer with a “1”-or a “0” bit pattern, respectively.
Owner:SONY CORP
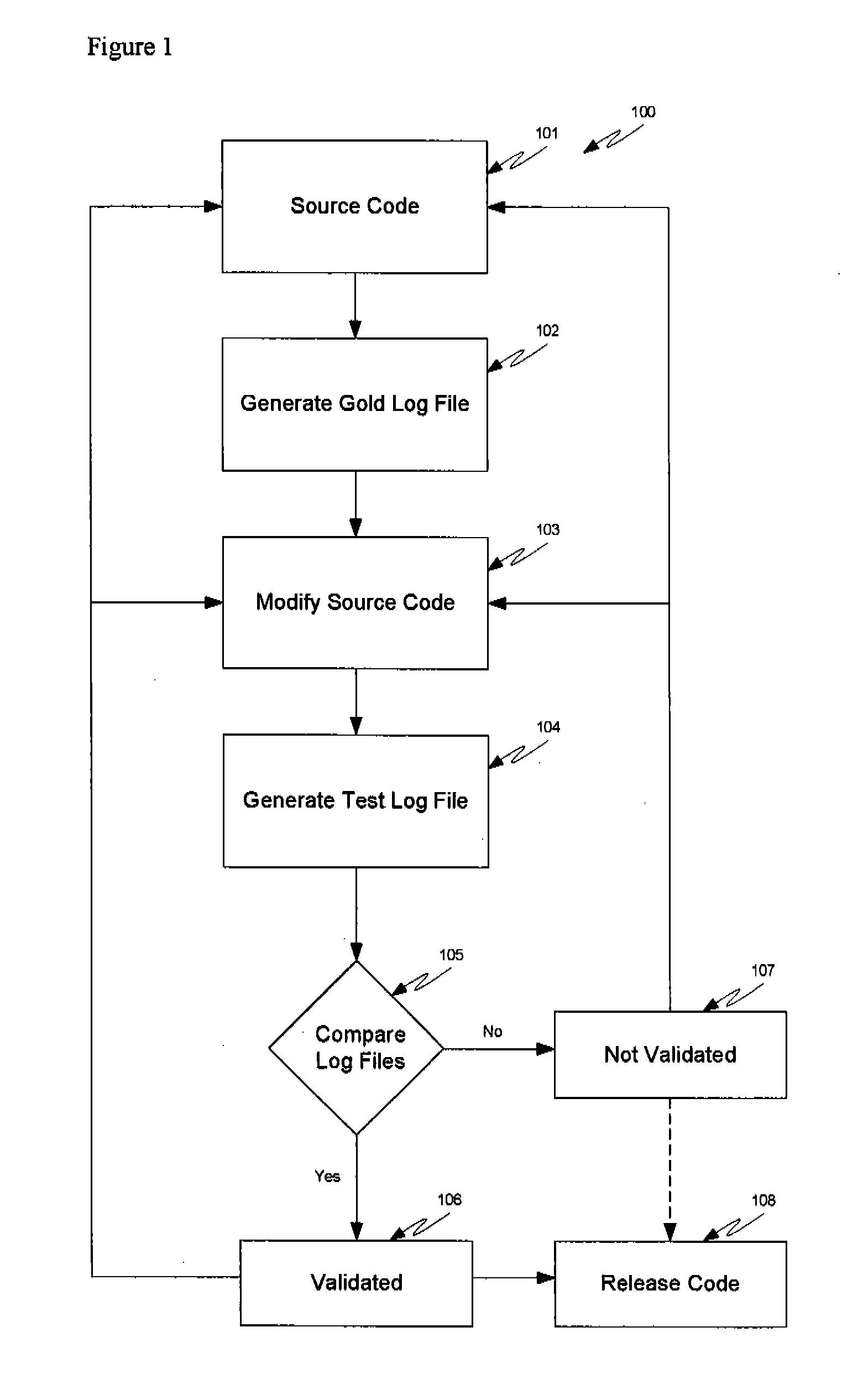
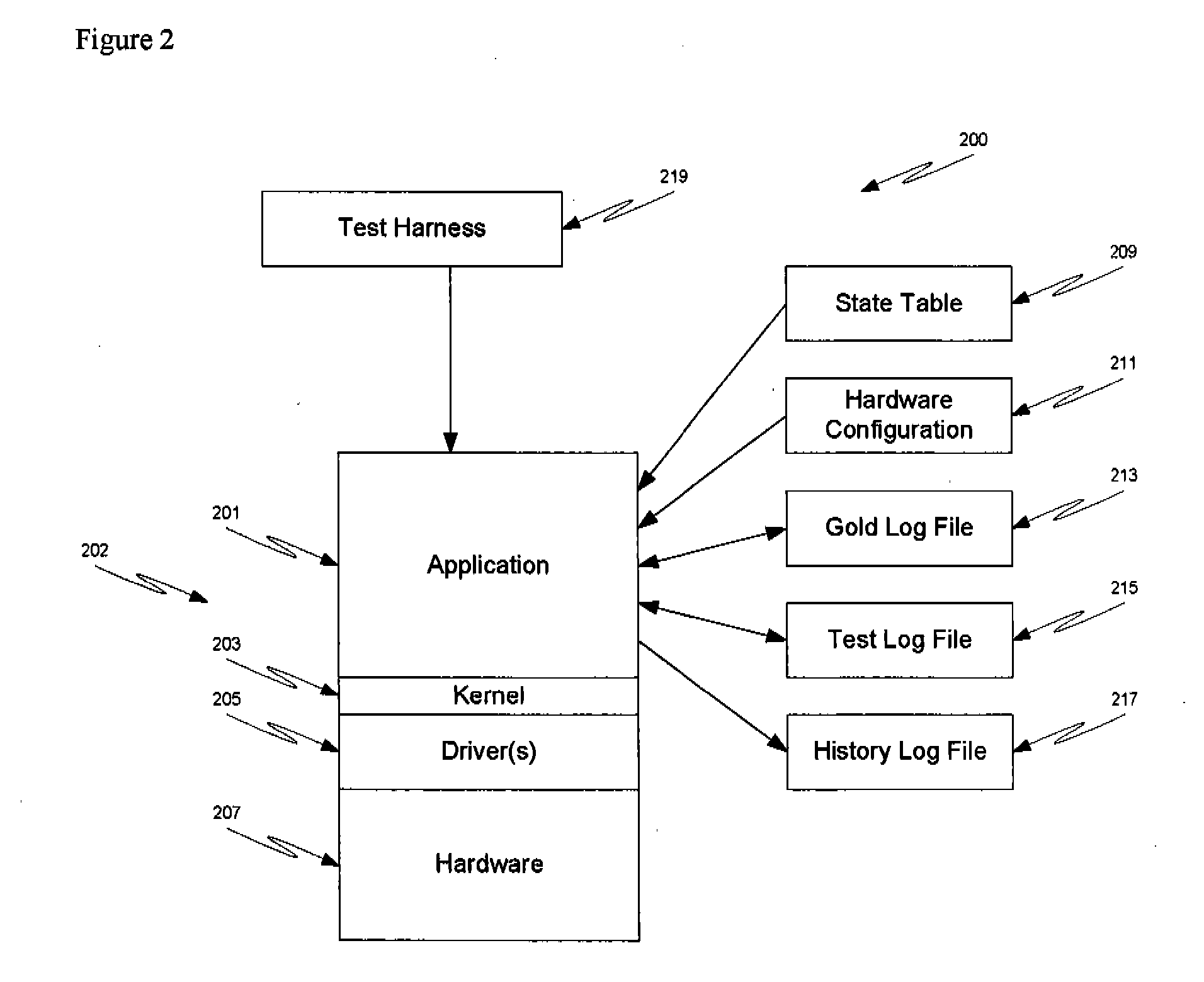
Method and Apparatus for Performing State-Table Driven Regression Testing
InactiveUS20070234300A1Error detection/correctionProgram code adaptionRegression testingQuality assurance
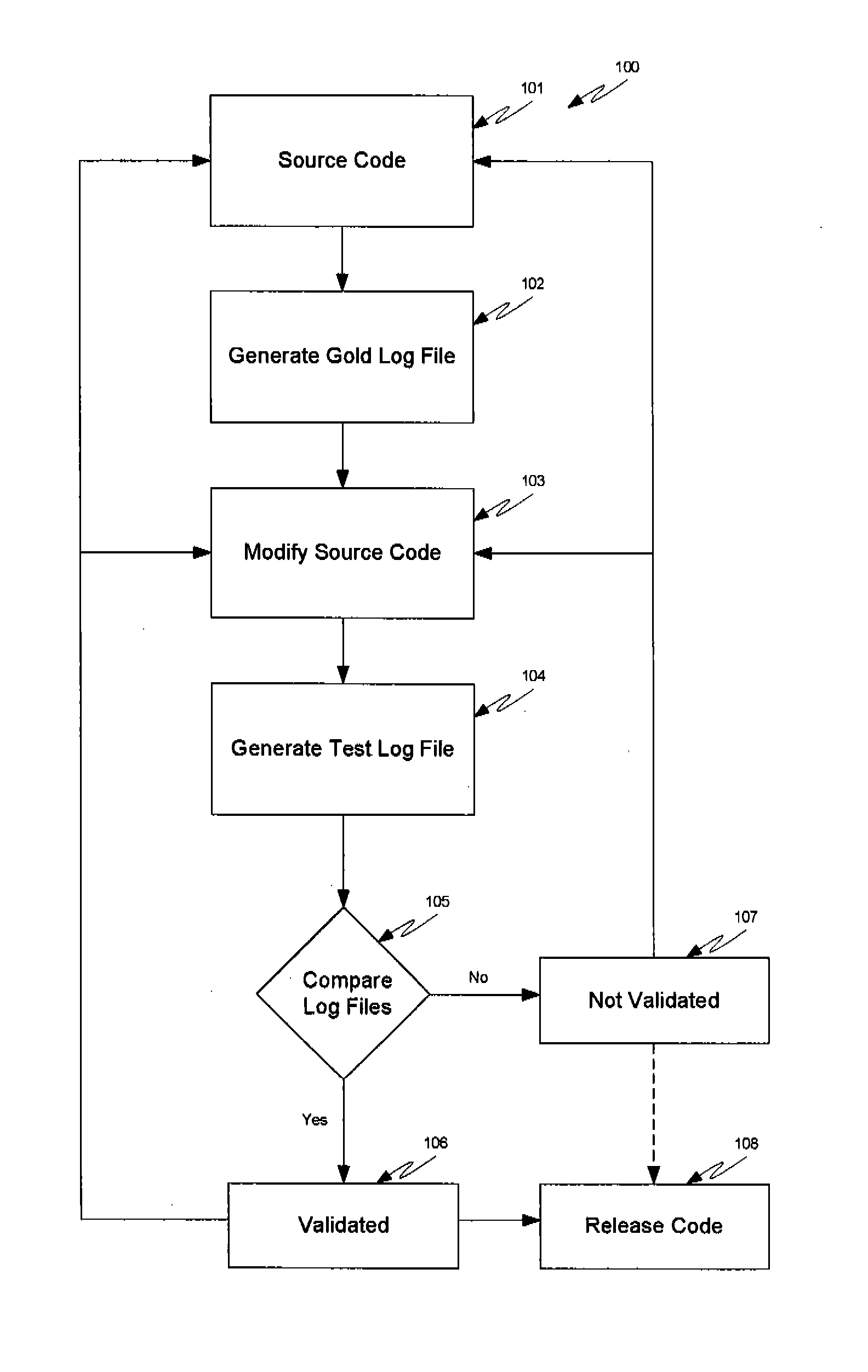
The invention relates to a method and apparatus for performing state-table driven regression testing. More particularly, the invention relates to an application wherein a release build is used without the use of a debug build, which ensures release of the same code that was tested with the exception of the device driver. In a third embodiment, the tested code is the same as the release code, thereby enhancing quality control, quality assurance, verification, and / or validation procedures are maintained. In one embodiment of the invention, at least one state table is used in testing release code. In another embodiment, the test code is developed using a first platform and the release code is used on a second, distinct platform. In yet another embodiment, the invention relates to regression testing using simulated faults as monitored through log files.
Owner:SENSYS MEDICAL
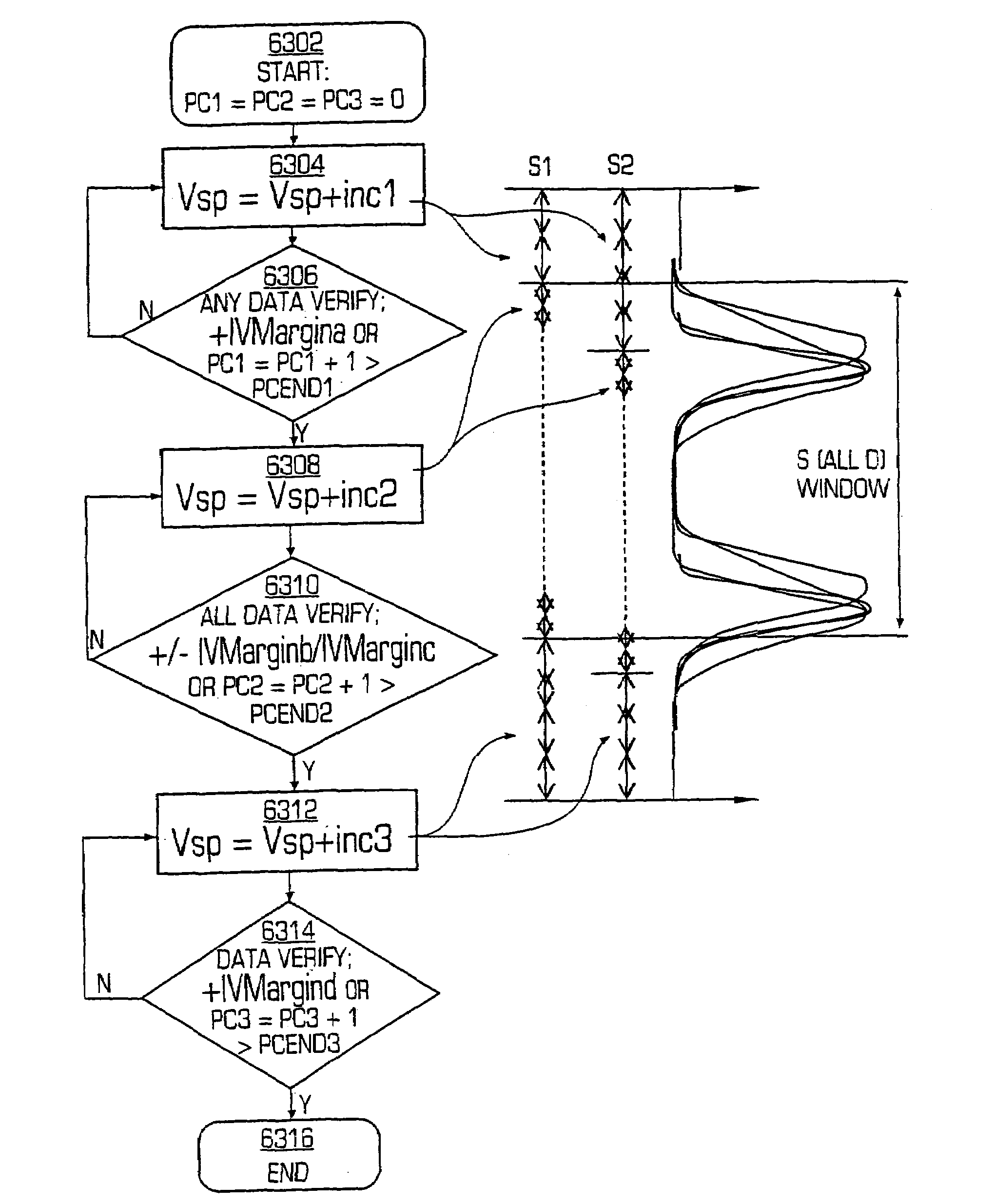
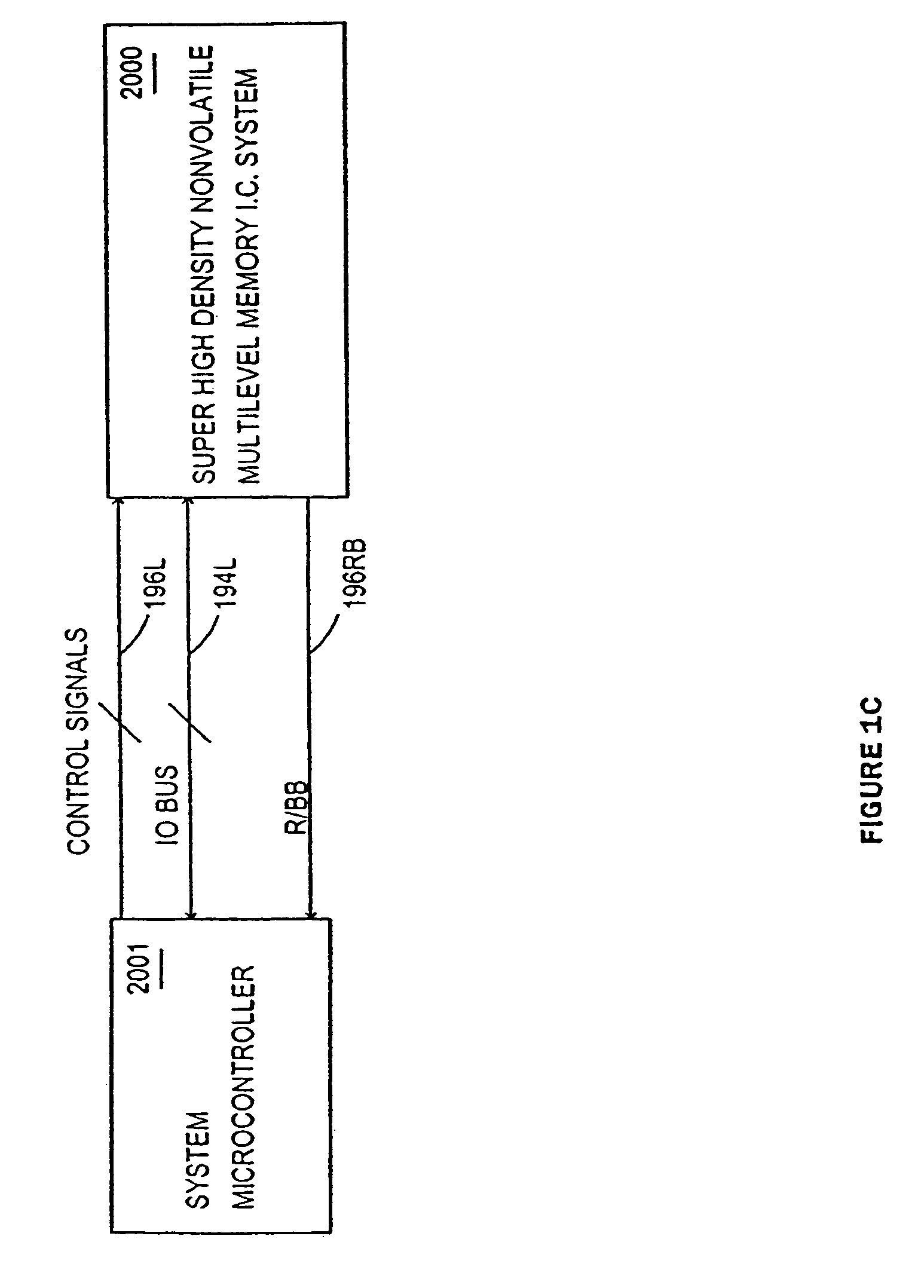
Seek window verify program system and method for a multilevel non-volatile memory integrated circuit system
A memory comprises a plurality of digital multilevel memory cells. A window of valid data voltages for accessing the said plurality of digital multilevel memory cells is detected. The window may be detected by incrementing a first programming voltage to program data in the plurality of memory cells and verifying whether the data in at least one of said plurality of memory cells is properly programmed. The incrementing and verifying may be repeated until data is verified to be properly programmed in one of said plurality of memory cells. The data in each memory cell of said plurality of memory cells is verified. The verification may be by incrementing a second programming voltage, and verifying whether data in each memory cell is properly programmed within a margin. The incrementing and verifying is repeated for each memory cell outside of the margin.
Owner:SILICON STORAGE TECHNOLOGY
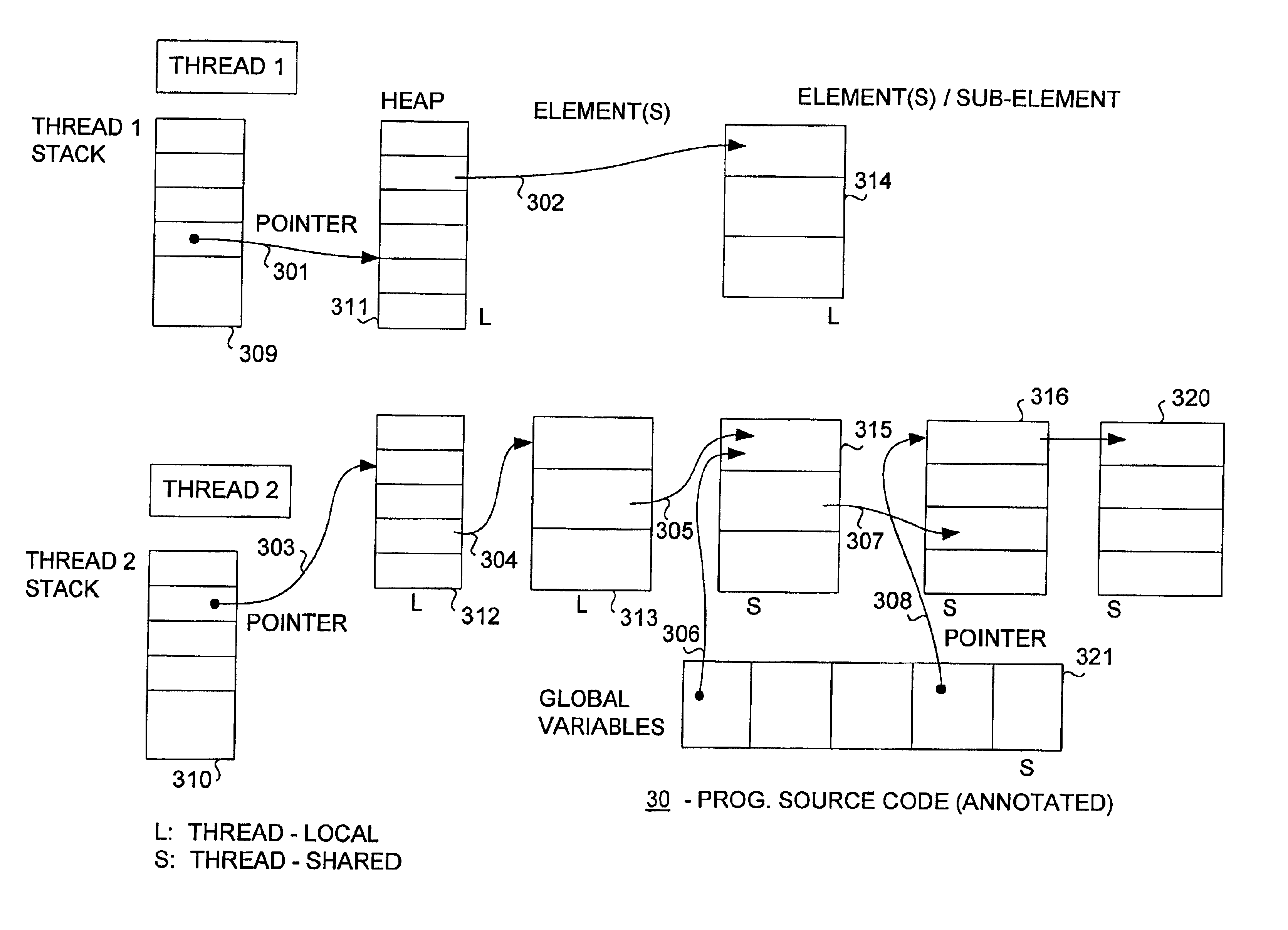
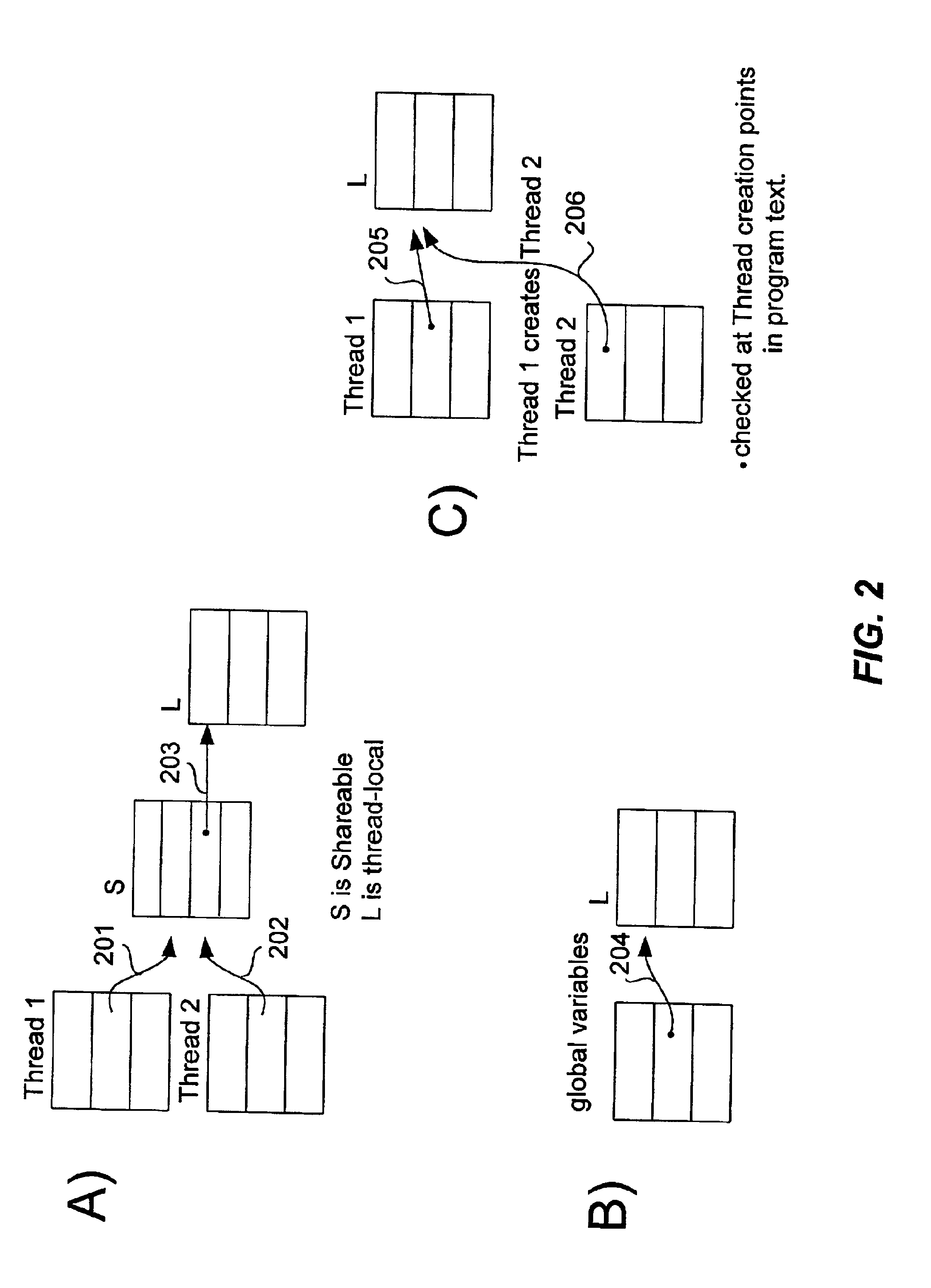
Method and apparatus for verifying data local to a single thread
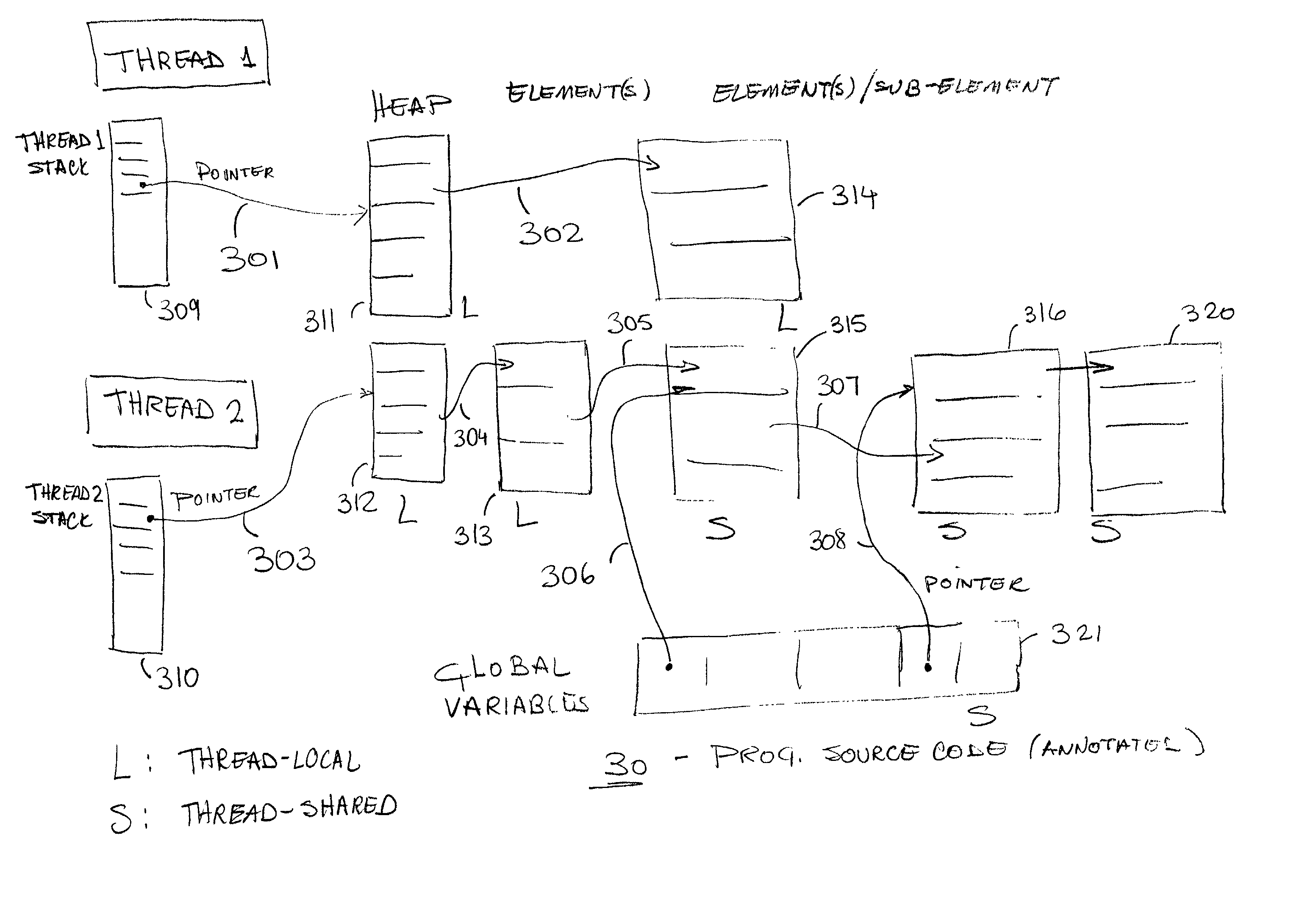
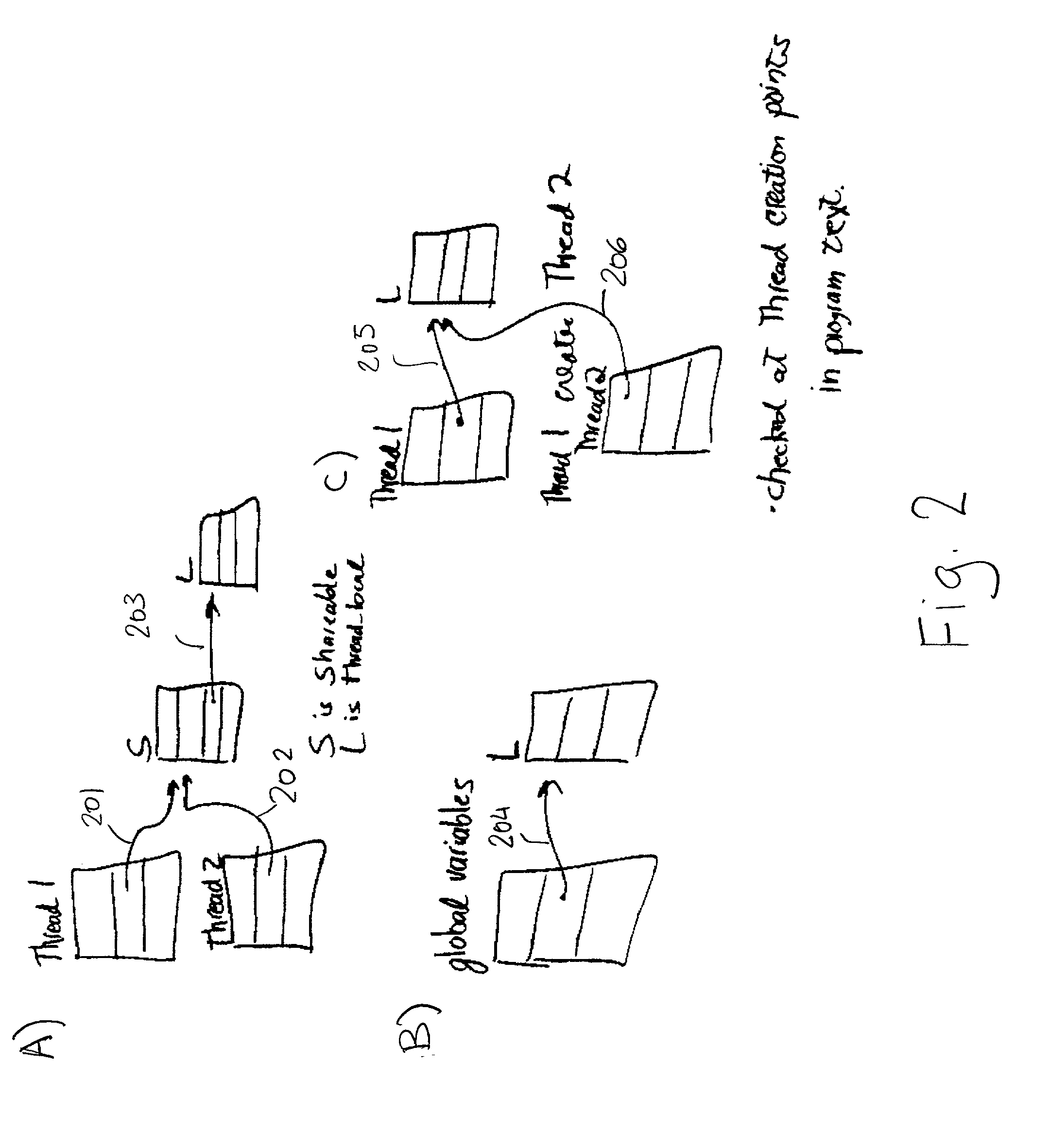
InactiveUS6817009B2Ensuring validityAccurate checkError detection/correctionSoftware engineeringProgram analysisSource code
Concurrent program analysis is fashioned for detecting potential race conditions such as data races in computer programs. One feature of this analysis is verifying annotations of addressable resources in a program. Annotations are verified by checking if thread-local resources are indeed thread-local, and that thread-shared data spaces are not in fact thread-local. Another feature is detecting potential race conditions, such as data races, in the computer program. The computer program can spawn a plurality of threads that are capable of being executed concurrently. The source code of the computer program being analyzed includes an element annotated as either thread-local or thread-shared. The validity of the thread-local annotation is verified if the element is annotated in the computer program as thread-local, wherein an invalid thread-local annotation may cause a race condition.
Owner:VALTRUS INNOVATIONS LTD +1
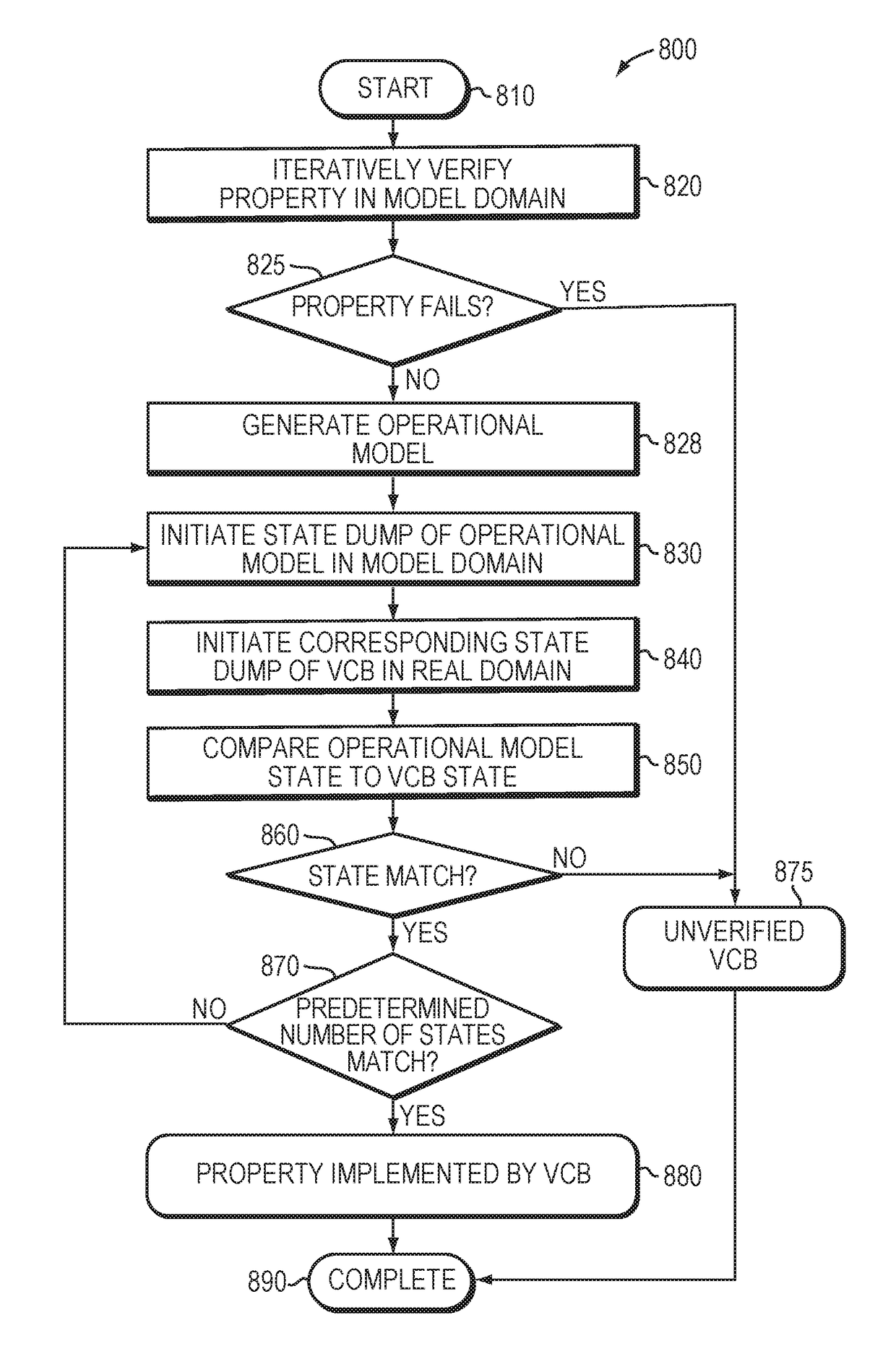
System and method for protected operating system boot using state validation
ActiveUS20060005034A1High degreeGuaranteed growthLink editingError detection/correctionOperational systemEngineering
Owner:MICROSOFT TECH LICENSING LLC
Automated system for capturing and archiving information to verify medical necessity of performing medical procedure
InactiveUS20070021977A1Simplifies auditing processSimple to executeFinanceHealth-index calculationClinical informationVerified procedure
An automated routine verifies the medical necessity of a procedure. When a procedure is scheduled, the routine searches for, captures and archives patient and clinical information in an audit file, to evidence medical necessity of the procedure. If the audit file lacks one or more pieces of information, medical personnel will be visually alerted to the shortcoming and what is lacking. The user may then activate one or more objects of a user interface, to search resources that contain the required information, so that the audit file may be updated, as necessary, so as to comply with requirements of the Center for Medicare / Medicaid Services.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
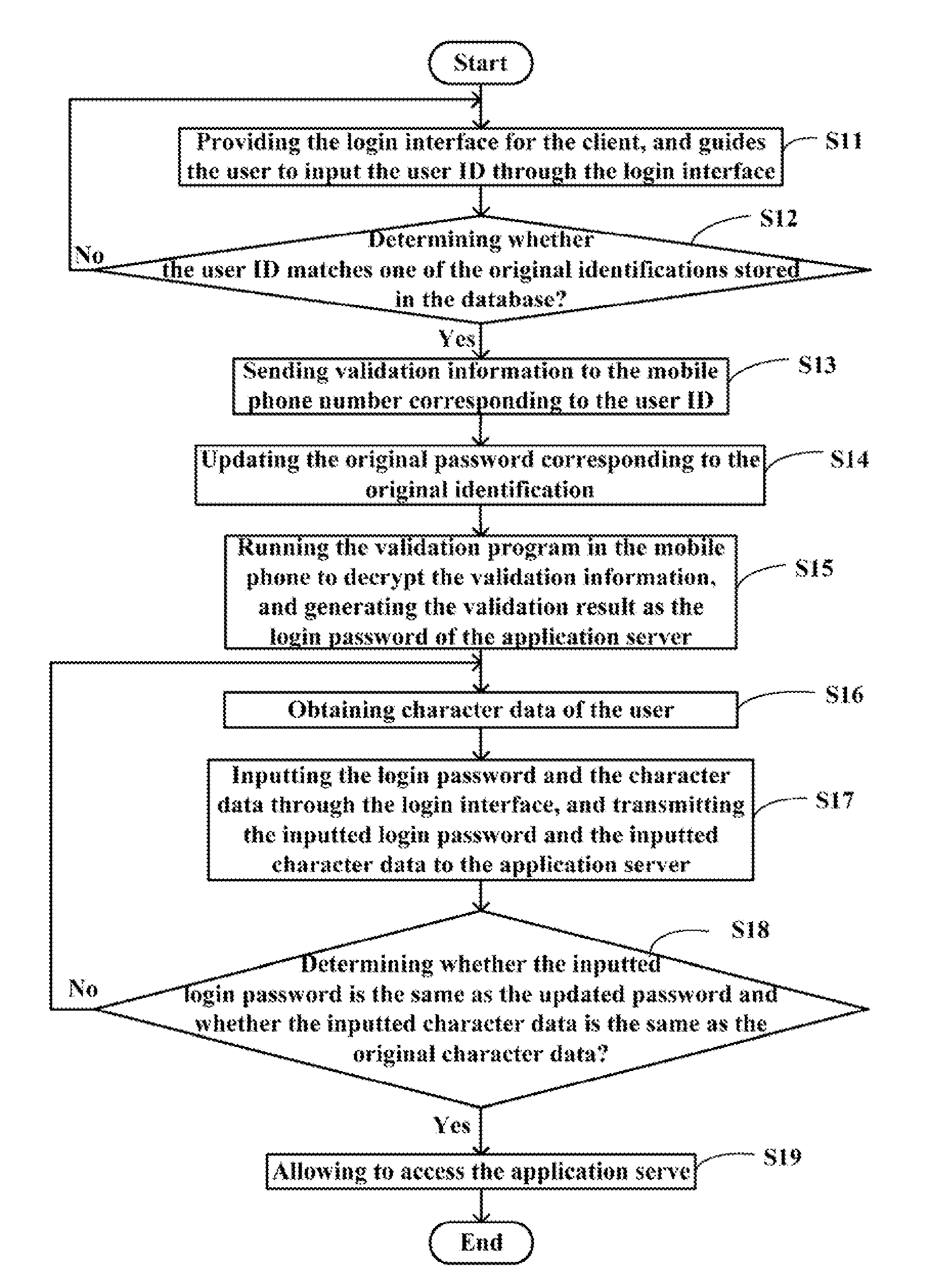
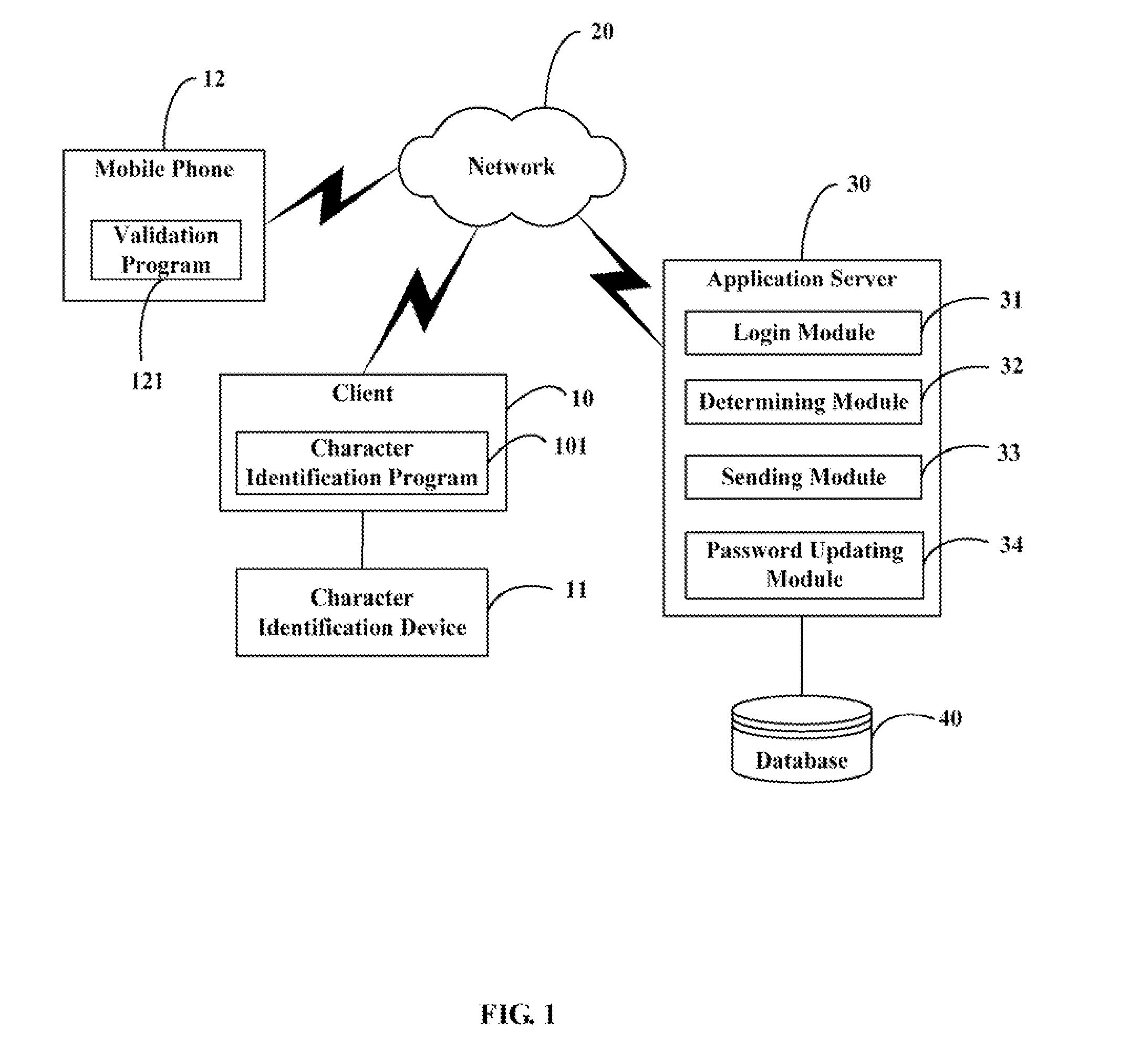
System and method for validating user identification
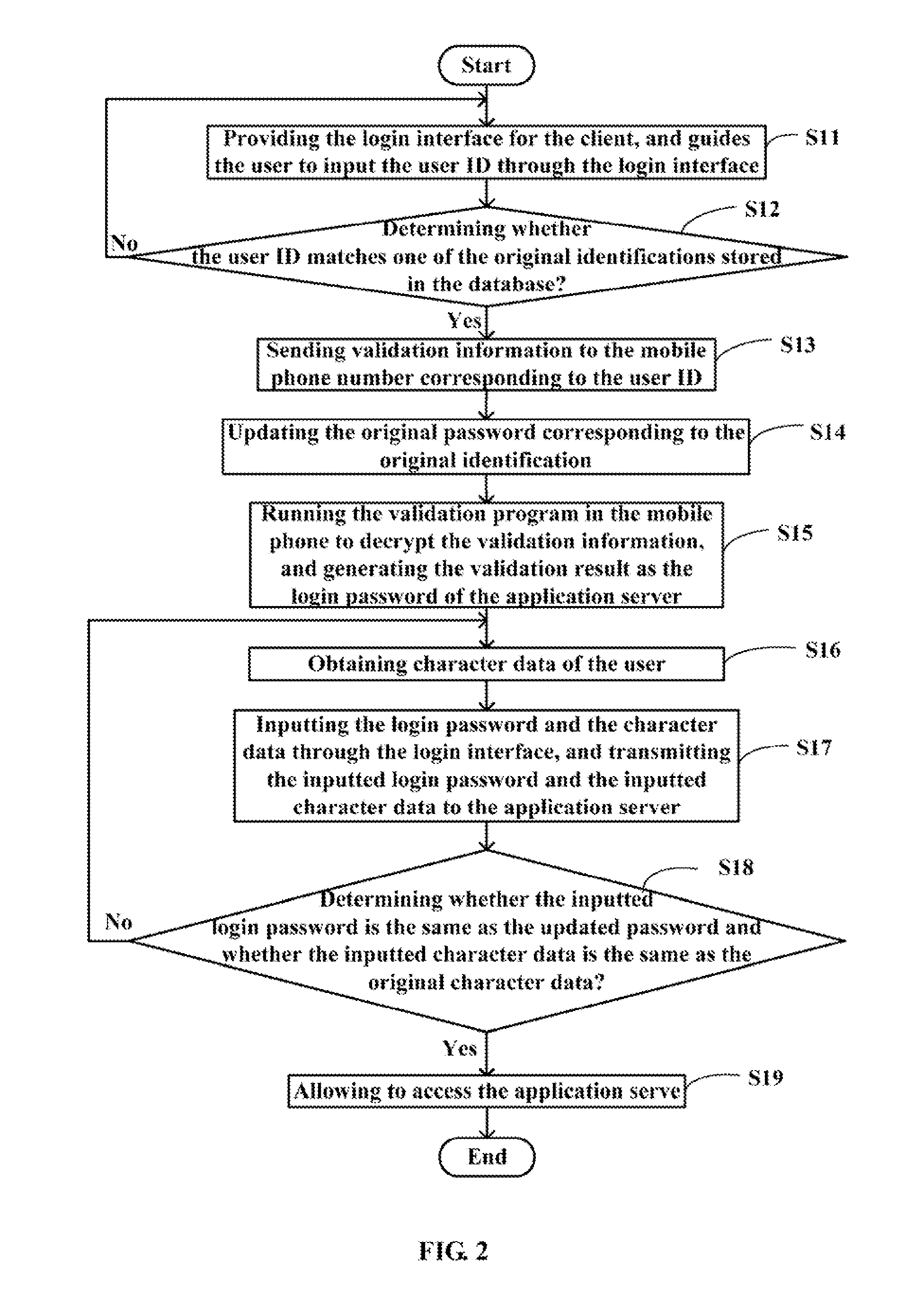
InactiveUS20090077640A1Digital data processing detailsMultiple digital computer combinationsApplication serverPassword
A method for validating user identification includes the steps of: guiding a user to input a user ID through a login interface; comparing the user ID with original identifications stored in a database (40) and determining whether the user ID matches one of the original identifications; sending validation information to a mobile phone number corresponding to the original identification; updating an original password, corresponding to the original identification, according to the validation information; running a validation program, installed in a mobile phone having the mobile phone number, to decrypt the validation information, and generating a validation result as a login password; inputting the login password through the login interface, and transmitting the inputted login password to an application server (30); and determining whether the inputted login password is the same as the updated password. A system for validating user identification is also provided.
Owner:CHI MEI COMM SYST INC
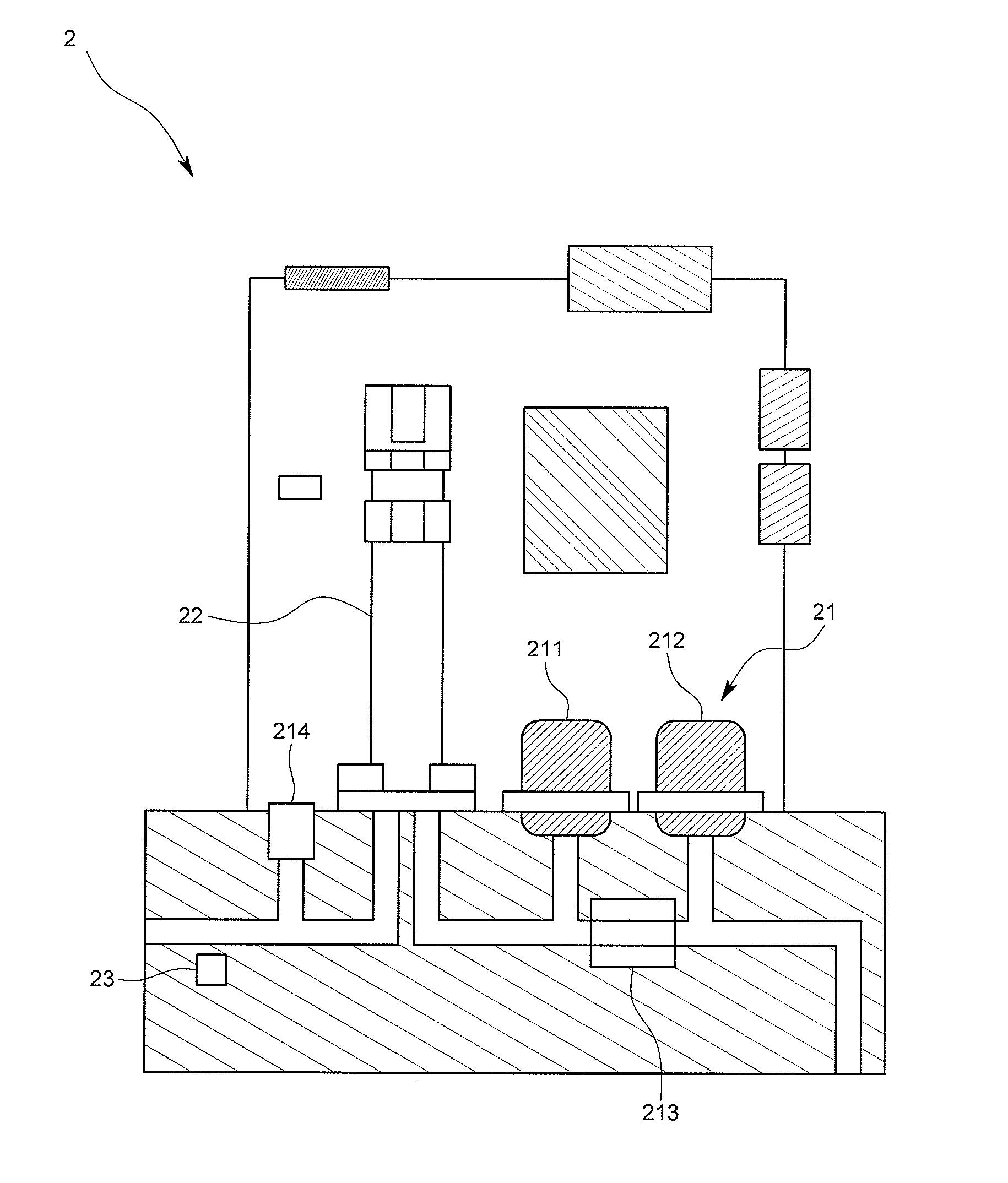
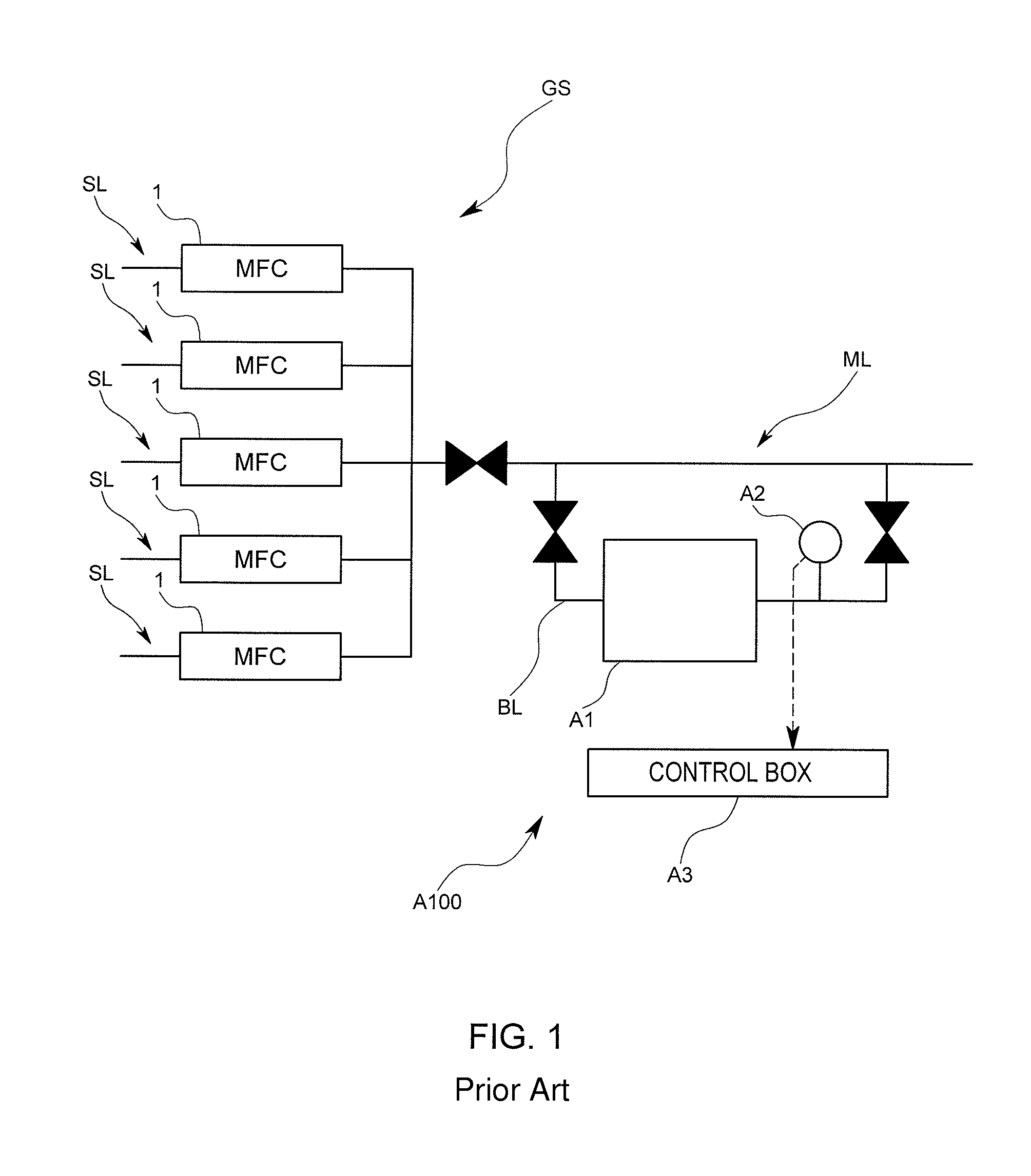
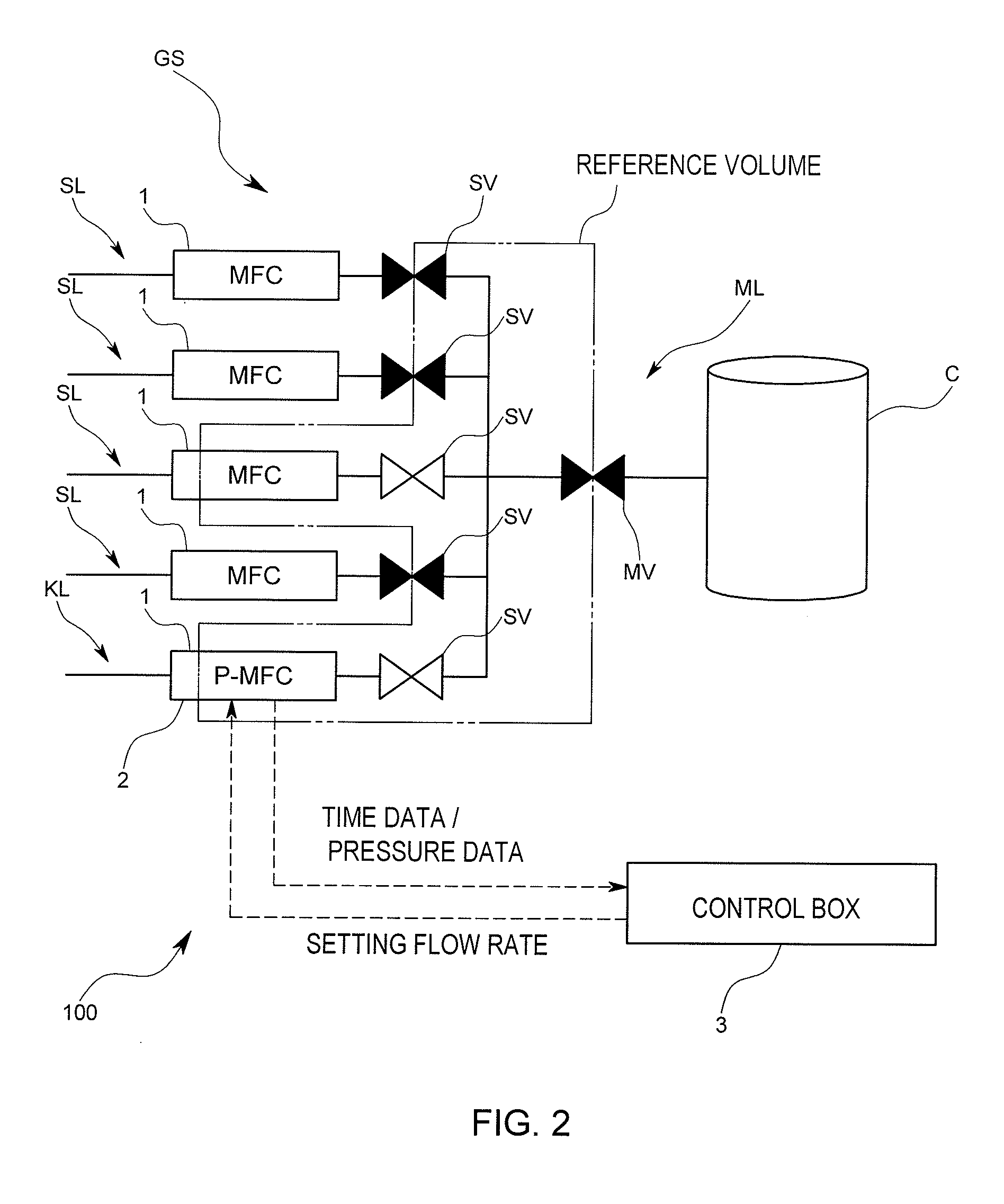
Mass flow controller verifying system, verifying method and verifying program
InactiveUS20100229967A1Minimized volumeReduce verification timeVehicle testingSemiconductor/solid-state device manufacturingLine tubingValidation methods
In a mass flow controller verifying system, there are provided a verifying gas line arranged in parallel to influent flow gas lines and joined into a post-confluent flow gas line, a reference volume calculating portion adapted to calculate a reference volume determined for a specified piping of a gas piping system, a verifying parameter calculating portion adapted to calculate a verifying parameter based on time series data of a measurement pressure measured by a pressure measurement unit during a control of a flow rate by a mass flow controller to be verified, and a comparing portion adapted to compare a reference parameter set based on the reference volume and the verifying parameter, whereby the verifying system can be introduced into an existing gas piping system used in a semiconductor manufacturing process and so forth at a low cost and is capable of verifying a mass flow controller quickly and accurately.
Owner:HORIBA STEC CO LTD
System and method for verifying delivery and integrity of electronic messages
InactiveUS7865557B2Verify reliabilityUser identity/authority verificationMultiple digital computer combinationsVerified procedureParagraph
A server transmits a message from a sender to a destination address. During transmission, the server and the destination address have a dialog constituting an attachment, via a particular one of SMTP and ESMTP protocols, concerning the message, the server and the destination address. The message passes through servers between the server and the destination address. This passage is included in the attachment. Verifiers are provided for the message and for the attachments. The verifiers may constitute encrypted hashes of the message and of the attachment. The sender receives the message, the attachments and the verifications from the server before authentication and transmits the message, the attachments and the verifiers to the server to obtain authentication by the server. The server operates on the message and the message verifier to authenticate the message and operates on the attachments and the attachments' verifier to verify the attachments.
Owner:RPOST COMM
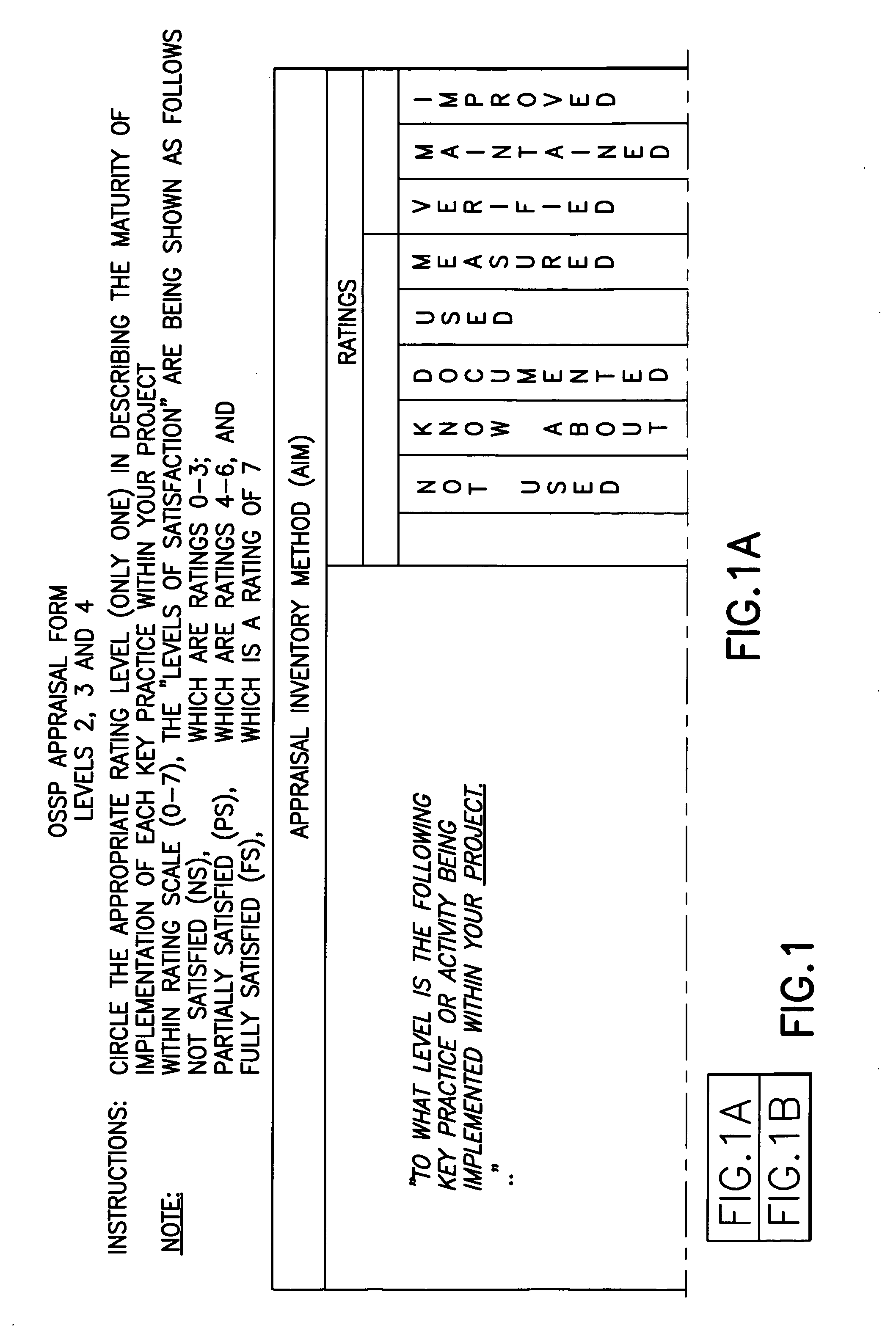
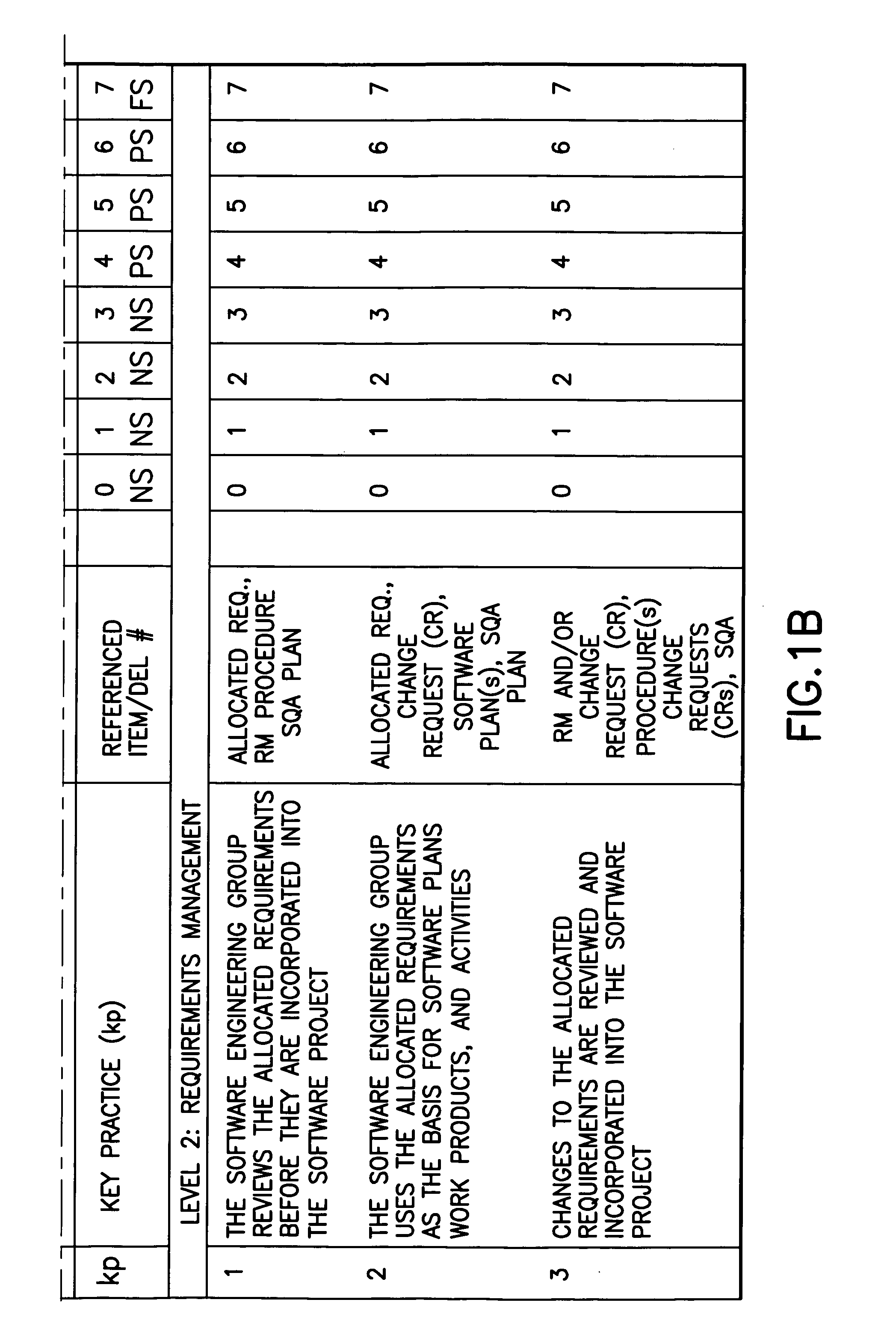
Method for validating software development maturity
InactiveUS20050125272A1Software testing/debuggingSoftware metricsSoftware engineeringSoftware development
A validation procedure for assessing the status a software engineering process for compliance, and improving the measured compliance, with the Carnegie Mellon SEI / CMM Software Maturity Model includes a validation meeting in the course of which a validation team reviews deliverables demonstrative of the process being performed and asks a structured set of questions that are structured in accordance with the CMM and correlate with the deliverables.
Owner:NOKIA SOLUTIONS & NETWORKS OY
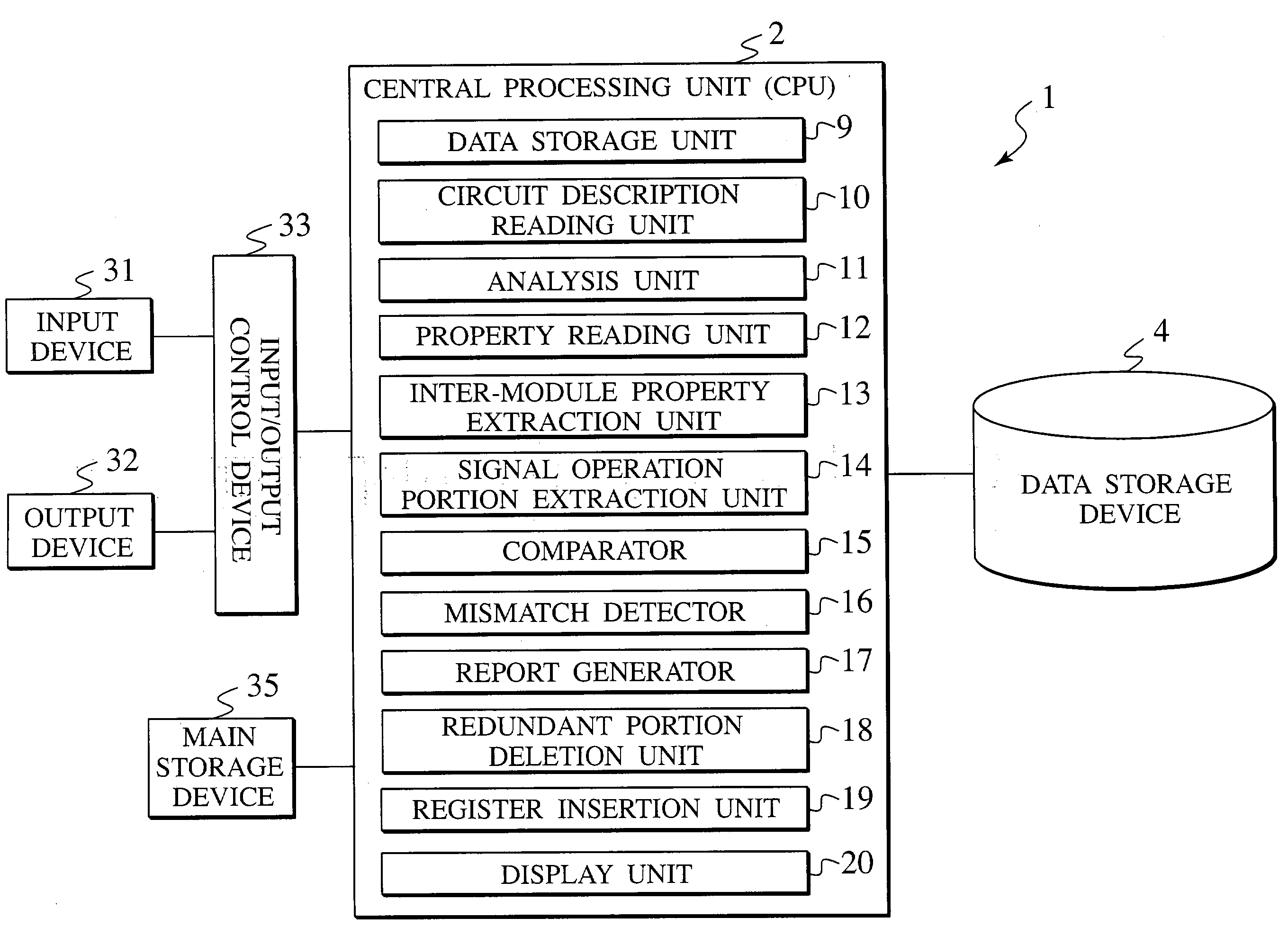
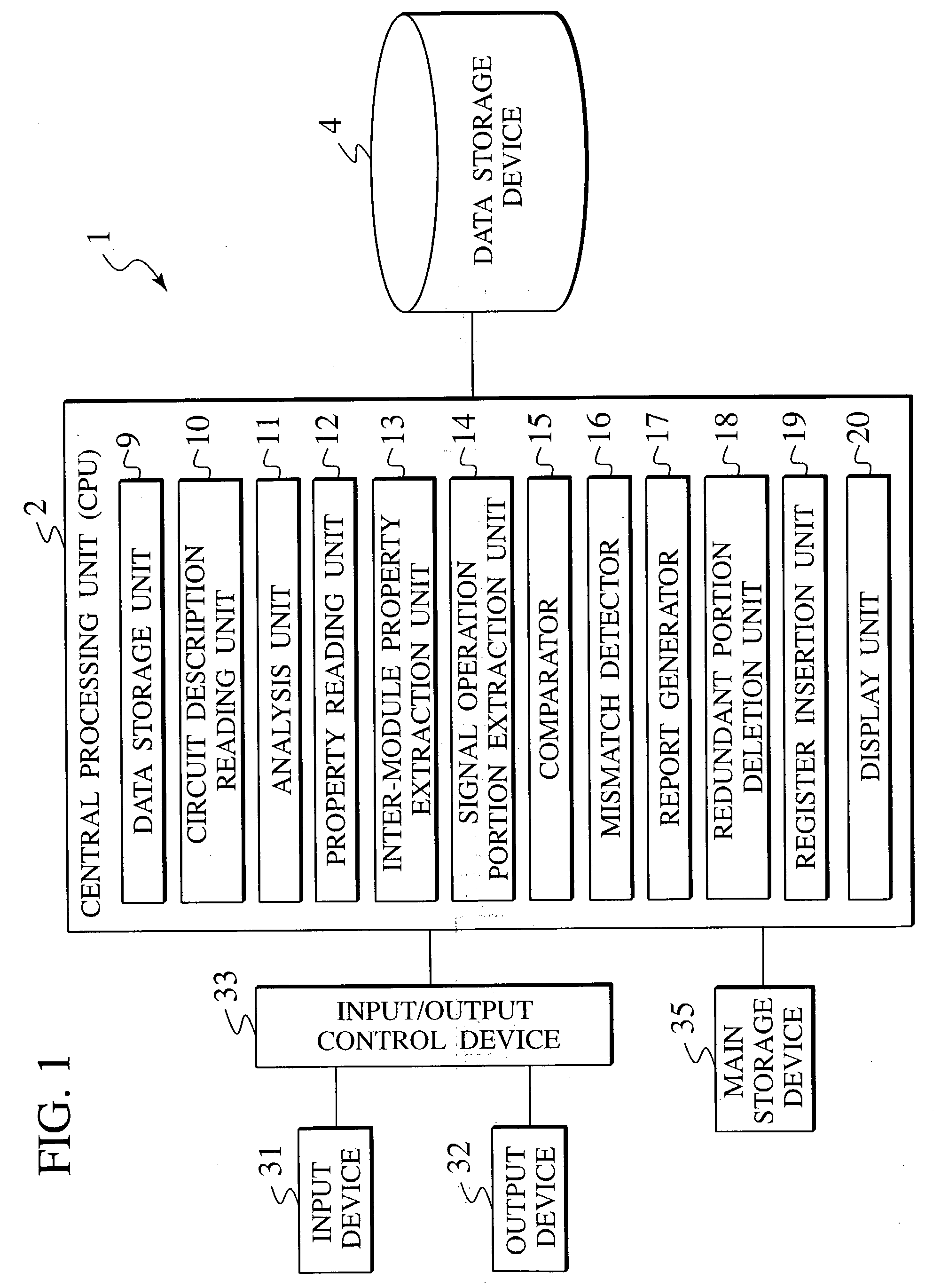
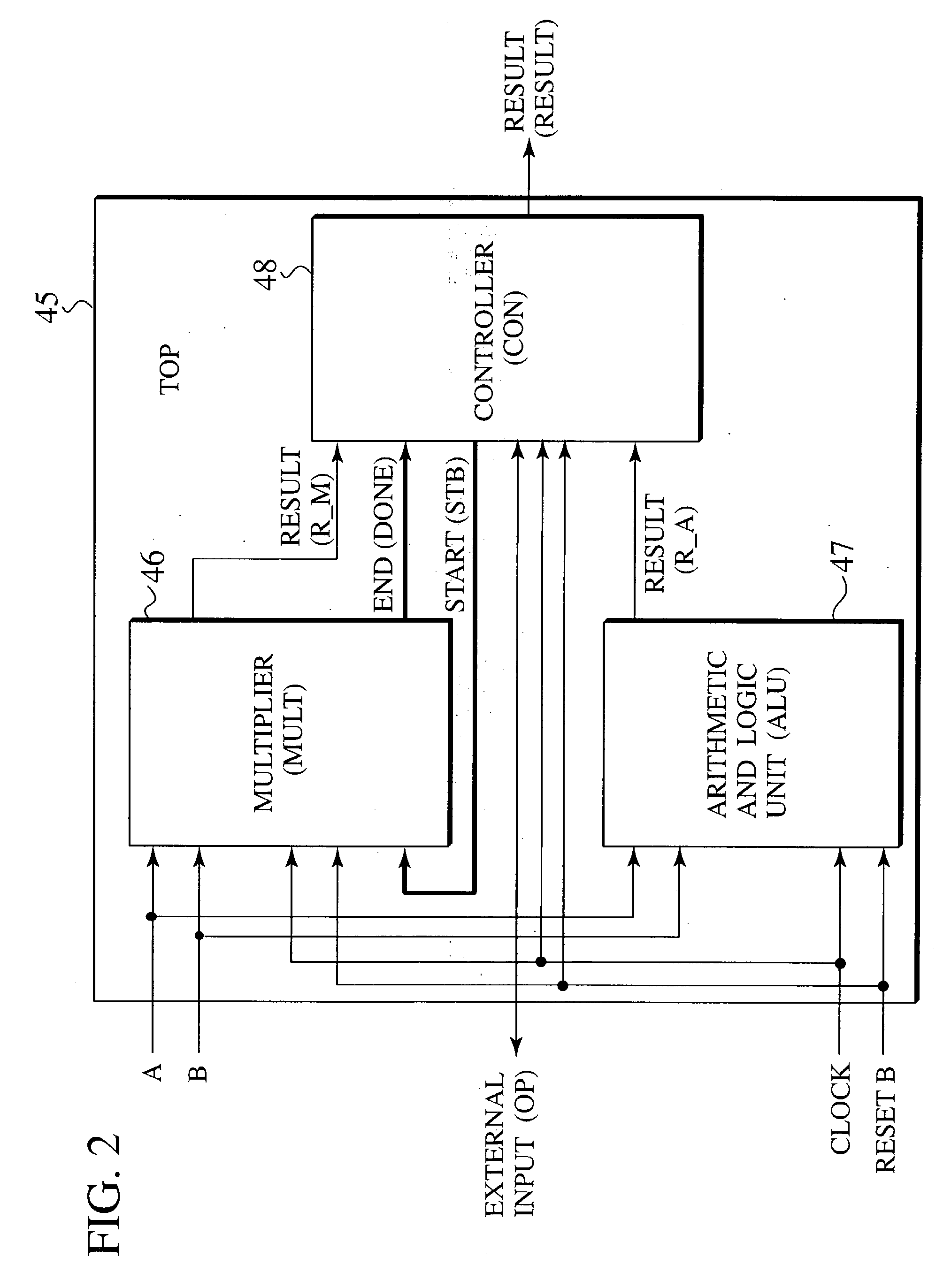
LSI design verification apparatus, LSI design verification method, and LSI design verification program
InactiveUS20030125920A1Electronic circuit testingSemiconductor/solid-state device manufacturingComputer architectureValidation methods
A computer implemented method for design verification using logical simulation of a circuit description having a plurality of hierarchies from top to bottom in accordance with abstraction of circuit components, which have an arithmetic and logic function, reads the circuit description and analyzes signal connection topologies between the hierarchies of the circuit description from top to bottom. The method stores the data of the signal connection topologies. The method reads properties of target modules implemented by the circuit components in the circuit description. The method extracts a property part having a signal communicating between the target modules. The method extracts an output operation property, defining output operation of an output side module, and an expecting operation property, defining an expecting operation of an input side module among the properties of the target modules. The method compares the output operation properties with the expecting operation properties.
Owner:KK TOSHIBA
Method and system usable in sensor networks for handling memory faults
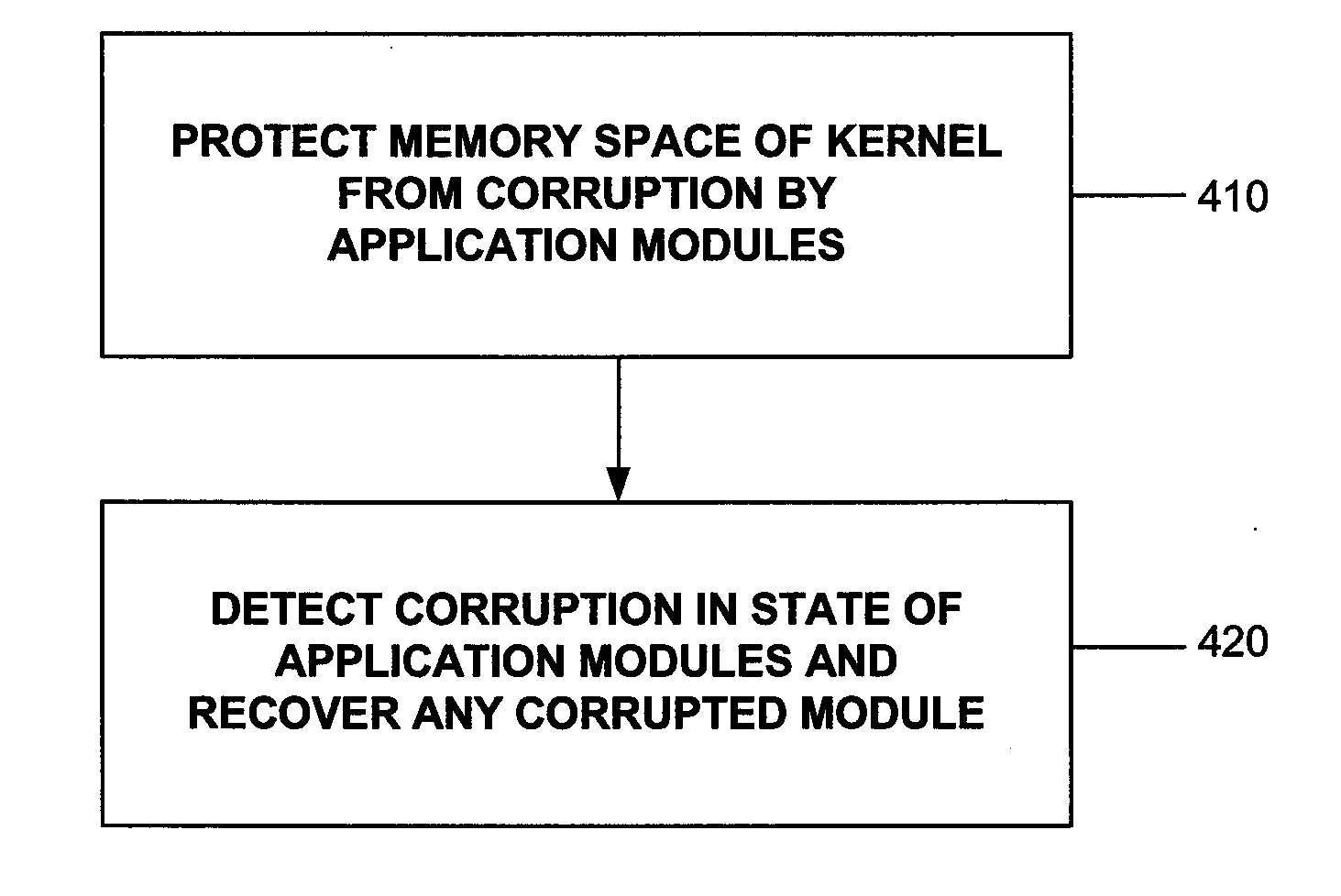
InactiveUS20070156951A1Corrupt stateProtection operationError detection/correctionMemory systemsMemory faultsOperational system
A method and system usable in sensor networks for handling memory faults is disclosed. In order to protect the operating system of a sensor node, coarse-grained memory protection is provided by creating and enforcing an application fault domain in the data memory address space of the sensor node. The data memory accessed by the application modules is restricted to the region (which defines the application fault domain) within the data memory address space. The application modules are prevented from accessing memory outside the application fault domain through software-based run-time checks. The state belonging to the operations system is maintained outside of the application fault domain, and is thus protected from memory corruption from any application module. In order to ensure that an application module does not operate on a corrupted state, fine-grained error detection and recovery is provided within the application fault domain. Any corruption of memory within the application fault domain is detected by a run-time memory integrity verifier implemented in the operating system kernel. Recovery involves purging the corrupted state and restarting only the affected application module to operate on an uncorrupted state.
Owner:NEC CORP
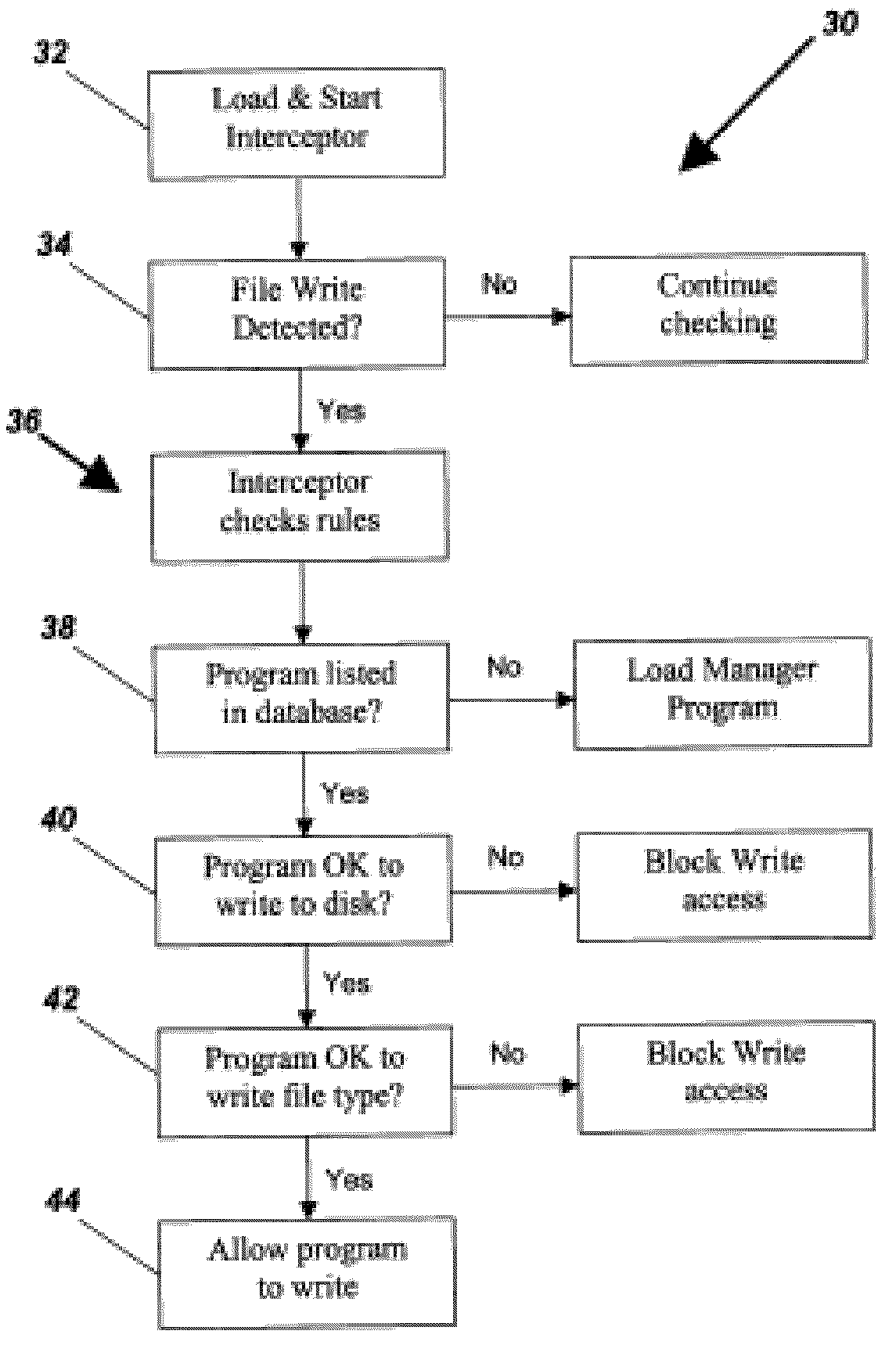
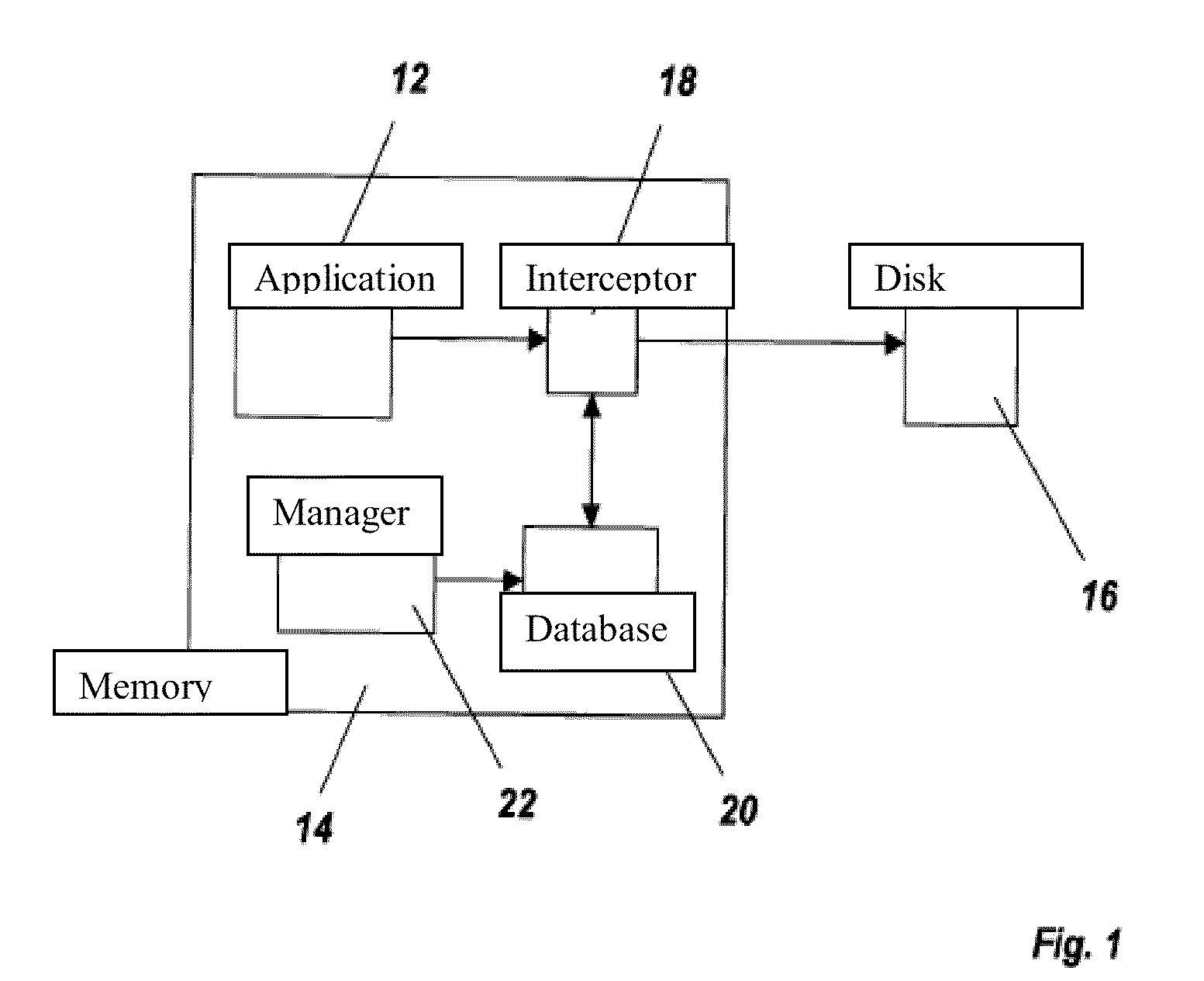
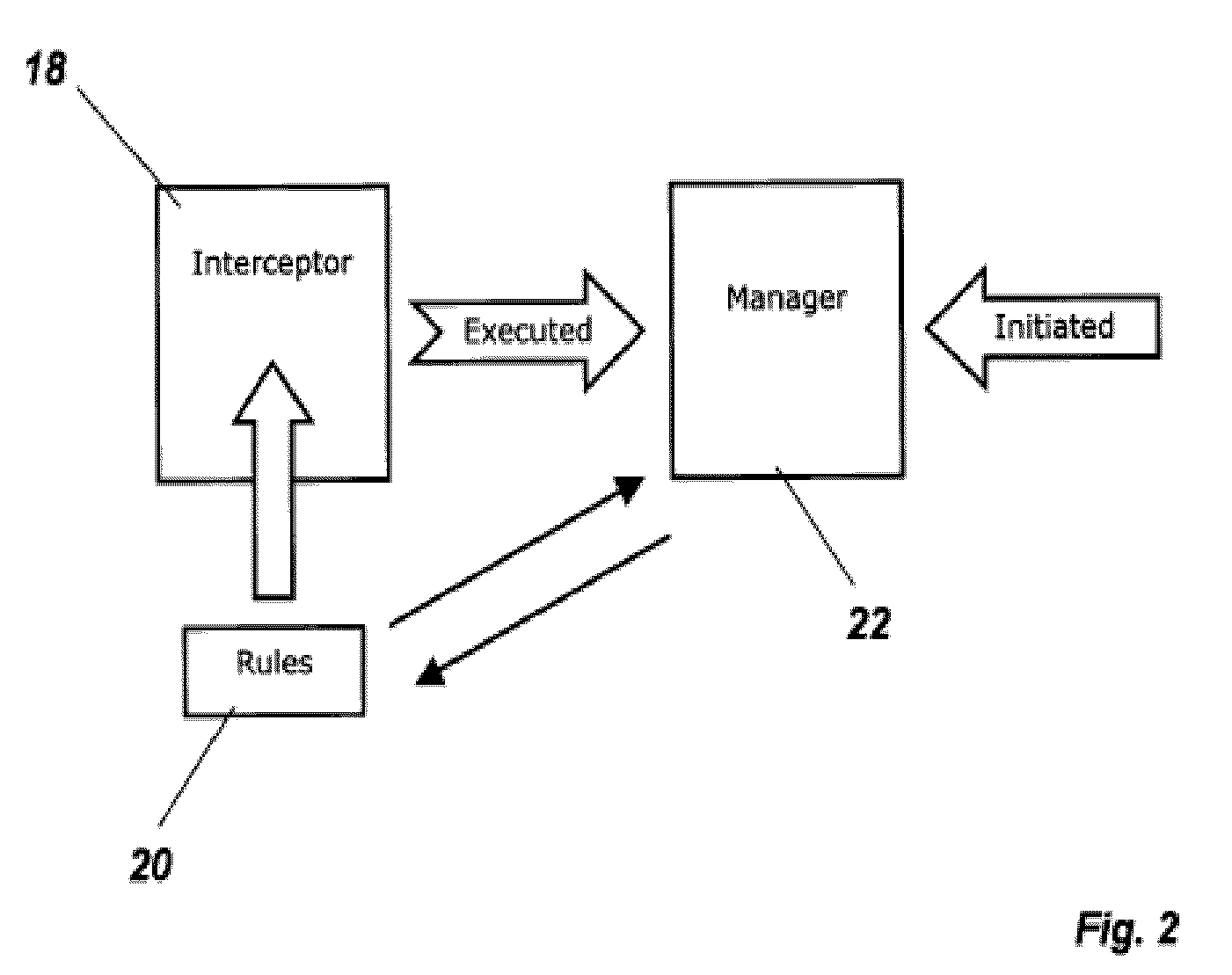
System and method to secure a computer system by selective control of write access to a data storage medium
InactiveUS20100153671A1Unauthorized memory use protectionPlatform integrity maintainanceVerified procedureData store
A system and method to securing a computer system from software viruses and other malicious code by intercepting attempts by the malicious code to write data to a storage medium. The invention intercepts the write access requests made by programs and verifies that the program is authorized to write before letting the write proceed. Authorization is determined by using the identity of the program as a query element into a database where permission values are stored. Depending on the presence or value of the permission value, write access is permitted or denied. Permission values can be set by the user, downloaded from a central server, or loaded into the central server by a group of users in order to collectively determine a permission value. The interception code can operate in kernel mode.
Owner:DRIVE SENTRY
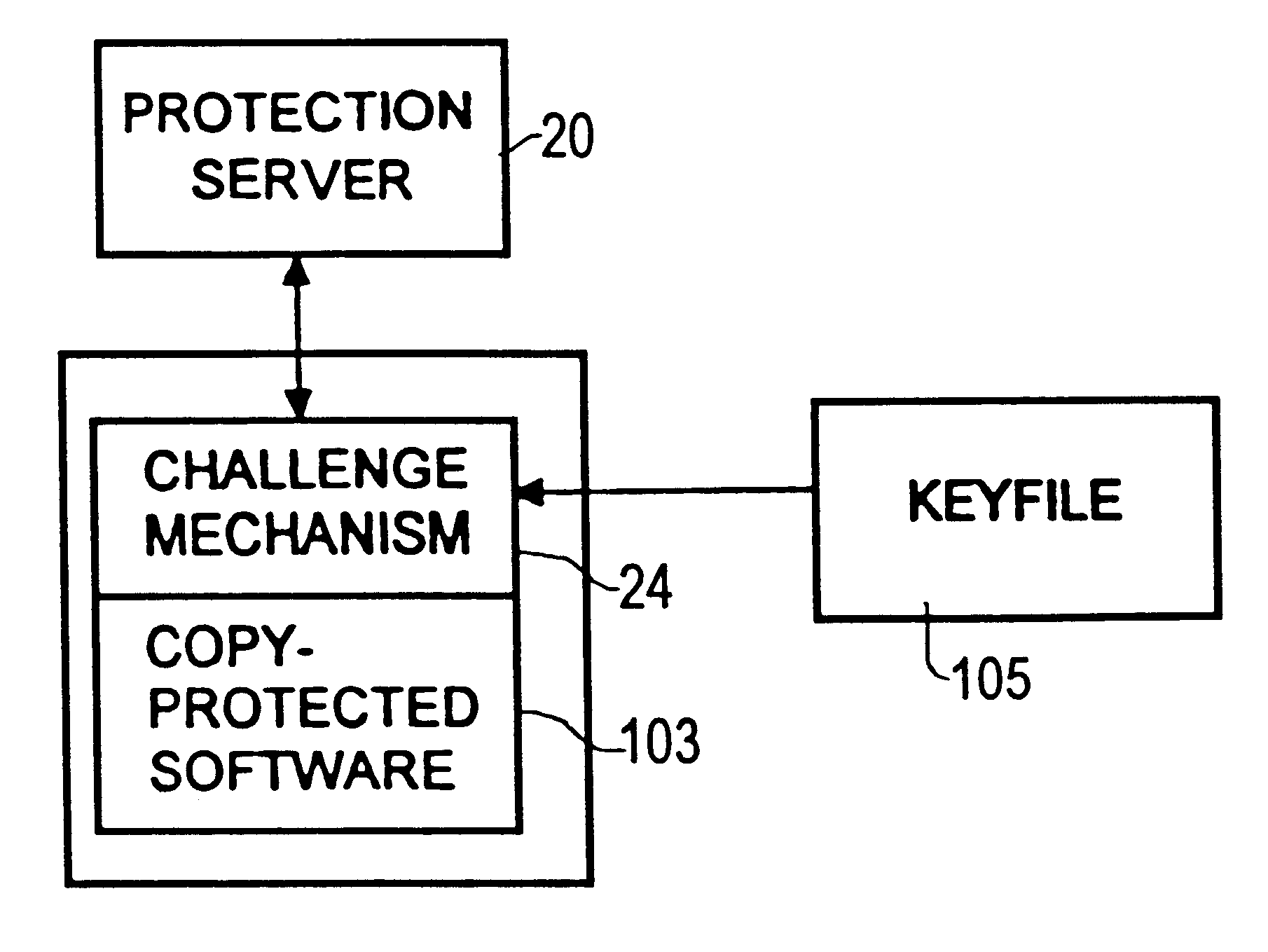
Protection of software using a challenge-response protocol embedded in the software
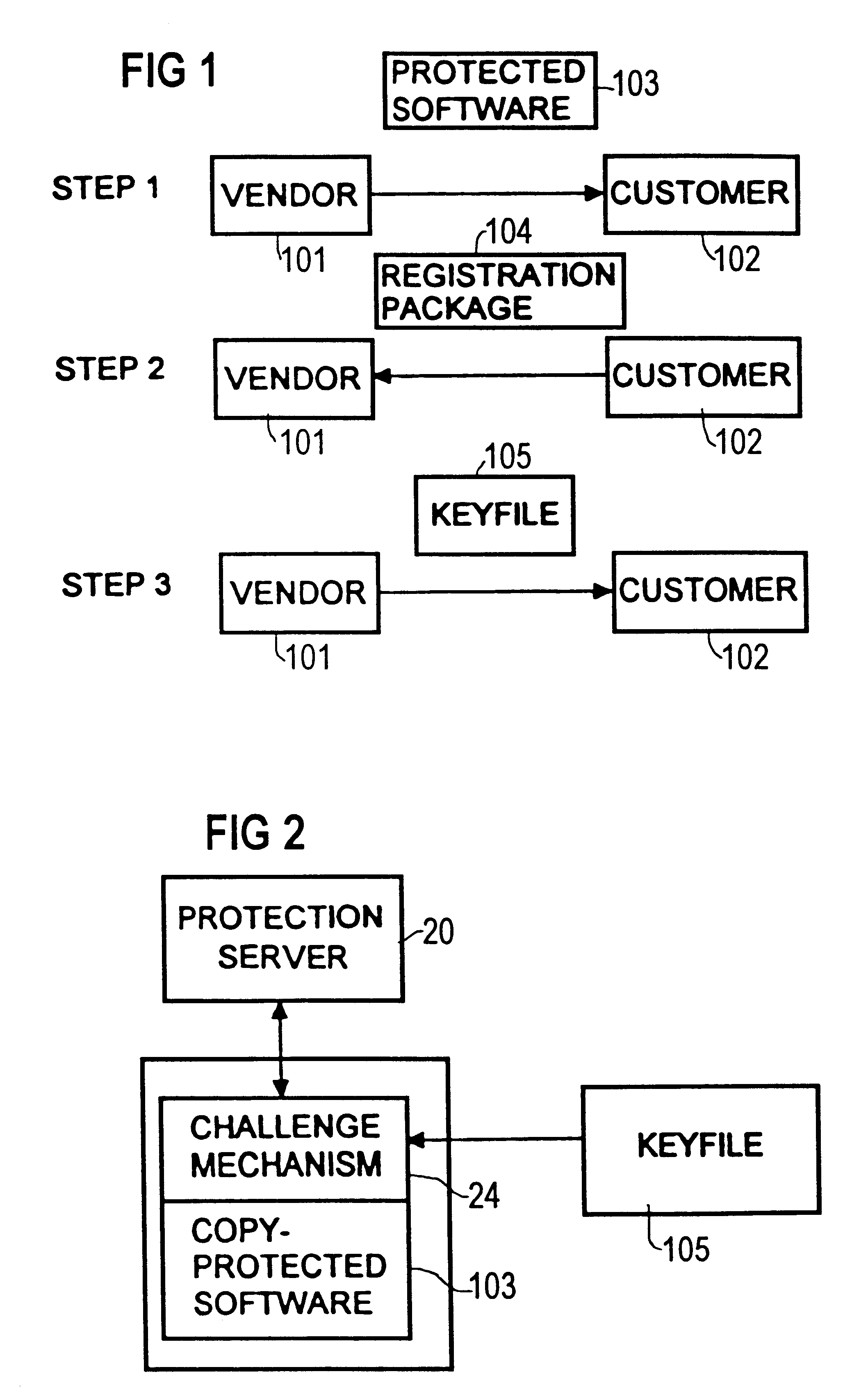
InactiveUS6651169B1Easy to useDigital data processing detailsUser identity/authority verificationConfidentialityVerified procedure
A method for protecting an item of software, wherein at least one challenge is associated with the protected item of software, and at least one response accesses one private keying material. The challenge has no access to the private keying material. The challenge and the response are generating shared secret information, respectively, in accordance with an asymmetric confidentiality scheme. The response proves that it discovered the shared secret and the challenge validates the proof. The challenge proof validation procedure uses the public keying material that corresponds to the response private keying material.
Owner:FUJITSU SIEMENS COMP GMBH
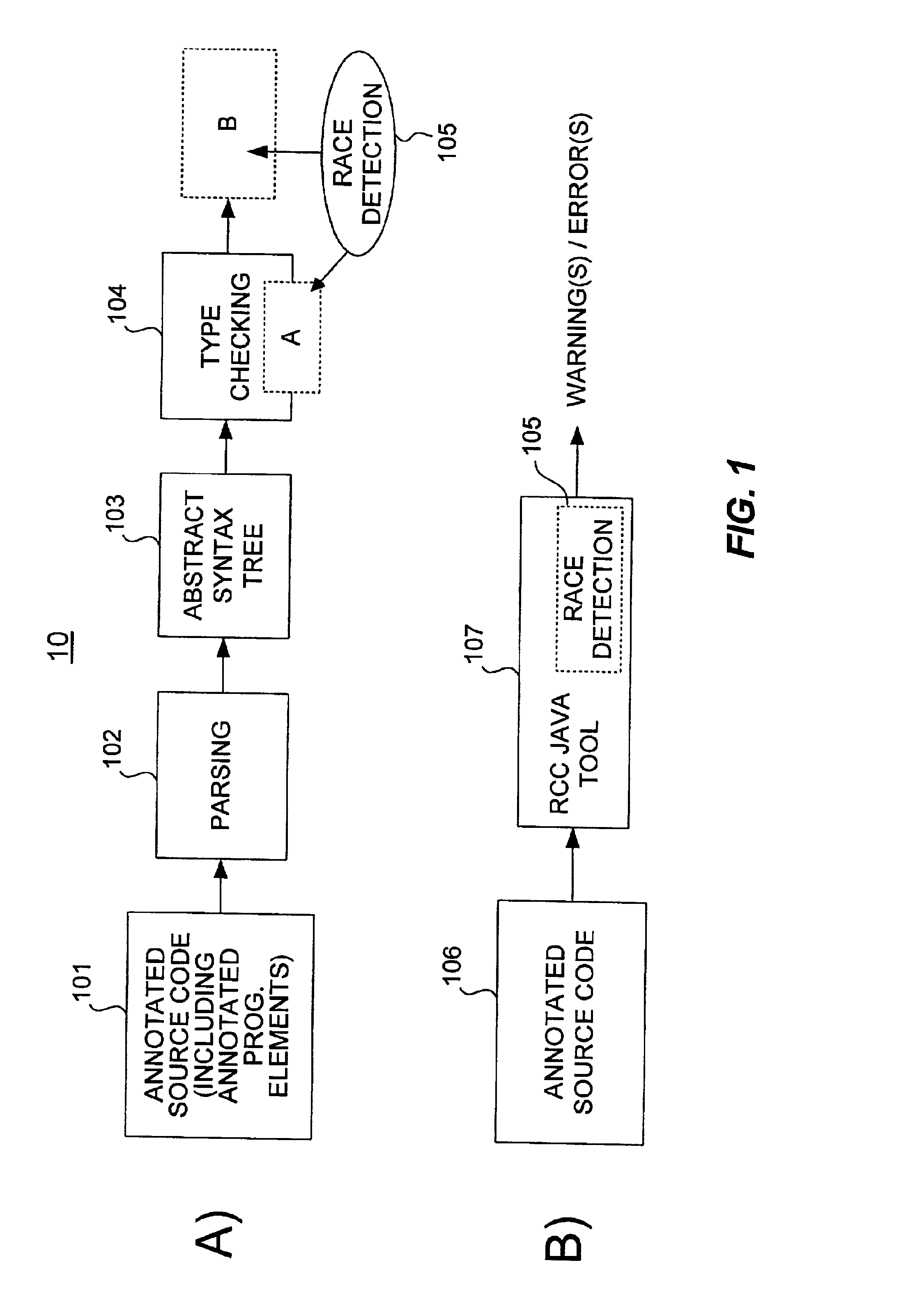
Method and apparatus for verifying data local to a single thread
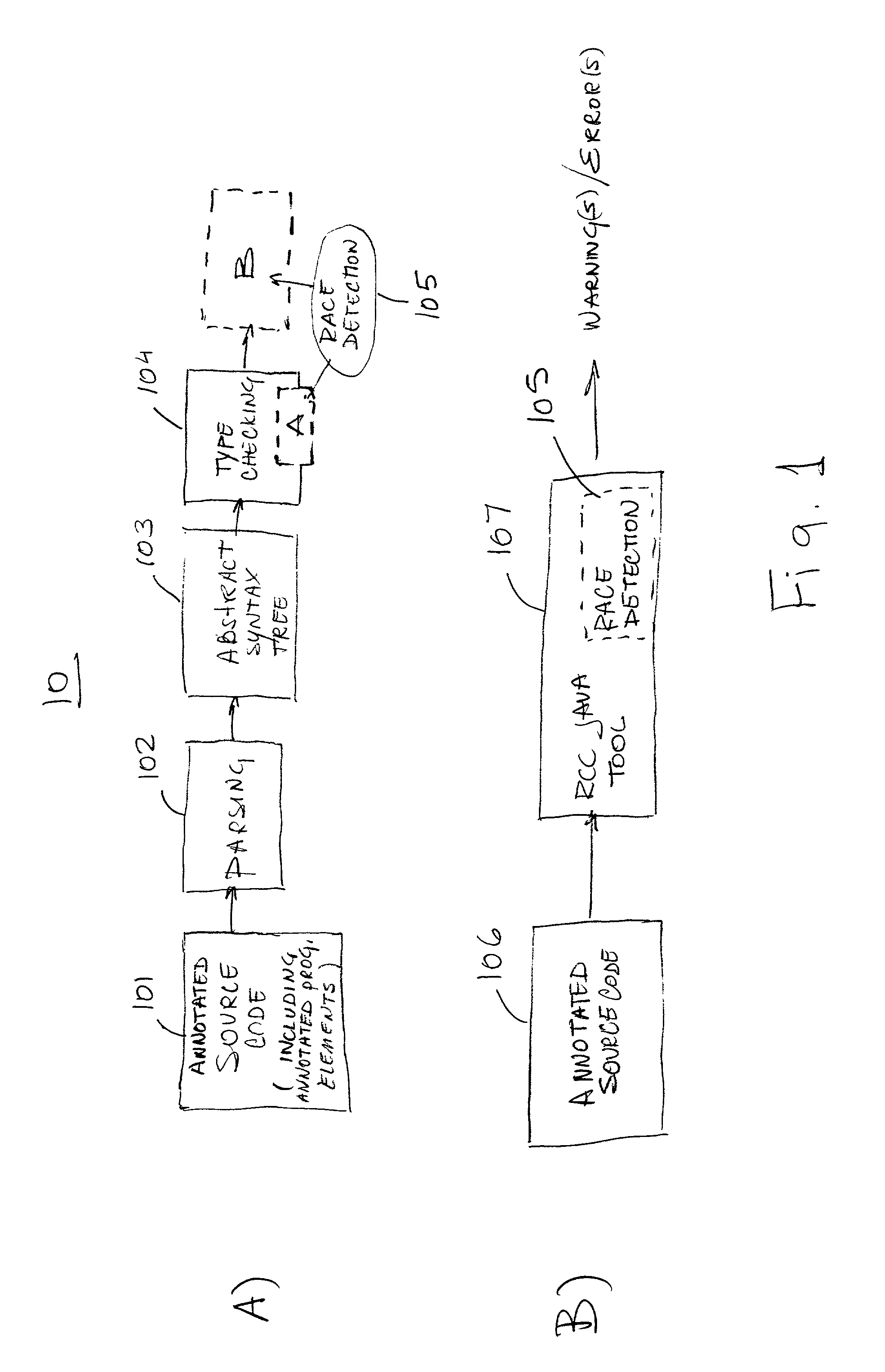
InactiveUS20020129306A1Ensuring validityValidity can be determinedError detection/correctionSoftware engineeringProgram analysisSource code
A method and apparatus are used in accordance with the present invention in concurrent program analysis for detecting potential race conditions such as data races in computer programs. A feature of the method and apparatus of the present invention is verifying annotations of addressable resources in a program. The present invention verifies annotations by checking if thread-local resources are indeed thread-local, and that thread-shared data spaces are not in fact thread-local. In accordance with the purpose of the invention, the method provides for detecting potential race conditions, such as data races, in a computer program. The computer program can spawn a plurality of threads that are capable of being executed concurrently. The method includes receiving a source code of the computer program. The source code includes an element annotated as either thread-local or thread-shared. The method also includes verifying the validity of the thread-local annotation if the element is annotated in the computer program as thread-local, wherein an invalid thread-local annotation may cause a race condition. The method can further include indicating a potential race condition if upon verifying the validity of the thread-local annotation it is determined that the element or a portion thereof is visible from more than one, rather than one and only one, of the plurality of threads. In further accordance with the purpose of the invention, the apparatus for concurrent program analysis includes means for receiving source code of the computer program. The source code includes an element annotated as either thread-local or thread-shared. The apparatus also includes means for type checking the source code; and means for thread-local checking located either inside or in series with the type checking means. The means for thread-local checking includes means for verifying the validity of the thread-local annotation if the element is annotated in the computer program as thread-local, where an invalid thread-local annotation may cause a race condition such as a data race. The apparatus can further include means for parsing the source code; and means for creating from the source code an abstract syntax tree. Accordingly, the present invention beneficially provides for a more effective concurrent program analysis.
Owner:VALTRUS INNOVATIONS LTD +1
Program verification apparatus and method, and signature system based on program verification
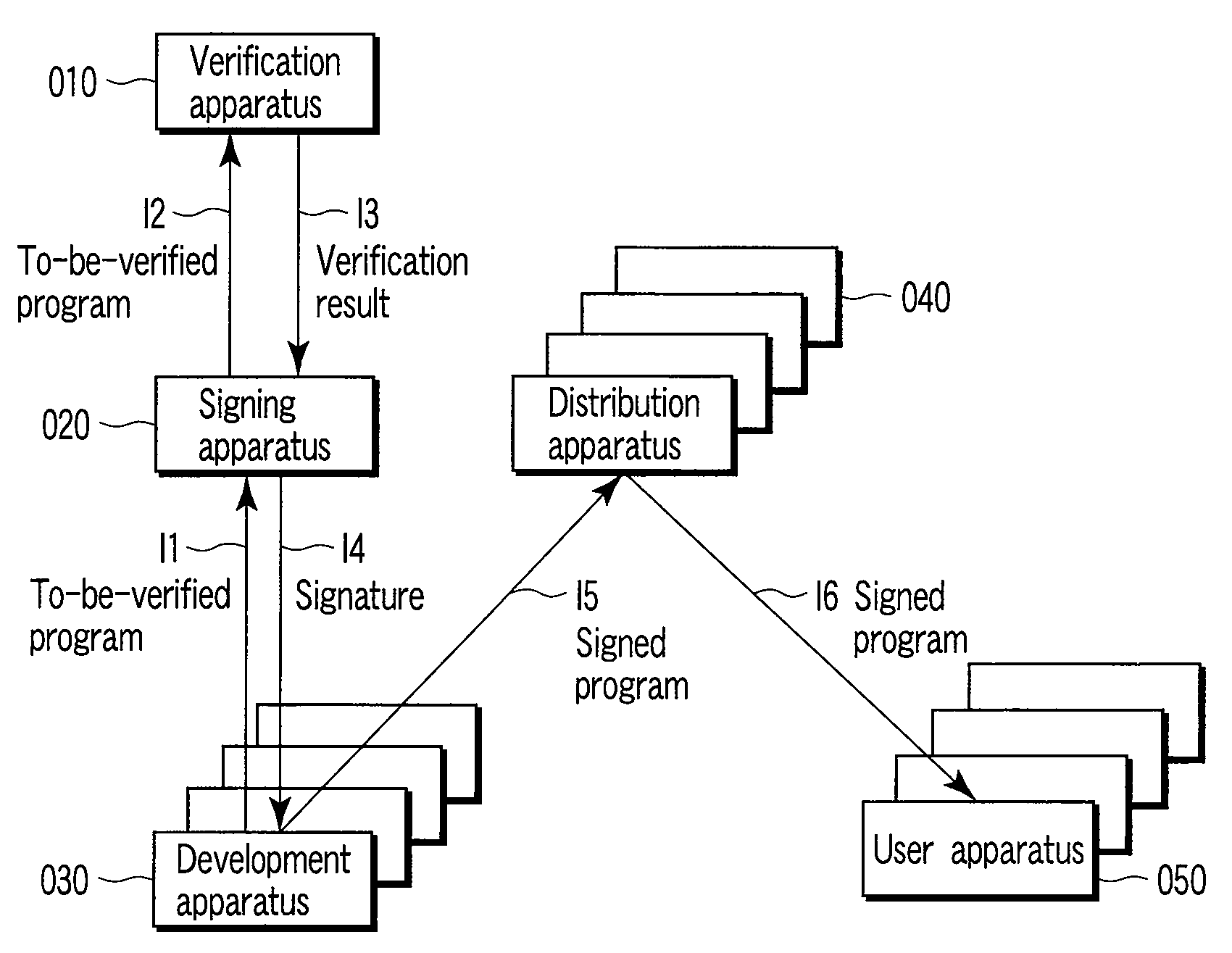
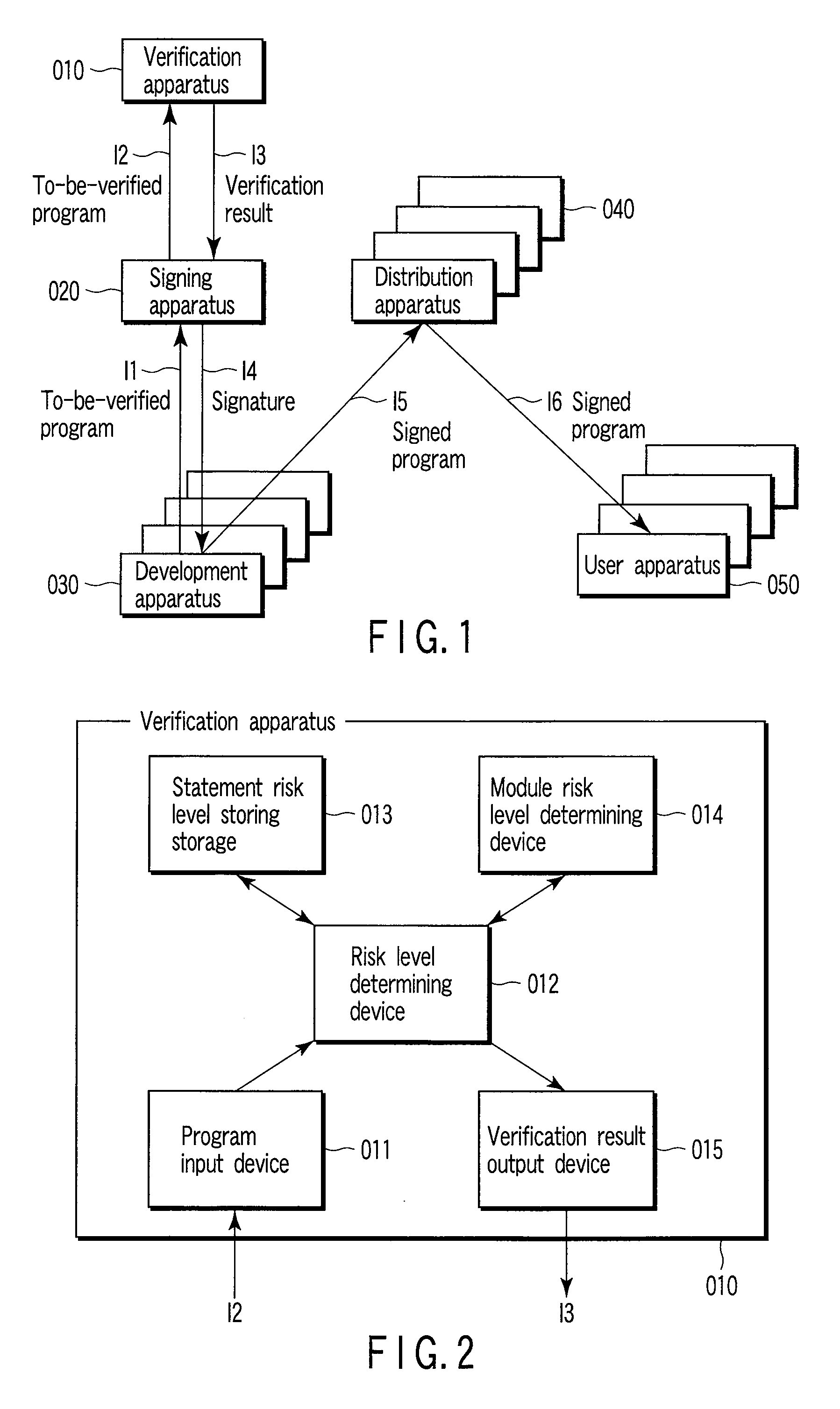
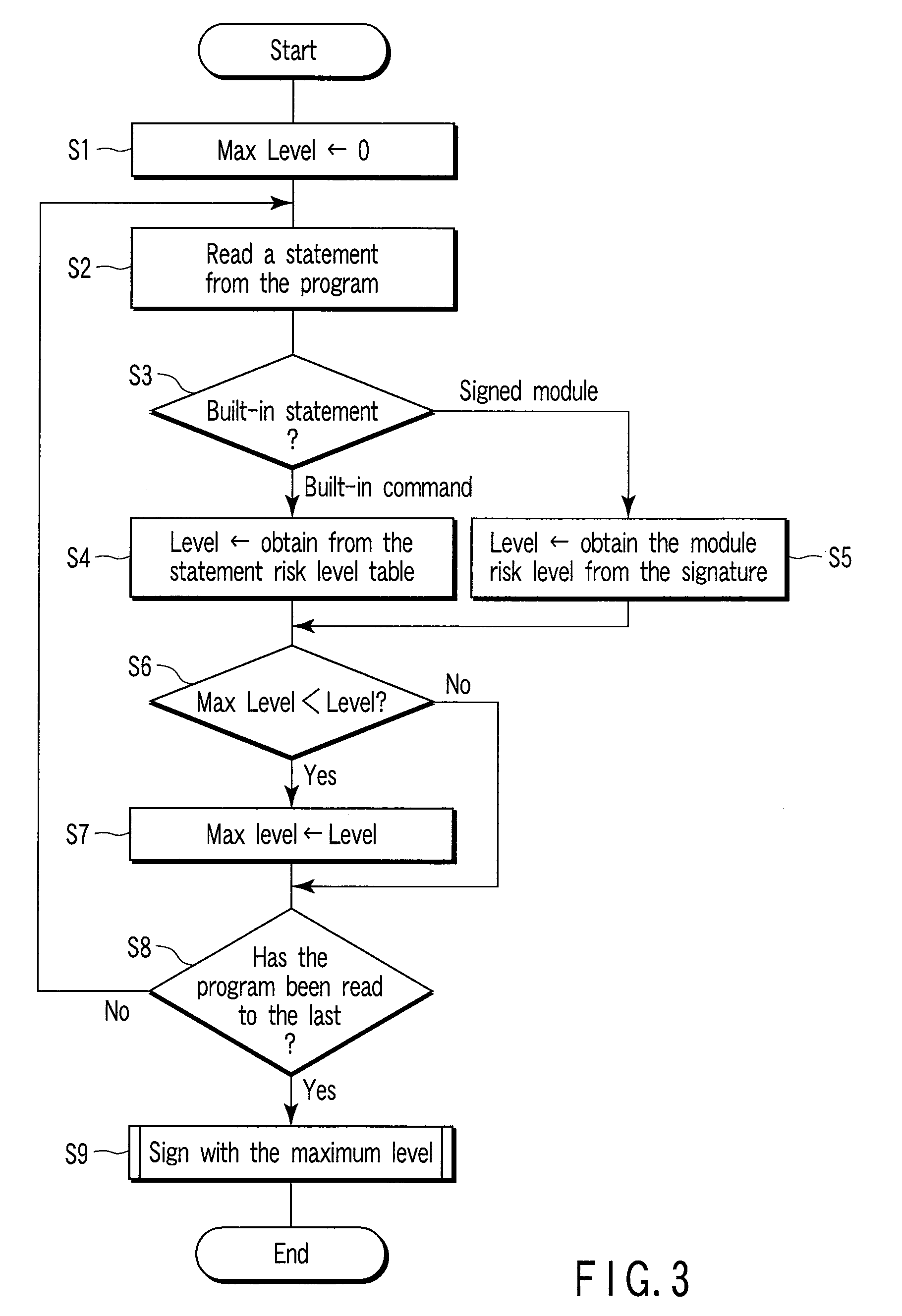
InactiveUS20080168533A1TransmissionProgram/content distribution protectionRisk levelProgram validation
A program verification apparatus includes a storing which stores a plurality of statements in correspondence with values of respective risk levels of the statements. Referring to a signature included in a signed module, a value indicating a risk level of the signed module is obtained. A to-be-verified program including a plurality of statements or signed modules is input to the apparatus. Values of first risk levels of the statements included in the to-be-verified program are determined by referring to the storing device. Values of second risk levels of the signed modules included in the to-be-verified program are also determined. Then, a maximum value of a risk level of the to-be-verified program is calculated from the values of the first risk levels and the values of the second risk levels. A verification result including the maximum value of the risk level is outputted accordingly.
Owner:KK TOSHIBA
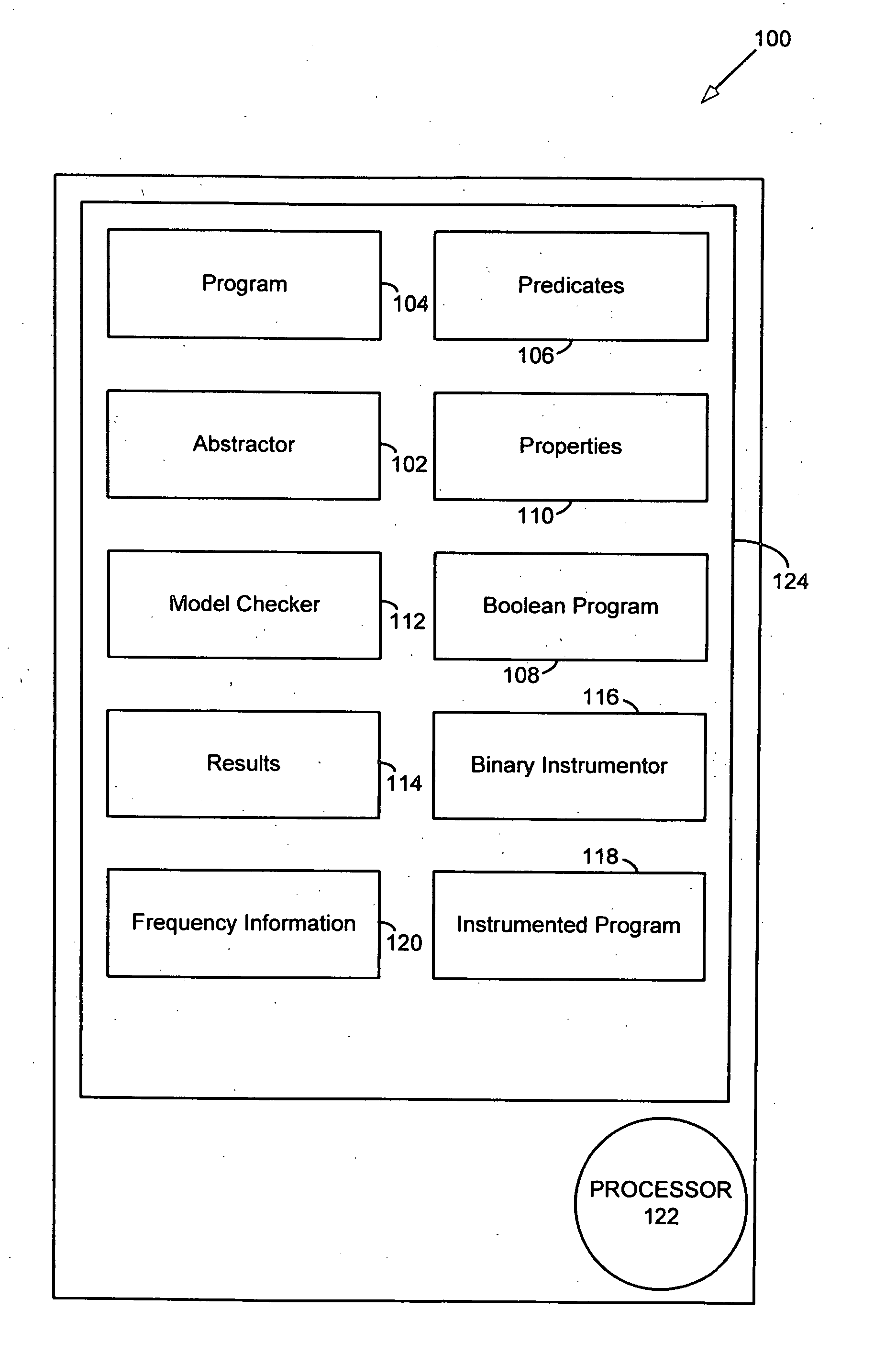
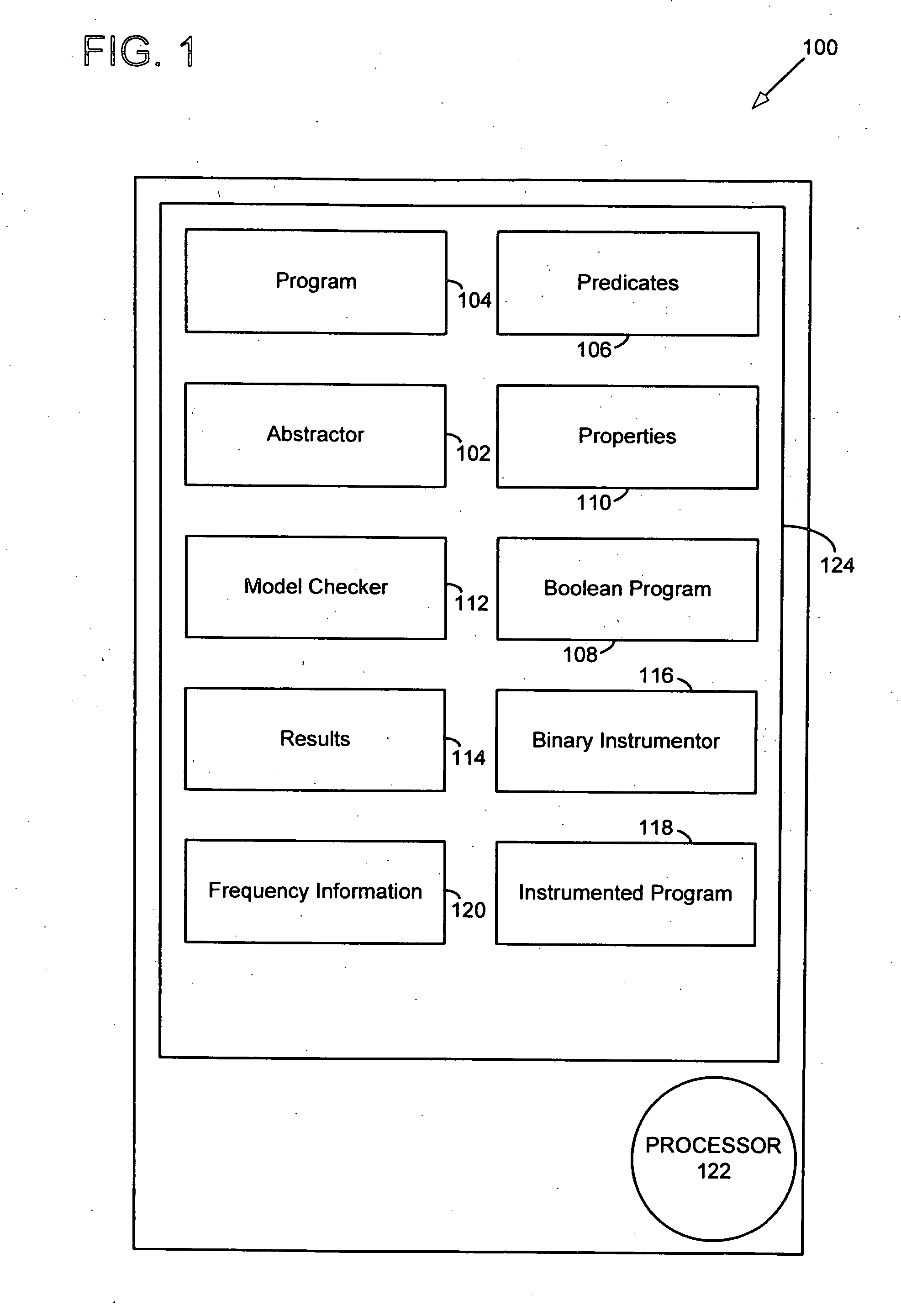
Using dynamic analysis to improve model checking
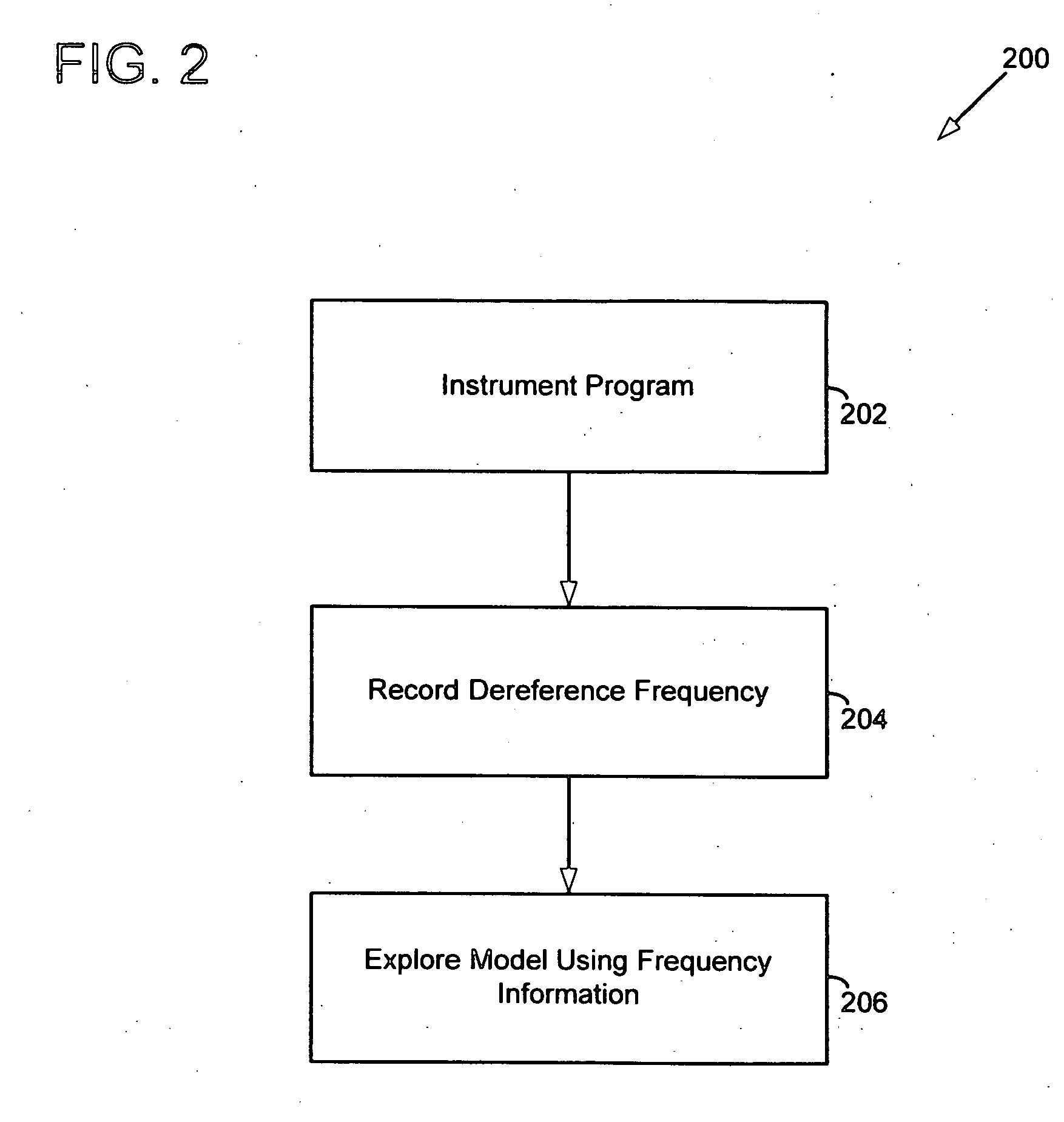
InactiveUS20070244942A1Error detection/correctionSpecific program execution arrangementsGeneral purposeProgram behavior
Model checking has been used to verify program behavior. However, exploration of the model is often impractical for many general purpose programs due to the complexity of an exploding state space. Instead, a program is instrumented with code that records pointer dereference information. The instrumented program is executed thereby recording pointer dereference frequency information. Then, a model of the program is explored using the pointer dereference frequency information to direct state space exploration of the model.
Owner:MICROSOFT TECH LICENSING LLC
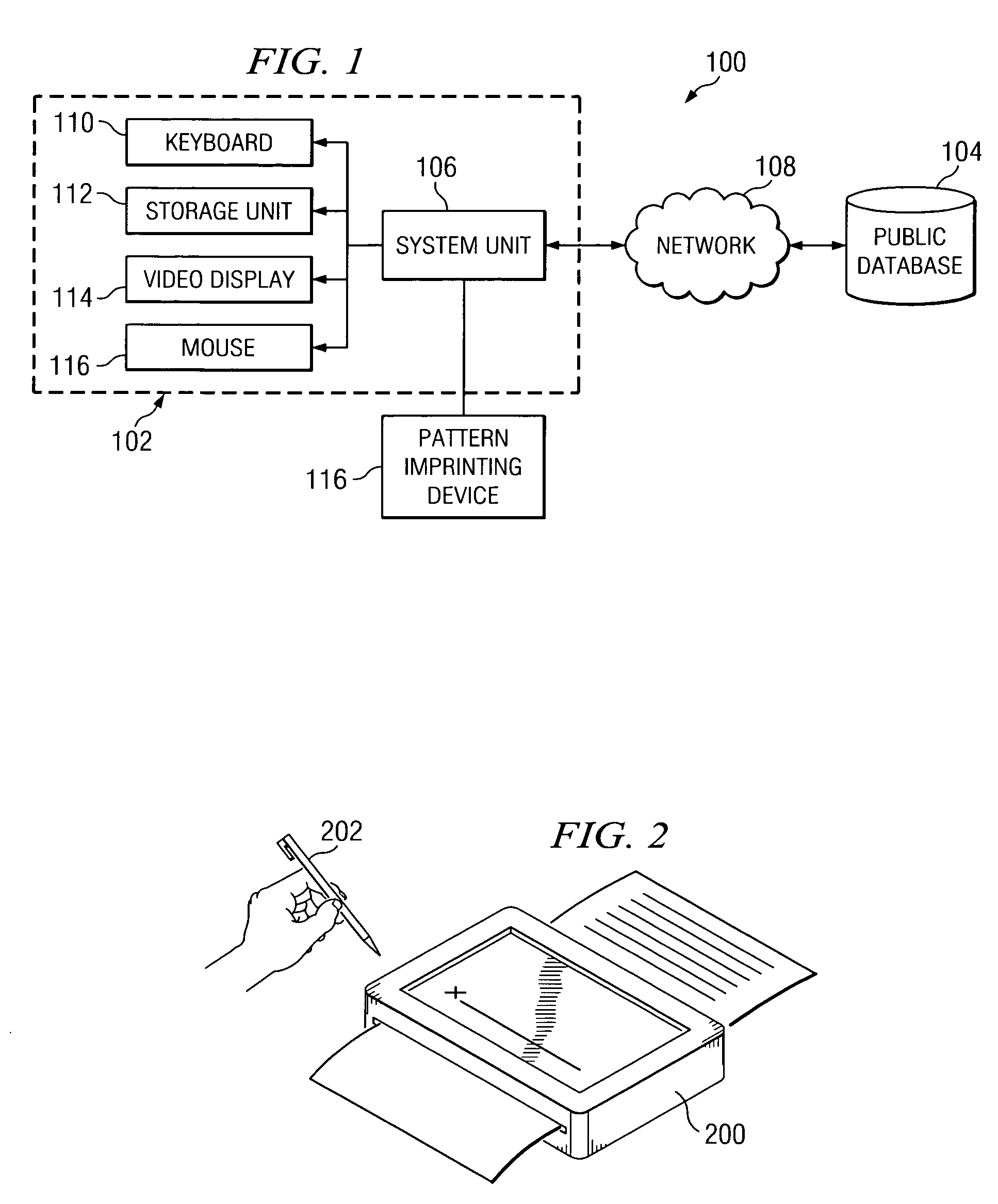
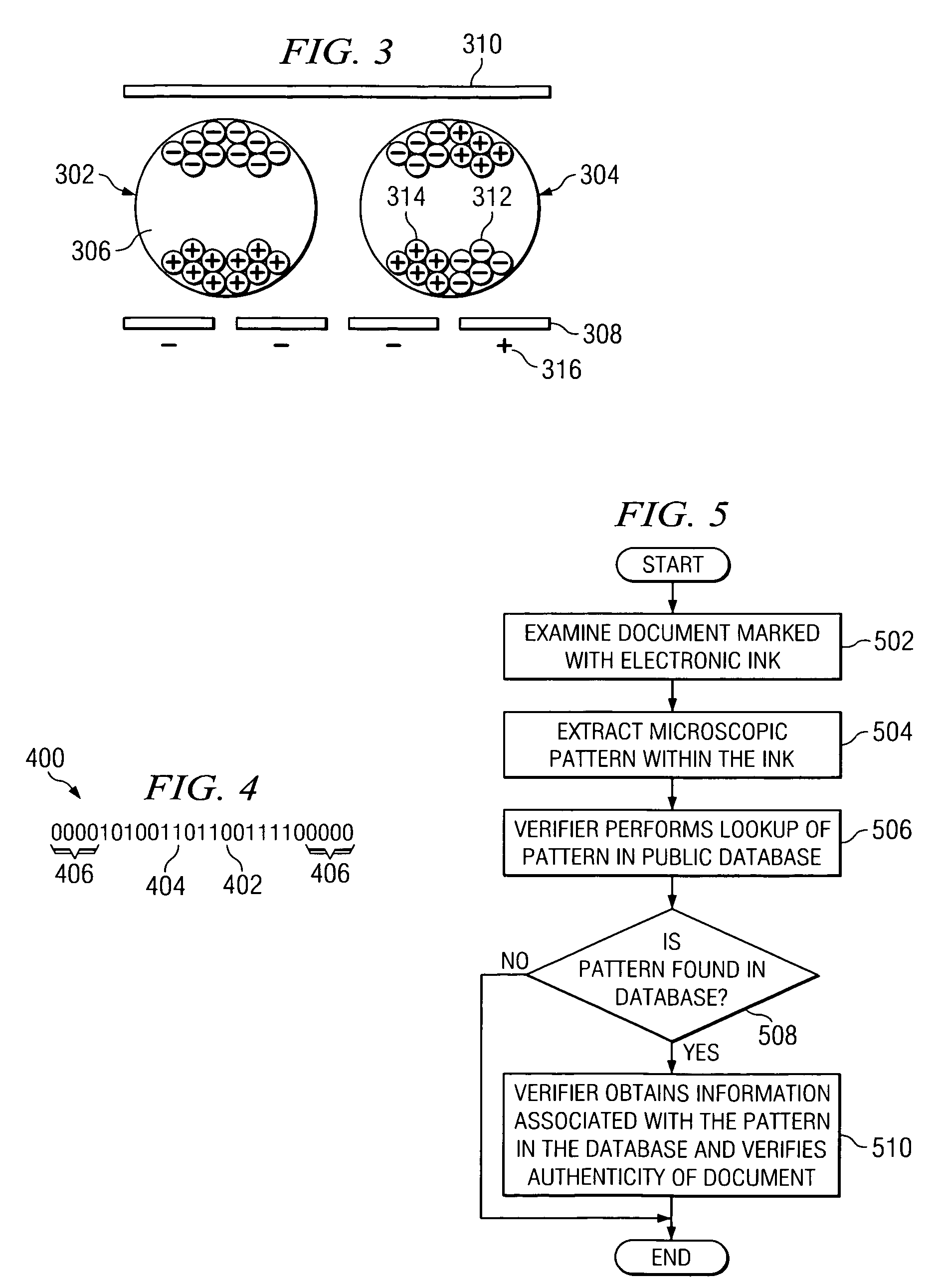
Mechanism for storing authenticity information about a written or printed document
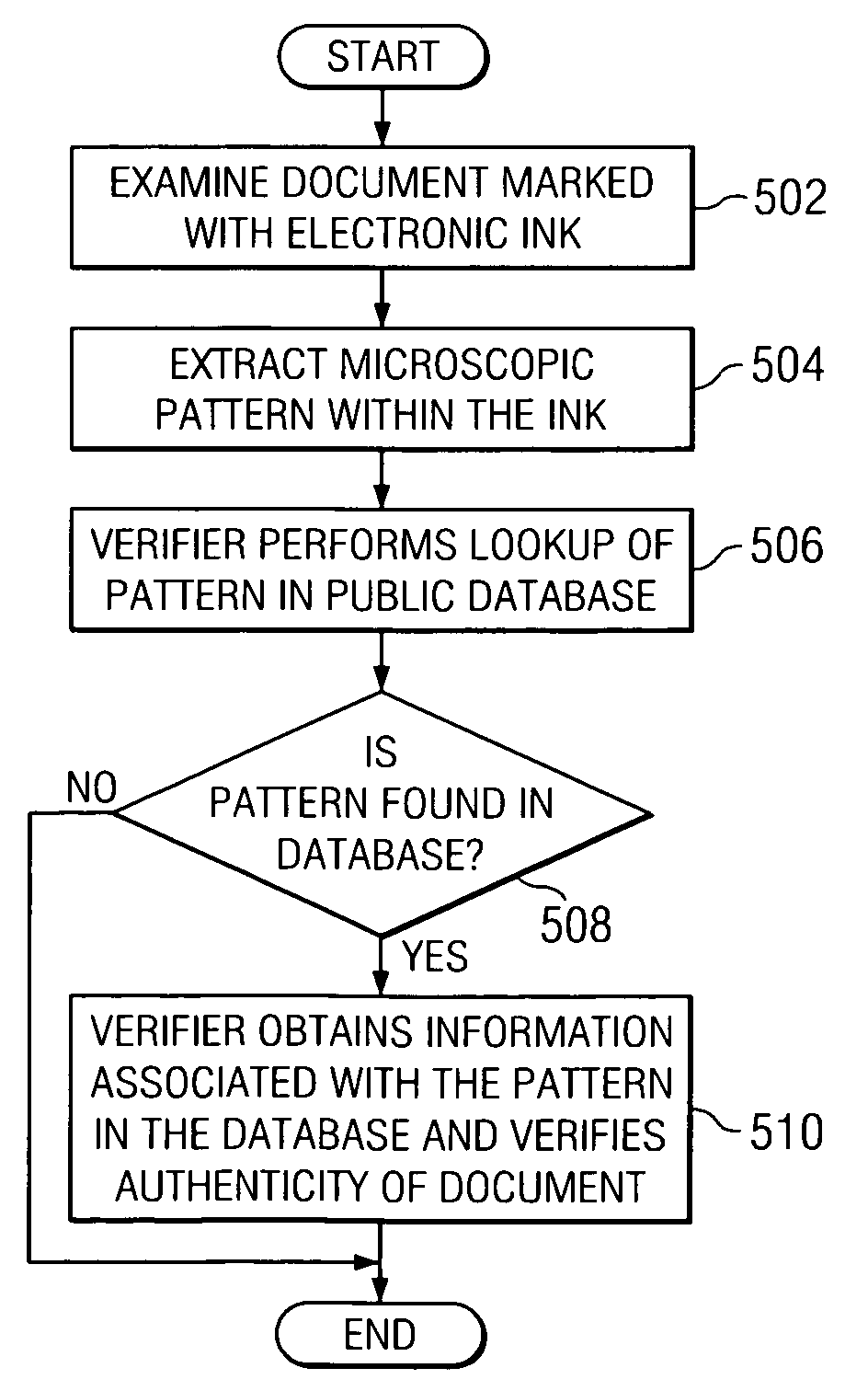
InactiveUS7357333B2Paper-money testing devicesCharacter and pattern recognitionMagnificationDocumentation
A mechanism for storing authenticity information about a written or printed document. This authenticity information may be stored in a publicly-accessible database. When a document patterned with electronic ink is to be verified, the verifier examines the electronic ink under magnification. The verifier locates start and end pattern markers within the ink, and extracts the pattern from the ink. Once the pattern is obtained, the verifier performs a lookup of the pattern in the database. If the pattern is found, the verifier obtains information associated with the pattern from the database. The verifier may then use this information to verify the authenticity of the document.
Owner:INT BUSINESS MASCH CORP
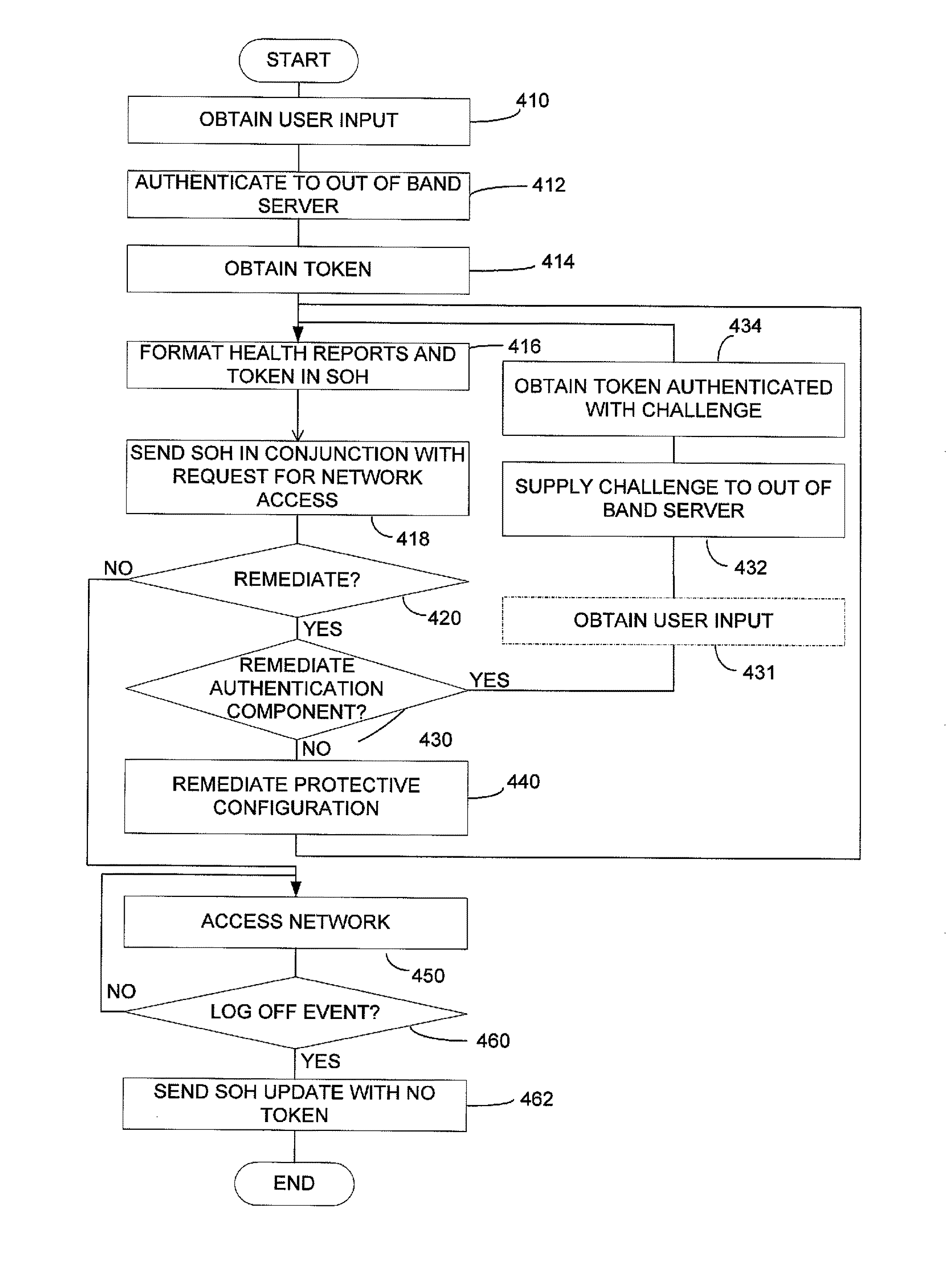
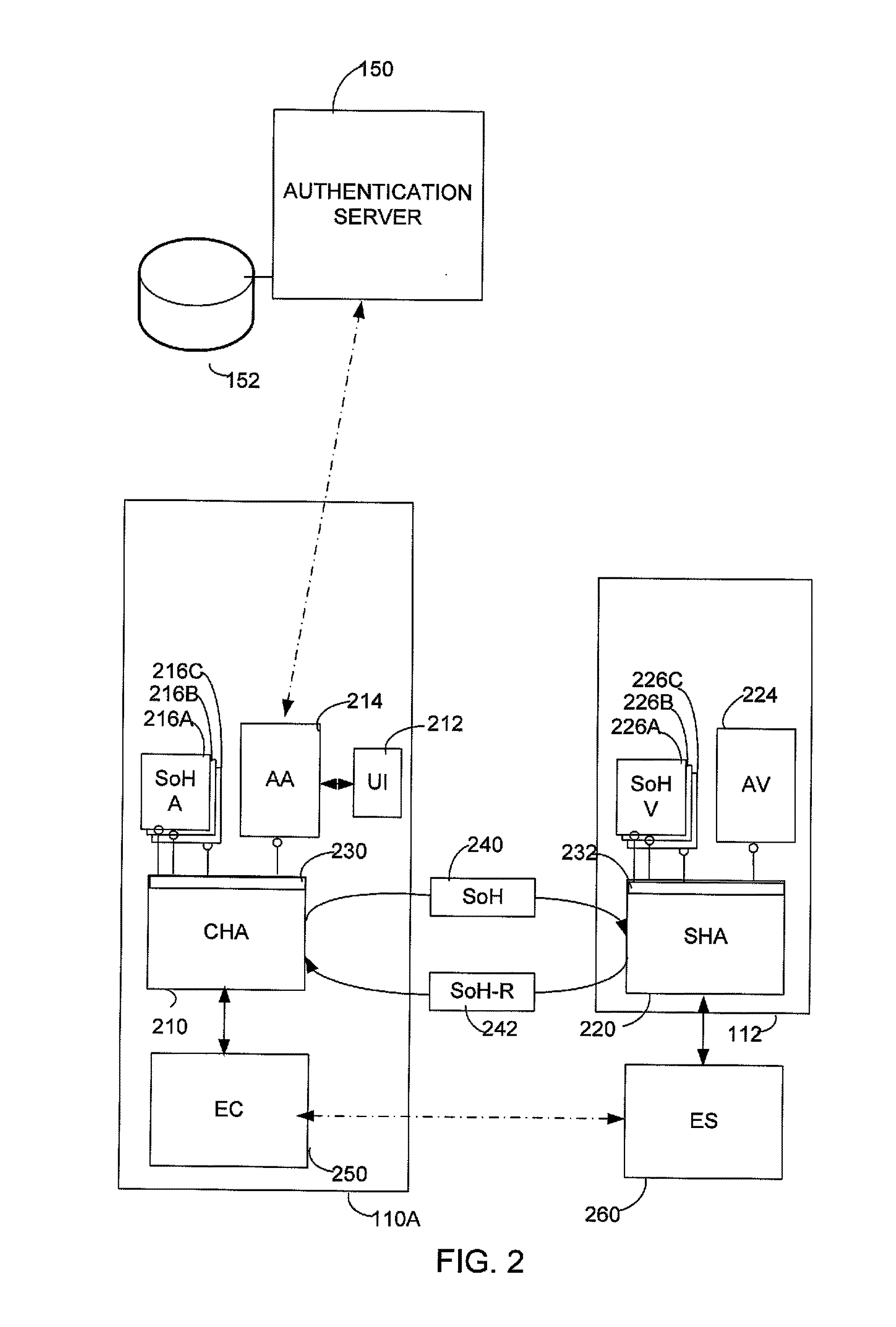
Authentication in a network using client health enforcement framework
ActiveUS9443084B2Optimize networkEasy to mergeDigital data processing detailsMultiple digital computer combinationsClient-sideVerified procedure
A network with authentication implemented using a client health enforcement framework. The framework is adapted to receive plug-ins on clients that generate health information. Corresponding plug-ins on a server validate that health information. Based on the results of validation, the server may instruct the client to remediate or may authorize an underlying access enforcement mechanism to allow access. A client plug-in that generates authentication information formatted as a statement of health may be incorporated into such a framework. Similarly, on the server, a validator to determine, based on the authentication information, whether the client should be granted network access can be incorporated into the framework. Authentication can be simply applied or modified by changing the plug-ins, while relying on the framework to interface with an enforcement mechanism. Functions of the health enforcement framework can be leveraged to provide authentication-based functionality, such as revoking authorized access after a period of user inactivity or in response to a user command.
Owner:MICROSOFT TECH LICENSING LLC
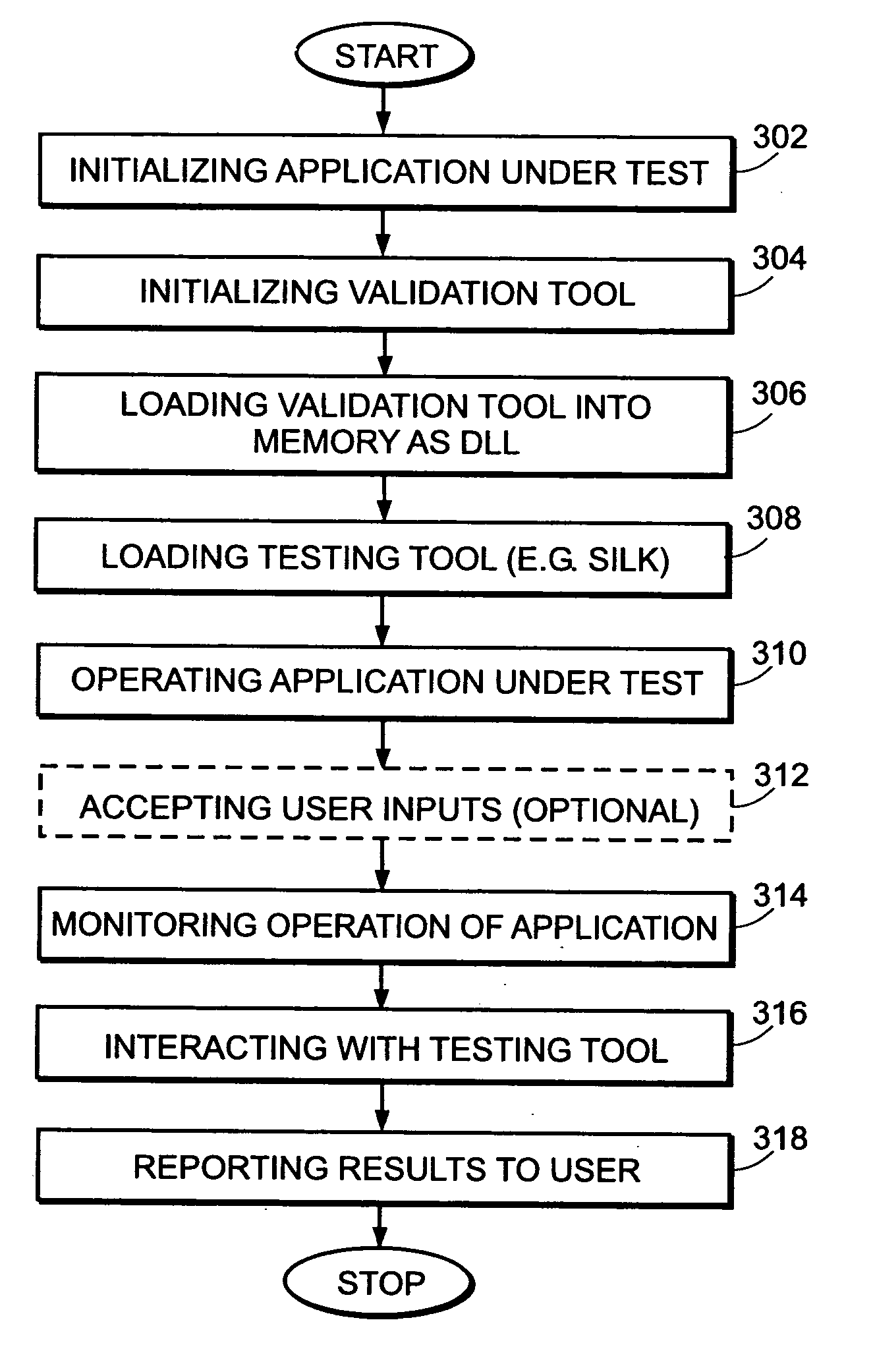
System and methods for client and template validation
InactiveUS20050289517A1Convenient verificationError detection/correctionSpecific program execution arrangementsClient-sideVerified procedure
A system and method for validating user developed applications operating in conjunction with distributed workforce collaboration systems is provided. The invention allows a user, such as a quality control engineer, to validate front and back end data as well as an application under test without requiring that the user be adept at computer programming. The validation tool runs in memory used by the application under test as a dynamic link library (DLL). As a result, the validator can monitor all actions of the application under test without adversely impacting normal operation of the application under test.
Owner:IBM CORP
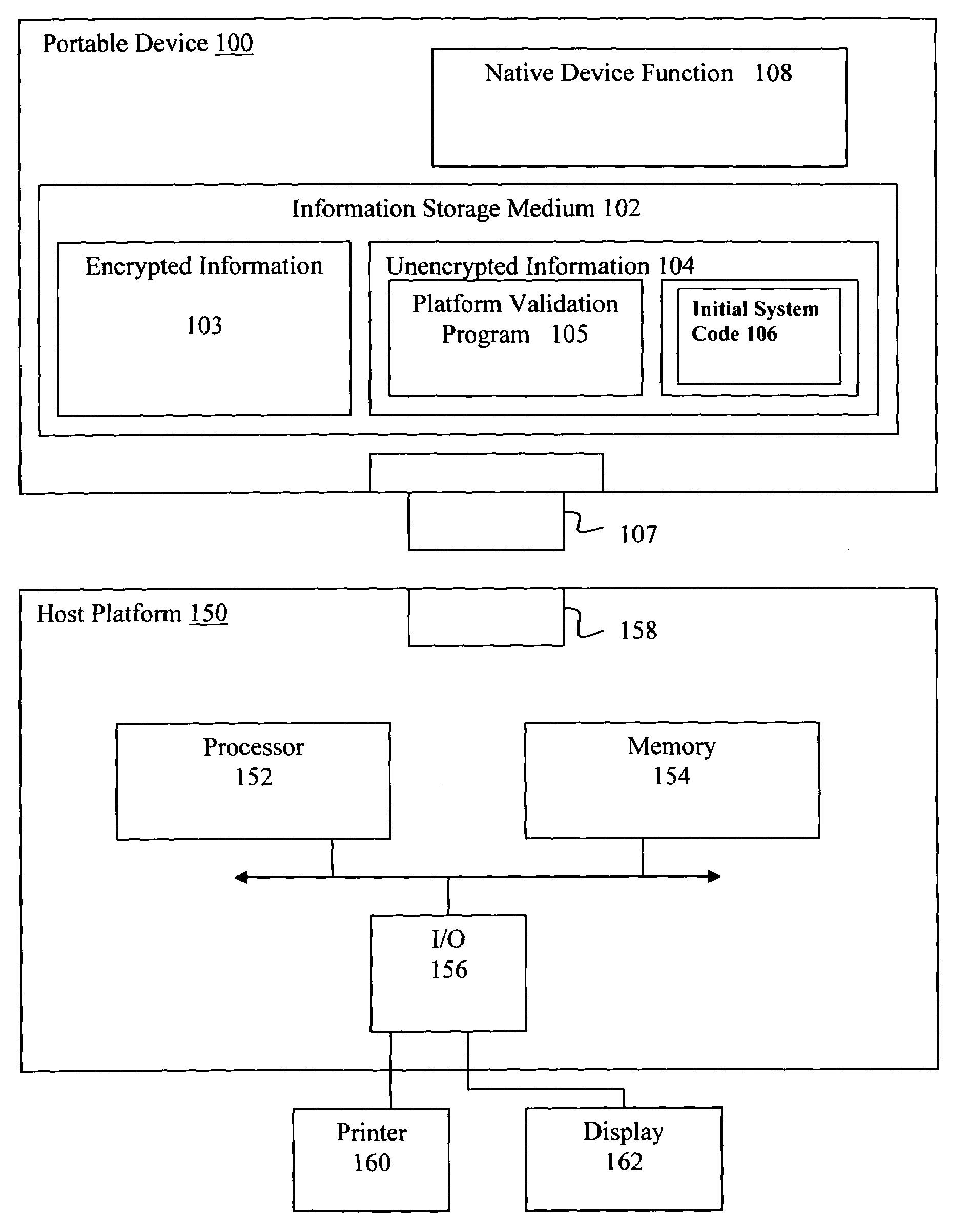
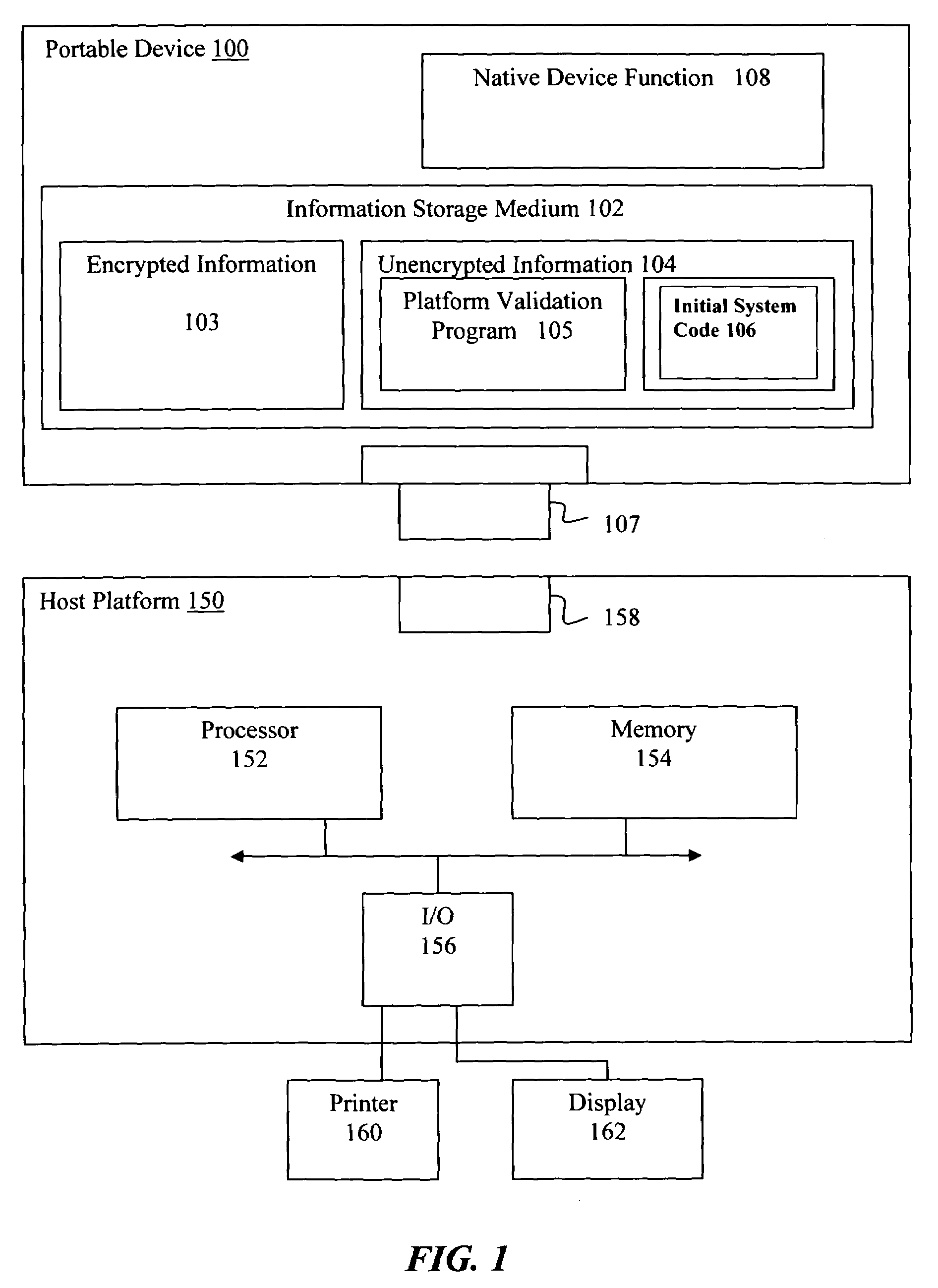
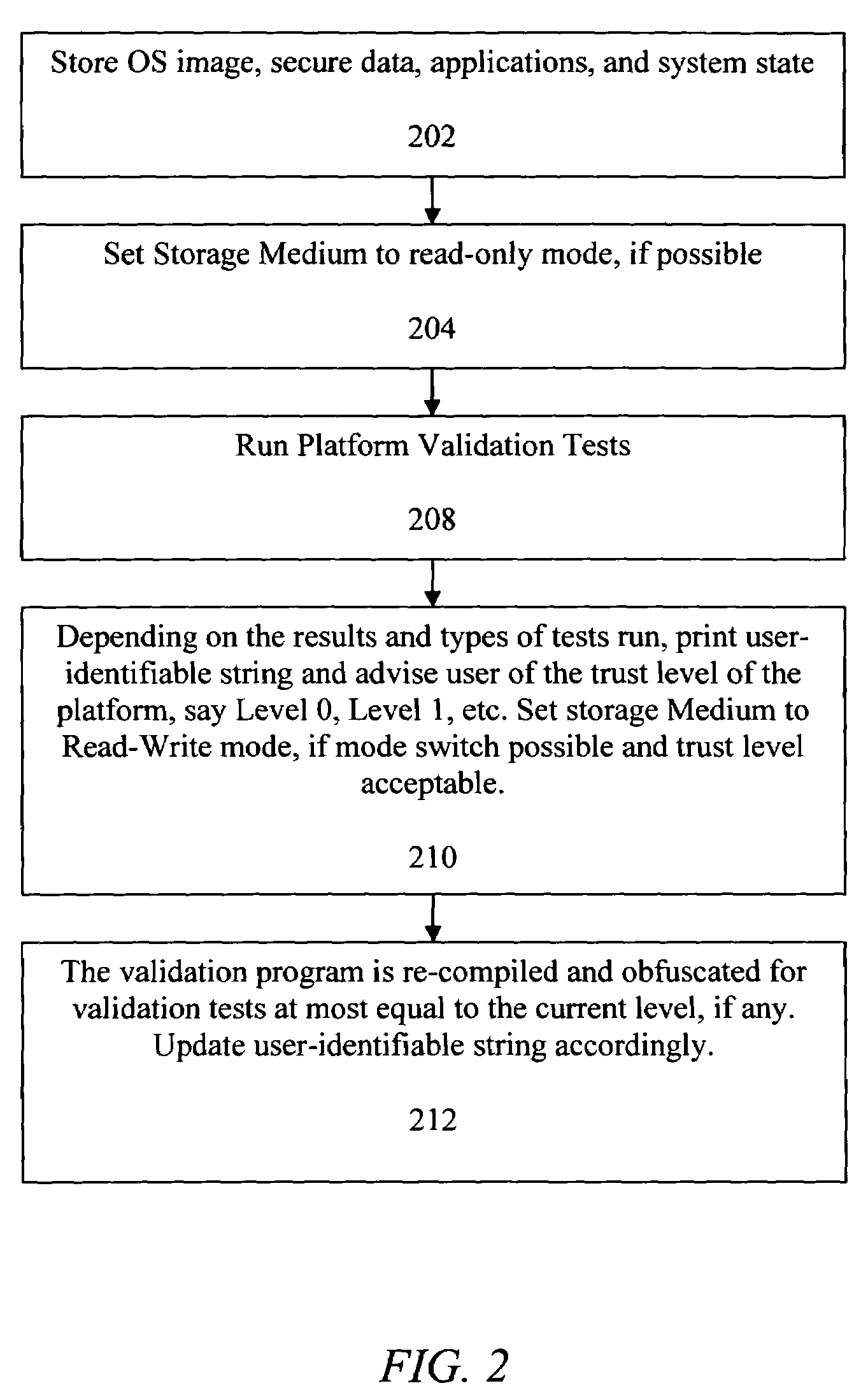
System and method for validating a computer platform when booting from an external device
ActiveUS7743422B2Memory loss protectionDigital data processing detailsInformation processingOperational system
Owner:TWITTER INC
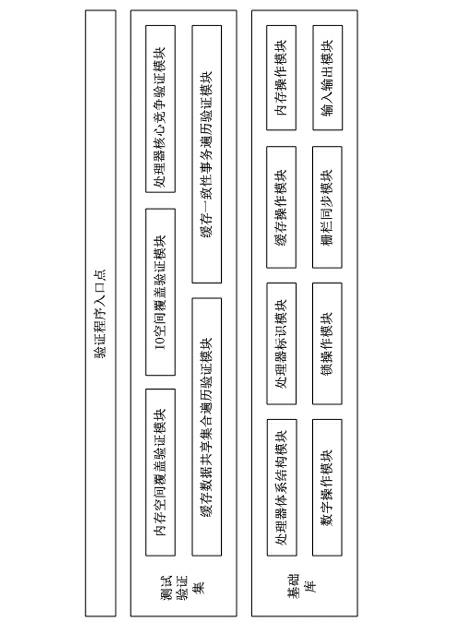
Correctness verifying method of cache consistency protocol
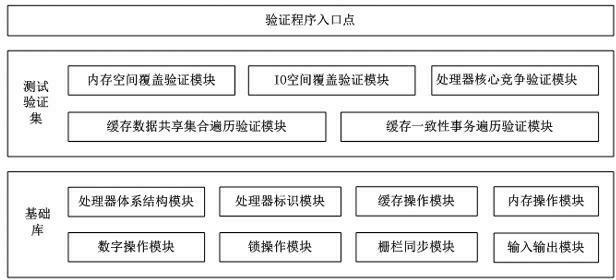
ActiveCN102681937AMake up for efficiencyMake up for poor verification coverageDigital computer detailsMultiprogramming arrangementsOperational systemTerm memory
The invention provides a correctness verifying method of a cache consistency protocol. After a computer enters an operating system, the complexity of a core and the application of the operating system is higher; the action of a processor is not easy to control accurately; therefore, in order to keep verification correctness, a verifying program for the cache consistency protocol is necessary to embed in a systematic procedure; the program is embedded in a BIOS (basic input / output system) code; after the initialization of a memory subsystem is completed at the initialization initial stage of the system, the verifying program is started to be executed; the verifying program needs to be capable of accurately controlling actions of each processor of the system, supports a user to select a verification item to be particularly executed, and feeds back a verification result to the user; by using the method, the verification of the correctness of the cache consistency protocol is realized at a system level; all application scenes of a real system can be completely covered; the disadvantages that a conventional verifying method based on an analog way is low in efficiency and poor in verification coverage rate are made up; the design period and the verifying period of an inter-domain cache consistency chip of the processor can be shortened; the one-time taping-out mission success rate of the chip can be guaranteed effectively; and therefore, the correctness verifying method has an extremely wide development prospect and an extremely high technical value.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com