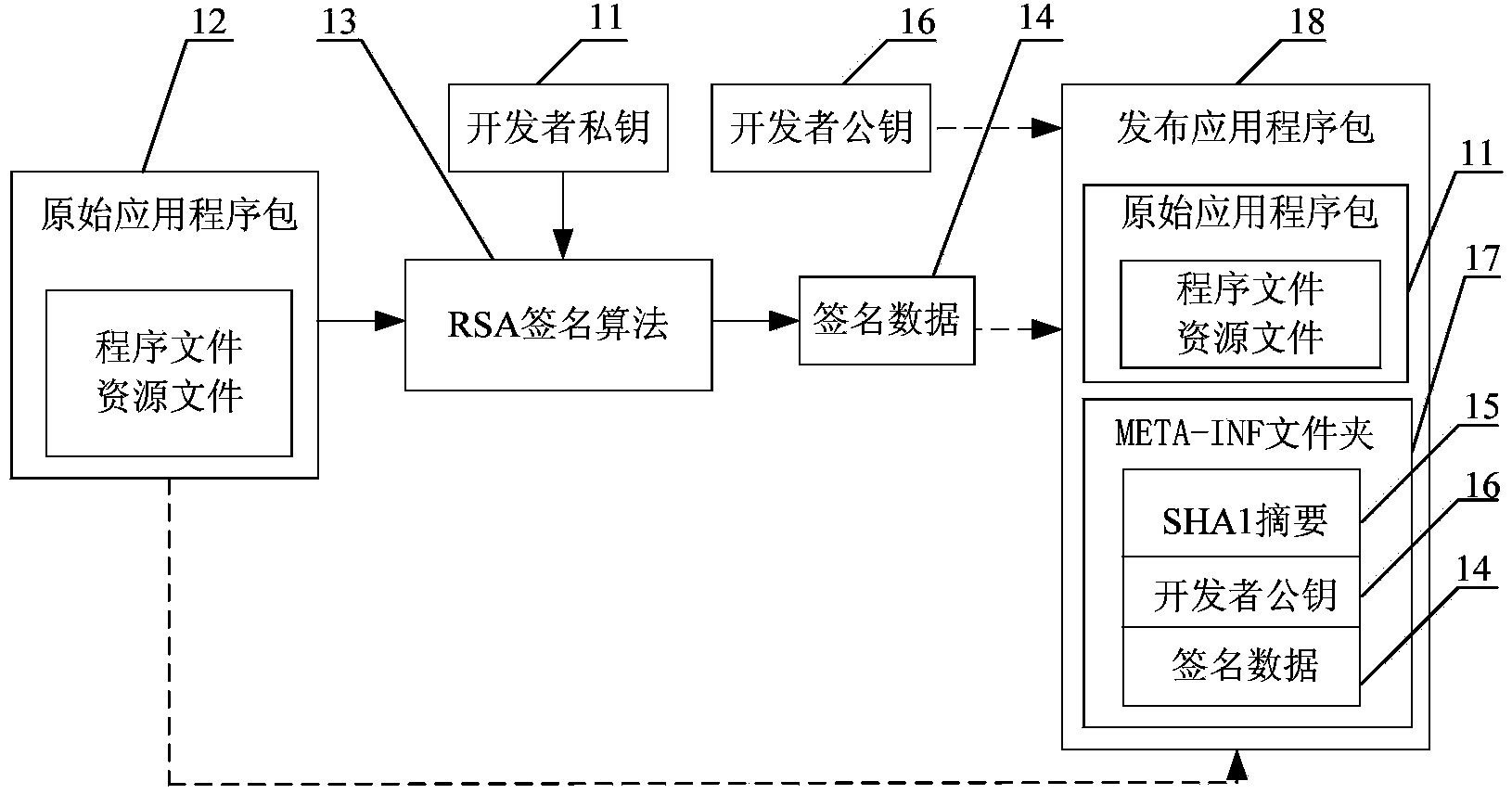
Installing verification method for intelligent terminal application program and system
An application program and smart terminal technology, applied in computer security devices, instruments, electrical digital data processing, etc., can solve problems such as the inability to effectively prevent the installation of illegal application programs, to protect interests, prevent the installation of illegal application programs, and prevent Effects of hacking and dissemination
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
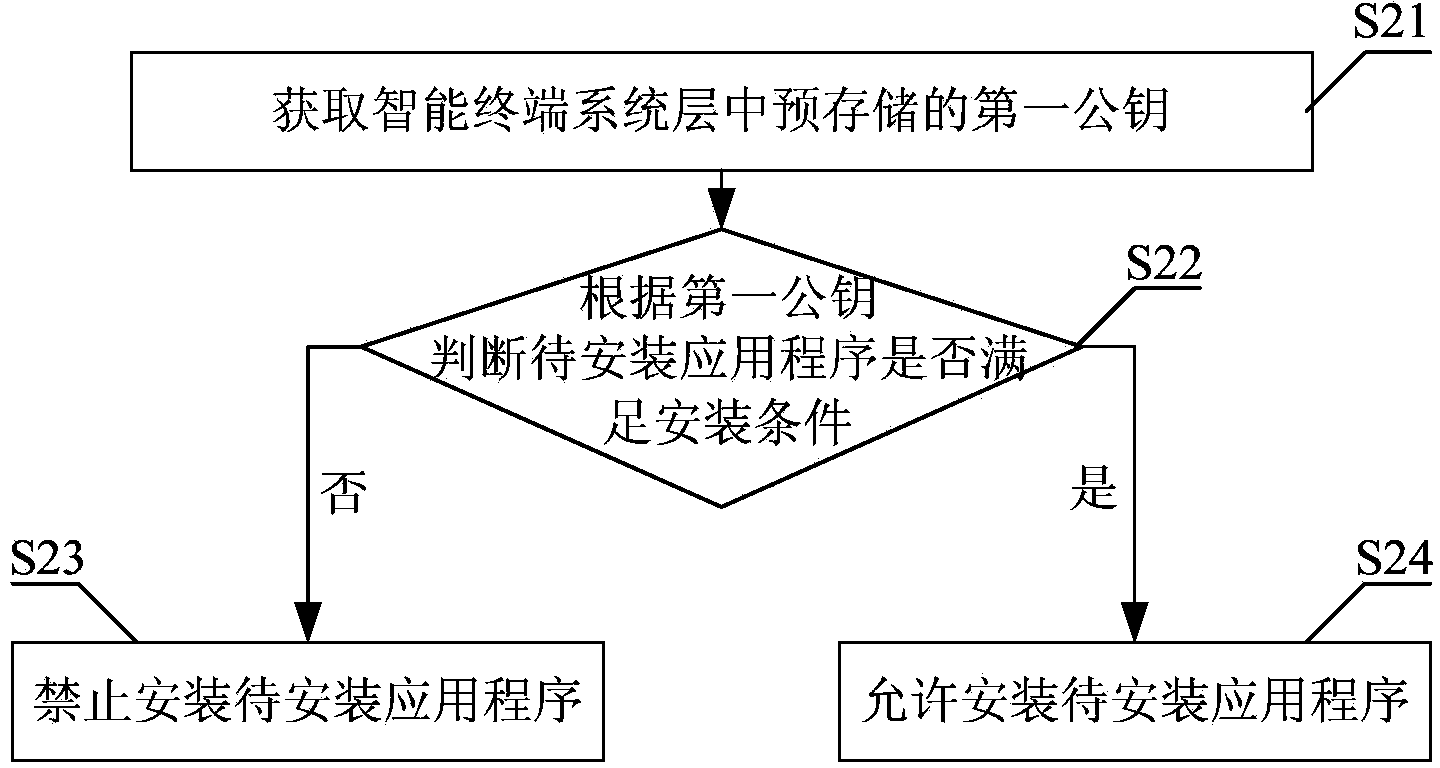
[0085] figure 2 A schematic flowchart of the method for verifying the installation of smart terminal applications provided by Embodiment 1 of the present invention is given.
[0086] Such as figure 2 The installation verification method of the smart terminal application program provided by the first embodiment includes the following steps:
[0087] Step S21, obtaining the first public key pre-stored in the system layer of the smart terminal;
[0088] In this step, the obtained first public key is pre-stored in the system layer and used to determine whether the application to be installed meets the installation conditions.
[0089] Step S22, judge whether the application to be installed satisfies the installation condition according to the first public key, if not, execute step S23, prohibit installation of the application to be installed; if yes, execute step S24, allow installation of the application to be installed.
[0090] The installation verification method of the s...
Embodiment 2
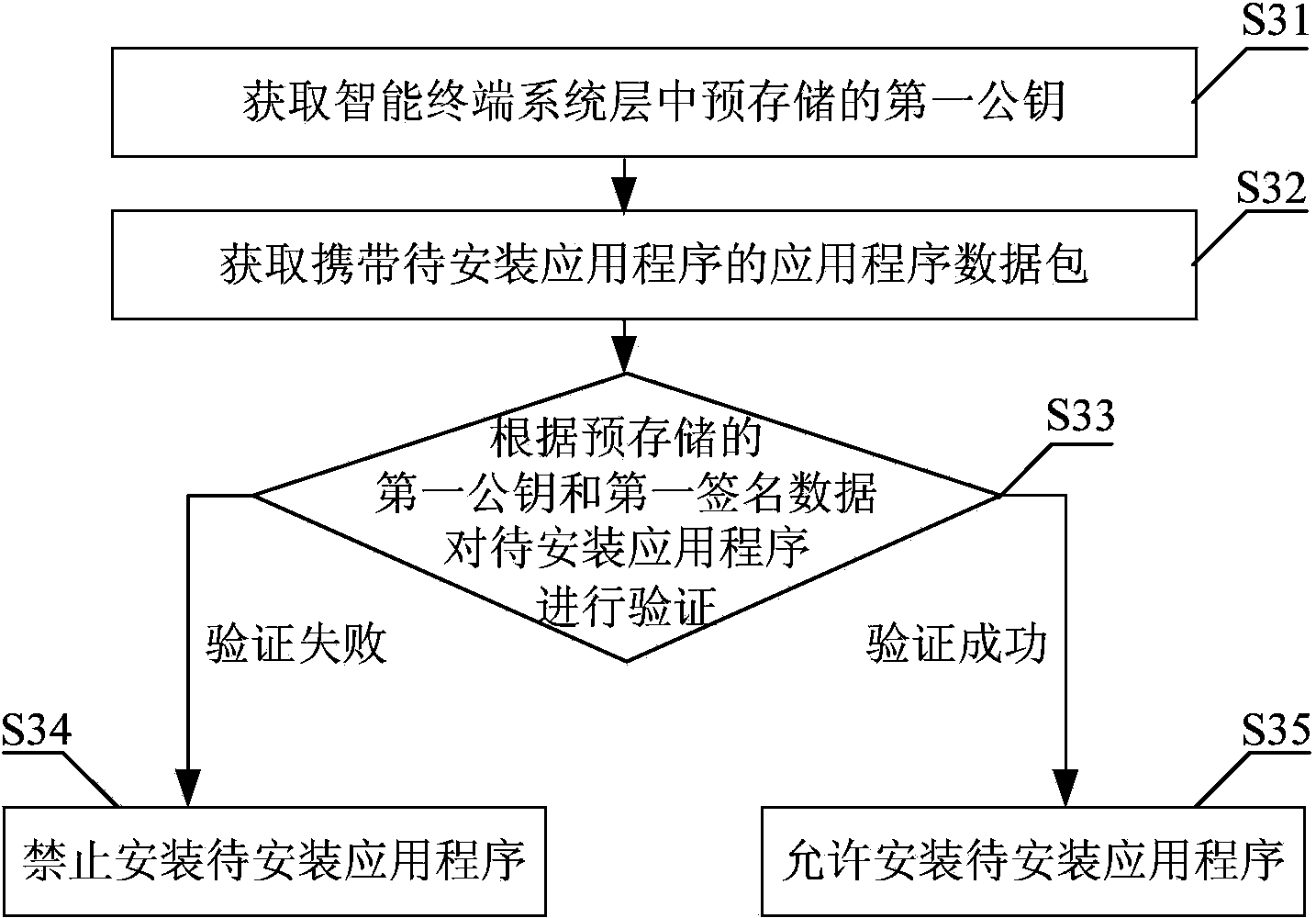
[0092] image 3 A schematic flow chart of the method for verifying the installation of smart terminal applications provided by Embodiment 2 of the present invention is given.
[0093] Such as image 3 As shown, the installation verification method of the smart terminal application program provided by Embodiment 2 of the present invention includes the following steps:
[0094] Step S31, obtaining the first public key pre-stored in the system layer of the smart terminal;
[0095] In this step, the obtained first public key is pre-stored in the system layer and used to determine whether the application to be installed meets the installation conditions.
[0096] Step S32, obtaining an application data packet carrying an application to be installed;
[0097] In this step, besides the application program to be installed, the obtained application data package also carries the first signature data obtained by using the first private key, and the signer needs to keep the first priva...
Embodiment 3
[0106] Figure 6 A schematic flow chart of the method for verifying the installation of smart terminal applications provided by Embodiment 3 of the present invention is given.
[0107] Such as Figure 6 As shown, the installation verification method of the smart terminal application program provided by Embodiment 3 of the present invention includes the following steps:
[0108] Step S61, obtaining the first public key pre-stored in the system layer of the smart terminal;
[0109] In this step, the obtained first public key is pre-stored in the system layer and used to determine whether the application to be installed meets the installation conditions.
[0110] Step S62, obtaining an application data packet carrying an application to be installed;
[0111] In this step, in addition to the application to be installed, the obtained application data package also carries the second signature data and the application public key obtained by using the first private key, and the sig...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com