Method and device for installing application software
A technology of application software and installation method, which is applied to computer security devices, program control devices, instruments, etc., and can solve problems such as the inability to confirm malicious modification of third-party software installation packages
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
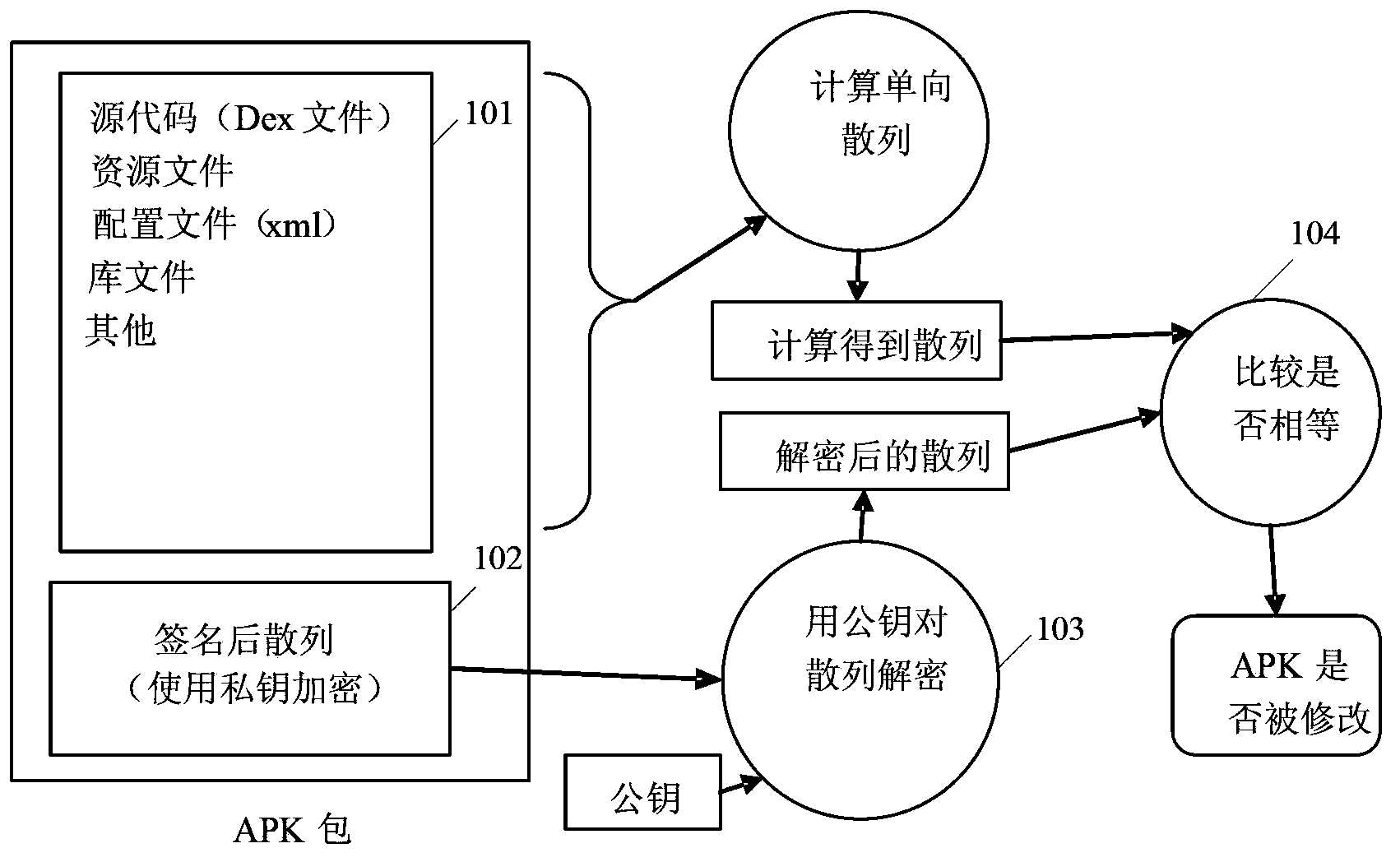
Image
Examples
Embodiment 1
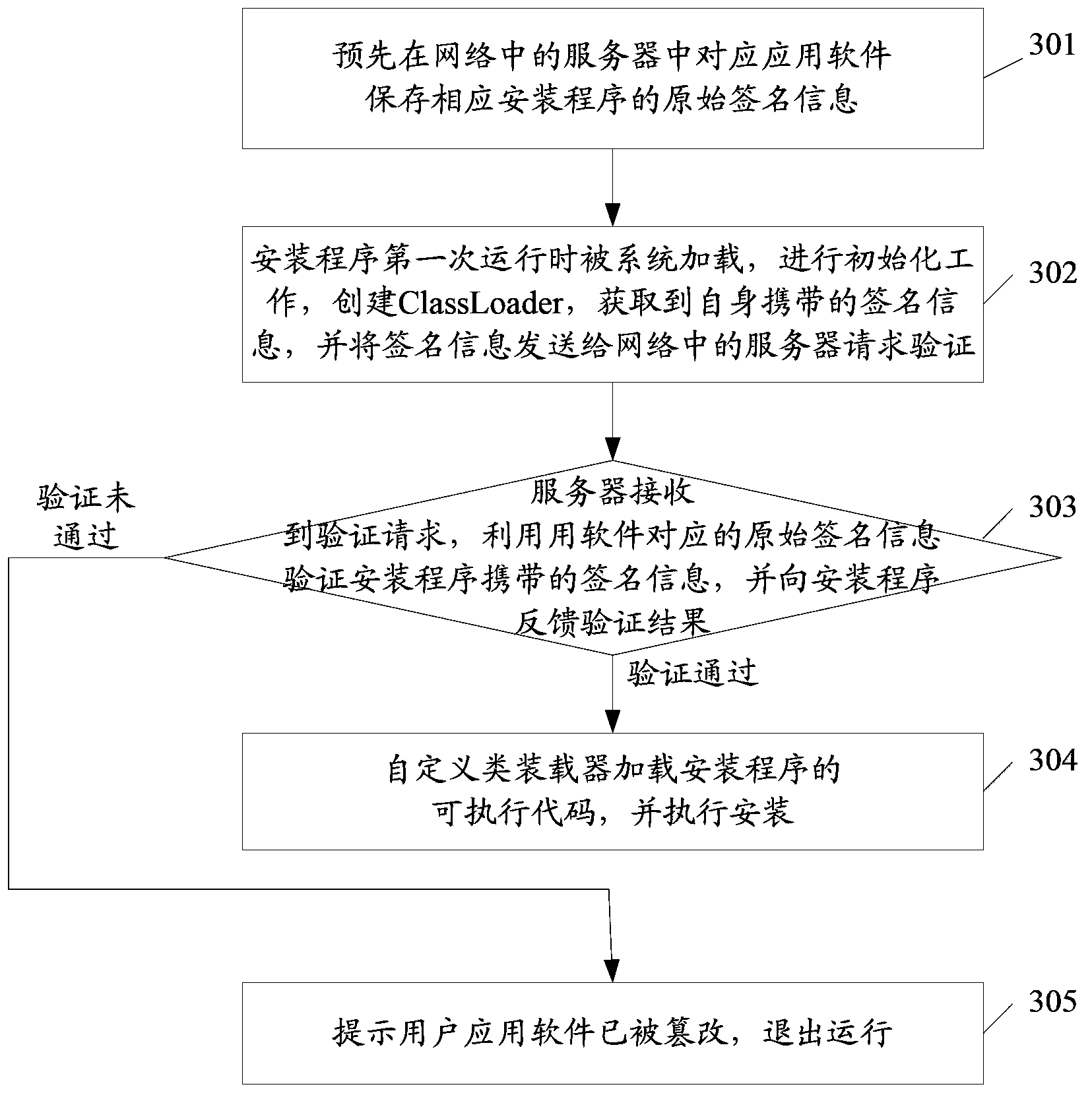
[0078] In this embodiment, processing is performed from the perspective of an installation program to implement the installation method of this application, and the method of this embodiment is a specific implementation in an accessible network environment.
[0079] image 3 This is a specific flowchart of the installation method in the first embodiment of this application. Such as image 3 As shown, the method includes:
[0080] Step 301: Pre-store the original signature information of the corresponding installation program in the server on the network corresponding to the application software.
[0081] In this embodiment, the original signature information is stored in a server on the network to isolate it from the installation program. When the public key is used to verify the signature information, if the public key is encrypted, the encryption algorithm of the public key can also be stored in the server in the network, and the public key cannot be obtained from the server.
[00...
Embodiment 2
[0092] In this embodiment, processing is also performed from the perspective of an installation program to implement the installation method of this application, and the method of this embodiment can be specifically implemented in an inaccessible network environment.
[0093] Figure 4 This is a specific flowchart of the installation method in the second embodiment of this application. Such as Figure 4 As shown, the method includes:
[0094] Step 401: Pre-store the original signature information of the corresponding installation program corresponding to the application software in the static library.
[0095] In this embodiment, the original signature information is stored in a static library to isolate it from the installation program. When the public key is used for signature information verification, if the public key is encrypted, the encryption algorithm of the public key can also be stored in the static library, and the public key cannot be obtained from the static library. ...
Embodiment 3
[0108] Figure 5 This is a specific flowchart of the installation method in the third embodiment of this application. Such as Figure 5 As shown, the method includes:
[0109] Step 501: Pre-store the original signature information of the corresponding installation program in the local database of the Android system corresponding to the application software.
[0110] In this embodiment, the original signature information is stored in the local database of the Android system to isolate it from the installation program.
[0111] When installing the application software, perform the following operations:
[0112] Step 502: The Android system parses the installation program, and obtains signature information carried by the installation program.
[0113] Step 503: The Android system prompts the application signing certificate information (namely signature information) on the application installation interface. The user chooses to trust the certificate or not to trust the certificate accordin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com