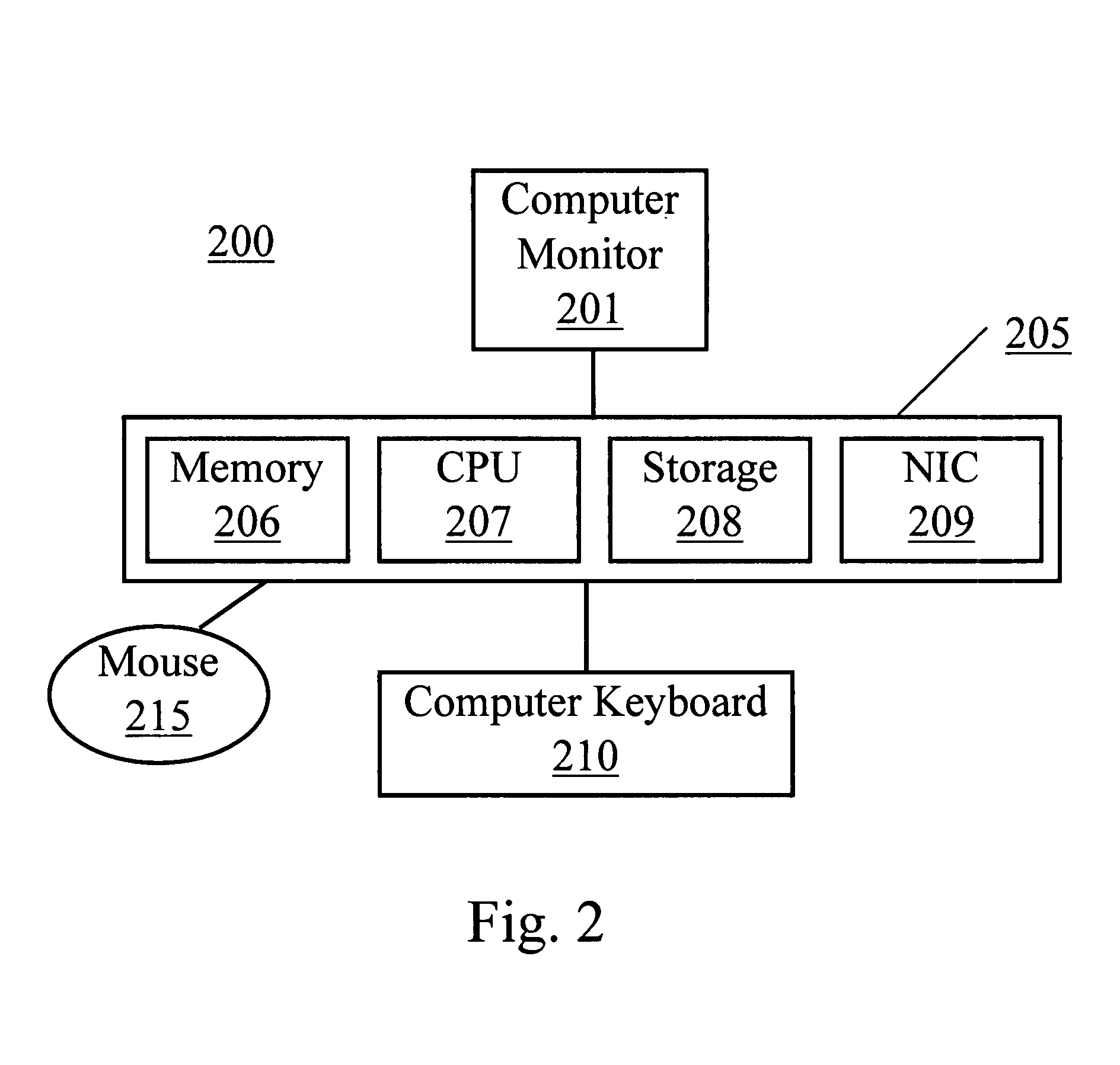
Patents
Literature
44 results about "Program trace" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
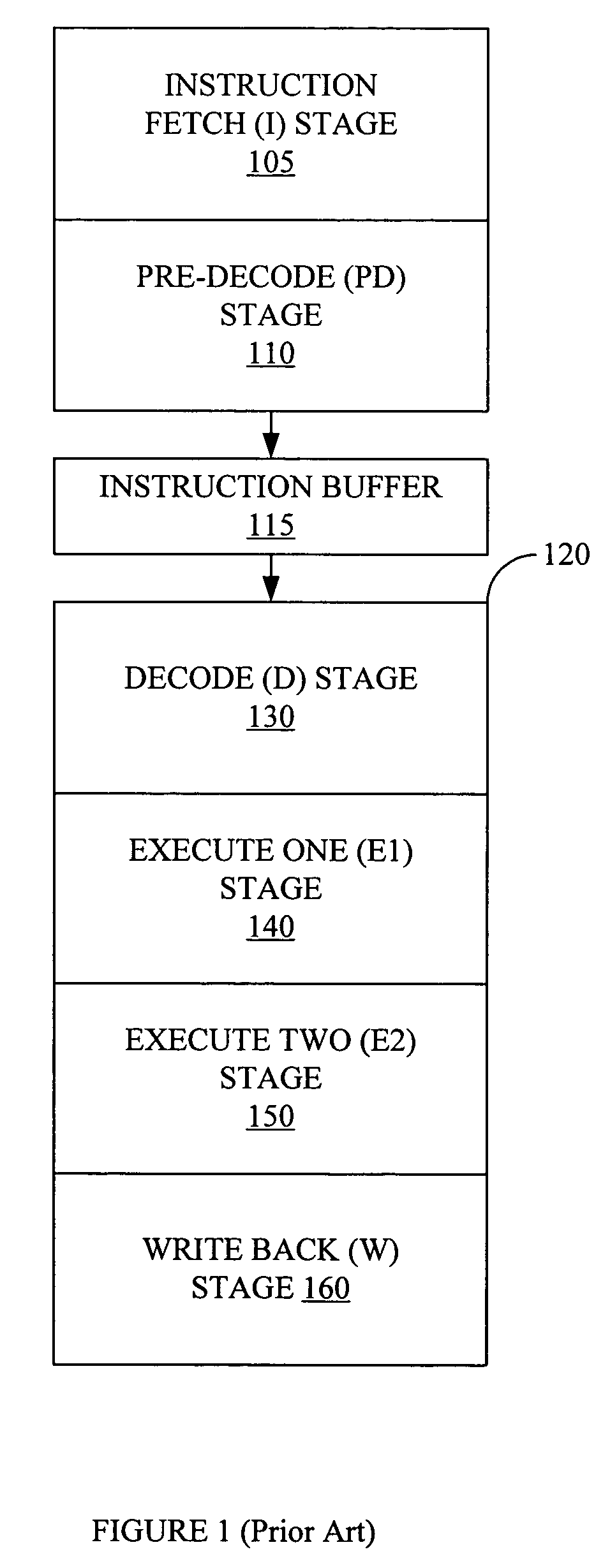
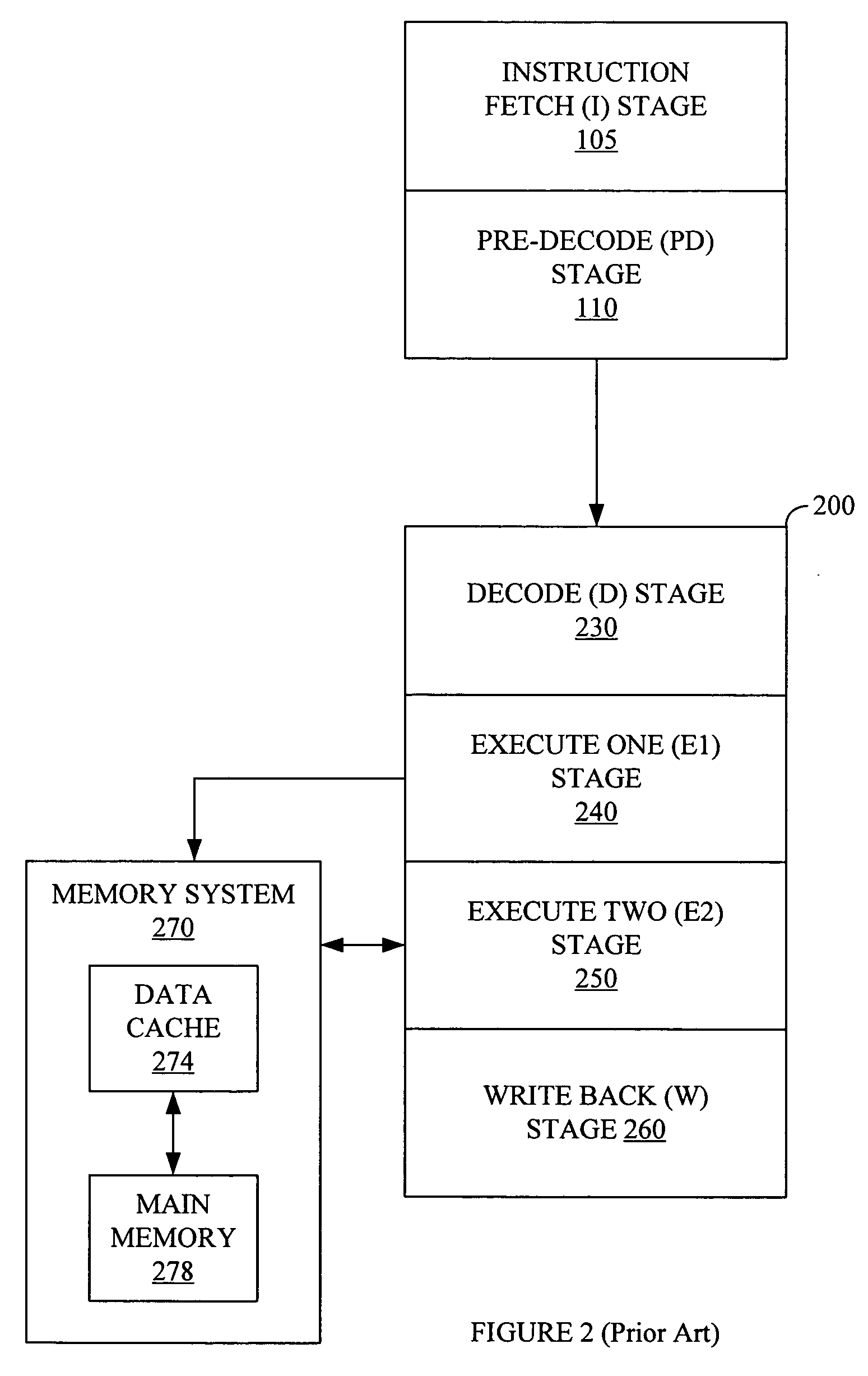
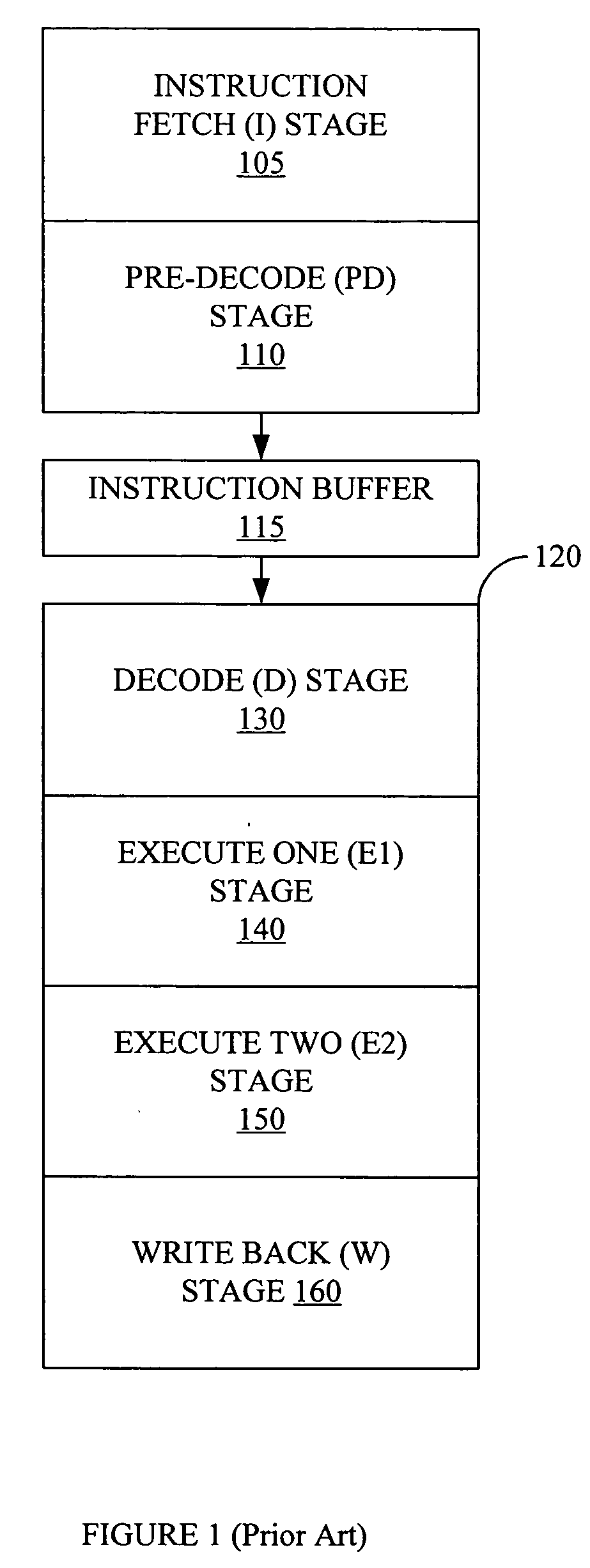
Trace program - a utility program that exhibits the sequence and results of executing the instructions in another program. snapshot program - a trace program that produces output for selected conditions.
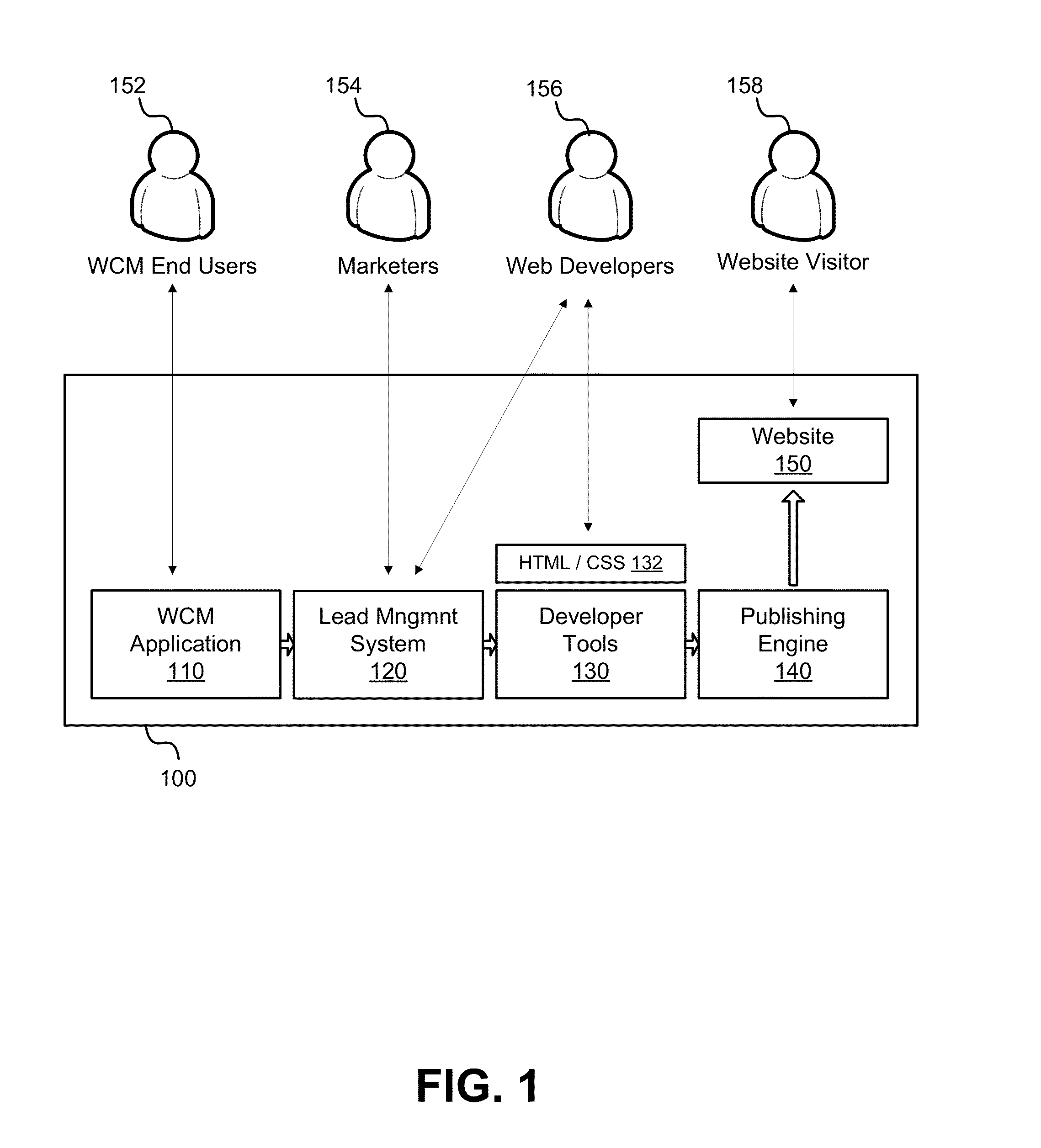
Risk Scoring Based On Endpoint User Activities
InactiveUS20100125911A1Minimize further violationMemory loss protectionError detection/correctionRisk rankingApplication software
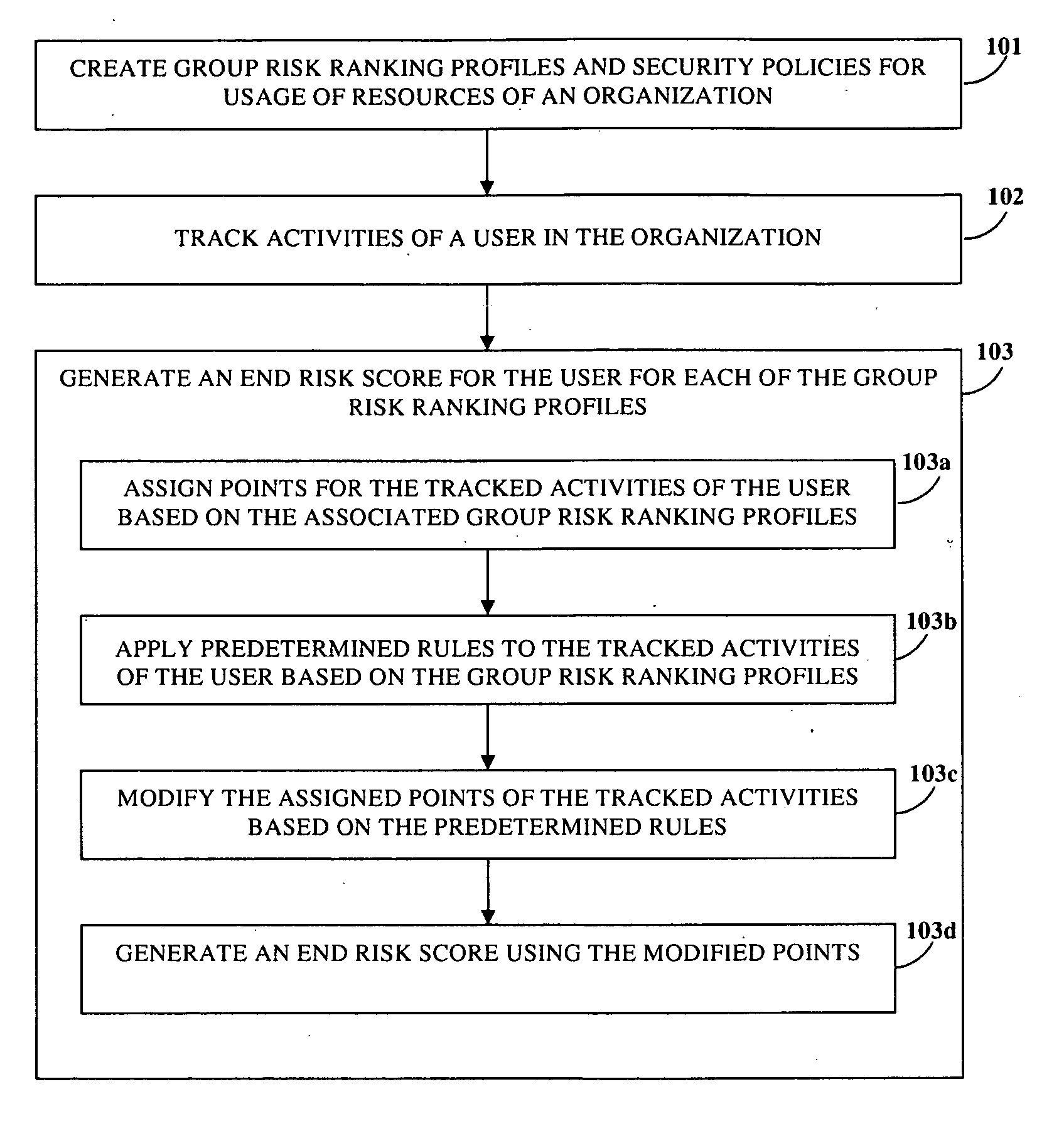
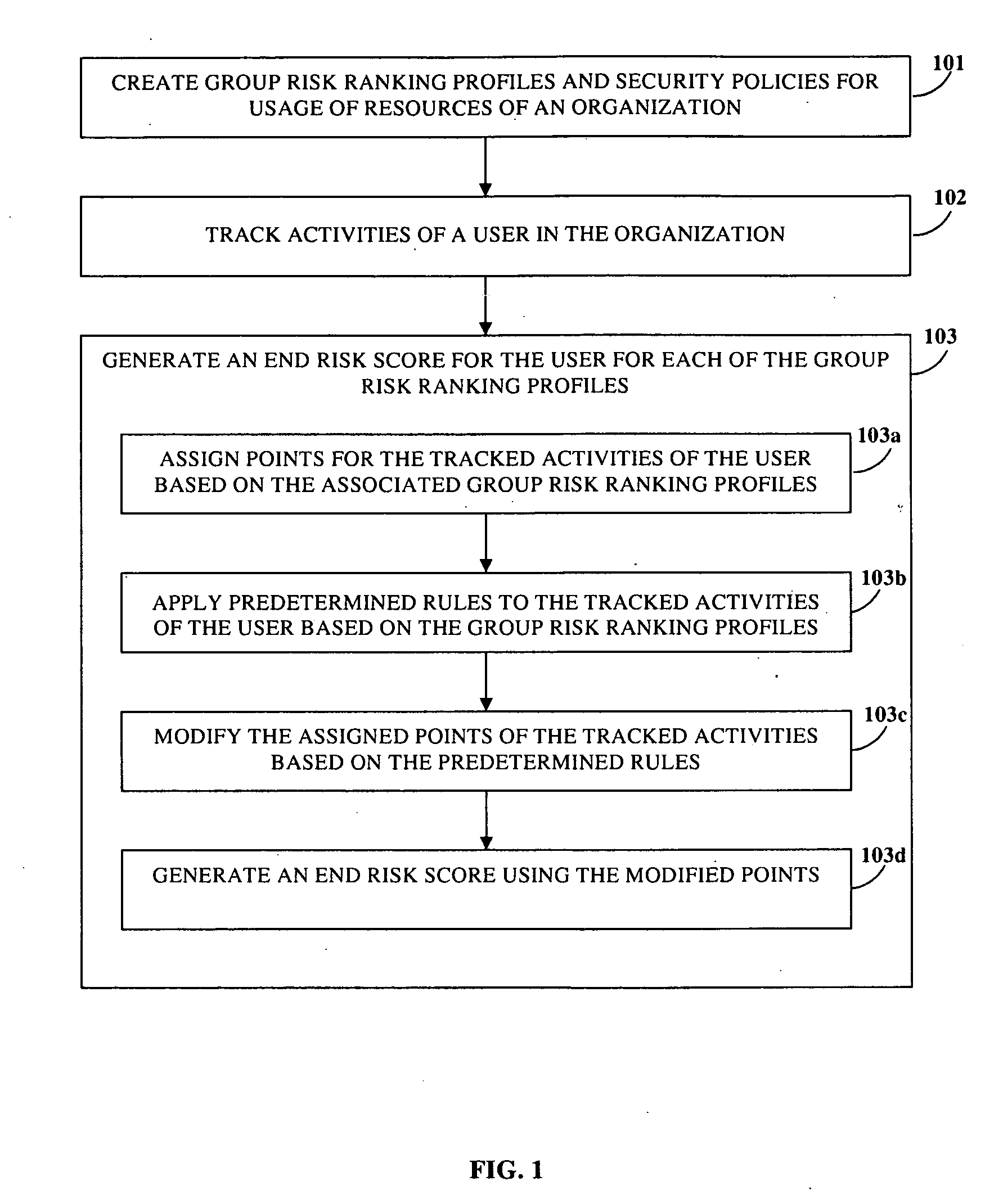
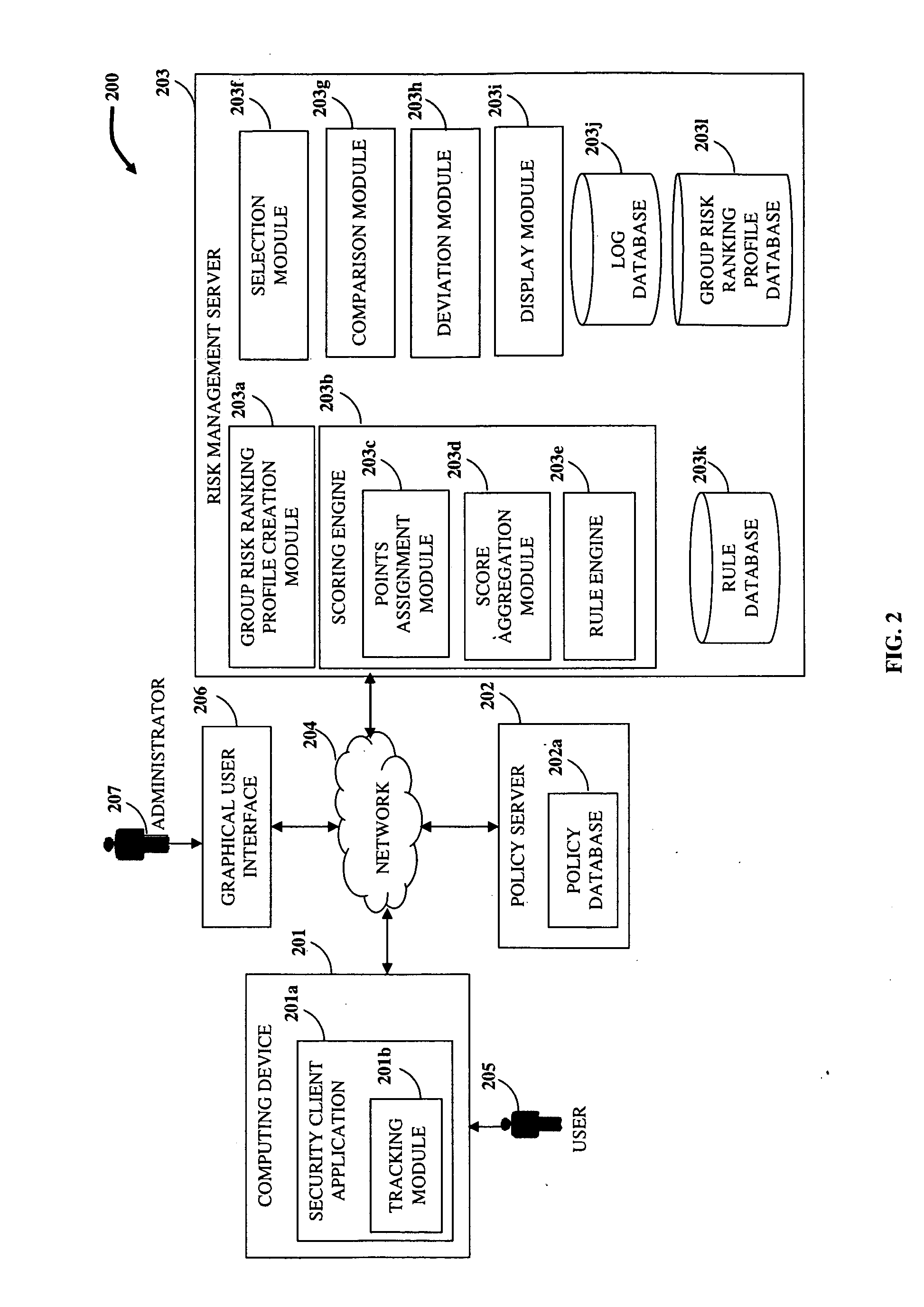
Disclosed herein is a computer implemented method and system for ranking a user in an organization based on the user's information technology related activities and arriving at an end risk score used for determining the risk involved in activities performed by the user and for other purposes. Group risk ranking profiles and security policies for usage of the organization's resources are created. The user is associated with one or more group risk ranking profiles. A security client application tracks the user's activities. Points are assigned to the user's tracked activities based on each of the associated group risk ranking profiles. The assigned points are aggregated to generate a first risk score. The assigned points of the user's tracked activities are modified at different levels based on predefined rules. The modified points are aggregated to generate the end risk score which is used for compliance and governance purposes, optimizing resources, etc.
Owner:CISCO TECH INC
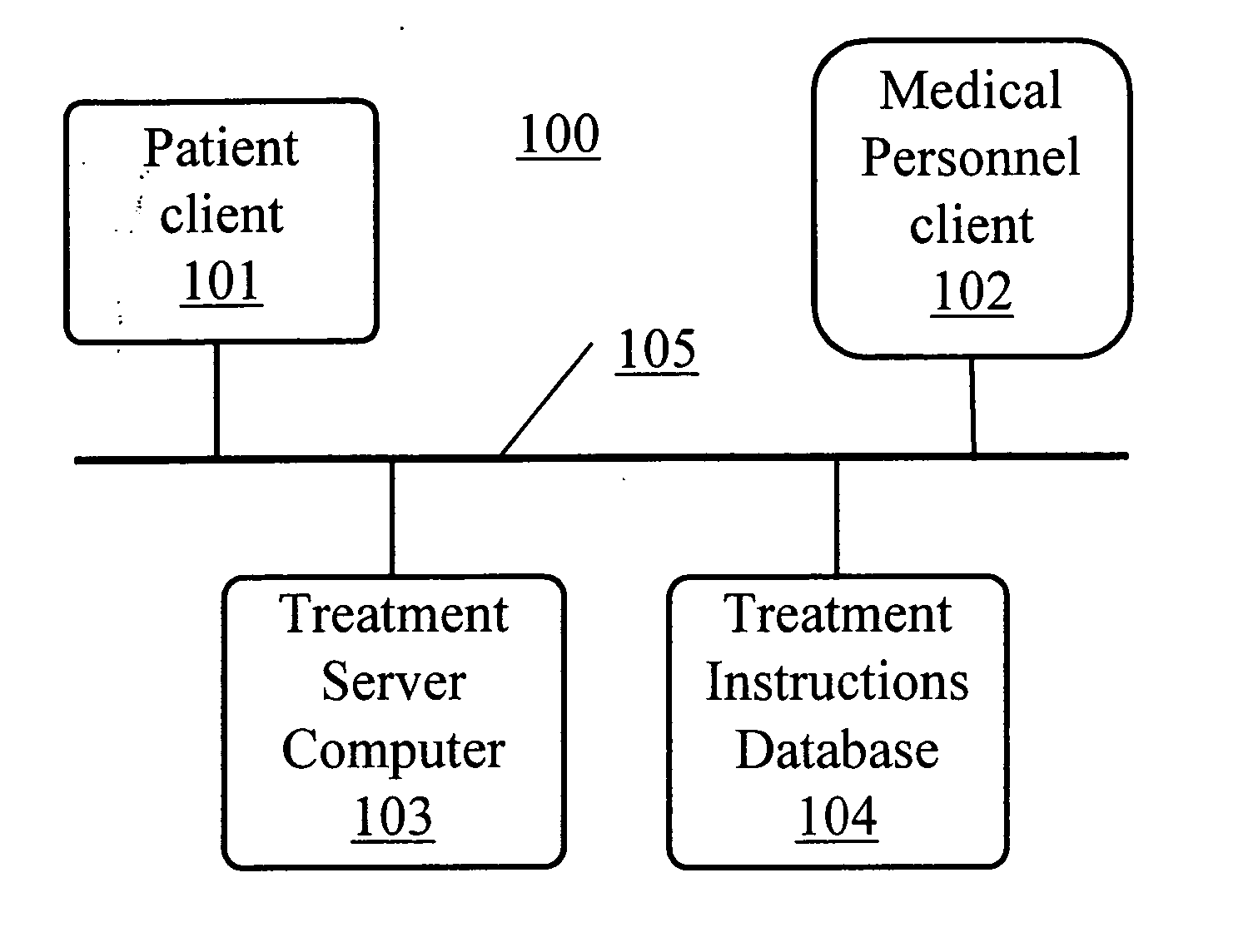
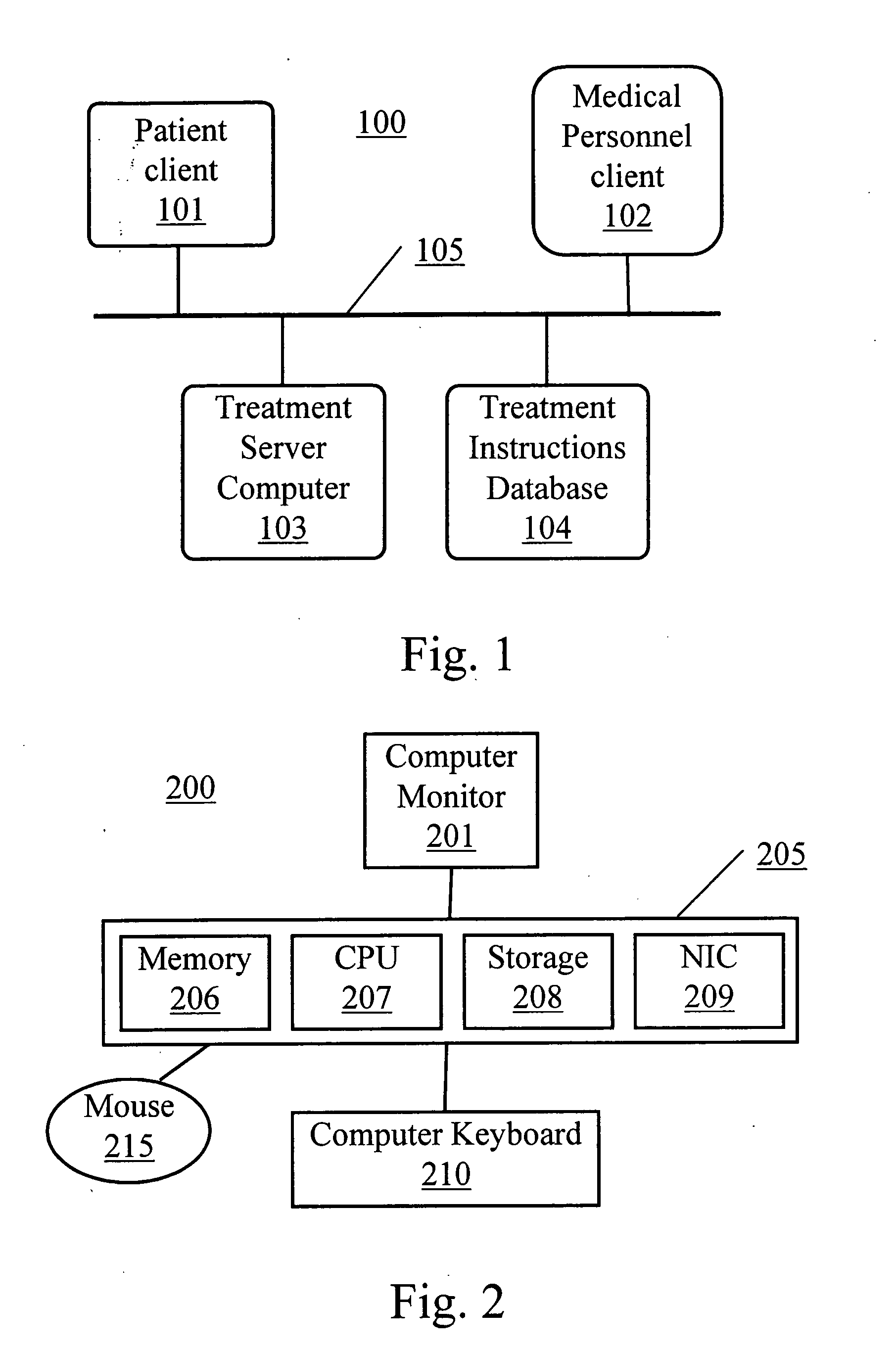
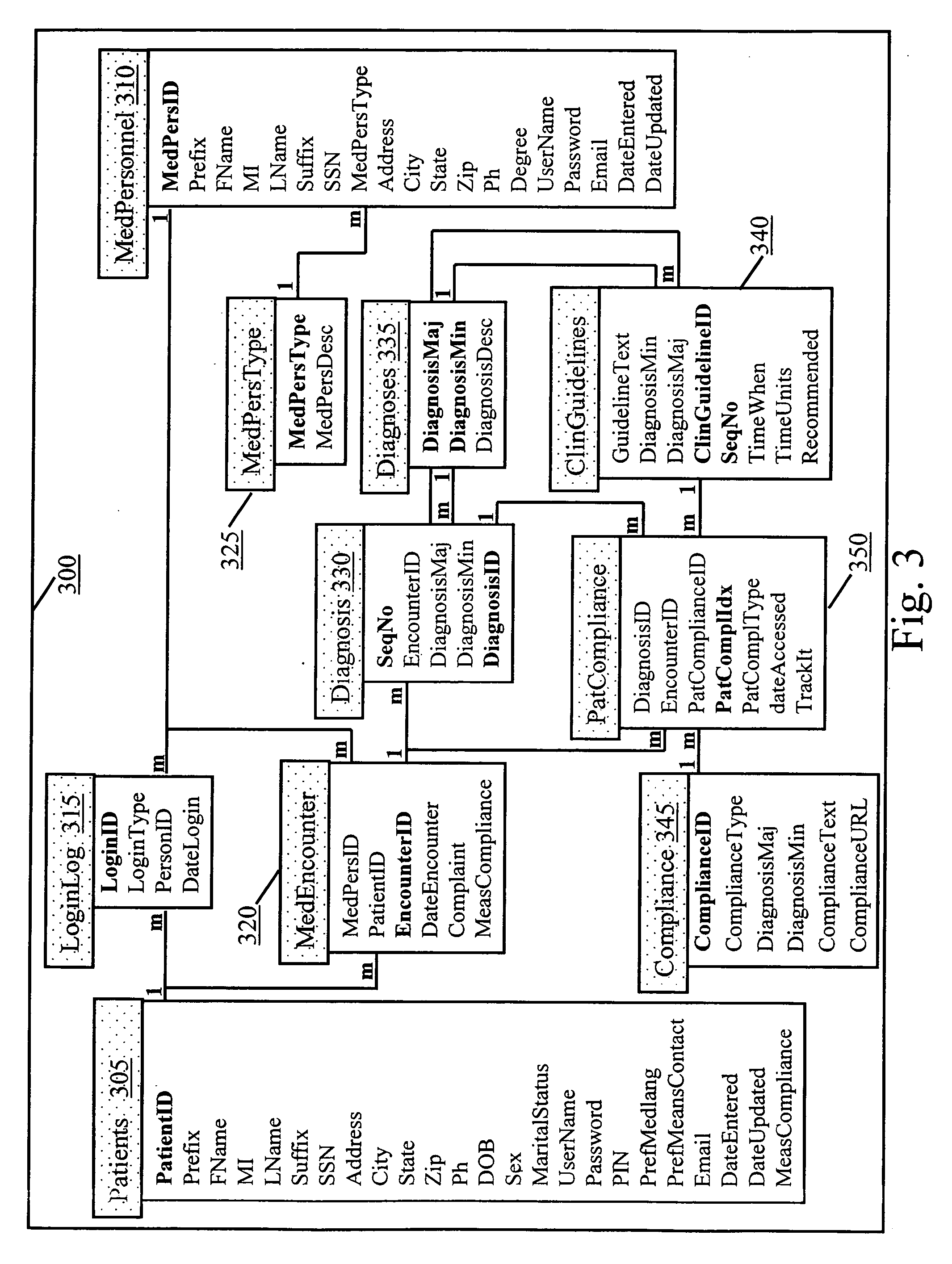
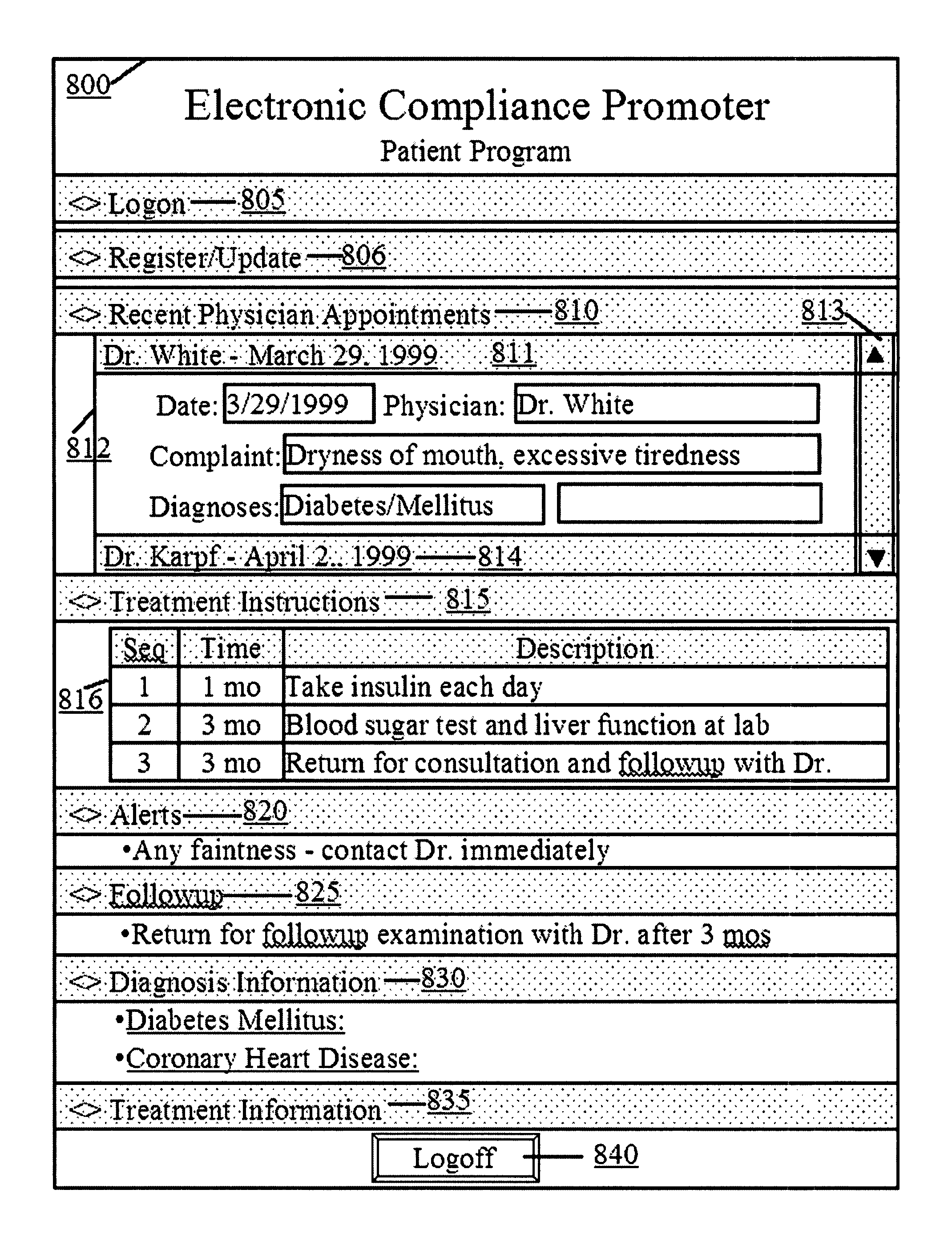
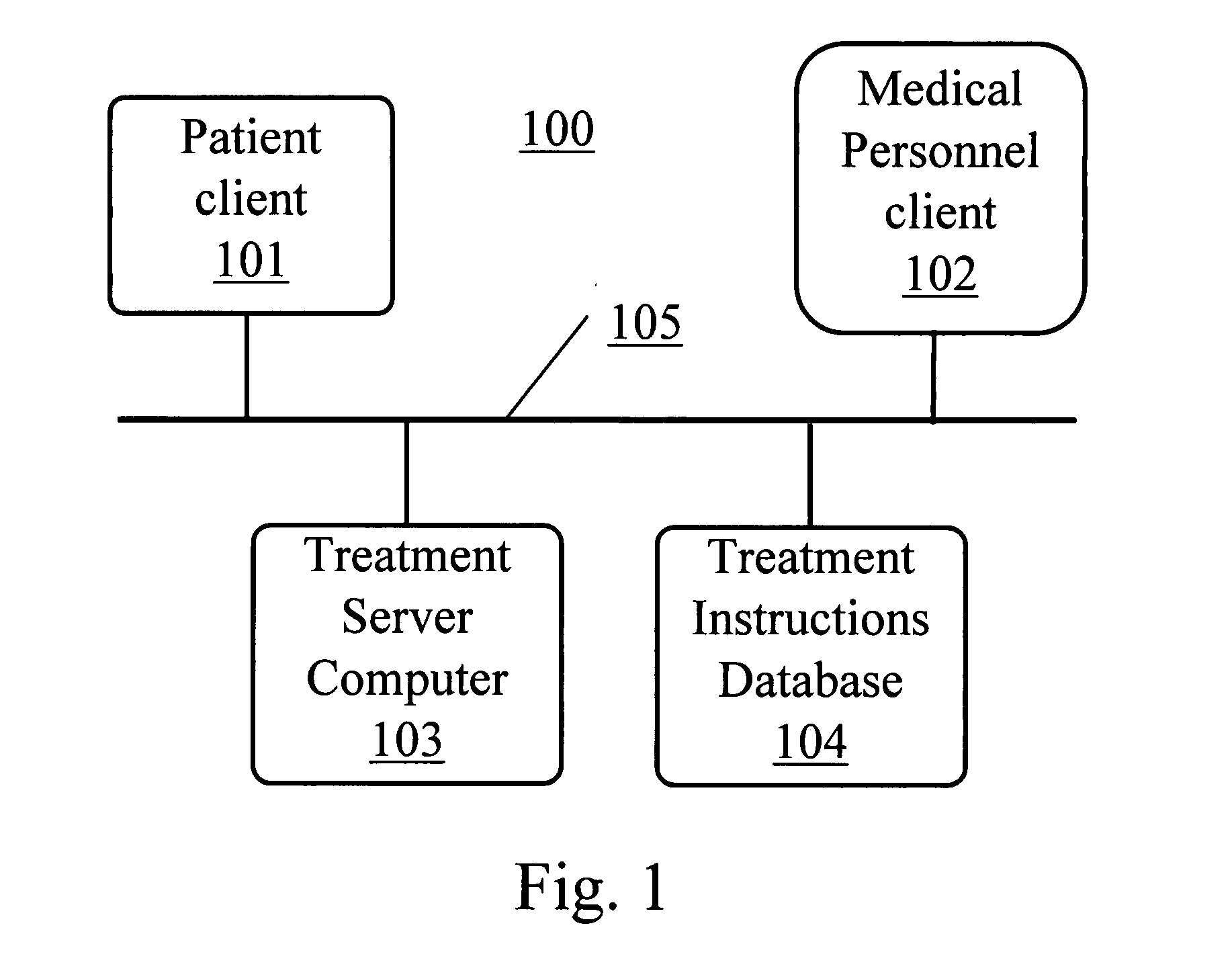
Computer system and method for increasing patients compliance to medical care instructions
InactiveUS20050165626A1Patient compliance is goodWide availabilityLocal control/monitoringPatient personal data managementGuidelinePatient compliance
The Electronic Compliance Promoter is a computer system for increasing a patient's compliance with medical post-care treatment instructions. The system permits the patient to review the treatment instructions that have been entered into a treatment instructions database by medical personnel at the time of the examination. The system includes a patient-client computer interface, a medical person-client interface, a treatment instructions database, and a compliance-server program. The database contains the post-visit care instructions and other types of information that the patient should have to understand and follow those instructions. The database also has treatment guideline information to assist the doctor in formulating the post-care treatment instructions. The patients client-computer interface provides a knowledge-based means for the patient to review interactively the Doctor's after care instructions, and measures compliance by tracking a patients' use of the specific designated diagnosis related resources. The medical personnel client-computer interface provides a knowledge-based means to designate the post-care medical visit instructions the patient is to follow. The compliance-server program tracks patients compliance and can send messages to patients reminding them to review the post-care treatment instructions. The Electronic Compliance Promoter system provides a means to significantly increase a patient's compliance with medical care instructions.
Owner:KARPF RONALD STEVEN
Computer system and method for increasing patients compliance to medical care instructions
InactiveUS7287031B1Maximize availabilityEasy accessLocal control/monitoringDiagnostic recording/measuringGuidelinePatient compliance
Owner:KARPF RONALD STEVEN +1
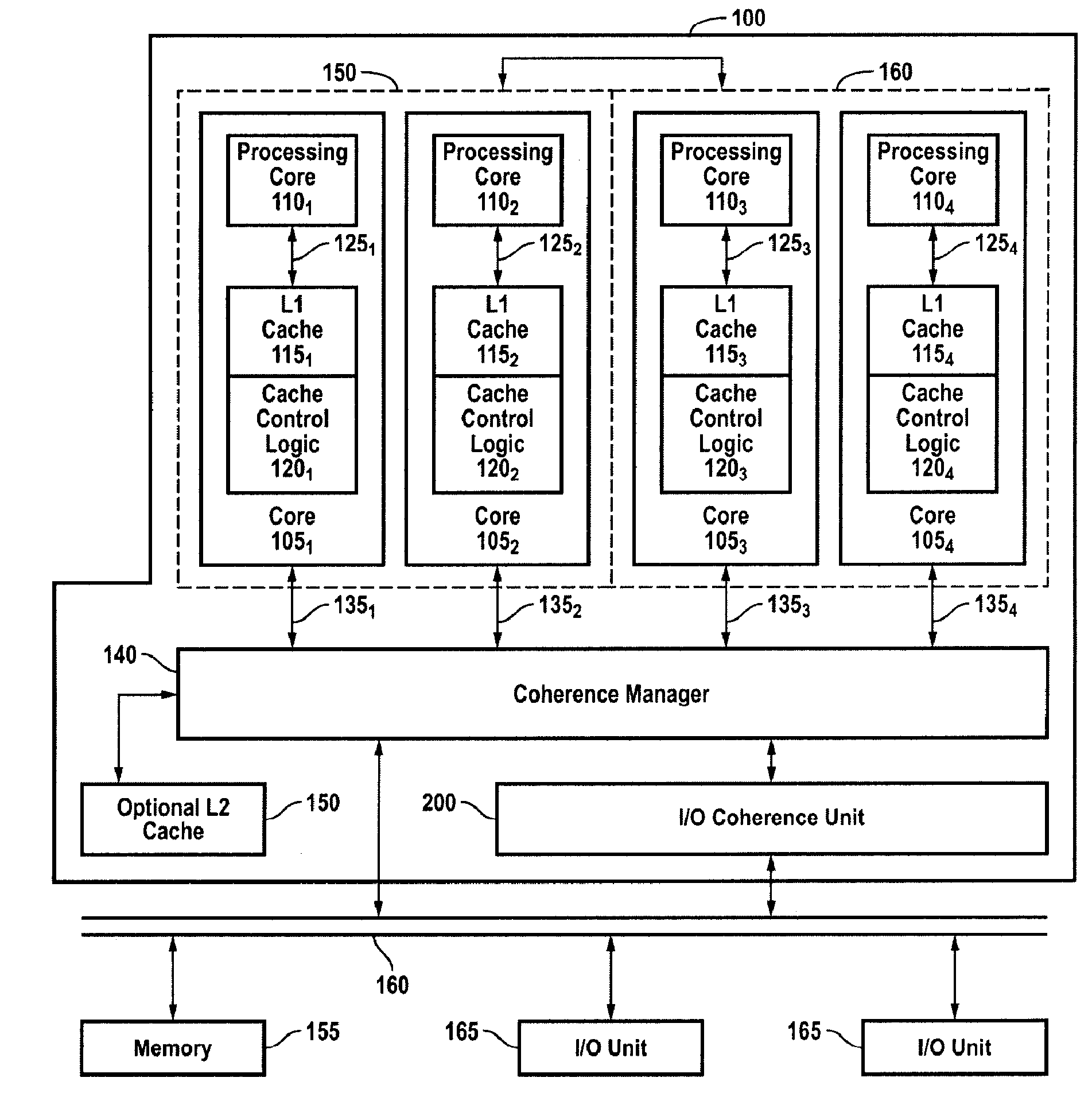
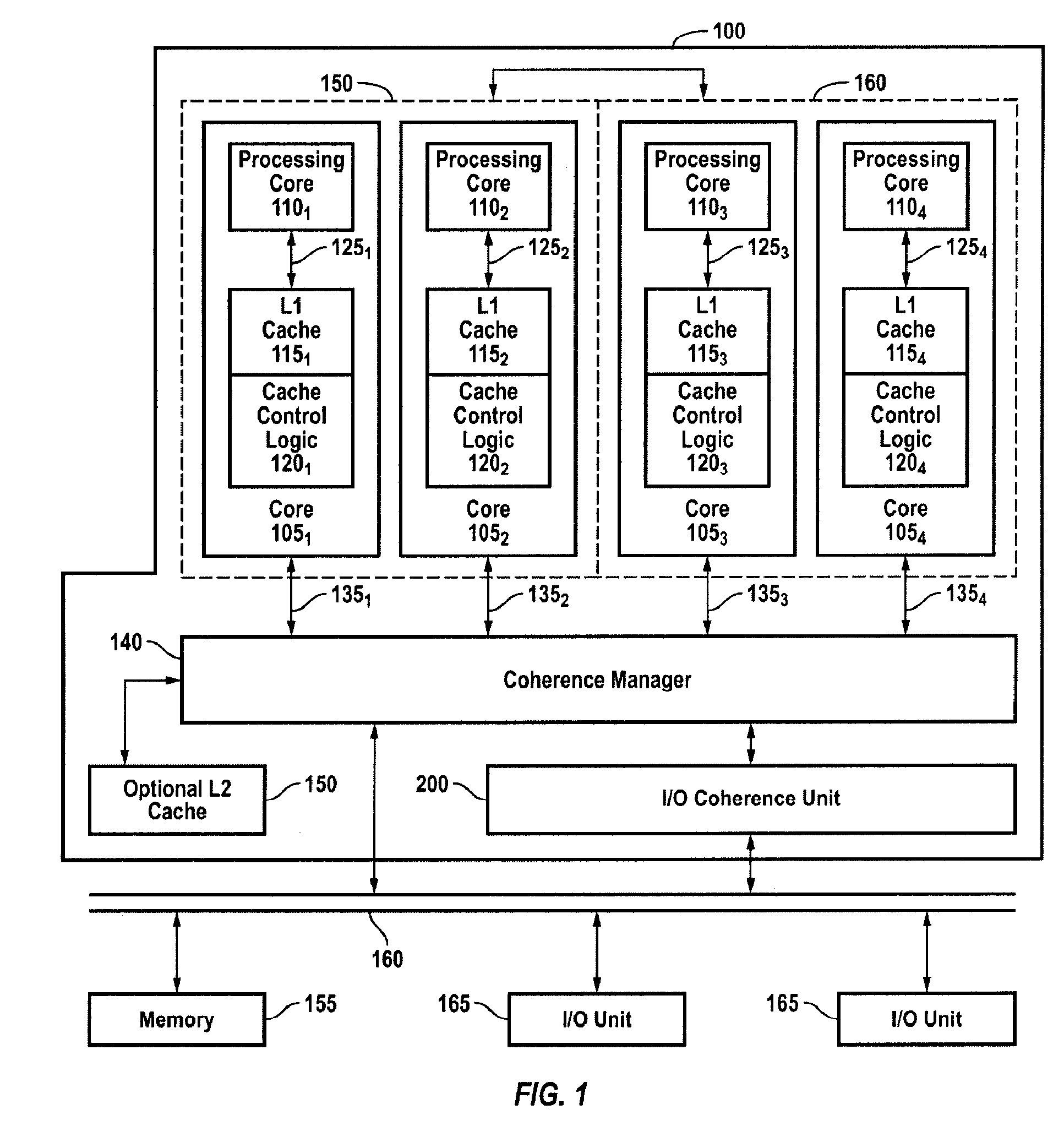
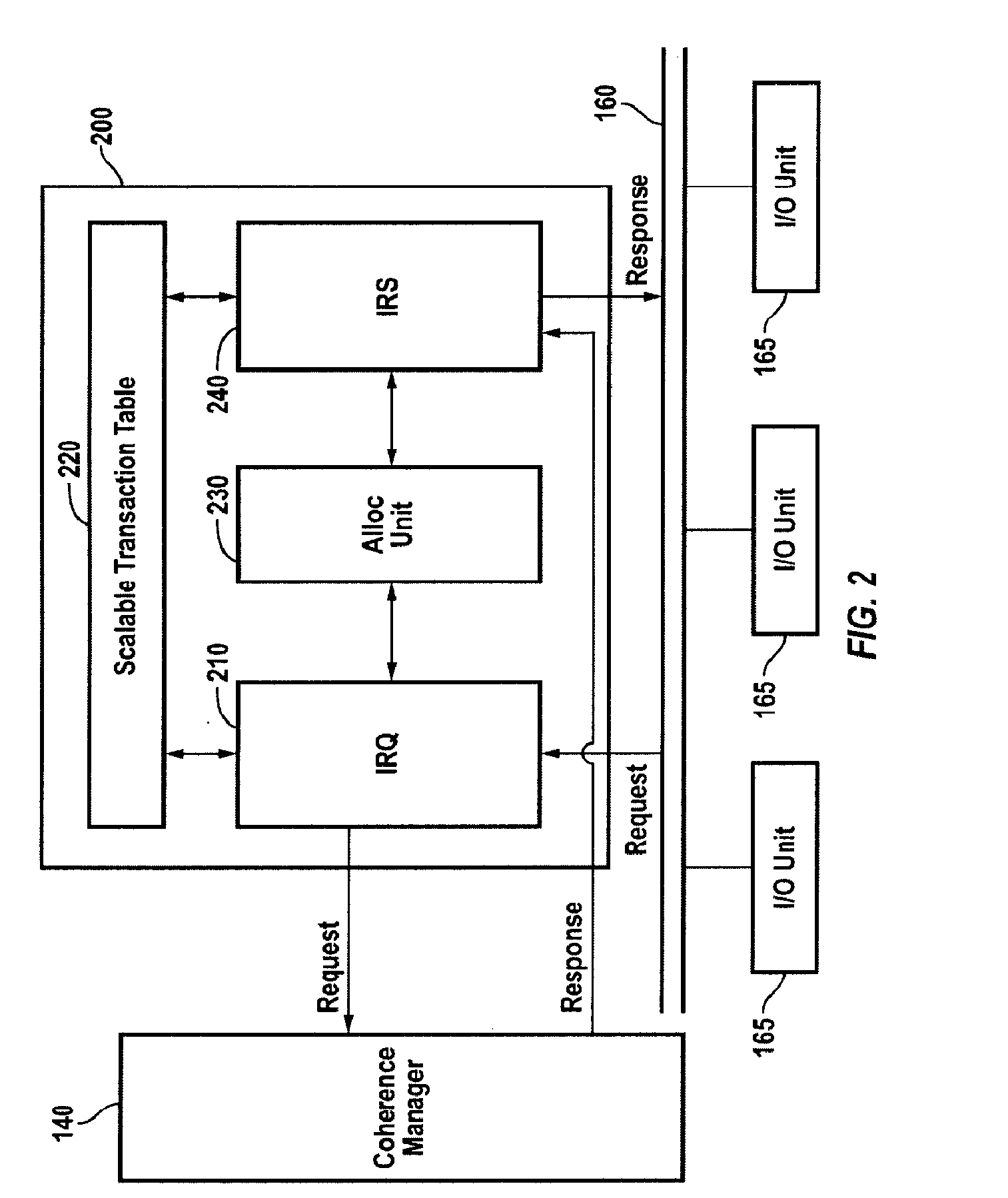
Efficient, Scalable and High Performance Mechanism for Handling IO Requests
A system, apparatus and method for managing input / output requests in a multi-processor system is disclosed. An IO coherence unit includes an IO request handler, a variable size transaction table, and an IO response handler. The size of the transaction table varies according to the number of pending IO requests. The IO request handler stores information about pending IO requests in the transaction table to establish an order among related requests and to permit out-of-order handling of unrelated requests. The IO response handler tracks responses to the IO requests and updates the information in the transaction table. The IO coherence unit returns responses to requesting devices in compliance with device ordering requirements.
Owner:ARM FINANCE OVERSEAS LTD
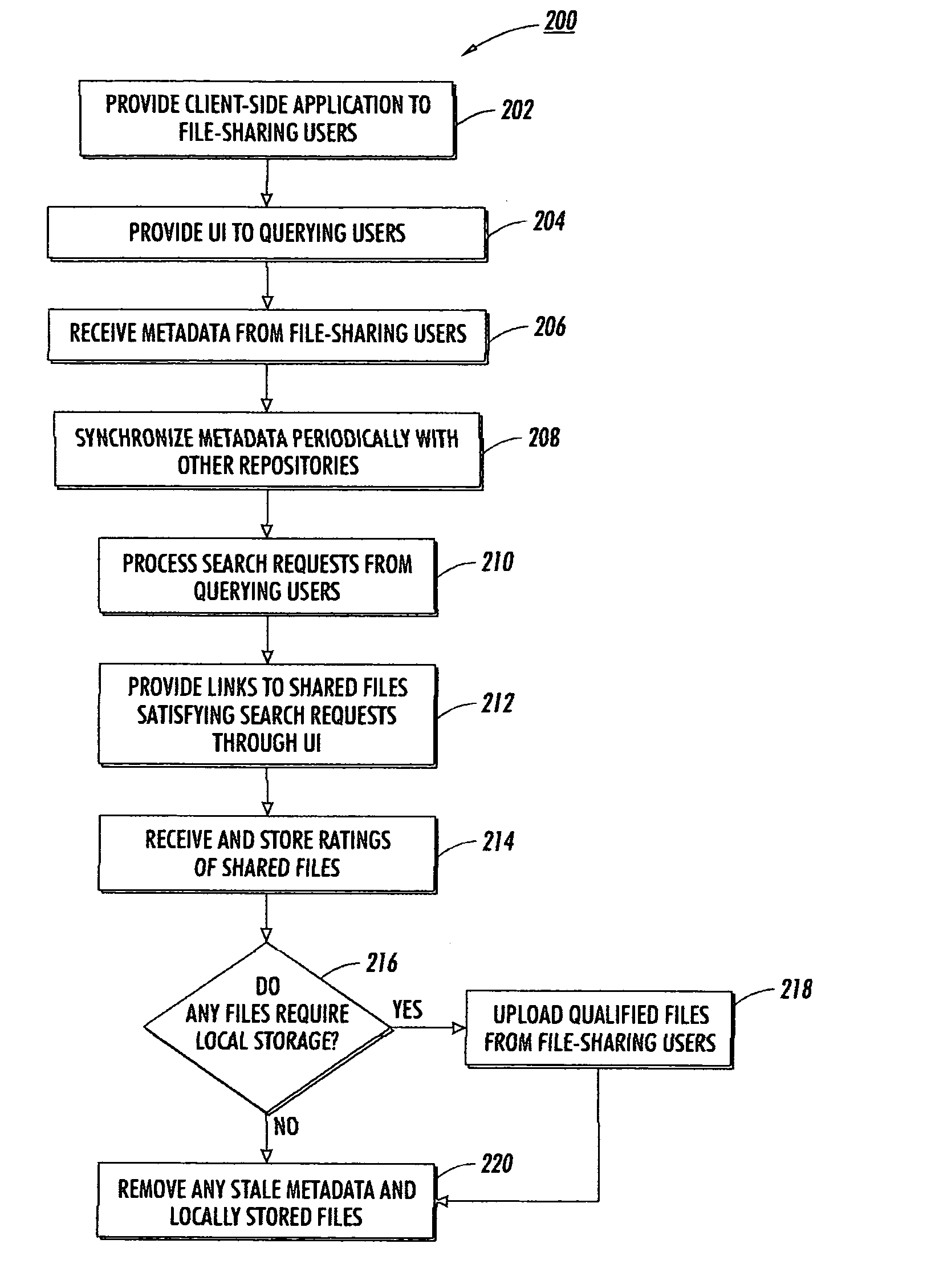
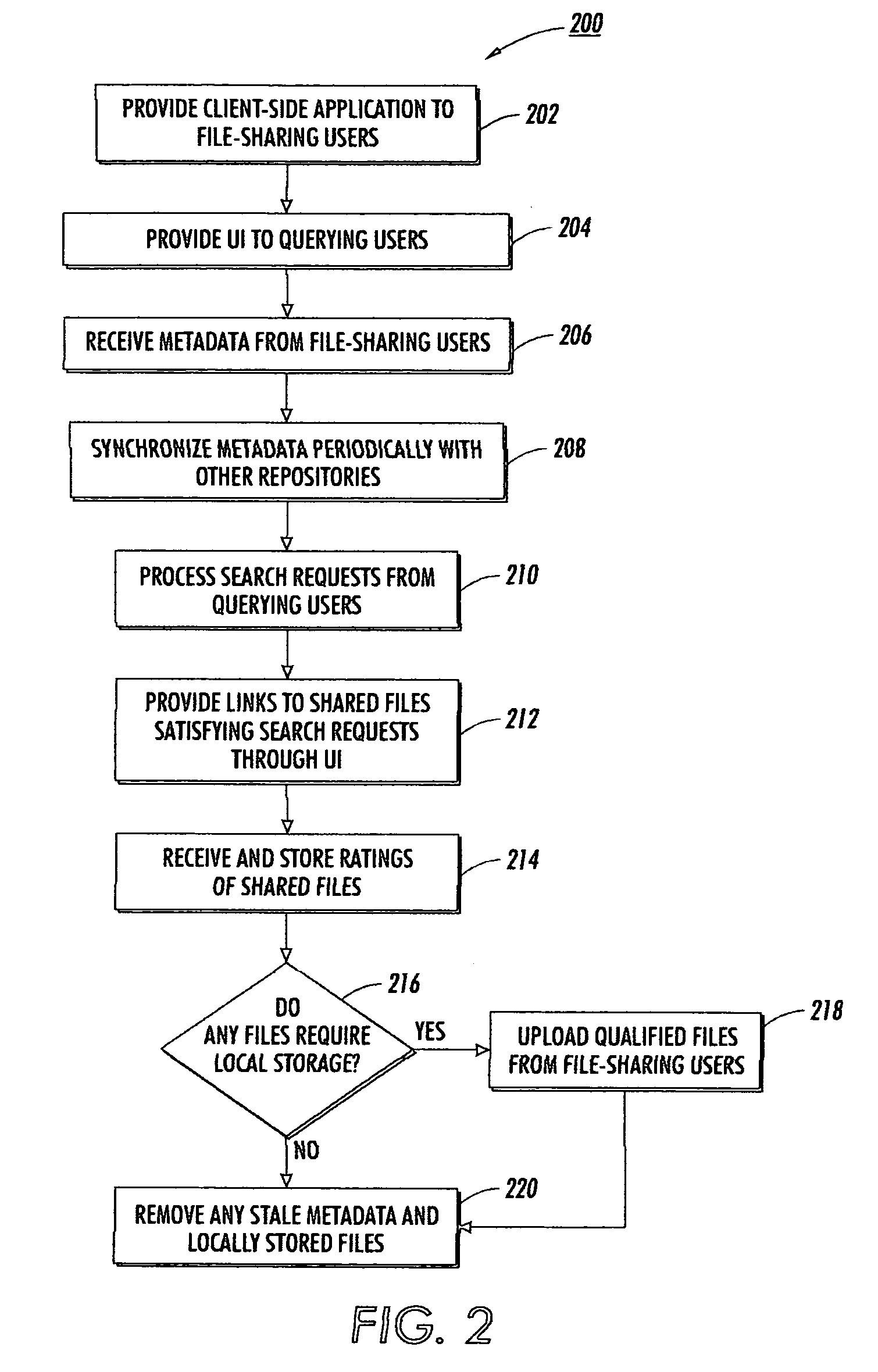
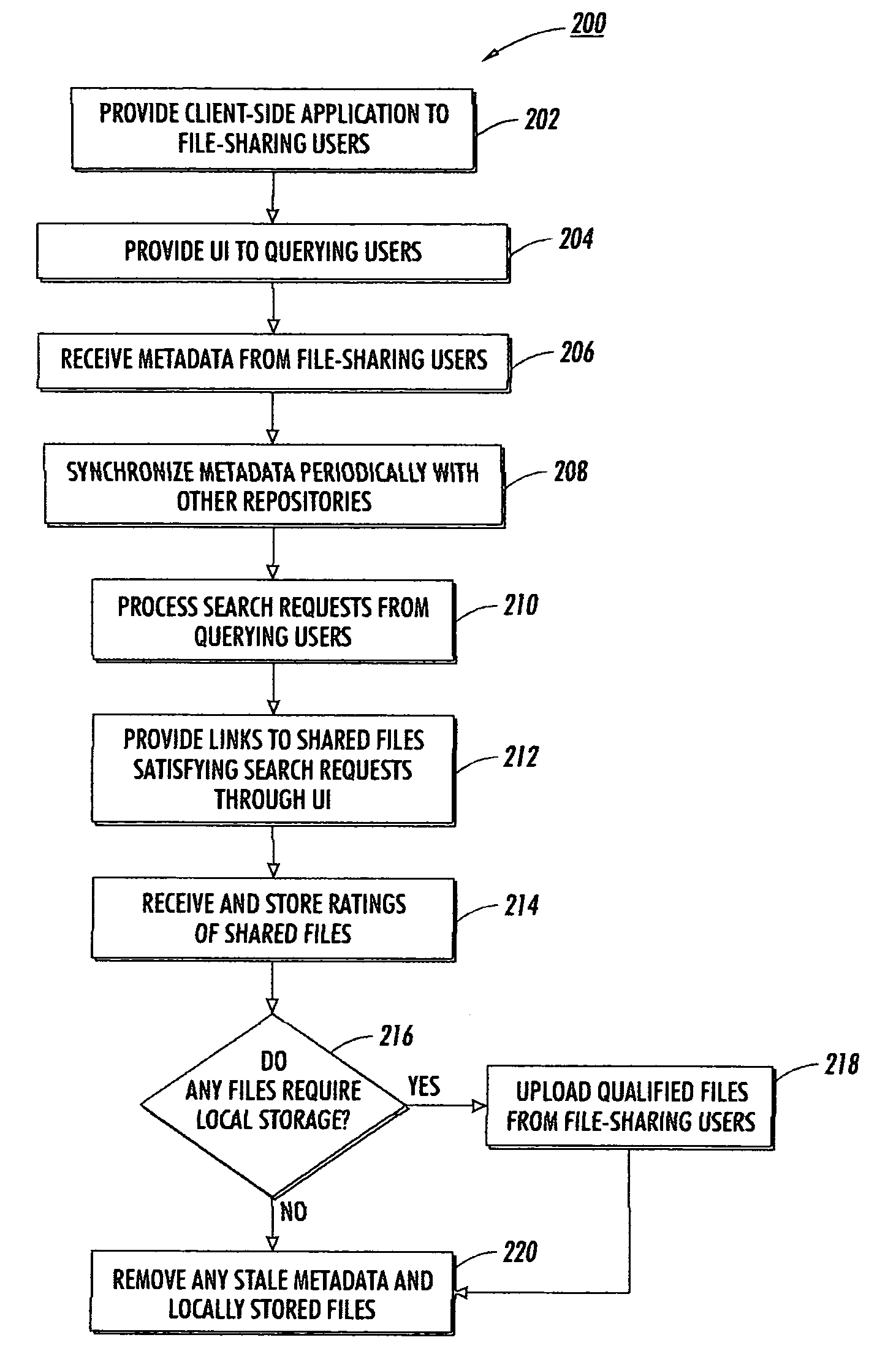
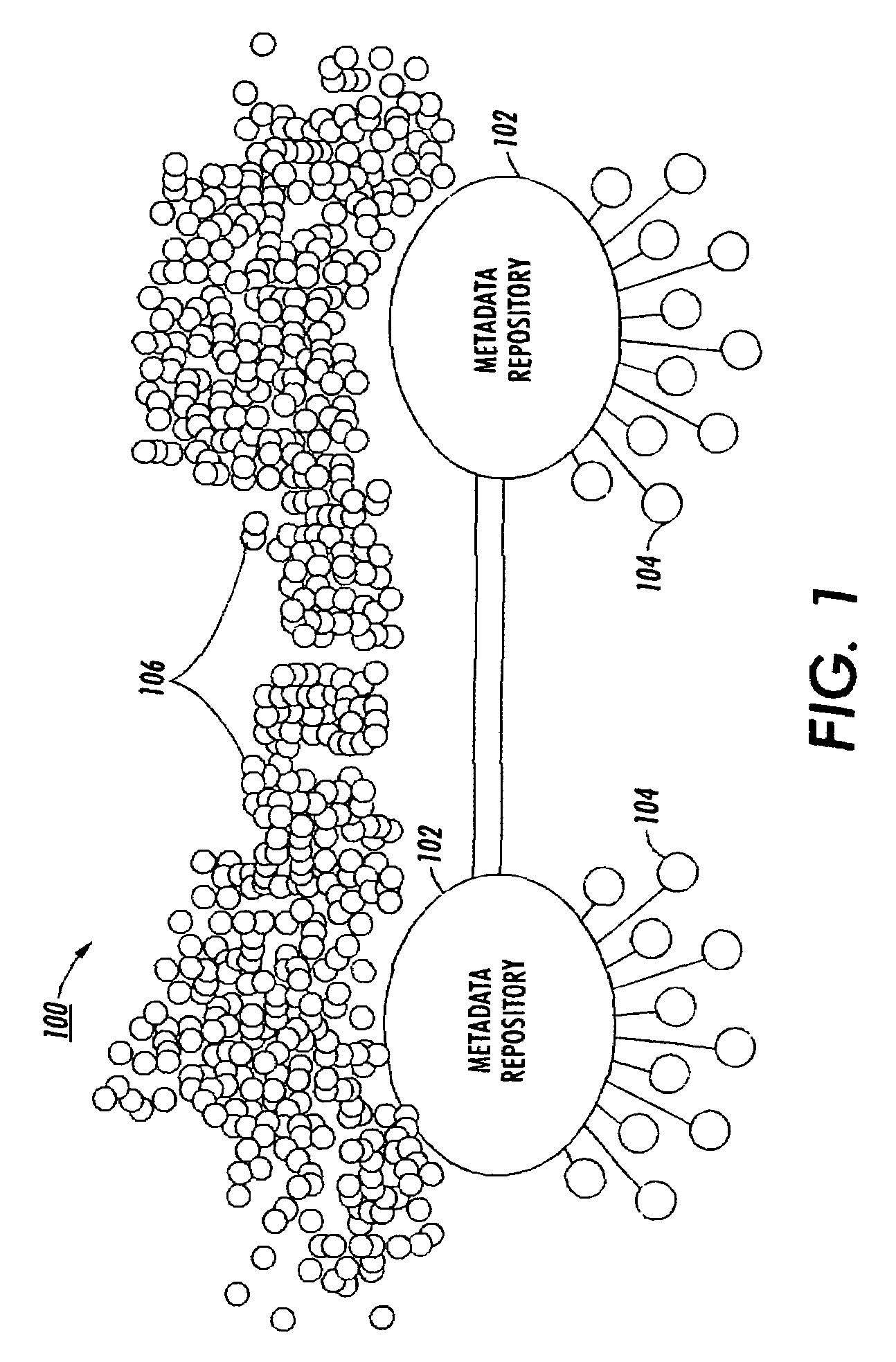
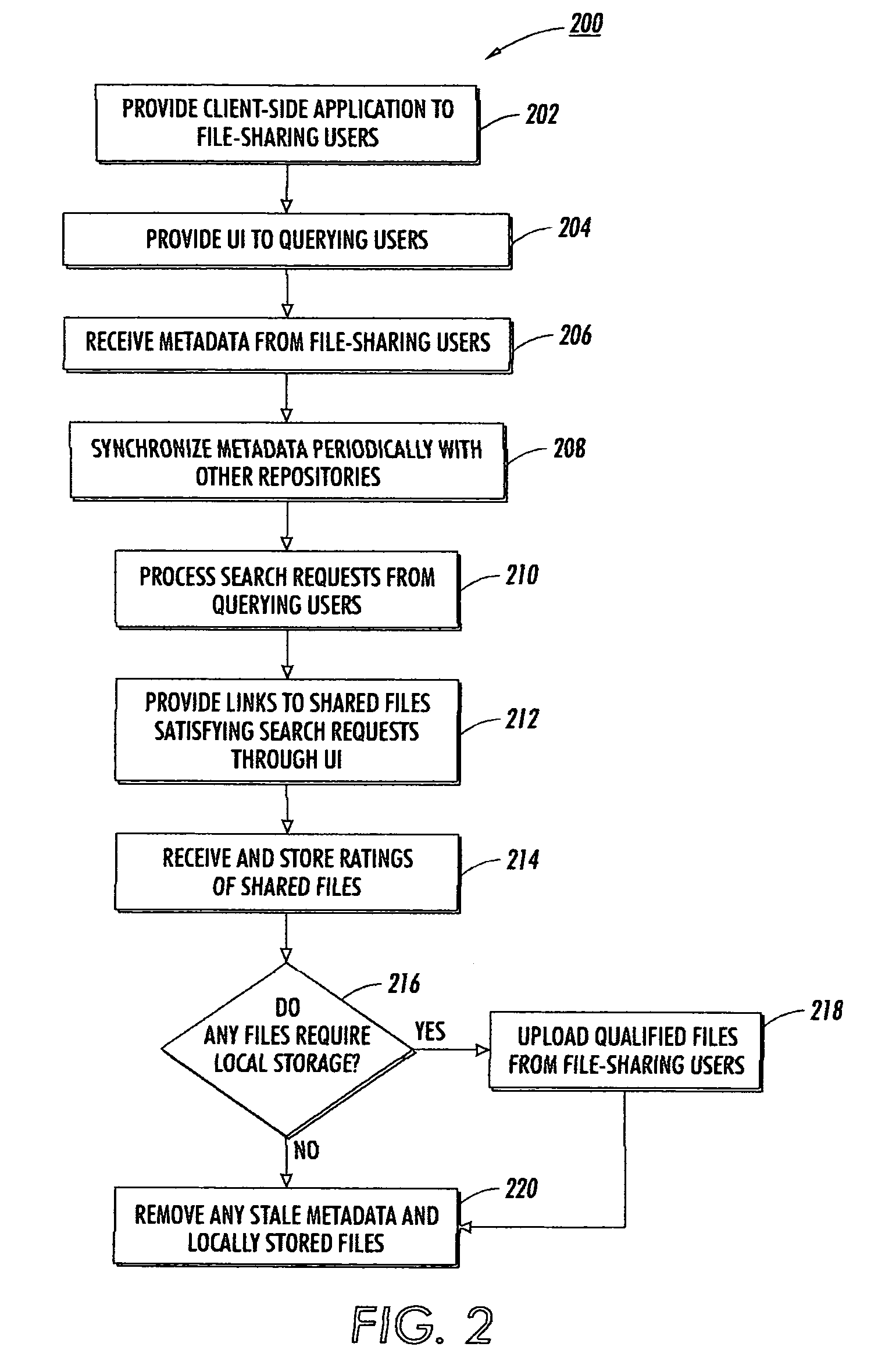
Multi-tiered structure for file sharing based on social roles
ActiveUS20050131871A1Facilitate search queriesData processing applicationsDigital data processing detailsClient-sideProgram trace
An Internet-scale file sharing system includes a client-side file sharing application that allows file-sharing users to identify files to share and transmit metadata corresponding to those files to a metadata repository. A server-side application operating on the metadata repository tracks metadata received from associated file-sharing users, as well as metadata from other affiliated metadata repositories. Each metadata repository acts as a search engine for any querying users and can provide search results based on locally stored metadata alone. Each metadata repository may additionally choose to locally-store popular files from an associated file-sharing user so as to alleviate transmission burdens on that file-sharing user. Associated metadata repositories each periodically synchronize their stored metadata so that all metadata repositories may generate similar search results. In such manner, file-sharing queries need only be performed by the metadata repository receiving the query, and not by all associated metadata repositories.
Owner:XEROX CORP
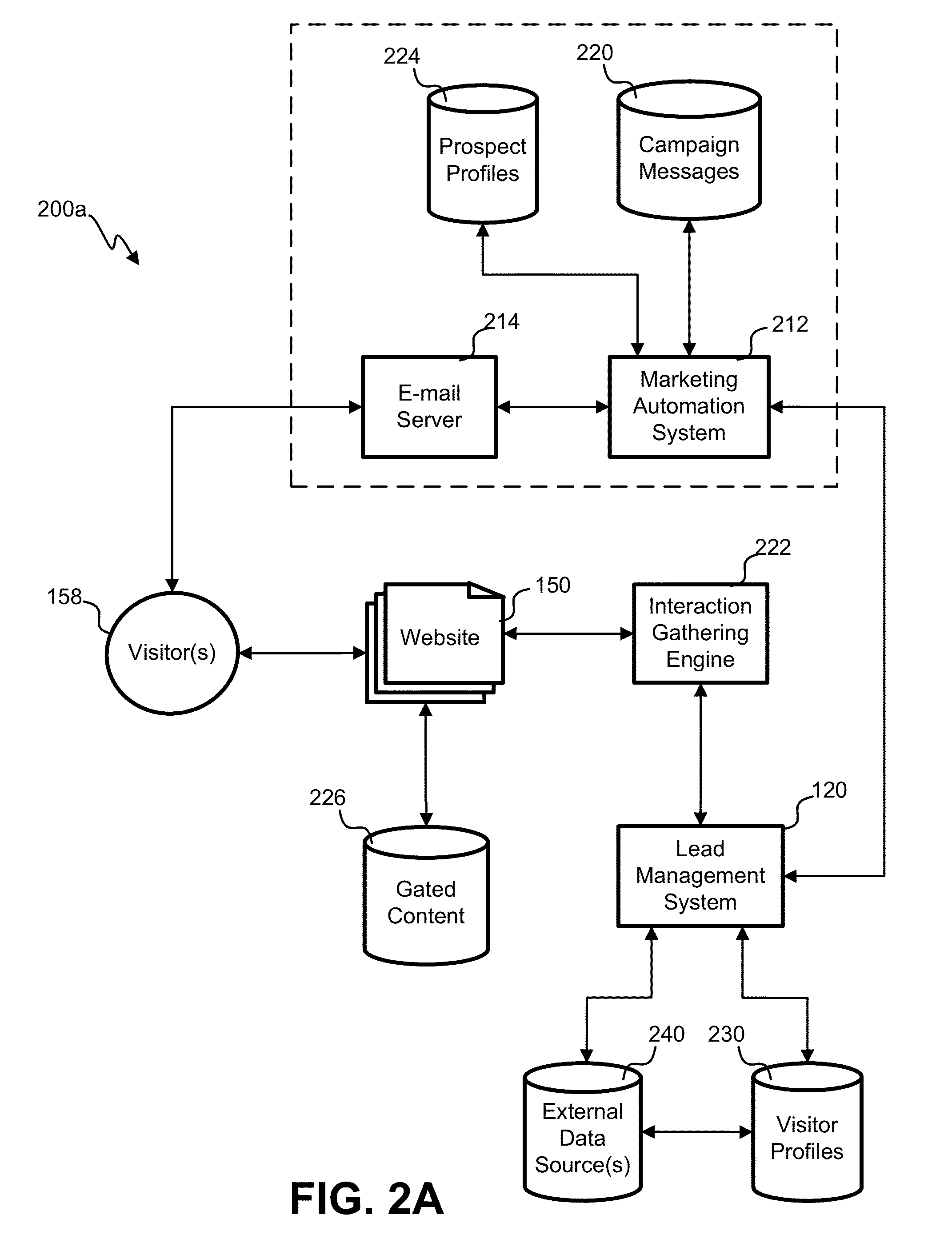
Augmenting progressive profile states with external data sources
A method for using an external login procedure to track interactions on a website includes detecting an interaction between a web server and a user device including a request for login credentials of the user; receiving a transmission that includes information provided by a remotely-located external data source in response to the external data source verifying the login credentials, the information including a user identifier, and information associated with the user that is stored at the external data source; accessing a user profile in a profile database using the user identifier, where profiles have a hierarchy of profile states based at least in part on an amount of information provided by each user; storing the information in the user profile; and determining whether the profile state associated with the user profile should be changed based on the information associated with the user.
Owner:CLICKABILITY
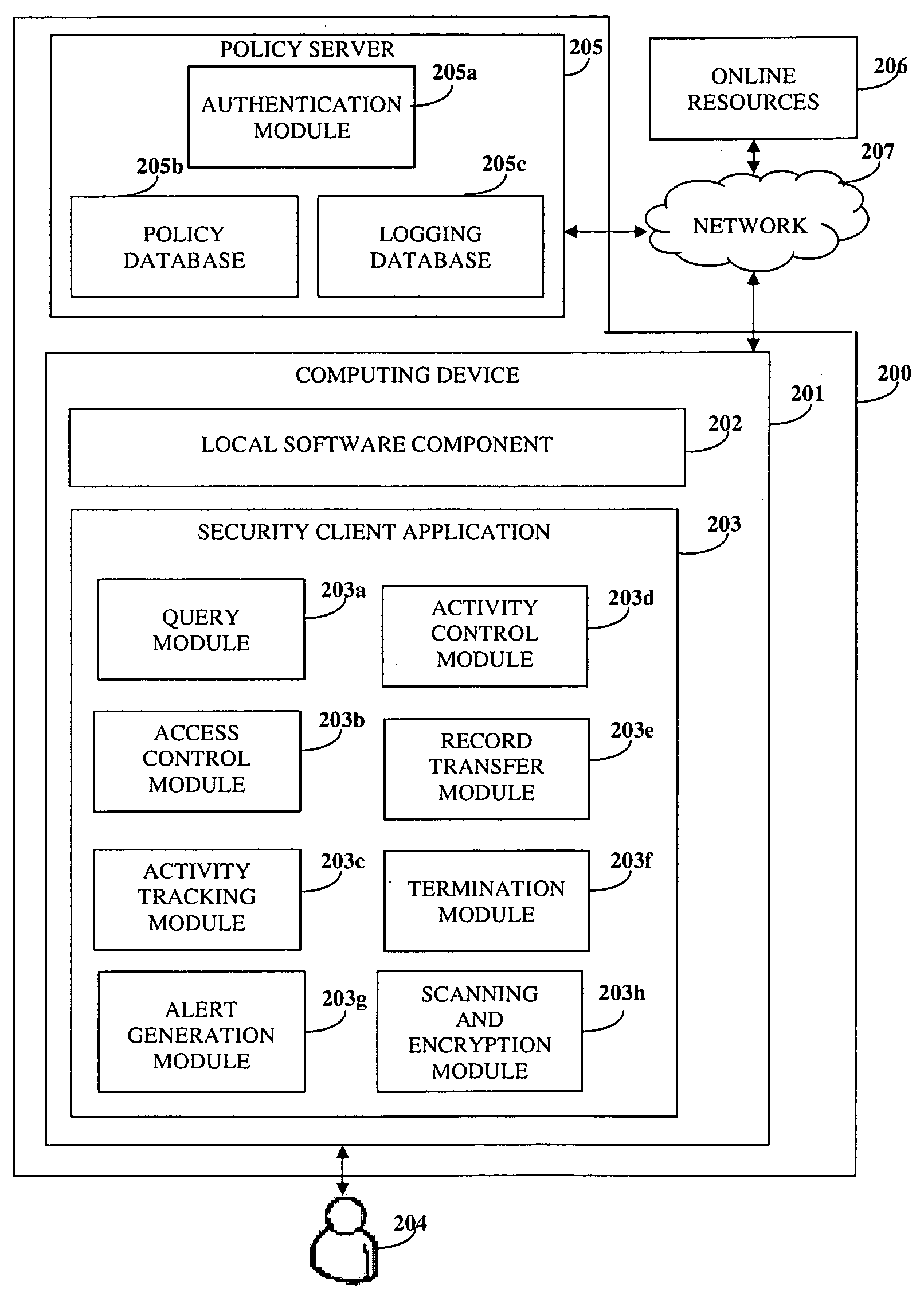
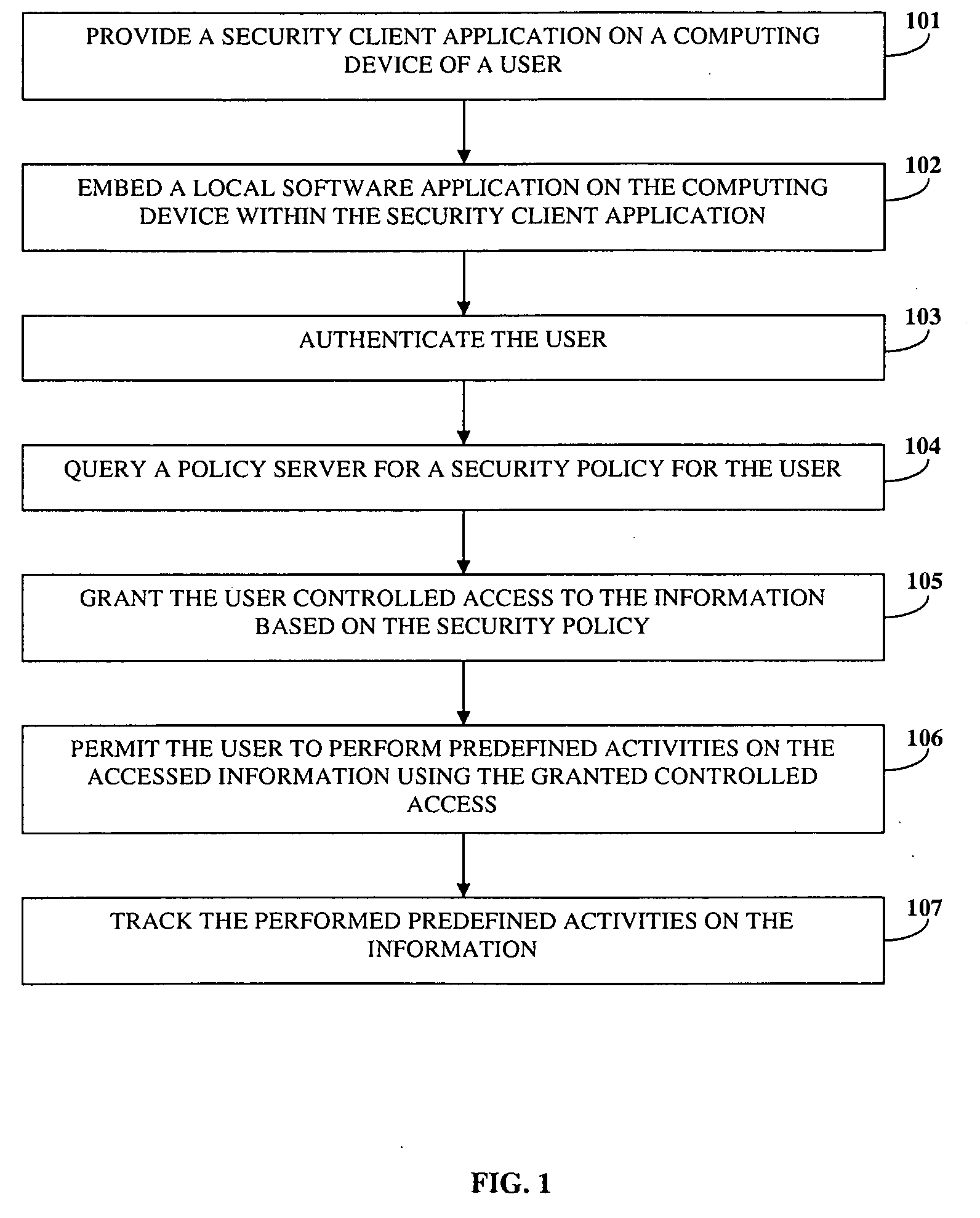
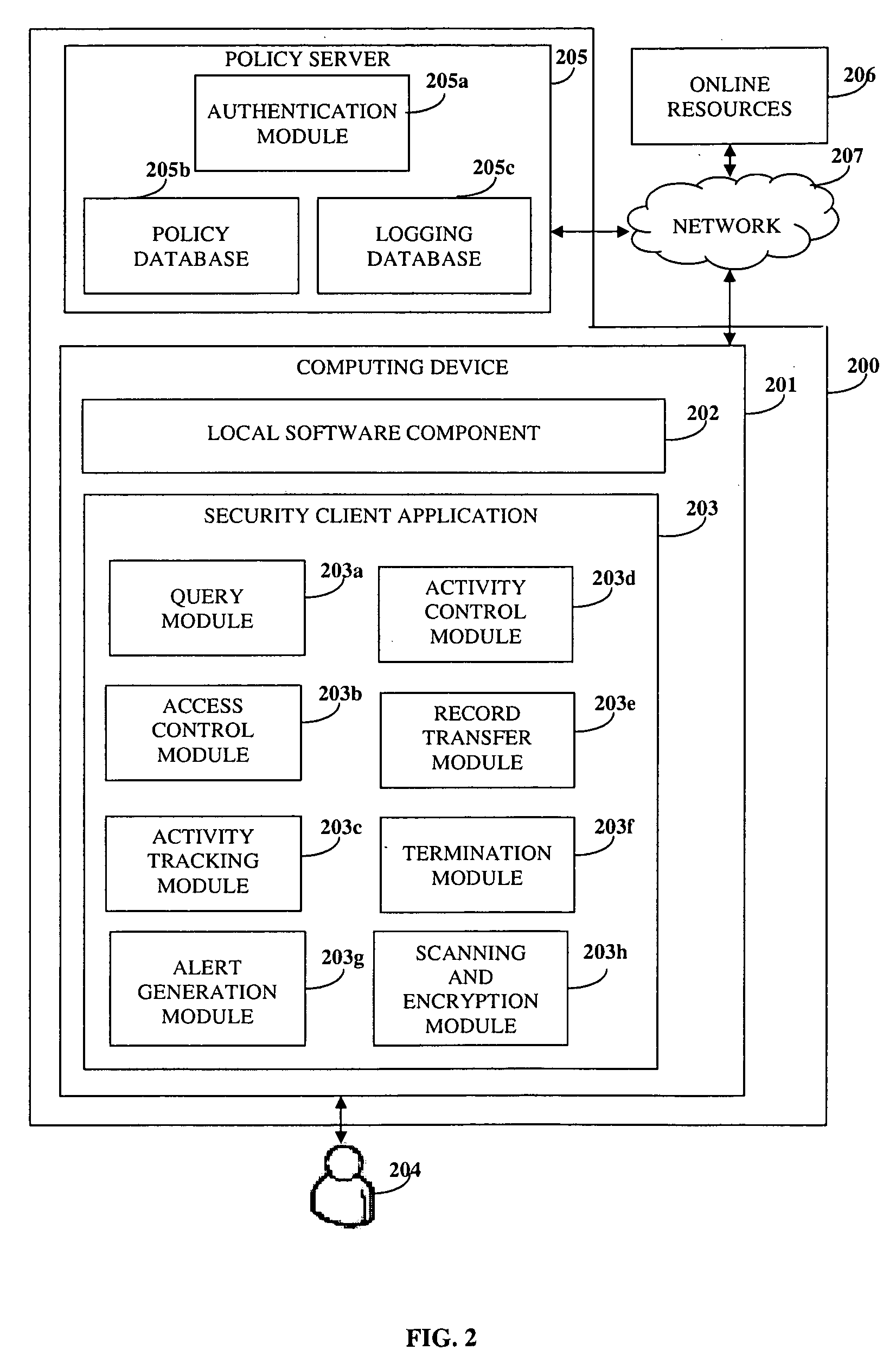
Activity Monitoring And Information Protection
InactiveUS20100125891A1Digital data processing detailsComputer security arrangementsInformation accessActivity monitoring
Disclosed herein is a computer implemented method and system for monitoring user activity and protecting information in an online environment. A security client application is provided on a computing device of a user. A local software component preloaded on the computing device is embedded within the security client application on the computing device. The security client application queries a policy server for a security policy for the user on receiving a request for access to the information from the user. The user is granted controlled access to the information based on the security policy. The granted controlled access enables enforcement of the security policy. The security client application permits the user to perform predefined activities on the information using the granted controlled access. The security client application prevents the user from performing activities apart from the predefined activities. The security client application tracks the performed predefined activities.
Owner:CISCO TECH INC
Multi-tiered structure for file sharing based on social roles
ActiveUS7529723B2Facilitate search queriesData processing applicationsDigital data processing detailsApplication softwareClient-side
An Internet-scale file sharing system includes a client-side file sharing application that allows file-sharing users to identify files to share and transmit metadata corresponding to those files to a metadata repository. A server-side application operating on the metadata repository tracks metadata received from associated file-sharing users, as well as metadata from other affiliated metadata repositories. Each metadata repository acts as a search engine for any querying users and can provide search results based on locally stored metadata alone. Each metadata repository may additionally choose to locally-store popular files from an associated file-sharing user so as to alleviate transmission burdens on that file-sharing user. Associated metadata repositories each periodically synchronize their stored metadata so that all metadata repositories may generate similar search results. In such manner, file-sharing queries need only be performed by the metadata repository receiving the query, and not by all associated metadata repositories.
Owner:XEROX CORP
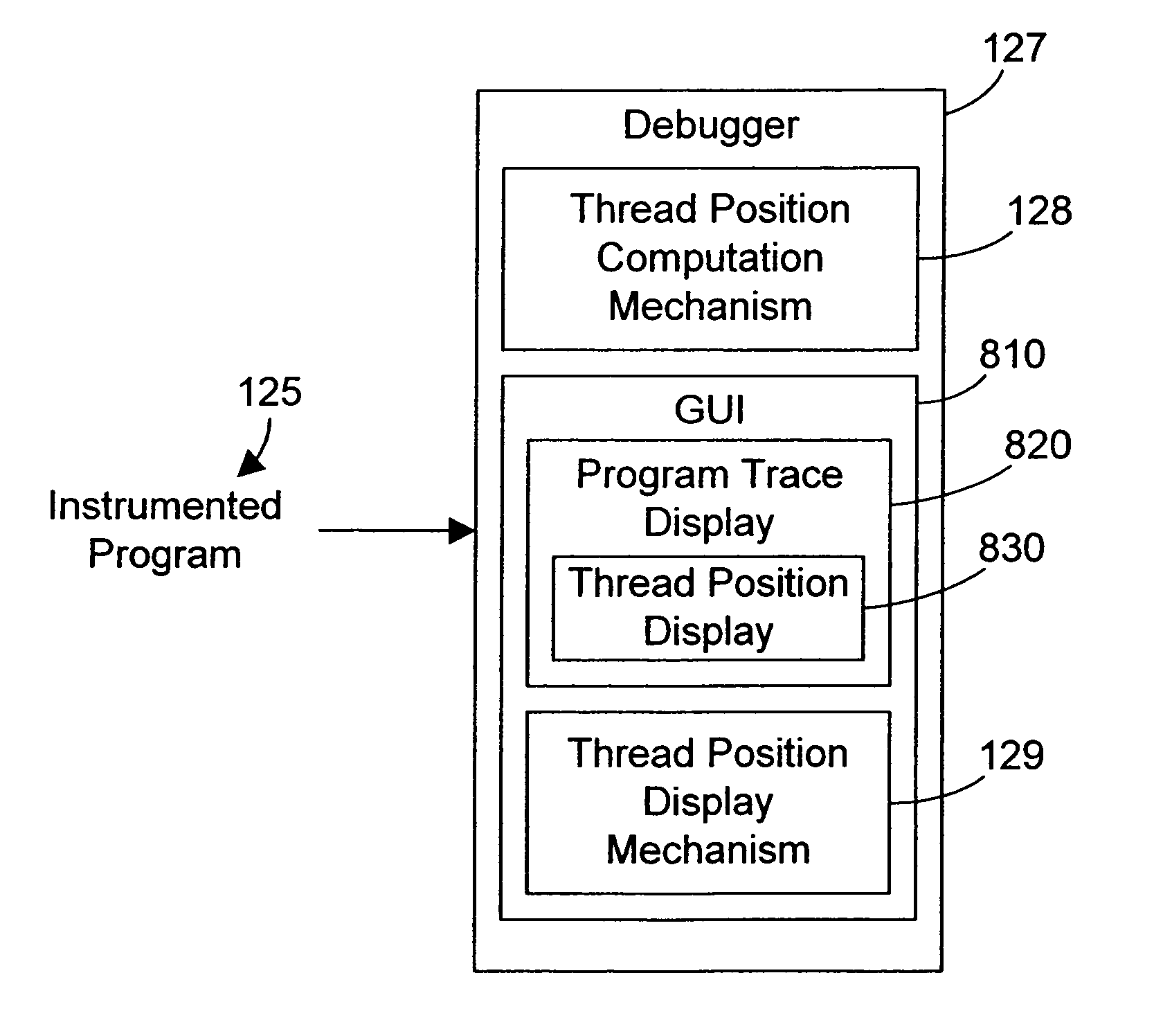
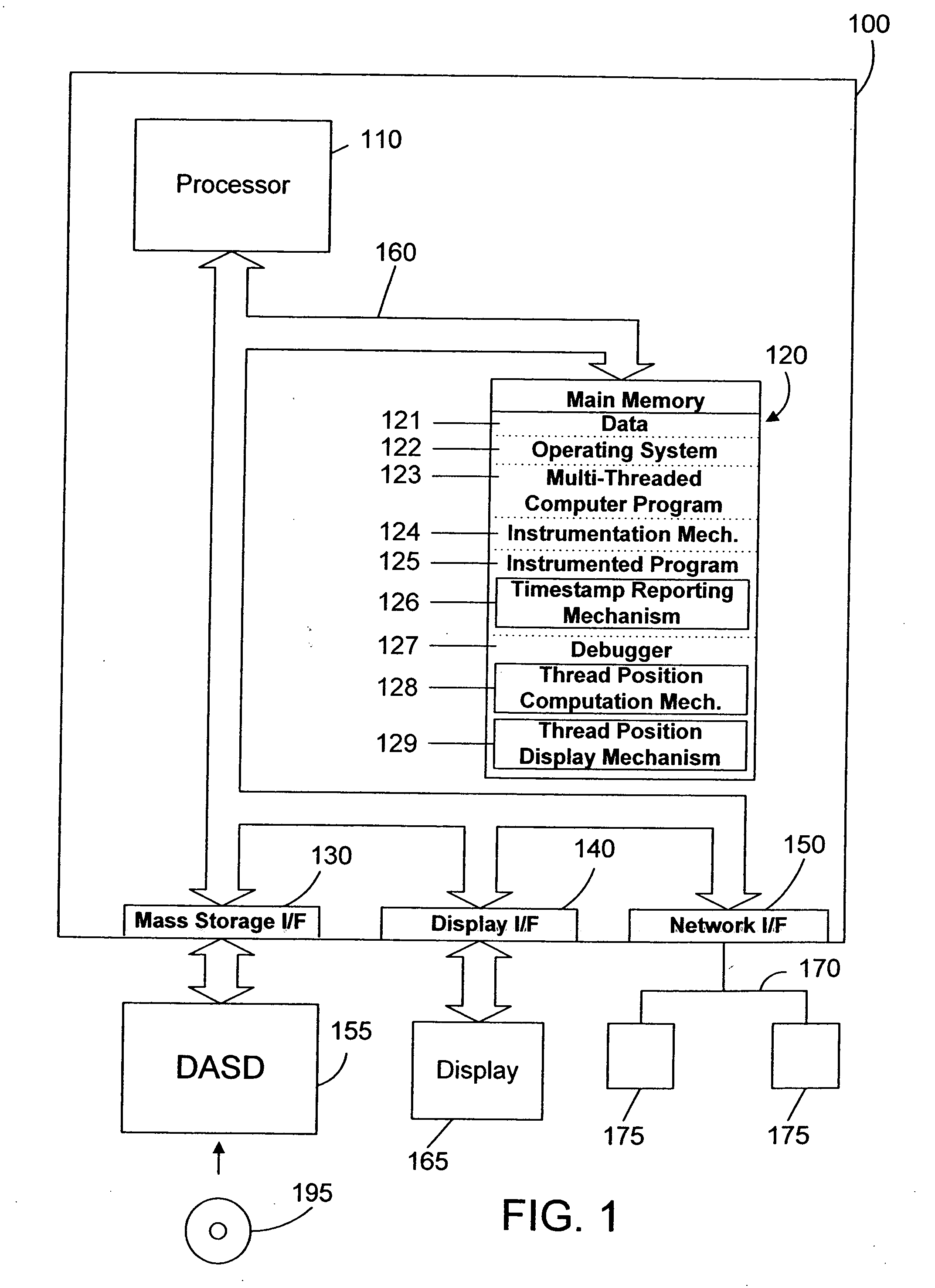
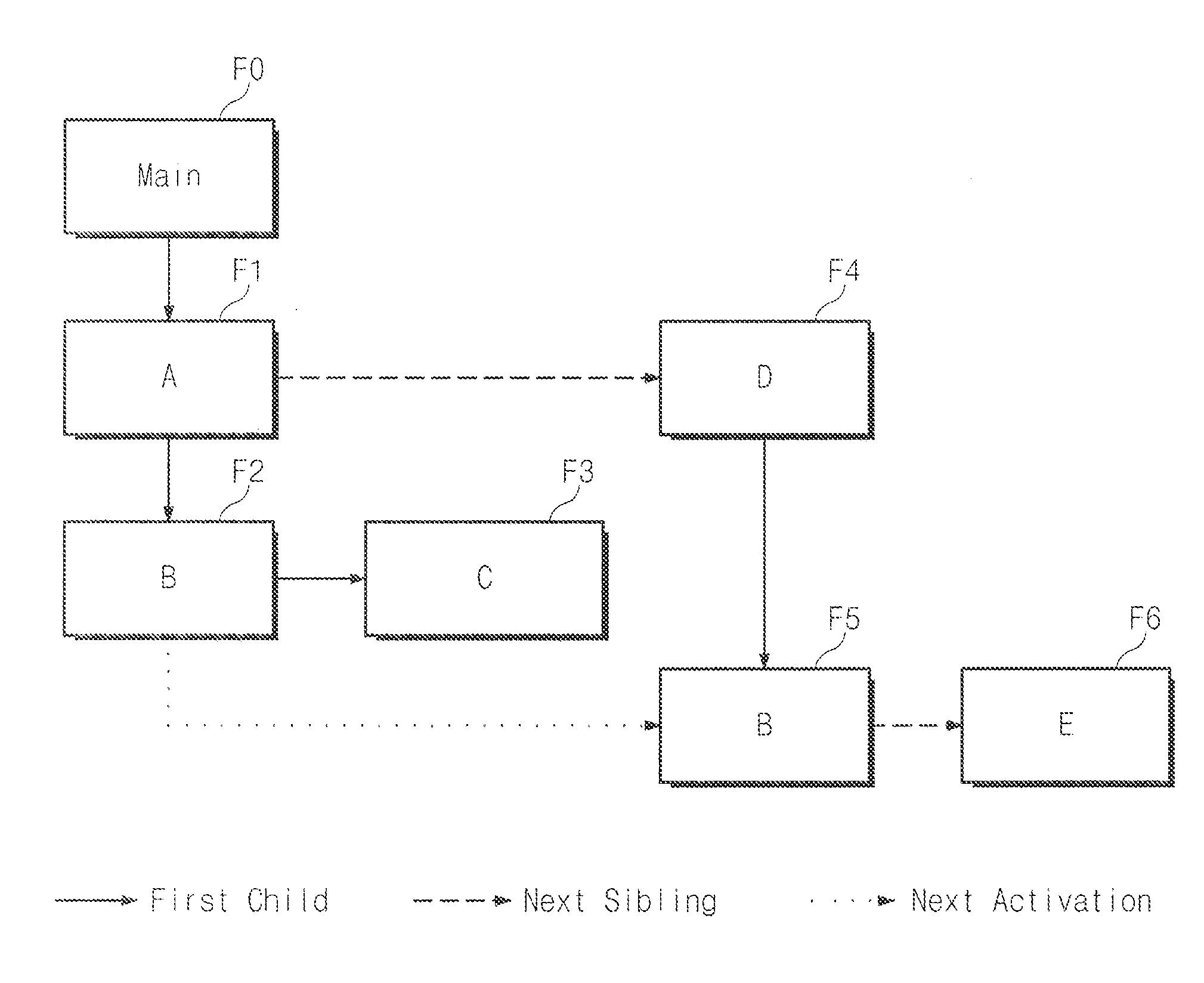
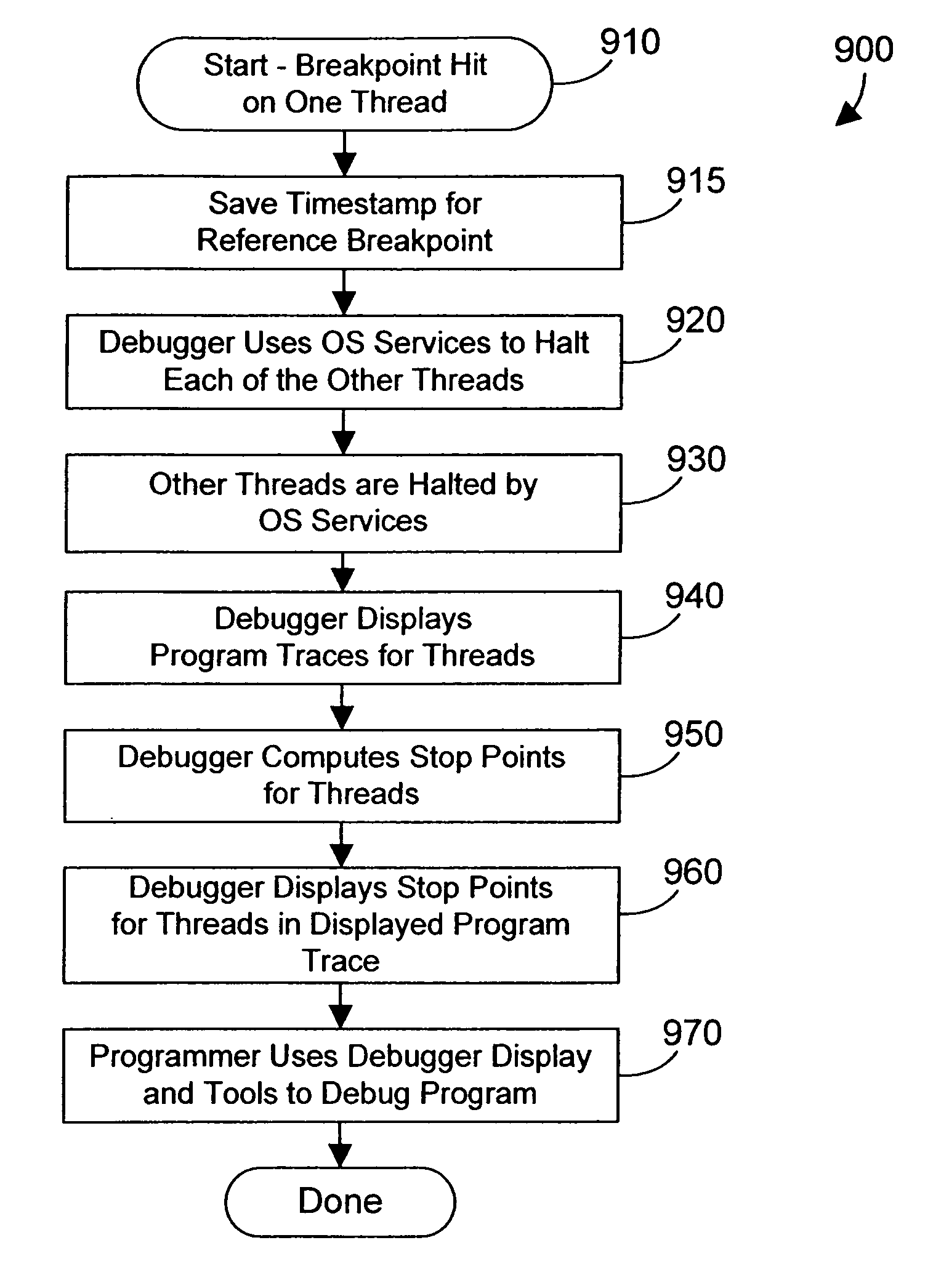
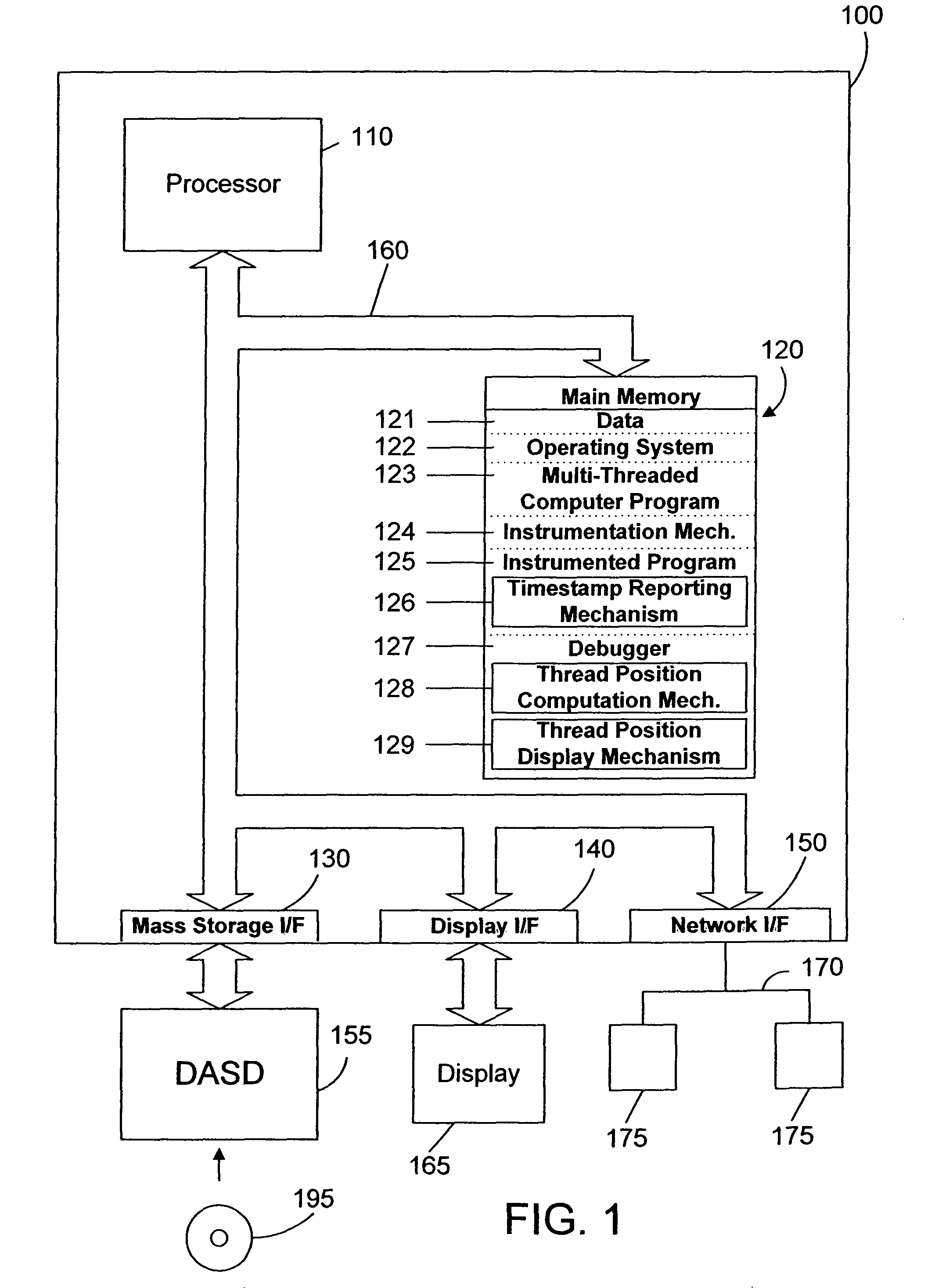
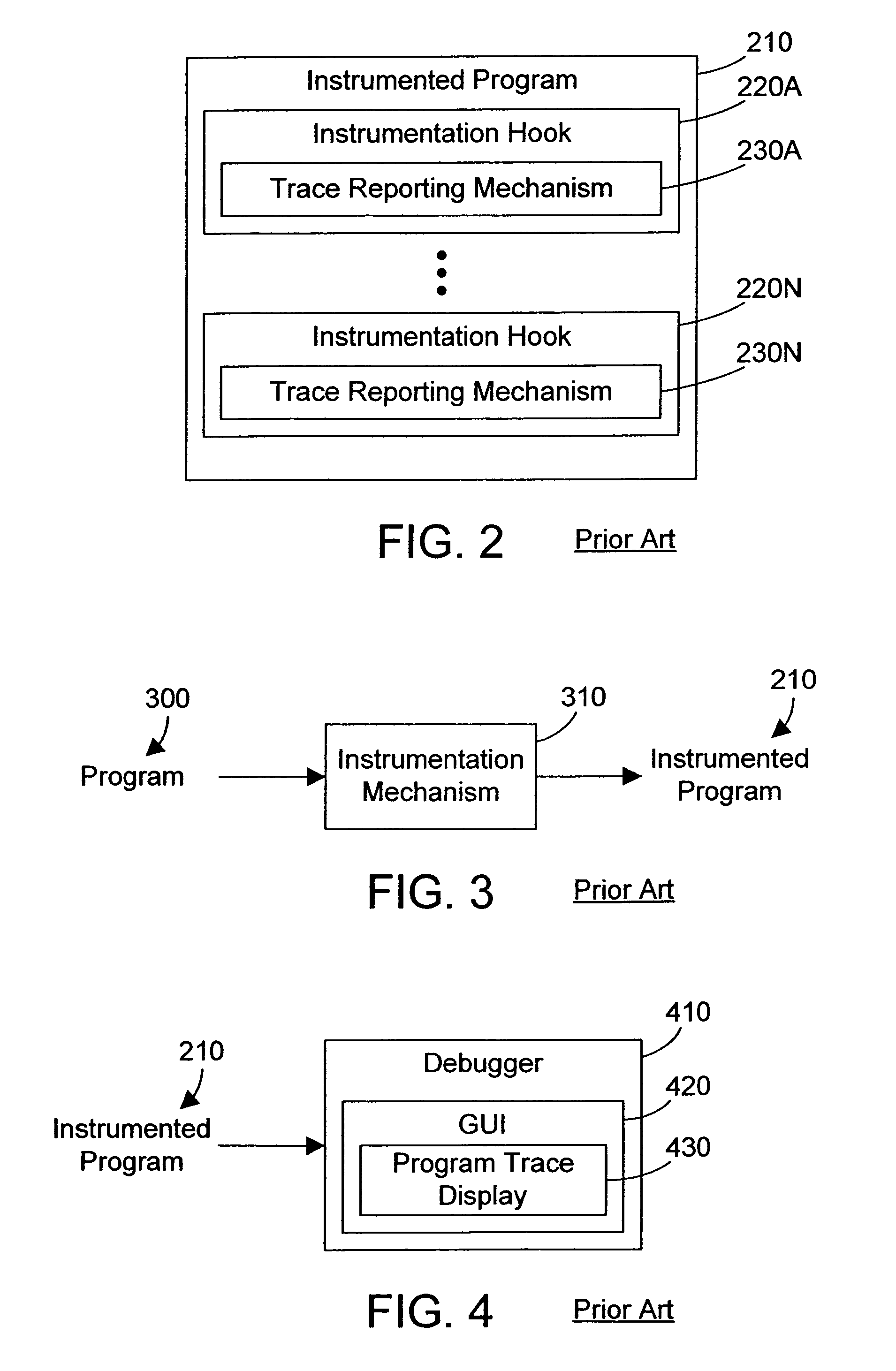
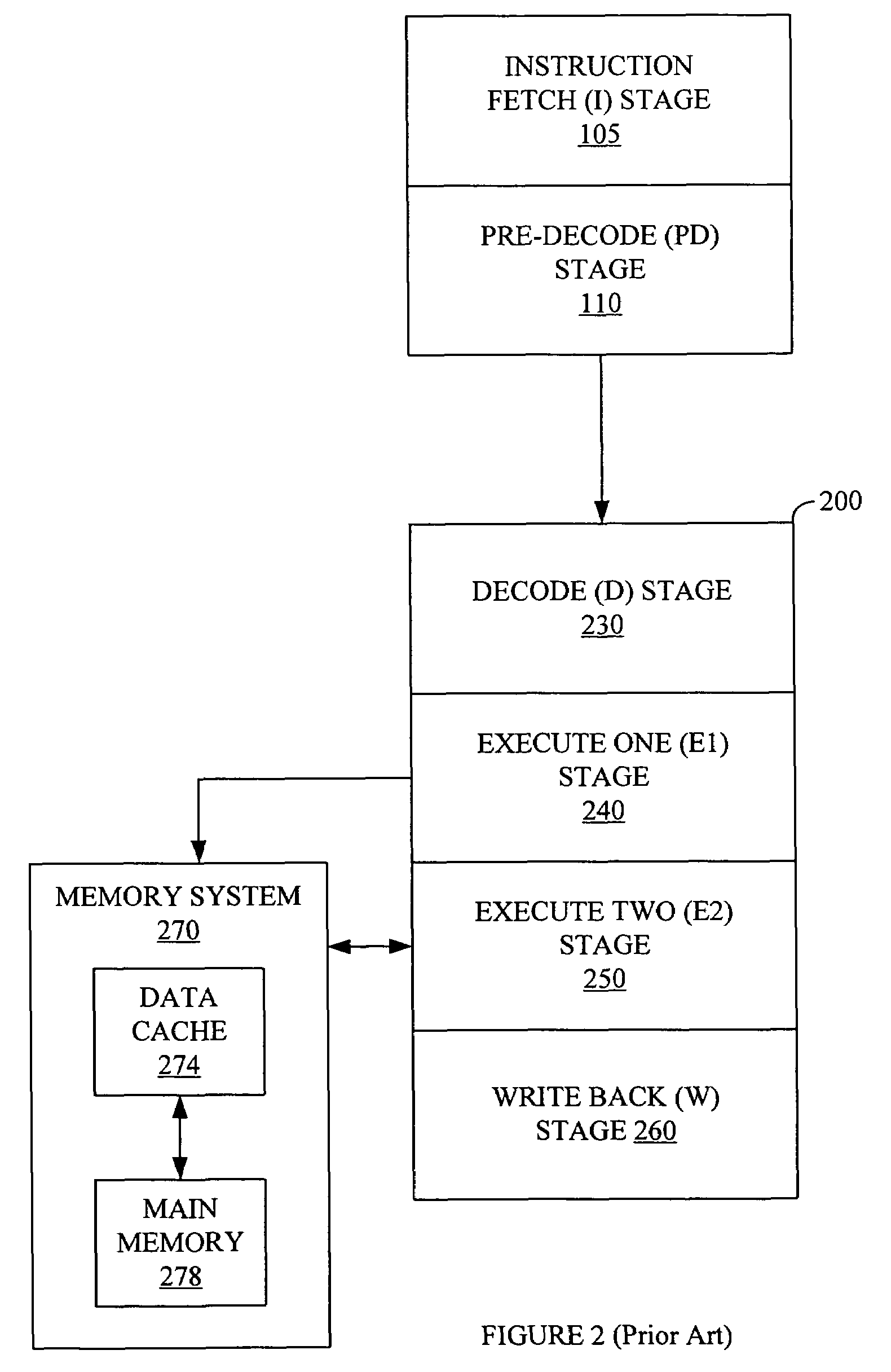
Debugger apparatus and method for indicating time-correlated position of threads in a multi-threaded computer program
InactiveUS20070168968A1Error detection/correctionSpecific program execution arrangementsTimestampProgram trace
A debugger inserts instrumentation hooks in a multi-threaded computer program that allow collecting a program trace and that provide timestamps that correspond to the program trace. When a breakpoint in a first thread is encountered, a timestamp corresponding to the breakpoint is retrieved. Execution of the other threads may continue until the debugger is able to halt their execution. Once the execution of all threads has been halted, the program trace for each thread is traced backwards to a point where the timestamp is less than the breakpoint timestamp. Instructions are then executed, one by one, until the execution time of the instructions plus the timestamp is approximately the same as the breakpoint timestamp. The instruction in the program trace display is then highlighted to indicate the instruction that was likely being executed when the breakpoint in the first thread is encountered.
Owner:IBM CORP
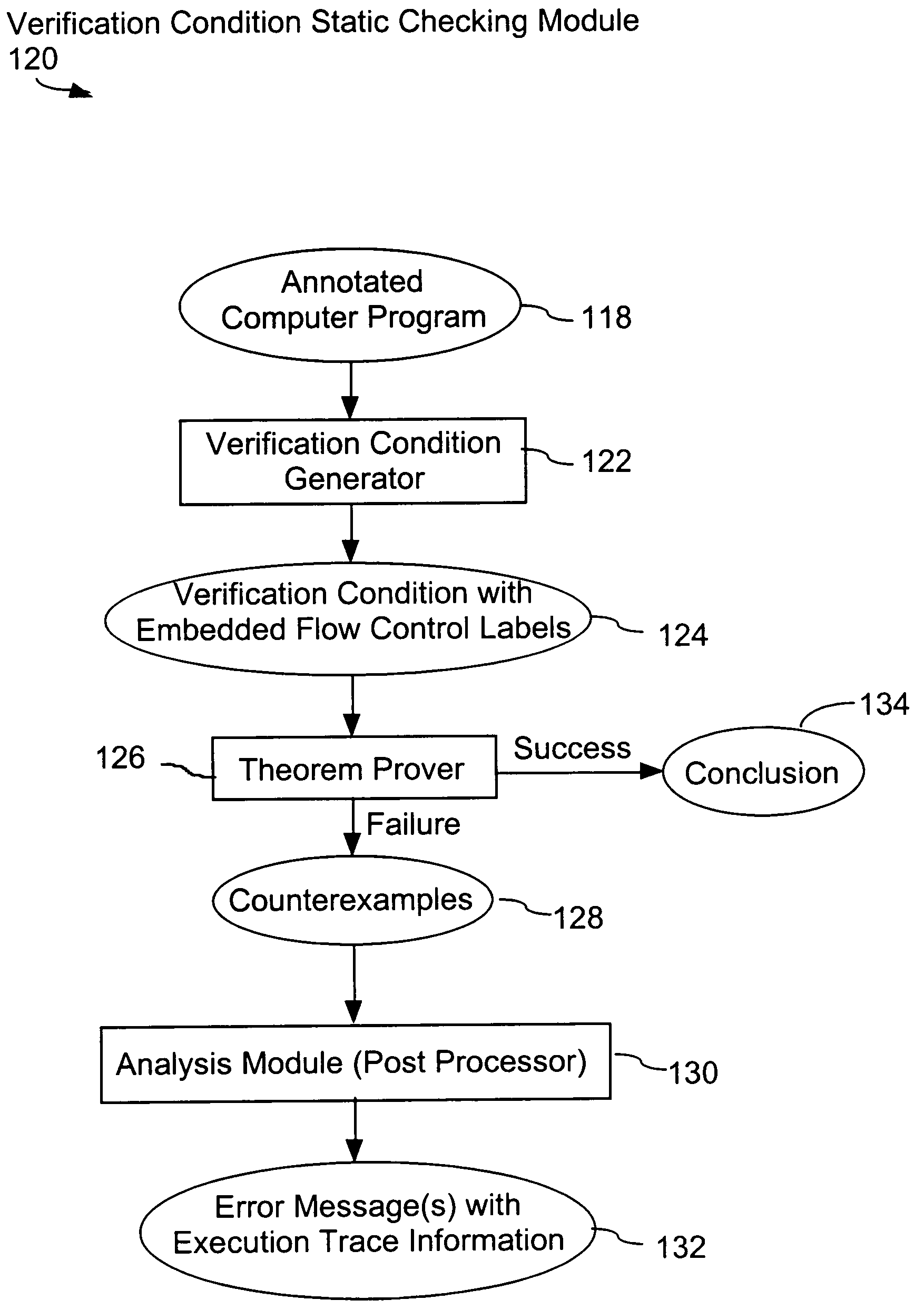
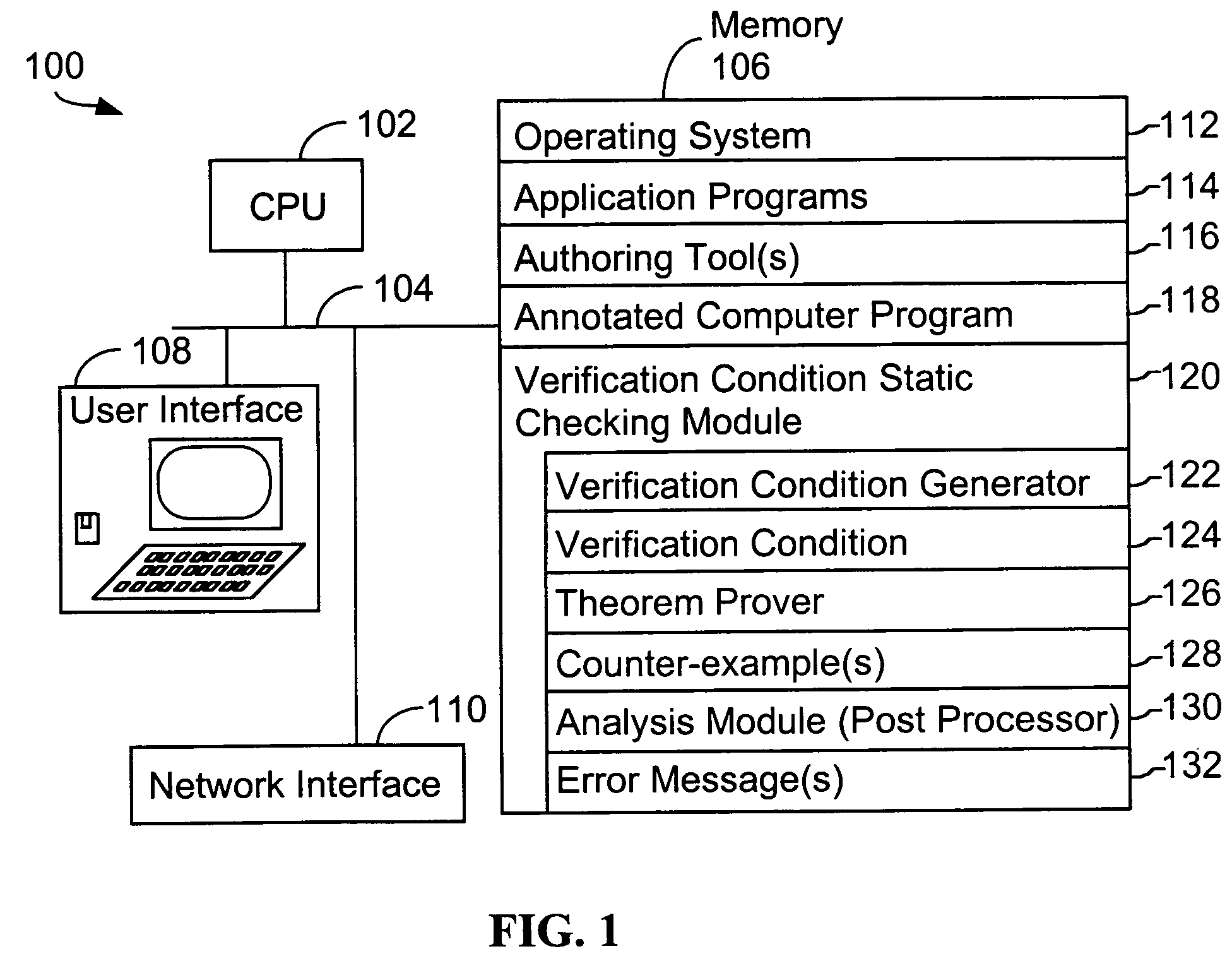
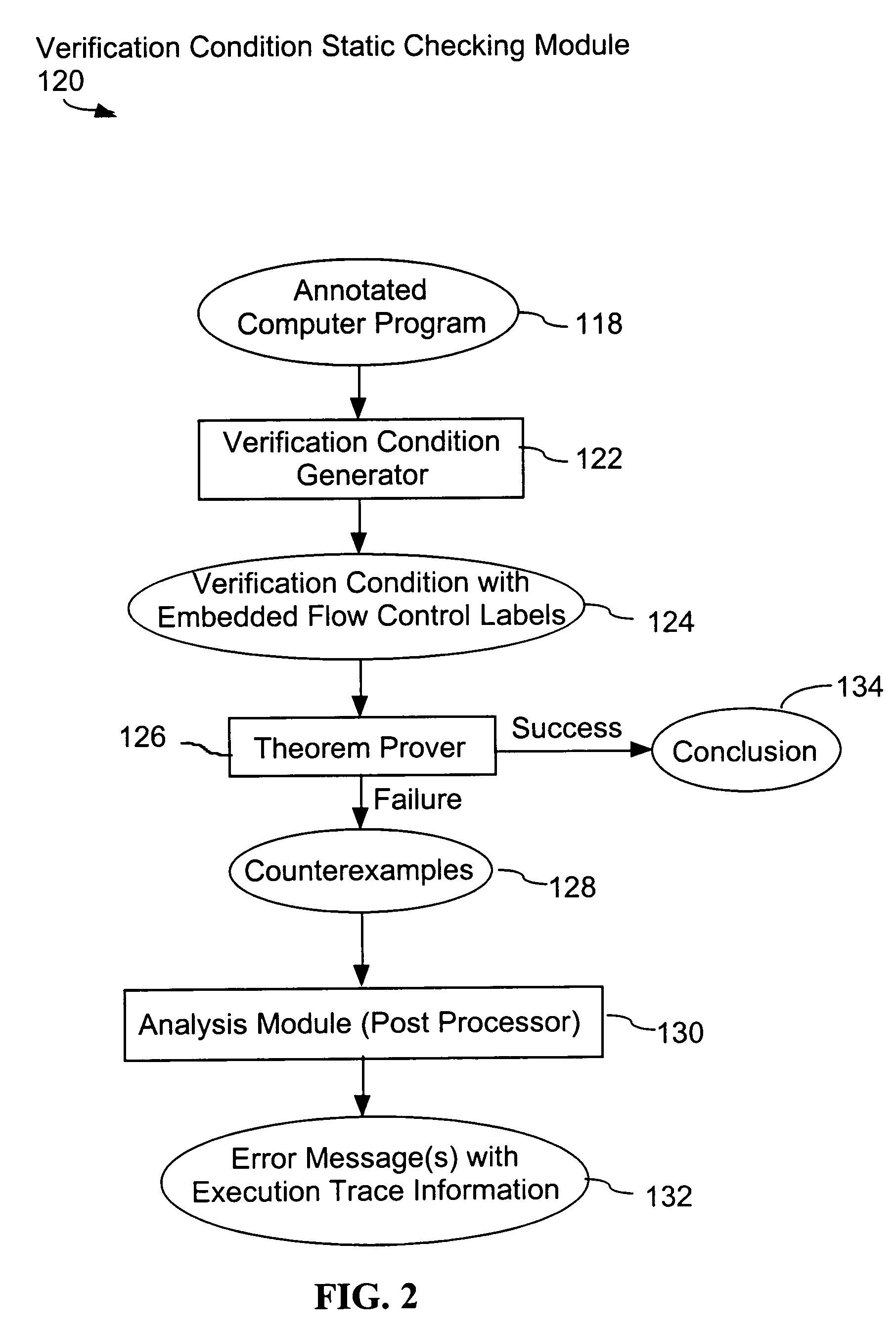
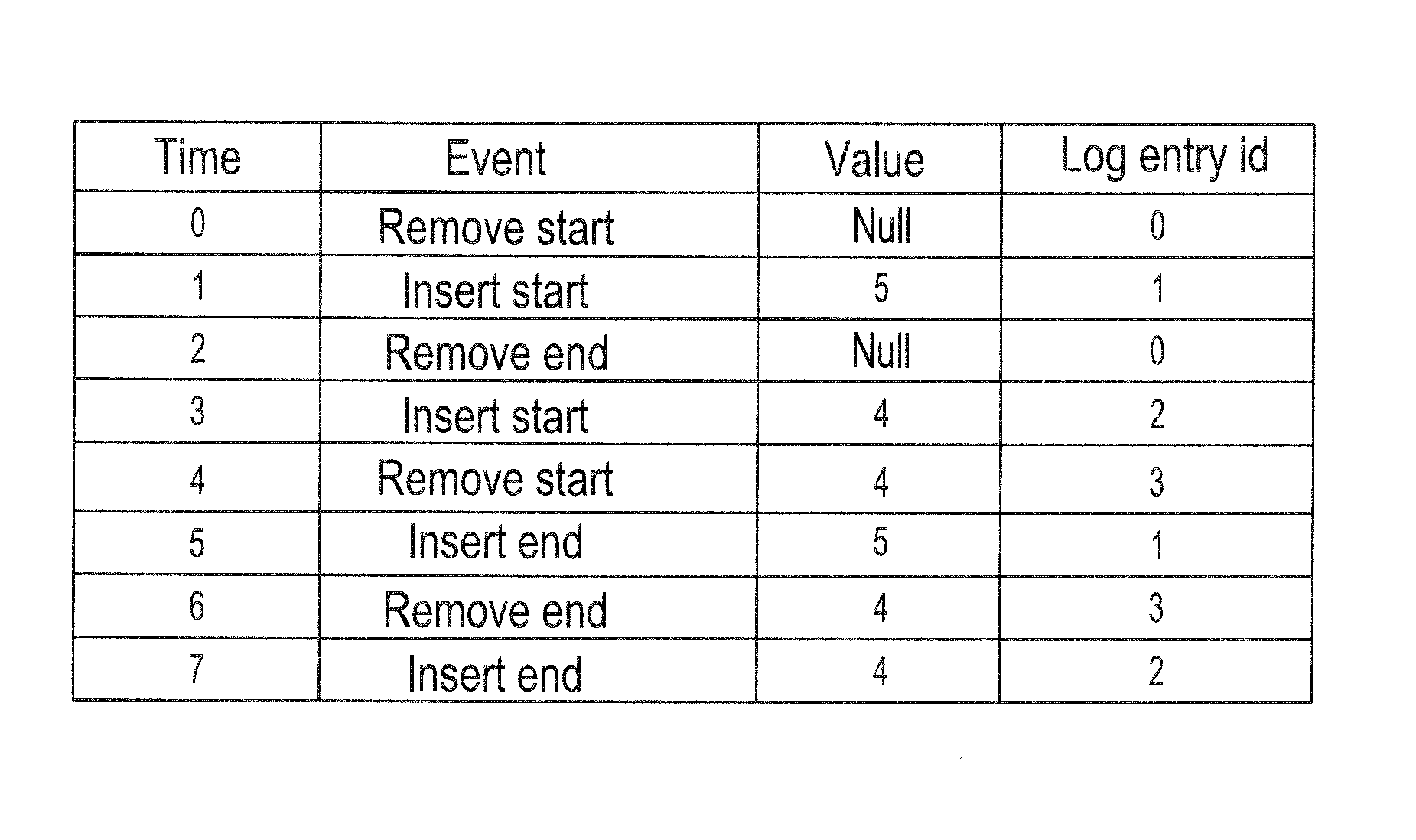
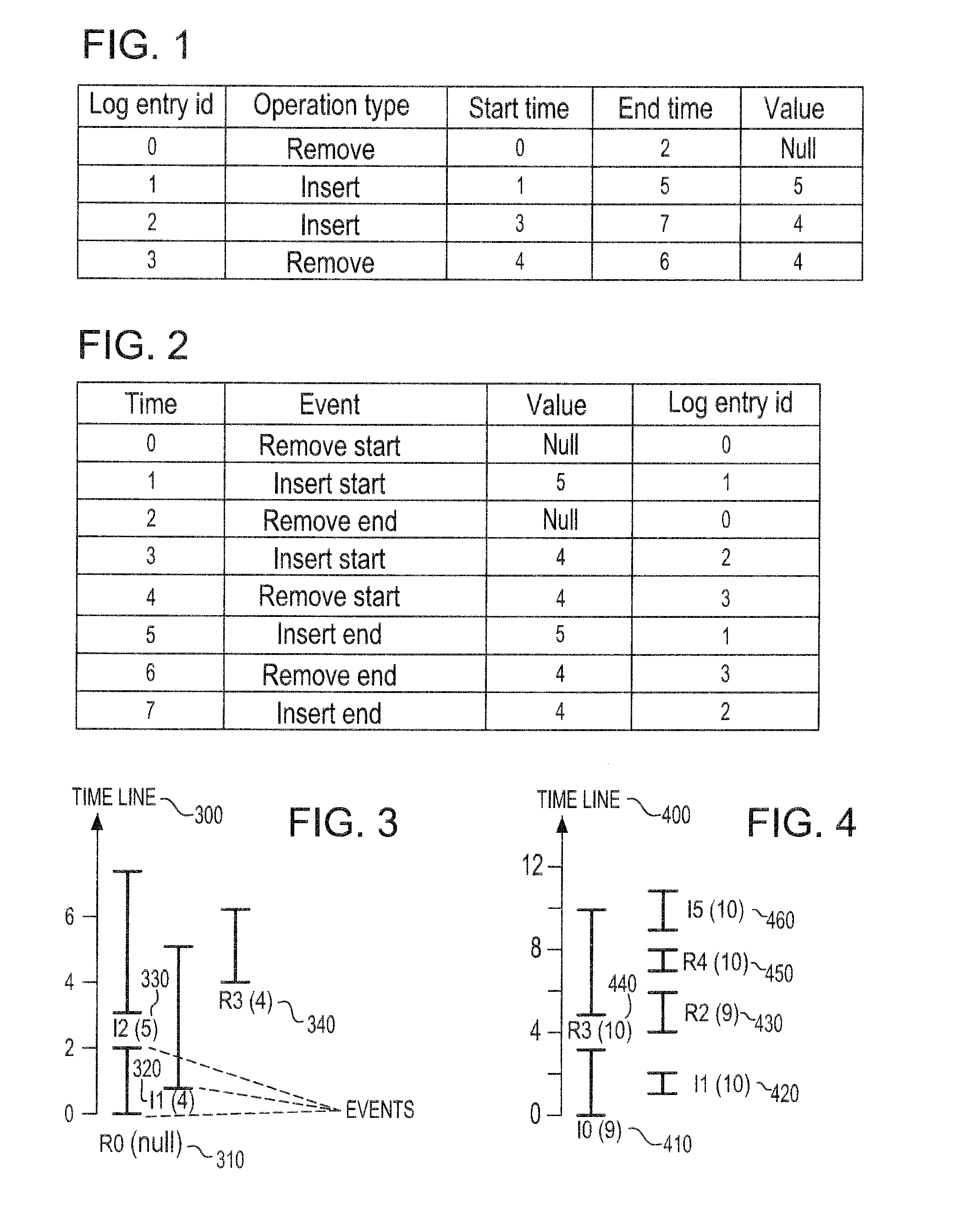
System and method for verifying computer program correctness and providing recoverable execution trace information
In a system for statically analyzing a specified computer, a verification condition generator converts the program into a logical equation, called a verification condition, and inserts program flow control labels into the sub-equations of the verification condition. The flow control labels identify conditional branch points in the specified computer program. A theorem prover is applied to the logical equation to determine truth of the logical equation, and when the truth of the logical equation cannot be proved, the theorem prover generates at least one counter-example identifying one of the conditions, one or more variable values inconsistent with that condition, and any of the flow control labels for conditional branch points of the program associated with the identified variable values. A post processing module converts each counter-example into an error message that includes a program trace when the counter-example identifies one or more of the flow control labels.
Owner:HEWLETT PACKARD DEV CO LP
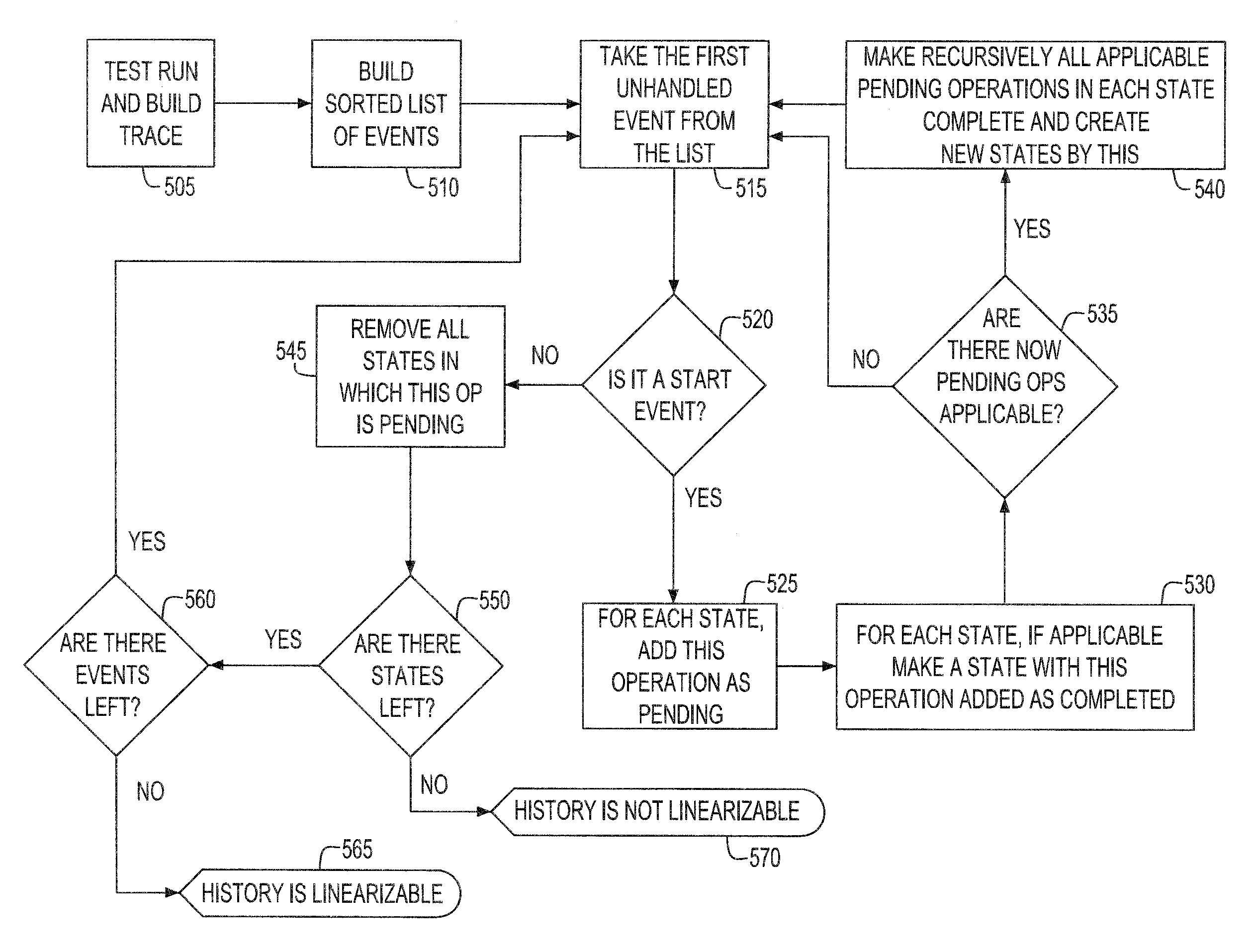
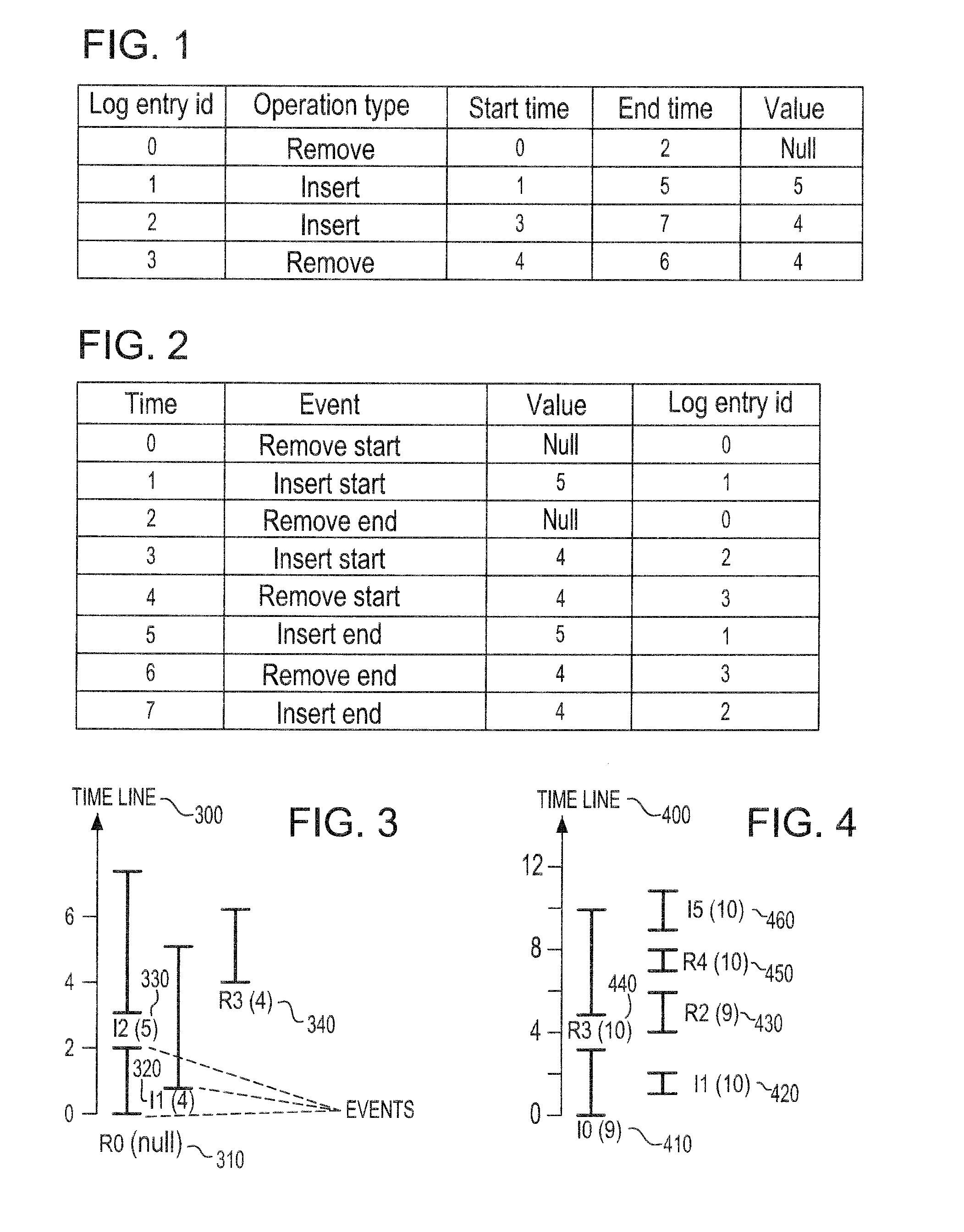
System and method for demonstrating the correctness of an execution trace in concurrent processing environments
InactiveUS20100205484A1Avoid backtrackingError detection/correctionSpecific program execution arrangementsGeneral purposeProgram trace
Since multi-core processors have become the standard architecture for general purpose machines, programmers are required to write software optimized for parallelism. Verification of correctness is an important issue for parallel code because of its complexity. There are still tools missing that provide verification for complex code, such as testing the execution of code provides. Consequently, described herein are systems and methods to evaluate the correctness of program traces. Furthermore, the systems and methods described herein do not demand excessive computational requirements and the size of the program trace being evaluated increases.
Owner:GLOBALFOUNDRIES INC
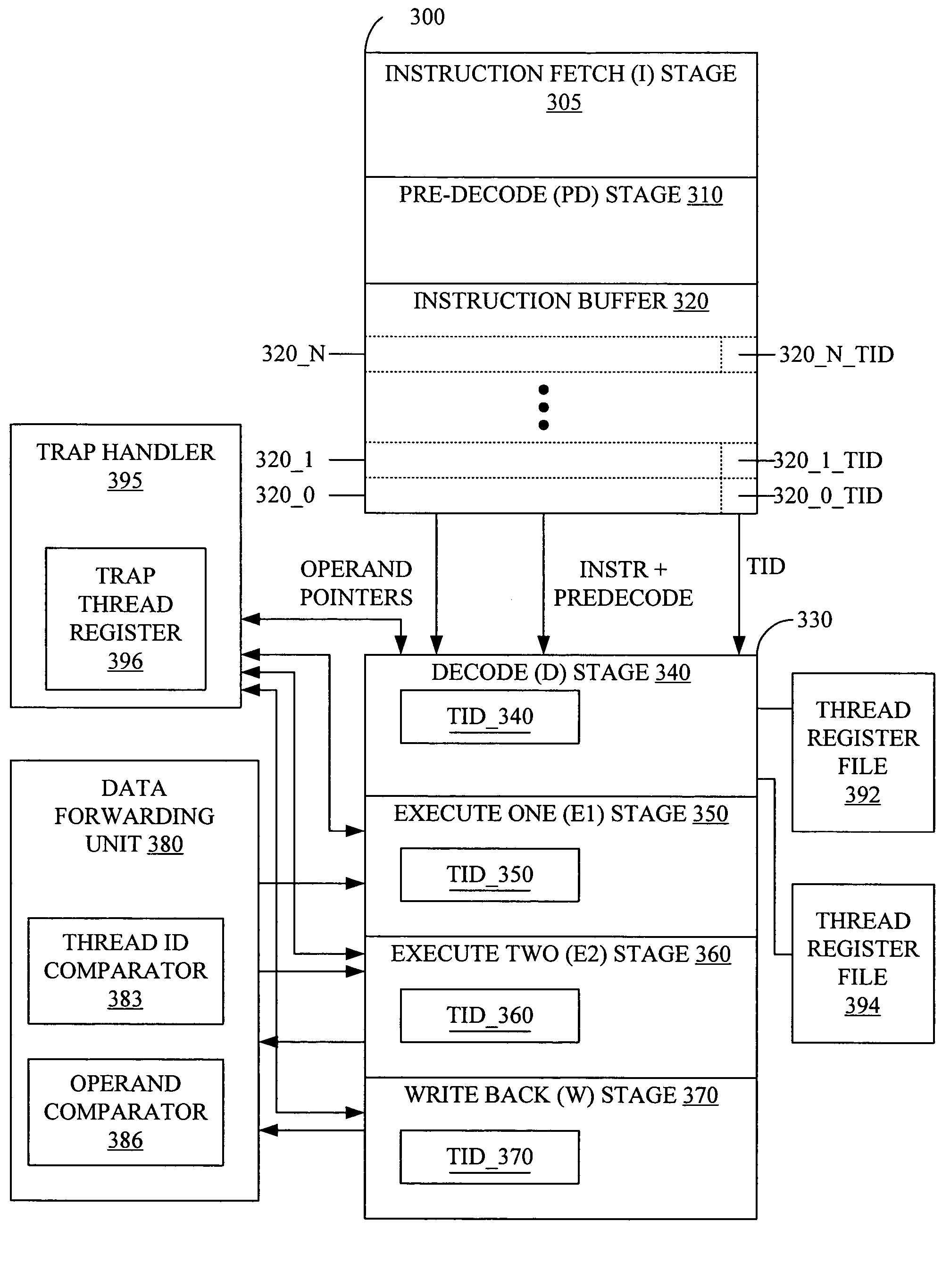
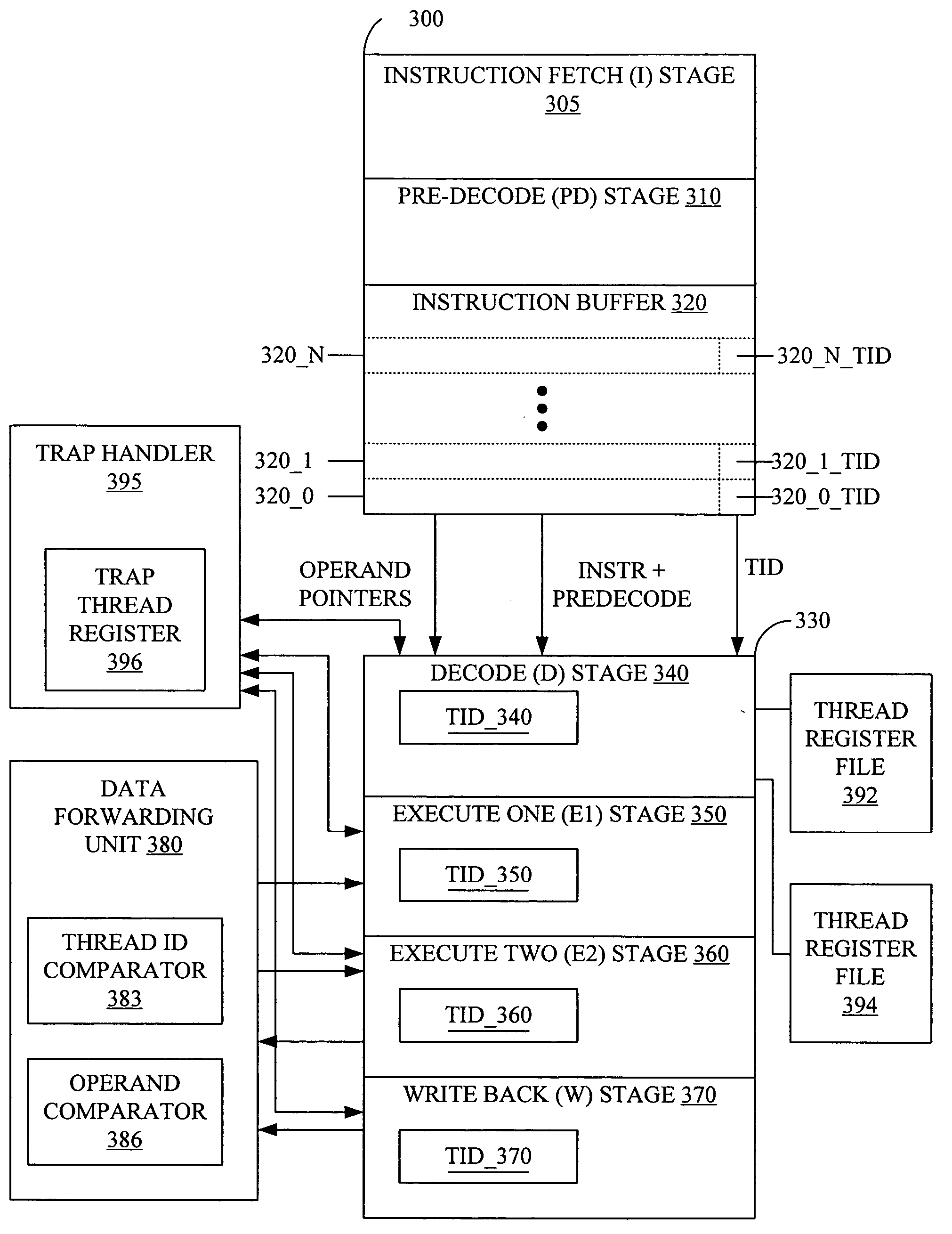
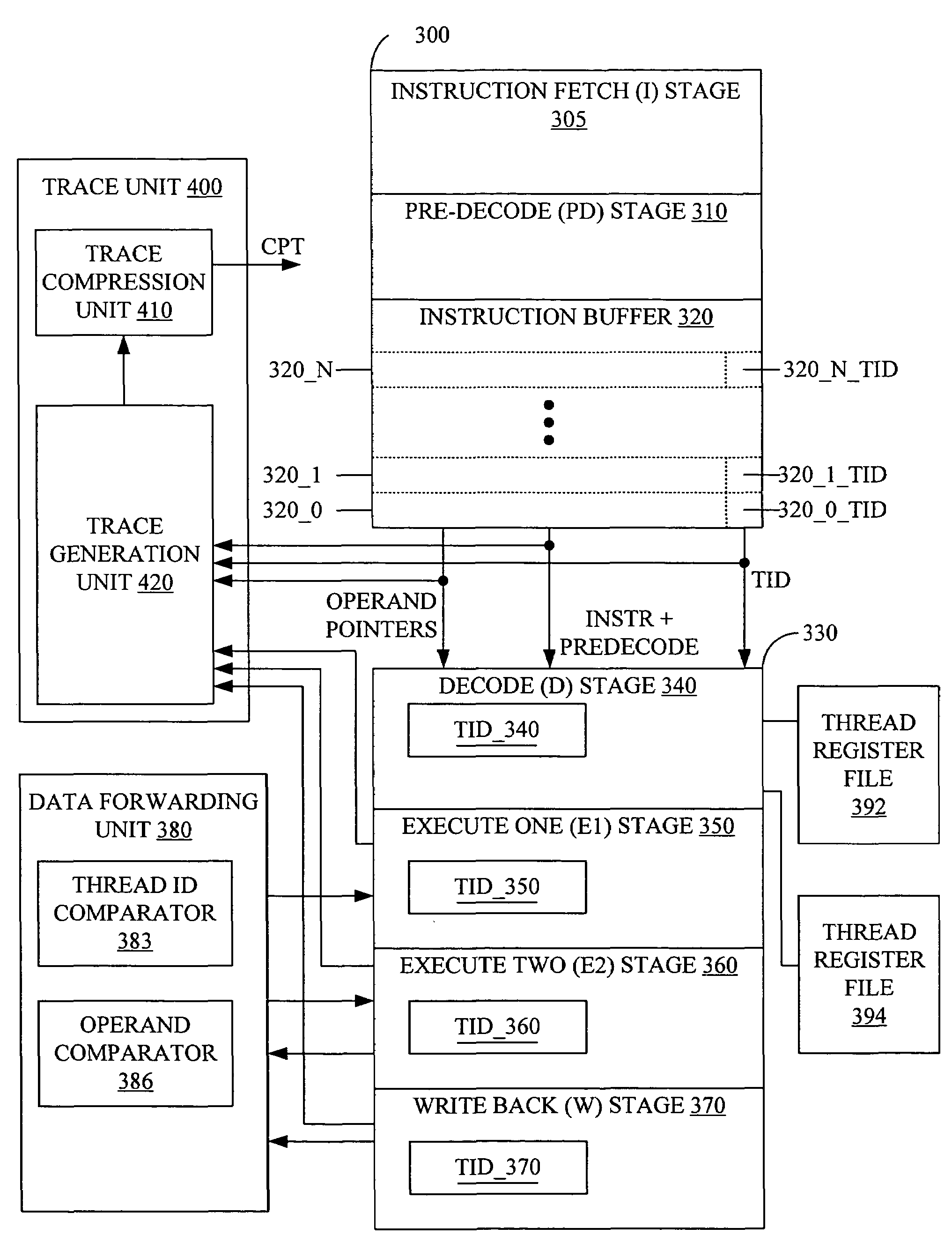
Thread ID in a multithreaded processor
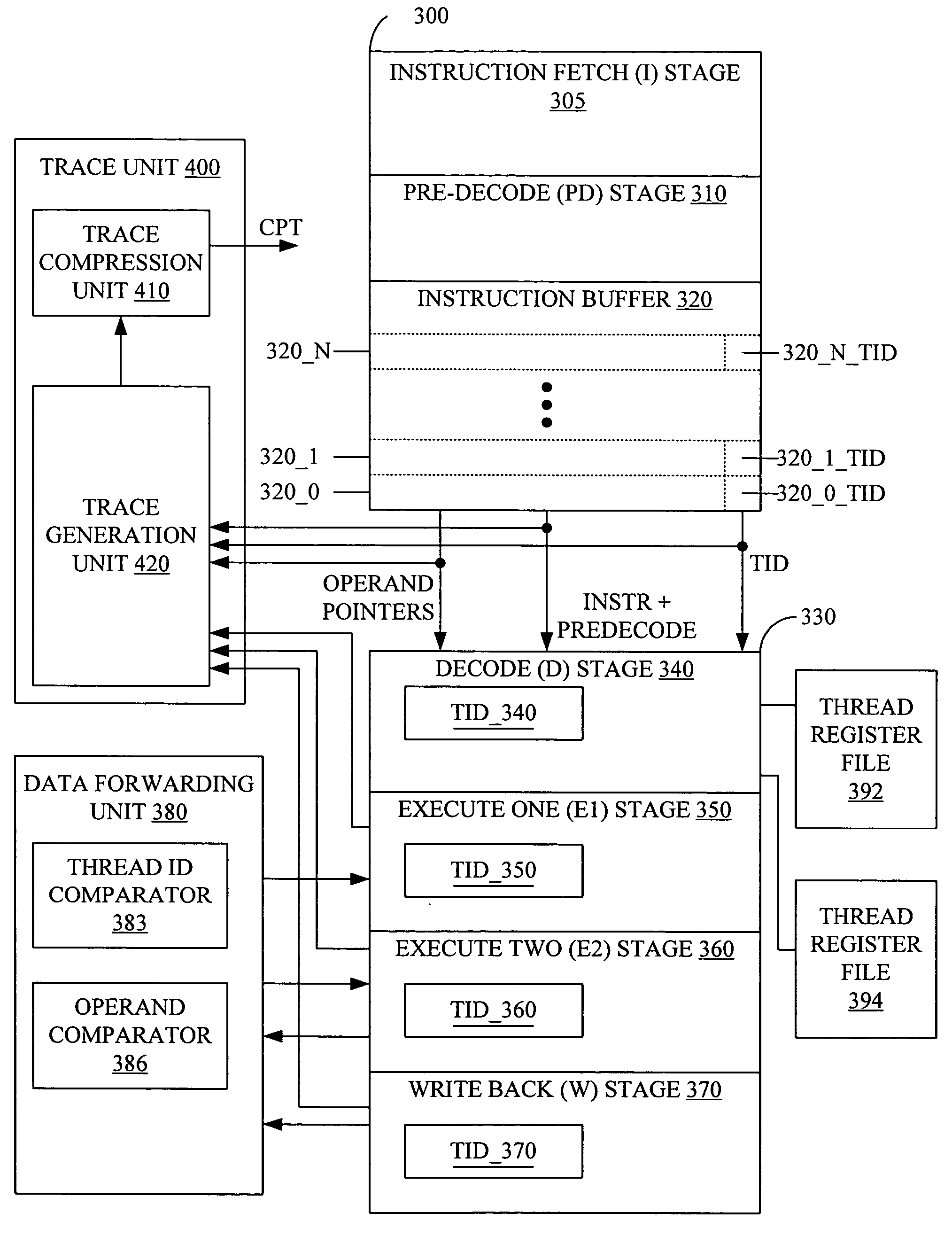
ActiveUS7263599B2Easy maintenanceHinder resolutionProgram initiation/switchingDigital computer detailsOperandProgram trace
A multithreaded processor includes a thread ID for each set of fetched bits in an instruction fetch and issue unit. The thread ID attaches to the instructions and operands of the set of fetched bits. Pipeline stages in the multithreaded processor stores the thread ID associated with each operand or instruction in the pipeline stage. The thread ID are used to maintain data coherency and to generate program traces that include thread information for the instructions executed by the multithreaded processor.
Owner:INFINEON TECH AG
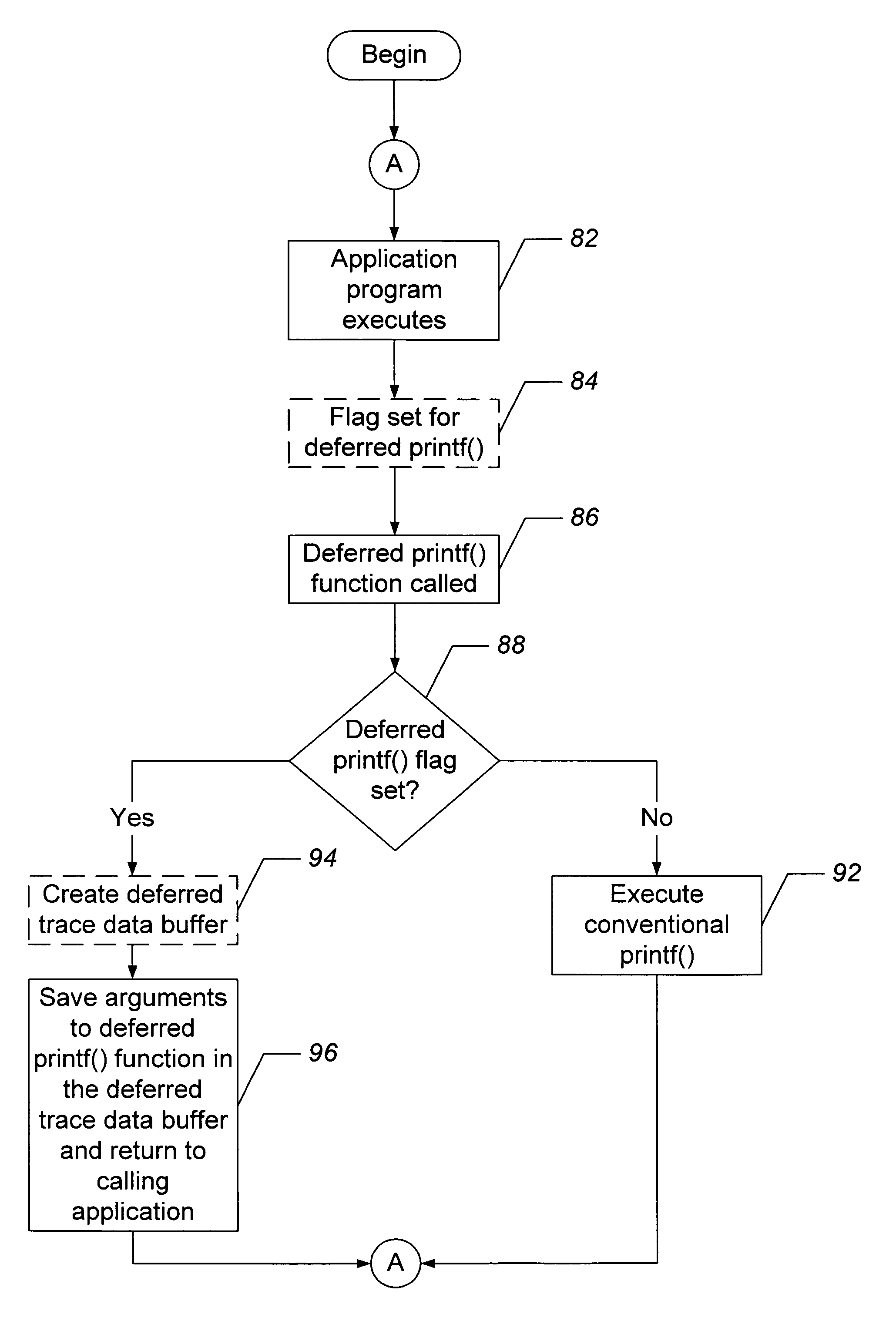
Methods, systems, and computer program products for deferred computer program tracing
ActiveUS7240334B1Improve programming efficiencyReduce the impactError detection/correctionSpecific program execution arrangementsProgram EfficiencyApplication software
An application (e.g., a computer program) prints data by invoking a print function with a format argument and, optionally, at least one data argument. The format argument and any data arguments are saved in a deferred trace data buffer. The print function returns to the application then, sometime after the print function has returned, the deferred trace data buffer is processed and the format argument and / or any data arguments are printed. By saving the format argument and any data argument(s) to a memory buffer instead of parsing and formatting the arguments in real-time, program efficiency may be improved and the impact of the print function on a software test scenario may be reduced.
Owner:TOSHIBA GLOBAL COMMERCE SOLUTIONS HLDG
Thread ID in a multithreaded processor
ActiveUS20050177703A1Easy maintenanceHinder resolutionProgram initiation/switchingDigital computer detailsOperandProgram trace
A multithreaded processor includes a thread ID for each set of fetched bits in an instruction fetch and issue unit. The thread ID attaches to the instructions and operands of the set of fetched bits. Pipeline stages in the multithreaded processor stores the thread ID associated with each operand or instruction in the pipeline stage. The thread ID are used to maintain data coherency and to generate program traces that include thread information for the instructions executed by the multithreaded processor.
Owner:INFINEON TECH AG
Program tracing in a multithreaded processor
ActiveUS20050177819A1Easy maintenanceHinder resolutionProgram initiation/switchingConcurrent instruction executionOperandProgram trace
A multithreaded processor includes a thread ID for each set of fetched bits in an instruction fetch and issue unit. The thread ID attaches to the instructions and operands of the set of fetched bits. Pipeline stages in the multithreaded processor stores the thread ID associated with each operand or instruction in the pipeline stage. The thread ID are used to maintain data coherency and to generate program traces that include thread information for the instructions executed by the multithreaded processor.
Owner:INFINEON TECH AG
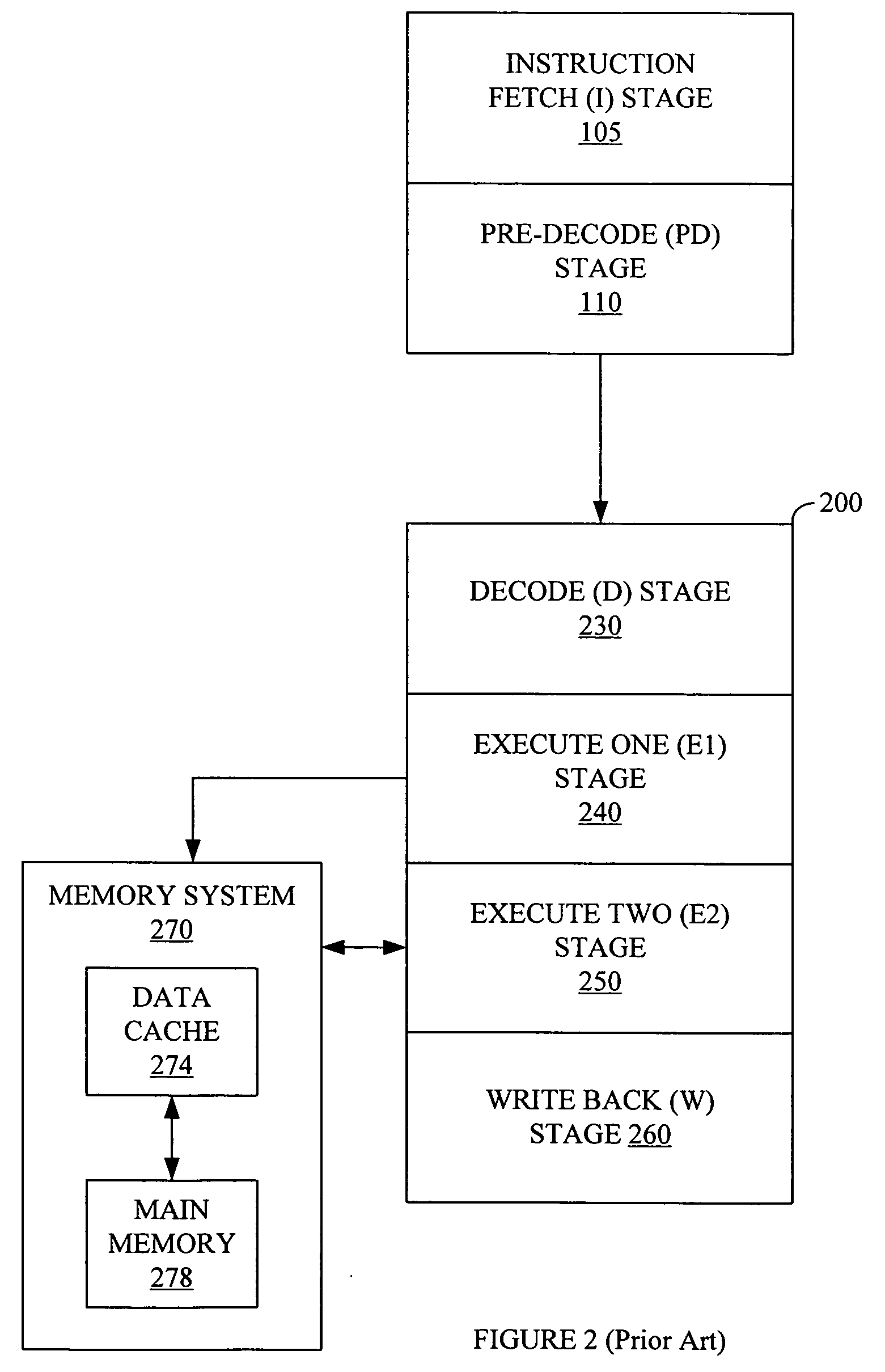
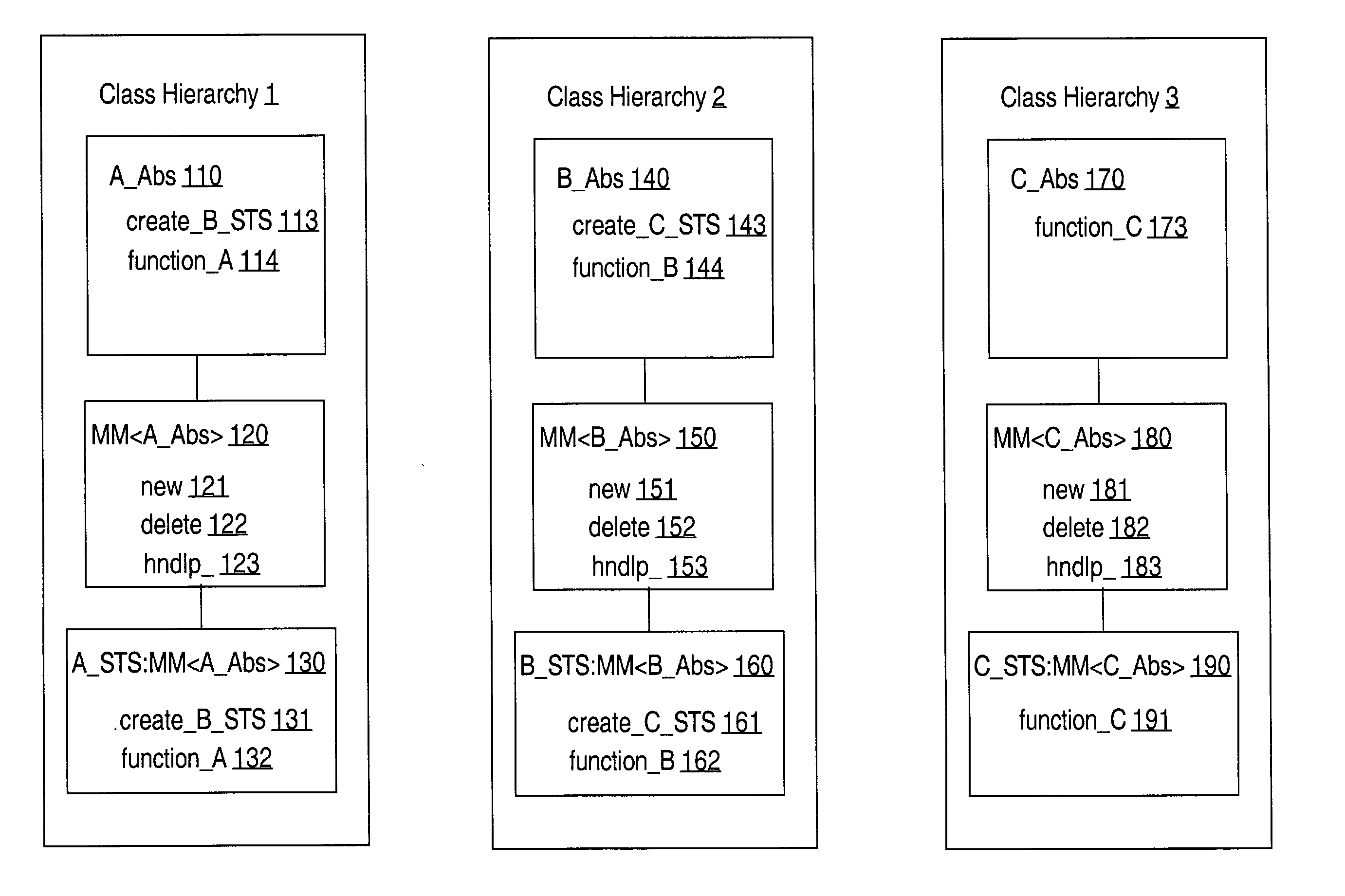
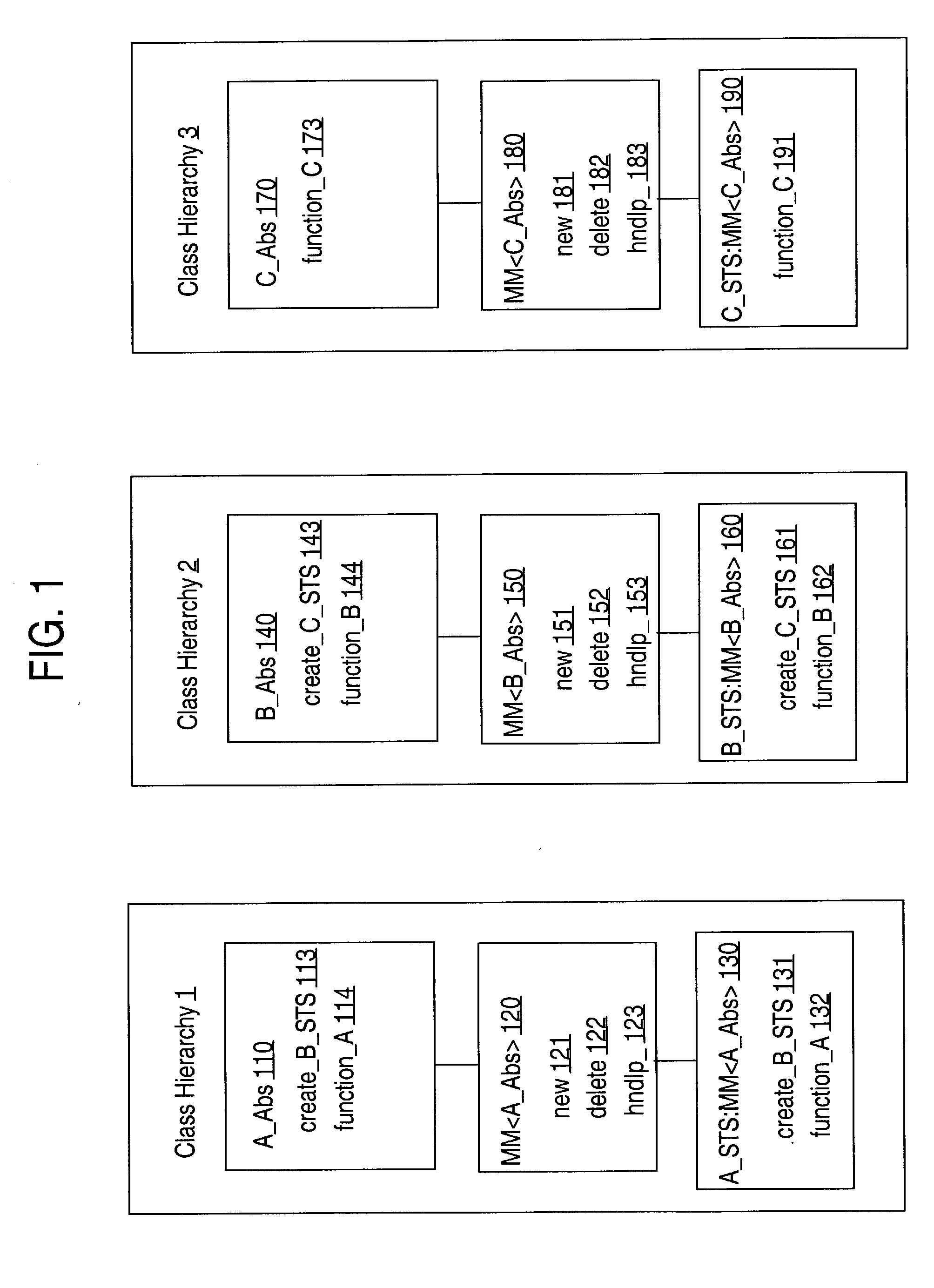
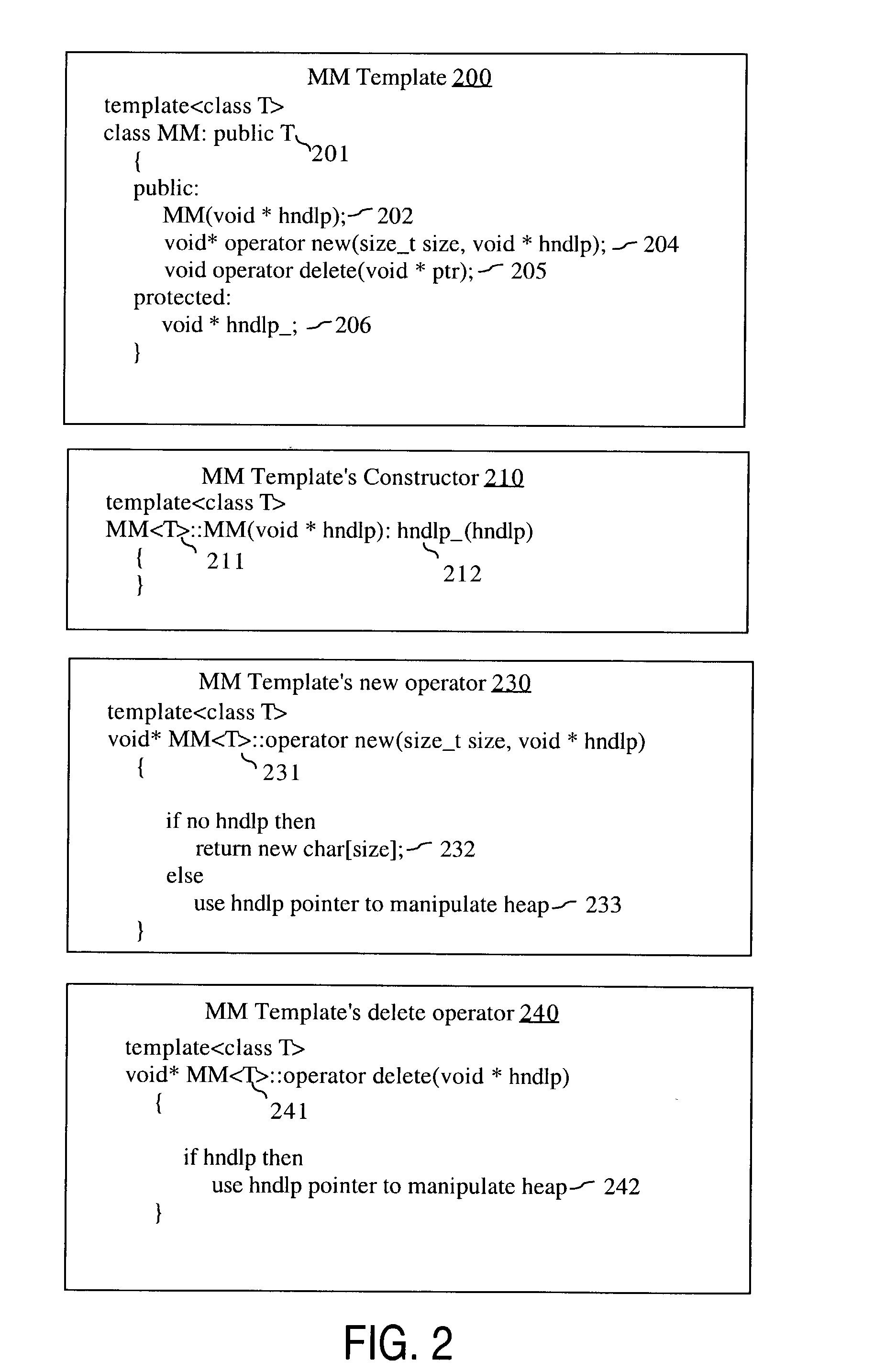
Providing common memory management code to objects that are instances of different classes
ActiveUS20050177836A1Memory adressing/allocation/relocationMultiprogramming arrangementsTerm memoryProgram trace
A method for providing memory management for objects is described. Specifically, techniques are described for providing common memory management code to objects that are instances of different classes and for releasing a memory management subtree that starts with a particular object in the memory management tree. A memory management template provides common pre-processor memory management code. A specialized version of the memory management template is used to create a specialized template subclass. When a memory management operator of an object that is an instance of the specialized template subclass is invoked the common memory management code in the specialized template is executed. Memory is associated with each object in a hierarchical tree. Data for the memory is maintained that reflects the hierarchical tree relationship between the objects. A subtree and the associated memory can be released without an application program tracking the relationships.
Owner:ORACLE INT CORP
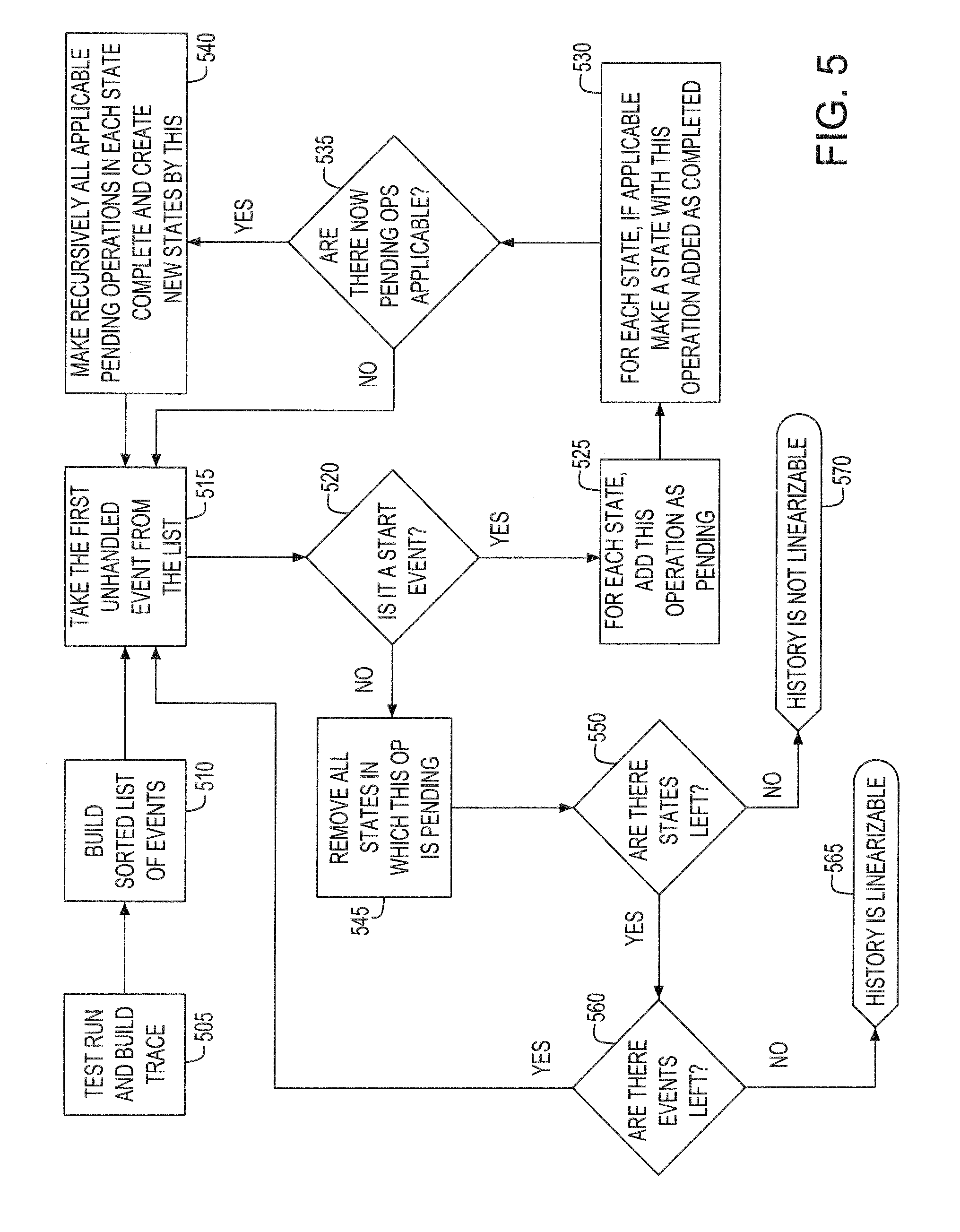
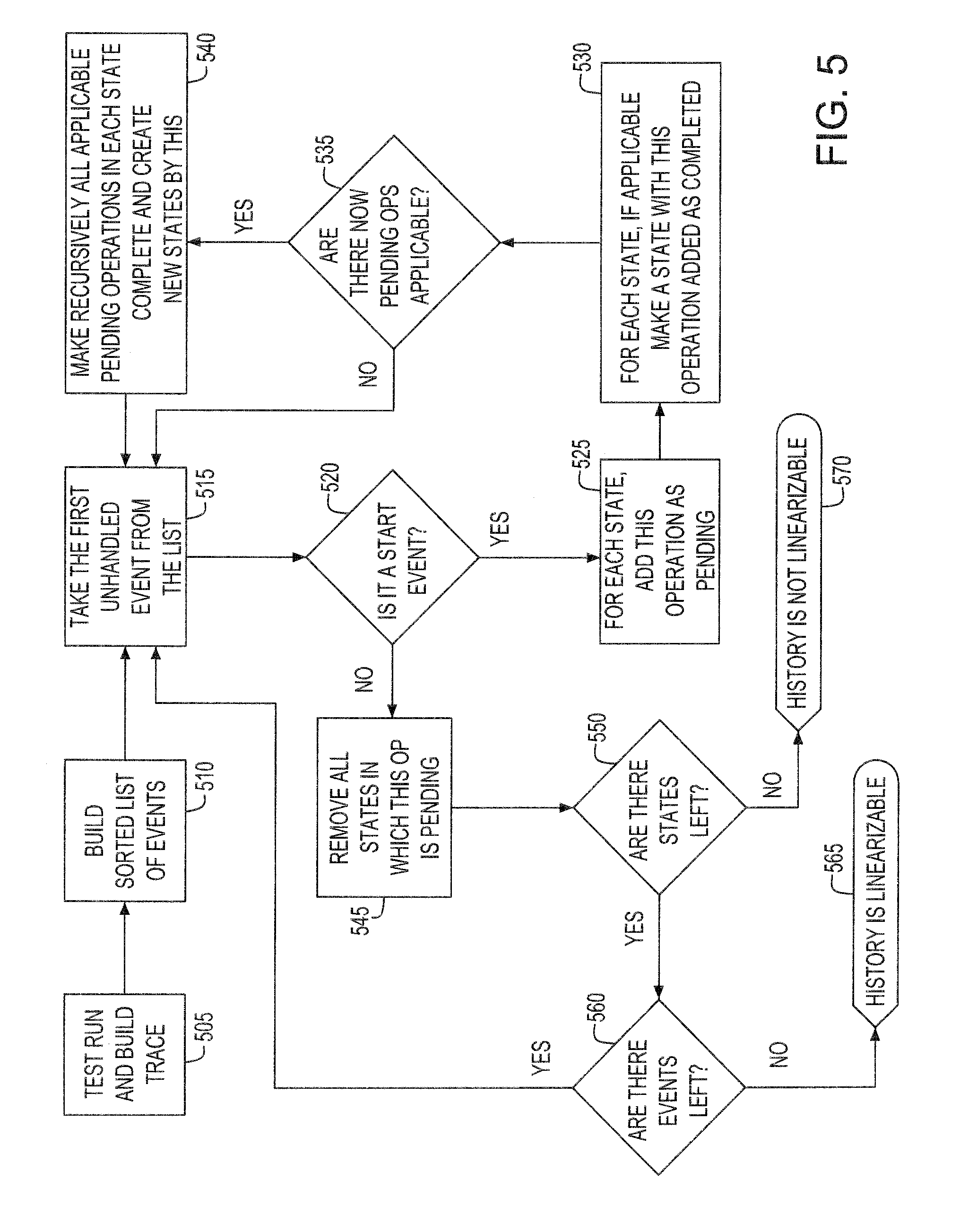
Program trace method
InactiveUS20080178158A1Program control using stored programsError detection/correctionRelational databaseParallel computing
Disclosed is a method of tracing a program that comprises: providing a relational database data structure defining a plurality of fields configured to store program trace information; executing a program comprising a plurality of functions including calling a function from the program; extracting first trace data of the function and storing the first trace data in a portion of the plurality of fields; and after executing the program, extracting second trace data associated with the first trace data and storing the second trace data in remaining portions of the plurality of fields.
Owner:SAMSUNG ELECTRONICS CO LTD
Debugger apparatus and method for indicating time-correlated position of threads in a multi-threaded computer program
InactiveUS7770155B2Error detection/correctionSpecific program execution arrangementsTimestampParallel computing
A debugger inserts instrumentation hooks in a multi-threaded computer program that allow collecting a program trace and that provide timestamps that correspond to the program trace. When a breakpoint in a first thread is encountered, a timestamp corresponding to the breakpoint is retrieved. Execution of the other threads may continue until the debugger is able to halt their execution. Once the execution of all threads has been halted, the program trace for each thread is traced backwards to a point where the timestamp is less than the breakpoint timestamp. Instructions are then executed, one by one, until the execution time of the instructions plus the timestamp is approximately the same as the breakpoint timestamp. The instruction in the program trace display is then highlighted to indicate the instruction that was likely being executed when the breakpoint in the first thread is encountered.
Owner:IBM CORP
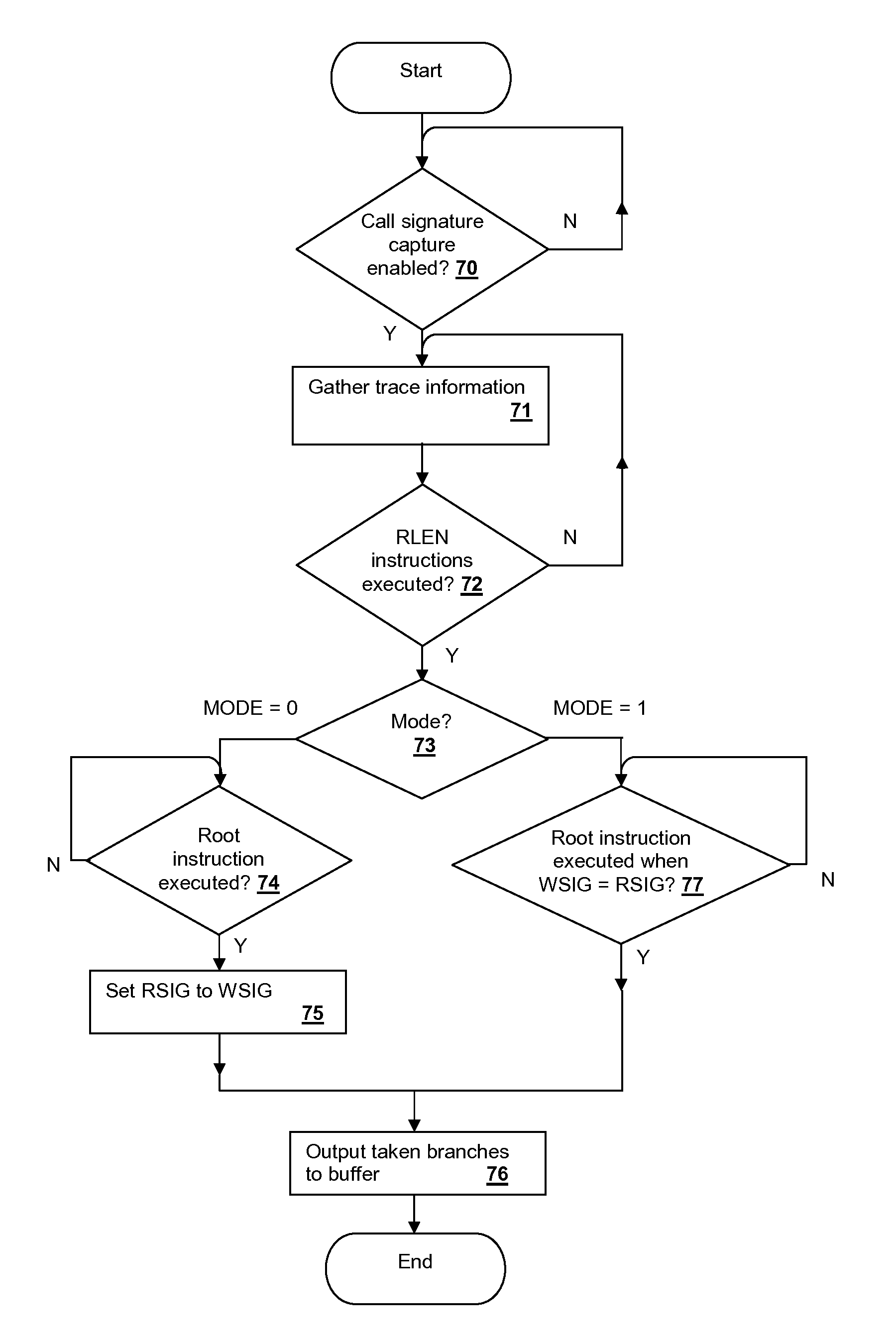
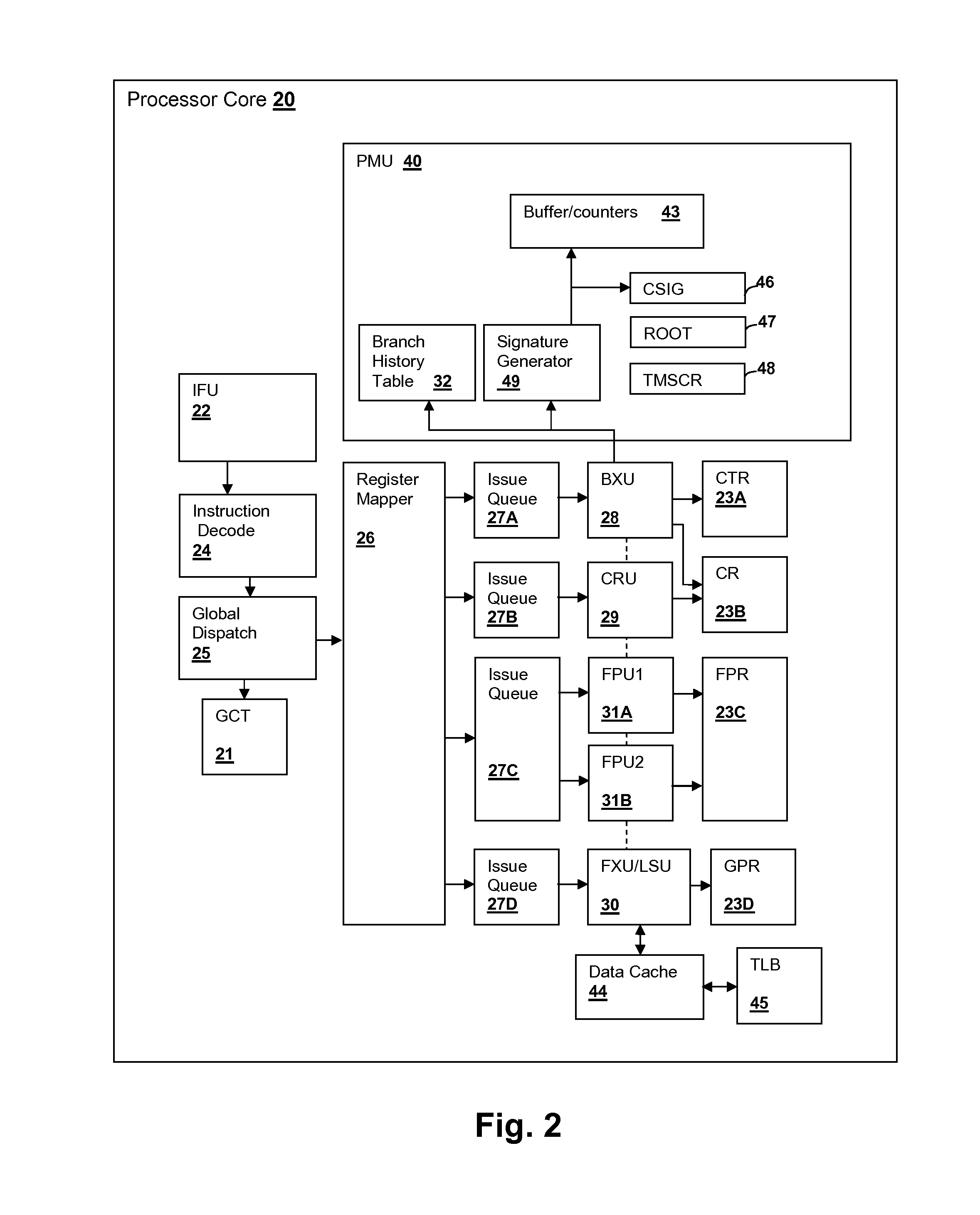
Hardware-assisted program trace collection with selectable call-signature capture
InactiveUS20140059523A1Hardware monitoringSpecific program execution arrangementsProgram instructionProcessor register
Hardware-assisted program tracing is facilitated by a processor that includes a root instruction address register, a program trace signature computation unit and a call signature register. When a program instruction having an address matching the root instruction address register is executed, a program trace signature is captured in the call signature register and capture of branch history is commenced. By accumulating different values of the call signature register, for example in response to an interrupt generated when the root instruction is executed, software that performs program tracing can obtain signatures of all of the multiple execution paths that lead to the root instruction, which is also specified by software in order to set different root instructions for program tracing. In an alternative implementation, a storage for multiple call signatures is provided in the processor and read at once by the software.
Owner:INT BUSINESS MASCH CORP
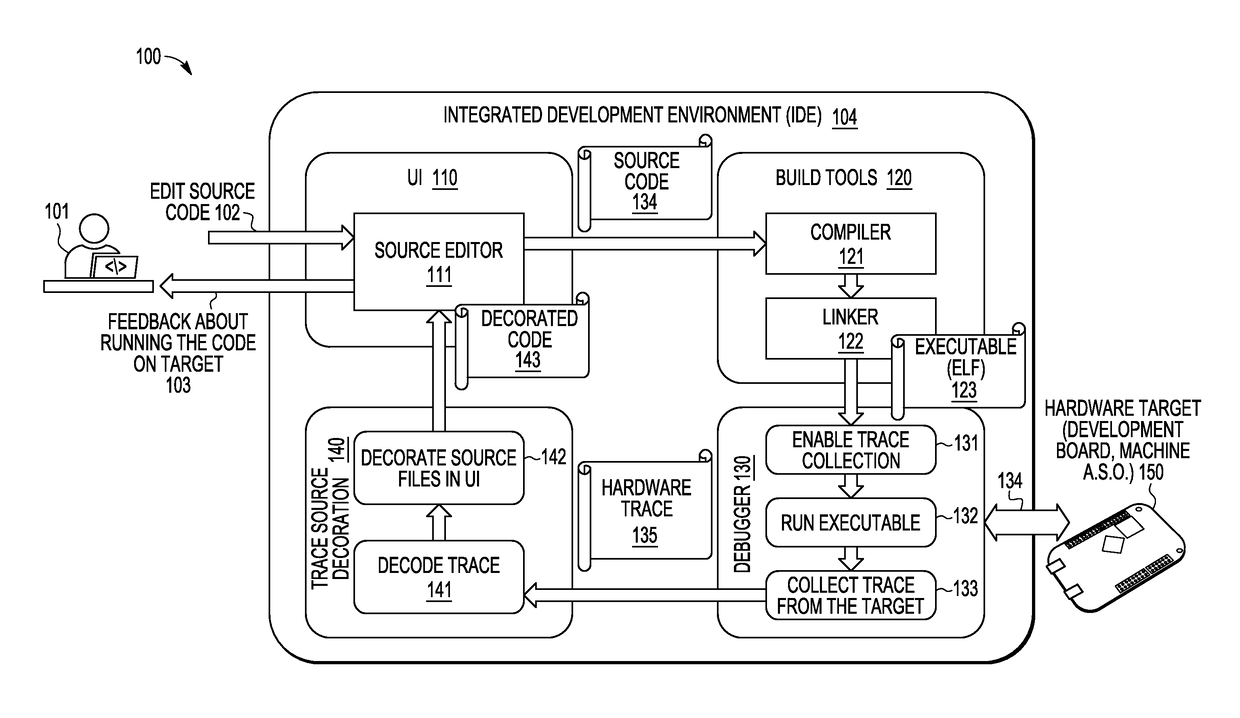
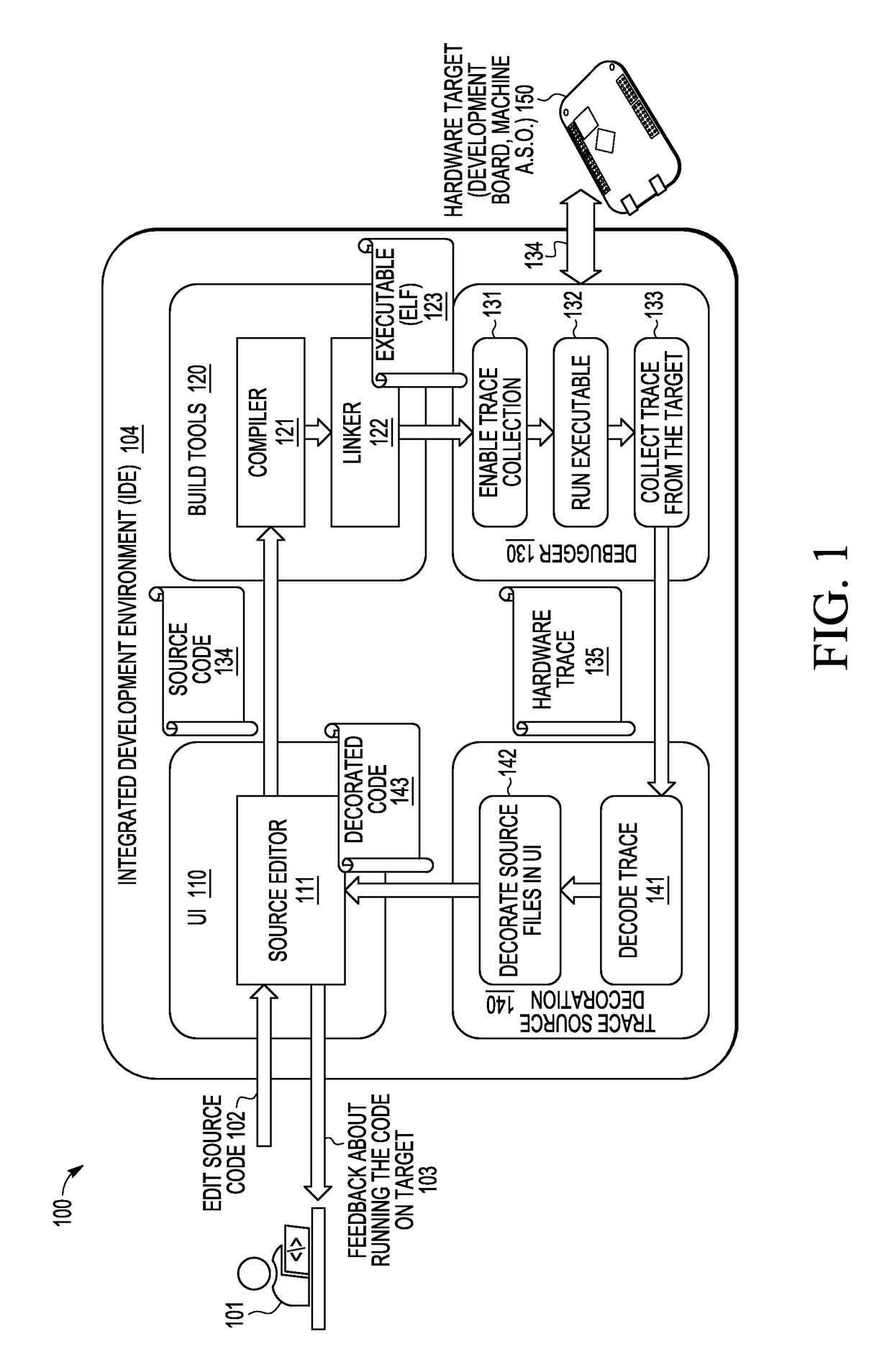
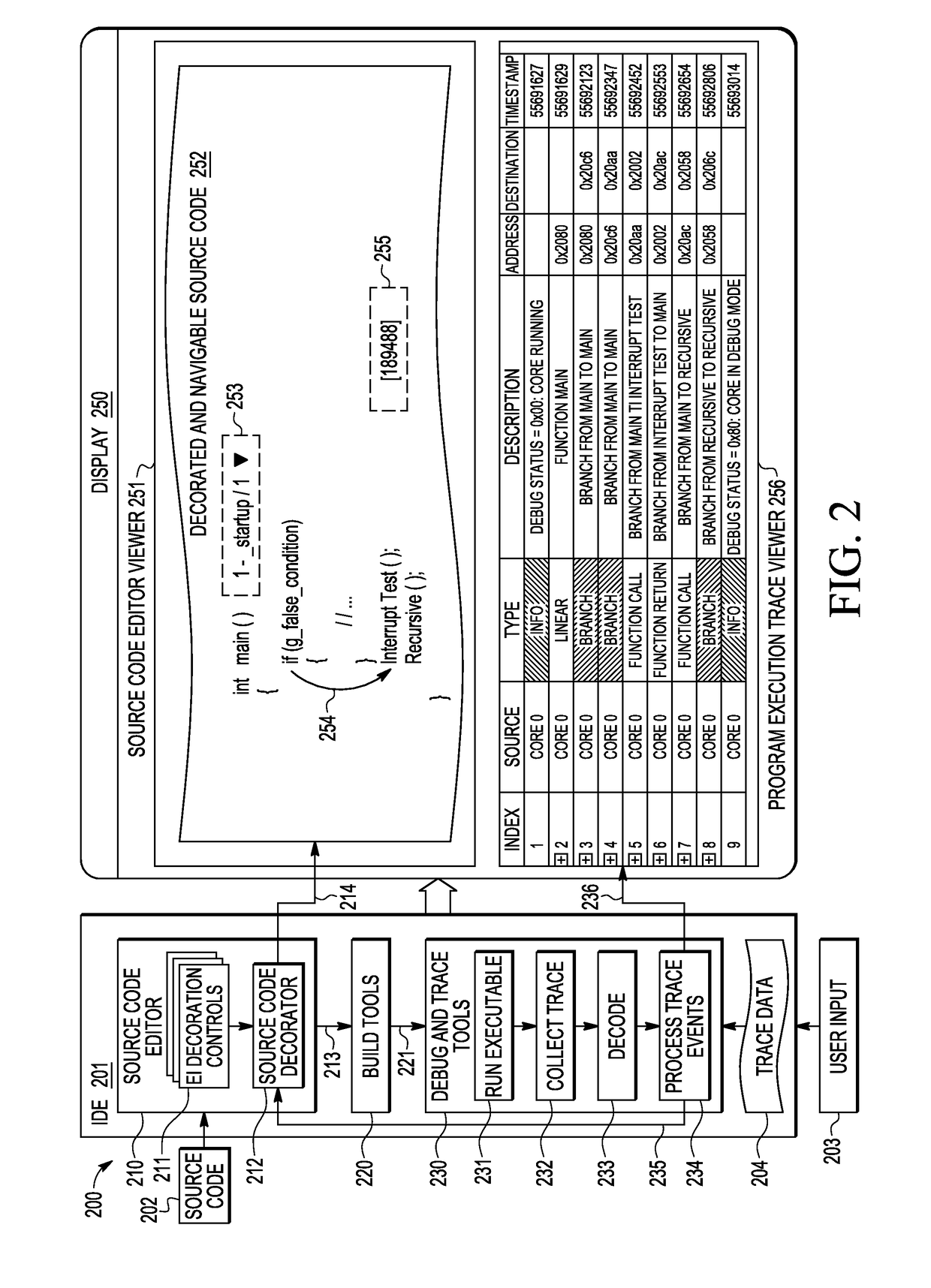
Method and System to Display and Browse Program Trace Using Source Code Decoration
A method and apparatus are provided for navigating source code (112) by capturing a program trace data history (134) from a target (150) in response to execution of application executable code (123) thereon and decorating the source code blocks (252) on a graphical user interface viewer (251) by displaying an execution instance control indicator (253-255) corresponding to each detected execution instance, where an execution instance control enables control of which execution instance is displayed and an execution instance indicator displays information about the sequence of instructions that were executed at runtime in that execution instance.
Owner:NXP USA INC
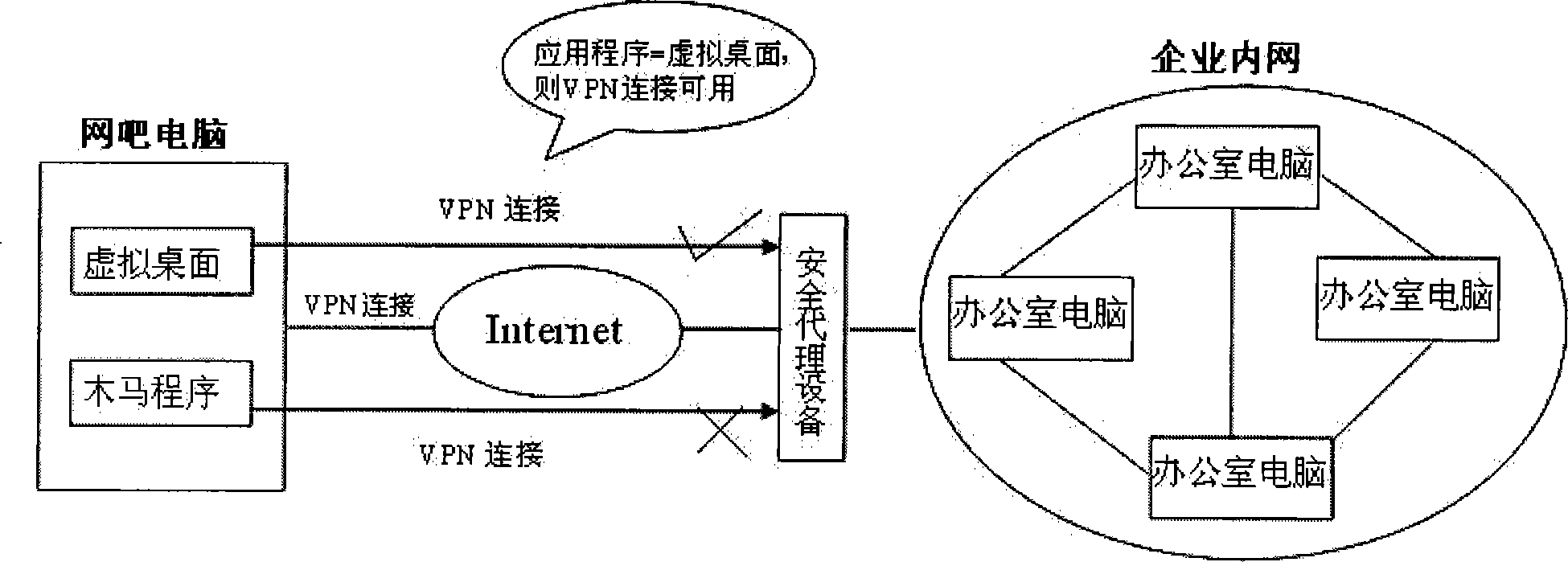
A VPN connection separation method based on operating system desktop
ActiveCN101242261AData switching detailsSecuring communicationOperational systemApplication software
The invention relates to a VPN connection separating method based on a operating system desktop, comprising: 1) setting a secure proxy equipment at the front end of a corporation inner net; 2) when an application program on a client machine accesses the VPN connection, firstly, the client machine downloads a VPN proxy program on the secure proxy equipment; 3) the VPN proxy program traces the application program sending the access after receiving the access require, then enumerates the operating windows of the application program, and finds corresponding desktop based on the windows; 4) the VPN proxy program judges whether the desktop is a virtual desktop; and 5) if the desktops is a virtual desktop, the VPN proxy program allows the application program accessing the VPN connection, and if the desktops is a real desktop, the VPN proxy program refuses the application program accessing the VPN connection. The invention makes only the application program operating on Symantec virtual desktop access the inner net resource of the corporation, while other programs operating in a real desktop of the operation system are forbidden to access the VPN connection to protect the sensitive information of the corporation.
Owner:ARRAY NETWORKS BEIJING
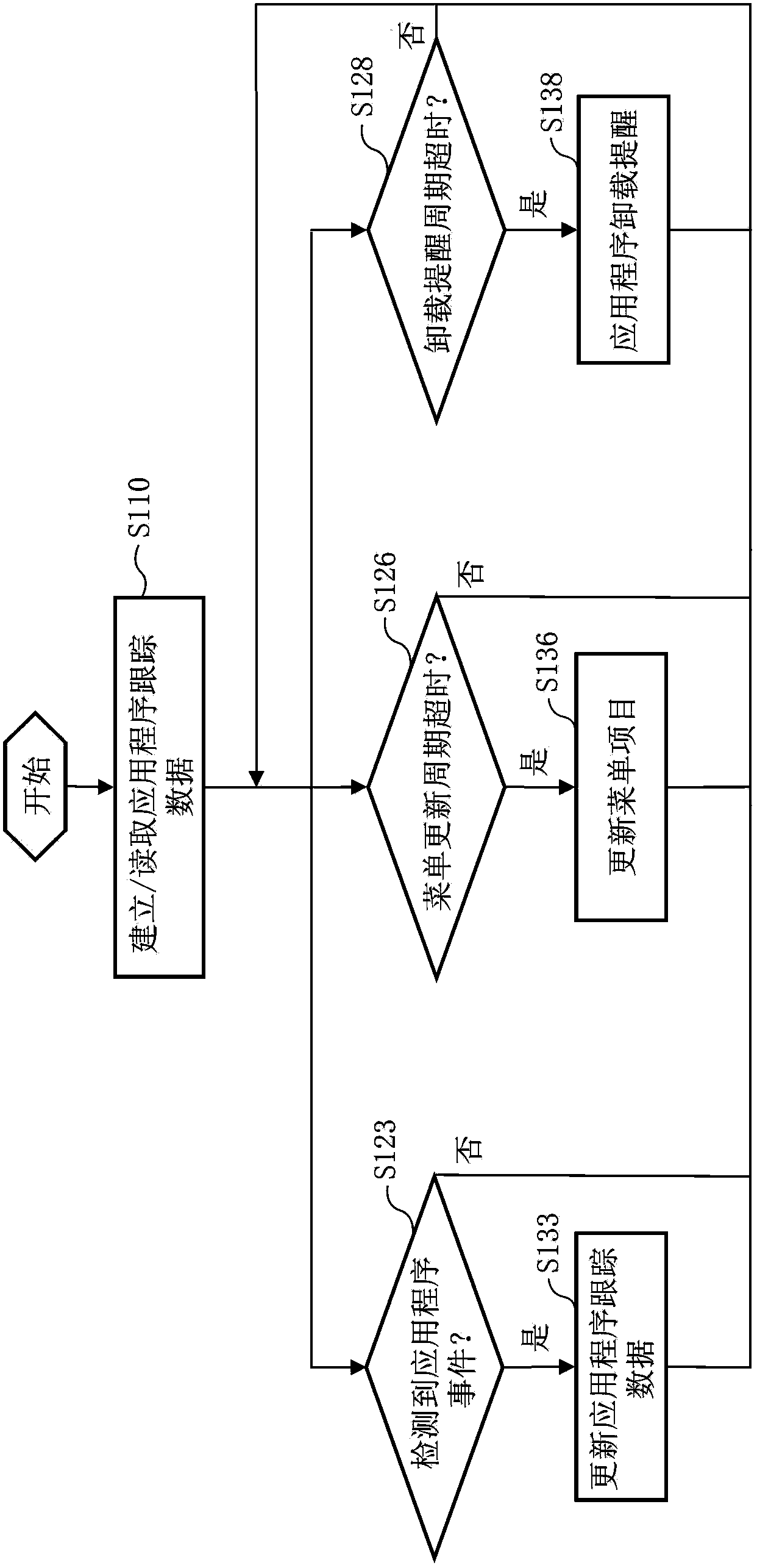
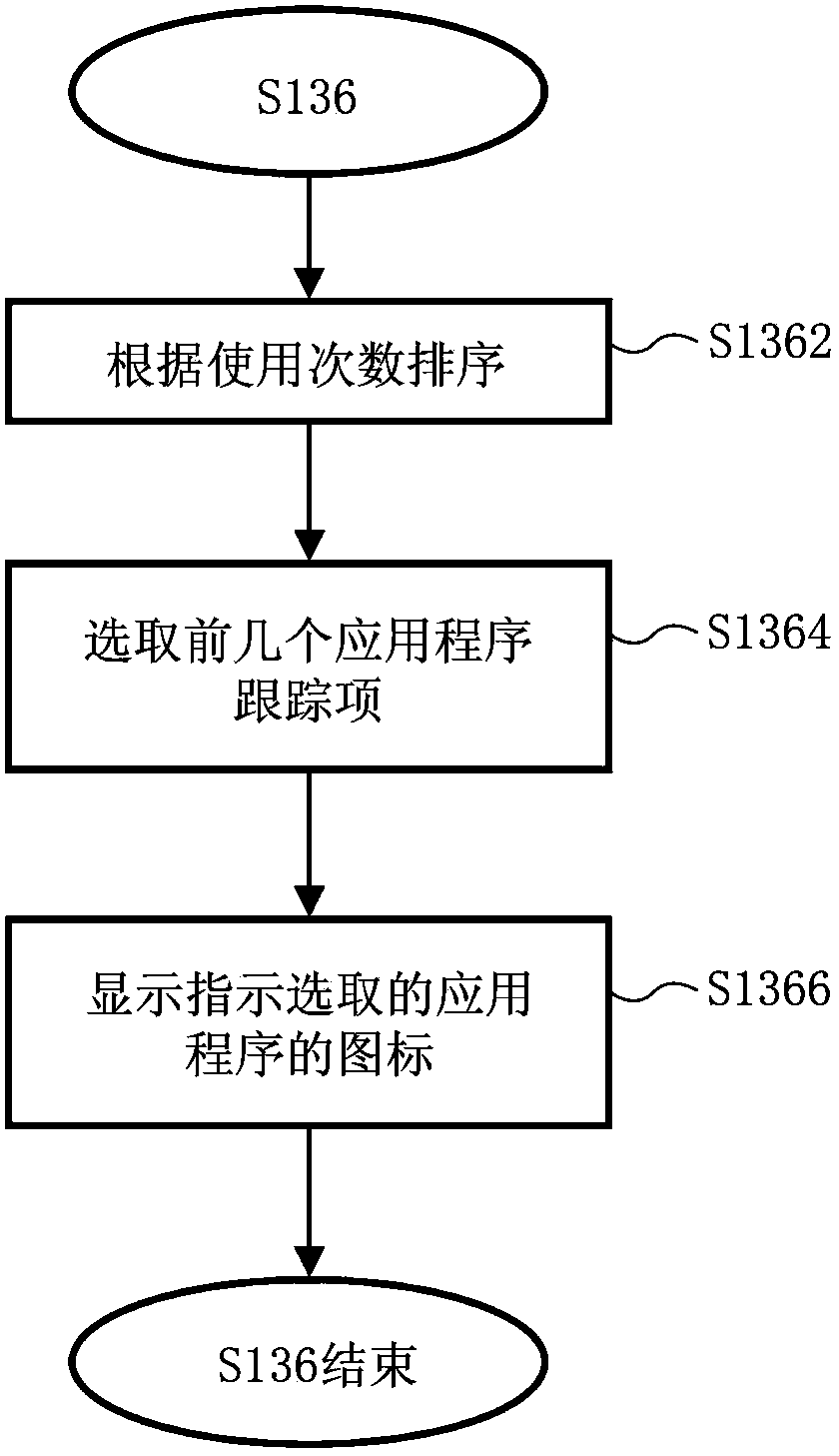
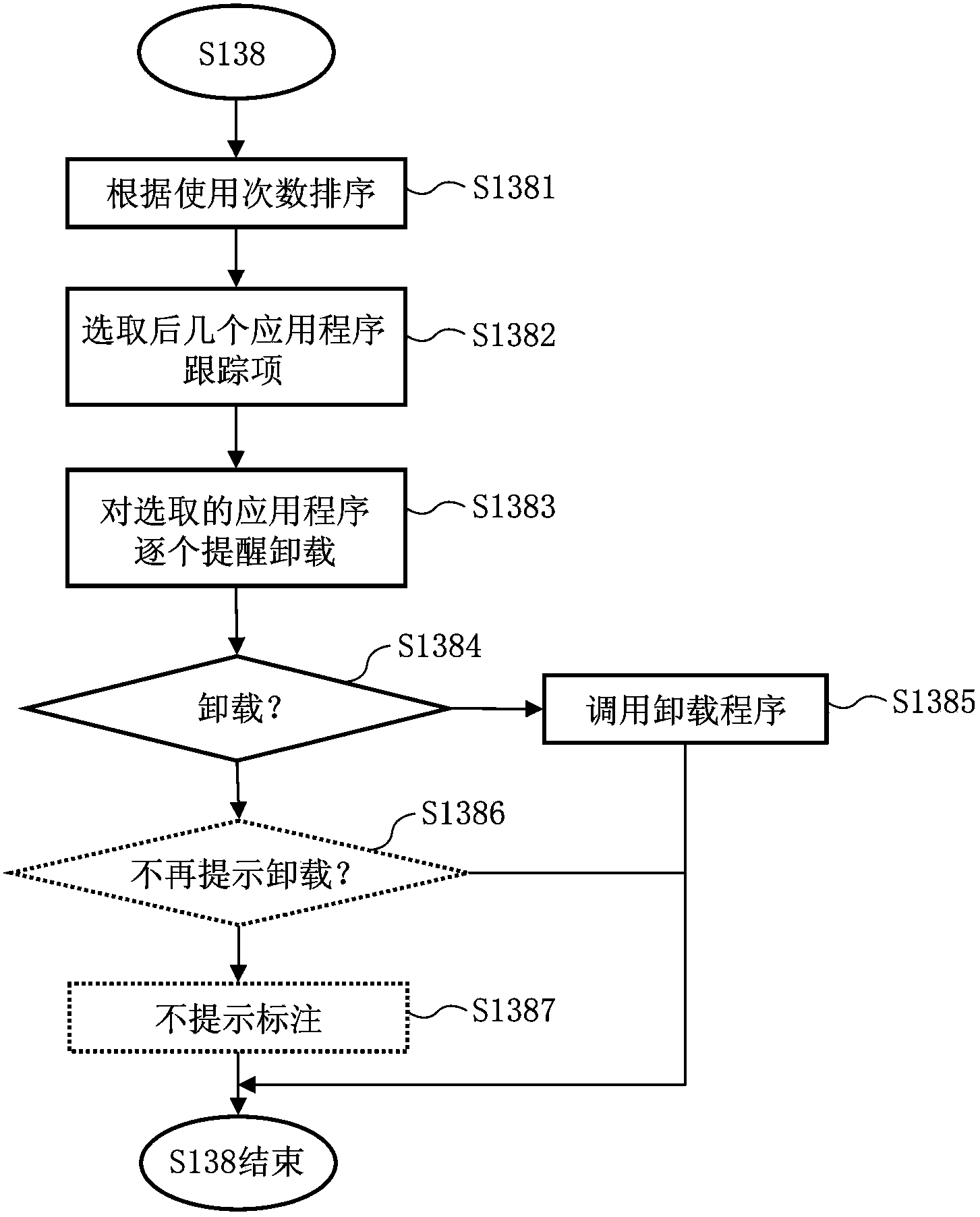
Application program managing method and terminal device
The invention provides an application program managing method and a terminal device. The application program managing method includes the following steps that when the event that any application program in the terminal device is installed, or uninstalled or started is detected, application program trace data are updated according to the detected event and include application trace items of all the installed application programs, and each application tracing item includes application program identification and the number of times of use; every other preset first updating period, the application program trace items in the application program trace data are sorted according to the number of times of use, the application program trace items with the largest number of times of use are selected, wherein the number of the application program trace items is a first preset number, and the application programs indicated by the selected application program trace items are updated to be items in a specific menu in a user interface. The steps are executed by using background programs.
Owner:SAMSUNG ELECTRONICS CHINA R&D CENT +1
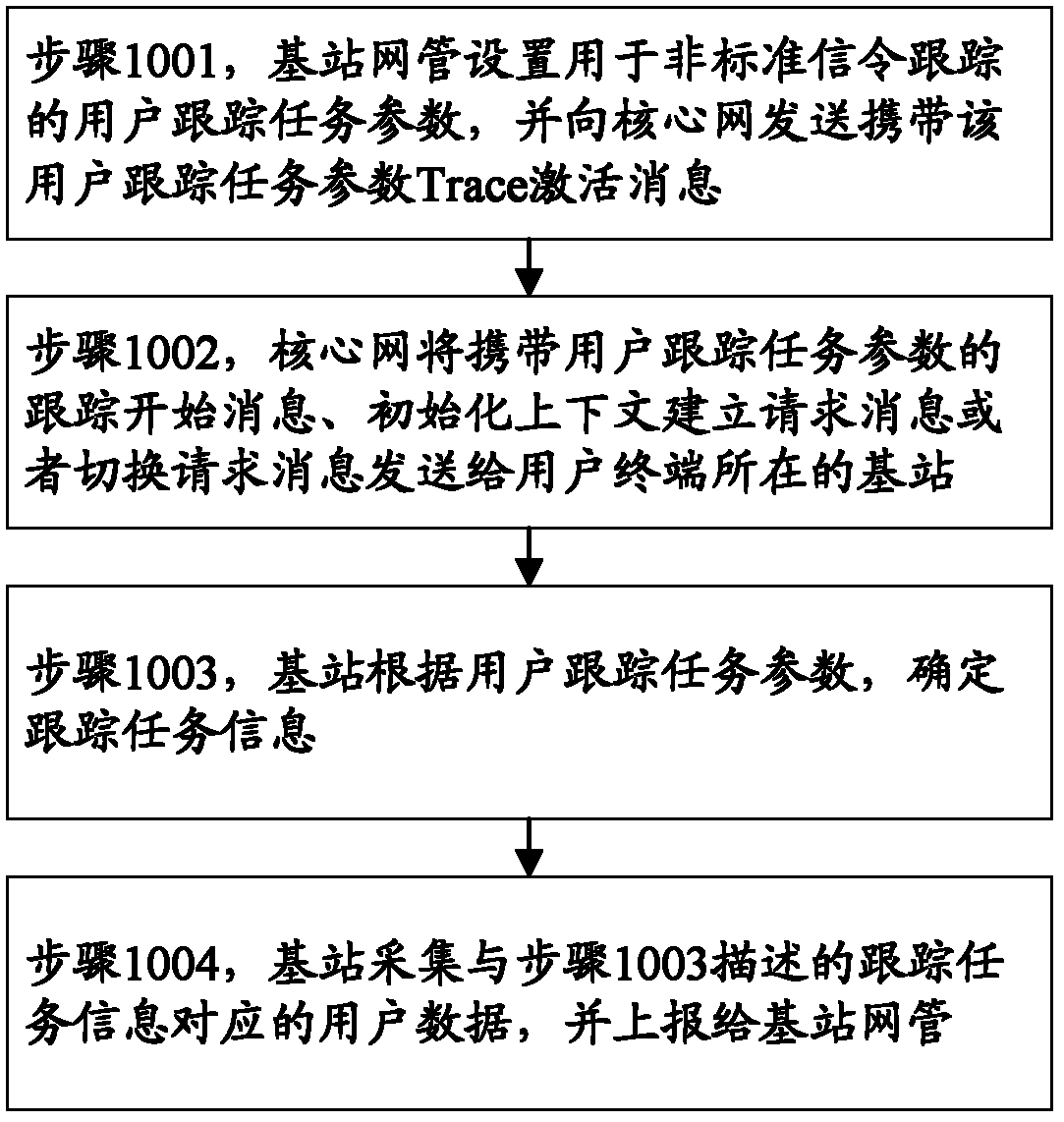
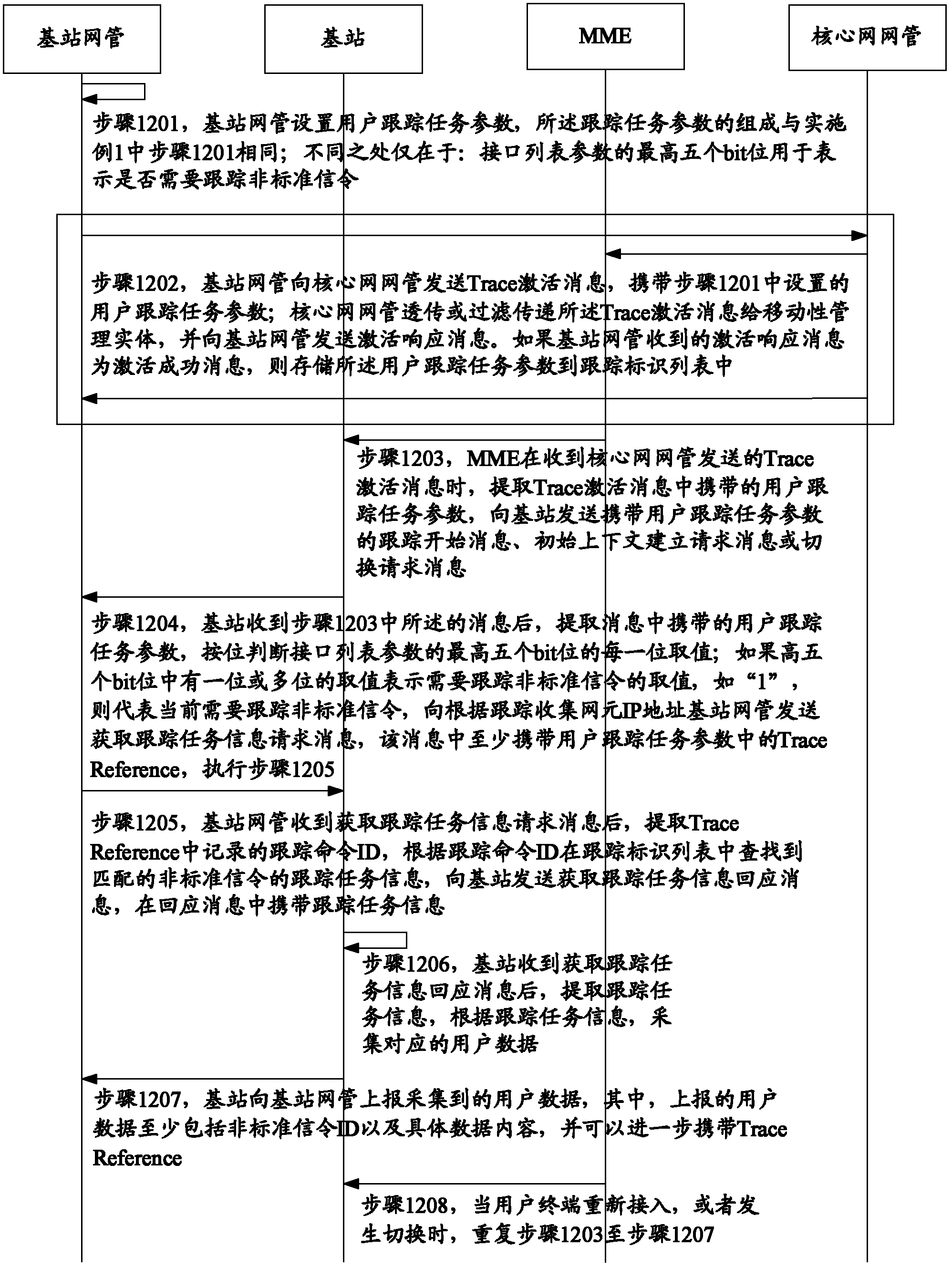
Method of user data tracking and system of user data tracking
The invention provides a method of user data tracking and a system of user data tracking. The method includes that a user tracking task parameter used for nonstandard signaling user data tracking is set on a base station network manager; the user tracking task parameter is transmitted to a core network according to tracking Trace activation information; the core network transmits carried tracking start information, initial context establishment request information or switch request information of the user tracking task parameter to a base station; tracking task information is determined by the base station according to the user tracking task parameter, user data corresponding to the tracking task information is collected by the base station, and the base station reports the collected user data to the base station network manager. The invention further provides the system of user data tracking. The method and the system achieve nonstandard signaling user data tracking based on a third generation partner program Trace mechanism.
Owner:ZTE CORP
Program tracing in a multithreaded processor
ActiveUS7360203B2Easy maintenanceHinder resolutionProgram initiation/switchingConcurrent instruction executionOperandProgram trace
A multithreaded processor includes a thread ID for each set of fetched bits in an instruction fetch and issue unit. The thread ID attaches to the instructions and operands of the set of fetched bits. Pipeline stages in the multithreaded processor stores the thread ID associated with each operand or instruction in the pipeline stage. The thread ID are used to maintain data coherency and to generate program traces that include thread information for the instructions executed by the multithreaded processor.
Owner:INFINEON TECH AG
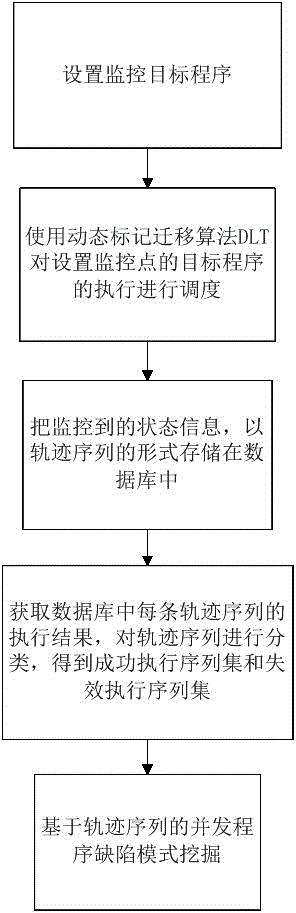
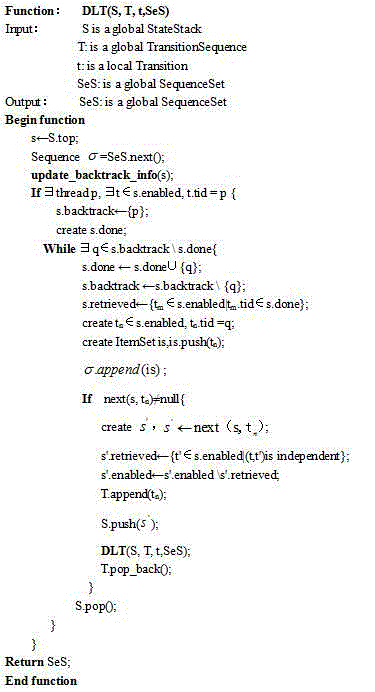
Discovering method for defect mode in concurrent program
ActiveCN104899137AAvoid repeated searchesImprove execution efficiencySoftware testing/debuggingSoftware faultProgram trace
The present invention belongs to the field of software fault diagnosis and provides an autonomously discovering method for a defect mode in a concurrent program, particularly a defect mode discovering method for mining system execution traces by using sequential patterns. According to the technical scheme provided by the invention, based on a plugged concurrent program, the execution of threads are dynamically scheduled during the operation of the plugged concurrent program; program execution information is collected in real time; a program trace sequence is stored as required; the execution sequence is mined; and the program defect pattern is autonomously discovered.
Owner:HUAZHONG NORMAL UNIV
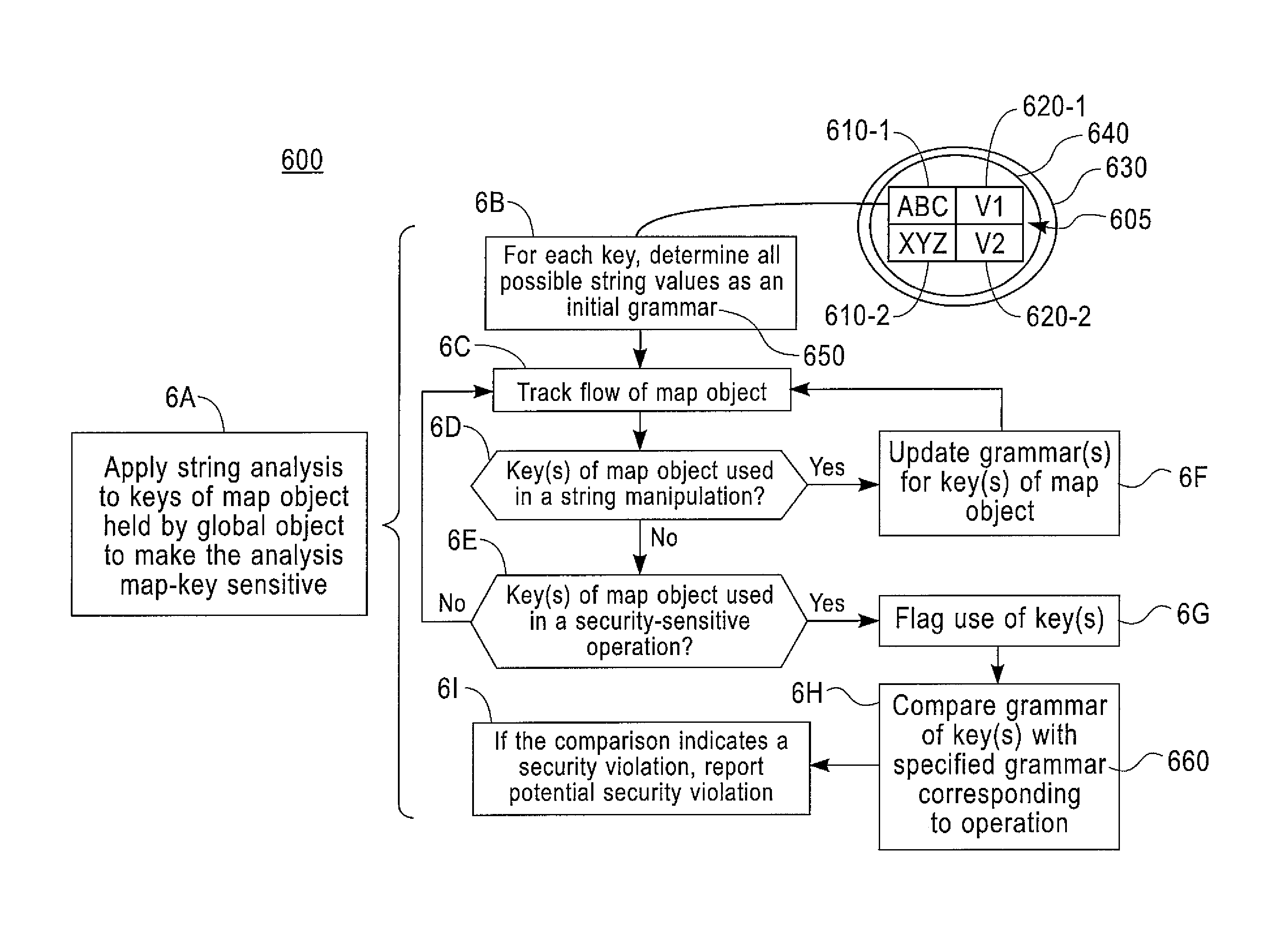
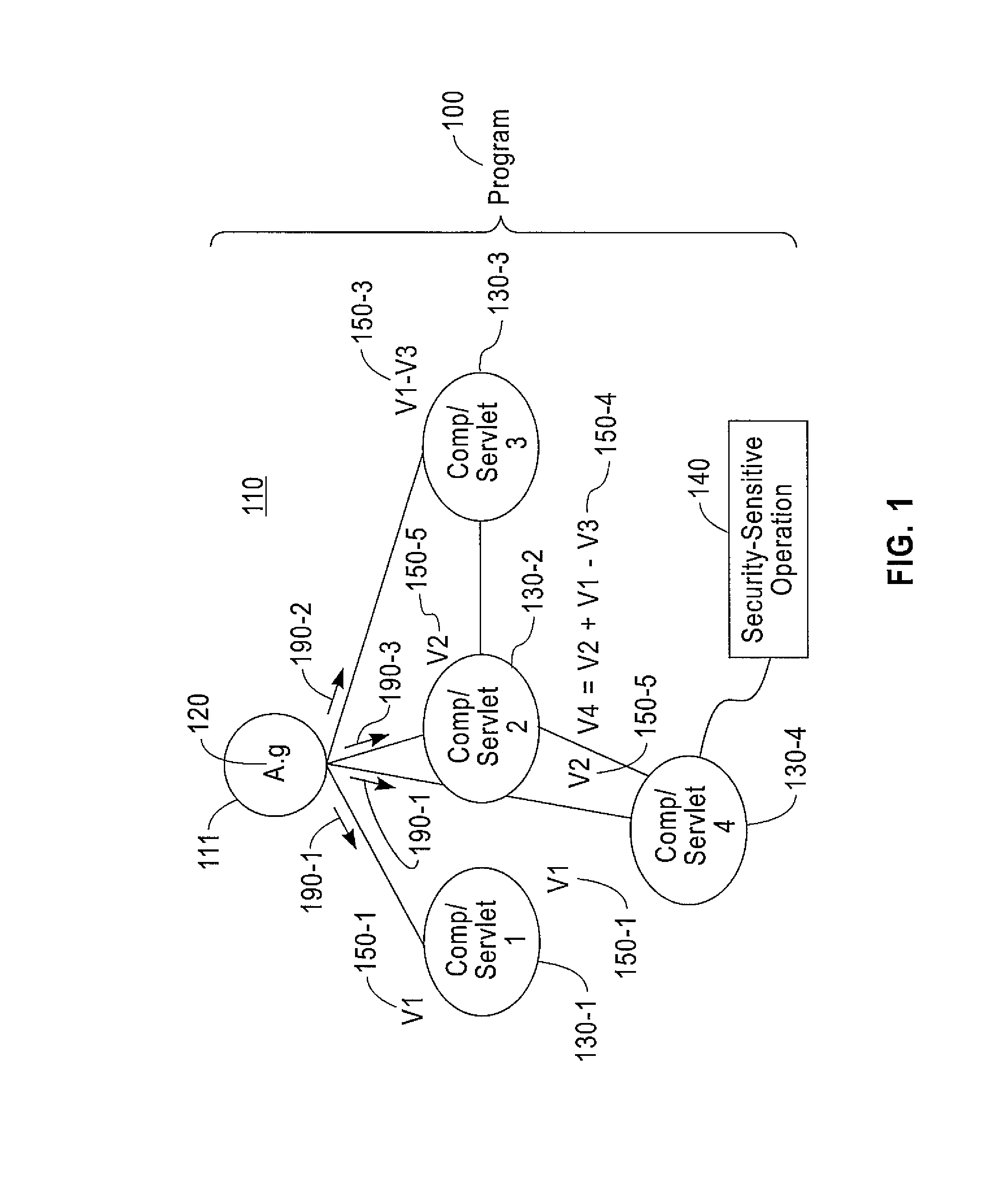
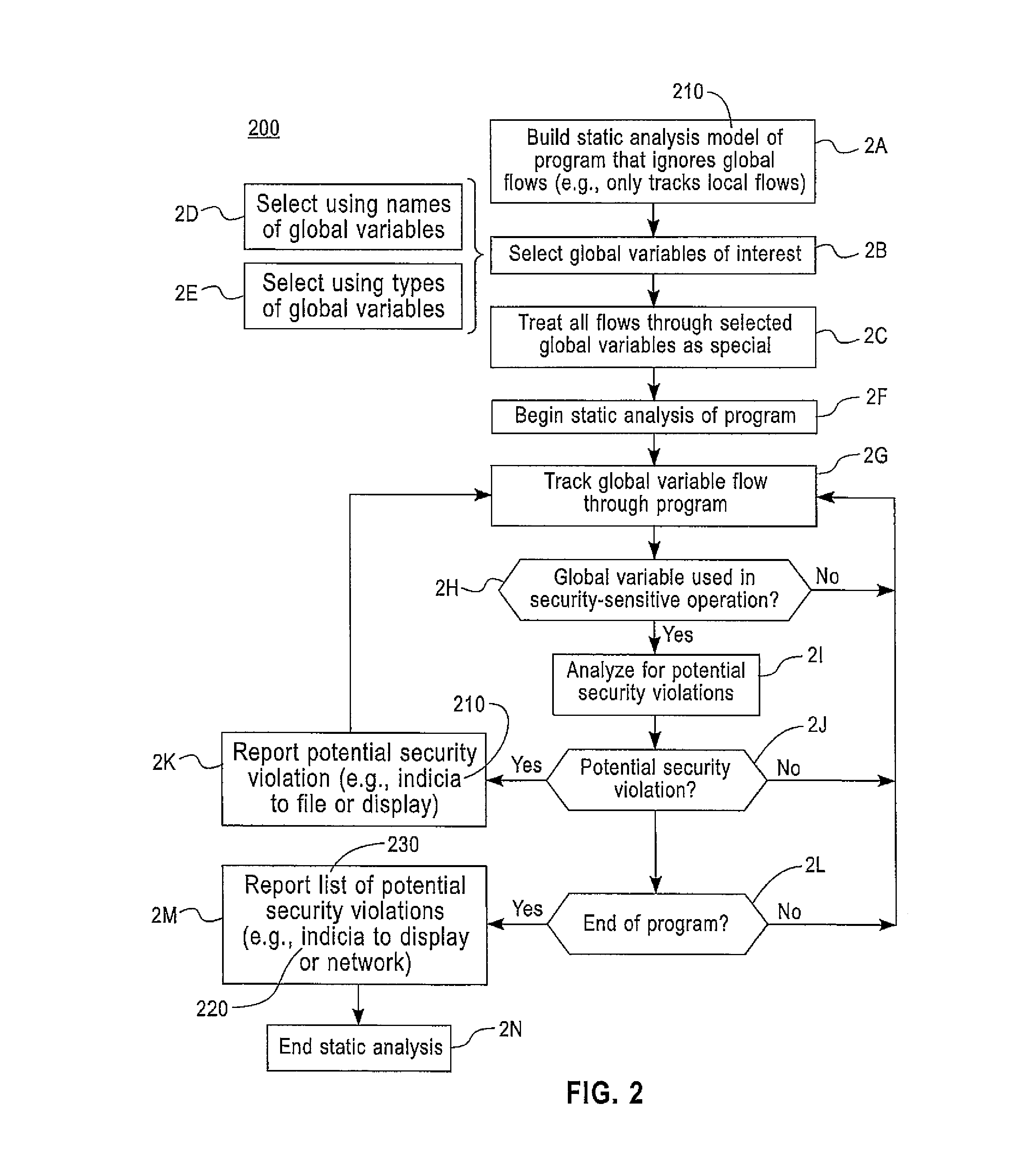
Global variable security analysis
InactiveUS9075997B2Easy to analyzeHardware monitoringSoftware testing/debuggingSecurity analysisProgram trace
A method includes determining selected global variables in a program for which flow of the selected global variables through the program is to be tracked. The selected global variables are less than all the global variables in the program. The method includes using a static analysis performed on the program, tracking flow through the program for the selected global variables. In response to one or more of the selected global variables being used in security-sensitive operations in the flow, use is analyzed of each one of the selected global variables in a corresponding security-sensitive operation. In response to a determination the use may be a potential security violation, the potential security violation is reported. Apparatus and computer program products are also disclosed.
Owner:IBM CORP
System and method for demonstrating the correctness of an execution trace in concurrent processing environments
InactiveUS8413122B2Avoid backtrackingError detection/correctionSpecific program execution arrangementsGeneral purposeProgram trace
Since multi-core processors have become the standard architecture for general purpose machines, programmers are required to write software optimized for parallelism. Verification of correctness is an important issue for parallel code because of its complexity. There are still tools missing that provide verification for complex code, such as testing the execution of code provides. Consequently, described herein are systems and methods to evaluate the correctness of program traces. Furthermore, the systems and methods described herein do not demand excessive computational requirements and the size of the program trace being evaluated increases.
Owner:GLOBALFOUNDRIES INC
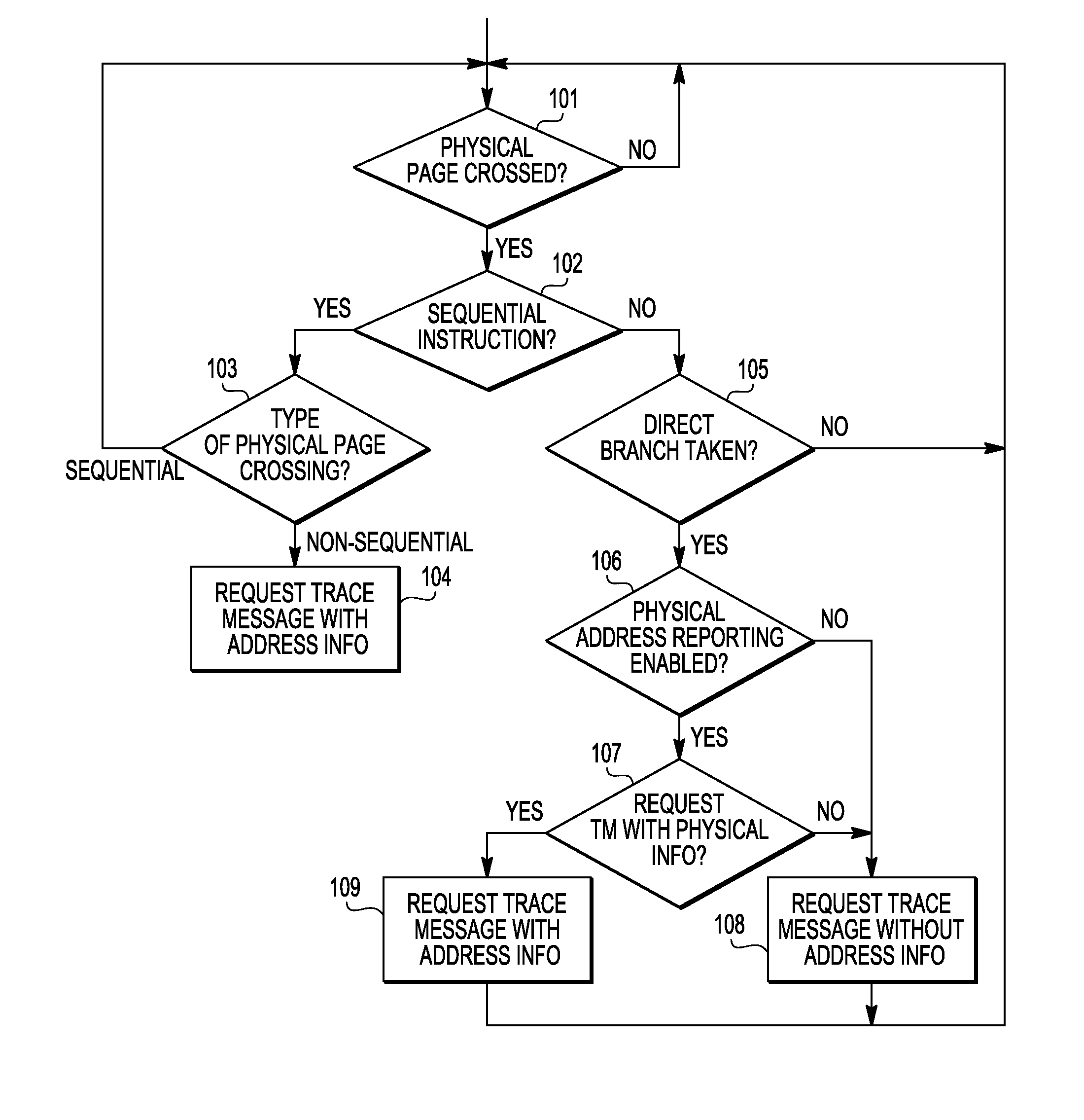
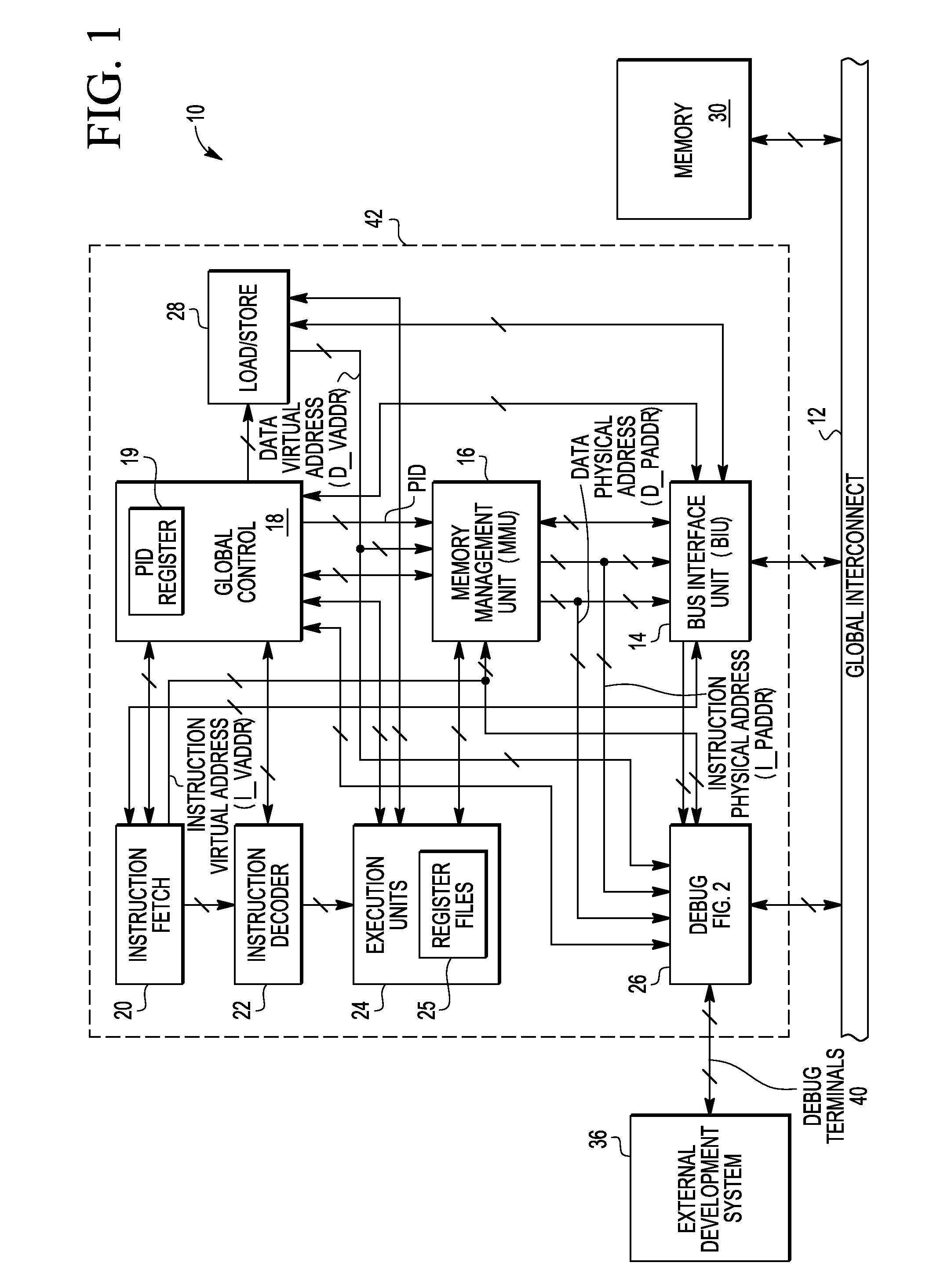
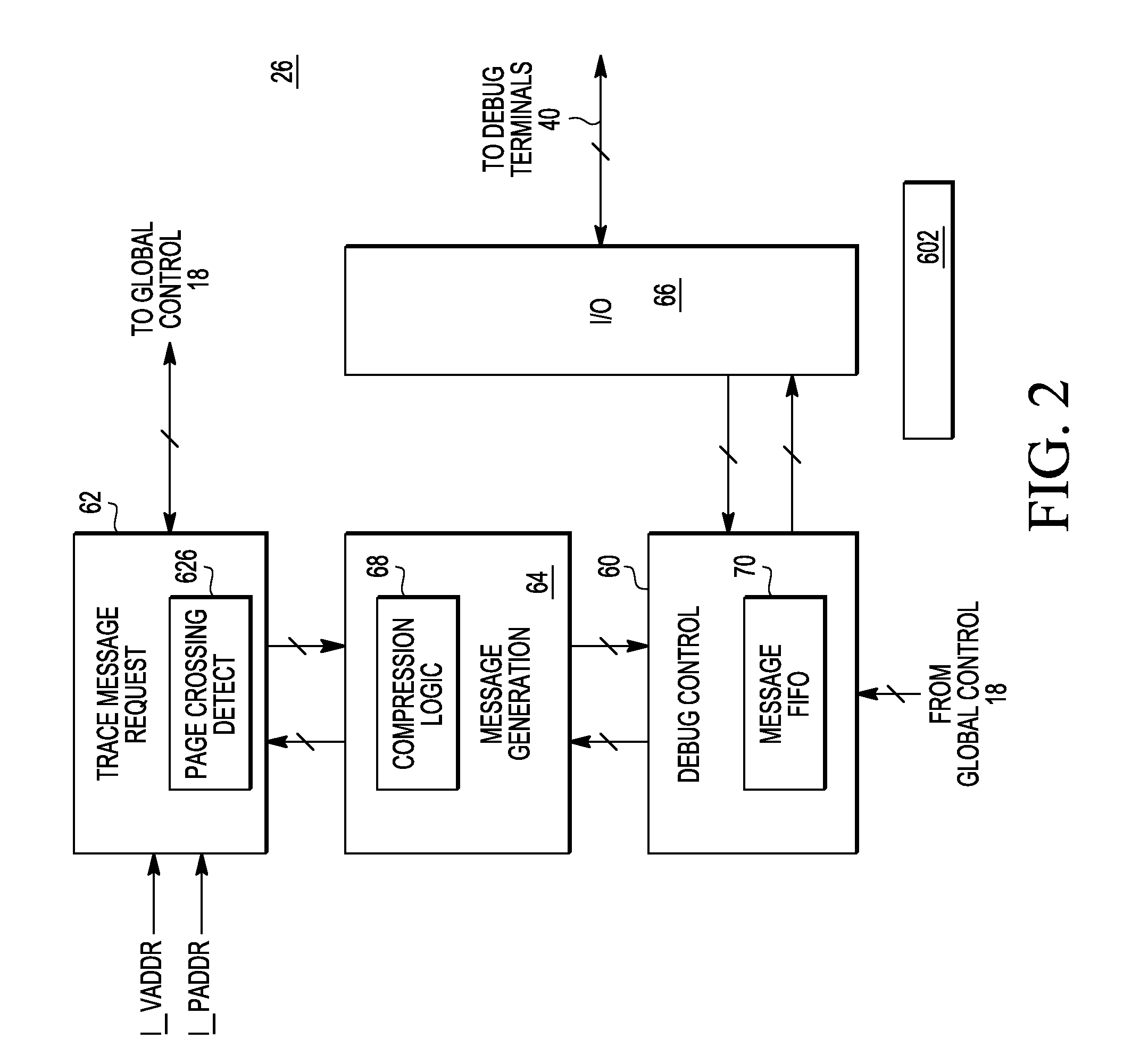
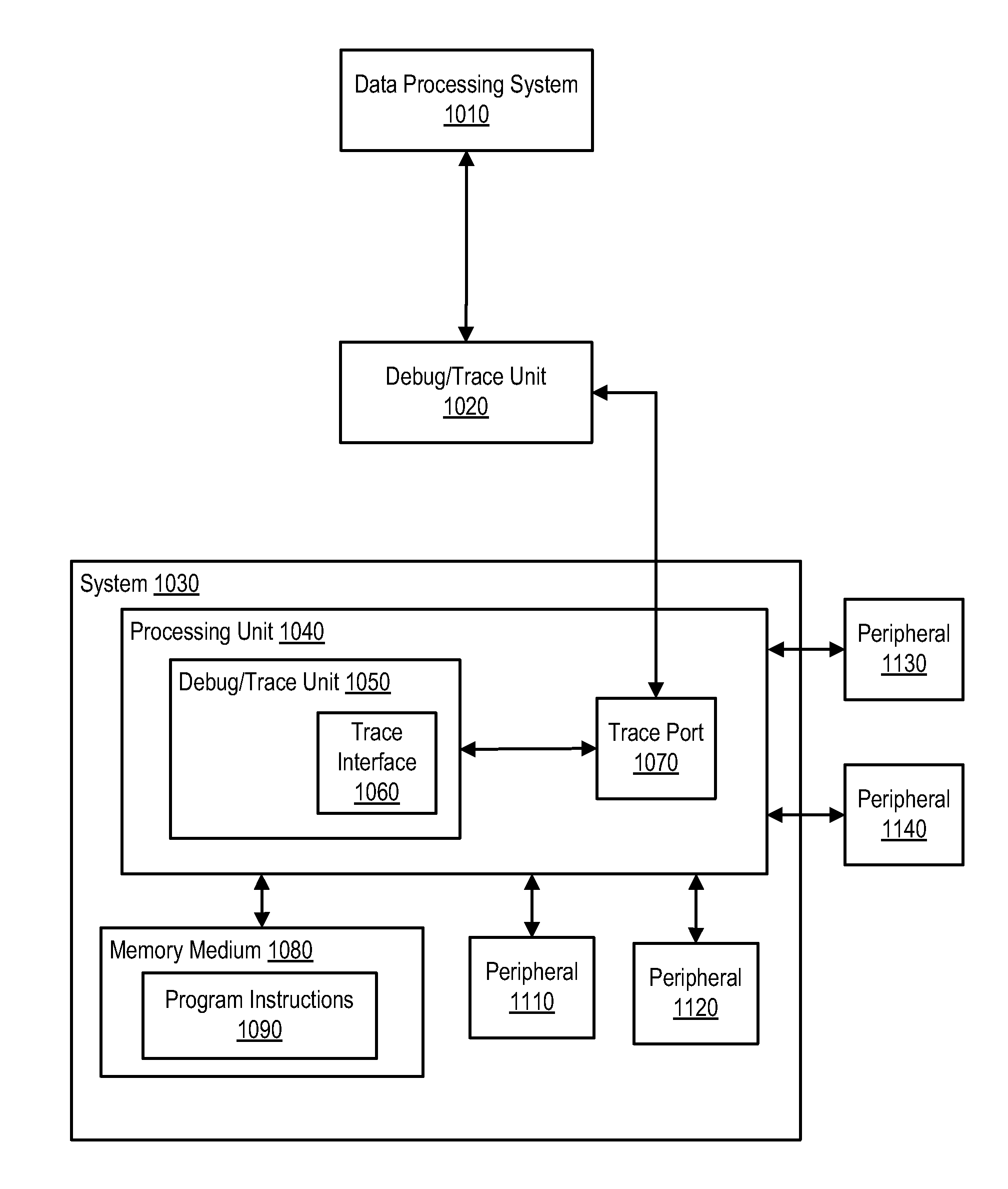
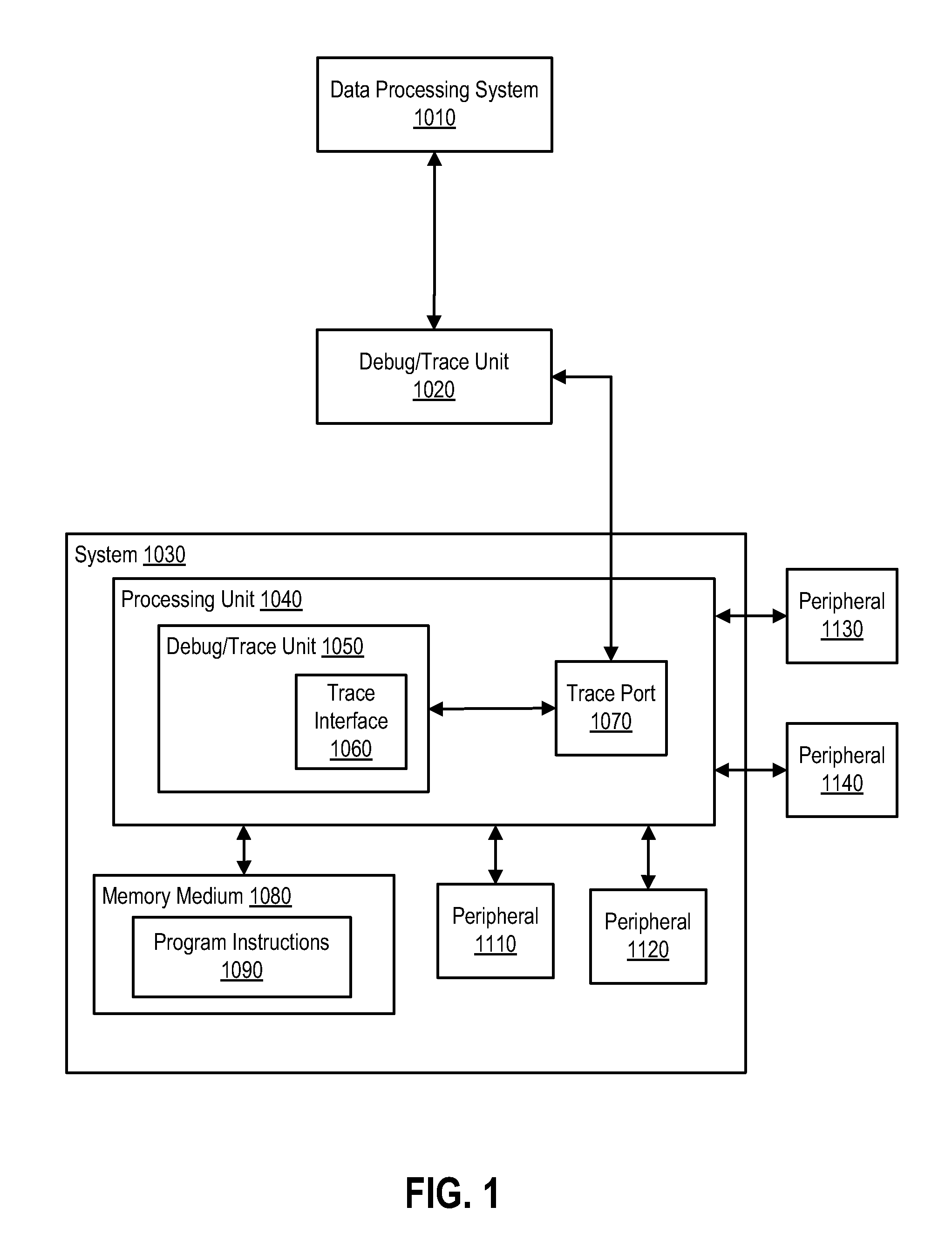
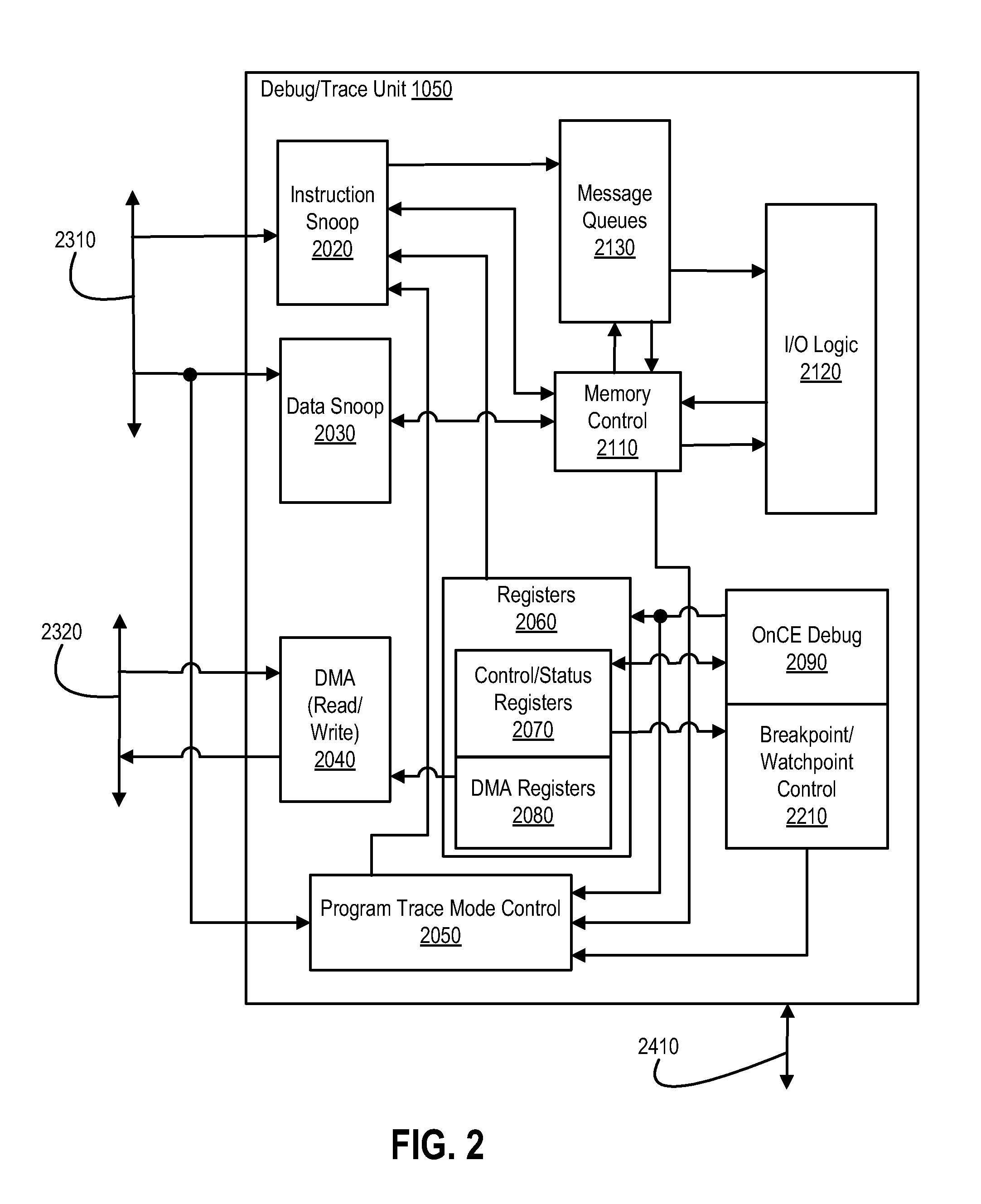
Program trace message generation for page crossing events for debug
ActiveUS8589738B2Memory architecture accessing/allocationError detection/correctionData processing systemData treatment
A data processing system has a trace message filtering circuit. A method includes: receiving a current page address corresponding to a current instruction in a sequence of instructions; determining that the current page address is for a different page of memory than a previous page address corresponding to a previous instruction in the sequence of instructions; comparing the current page address with a plurality of page addresses stored in a message filtering circuit; and when the current page address is determined to be different than any of the plurality of page addresses, storing the current page address in the message filtering circuit.
Owner:NXP USA INC
Switching Between Traditional and History Program Trace Modes Without Halting a Processor
In one or more embodiments, one or more systems, method, and / or processes described herein can change / switch from a first trace mode to a second trace mode without halting a system under development and / or under test. For example, a debug / trace unit can switch a trace mode without halting a processing unit of a system under development and / or under test. For instance, a debug / trace unit can switch a trace mode that can occur on a change of flow boundary of program instructions executable by a processing unit, at a branch instruction, if a region of program instructions is entered or exited, and / or if a capacity of a buffer changes. In one or more embodiments, Nexus messages can be utilized, and trace mode switches can include switches to and / or from traditional and history traces modes.
Owner:NXP USA INC
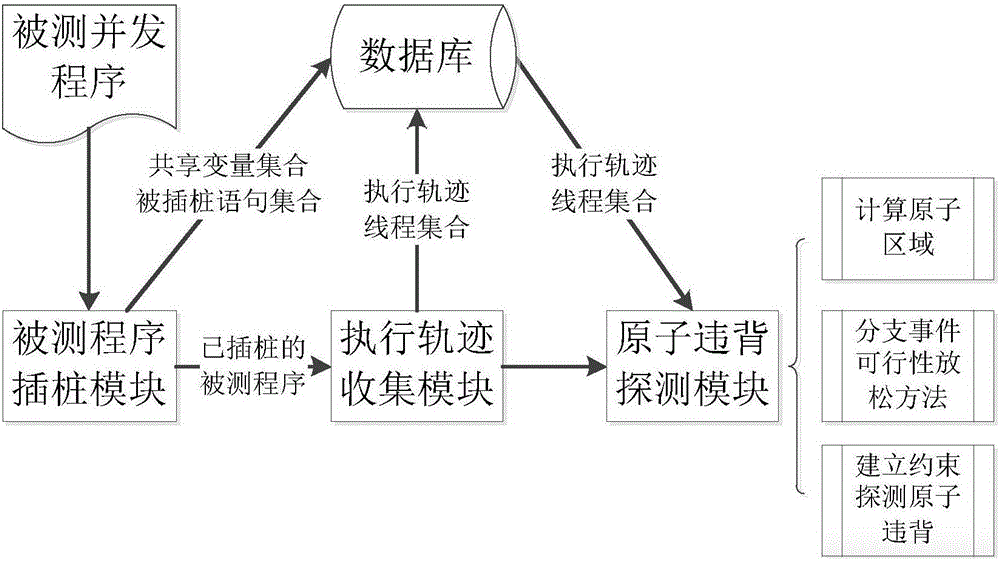
Constraint solving based atomic violation detection method
ActiveCN106844215AHigh precisionEasy detectionSoftware testing/debuggingTheoretical computer scienceProgram trace
The invention provides a constraint solving based atomic violation detection method. The method includes: determining an atomic region by the aid of an original execution trace of a concurrent program; establishing constraint relation of execution sequence among events in the original execution trace by combining with various error modes of atomic violation; performing constraint solving by the aid of a Z3 solver and converting the atomic violation detection problem into a solving problem of constraint equation. The method belongs to runtime prediction technique, an unexposed atomic violation error hidden in the original execution trace can be solved according to constraints, and better capability in detecting atomic violation is achieved; a set of constraints is established in an intertwining manner for the original program trace and unserializable executions, the atomic violation detection problem is converted into the solving problem of the constraints, and precision in atomic violation detection can be improved.
Owner:SOUTHEAST UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com