Method for utilizing Elagamal public key algorithm to generate software license code
A technology for generating software and public key algorithms, applied to public keys for secure communications, computing, computer security devices, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
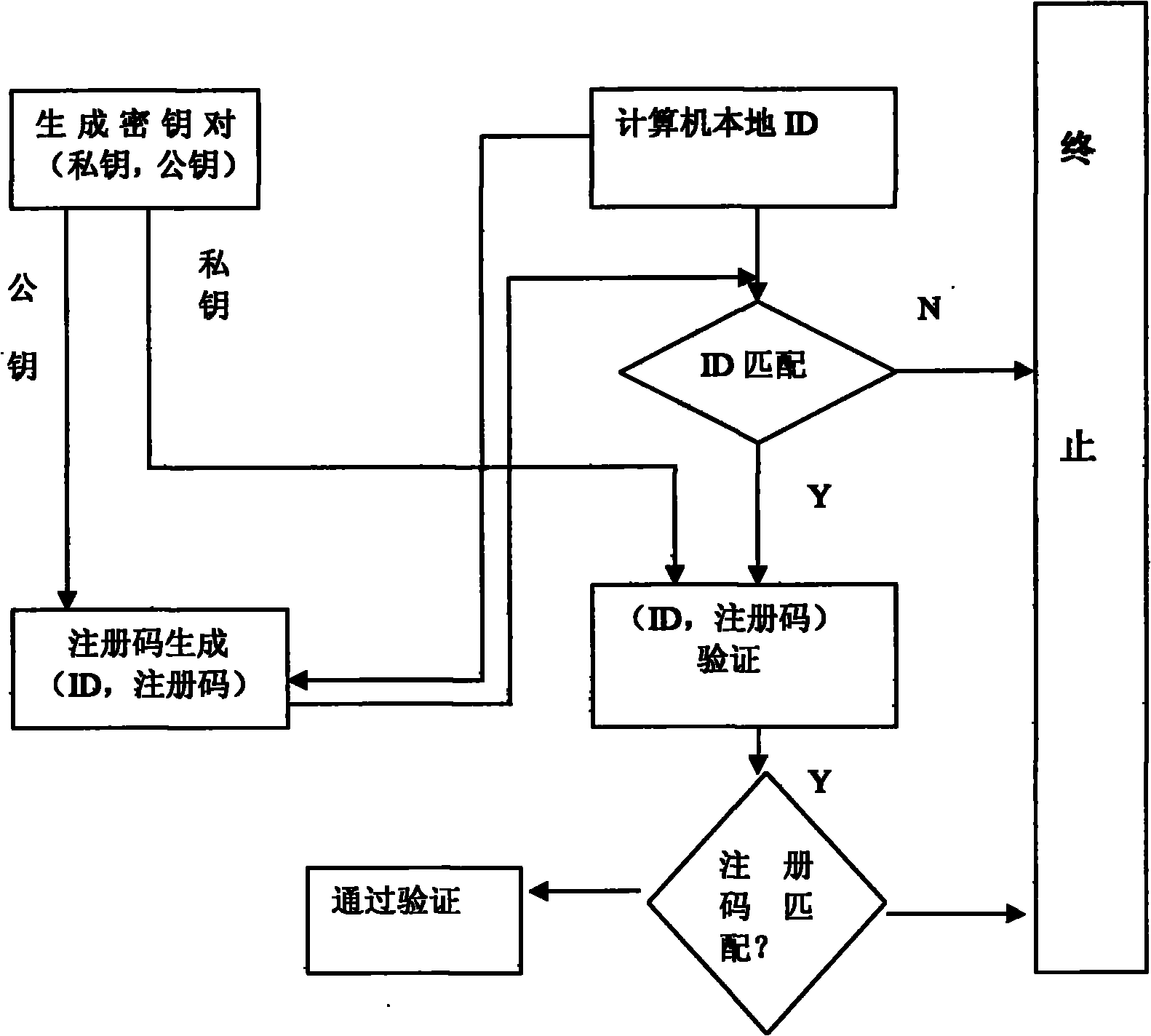
[0035] Such as image 3 Shown, the embodiment of the present invention is:
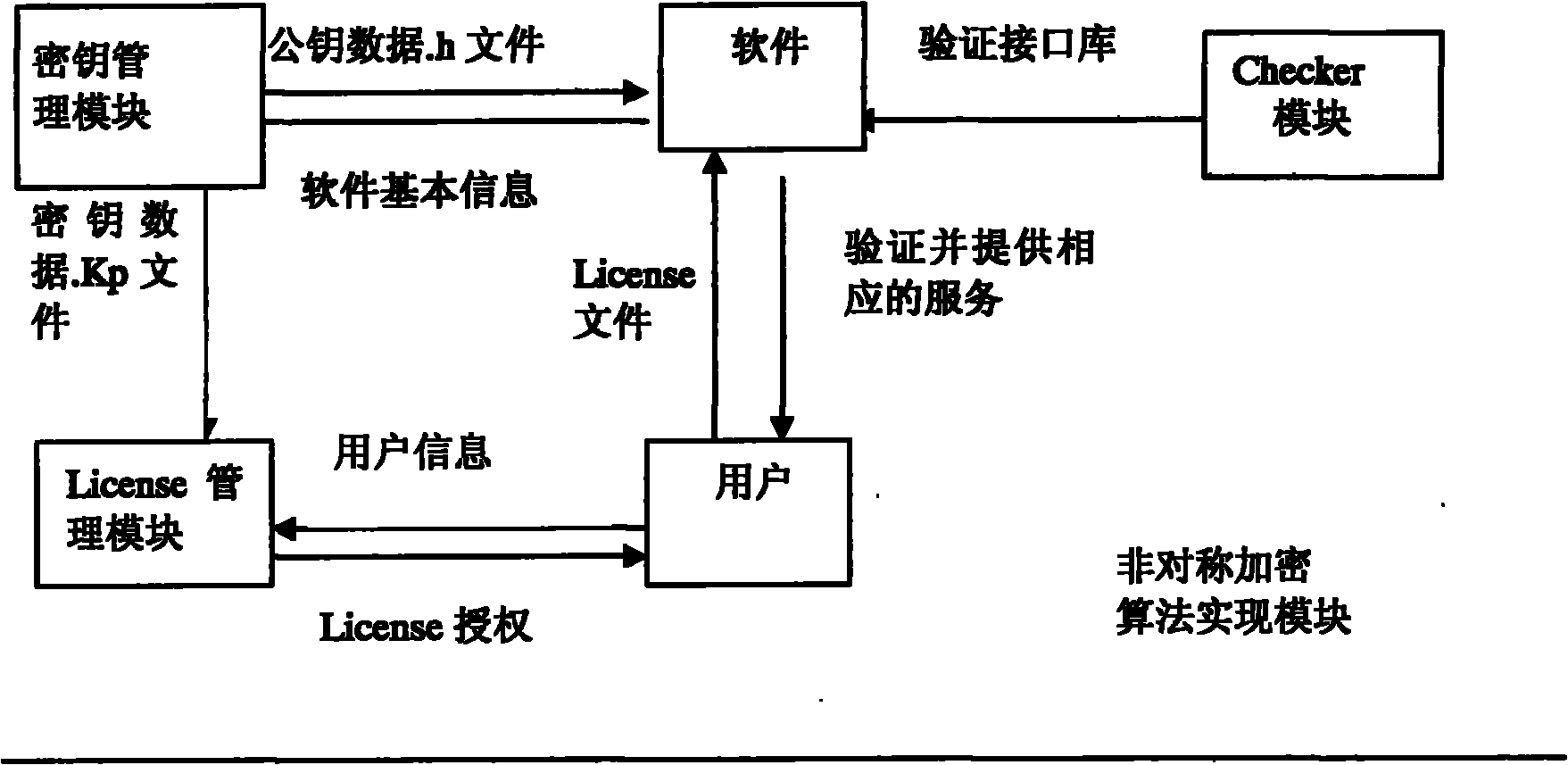
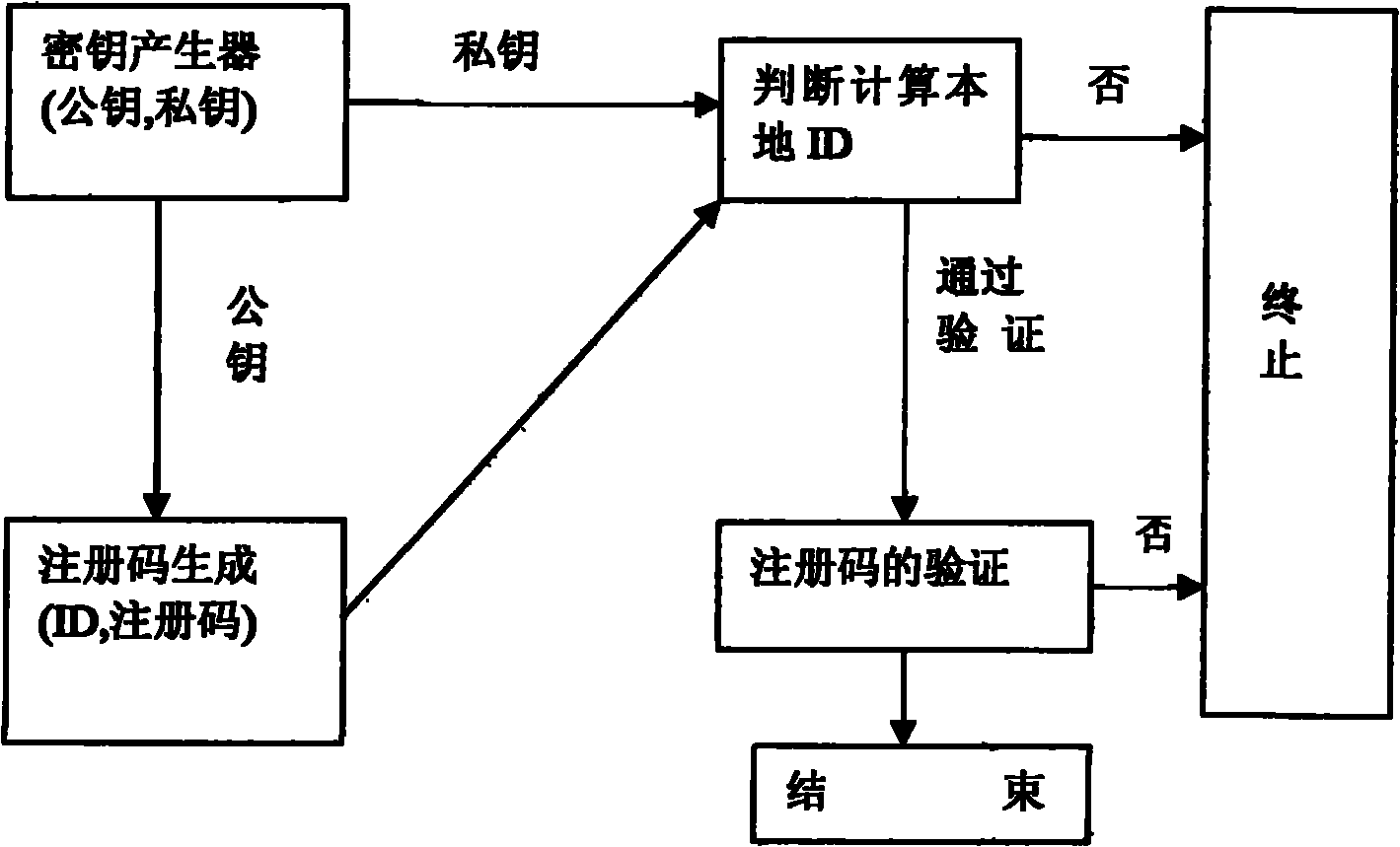
[0036] (1) First, the key generation module generates a public key / private key pair with a certain length through a random key generator. The public key is used by the registration code verification module, and the private key is used by the registration code generation module.
[0037] (2) The host ID generation module calculates a fixed-length ID according to the hardware information of the host (disk serial number, physical address of the network card and other unique hardware host identifiers) and a random number Rand. The software user hands over the host ID to the software developer.
[0038] (3) The registration code calculation module calculates the corresponding registration code according to the host ID and the random number Rand, and the registration code is the digital signature of the host ID, which is signed using the private key provided by the key generation module. The software dev...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com