Patents
Literature
68results about How to "Easy to add and delete" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
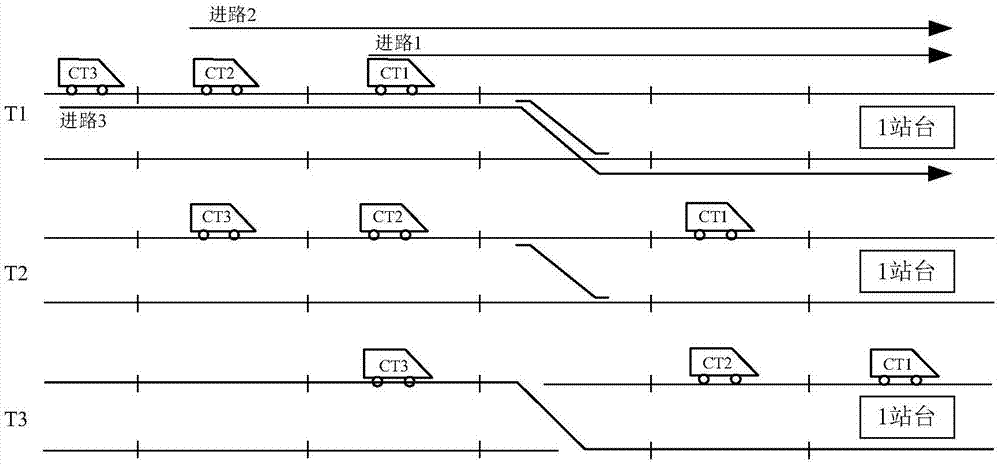
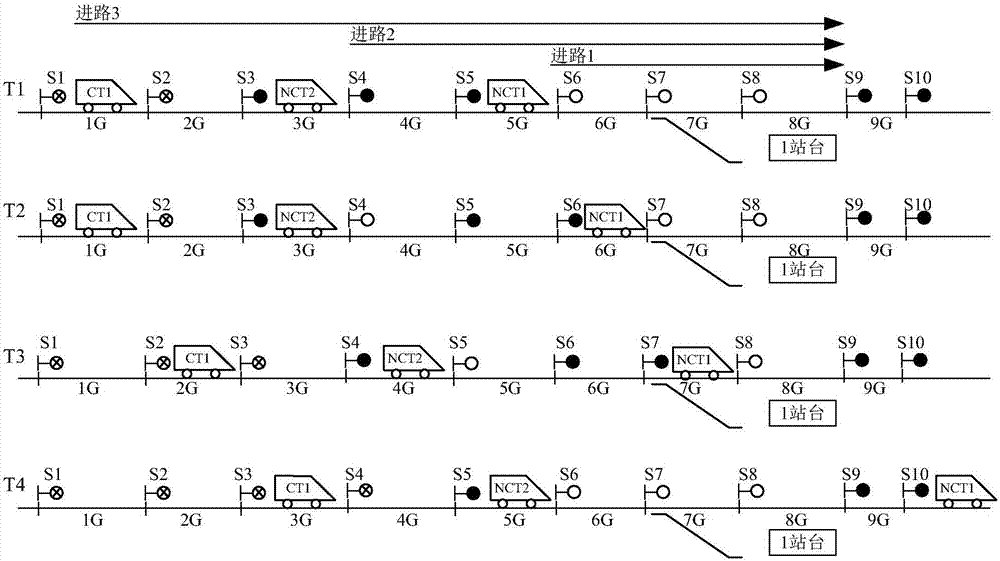
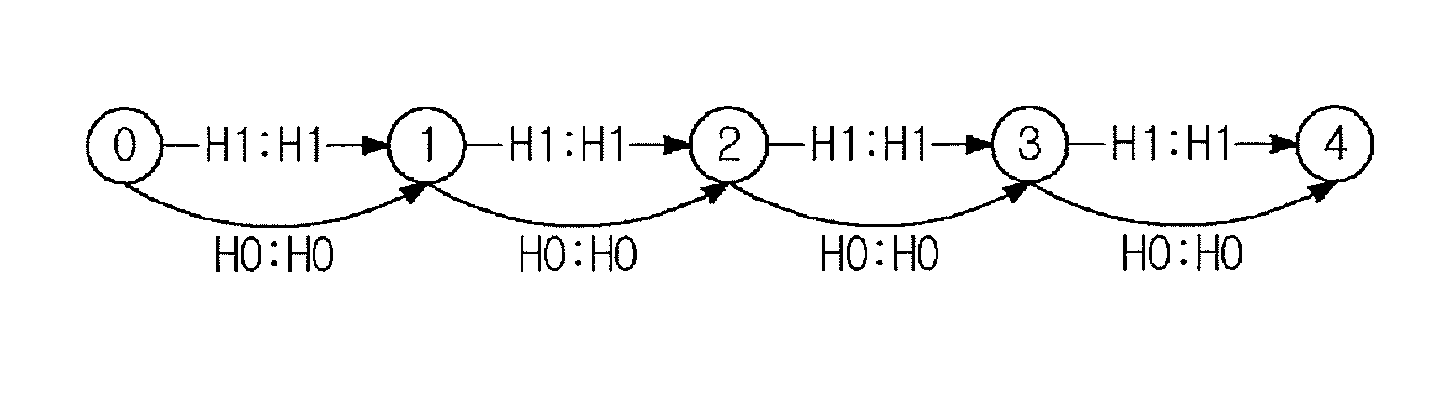
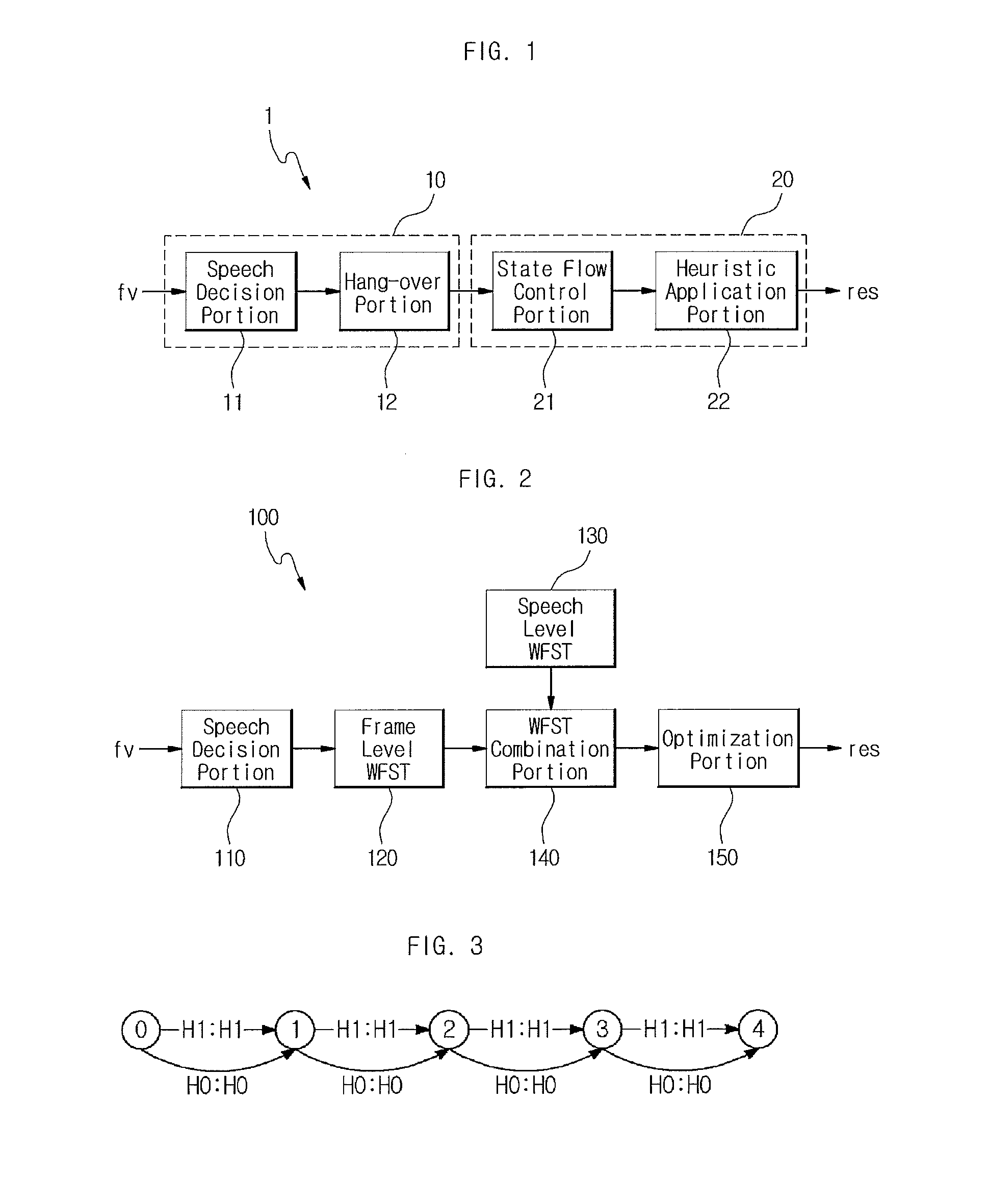
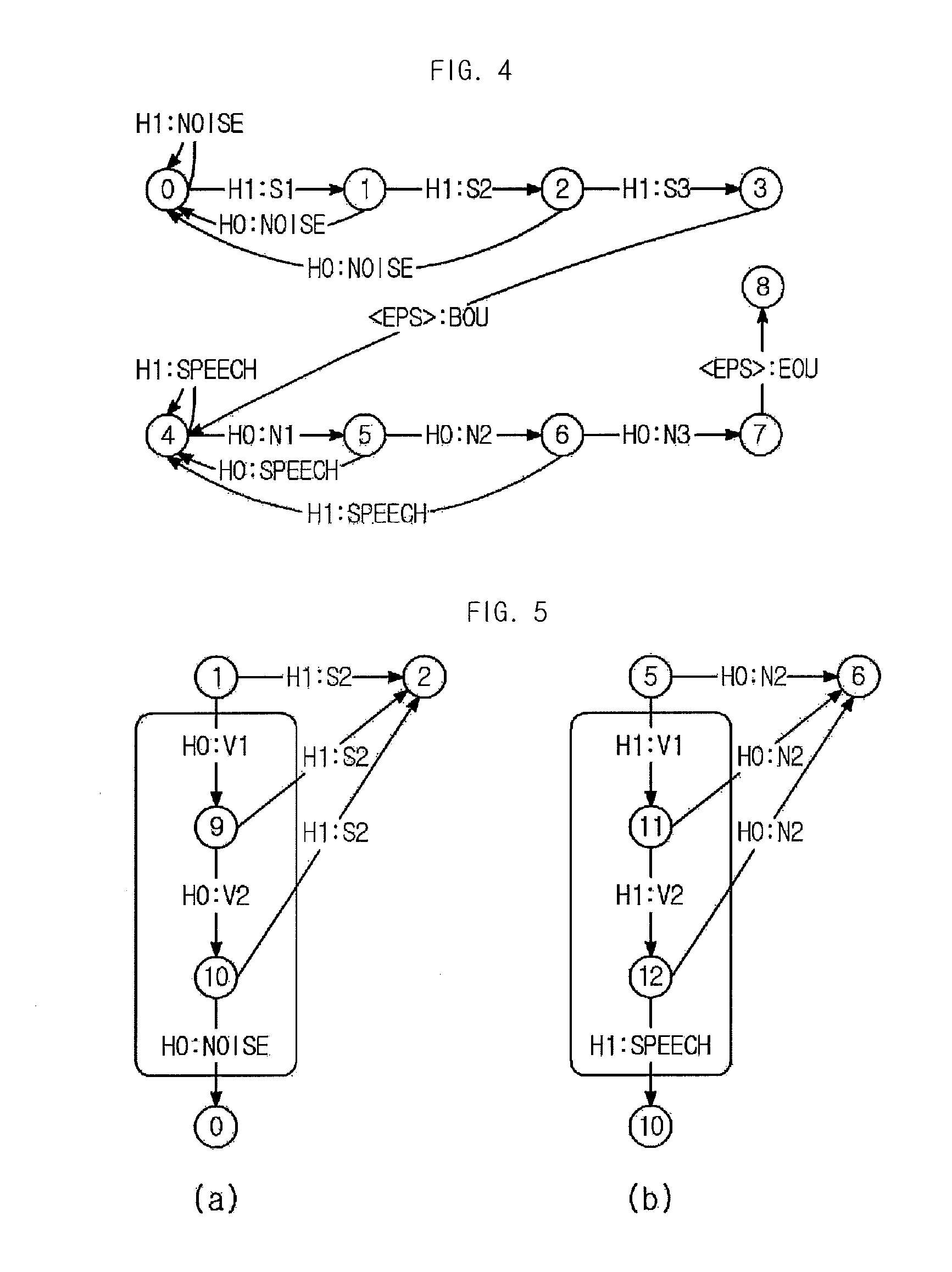
Method and apparatus for detecting speech endpoint using weighted finite state transducer
InactiveUS9396722B2Easy to add and deleteAvoid mistakesSpeech recognitionFeature vectorFinite state transducer
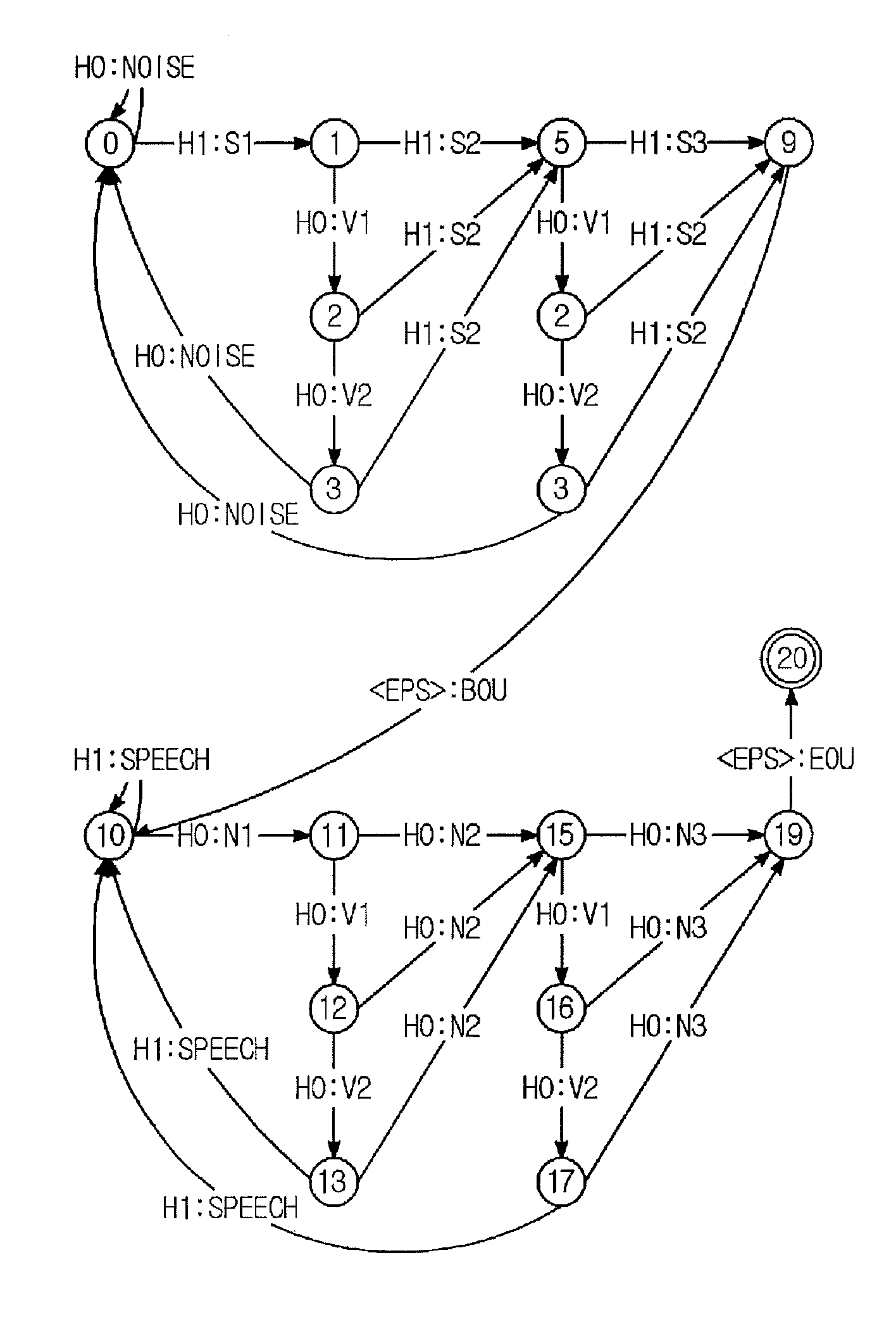
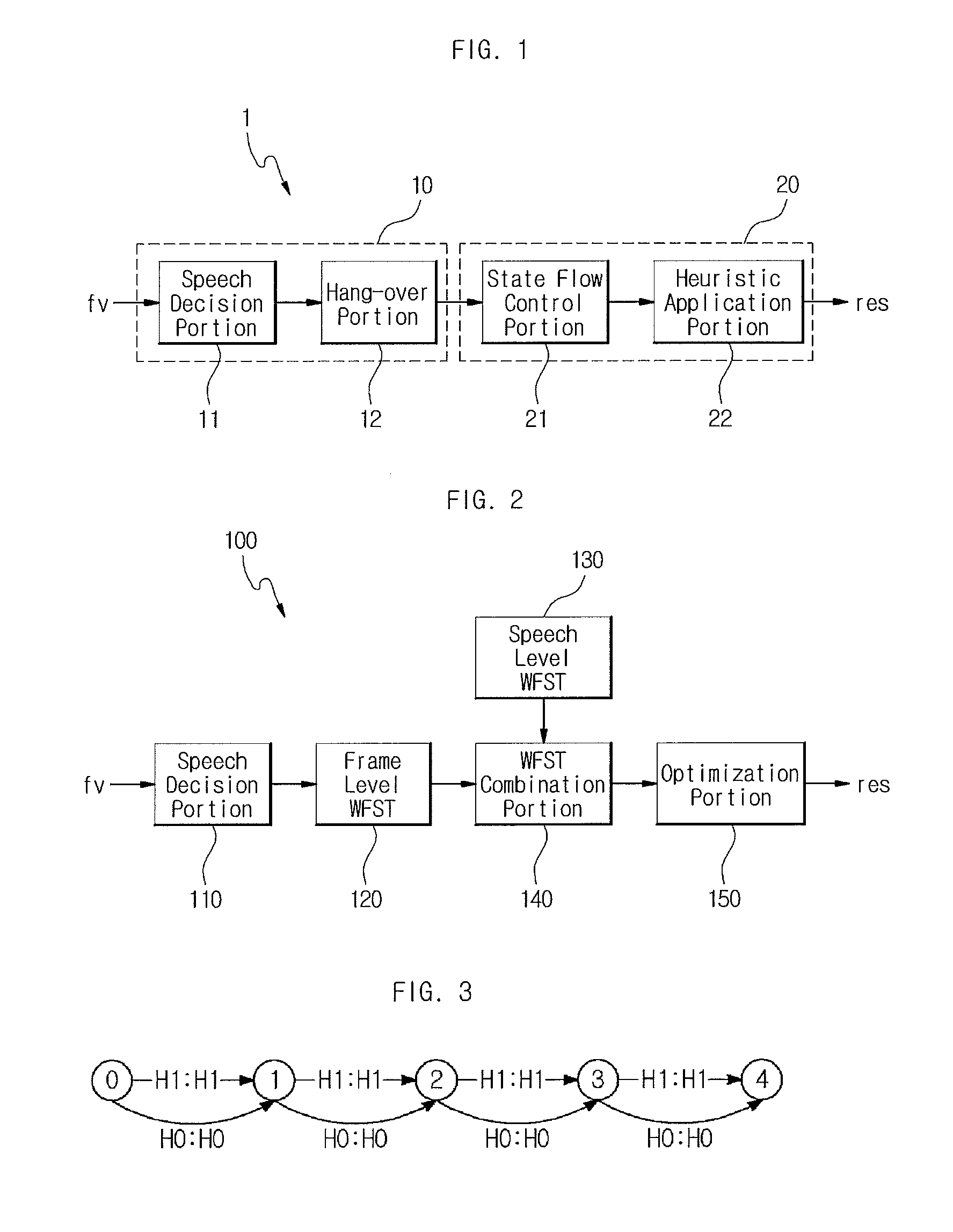
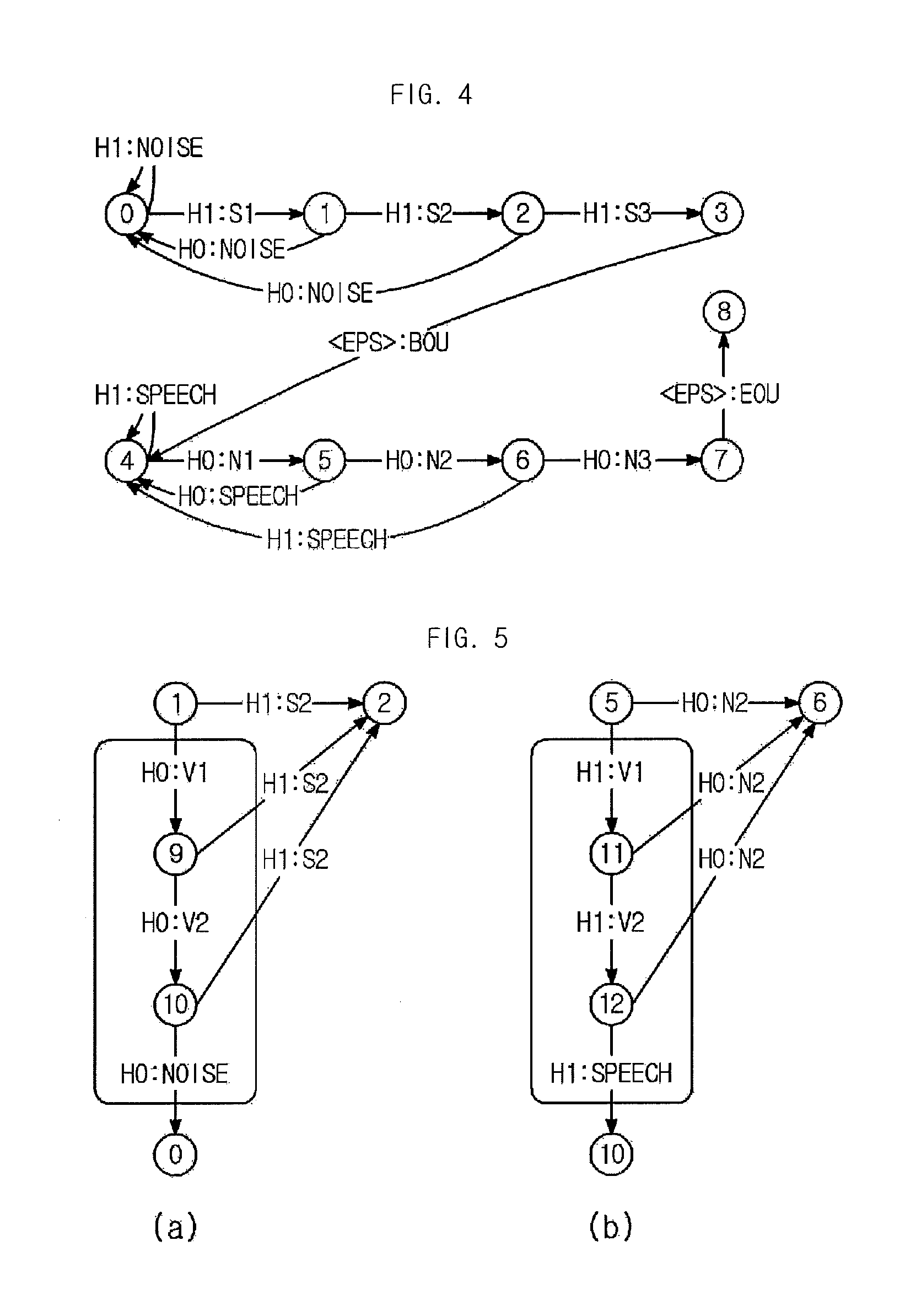
Disclosed are an apparatus and a method for detecting a speech endpoint using a WFST. The apparatus in accordance with an embodiment of the present invention includes: a speech decision portion configured to receive frame units of feature vector converted from a speech signal and to analyze and classify the received feature vector into a speech class or a noise class; a frame level WFST configured to receive the speech class and the noise class and to convert the speech class and the noise class to a WFST format; a speech level WFST configured to detect a speech endpoint by analyzing a relationship between the speech class and noise class and a preset state; a WFST combination portion configured to combine the frame level WFST with the speech level WFST; and an optimization portion configured to optimize the combined WFST having the frame level WFST and the speech level WFST combined therein to have a minimum route.
Owner:ELECTRONICS & TELECOMM RES INST
Method for structuring and searching information
InactiveUS6691123B1Low costEasy to add and deleteDigital data information retrievalData processing applicationsThe InternetDigital storage
A system for structuring digitally stored information and methods for searching the resulting structure are described. The structuring system comprises a database comprising a number of cells arranged in rows and columns for holding pieces of data representing the information. Only one piece of data may be stored in each cell and the pieces of data contained in cells in one row of the database constitutes a certain information. This information may be files on a computer hard disk, pages on the www etc. An index for each unique piece of data occurring in the database, where each index table providing information concerning all locations of that unique piece of data in the database, a main index listing once all the unique pieces of data in the database together with a corresponding index table identifier, the index table identifier providing a link to the corresponding index table for that particular piece of data, are also necessary elements in the structuring system, The structure of the database / index system in itself provides fast and simple access to the information contained therein. The information structuring system and the methods for structuring and searching digitally stored information may e.g. be used in a search engine for the Internet, in a mobile phone, WAP or as a search system for retrieving files and controlling the information stored in a LAN or computer hard disk.
Owner:IMP TECH
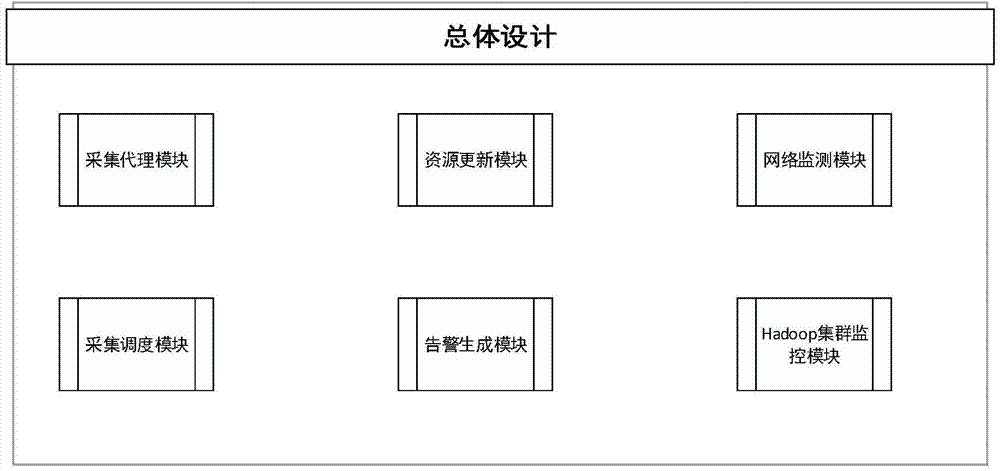
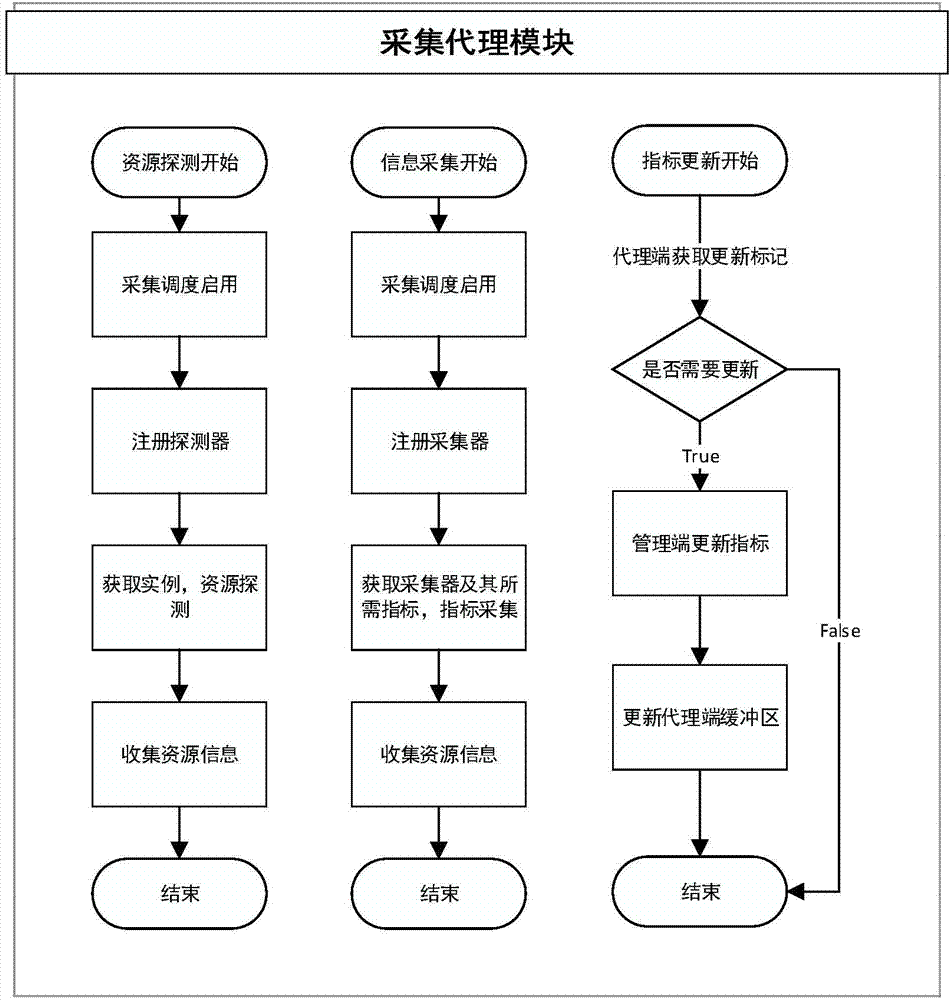
Distributed monitoring system based on hadoop cluster and method thereof
InactiveCN103618644ASimple structureEasy to implementData switching networksObservation dataMonitoring system
The invention relates to a distributed monitoring system based on a hadoop cluster and a method thereof. The system comprises a collection agency module, a resource updating module, a network monitoring module, a collection scheduling module, a warning generating module and a hadoop cluster monitoring module, wherein the hadoop cluster monitoring module is connected with the collection agency module, the resource updating module, the network monitoring module, the collection scheduling module and the warning generating module. The method includes the steps of (1) collecting needed detection resources and all index information, (2) storing and caching the collected data, (3) scheduling and updating collected information, (4) timely sampling to generate a data graph needed by a foreground web, (5) monitoring the network state of nodes in the cluster, and (6) determining whether a warning needs to be sent out according to a threshold value and generating warning information if the warning is needed. The distributed monitoring system can serve as an independent cluster monitoring system, a basic index database can be conveniently extended, a current index value can be taken back, a convergence view of indexes can be checked, and the trend of data timing sequences can be observed.
Owner:SUGON INFORMATION IND
Virtual wall system applied to mobile devices and realization method thereof
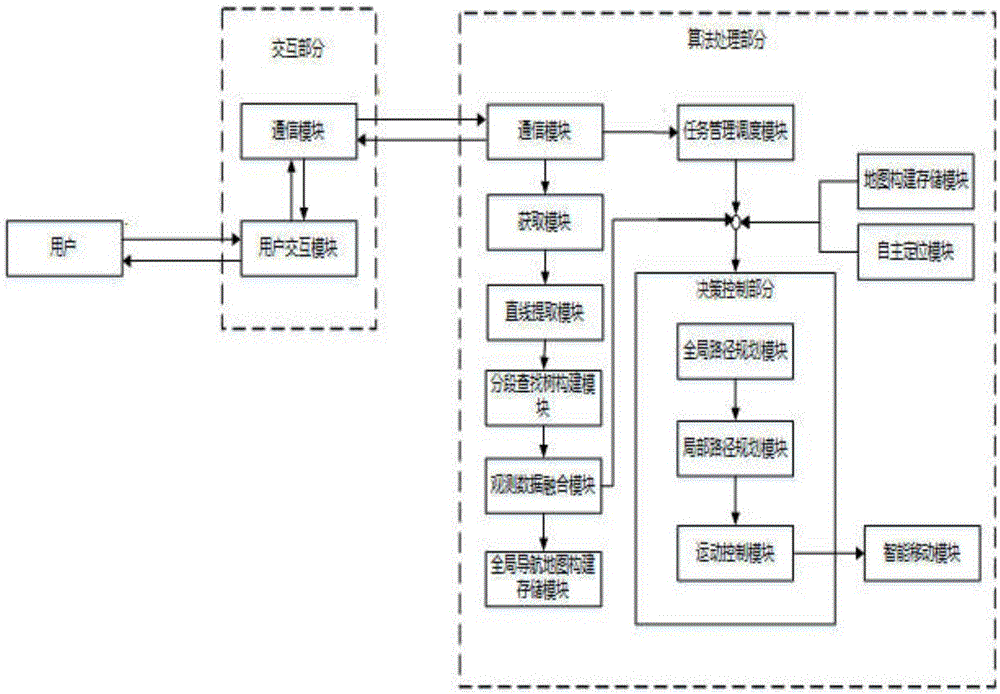
ActiveCN106843230AFacilitate data fusionEasy to useAutonomous decision making processNavigation instrumentsHuman–computer interactionMobile device
The invention discloses a virtual wall system applied to a mobile device and a realization method thereof. The virtual wall system applied to the mobile device comprises a communication module, an interaction module and an obtaining module, wherein the communication module is mainly used for transmitting relevant map information, virtual wall information, positioning information and task information, and achieves a bridge effect; the interaction module is used for setting, adding or deleting virtual wall information in any shape by a user through graphical editing environment, and sends the information to an intelligent moving algorithm processing part; the obtaining module obtains virtual wall information provided by the interaction module, and performs relevant data storage. The system and the realization method have the advantages that additional auxiliary hardware equipment can be produced without additional cost; the use is more convenient, flexible and fast.
Owner:SHANGHAI SLAMTEC
Multi-channel video and audio online-type playing and editing system
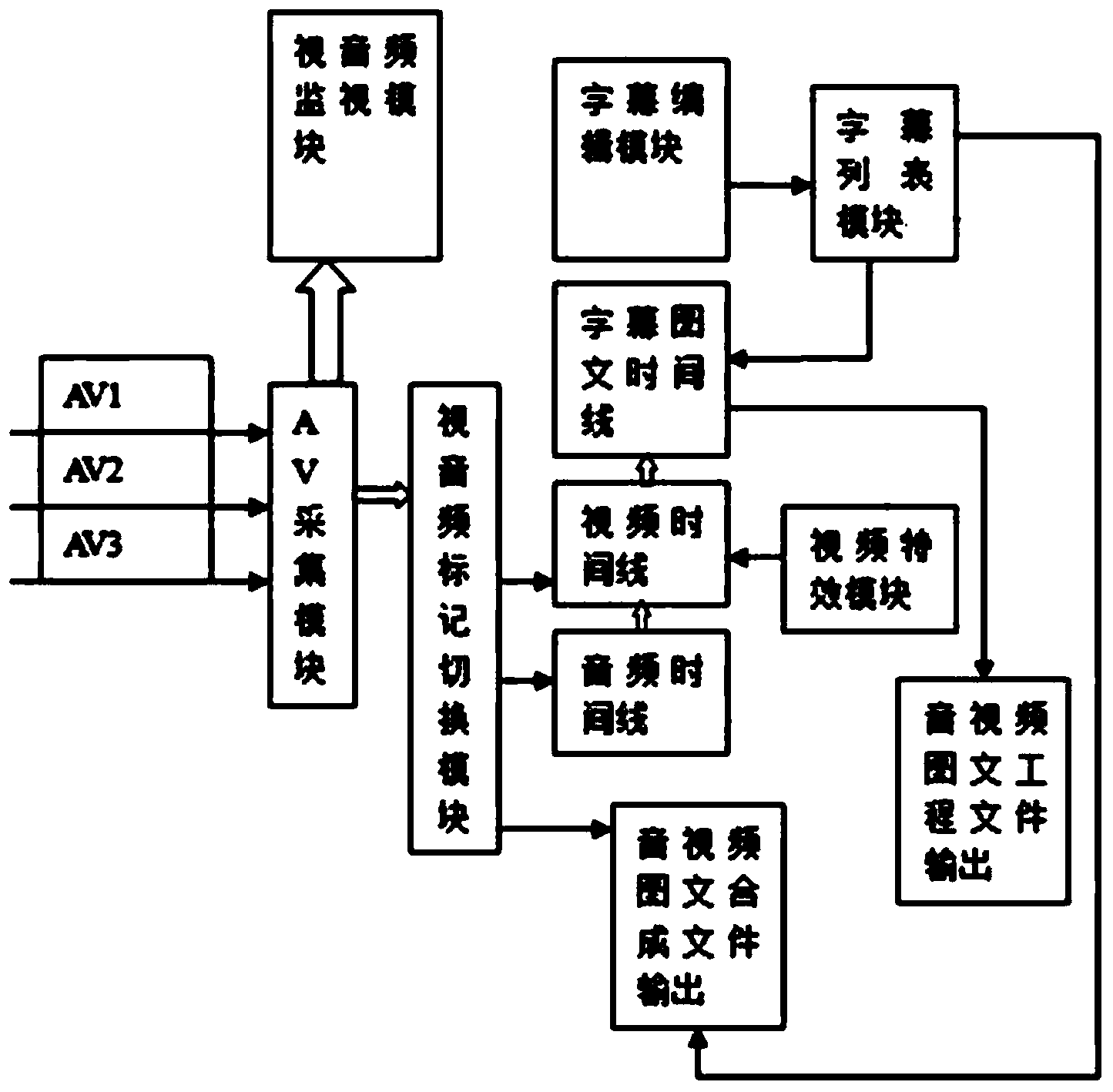
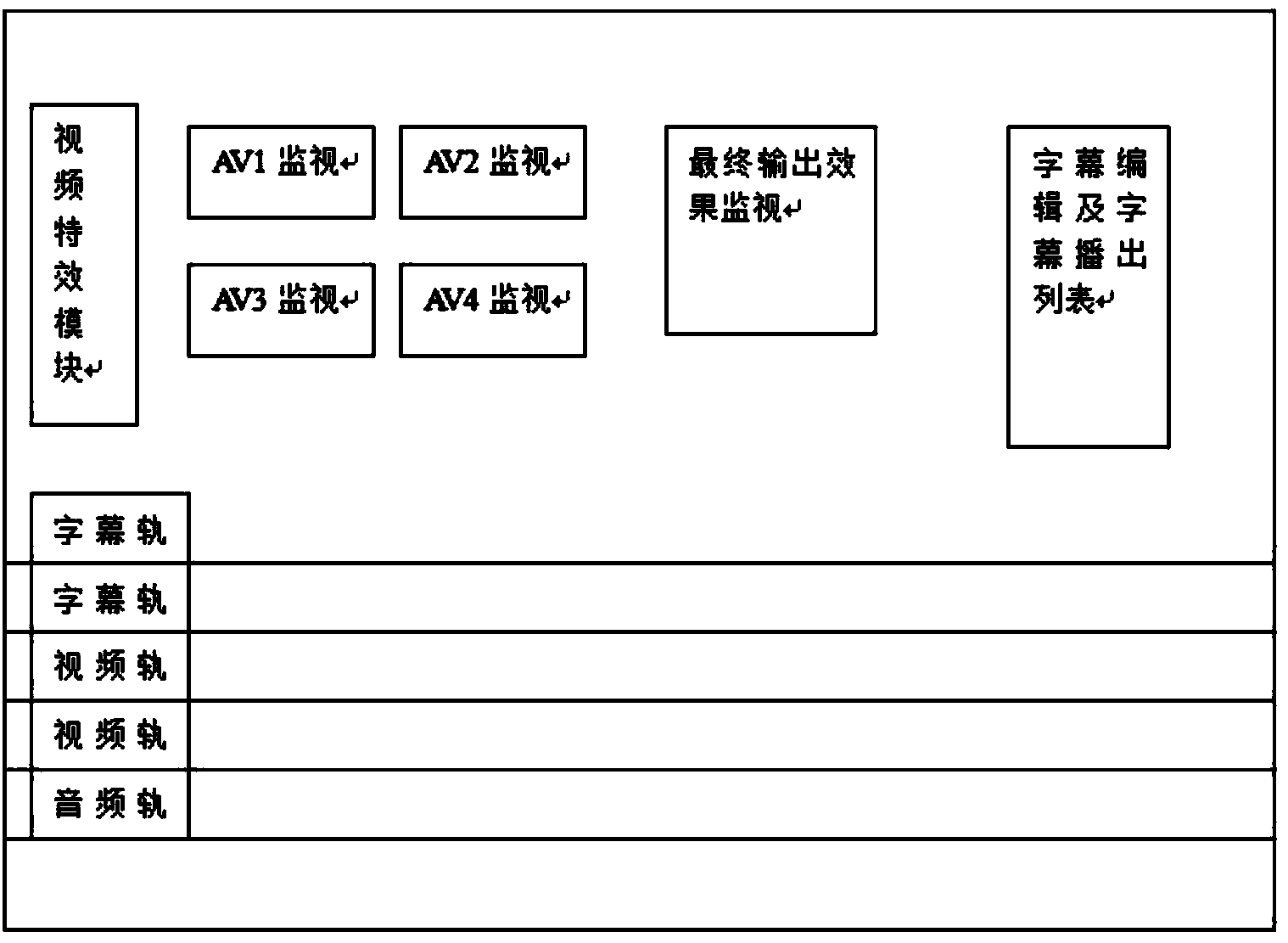
ActiveCN103761985ABacktracking implementation of director switchingToggle backtracking implementationTelevision system detailsElectronic editing digitised analogue information signalsSoftware systemTime line
The invention provides a multi-channel video and audio online-type playing and editing system which comprises a computer hardware system as an operation platform and a software system. The software system comprises a video and audio collecting module, a video and audio monitoring module, a video and audio marking and switching module, a video timeline module, an audio timeline module, a video and audio image-text composite file output module, a caption editing module, a caption listing module, a caption image-text timeline module and a video and audio image-text project file output module, wherein the video and audio collecting module is used for collecting signal sources, the video and audio monitoring module is used for monitoring the signal sources, the video and audio marking and the switching module is used for marking the collected signal sources, sending marked videos to the video timeline module to obtain editable video project files, sending marked audios to the audio timeline module to obtain editable audio project files and sending the videos and the audios to the video and audio image-text composite file output module to obtain composite finished video and audio files, the caption editing module, the caption listing module and the caption image-text timeline module are connected in sequence to form editable caption image-text project files, and the video and audio image-text project file output module is used for forming editable video and audio image-text project files. The multi-channel video and audio online-type playing and editing system can form finished files and editable project files and can achieve the functions of broadcasting director recall, simultaneous recording and editing, one-way recording and multi-way recording.
Owner:HUAKEFEIYANG
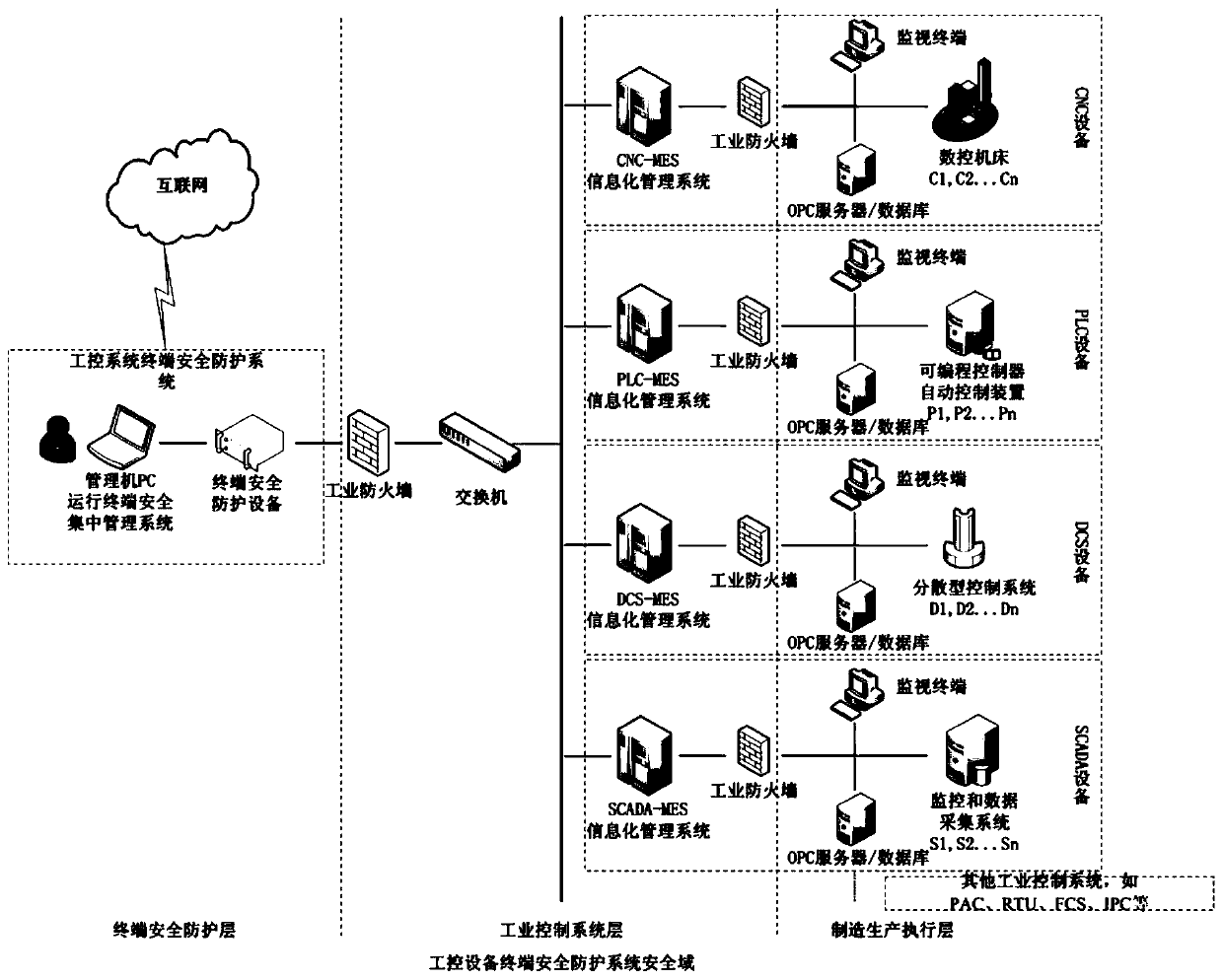
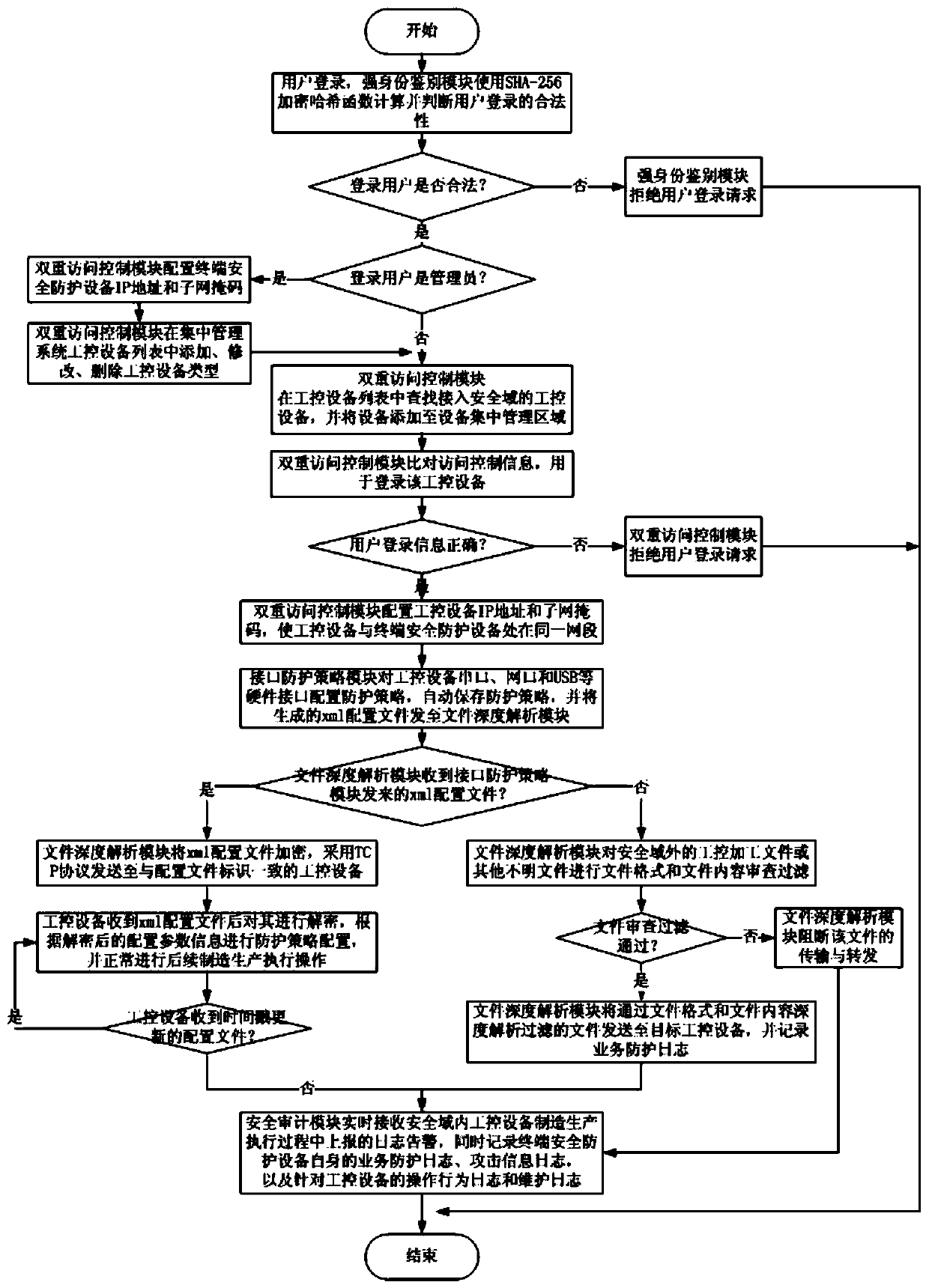
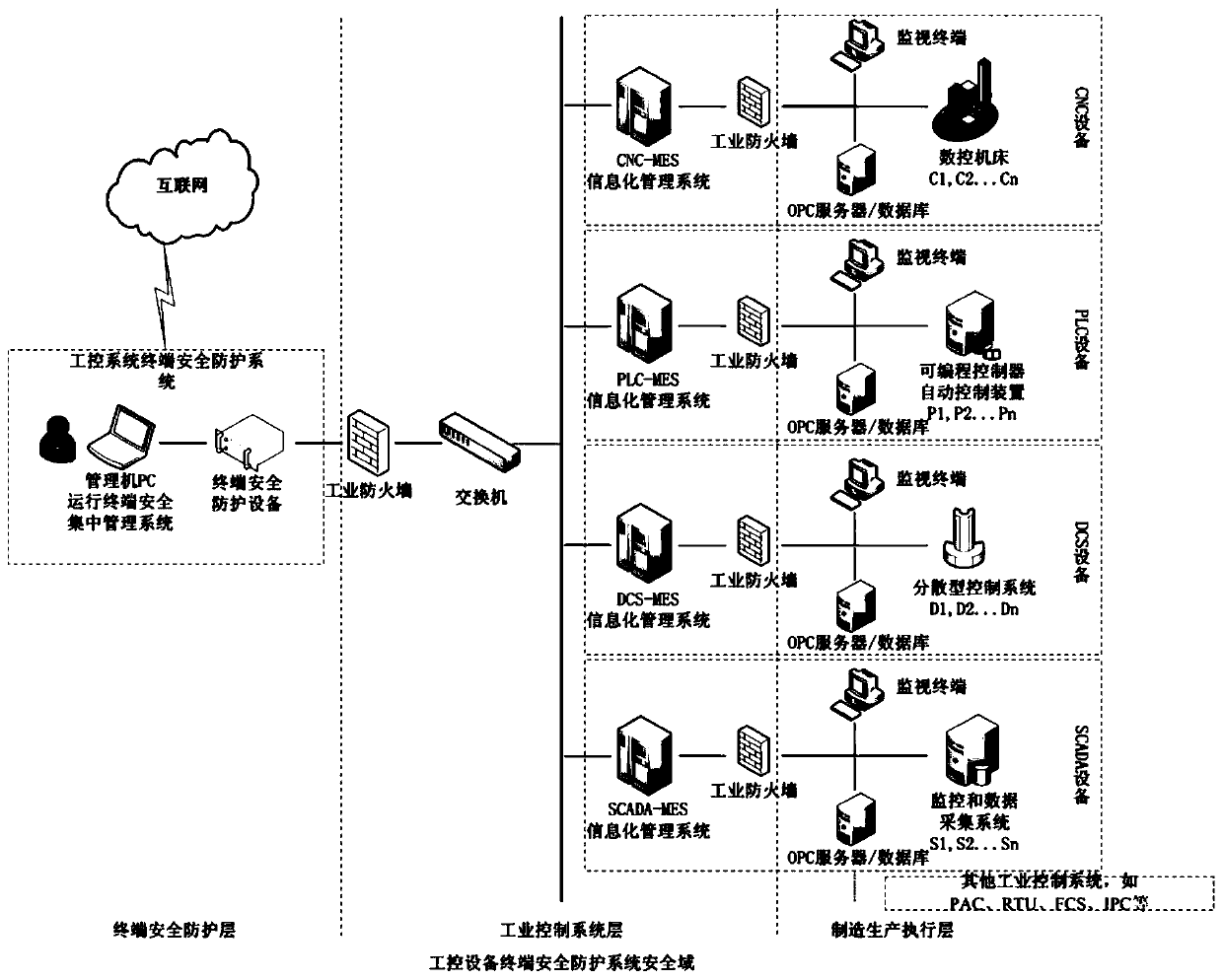
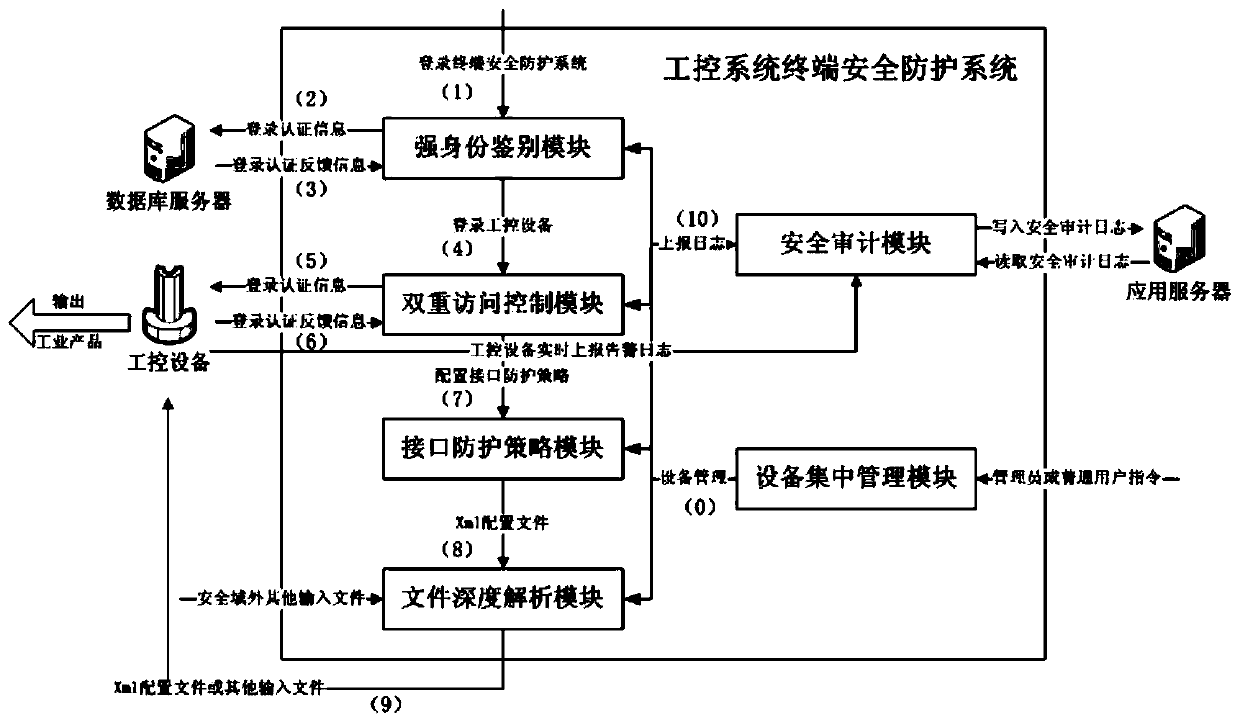
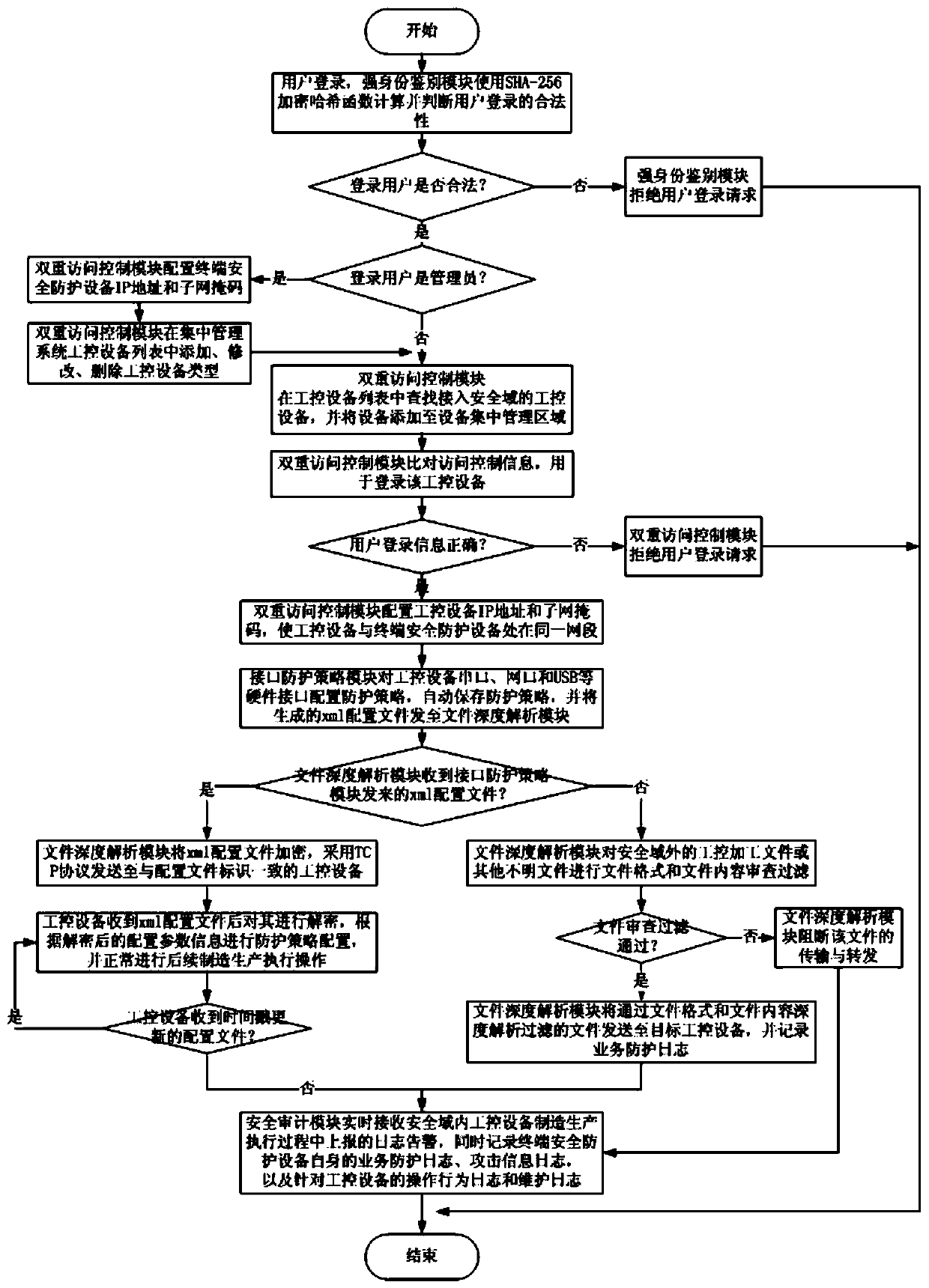
Industrial control system terminal safety protection method
ActiveCN109995796AImprove the protective effectImprove the level ofEncryption apparatus with shift registers/memoriesComputer compatibilityEngineering
The invention belongs to the technical field of industrial control system terminal safety protection, and particularly relates to an industrial control system terminal safety protection method. The method is implemented based on an industrial control system terminal safety protection system, and the system comprises terminal safety protection equipment and a terminal safety centralized managementsystem. According to the scheme, a series of technical means of strong identity authentication, dual access control, an interface protection strategy, file deep analysis, security audit and equipmentcentralized management are comprehensively applied; malicious behaviors such as network attack and illegal access in operation of industrial control system equipment are effectively blocked, and centralized configuration and management of security protection strategies of a plurality of industrial control system equipment terminals of the same type or different types are realized at the same time.The scheme has the advantages that the safety protection level of the industrial control equipment terminal is high, centralized and unified management of multiple pieces of equipment is supported, and the centralized management platform is suitable for multiple application environments and multiple industrial protocols, good in compatibility, flexible in protection strategy configuration, efficient in alarm reporting and equipment management and the like.
Owner:北京京航计算通讯研究所
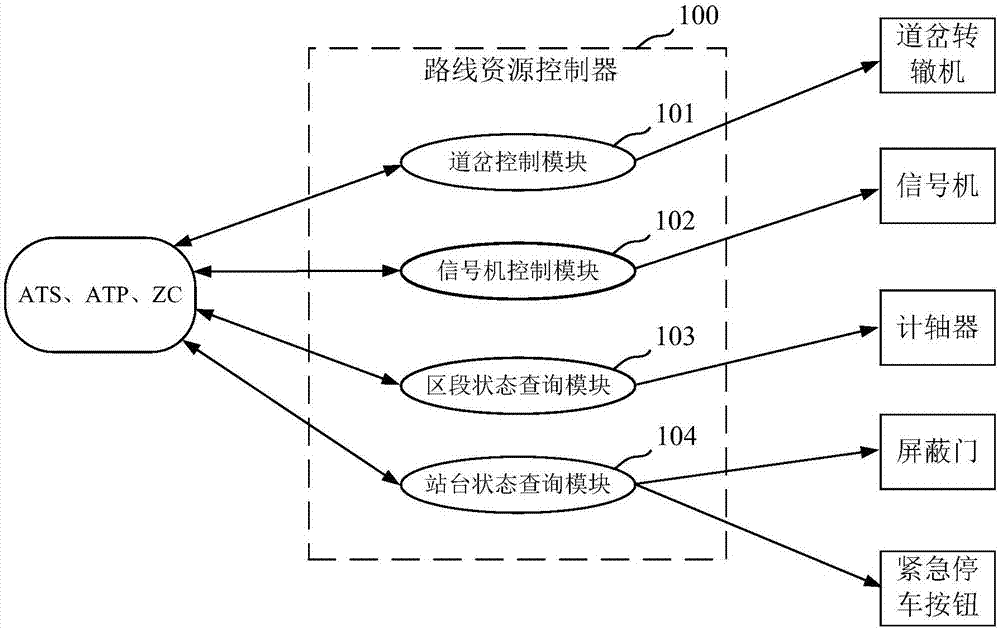
Circuit resource controller
ActiveCN107571889AIncrease profitImprove driving efficiencyRailway traffic control systemsMachine controlComputer module
The invention discloses a circuit resource controller. The controller comprises a turnout controlling module, a signal machine controlling module, a zone controlling module and a platform controllingmodule; the turnout controlling module is configured to conduct priority level sequencing on turnout requisition applications issued by application equipment and orderly distribute the right of turnout requisition in order of priority from high to low; the signal machine controlling module is configured to receive route applications of a train automatic monitoring system and control lamp displaying of a signal machine in an application route; the zone controlling module is configured to collect a occupying / idle state of an axle-counting zone and receive state query applications for the zone and feed back the state of query equipment to applicants; and the platform controlling module is configured to collect the state of an emergency stopping button and a shield door and receive state queryapplications for the platform and feed back the query result to the applicants.
Owner:HUNAN CRRC TIMES SIGNAL & COMM CO LTD
Method and apparatus for detecting speech endpoint using weighted finite state transducer
InactiveUS20140379345A1Easy to addEasy to deleteSpeech recognitionFeature vectorFinite state transducer
Disclosed are an apparatus and a method for detecting a speech endpoint using a WFST. The apparatus in accordance with an embodiment of the present invention includes: a speech decision portion configured to receive frame units of feature vector converted from a speech signal and to analyze and classify the received feature vector into a speech class or a noise class; a frame level WFST configured to receive the speech class and the noise class and to convert the speech class and the noise class to a WFST format; a speech level WFST configured to detect a speech endpoint by analyzing a relationship between the speech class and noise class and a preset state; a WFST combination portion configured to combine the frame level WFST with the speech level WFST; and an optimization portion configured to optimize the combined WFST having the frame level WFST and the speech level WFST combined therein to have a minimum route.
Owner:ELECTRONICS & TELECOMM RES INST
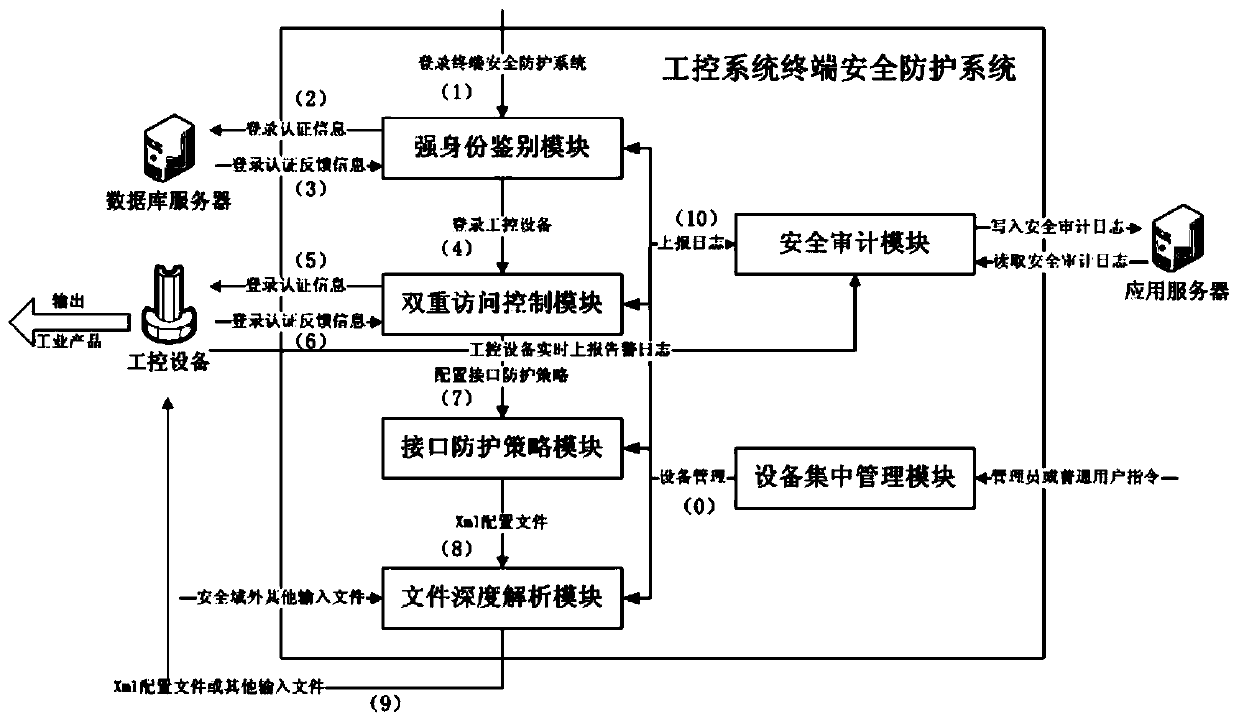
Industrial control system terminal safety protection system
ActiveCN109976239AImprove the protective effectImprove the level ofProgramme controlComputer controlEngineeringCentralized management
The invention belongs to the technical field of safety protection of industrial control system terminals and particularly relates to an industrial control system terminal safety protection system. Theindustrial control system terminal safety protection system comprises a terminal safety protection device and a terminal safety centralized management system. According to the scheme, a series of technological means of strong identity authentication, double access control, an interface protection strategy, file depth analysis, safety audit and equipment centralized management are comprehensivelyapplied, so that malicious behaviors such as network attack, illegal access and the like during operation of the industrial control system equipment are effectively blocked, and meanwhile, centralizedconfiguration and management on safety protection strategies of a plurality of industrial control system equipment terminals of the same type or different types can be realized. The scheme has the advantages that the safety protection level of the industrial control equipment terminal is high, the centralized and unified management of multiple equipment is supported, the centralized management platform is suitable for various application environments and multiple industrial protocols, the compatibility is good, adding and deleting of the equipment is simple, configuration of the protection strategies is flexible, alarm reporting and equipment management are efficient, and the like.
Owner:北京京航计算通讯研究所
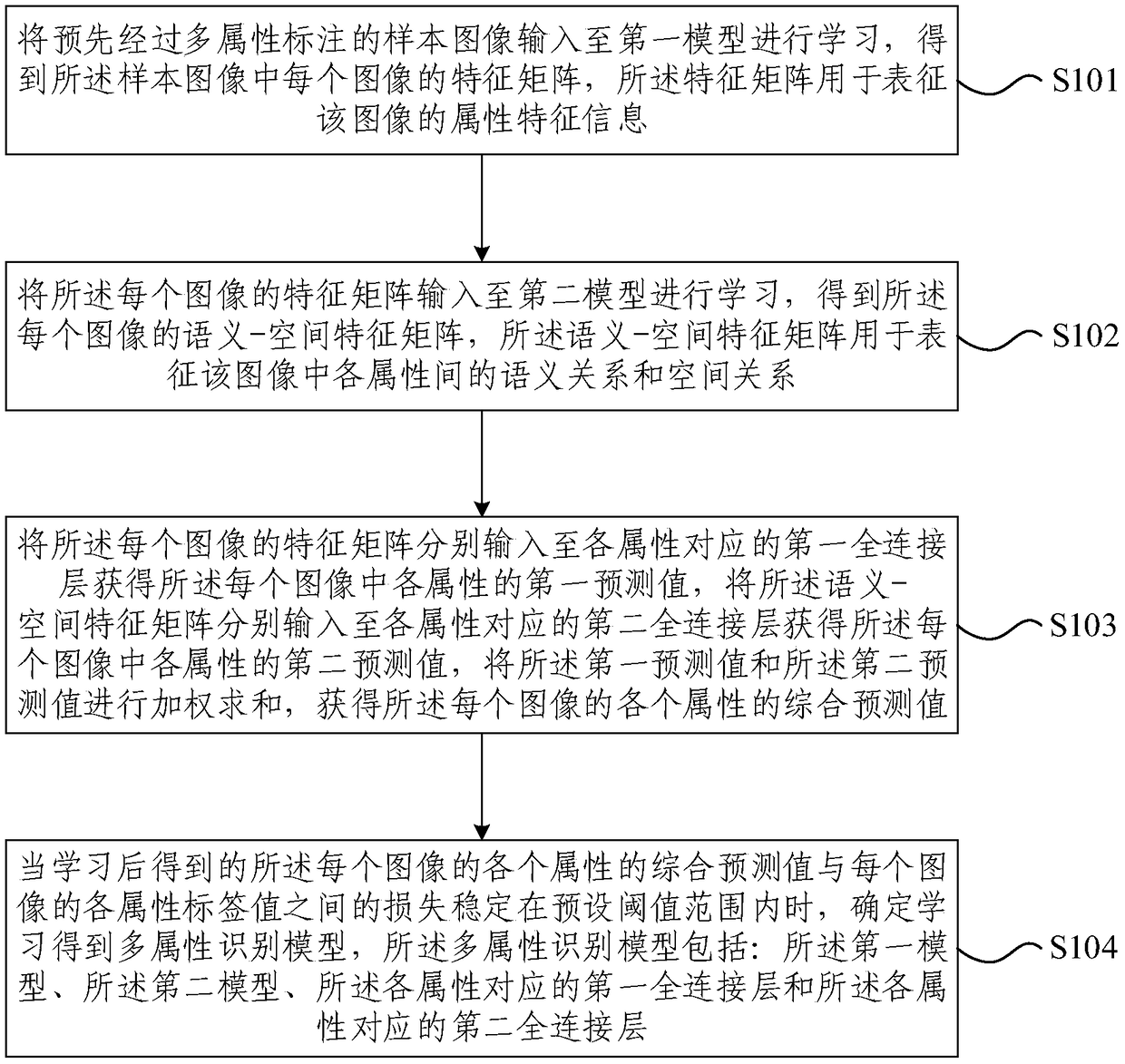
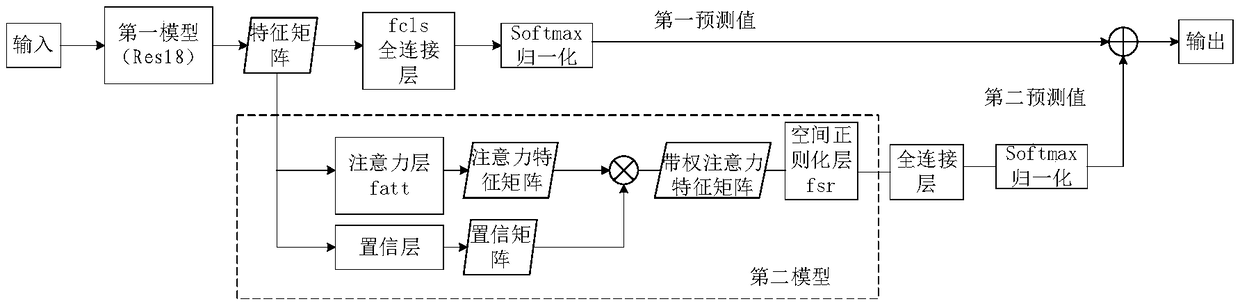
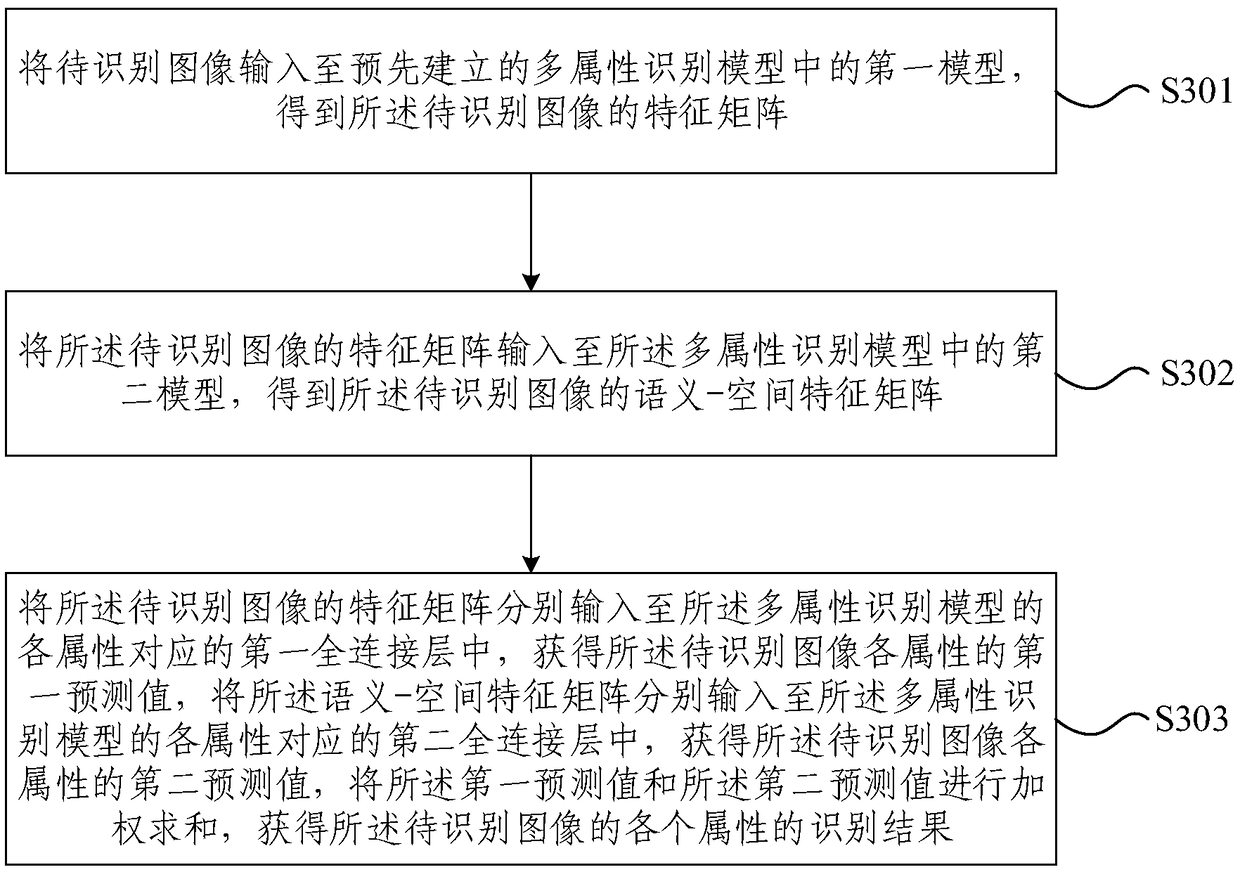
Method and device for establishing multi-attribute recognition model and method for multi-attribute recognition
ActiveCN109117781AImprove recognition accuracyReduce training costsBiometric pattern recognitionNeural architecturesSample imageMachine learning
The embodiment of the invention provides a method for establishing a multi-attribute recognition model, a device and a multi-attribute recognition method. The method comprises the following steps: inputting a sample image labeled with multi-attributes in advance to a first model for learning, and obtaining a characteristic matrix of each image in the sample image; the feature matrix of each imagebeing input to the second model for learning to obtain the semantics of each image; the first predictive value of each attribute being obtained according to the feature matrix, and the second predictive value of each attribute being obtained according to the semantic- spatial eigenmatrix; obtaining a second prediction value of each attribute by a spatial feature matrix, weighting and summing the first prediction value and the second prediction value to obtain a comprehensive prediction value of each attribute of each image; when the loss between the synthesized prediction value and the label value is stable in the preset threshold range, the multi-attribute recognition model can be obtained by learning. The embodiment of the invention can effectively utilize the labeling information to obtain the spatial and semantic association of the multiple attributes, and the recognition accuracy is high.
Owner:北京一维大成科技有限公司
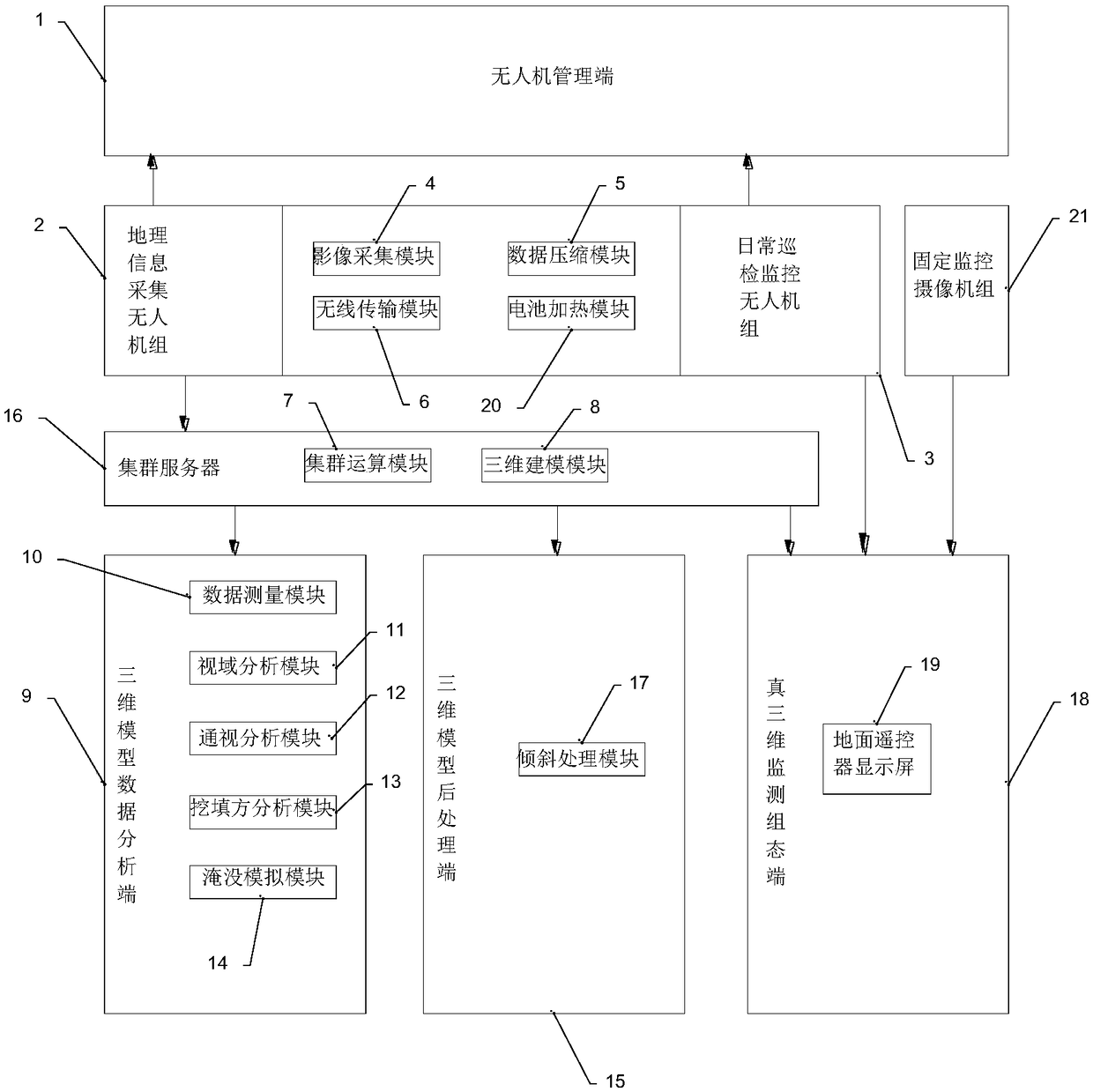
Security monitoring system and method of tailings pond based on unmanned aerial vehicle and three-dimensional modeling technology
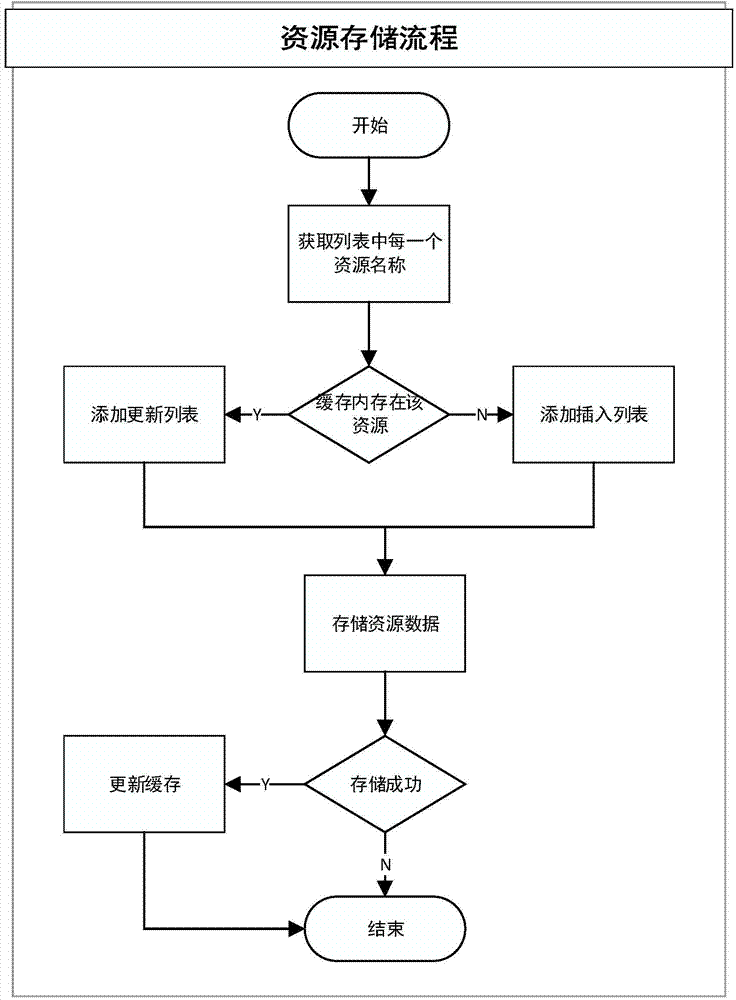
InactiveCN109269555AEasy to add and deleteEasy maintenanceTelevision system detailsDetails involving processing stepsData compressionTailings dam
The invention provides a security monitoring system and method of a tailings pond based on an unmanned aerial vehicle and a three-dimensional modeling technology. An image acquisition module is used for acquiring geographical information of a to-be-detected tailings pond; a data compression module is equipped with an encoder supporting an onvif protocol and used for compression coding of an acquired video signal, an audio signal and a data signal of the to-be-detected tailings pond; a wireless transmission module is equipped with antennas of 2.4 GHz and 5.8 GHz frequency bands and used for wireless data transmission between a geographical information acquisition unmanned aerial vehicle group and a daily tour inspection monitoring unmanned aerial vehicle group; a cluster operation module isused for performing cluster operation image processing on obtained image geographical information data of the to-be-detected tailings pond; and a three-dimensional modeling module is used for performing aerotriangulation resolution and remodeling on the obtained geographical information data of the to-be-detected tailings pond. According to the system and method, all-weather monitoring of surrounding environments including onsite transmission tail pipelines, tailings dams, water lines, phreatic lines, and tailings ponds without dead angles can be realized.
Owner:空中梦想(北京)科技有限公司
Modular design method for watt-hour meter software
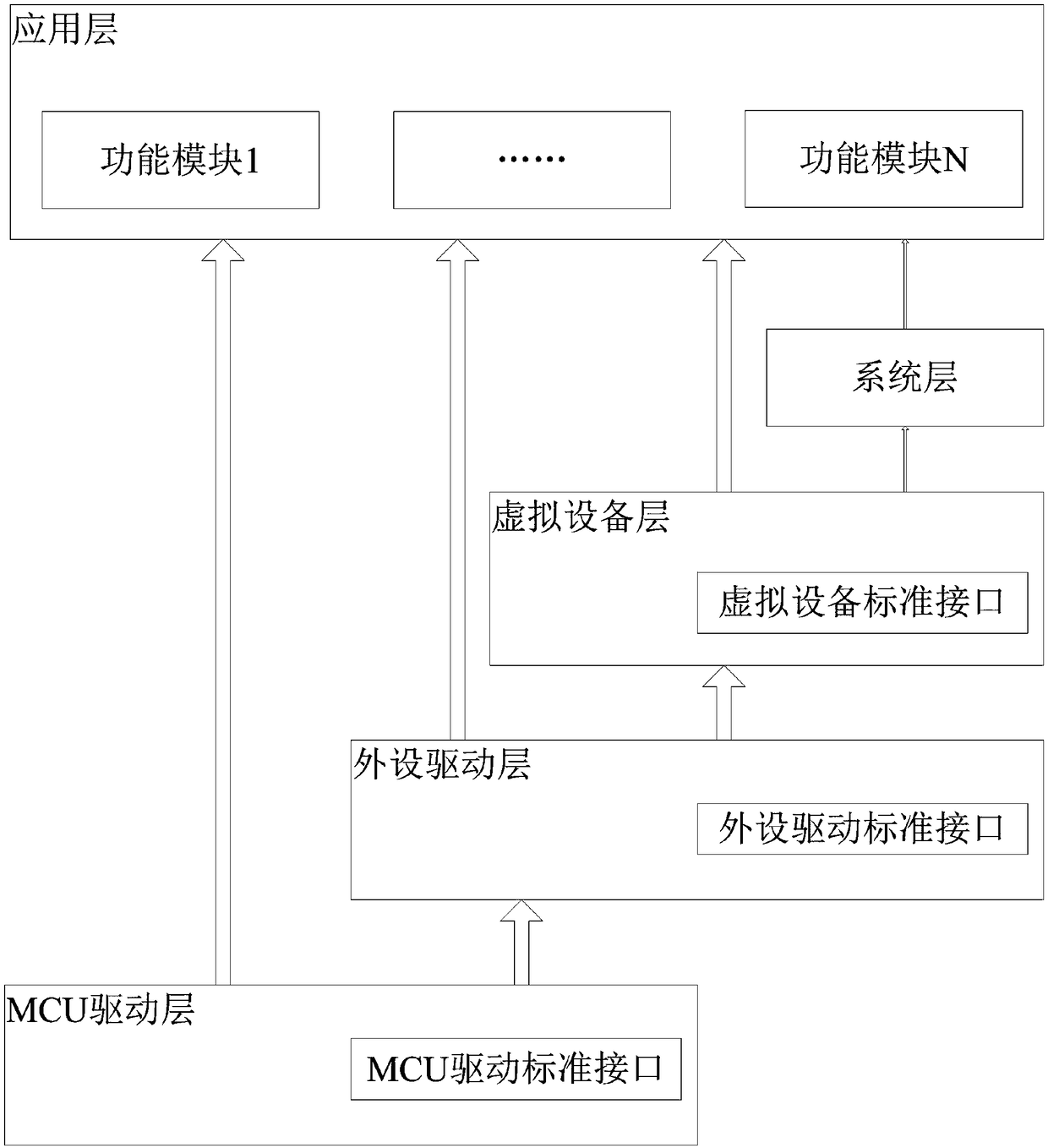
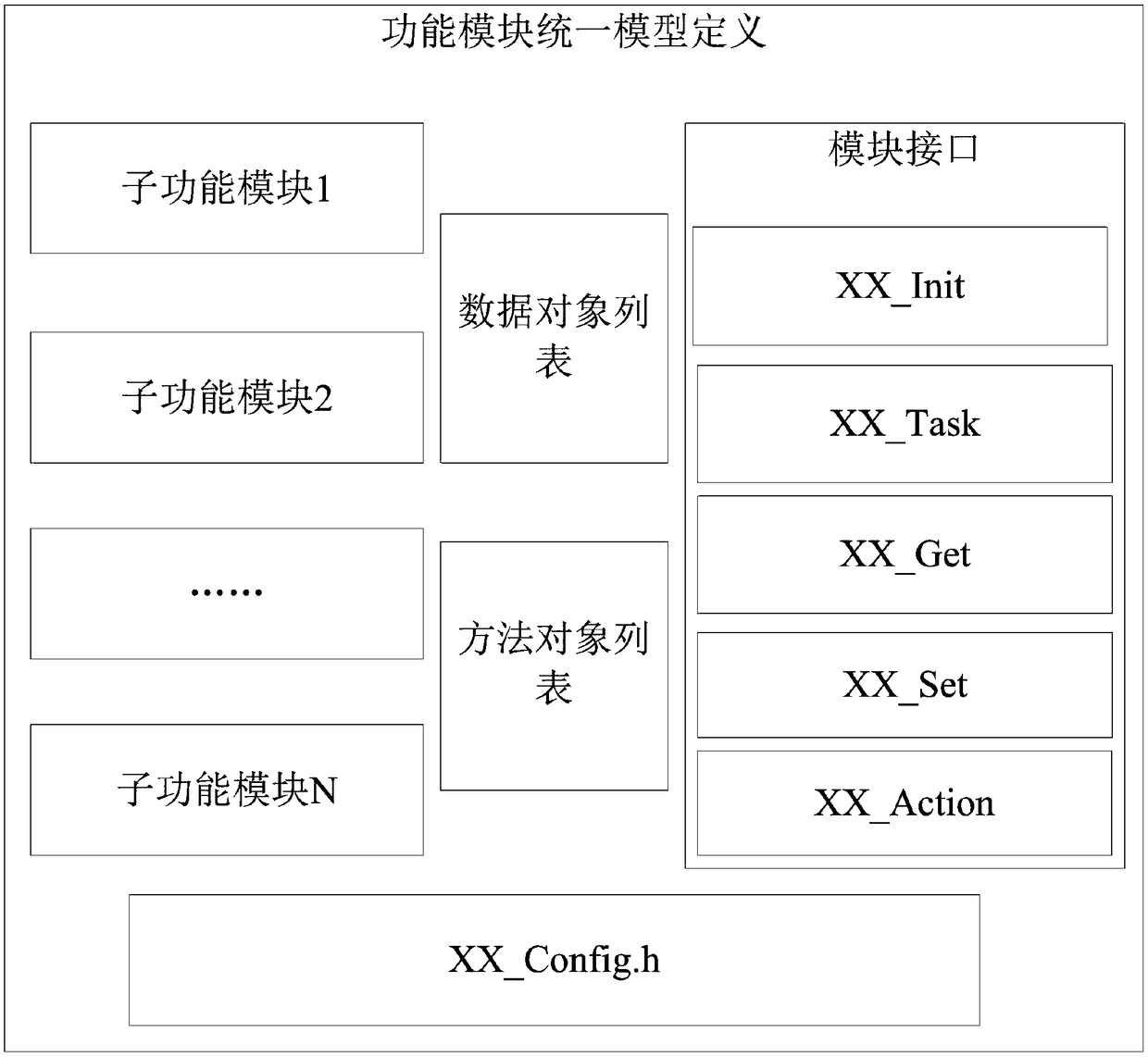
InactiveCN109271146AImprove porting development efficiencyImprove versatilityVersion controlSoftware designSoftware development processModularity
The invention discloses a modular design method for electric energy meter software, which comprises the following steps: electric energy meter software layering design, electric energy meter softwaremodule definition, module interaction definition, software module configuration management and electric energy meter software minimum system. The watt-hour meter software layered design is used to design the software layered and define the contents and calling rules of each level. The watt-hour meter software module definition is used to establish a unified software function module model. The module interaction definition is used to define data interaction rules between software modules. The software module configuration management performs macro definition of functional configuration optionsfor software modules; The watt-hour meter software minimum system is used to define the minimum configuration scheme of watt-hour meter software. The modularized design method of the electric energy meter software of the invention enables the software development process of the electric energy meter to be applicable to today's changeable market environment, the software development speed is fast,the functions are diversified and the cost is low.
Owner:WASION GROUP HLDG
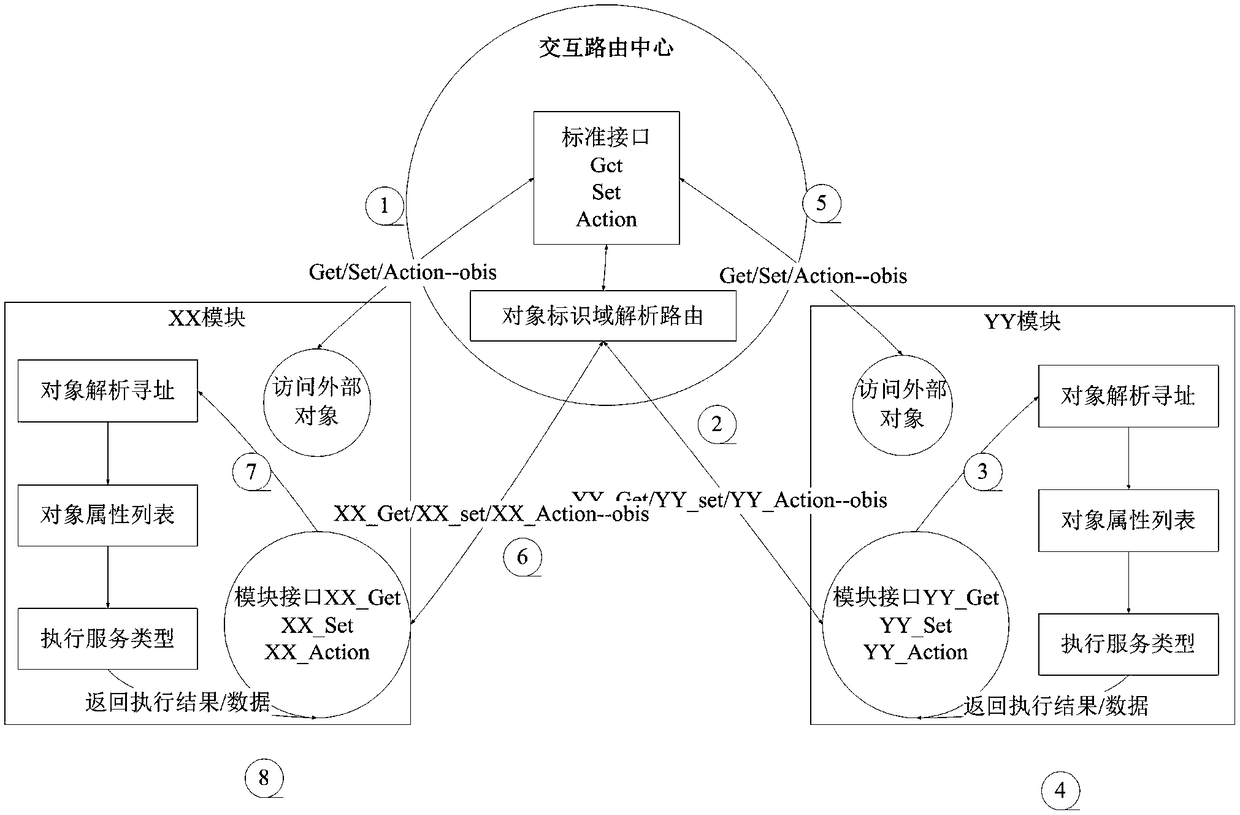
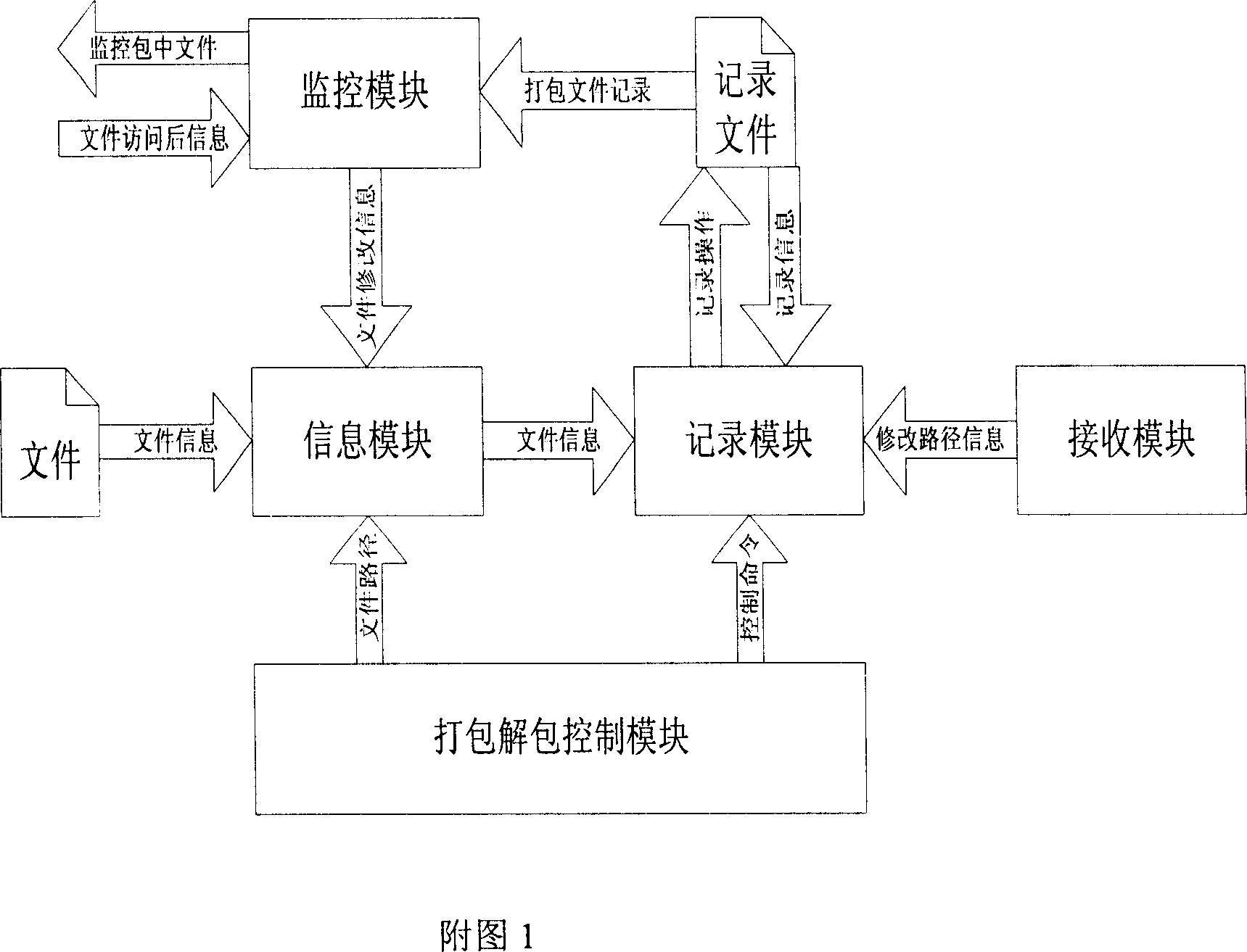
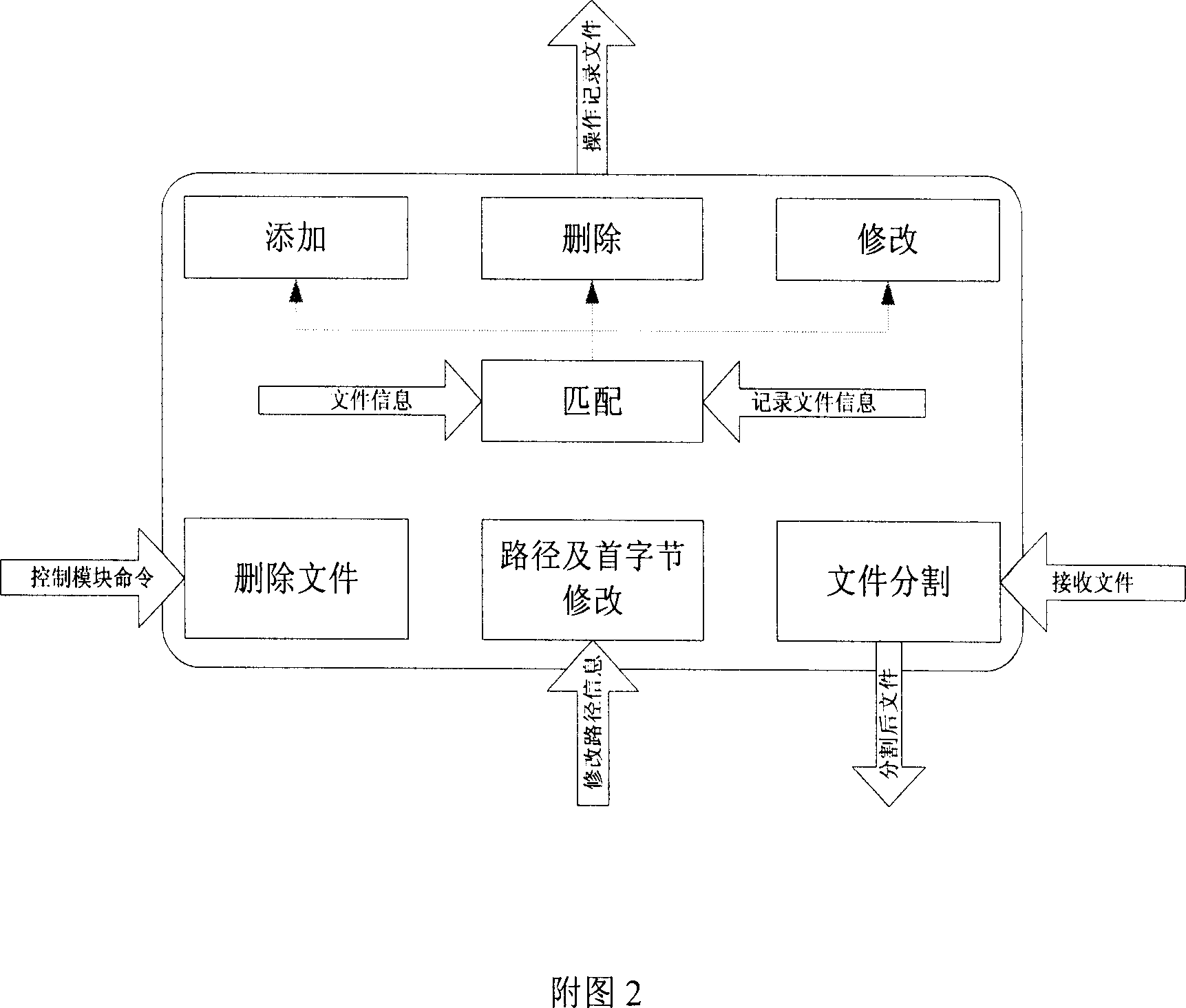
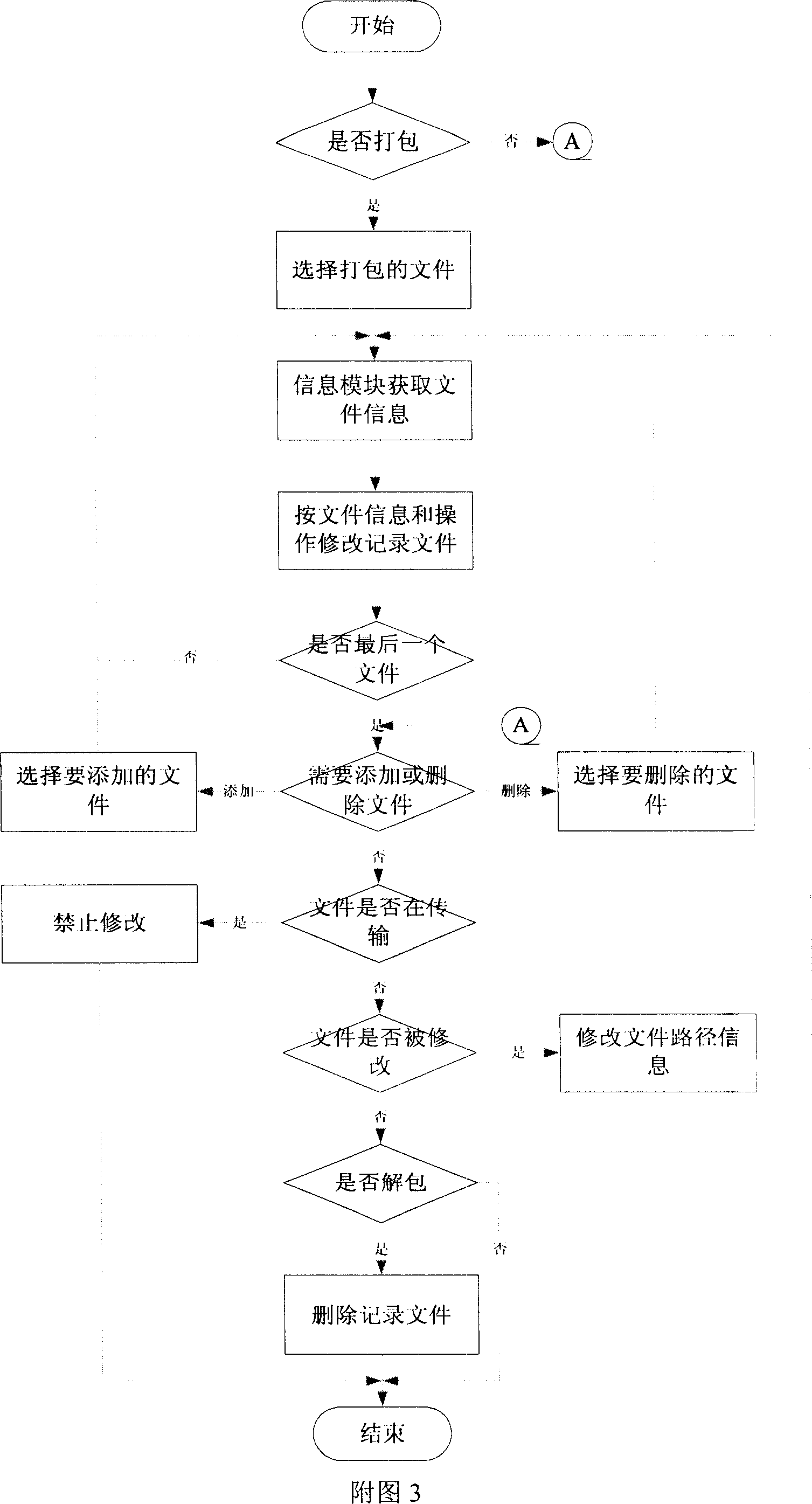
File packing and unpacking method for communication transmission
The present invention provides a method for packing and unpacking file according to the deficiency of existing file compression mode. The main content is that the first byte position and file size of each file to be packed are acquired; thereby the end byte position can be calculated and record in a file, in the record file, the end byte of the former file is pointed to the first byte position of the later file to realize the connection of two files. The files can be connected by the method and the packing for all files can be realized. For the unpacking for the packing mode, the unpacking can be realized by only deleting the record file. Next, during the transmitting process, the record file is first transmitted to the receiver, the receiver then modifies the path information and first byte position based on the storing path and storing condition, then the packed file is transmitted, so the file to be received can be divided into several files during the receiving process. The transmitting speed can reach the transmitting speed of compressing and packing, and the packing time and space is greatly reduced.
Owner:SUN YAT SEN UNIV
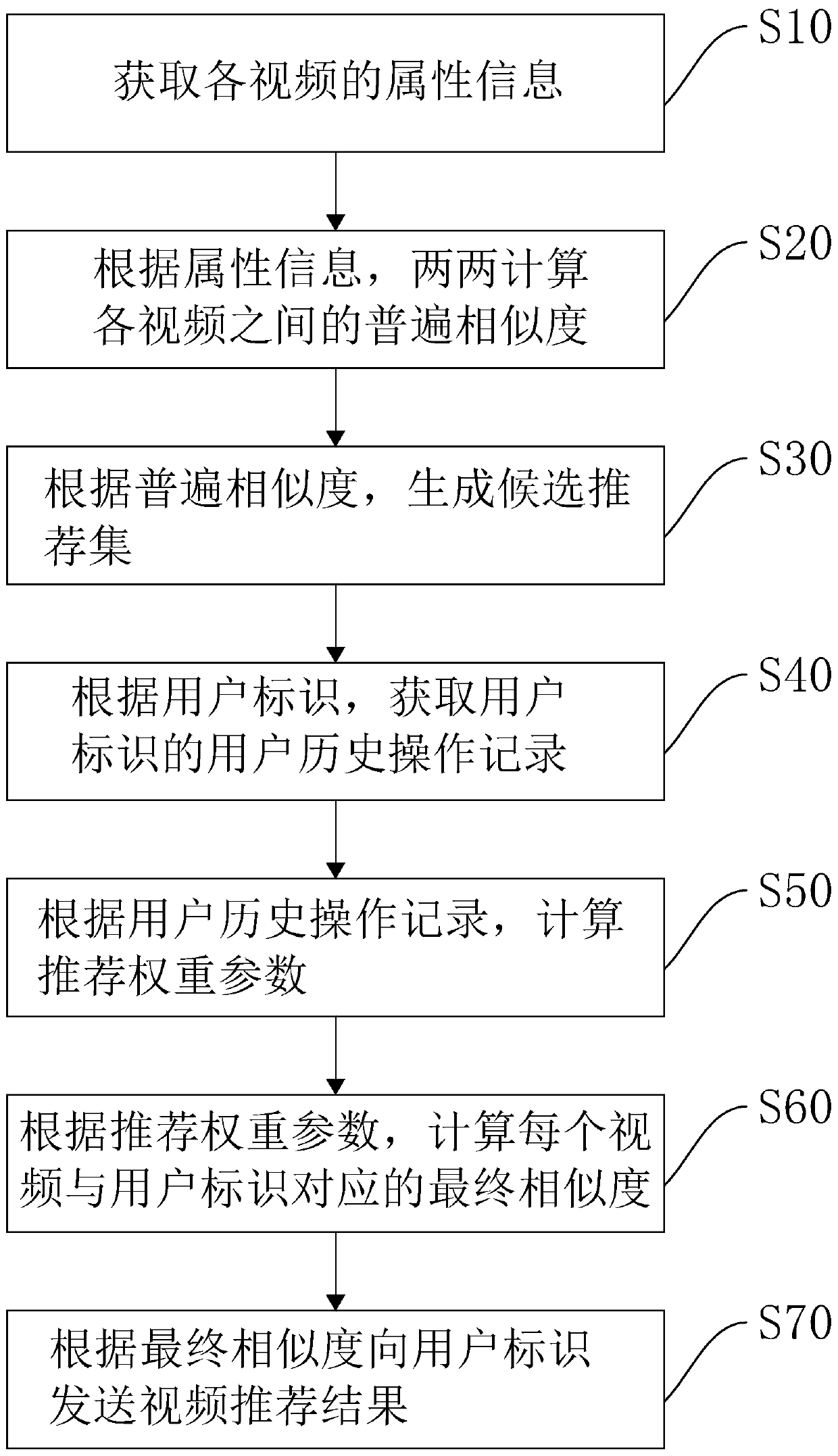
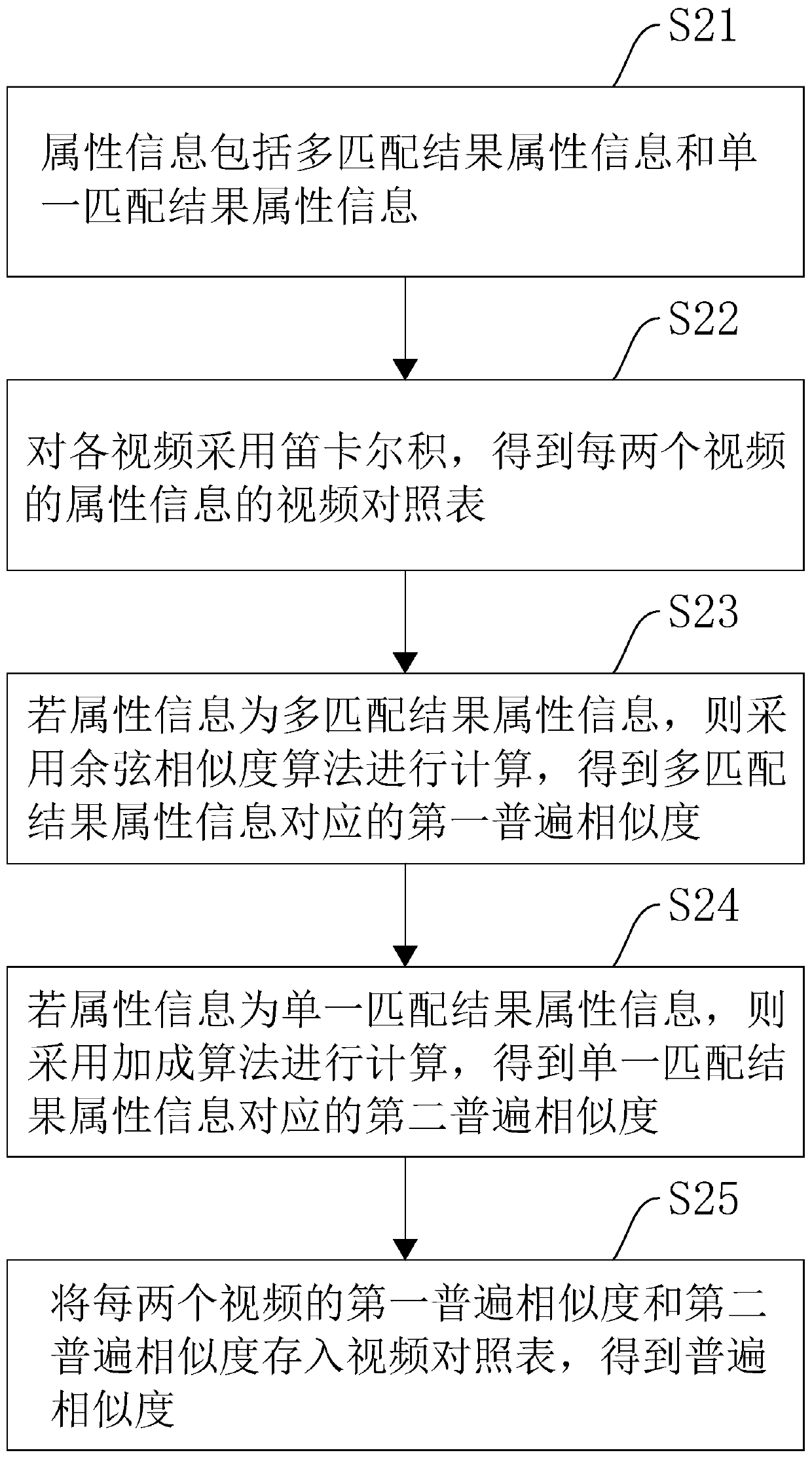
Graph structure-based recommendation method, apparatus and device, and storage medium
PendingCN109783687AEasy to add and deleteRealize individual adjustmentMetadata video data retrievalSpecial data processing applicationsUser identifierStructure based
The invention relates to a graph structure-based recommendation method, apparatus and device, and a storage medium. The graph structure-based recommendation method comprises the steps of obtaining attribute information of each video; According to the attribute information, calculating the common similarity between every two videos; Generating a candidate recommendation set according to the generalsimilarity; Obtaining a user historical operation record of the user identifier according to the user identifier; Calculating a recommendation weight parameter according to the historical operation record of the user; Calculating the final similarity between each video and the user identifier according to the recommendation weight parameter; And sending a video recommendation result to the user identifier according to the final similarity. The video recommendation method has the effects of improving the video recommendation result and enabling the video recommendation result to be closer to the interest of the user.
Owner:广州市易杰数码科技有限公司
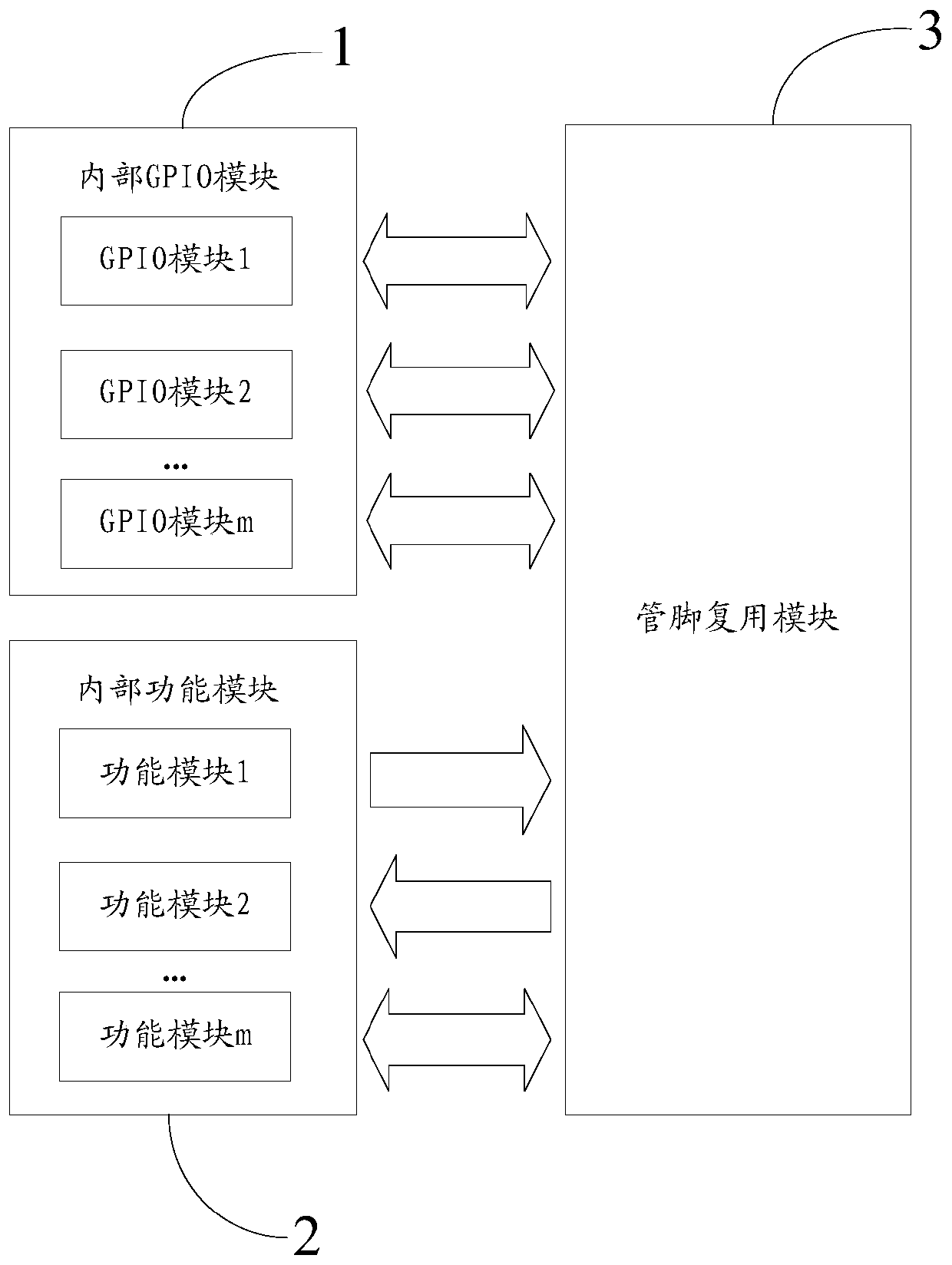
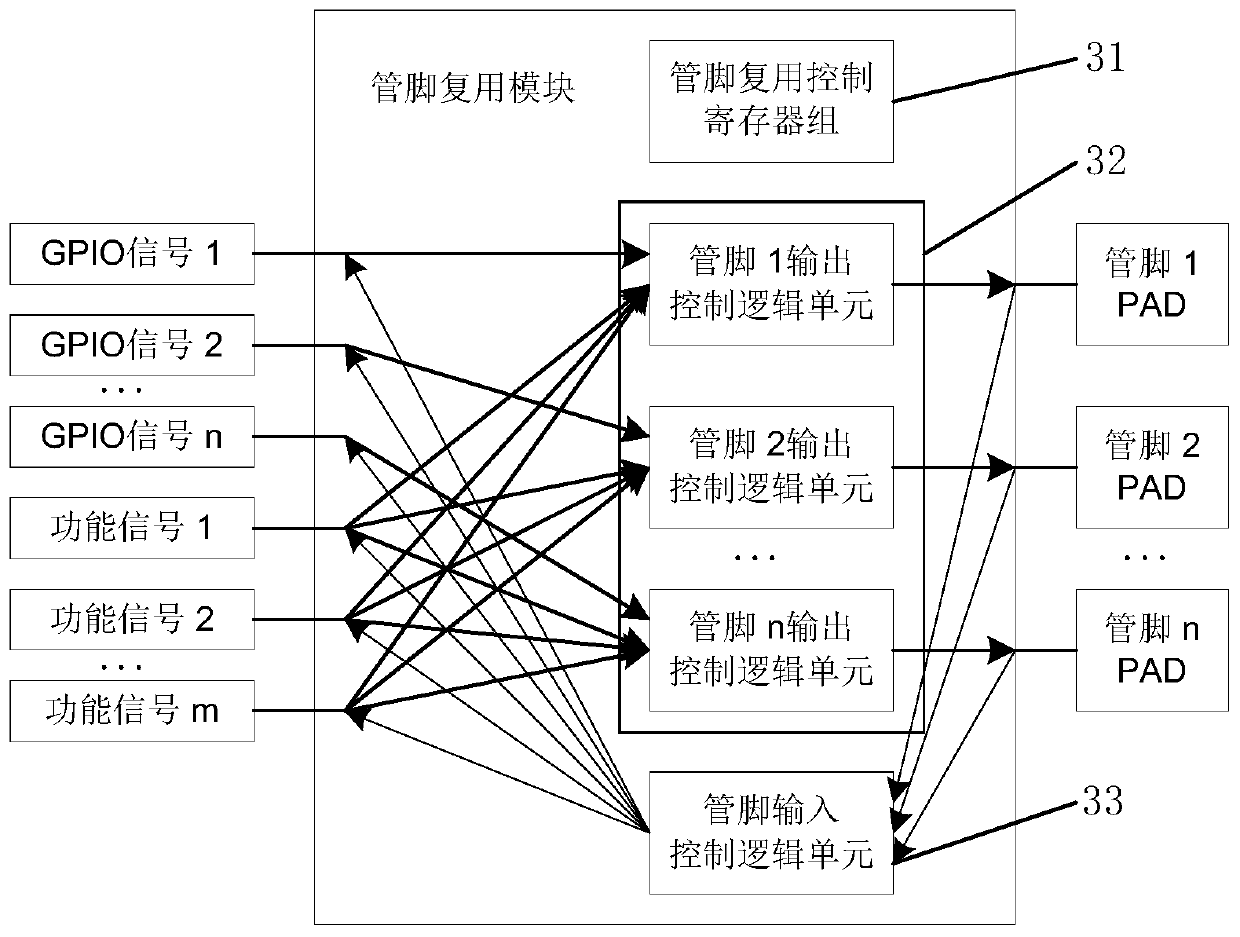
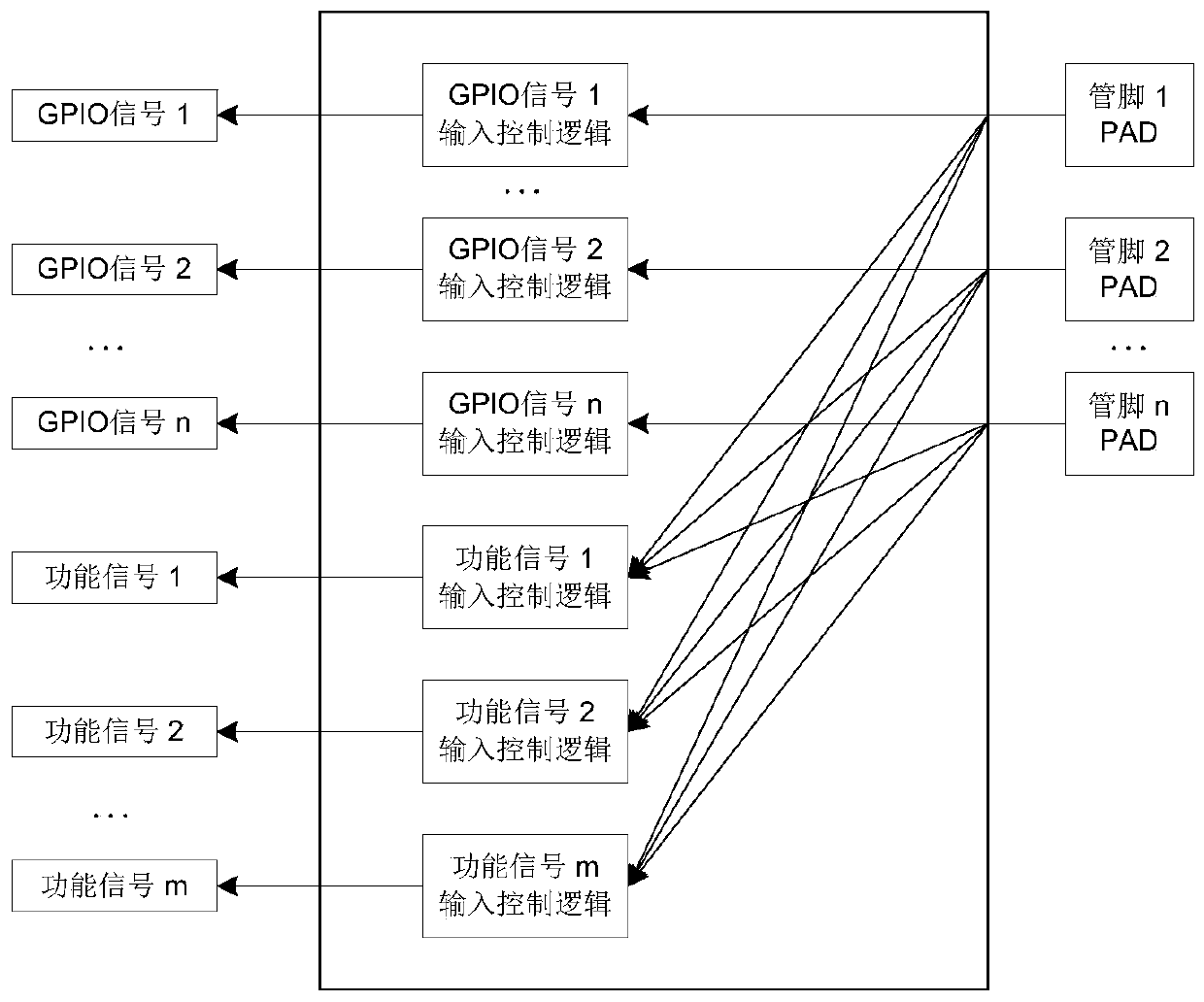
Chip and implementation method for multiplexing pins of chip
ActiveCN110647485AFlexible function expansionEasy to changeElectric digital data processingComputer hardwareMultiplexing
The invention discloses a chip and an implementation method for multiplexing pins of the chip. The chip comprises an internal function module, an internal GPIO module and a pin multiplexing module, wherein the internal function module provides a function signal led out to a chip pin, the internal GPIO module provides a GPIO signal, and the pin multiplexing module leads out the GPIO signal to the chip pin and maps the function signal provided by the internal function module to any chip pin. According to the chip, the pin multiplexing module is additionally arranged, so that function signals inthe chip can be mapped to any pin, the function expansion of the chip is more flexible, the chip function can be conveniently changed or added or deleted according to the actual requirement in the later period, and the application range of a chip product is further expanded. The pin multiplexing table is simplified, the script file is operated according to the pin multiplexing table, the pin multiplexing code file is automatically generated, and when the design is changed, the pin multiplexing code file can be generated only by updating the pin multiplexing table and then operating the scripttool again, so that the method is safer and more reliable.
Owner:大唐半导体科技有限公司
Tower information modeling method for power transmission lines
InactiveCN107247837AImprove protectionFacilitate data exchangeDesign optimisation/simulationSpecial data processing applicationsInformatizationTransformer
The invention discloses a tower information modeling method for power transmission lines. The method is characterized in that the power transmission lines are called lines, two ends of the lines are called breaking points, transformer substations are called nodes, each tower is called a sub-node, the lines among the towers are called segments, each sub-node has the attributes of the affiliated unit and geographic position, each sub-segment has the use span attribute, and a dispatching system can directly acquire the affiliated unit of a fault point and the tower corresponding to the fault point through the distance between the fault point and a transformer substation according to the use span information among the towers and timely distribute the fault point to the corresponding unit to perform processing; the construction of the power grid power transmission lines is a progressive process, and the power transmission lines and the towers need to be added, modified and deleted at any time during the construction. By the method, informatization modeling of tower information can be achieved, tower positioning speed and precision can be increased greatly, system flexibility is enhanced greatly, and power business information interaction is facilitated.
Owner:YUNNAN POWER GRID
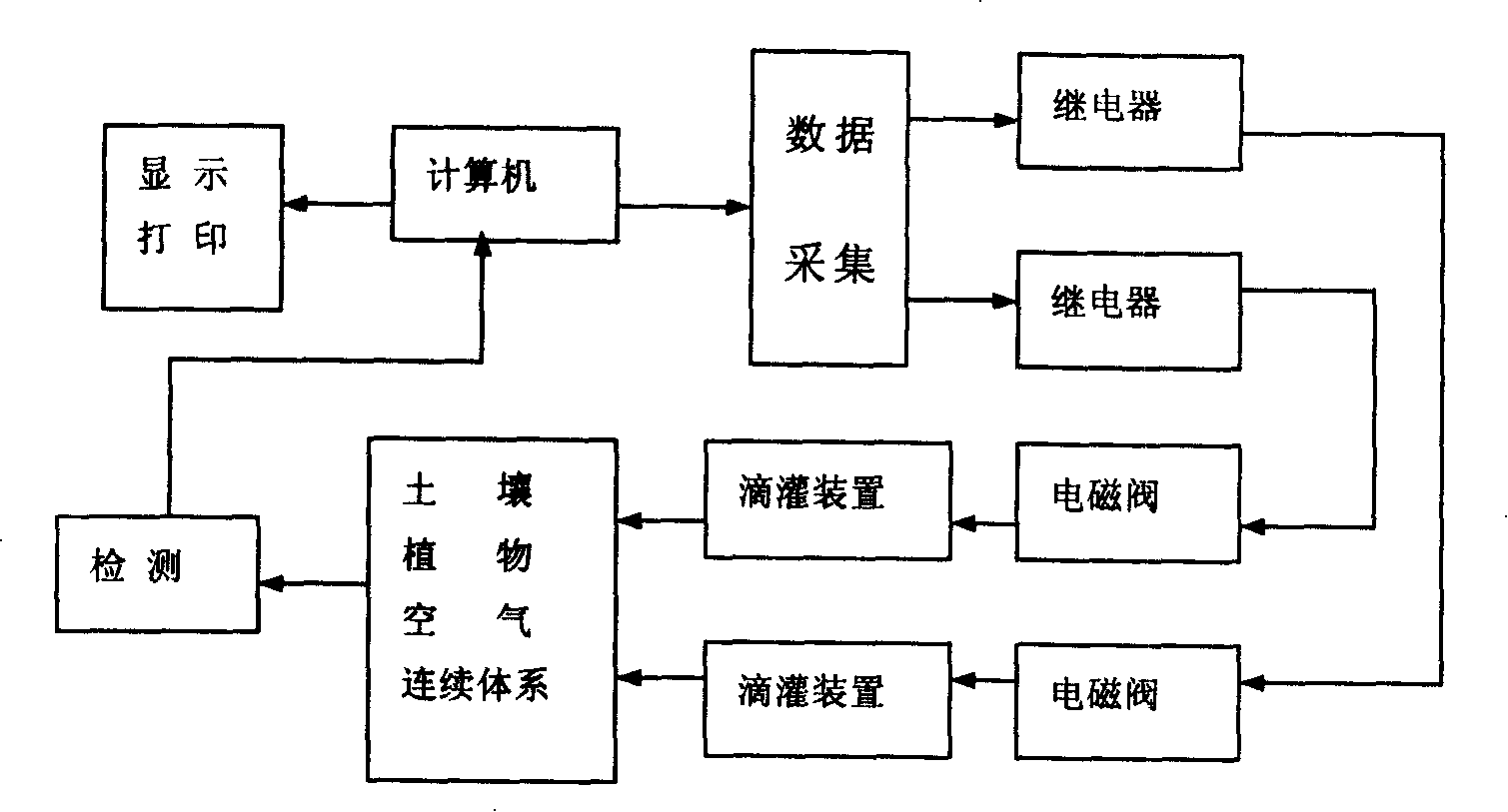
Vision irrigation system for detecting emission character based on crop water duress sound
InactiveCN101176419AWon't hurtImprove test accuracyClimate change adaptationWatering devicesAutomatic controlData acquisition
The invention relates to a condition irrigation system that detects by water stress acoustic emission characteristics of crops, which is mainly characterized in that an acoustic emission sensor is arranged on the main diameter of the crop plant on an electronic balance; the acoustic emission sensor is successively connected with a signal conditioner, a PCI data acquisition card and a computer system; the electronic balance is connected with a computer by a PCI control bus, and the condition irrigation system of crop is automatically controlled by the computer. The invention has the advantages that intelligent condition precision sprinkling irrigation and drip irrigation are implemented according to the woe signals and the transpiration changing signals emitted by the crop experiencing water stress; meanwhile according to various soil moisture needed by the crop in different growth periods, the water supply efficiency and the water supply time of the crop is determined and properly adjusted by a computer software; appropriate soil moisture for the growth of crop is guaranteed, and the objective of water saving is achieved; thus the growth of crop under best soil water condition is effectively ensured.
Owner:TIANJIN UNIV OF SCI & TECH
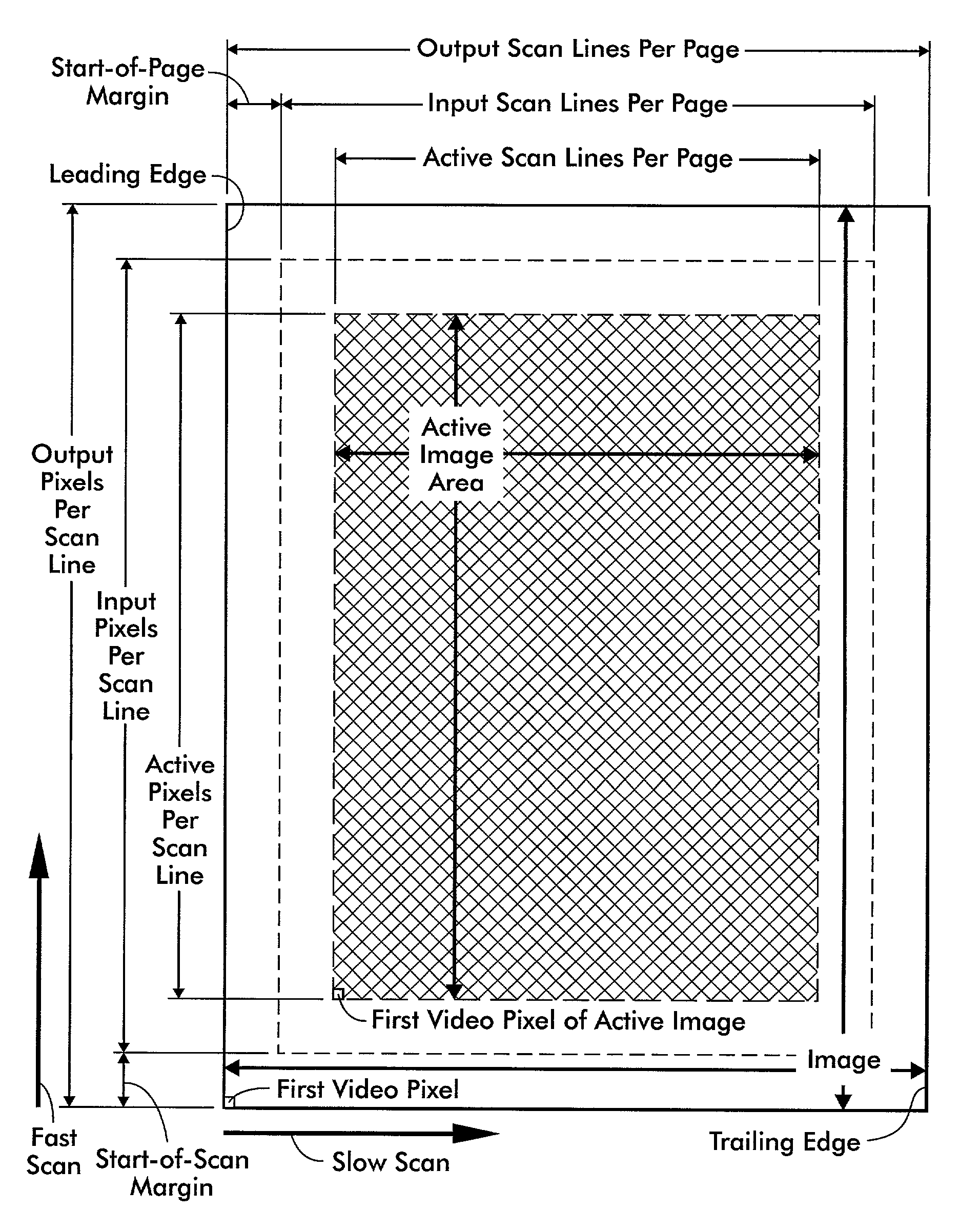
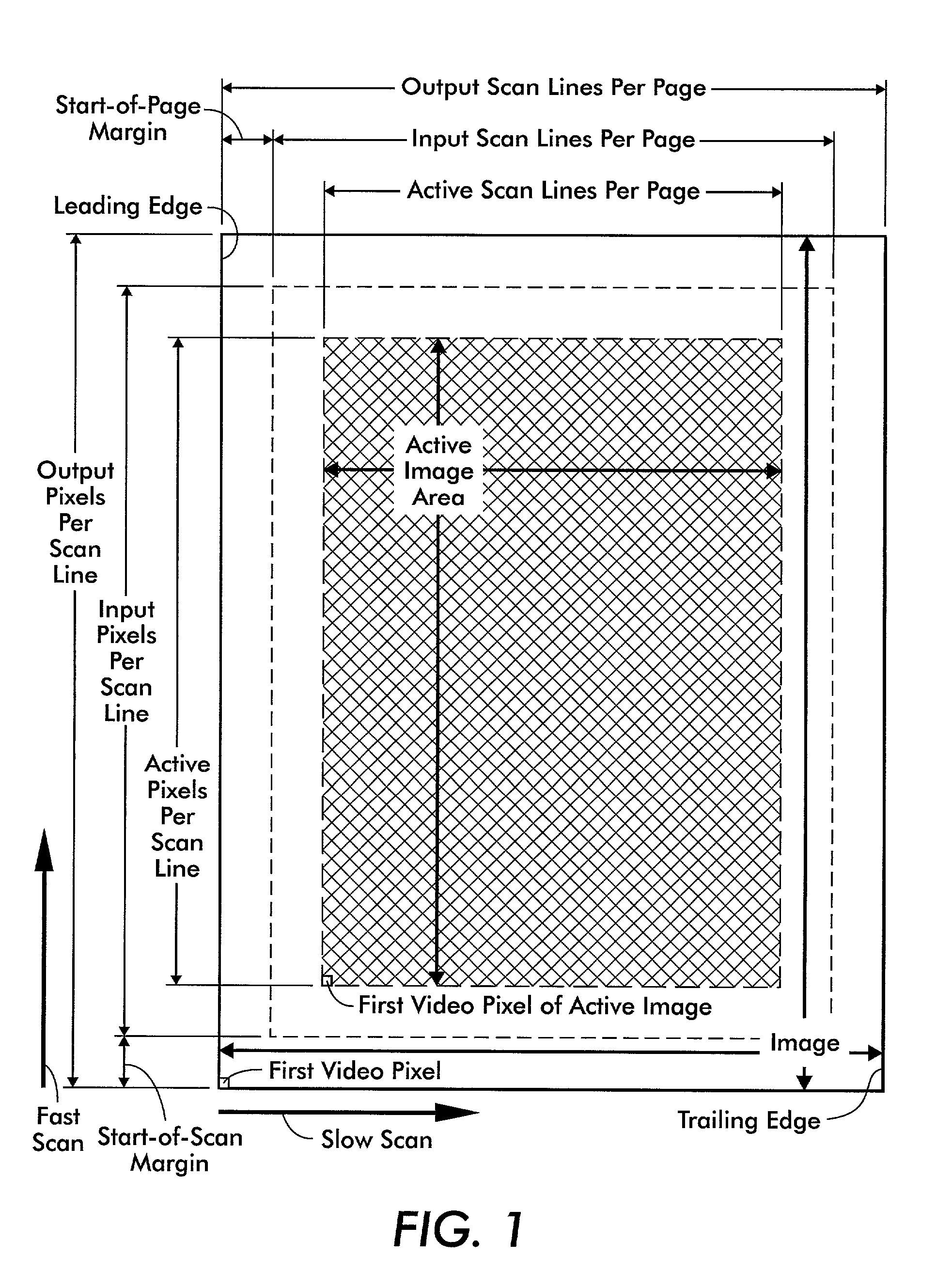
Progressive image shift for a saddle-stitched document
InactiveUS6977741B2Easy to addEasy to deleteDigitally marking record carriersGeometric image transformationComputer graphics (images)Documentation
Owner:XEROX CORP
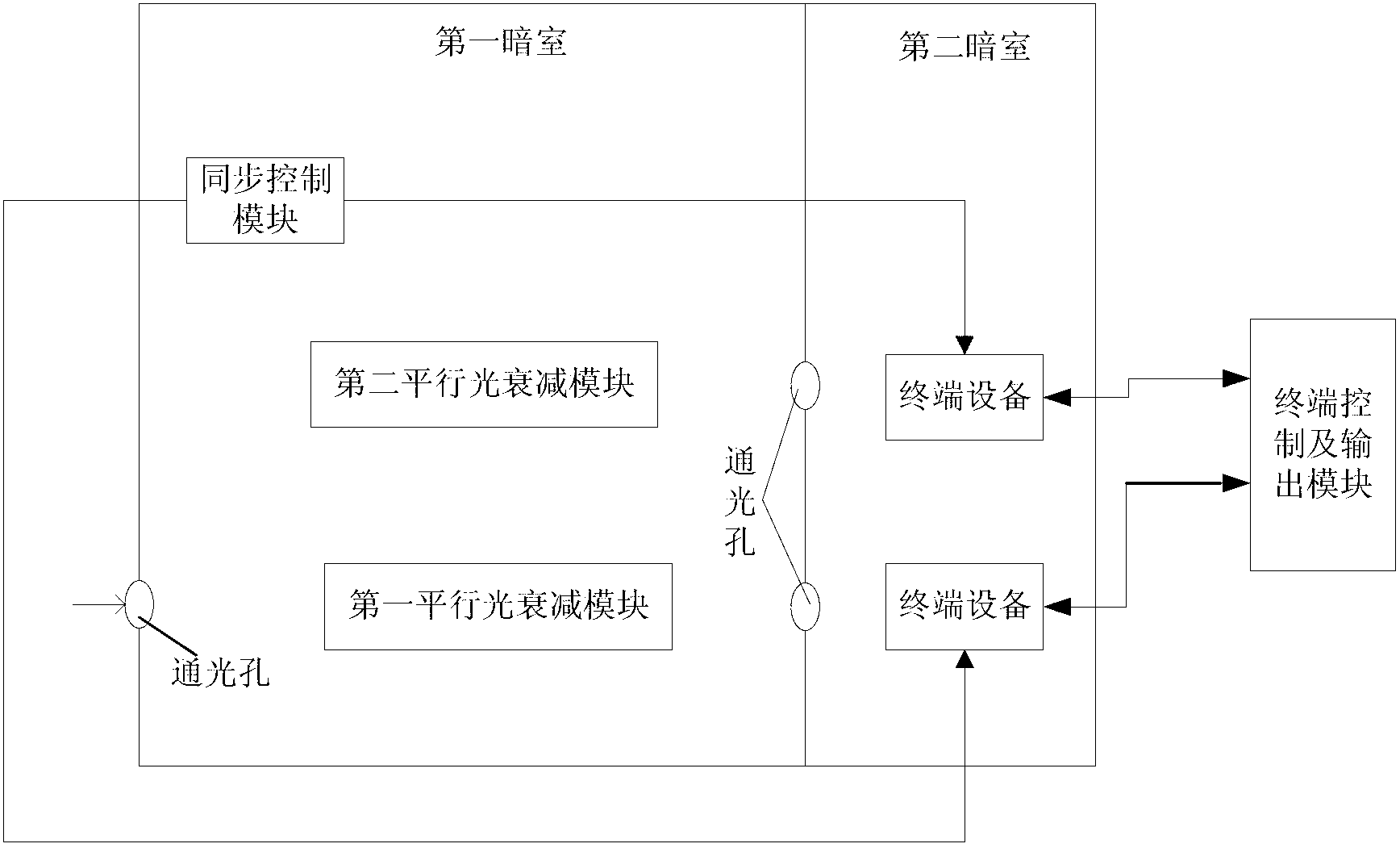
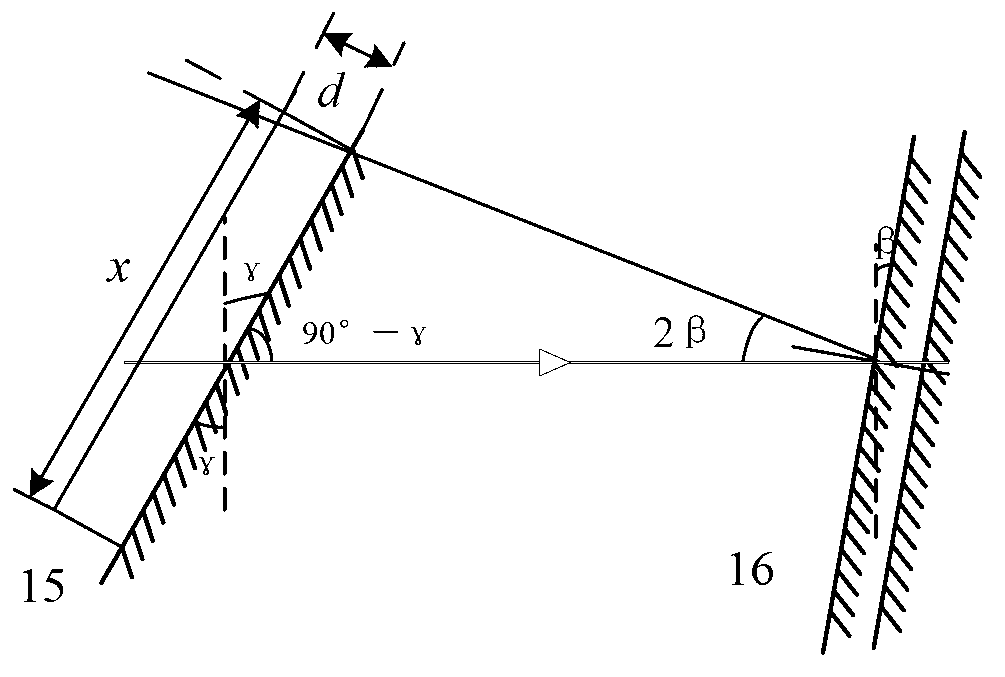
High-energy pulse laser multi-path measuring device and method
ActiveCN103308188AHigh measurement accuracyFlexible controlInstrumentsUltrasound attenuationSignal on
The invention relates to a high-energy pulse laser multi-path measuring device and method. According to the high-energy pulse laser multi-path measuring device and method, a first darkroom and a second darkroom are built. The first darkroom is used for performing attenuation and light split processing on incident beam, and the processed beam enters the second darkroom through a light through hole of the first darkroom. The second darkroom provided with a beam collecting device is used for collecting the beam from the first darkroom. An output module is used for outputting beam collecting results from the second darkroom. A first parallel light attenuation module, a second parallel light attenuation module and a synchronous control device are arranged in the first darkroom. The synchronous control device generates synchronous control signals on the basis of reflected light generated by the fact that the first parallel light attenuation module performs attenuation on the incident beam and controls the beam collecting device located in the second darkroom to perform beam collection on corresponding parallel beam meanwhile. The high-energy pulse laser multi-path measuring device is suitable for measurement of high-energy pulse laser, and meanwhile can be used for measuring low-energy and continuous laser.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
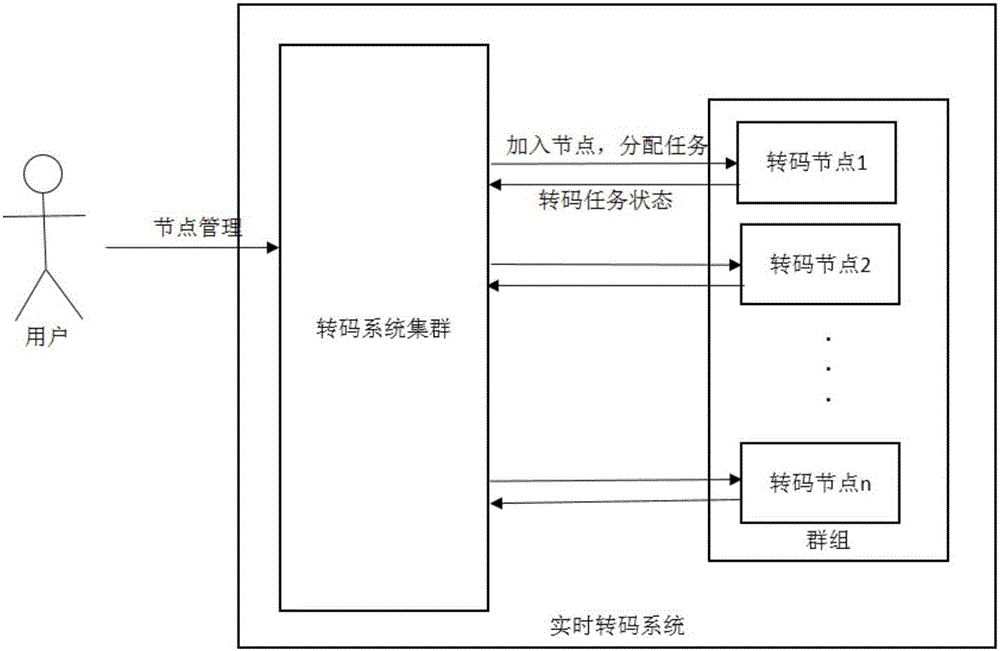
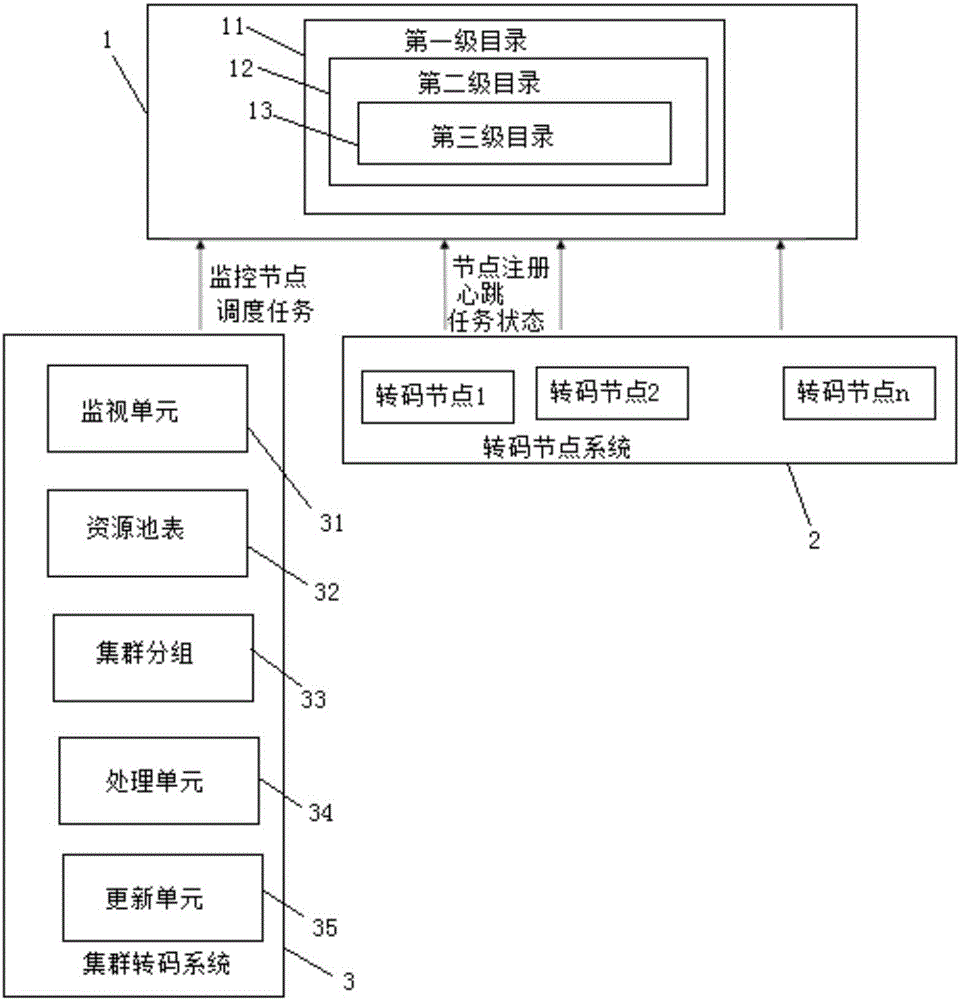
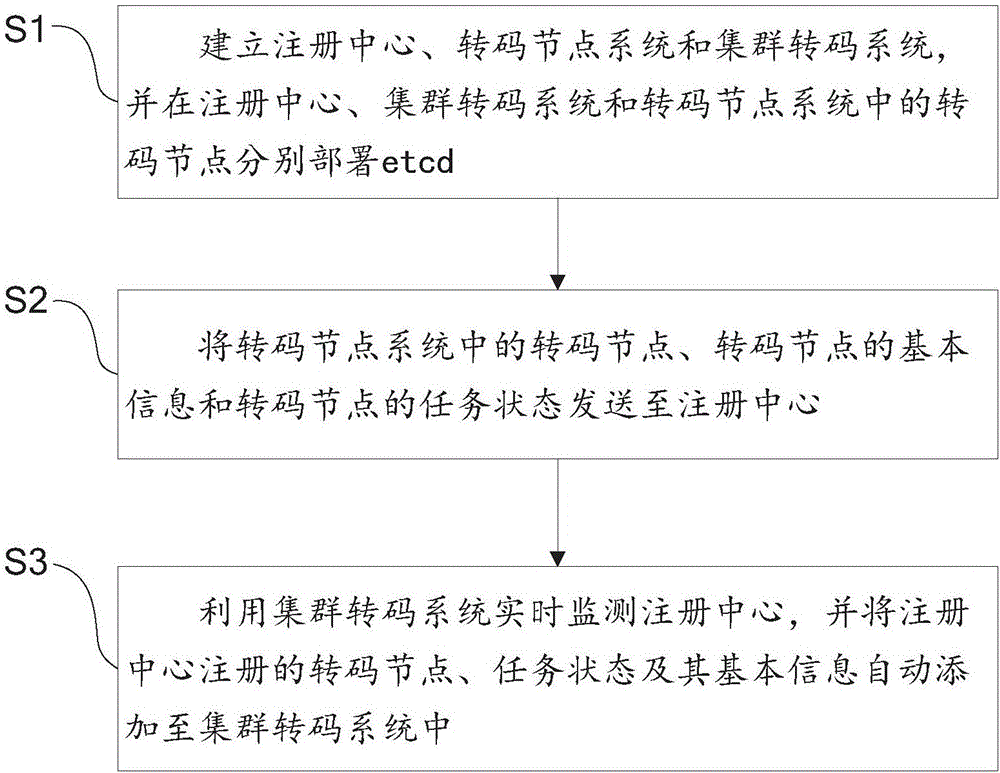
Transcoding node management system and method for distributed real-time transcoding system
ActiveCN106850747AGuaranteed maintenanceEasy to add and deleteChannel coding adaptationData switching networksIp addressManagement system
The invention relates to a transcoding node management system for a distributed real-time transcoding system. The transcoding node management system comprises a registration centre, a transcoding node system and a cluster transcoding system; transcoding nodes in the registration centre, the cluster transcoding system and the transcoding node system are separately deployed with etcd; the transcoding node system is used for sending the transcoding nodes, the basic information of the transcoding nodes and the task states of the transcoding nodes to the registration centre; and the cluster transcoding system is used for monitoring the registration centre in real time, and automatically adding the transcoding nodes, the task states and the basic information registered in the registration centre. By means of the transcoding node management system disclosed by the invention, the real-time states of the transcoding nodes can be obtained more rapidly and accurately; real-time monitoring and maintaining of the transcoding nodes can be ensured; all requests are sent to the local of the registration centre; risks, such as the state mismatching risk due to frequent sending of HTTP requests between servers, can be greatly reduced; simultaneously, related operations, such as adding and deleting of the transcoding nodes, are convenient; and thus, the transcoding nodes still can be effectively managed when the IP addresses of the transcoding nodes are unknown.
Owner:上海网达软件股份有限公司
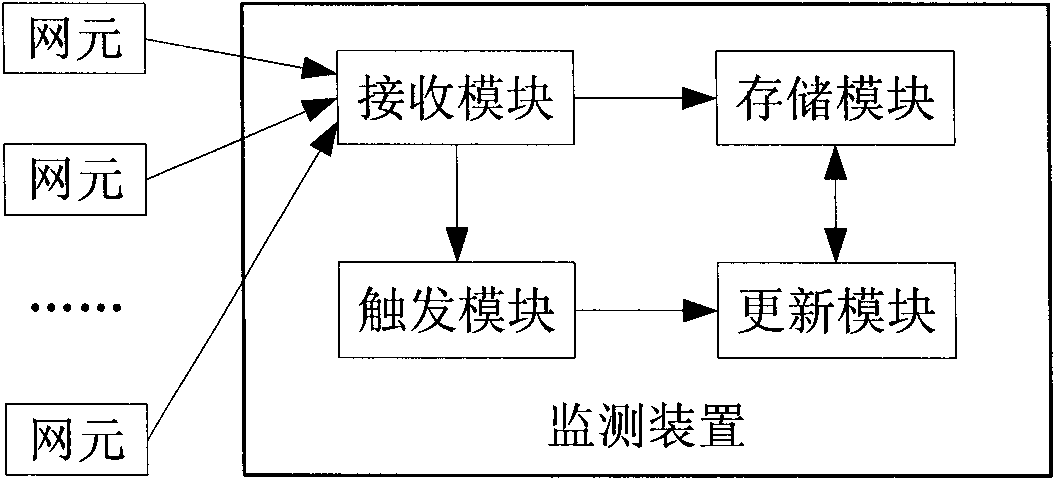
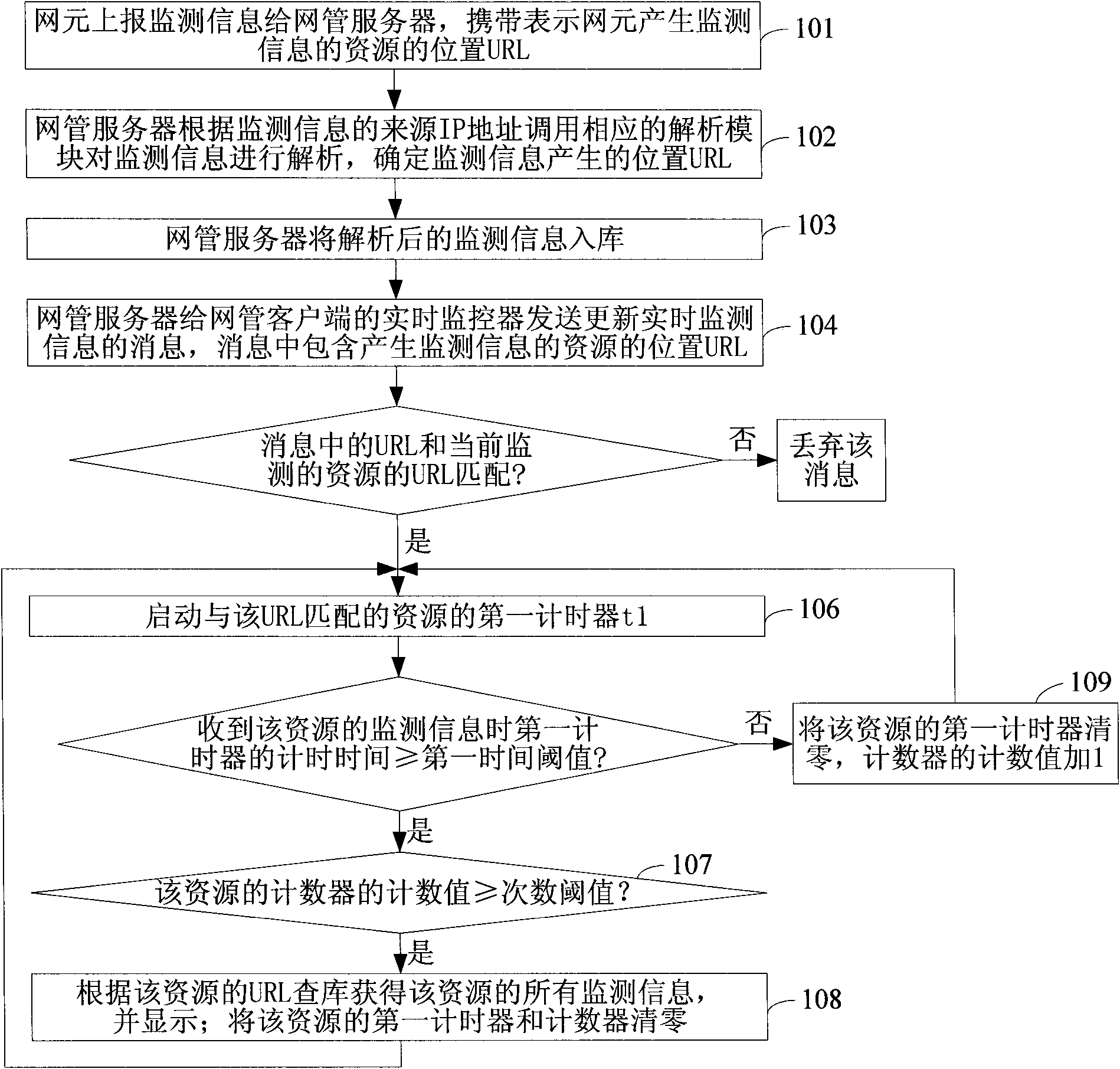
Network monitoring system and network monitoring method
InactiveCN101808023AEasy to viewEasy to manageData switching networksMonitoring methodsNetwork monitoring
The invention relates to a network monitoring system and a network monitoring method. The network monitoring system comprises a plurality of network elements which are respectively used for transmitting monitoring information of one or a plurality of resource(s) therein and a monitoring device which is used for receiving and storing the monitoring information. When the frequency of receiving the monitoring information on a resource currently monitored is higher than or equal to a frequency threshold and the interval between the current reception of the monitoring information on the resource and the previous reception of the monitoring information on the resource is large than or equal to a first time threshold, the latest monitoring information on the resource is inquired in the stored monitoring information. The invention can reduce the occupation of system resources while promptly monitoring the situation of the network elements to the largest extent.
Owner:RAISECOM TECH
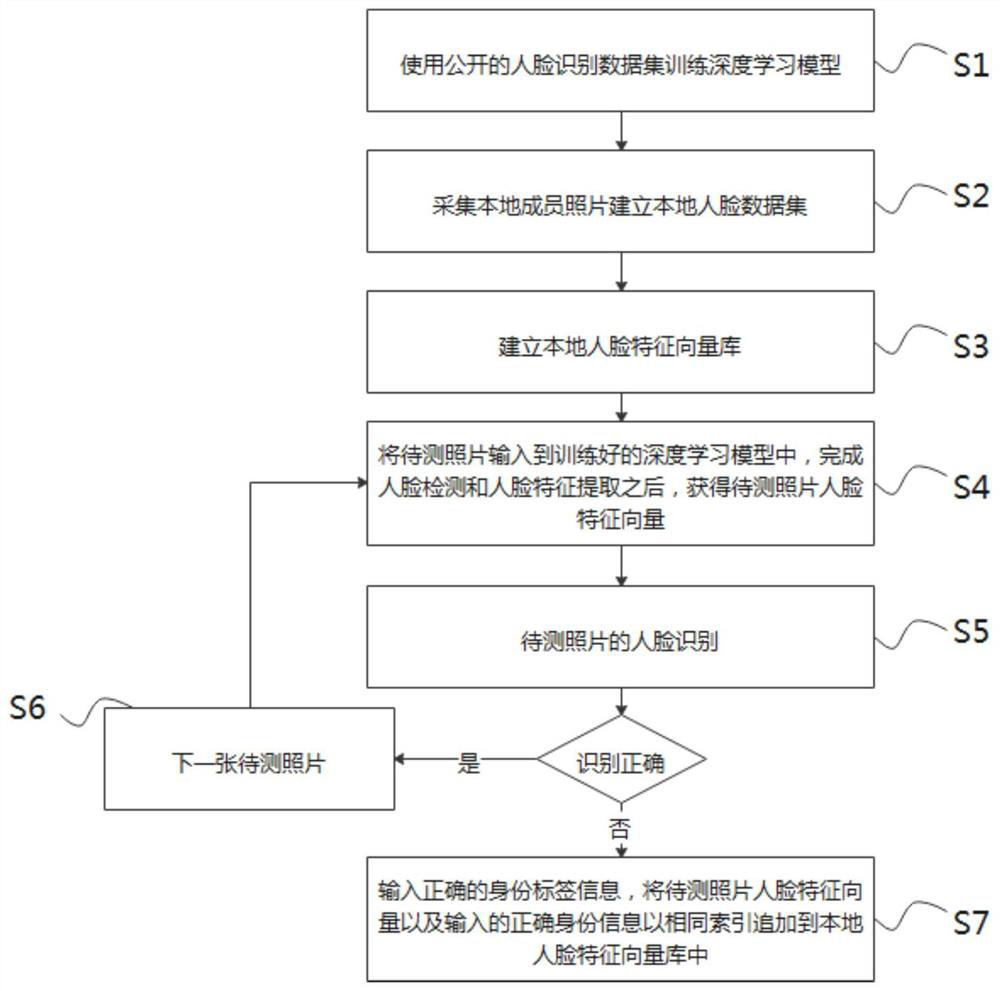
Simple face recognition online learning method based on deep learning model
PendingCN112418067ARealize face feature extractionImprove robustnessCharacter and pattern recognitionNeural learning methodsFeature vectorFeature extraction
The invention is applicable to the technical field of computer vision, and provides a simple face recognition online learning method based on a deep learning model. Face feature vectors and identity label information are stored by using files capable of adding data types, such as hdf5 and the like; the human face feature vectors and the corresponding identity tags are added to the local human facefeature vector library with the same index, so that members are added and deleted more simply and conveniently, the trouble of re-collecting samples and training again in a traditional method is solved, and the method is simple to operate, easy to master, remarkable in effect. The updating of the local face feature vector library does not need to carry out face feature extraction on all local members again, only face feature extraction is carried out on newly added personnel, and the face feature vectors and the identity label information of the newly added members are added to the local facefeature vector library. And the updating of the local face feature vector library is greatly facilitated.
Owner:湖北芯楚光电科技有限公司
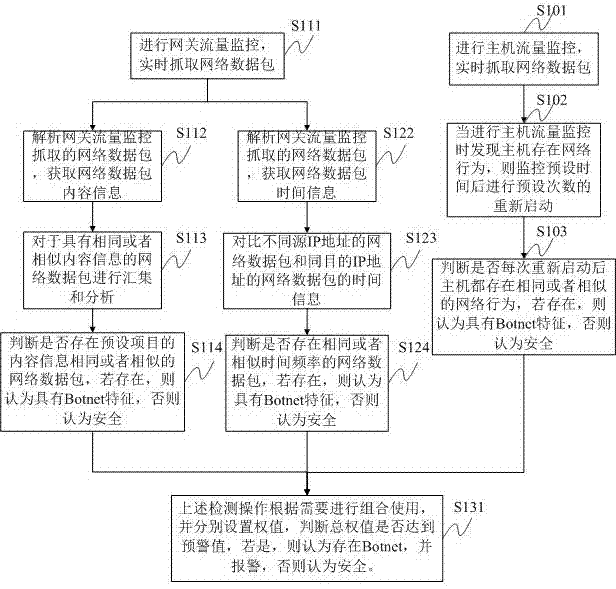
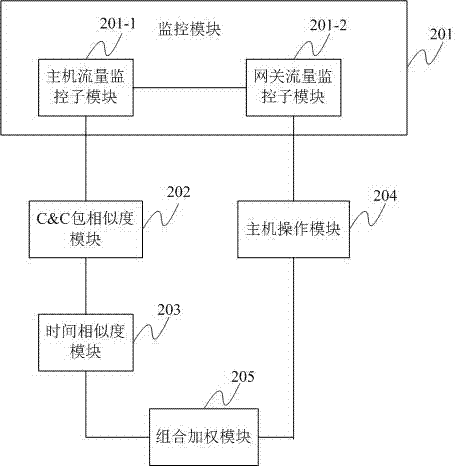
A botnet detection method and system based on gateway and local
ActiveCN103916288BEasy to add and deleteImprove scalabilityData switching networksHysteresisTime information
The invention discloses a Botnet detection method and system based on a gateway and a local. Firstly, the host flow monitoring and the gateway flow monitoring are carried out respectively, and the network data packets are captured in real time; the content information and time information of the network data packets are acquired through analysis; the network data packets are judged The content similarity, time similarity or host network behavior between data packets, the above three detection operations are used in combination according to needs, and the weights are set separately to judge whether the total weight reaches the warning value. If so, it is considered that there is a Botnet. And call the police, otherwise it is considered safe. The technical solution provided by the present invention solves the problem of detection lag in signature code scanning and network traffic technology, and does not require cluster construction like honeypot technology, saving resources and time.
Owner:SHENZHEN ANZHITIAN INFORMATION TECH
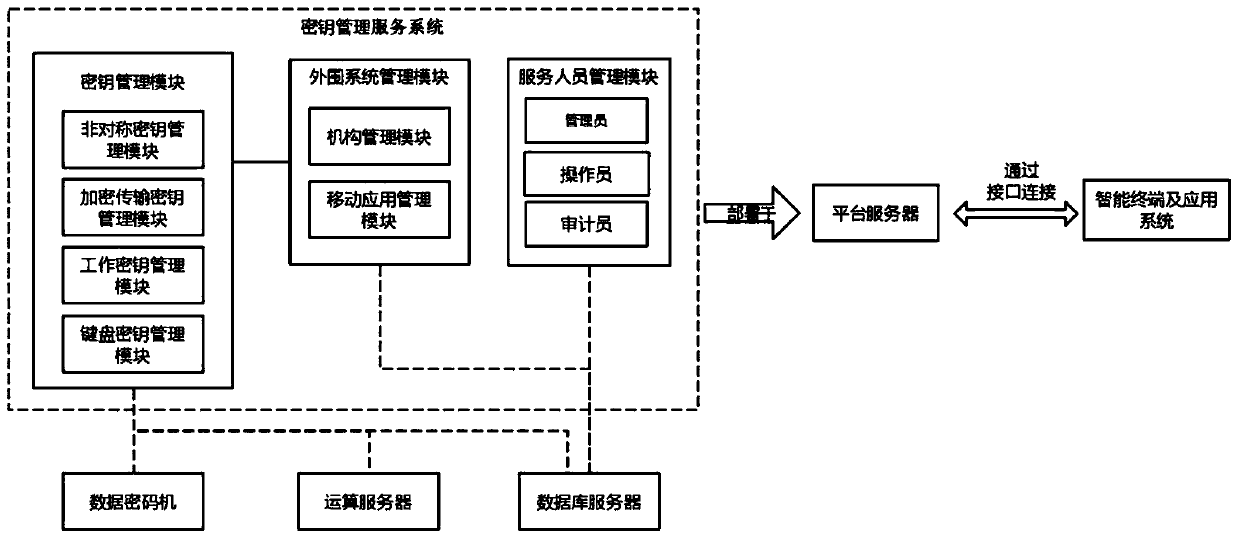
Key management system
InactiveCN109756333ATroubleshoot encryption issuesPrevent leakageKey distribution for secure communicationDatabase serverEngineering
The invention discloses a key management system. The method is characterized in that the method is characterized by comprising, The system comprises a data cipher machine providing the highest secretkey, an operation server providing decryption encryption operation basis, a database server used for storing the secret key and related data of the secret key, a platform server providing system service, and a secret key management service system arranged on the platform server and used for providing secret key service for an intelligent terminal and an application system. Wherein the data ciphermachine, the operation server and the database server are respectively connected with the key management service system, and the platform server is provided with an interface used for connecting the key management service system with the intelligent terminal and the application system; According to the invention, a systematic perfect key management service is provided for the intelligent terminaland the application system, comprehensive encryption protection is provided for the information, and the information security is ensured not to be leaked.
Owner:西安得安信息技术有限公司
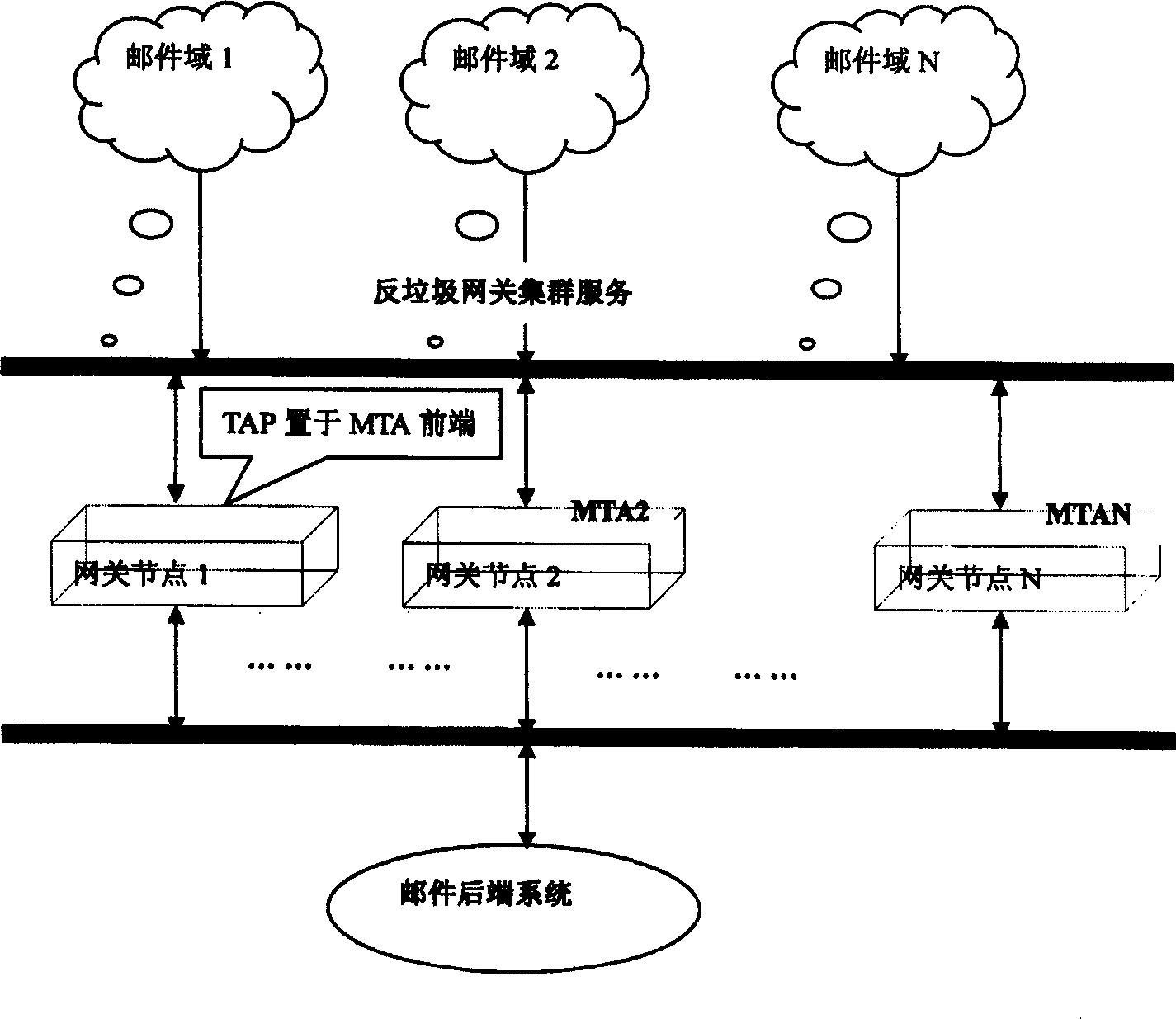
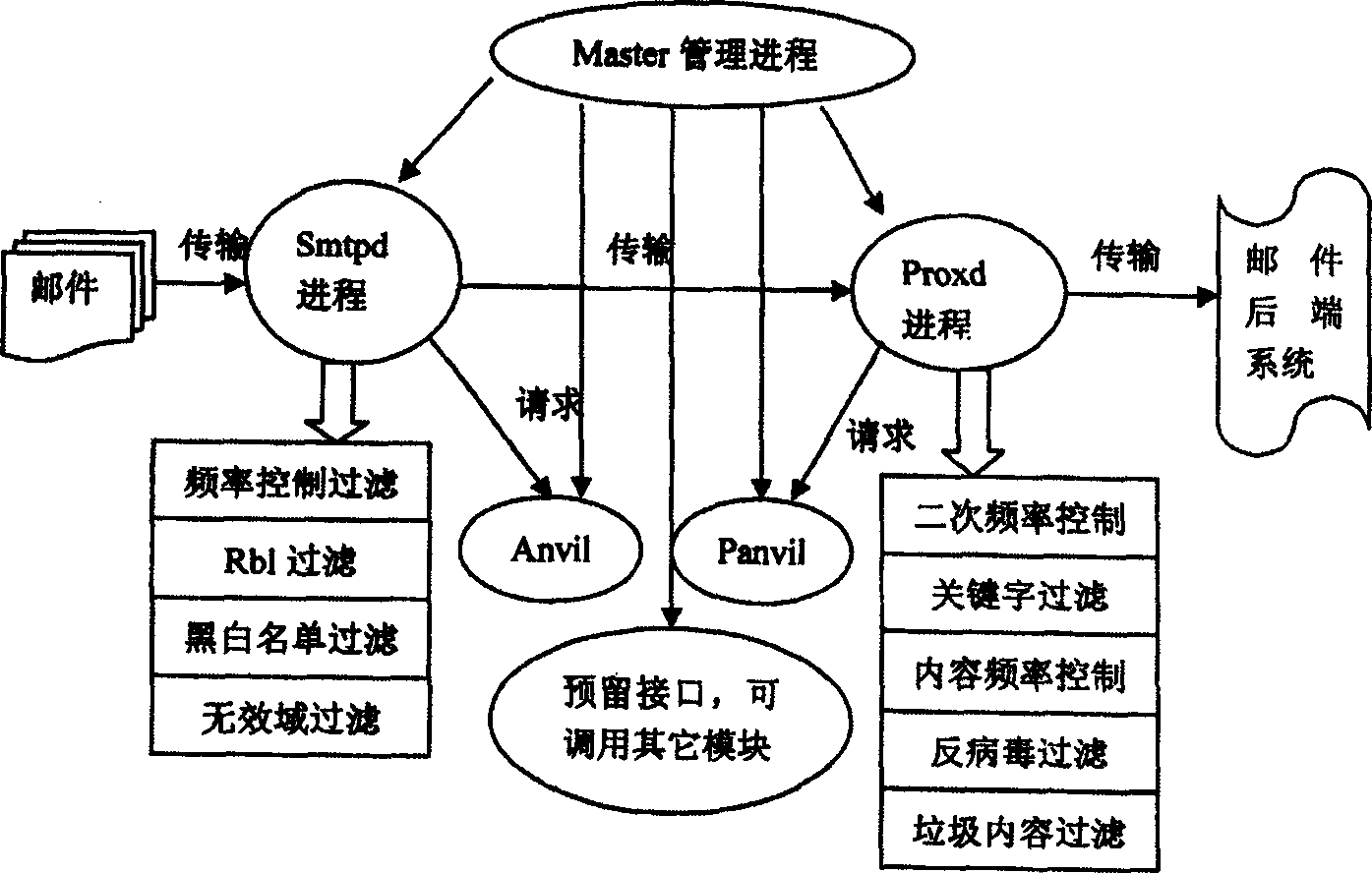
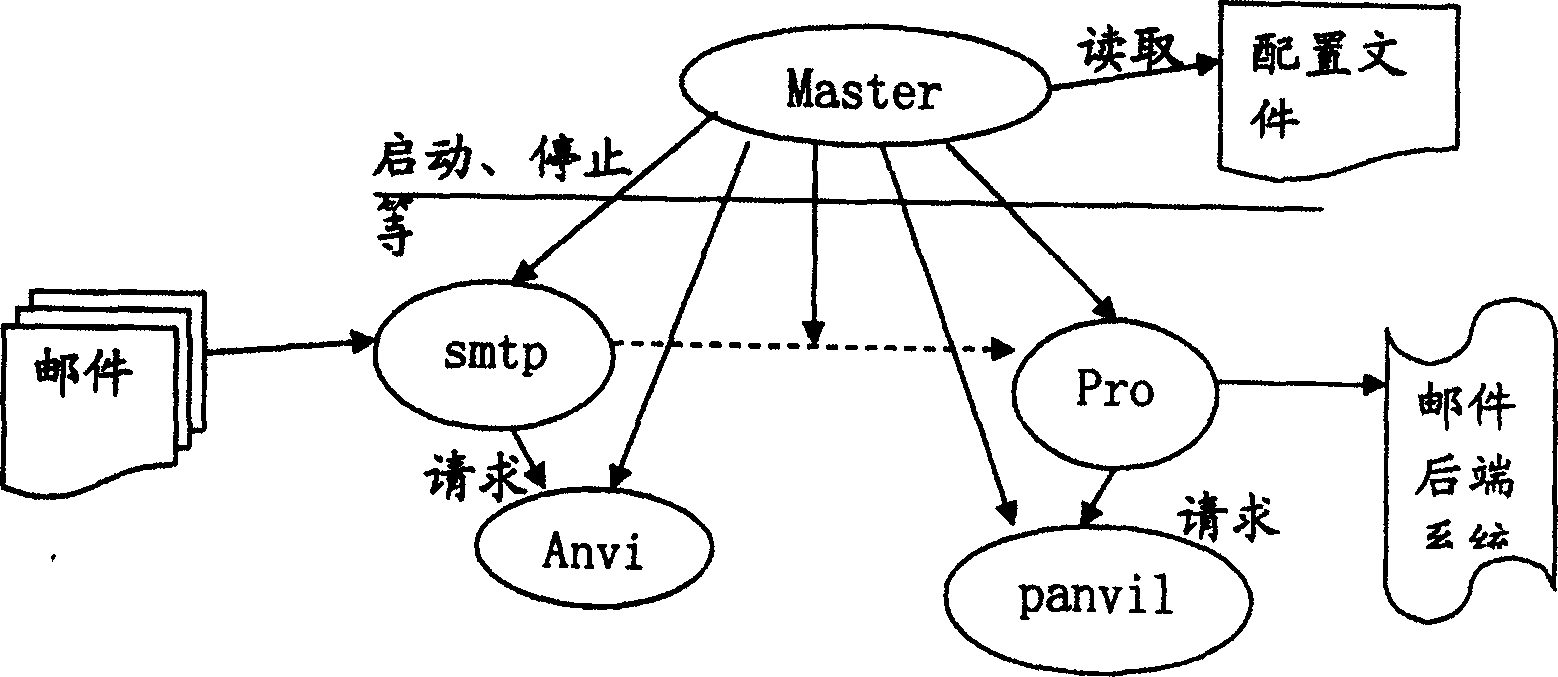
Method for setting multi-layer gateway frame against rubbish
ActiveCN1747458AImprove scalabilityImprove the efficiency of multi-layer filtrationNetwork connectionsInstrumentsComputer moduleMulti tier
A method for setting up multi-layer and anti-garbage gateway frame features that a multi-layer garbage filter module is arranged on the gateway node in the front of MTA of mail server and the gateway frame is running in the mode of Master manage progress to monitor the running of relative modules in memory and starting or stopping various garbage filter modules according their configuring parameters, so in creasing the filtering efficiency.
Owner:BEIJING 263 ENTERPRISE COMM
System and method for searching and killing malicious codes based on expandable mode
ActiveCN102810142ASolve problemsSolve the hysteresisComputer security arrangementsSpecific program execution arrangementsScheduling functionComputer module
The invention discloses a system for searching and killing malicious codes based on an expandable mode. The system comprises a function component, a script component and an engine object, wherein the function component comprises a function module for implementing a malicious code processing strategy and supplies a lead-out interface for the function module; the script component comprises a processing script for implementing the malicious code processing strategy and supplies a calling interface for the processing script; the processing script calls the processing strategy corresponding to the function module through the lead-out interface of the function component; and the engine object manages and schedules the function component and the script component, executes the processing script in the script component, implements the malicious code processing strategy and finish searching and killing of the malicious codes. The invention also discloses a method for searching and killing the malicious codes based on the expandable mode. By the method and the system, according to the popular malicious codes of new varieties or new families, a searching and killing scheme can be formed at the first time and is easy to add, delete, expand and maintain; extra development and manual expense are avoided; and processing, searching and killing for the malicious codes are greatly facilitated.
Owner:BEIJING ANTIY NETWORK SAFETY TECH CO LTD
A method and system for filtering BFD protocol packets
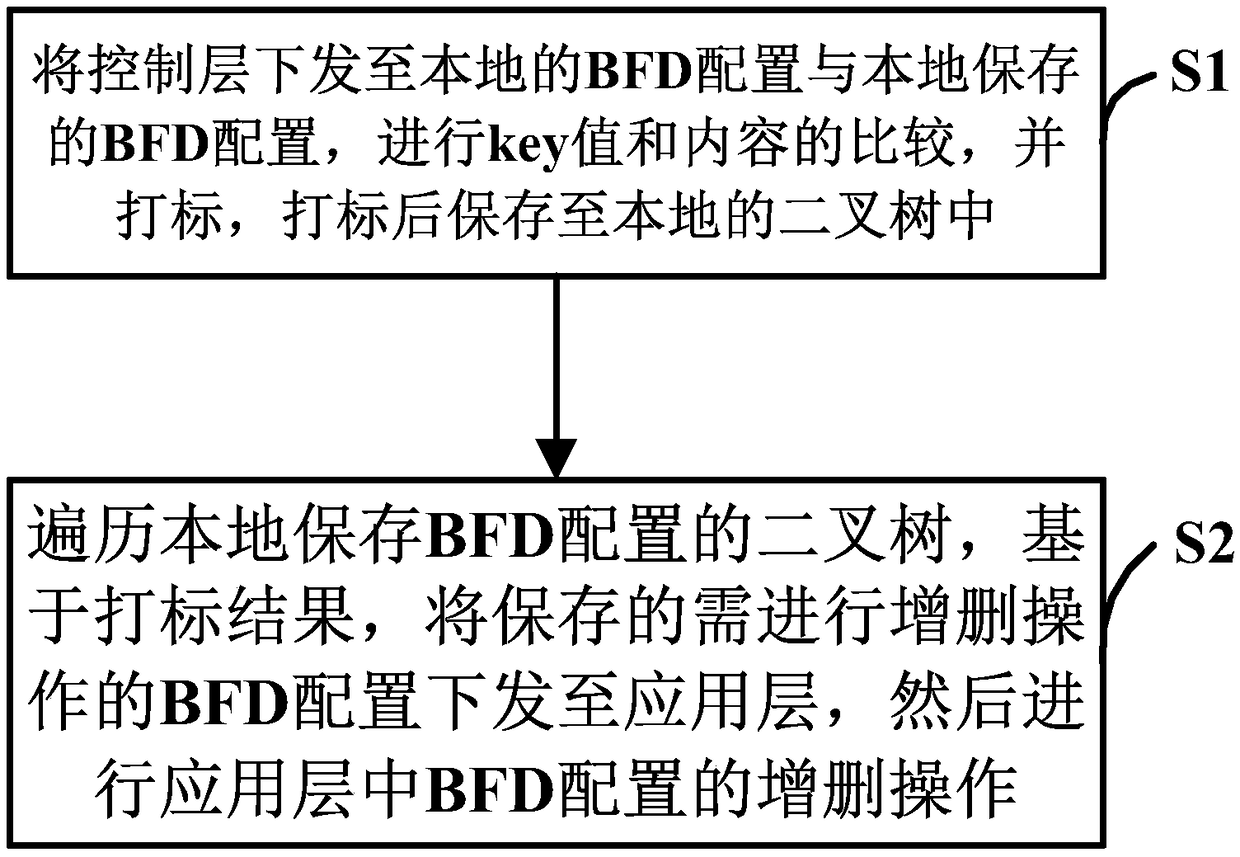
ActiveCN109039822AEasy to add and deleteAvoid repeated reading and writingData switching networksComputer hardwareControl layer
A method and system for filtering BFD protocol packets are disclosed, relating to the technical field of communication. The method comprises the following steps of: comparing the key value and contentof the BFD configuration sent to the local control layer with the BFD configuration saved locally; marking the BFD configuration sent to the control layer with the mark; saving the marking BFD configuration in the local binary tree; When the timer interrupts the response, traversing the binary tree which locally stores the BFD configuration, and based on the marking result of the BFD configuration, sending the BFD configuration stored in the binary tree and needing addition or deletion operation to the application layer, and then performing addition or deletion operation of the BFD configuration in the application layer according to the marking result of the BFD configuration. The invention realizes the filtering of the BFD message on the forwarding layer, avoids the repeated reading andwriting of the FPGA by the BFD addition or deletion operation of the same descriptor, and avoids the configuration redundancy on the FPGA.
Owner:FENGHUO COMM SCI & TECH CO LTD
Sign-up & Login Interface Using a Messaging System
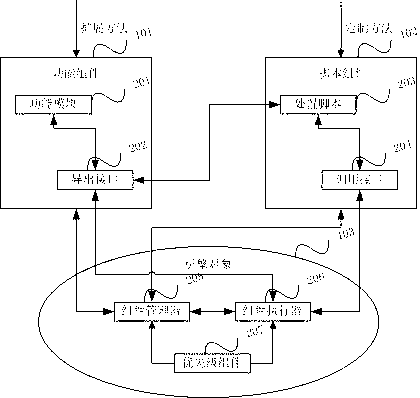
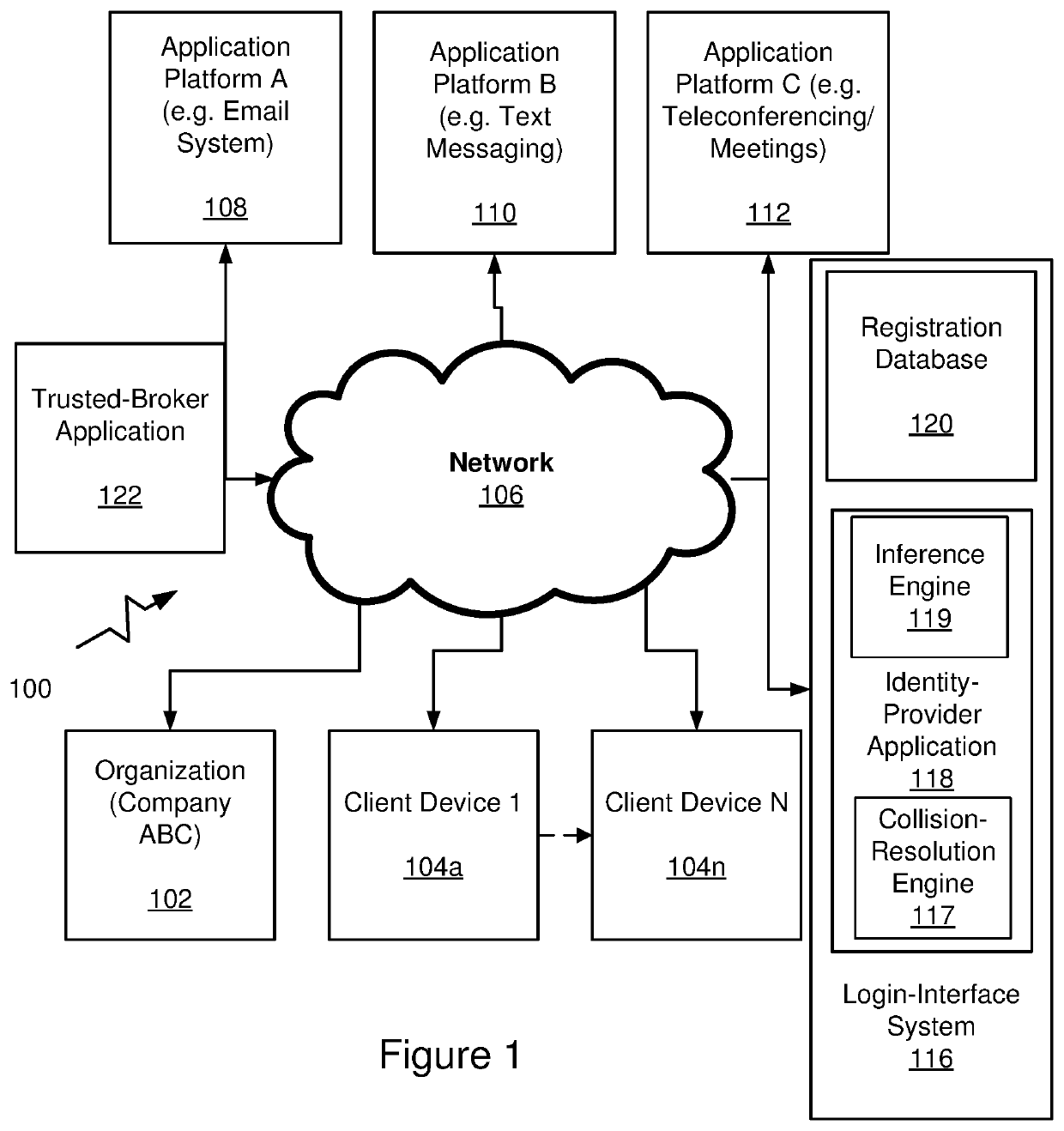
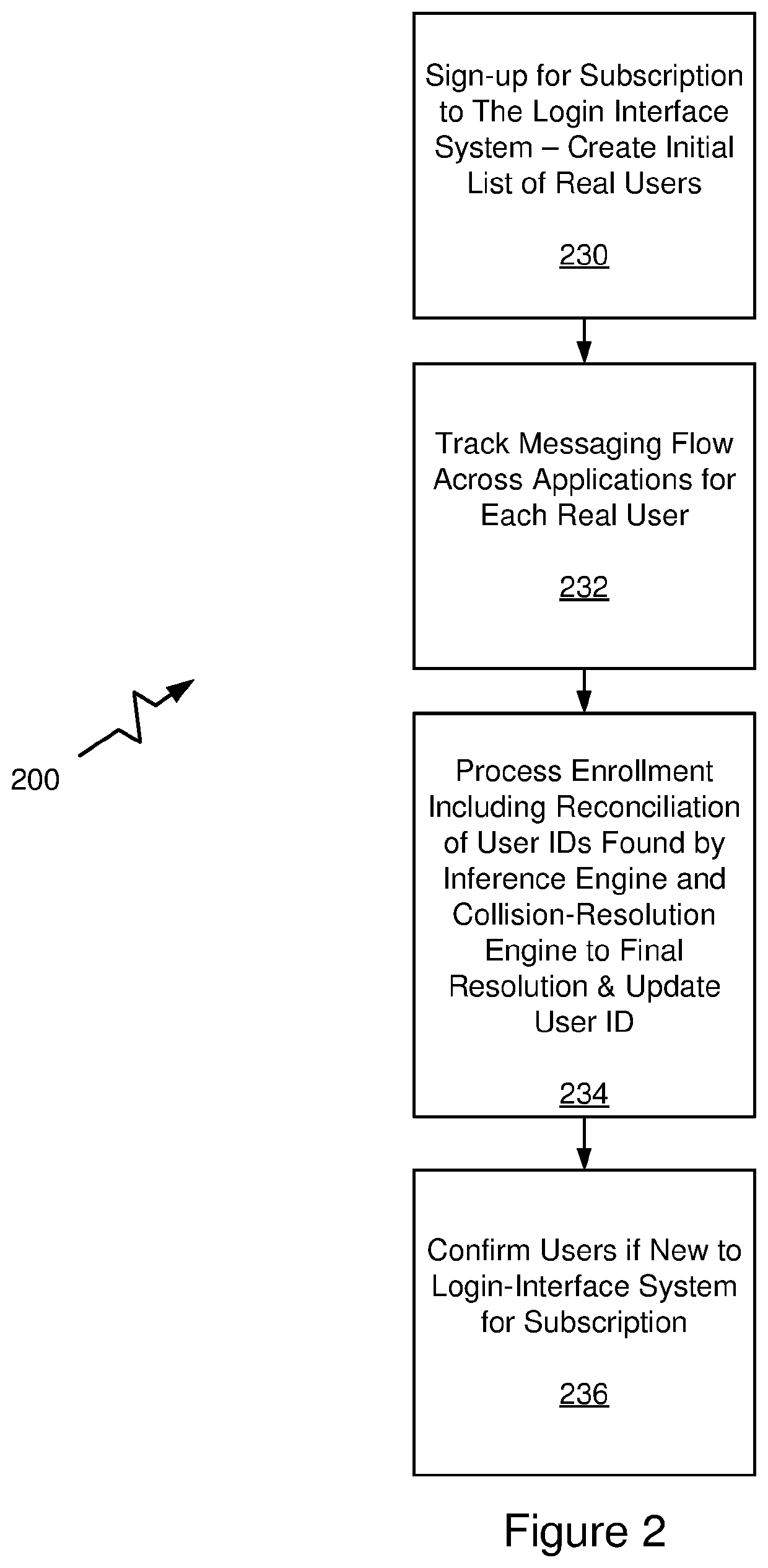
PendingUS20220014510A1Simple processEasy to addInference methodsData switching networksMessage deliveryEngineering
A system and method for improving login processes with a unique login-interface system is disclosed. The unique login-interface system allows users to subscribe, join, or sign-up for an automatic login interface that does not require explicit registration other than inclusion in a messaging system. The messaging system may be any number of systems such as email, text messaging, phone calls, or any other messaging system in which there is a user identification or alias associated with a user. The user identification may be of any type that is presented or recognized in a computing world. The unique login-interface system includes an identity-provider application with a collision-resolution engine to ensure unique user identity credentials and an inference engine to identity multiple participant entries for a single user.
Owner:STRETCH IND LLC
Modular alga photobioreactor
ActiveCN103740581AImprove stabilityImprove cultivation efficiencyBioreactor/fermenter combinationsBiological substance pretreatmentsModularityPhotobioreactor
The invention discloses a modular alga photobioreactor. An alga culture standard module is connected with an illumination standard module through a bolt; the other side surface of the alga culture standard module is connected with a gas exchange standard module through a bolt; the alga culture standard module is connected with a culture liquid measurement and control unit through a hose; a first liquid inlet of the alga culture standard module is connected with a second liquid outlet of the culture liquid measurement and control unit; a liquid outlet of the alga culture standard module is connected with a second liquid inlet of the culture liquid measurement and control unit; the gas exchange standard module is connected with a gas measurement and control unit through a hose; a first gas inlet of the gas exchange standard module is connected with a second gas outlet of the culture liquid measurement and control unit; a first gas outlet of the gas exchange standard module is connected with a second liquid outlet of the culture liquid measurement and control unit. The modular alga photobioreactor disclosed by the invention is simple in structure and convenient to use, improves the operation stability of the equipment, improves the culture efficiency by 5-8 times, and provides a good standard experimental equipment platform for further optimizing the design and expanding the reaction volume and the like.
Owner:INST OF AQUATIC LIFE ACAD SINICA
Airport ground scheduling flow modeling system oriented to task simulation
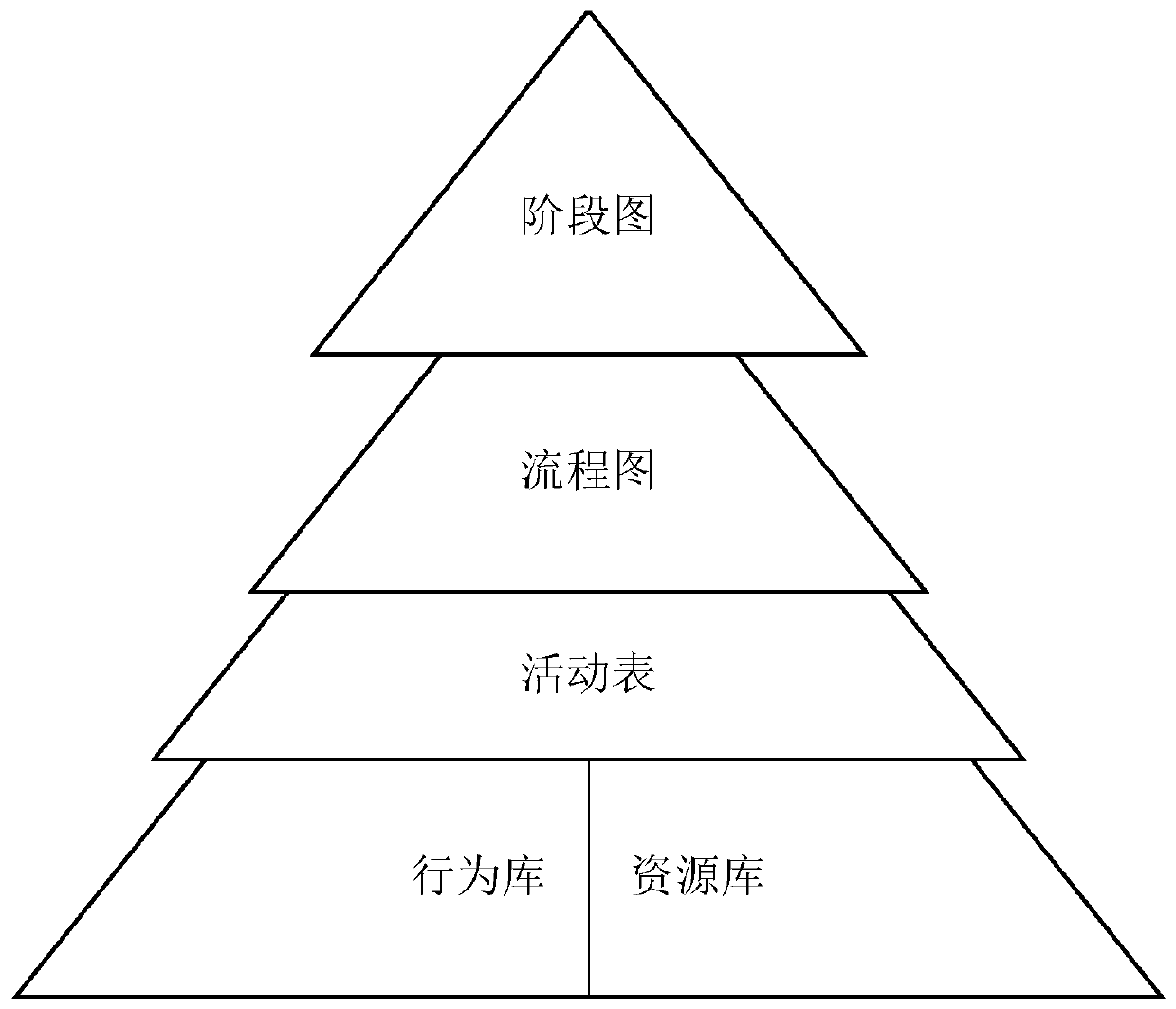
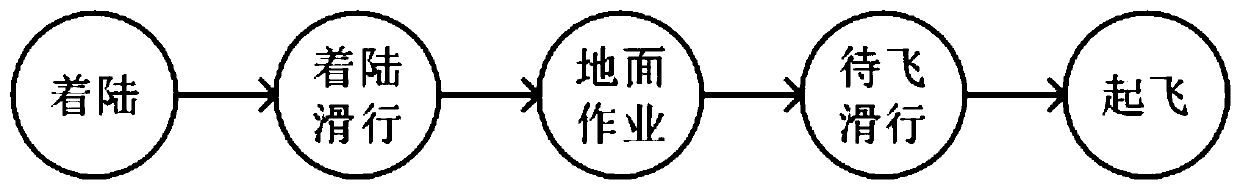
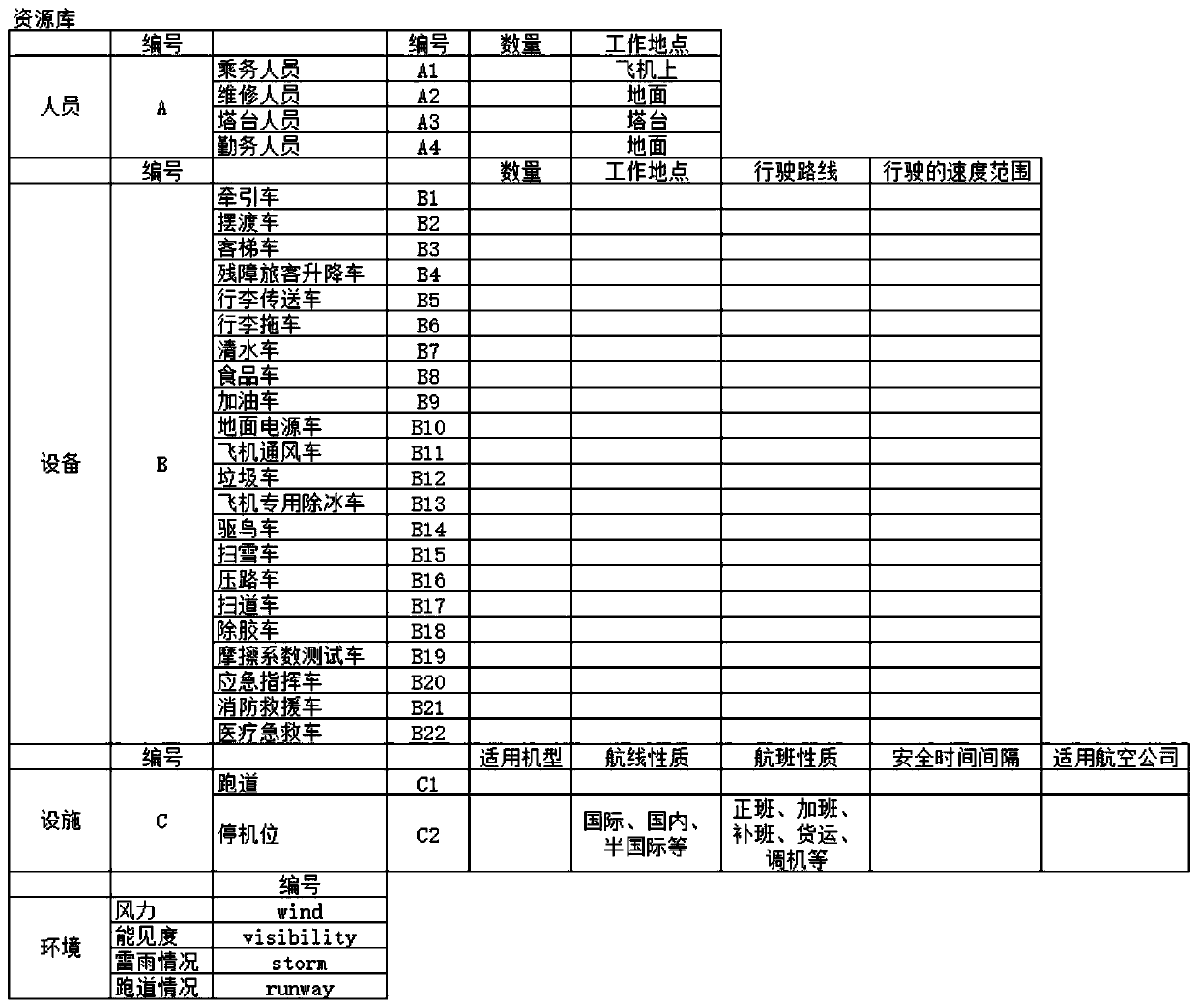
ActiveCN110008581AEasy to understandStrong maintainabilitySpecial data processing applicationsNatural languageProcess modeling
The invention discloses an airport ground scheduling flow modeling system oriented to task simulation, and the system comprises a scheduling management module which is used for receiving the state information of an airport ground scheduling task and a simulation main body, and monitoring the real-time progress of the airport ground scheduling task; a stage diagram generation module; a resource library generation module; a behavior library generation module; an activity table generation module; and a flow chart generation module. When an airport scheduling problem needs to deploy various different objects, simulation entity characteristics are described mainly by using graphs and natural languages to quickly model core functions of scheduling objects, process constraints caused by processesand the like, and the method is suitable for analyzing complex collaborative tasks and used for task simulation.
Owner:BEIHANG UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com