System and method for searching and killing malicious codes based on expandable mode
A malicious code and extended mode technology, applied in the fields of instruments, digital data processing, computer security devices, etc., can solve problems such as deficiencies, and achieve the effects of easy addition and deletion, easy disposal and killing, and easy maintenance.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
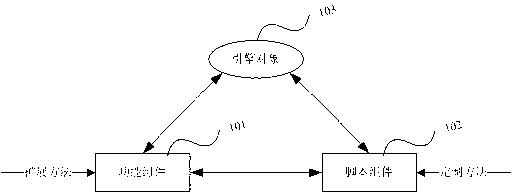
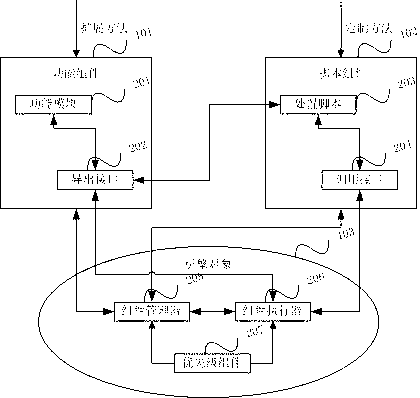
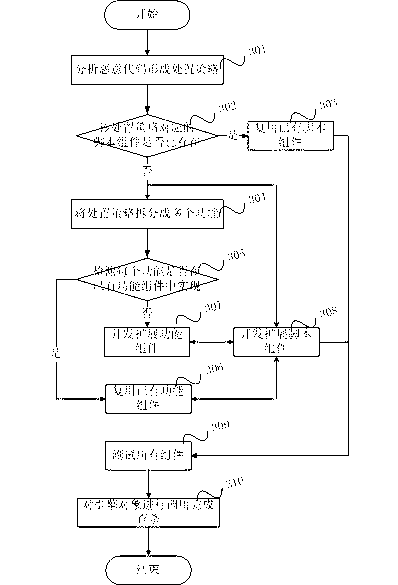
Image
Examples
example 1
[0083] =| = | =| =| =
[0084] value:
[0085] 01. Full file path
[0086] value:
[0087] 01. FullFile / / full file
[0088] 02. FullPE / / full PE
[0089] 03. MZHeader / / Dos header and Dos body
[0090] 04. PEHeader / / PE head to PE tail
[0091] 05. AddressOfEntryPoit / / entry point
[0092] / / If Offset is +: then the entry point to the end of the file. If Offset is -: then the file starts to the entry point
[0093] 06. Import / / import table
[0094] 07. Export / / Export table
[0095] 08. Resource / / Resource section
[0096] 09. Section / / Each section When it is Section, Offset is: which section_offset, for example: =
[0097] 10. LastSection / / The last section
[0098] 11. PEAttach / / PE additional information
[0099] Value: Prefix + - Required. If Offset is 0, the head offset is +0 and the tail offset is -0
[0100] 01. + / / offset from the beginning
[0101] 02. - / / Tail start offset
[0102] Value: If not t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com