Mobile-terminal-based identity authentication system and method
A mobile terminal and identity authentication technology, applied in the field of strong identity authentication security system, can solve problems such as high cost, inability to solve dynamic factor synchronization, and inability to communicate, achieving cost savings, flexible and convenient software clients Synchronized effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0040] The mobile terminal-based identity authentication method provided by the present invention is implemented according to the following steps:
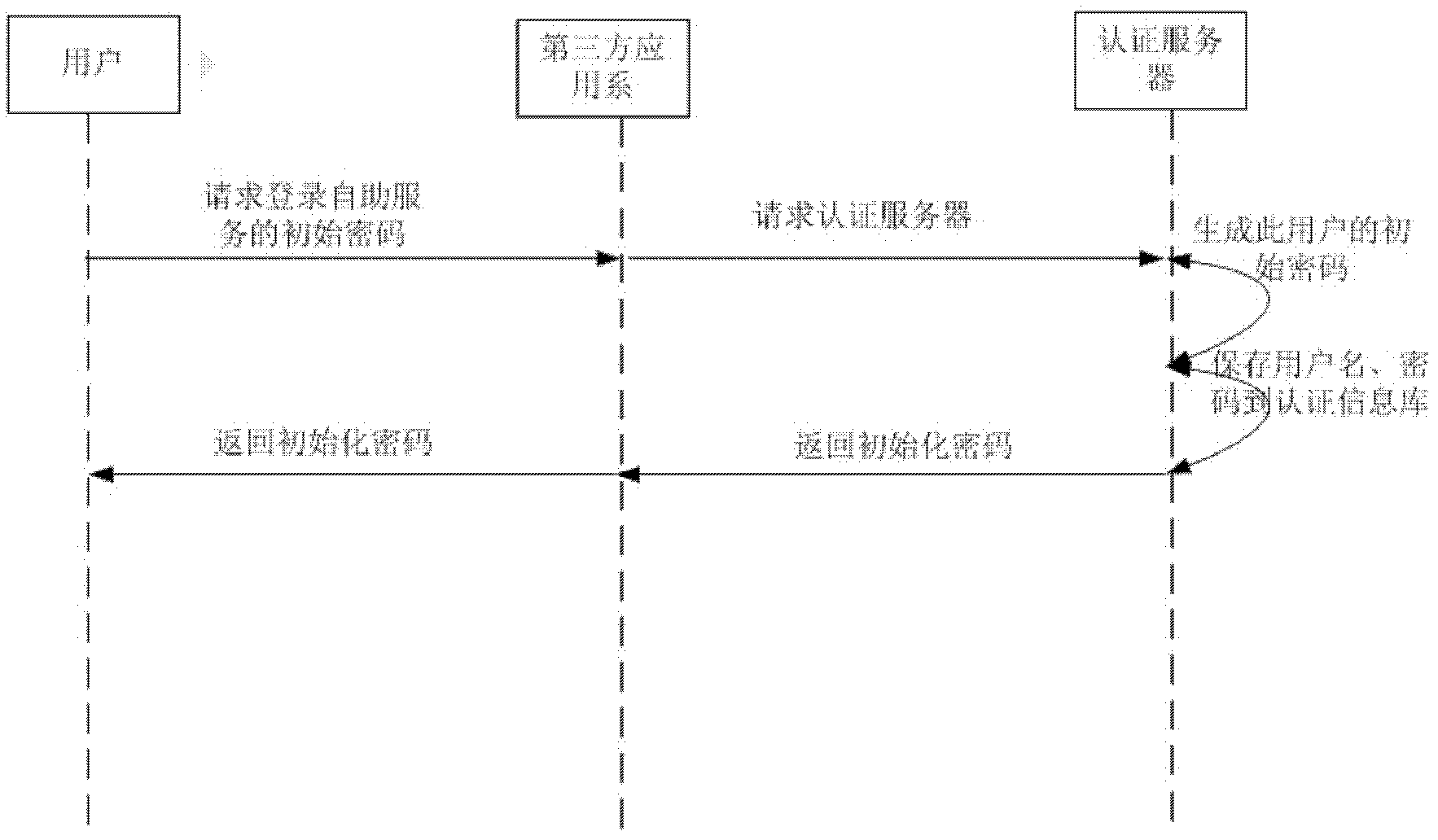
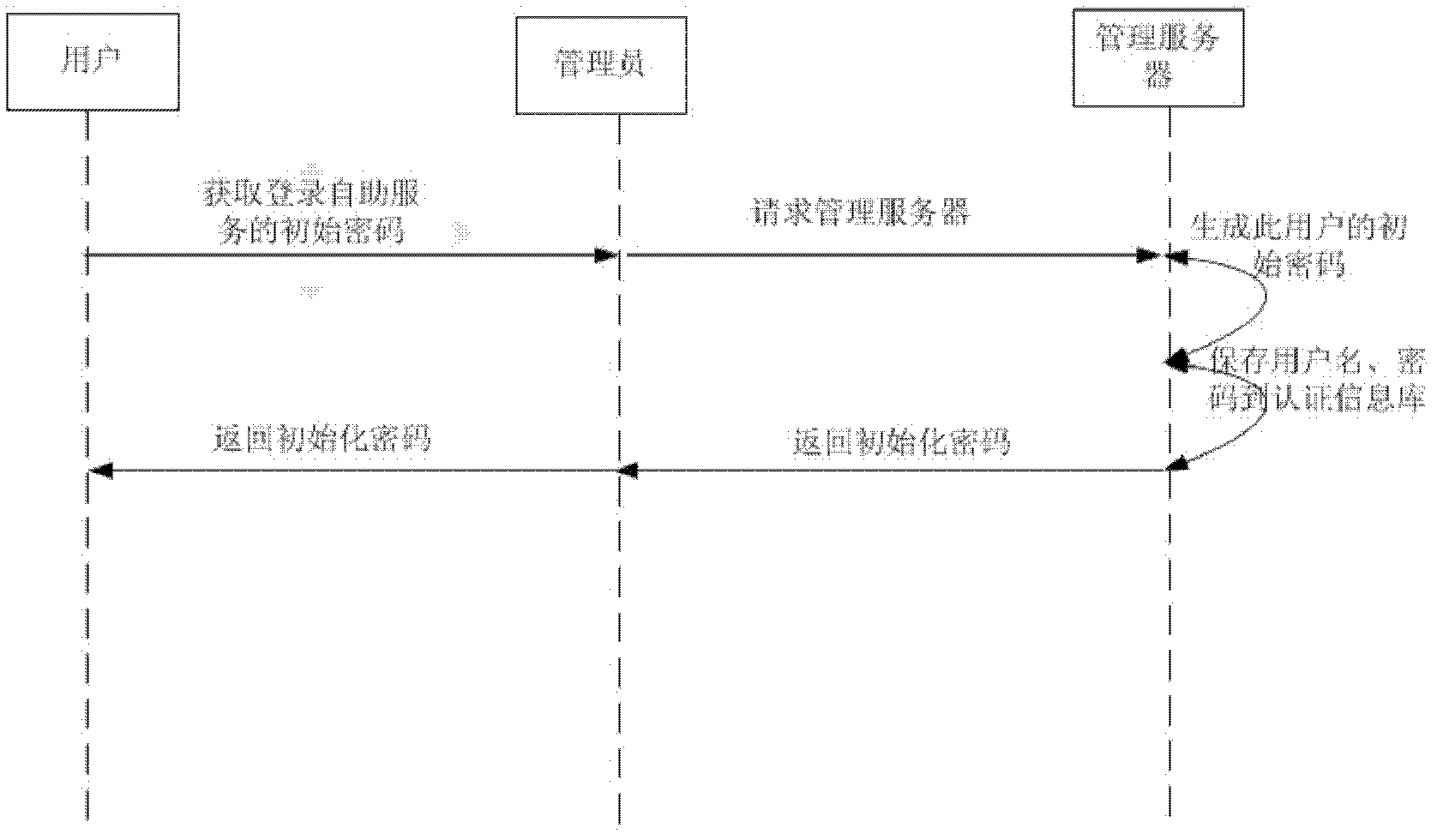
[0041] (1) The user can obtain the initial password to log in to the self-service terminal through a third-party application system (B / S) or from the administrator (such as figure 2 Said).
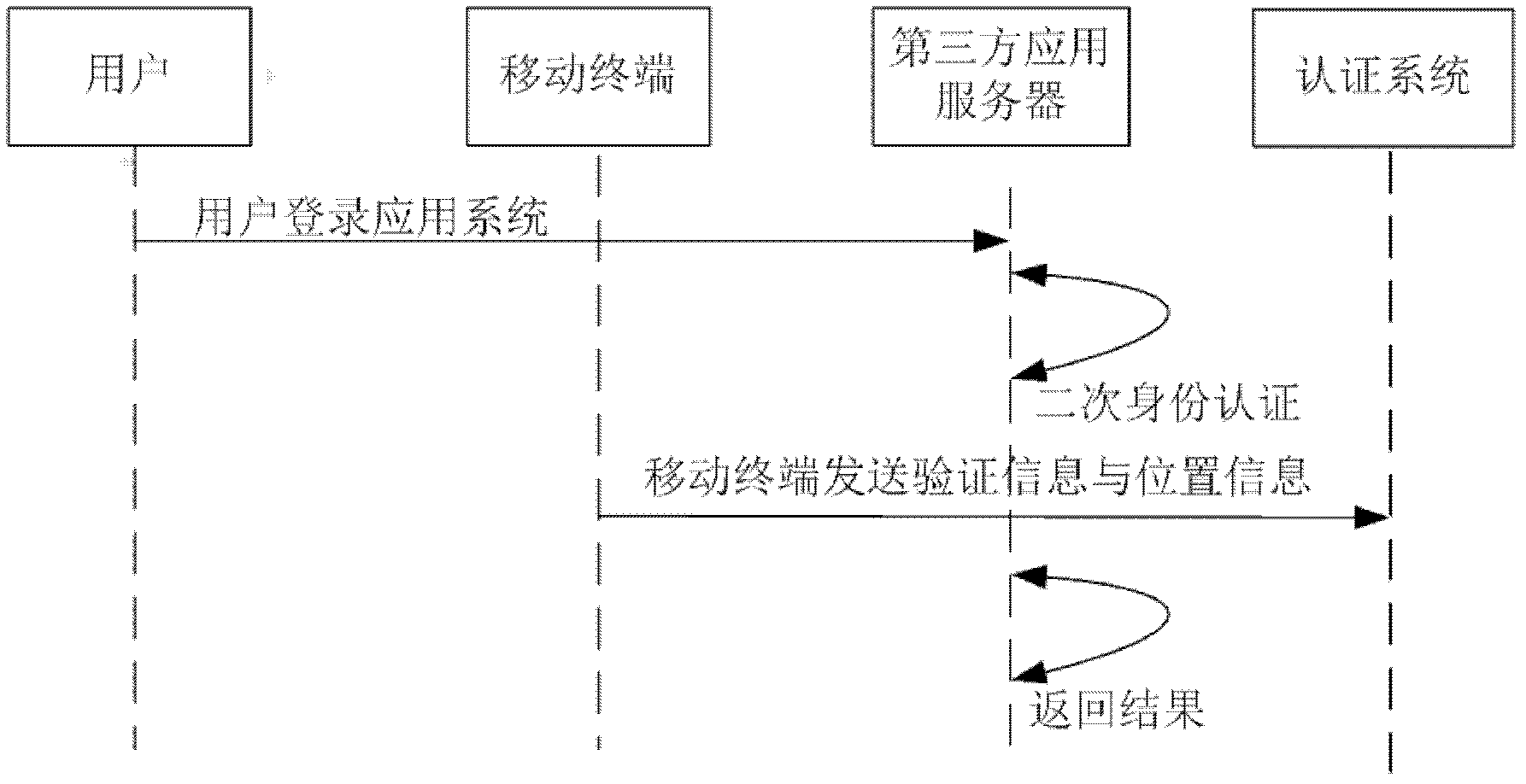
[0042] (2) Generate the serial number to initialize the mobile client, (such as image 3 (Mentioned) (3) Initialization of the mobile client, (such as Figure 4 Said) (4) Identity authentication: When the user submits a login application to the third-party application server, the mobile terminal submits an authentication request to the authentication server, and the third-party application server returns the authentication result to the user after obtaining the authentication result of the mobile terminal by the authentication server ( Such as Figure 5 Said).
[0043] The system of the present invention for realizing the above-mentioned identity au...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com