System and method for delivering versatile security, digital rights management, and privacy services from storage controllers
a storage controller and digital rights management technology, applied in the field of methods and systems for securing computer systems, can solve the problems of not implementing an overall corresponding improvement in the client platform, limited security of traditional operating systems, and inability to test local or remote users
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
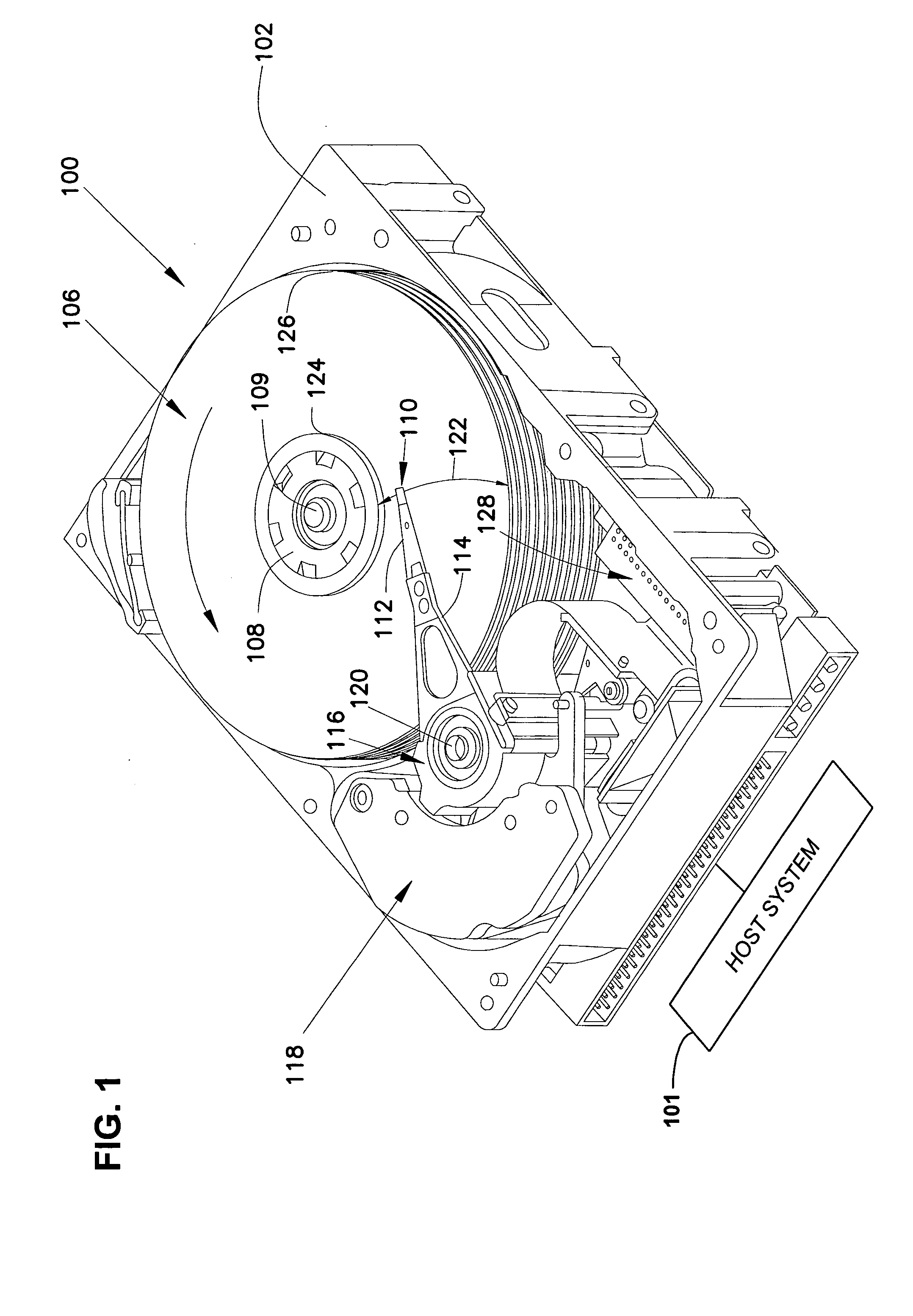
[0027]FIG. 1 is a perspective view of a disc drive 100 in which the present invention may be used. Disc drive 100 can be configured as a traditional magnetic disc drive, a magneto-optical disc drive or an optical disc drive, for example. Disc drive 100 includes a housing with a base 102 and a top cover (not shown). Disc drive 100 further includes a disc pack 106, which is mounted on a spindle motor (not shown) by a disc clamp 108. Disc pack 106 includes a plurality of individual discs 107, which are mounted for co-rotation about central axis 109. Each disc surface has an associated slider 110, which is mounted to disc drive 100 and carries a read / write head for communication with the disc surface.
[0028] In the example shown in FIG. 1, sliders 110 are supported by suspensions 112 which are in turn attached to track accessing arms 114 of an actuator 116. The actuator shown in FIG. 1 is of the type known as a rotary moving coil actuator and includes a voice coil motor (VCM), shown gen...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com