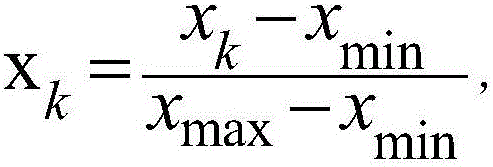Patents
Literature
36 results about "Policy information base" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
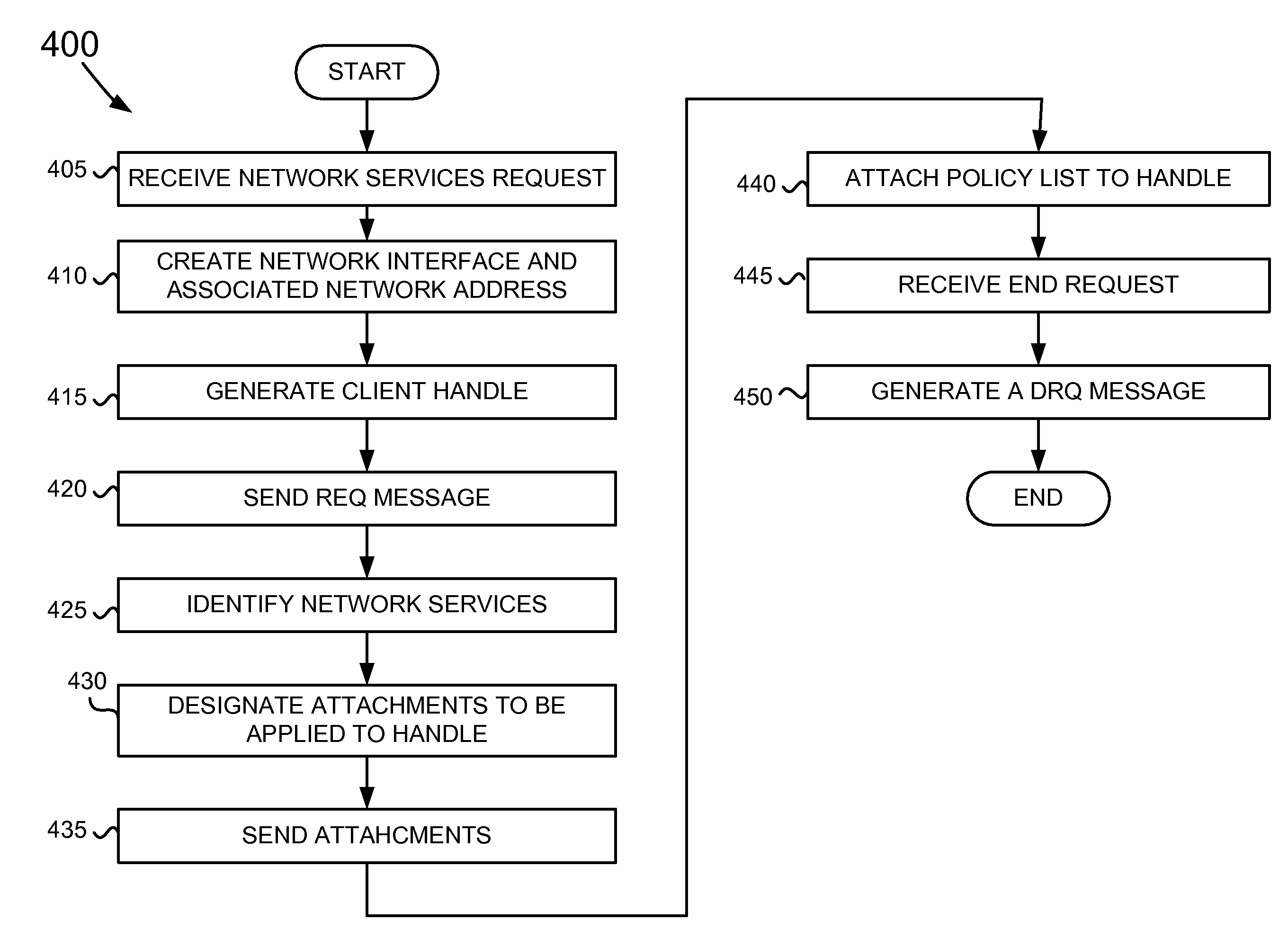
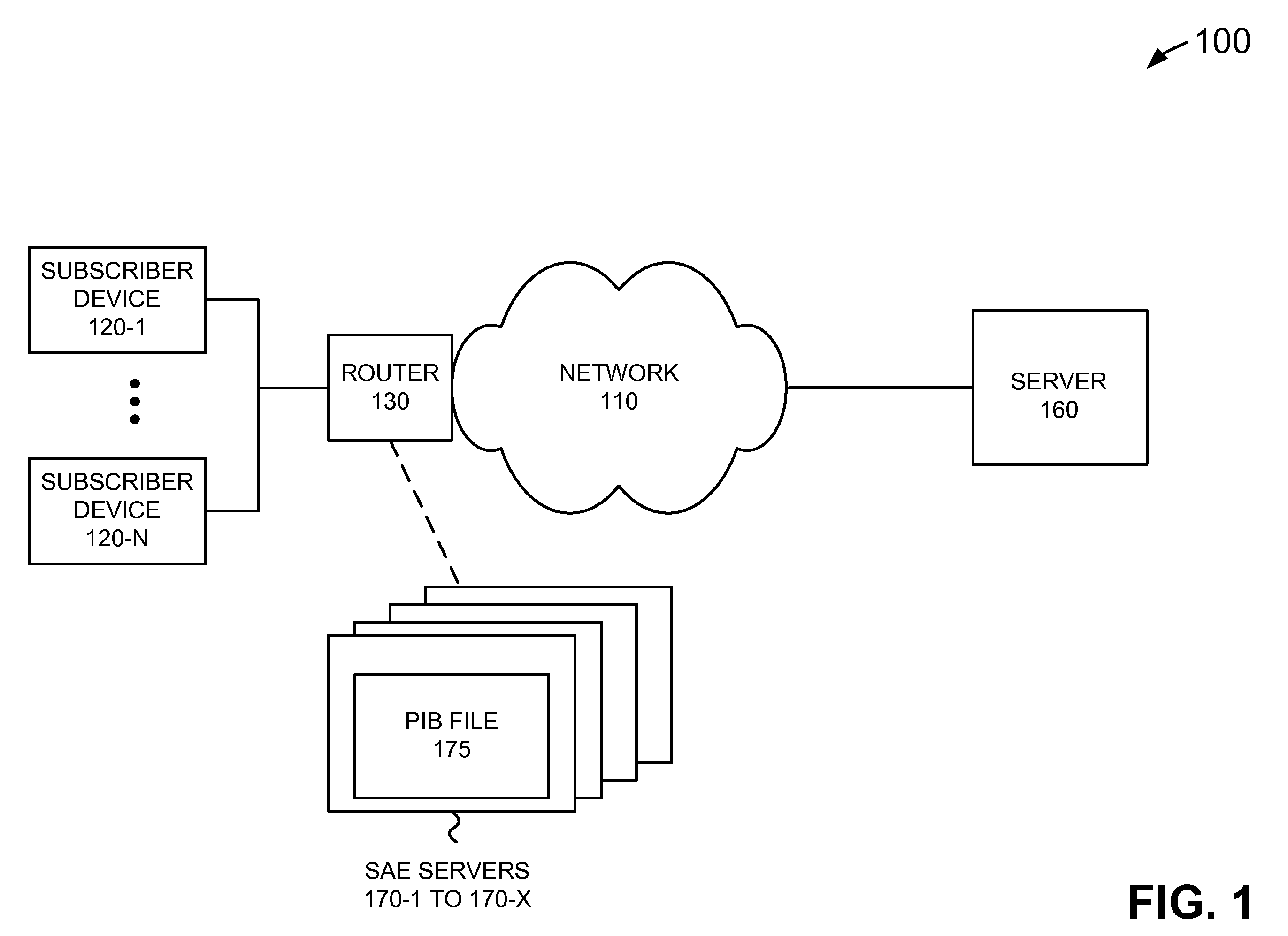
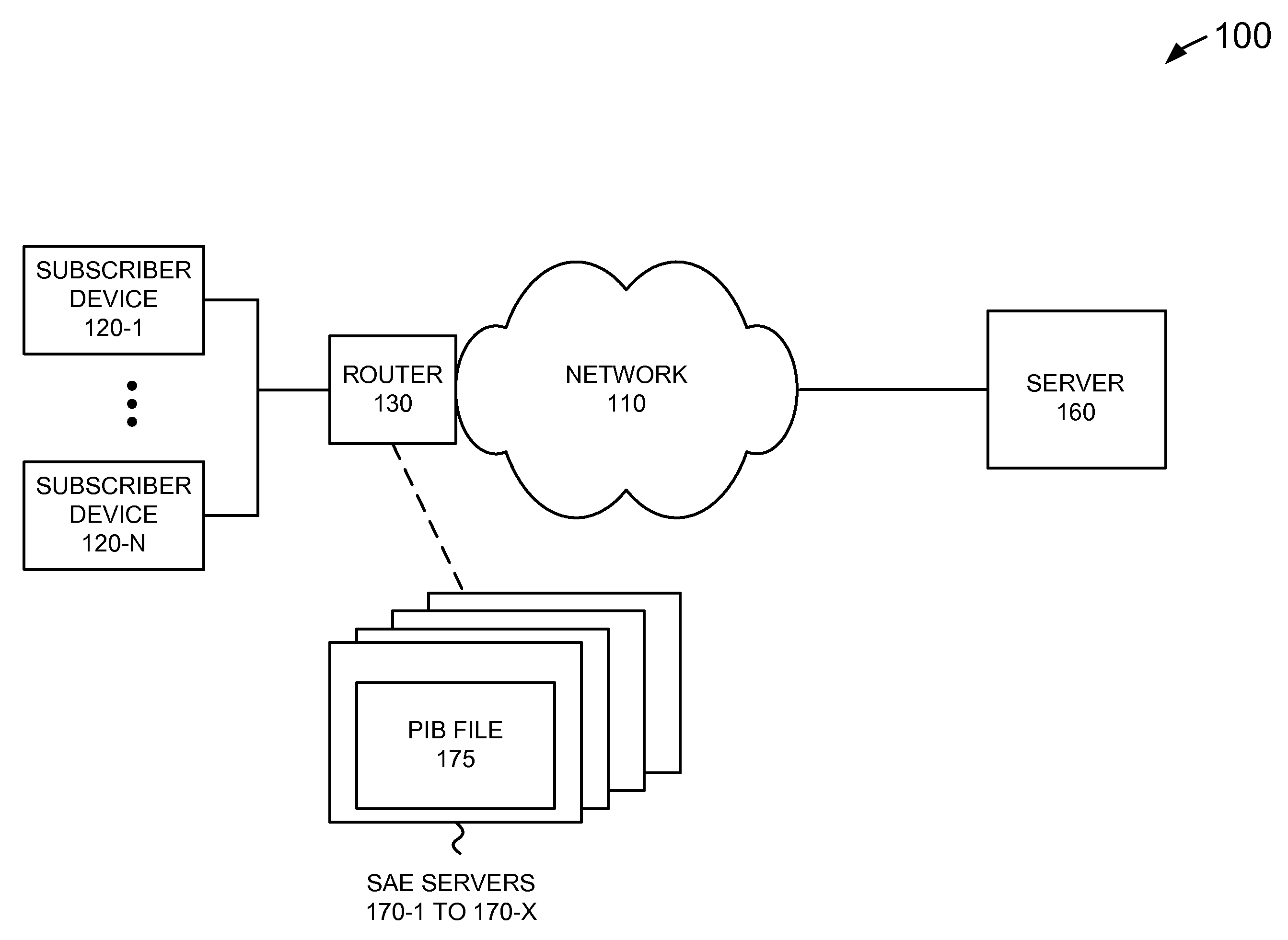
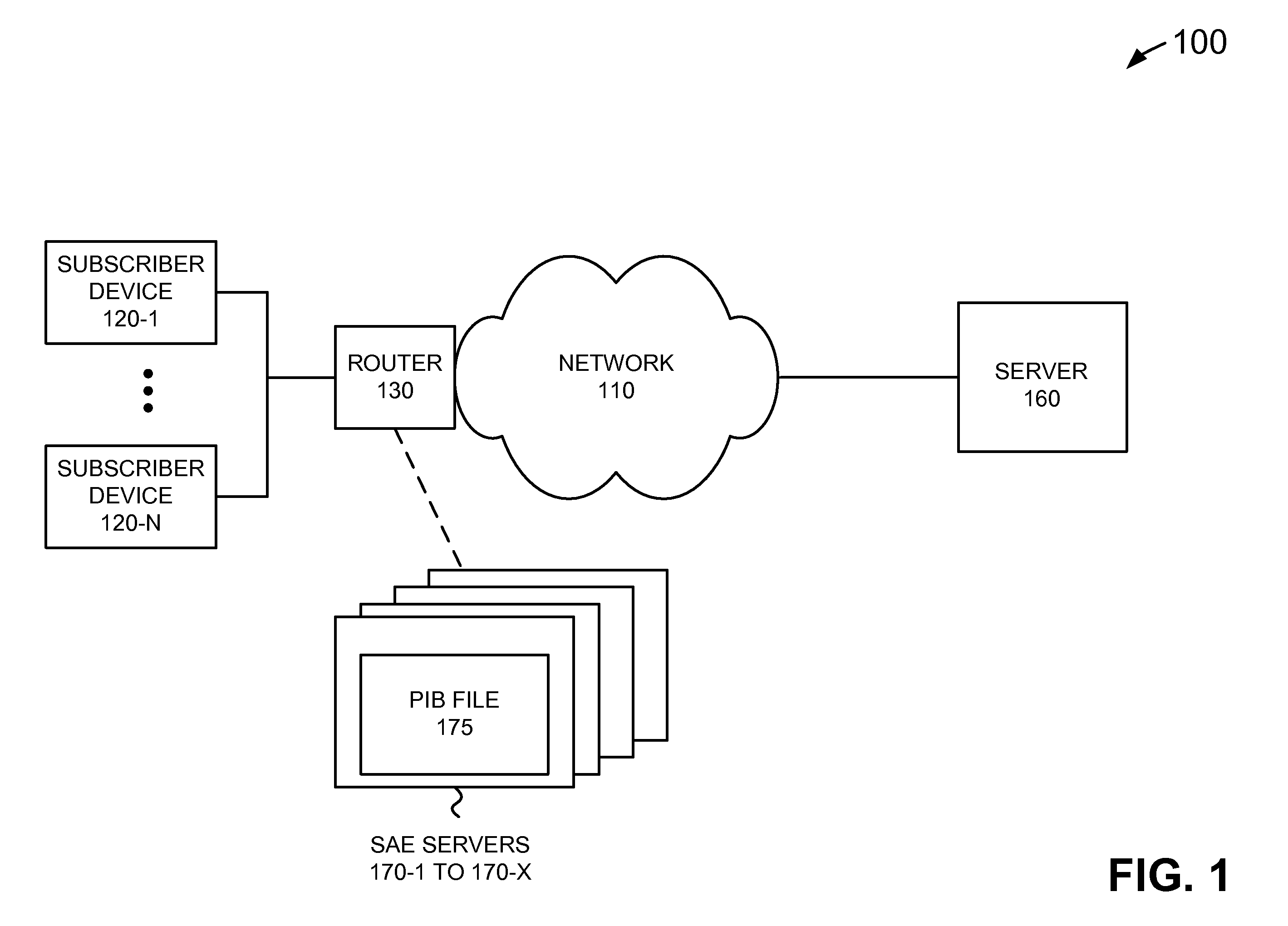
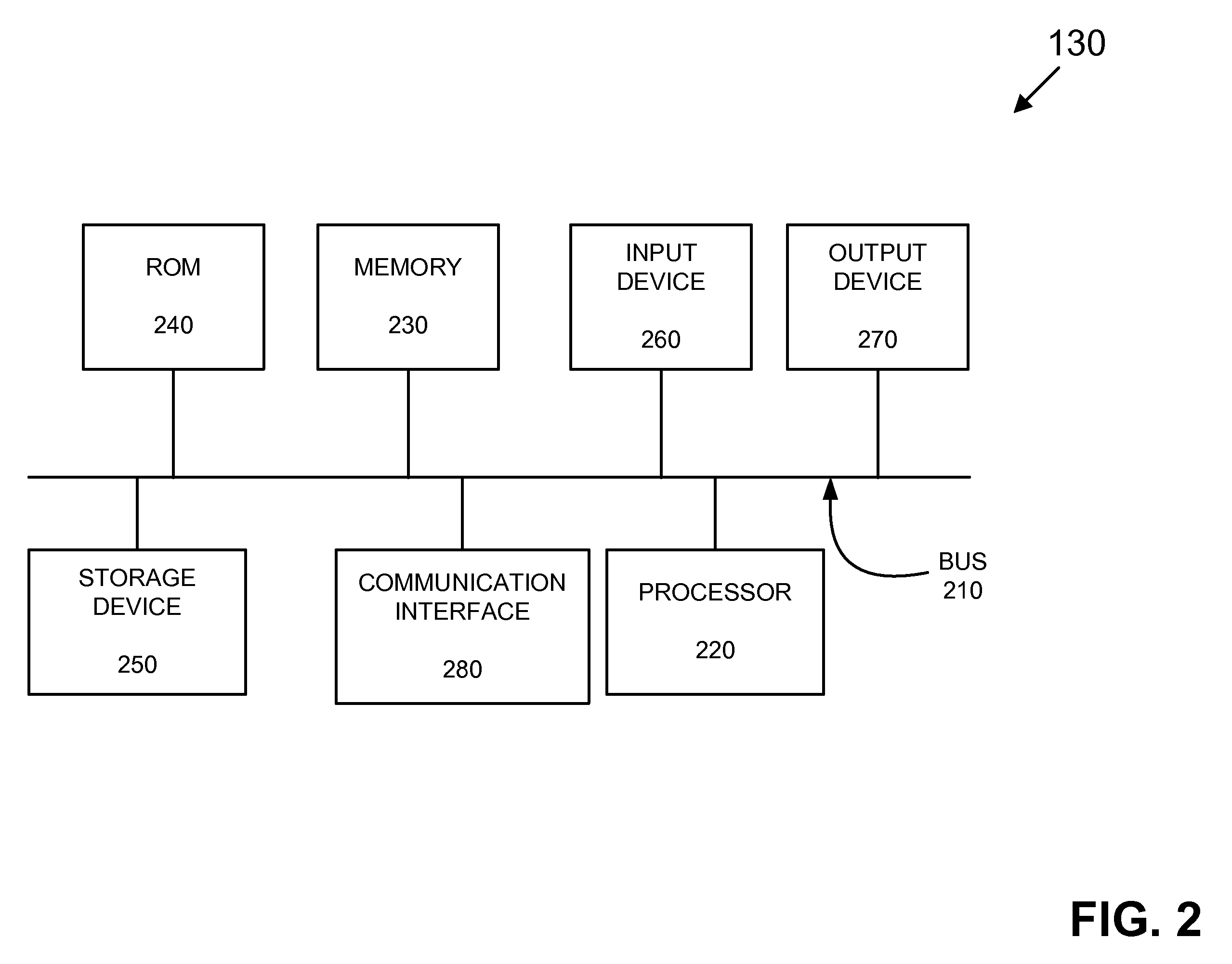
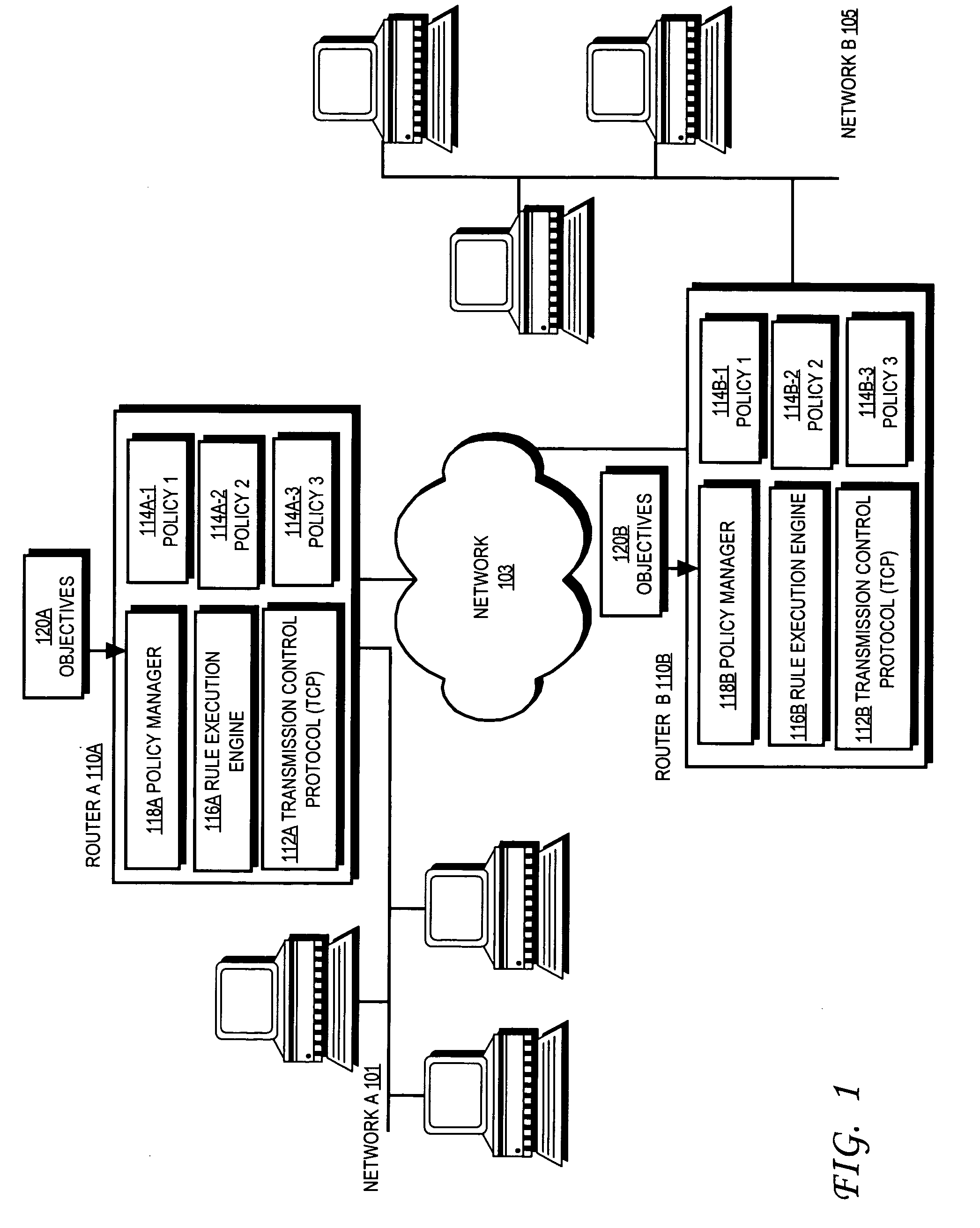
Dynamic service activation using COPS-PR to support outsourcing and configuration models for policy control
ActiveUS7734784B1Service provisioningMultiple digital computer combinationsInformation repositoryCommon Open Policy Service
A device may include a service activation engine (SAE) including: a policy information base (PIB) file that defines a plurality of attachments that correspond to a plurality of network policies; and a server. The server may receive a request, using common open policy service for policy provisioning (COPS-PR), for a network service related to an interface handle associated with a subscriber device; determine which ones of the network policies correspond to the network service; and send, using COPS-PR, a provisioning instance (PRI) including a first of the attachments to implement the ones of the network policies to the interface handle based on the attachments.
Owner:JUMIPER NETWORKS INC
Apparatus and method for managing quality of service in integrated network of heterogeneous mobile network
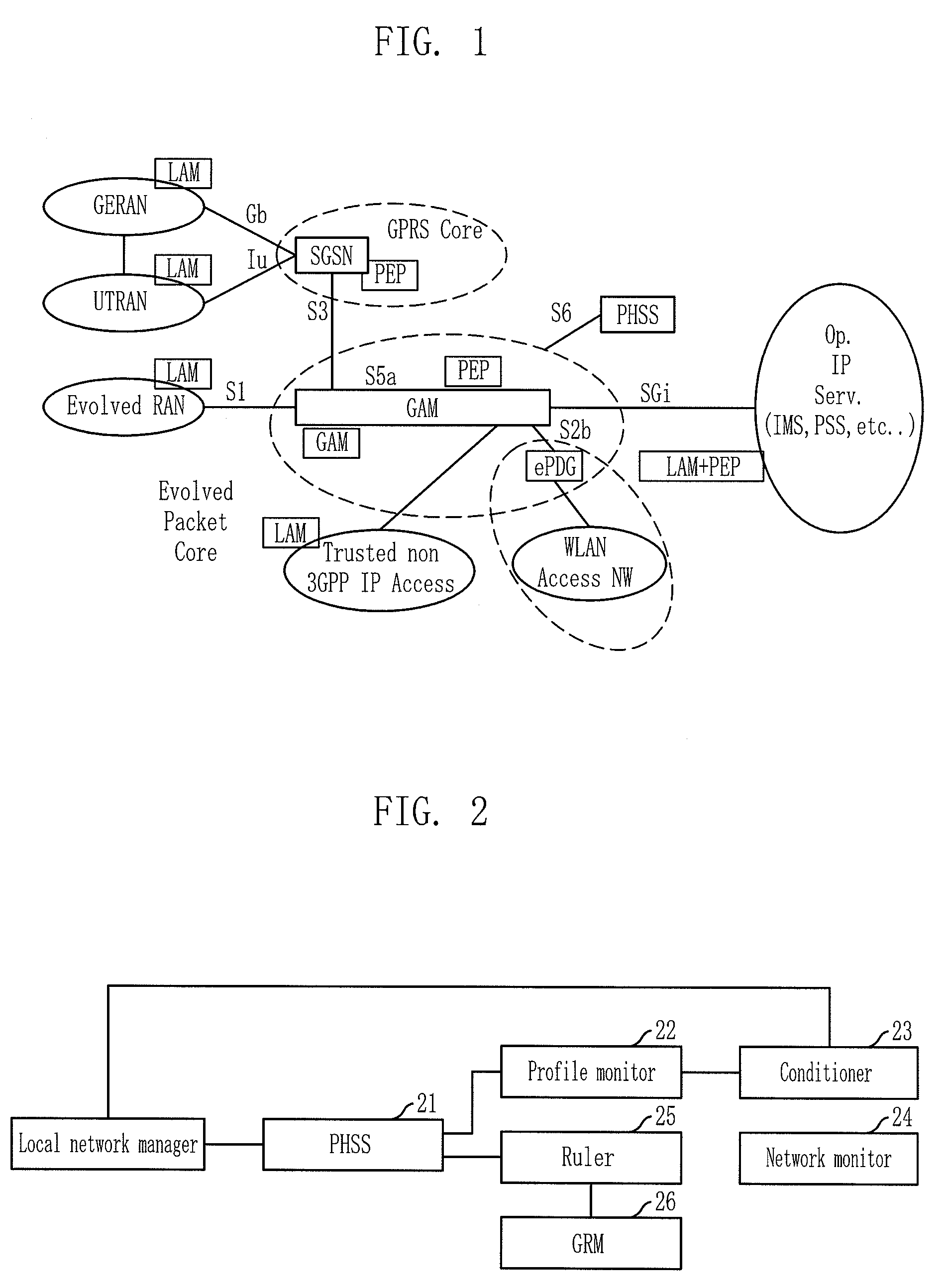
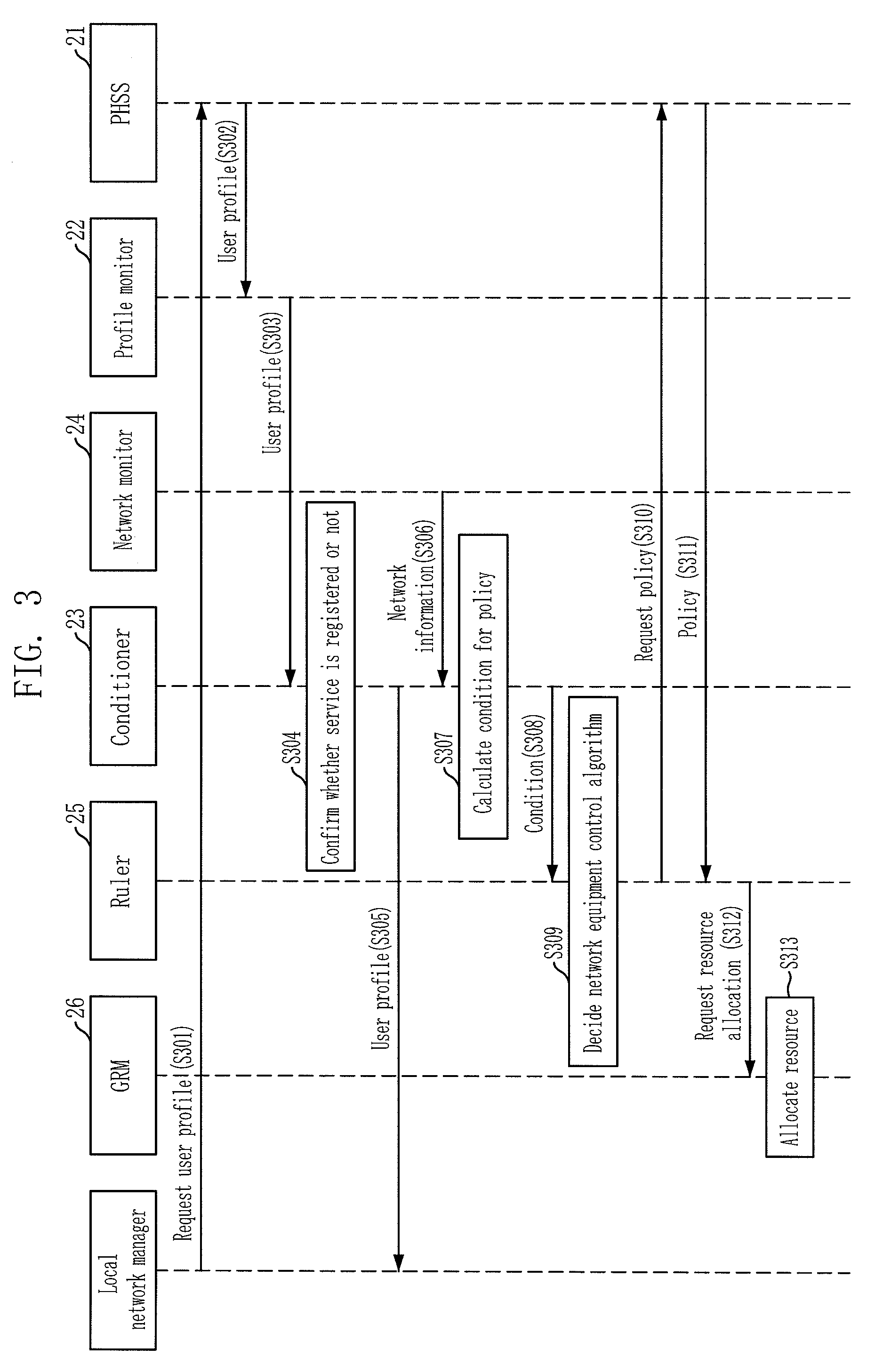
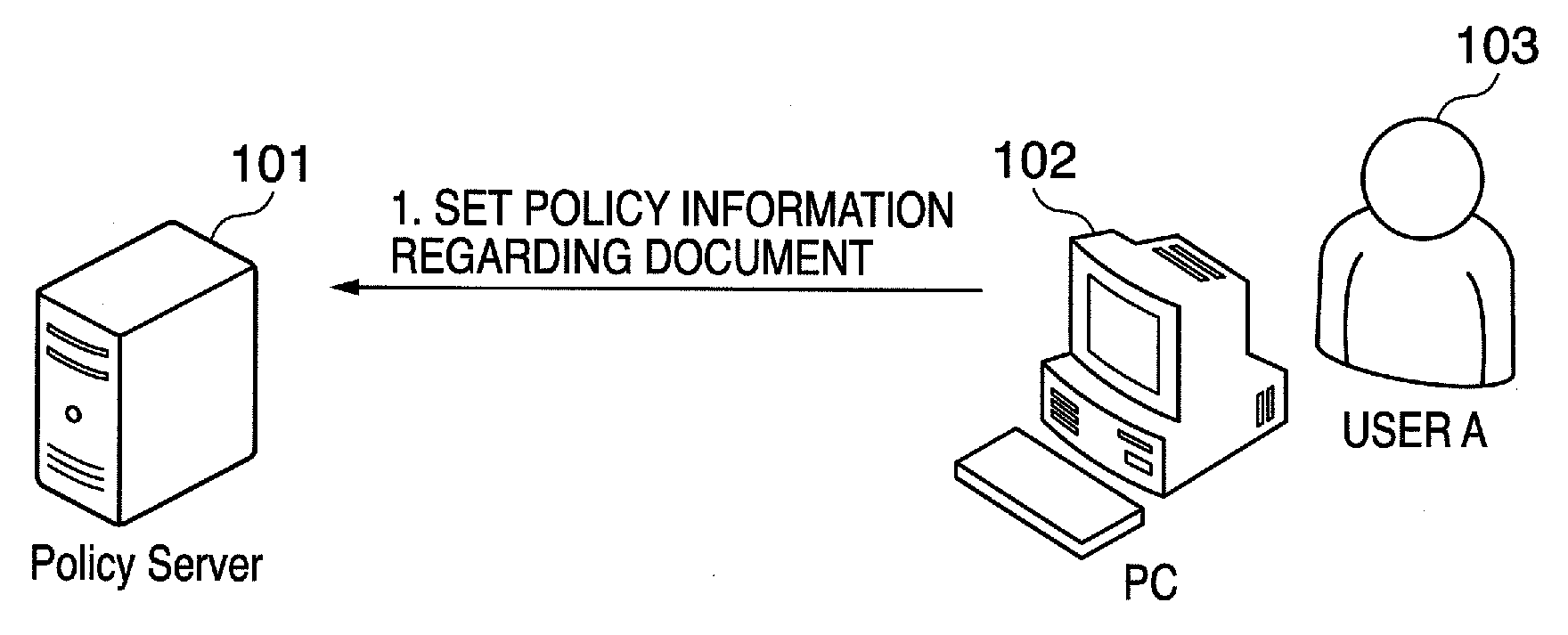
InactiveUS7756056B2Efficient managementError preventionFrequency-division multiplex detailsQuality of serviceNetworked system
An apparatus and method for managing QoS in an integrated network system are provided. The apparatus includes: an information provider, a condition calculator, a policy deciding unit, and a resource allocator. The information provider is for providing policy information based on a network equipment control algorithm, a user profile and network information. The condition calculator is for calculating conditions that are used for selecting a policy based on the user profile and the network information received from the information provider. The policy deciding unit is for deciding a network equipment control algorithm in accordance with the conditions, receiving the policy information corresponding to the decided network equipment control algorithm from the information provider, and requesting resource allocation. The resource allocator is for receiving the request of resource allocation from the policy deciding unit and allocating resources.
Owner:SAMSUNG ELECTRONICS CO LTD +1
Information processing apparatus, printing apparatus and printing system including thereof apparatuses
InactiveUS7861282B2Digital data processing detailsUser identity/authority verificationInformation processingDocumentation
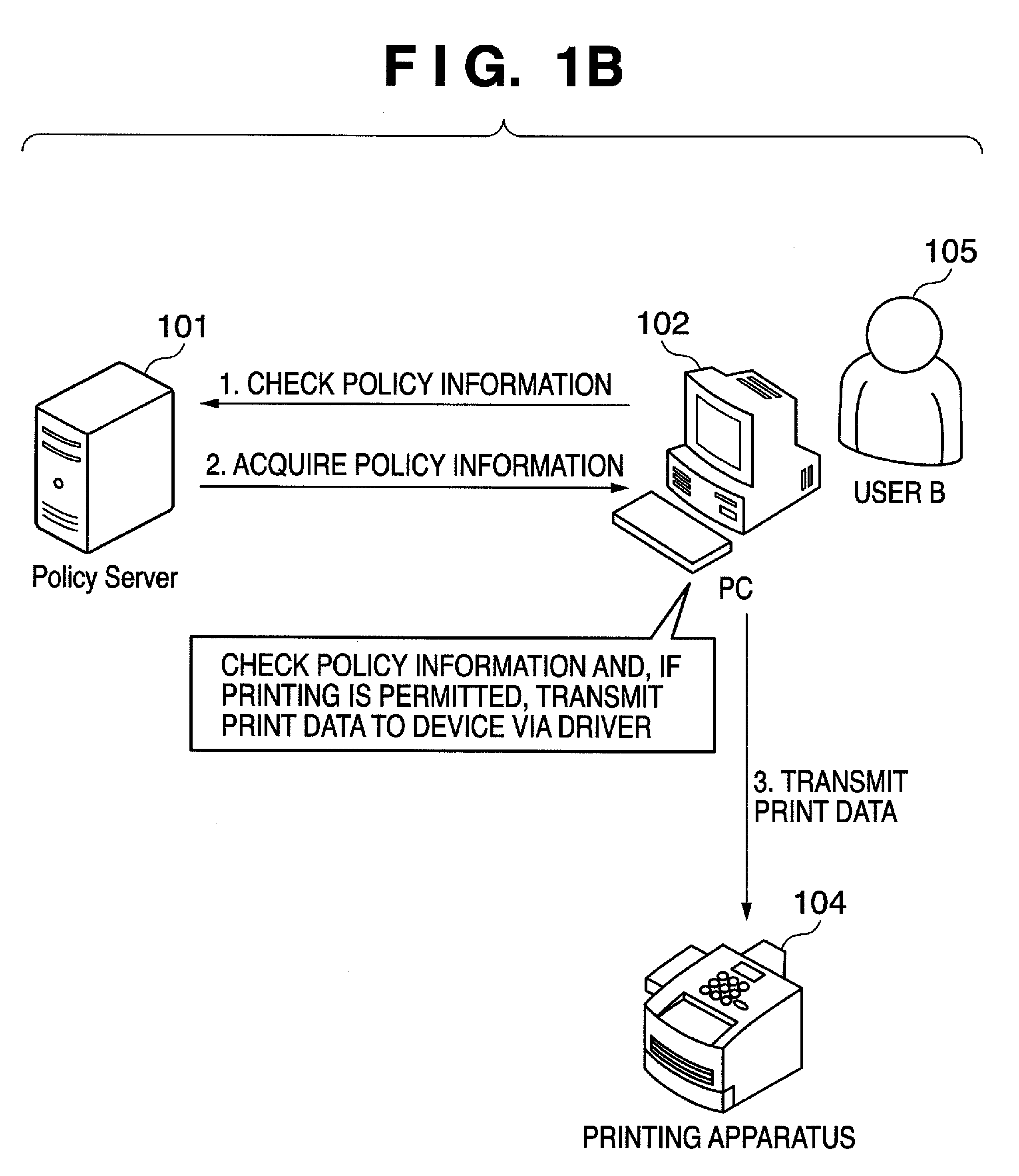
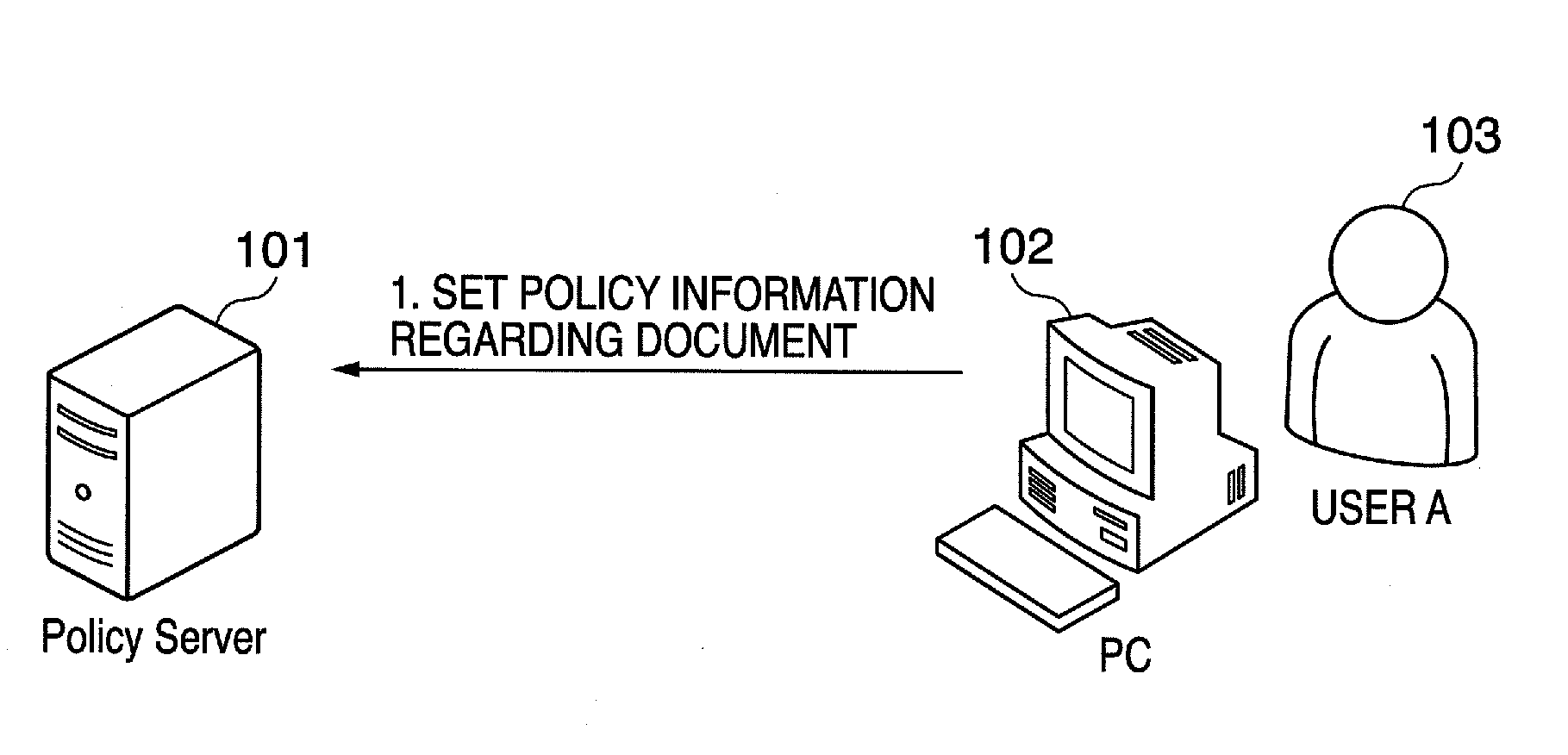
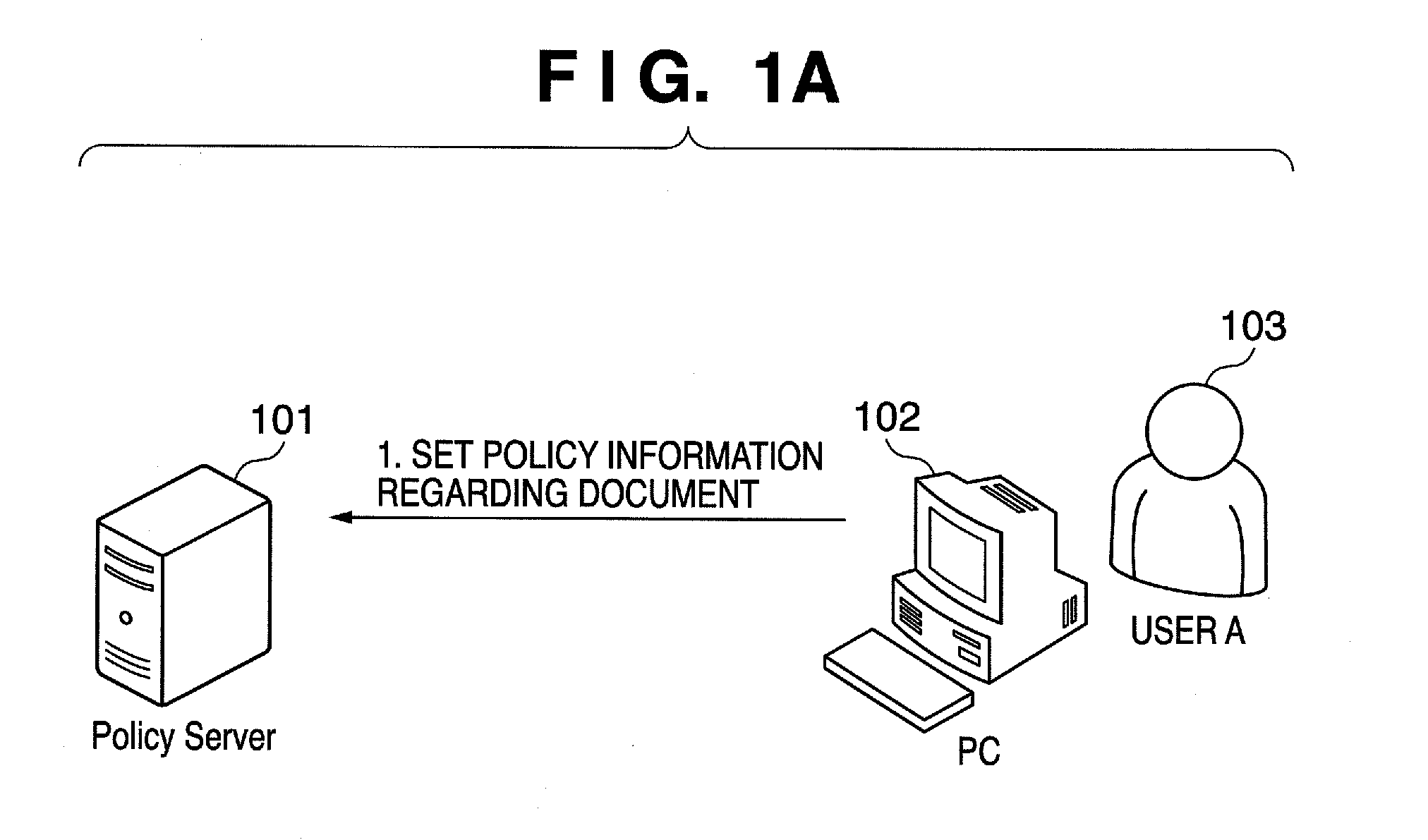
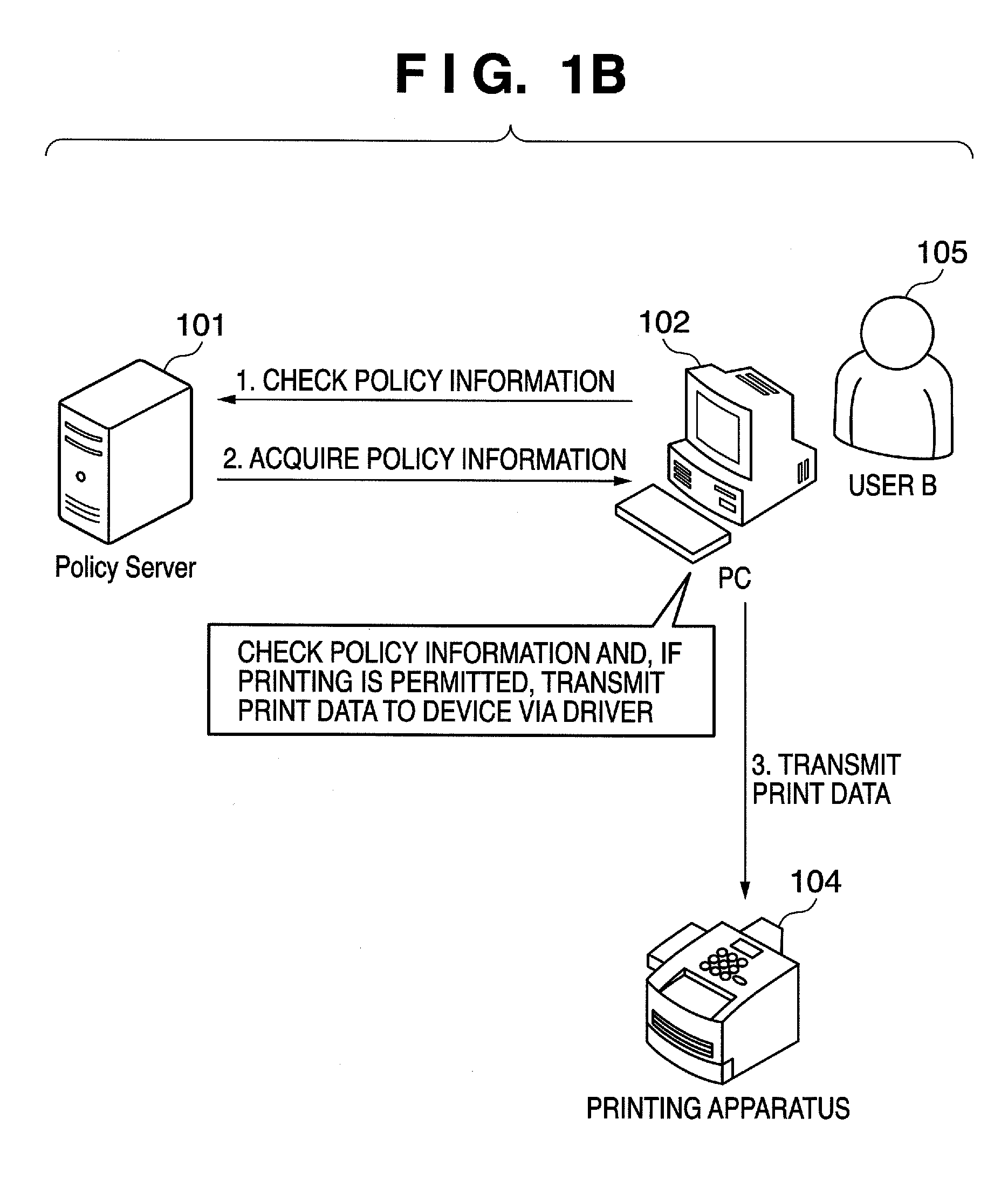
Provided is a printing system in which the latest policy information is reflected at all times and document-by-document policy information is checked. To accomplish this, the printing system includes an information processing apparatus adapted to output print data, a policy server adapted to manage policy information and at least one printing apparatus. The information processing apparatus outputs print data to which an identification information has been appended. The printing apparatus acquires print data via an information communication medium, accesses the policy server based upon access information and acquires policy information by transmitting authentication information and an identification information to the policy server. Further, in accordance with the acquired policy information, the printing apparatus determines whether or not to execute printing. The policy server issues the policy information based upon authentication information and identification information.
Owner:CANON KK
Information processing apparatus, printing apparatus and printing system including thereof apparatuses
InactiveUS20080034403A1Digital data processing detailsComputer security arrangementsInformation processingInformation access
Provided is a printing system in which the latest policy information is reflected at all times and document-by-document policy information is checked. To accomplish this, the printing system includes an information processing apparatus adapted to output print data, a policy server adapted to manage policy information and at least one printing apparatus. The information processing apparatus outputs print data to which an identification information has been appended. The printing apparatus acquires print data via an information communication medium, accesses the policy server based upon access information and acquires policy information by transmitting authentication information and an identification information to the policy server. Further, in accordance with the acquired policy information, the printing apparatus determines whether or not to execute printing. The policy server issues the policy information based upon authentication information and identification information.
Owner:CANON KK
Implementation method for bidirectional protective switching of multi-protocol label switching
ActiveCN101146115AEffective protectionLatency is equalError preventionData switching networksBidirectional trafficTraffic capacity
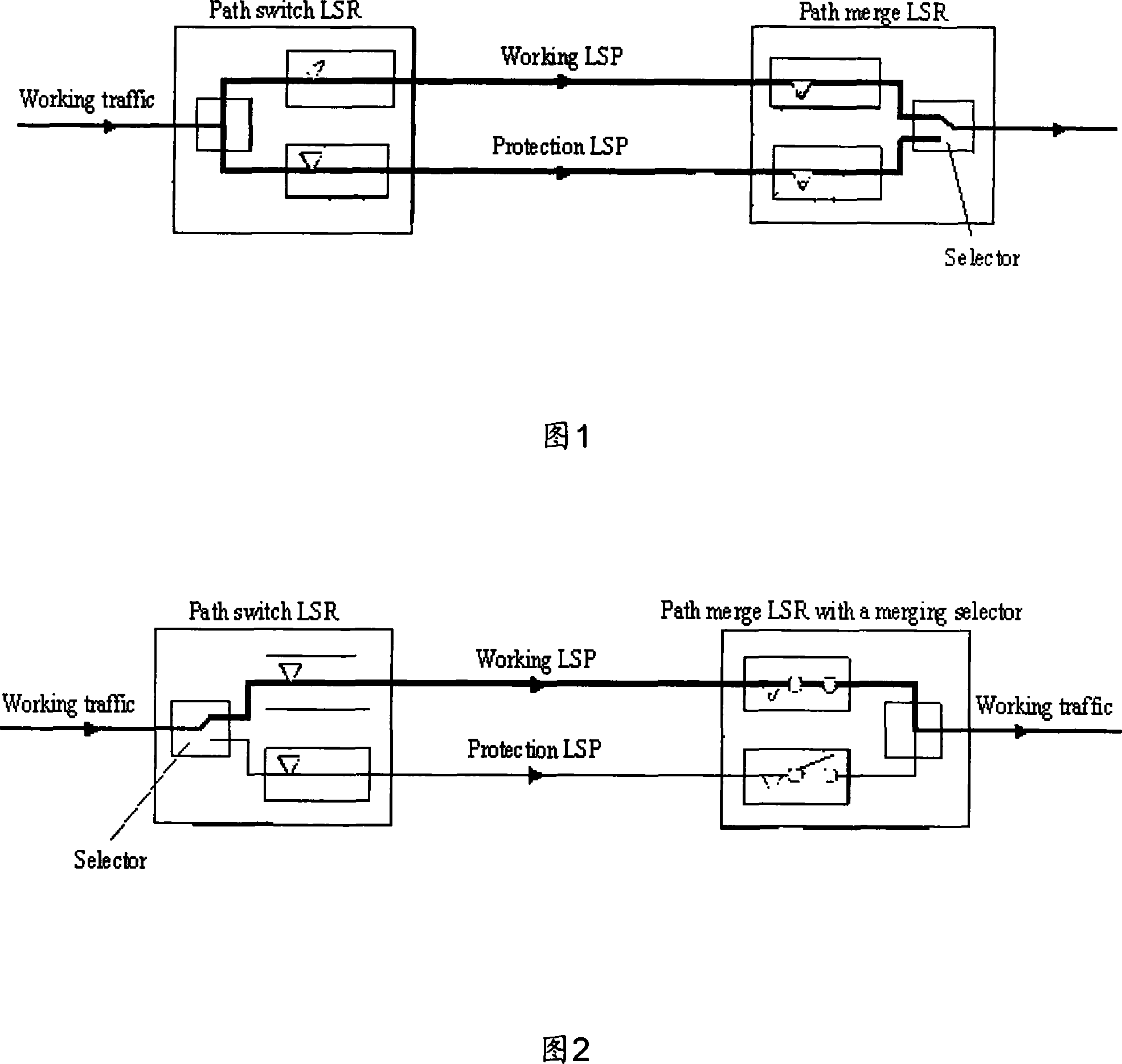
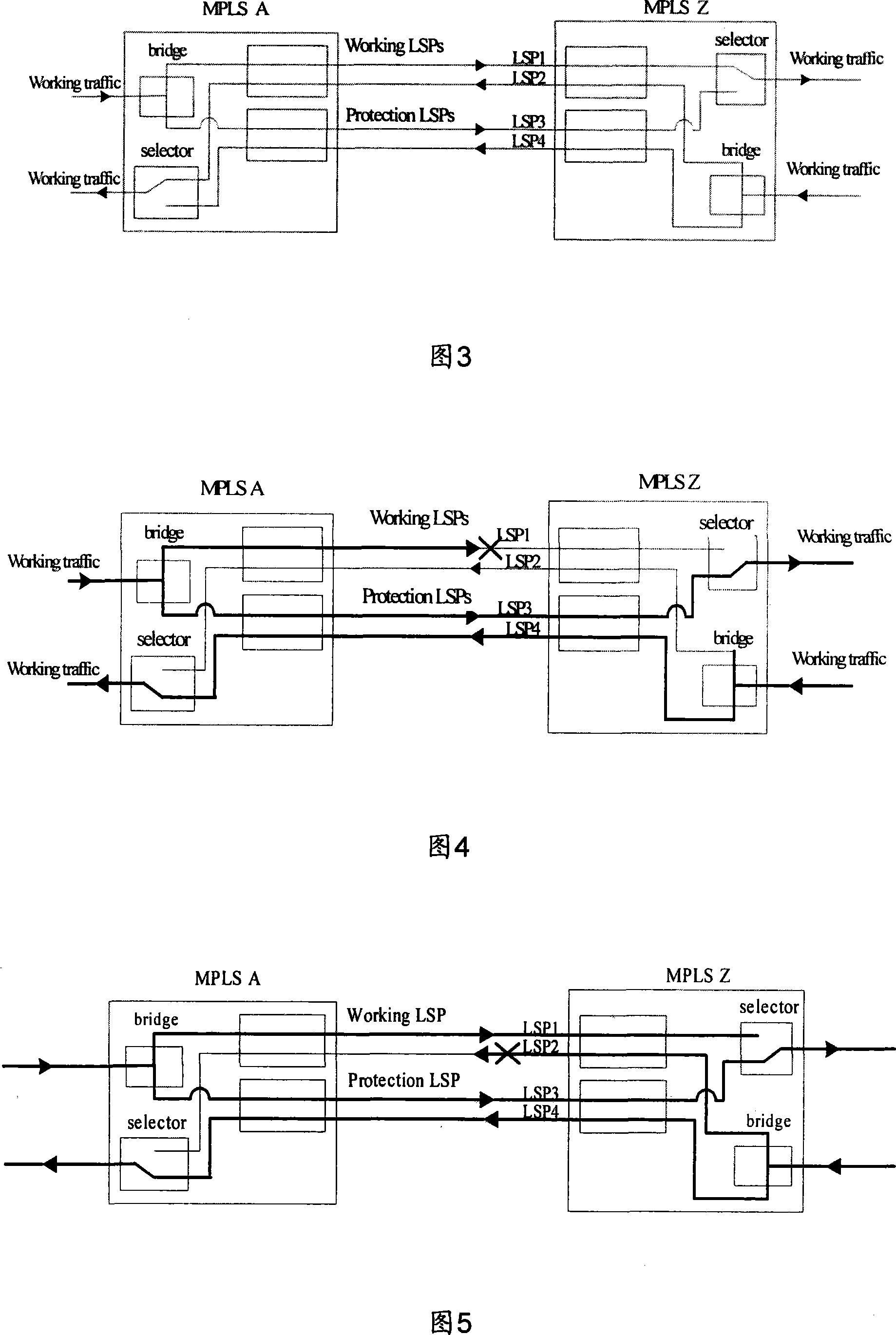
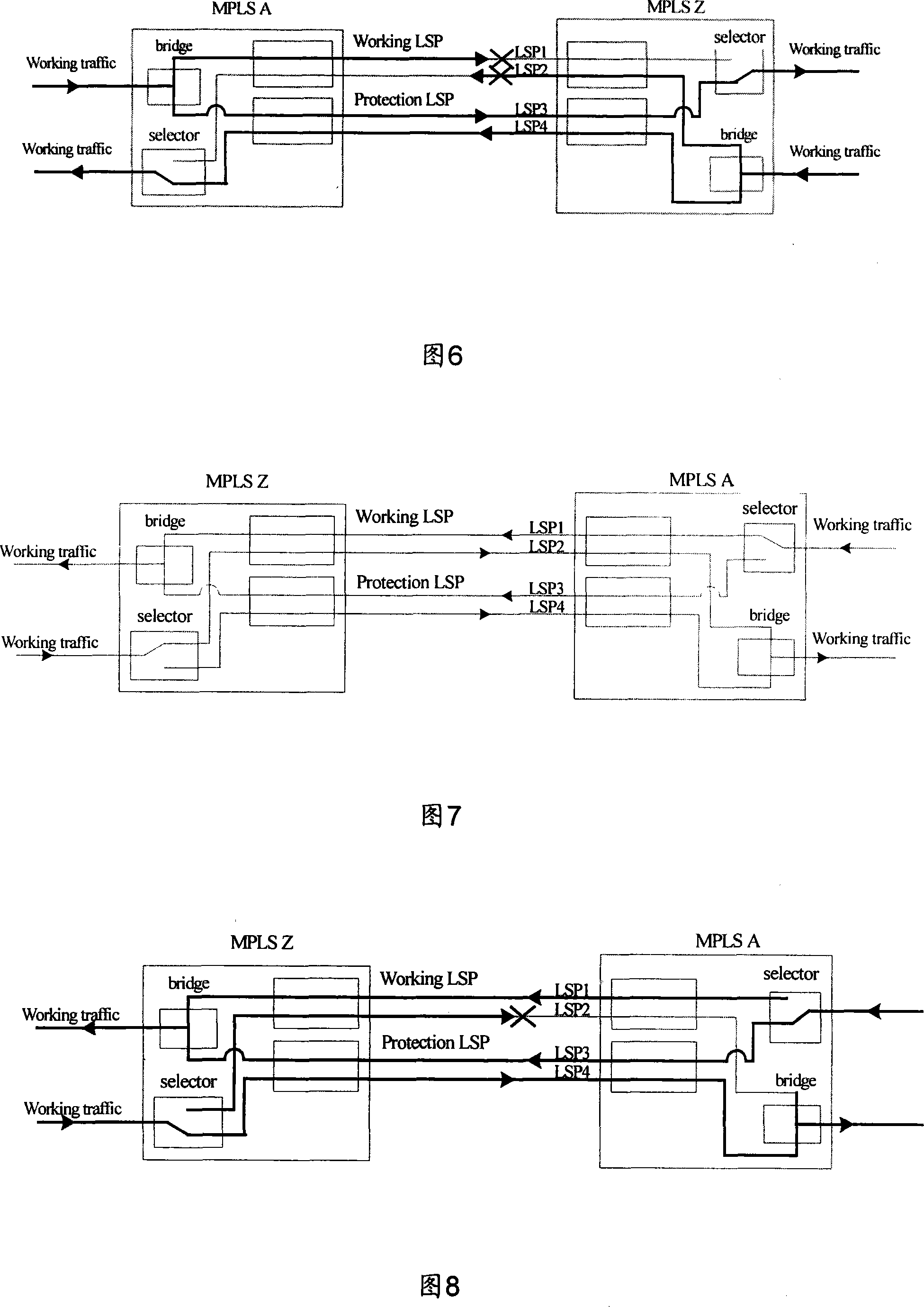
The invention relates to a method for realizing multi-protocol label switching bidirectional protection switching. The method mainly includes: first, in an MPLS (multiprotocol label switching) network, configure corresponding bidirectional protection switching policy information for a bidirectional LSP (label switching path) based on an APS (automatic protection switching) protocol; then, when in the MPLS network based on When the APS protocol determines that bidirectional protection switching is required, the bidirectional protection switching operation is performed according to the configured bidirectional protection switching policy information. Therefore, the present invention can realize effective protection to MPLS LSP two-way data channel, guarantees that the time delay of two-way flow is in equal; Simultaneously, the APS agreement that the present invention introduces can cover the protection of MPLS LSP one-way data channel, thereby unified one-way and The realization of the mechanism of two-way protection.
Owner:HUAWEI TECH CO LTD
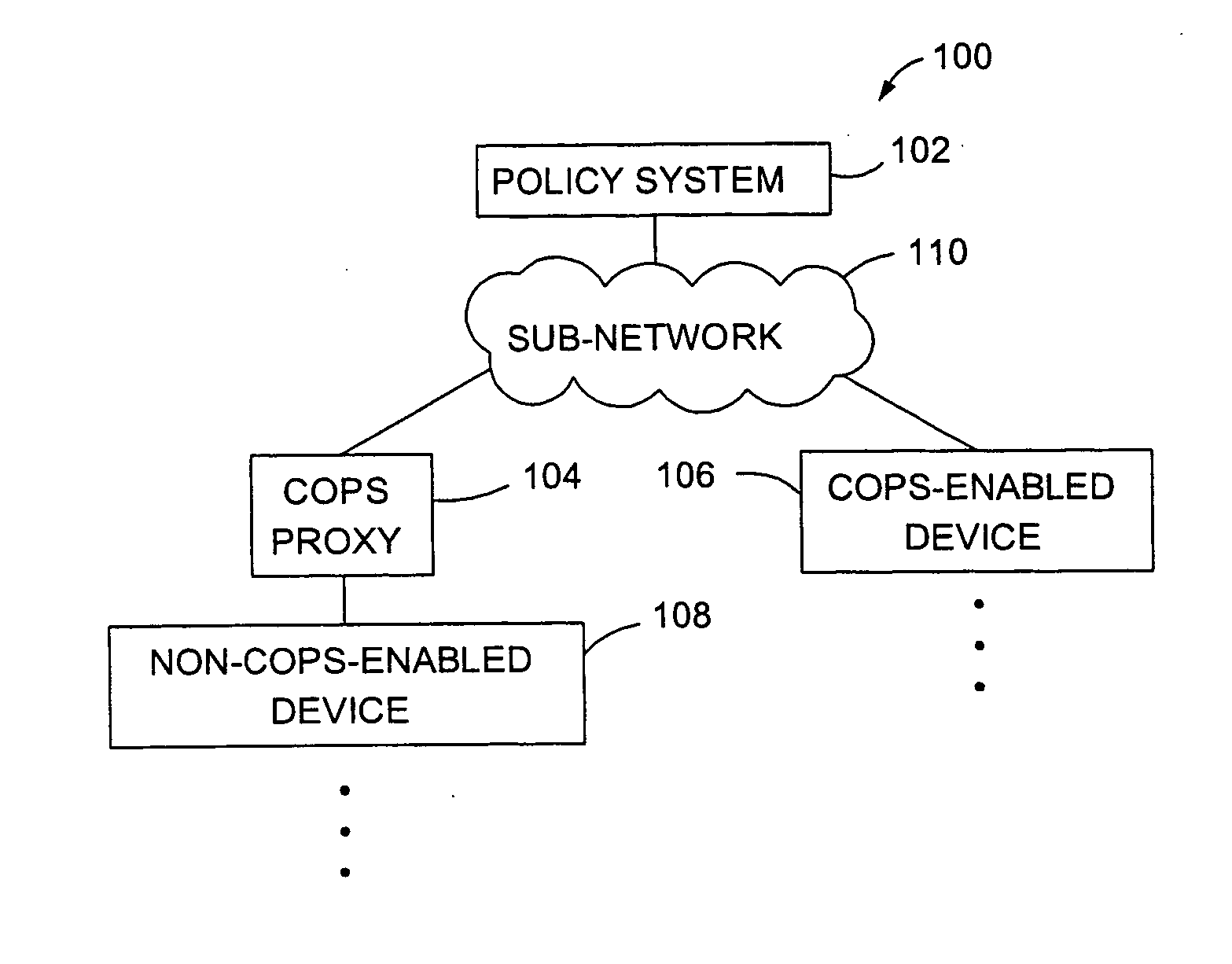
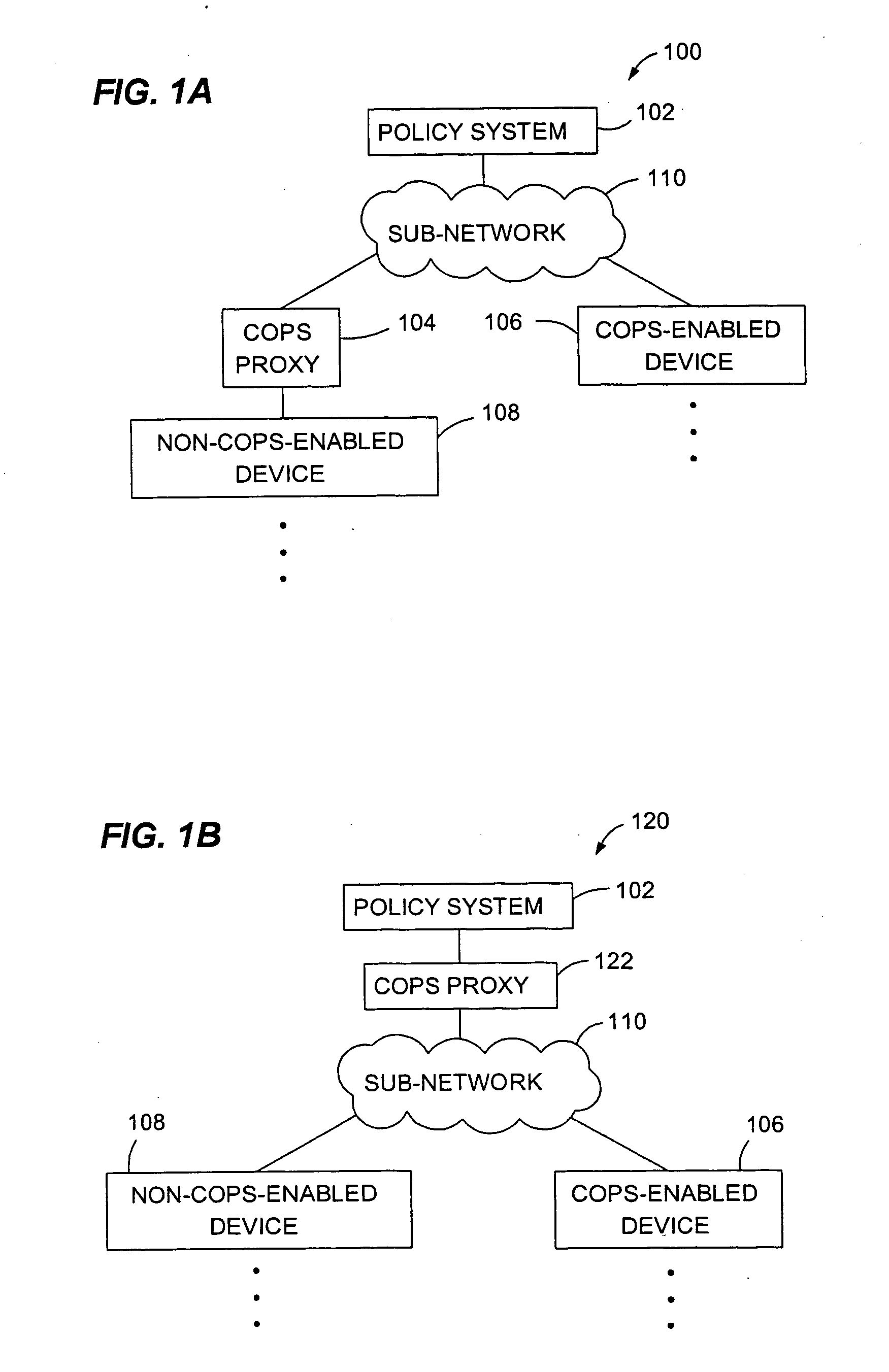
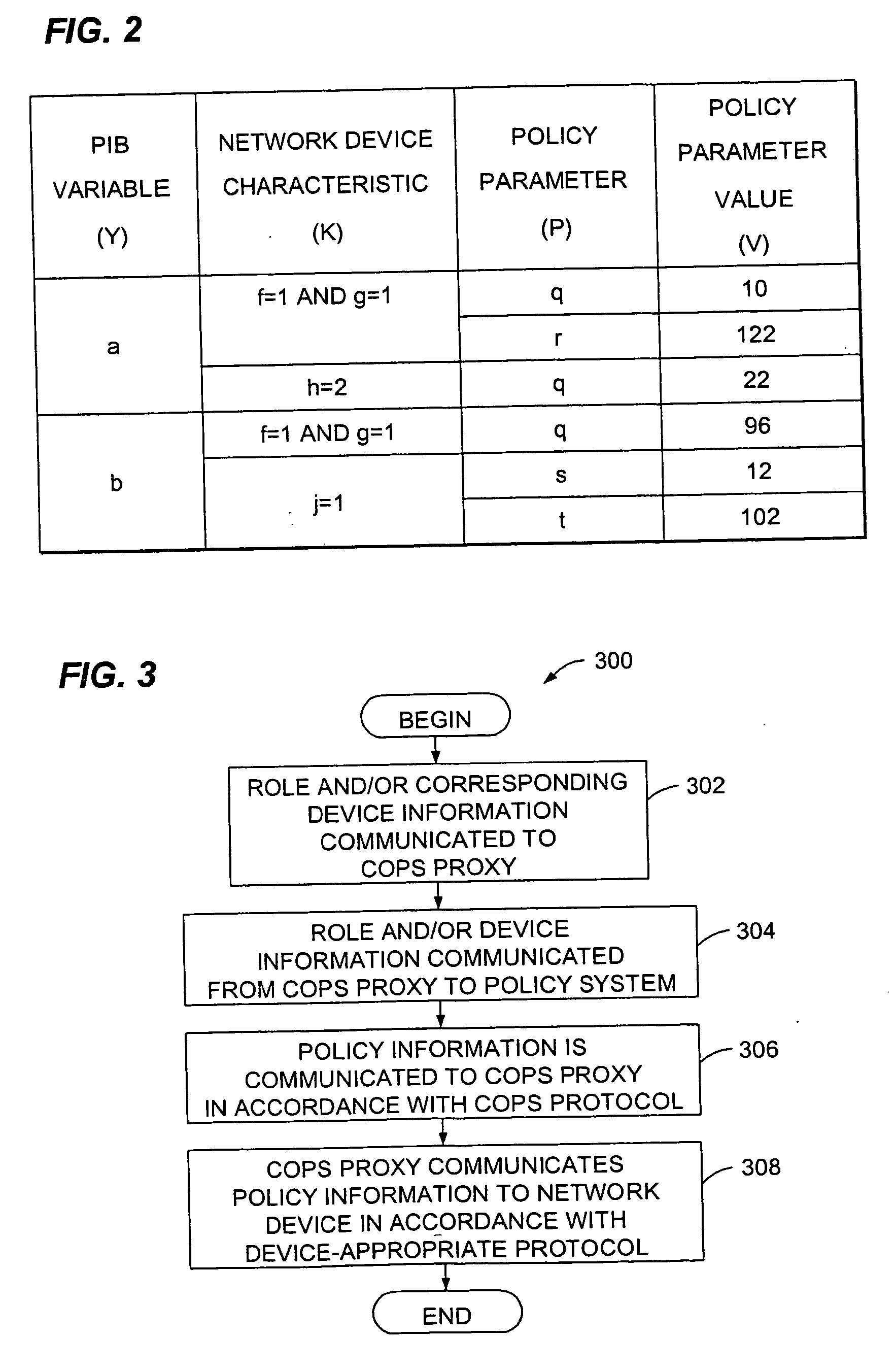
Method and apparatus for communicating COPS protocol policies to non-COPS-enabled network devices
InactiveUS20050060393A1Multiple digital computer combinationsData switching networksComputer networkProtocol for Carrying Authentication for Network Access
Owner:CISCO TECH INC
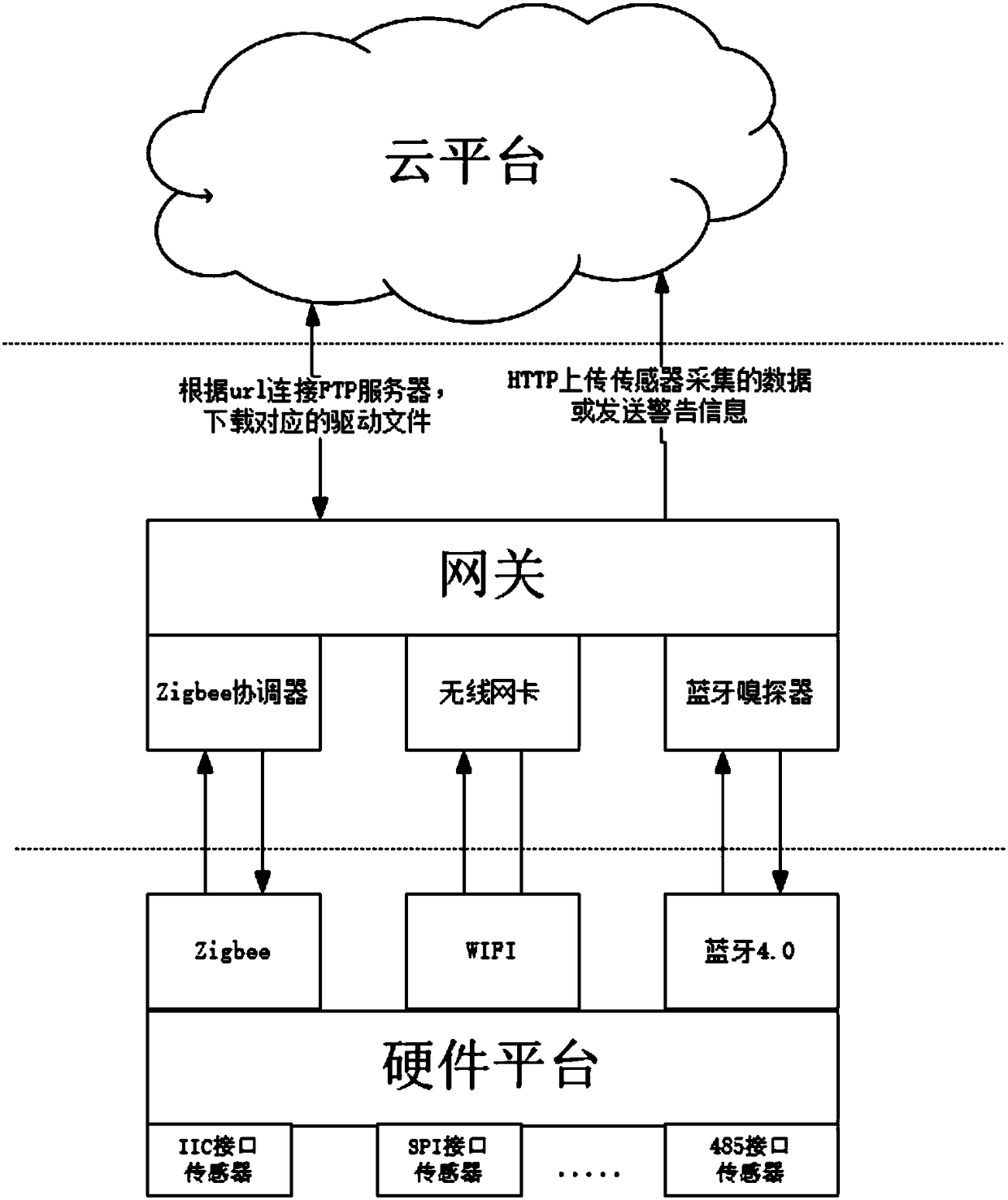
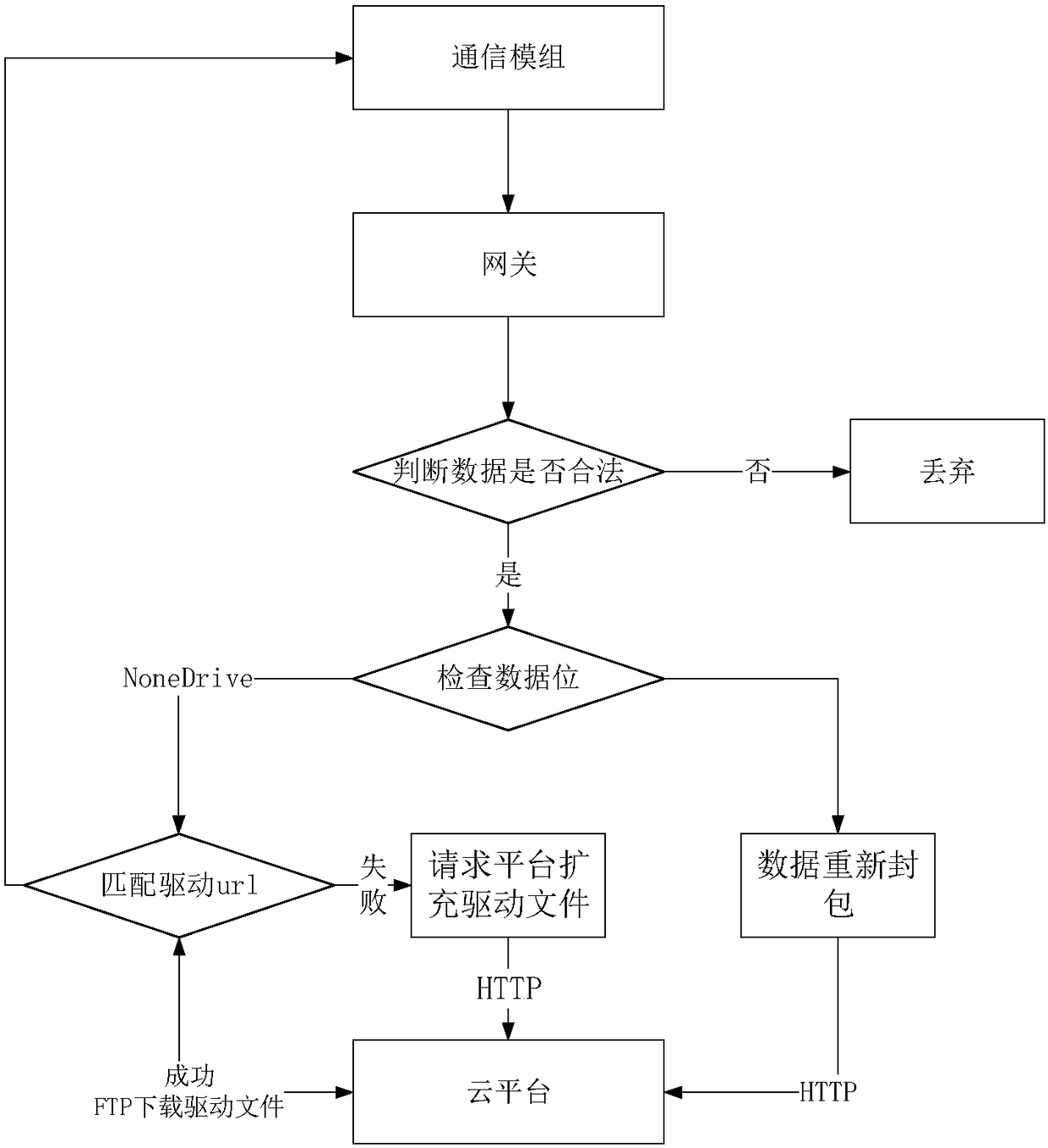
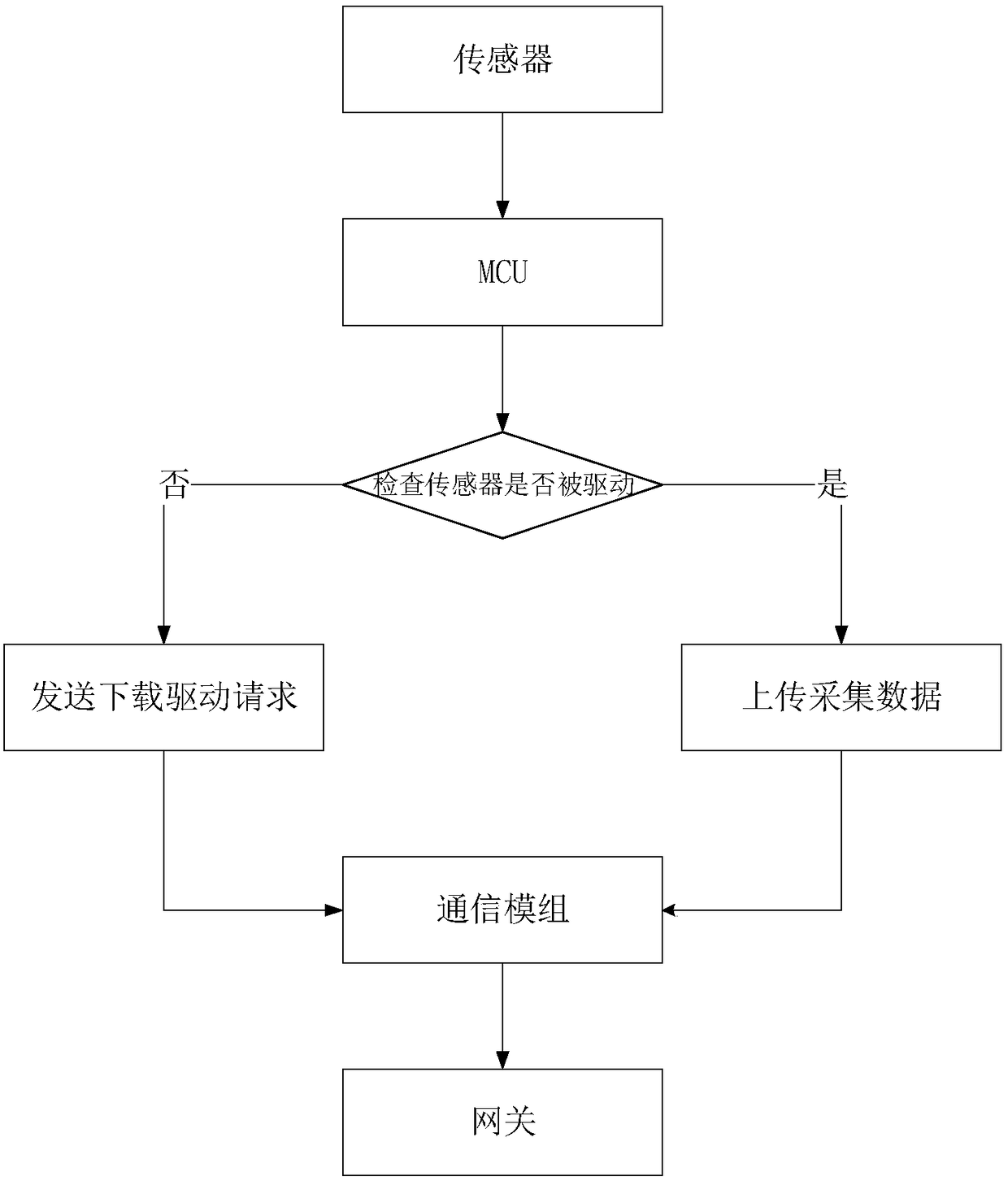
Automatic access control system for sensor based on Internet of things
InactiveCN108429786ARealize online downloadRealize plug and playTransmissionAutomatic controlControl system
The invention discloses an automatic access control system for a sensor based on Internet of things, comprising: a cloud platform configured to establish a driver file library, synchronously send a url corresponding to each driver file to a gateway, carry an FTP server, and store the sensor data uploaded by the gateway; a hardware platform configured to detect whether the sensor is driven, uploadthe acquired sensor data or generate a driver file acquisition request and upload the request, and receive and store the driver file; a gateway including a driver url library and configured to store the url corresponding to each driver file; and a policy information base configured to parse and judge that the uploaded data is a driver file acquisition request or sensor data, obtain corresponding url according to the identity information match in the request, receive the driver file and deliver the same to the hardware platform, or extract and upload the sensor data after encapsulation. The invention realizes the plug and play of the sensor, reduces the difficulty of the sensor accessing the platform, and improves the development efficiency.
Owner:NANJING UNIV OF POSTS & TELECOMM
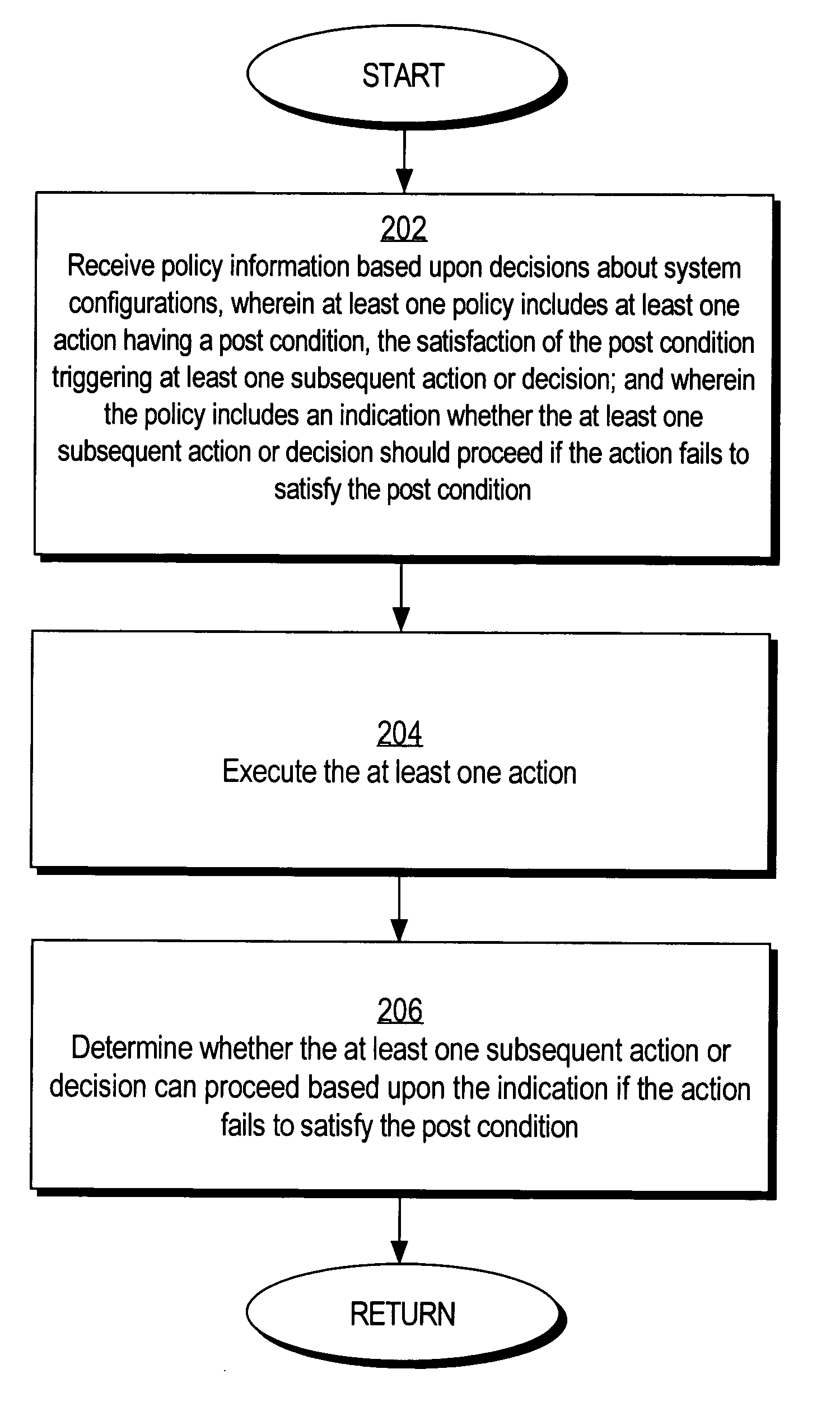
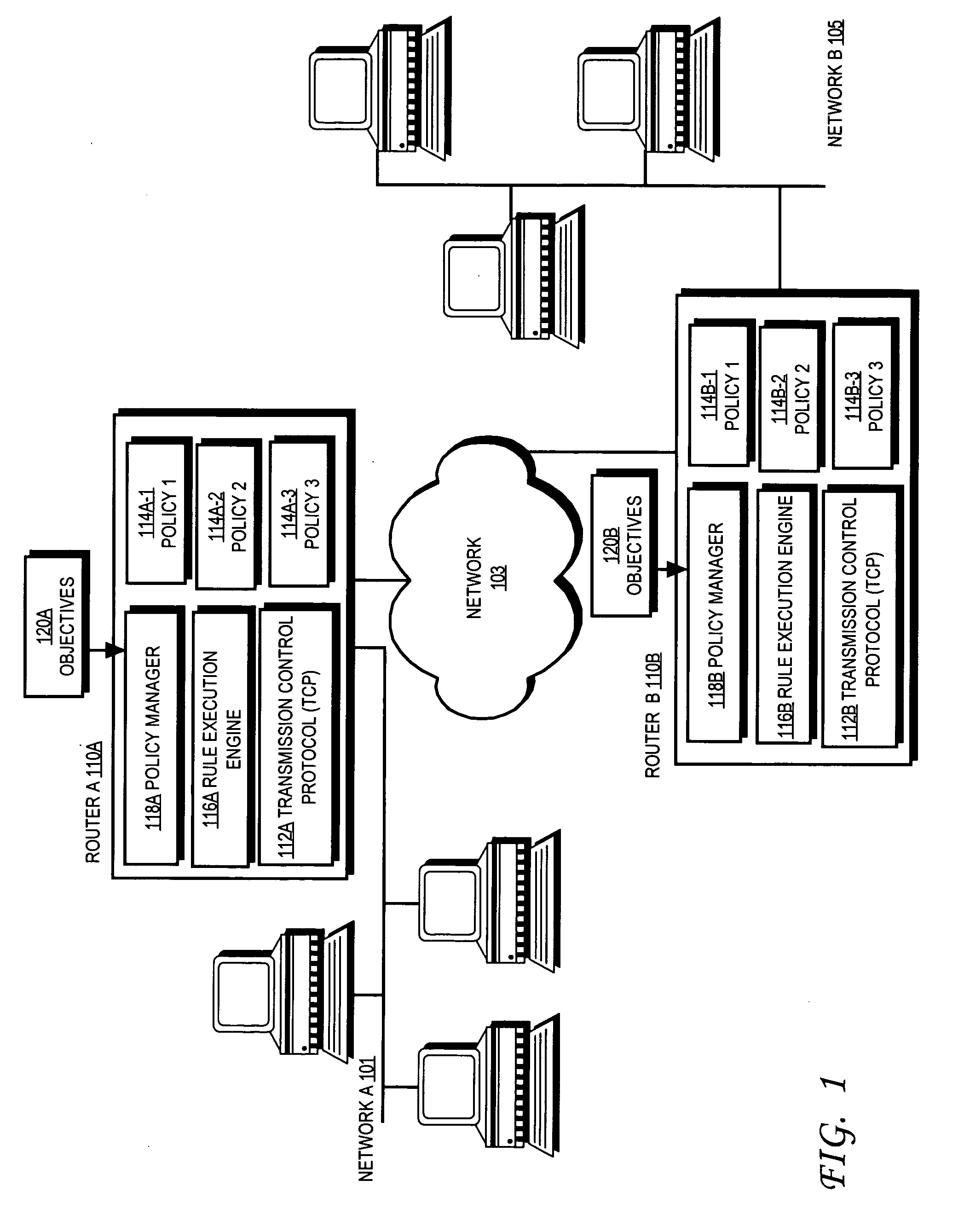
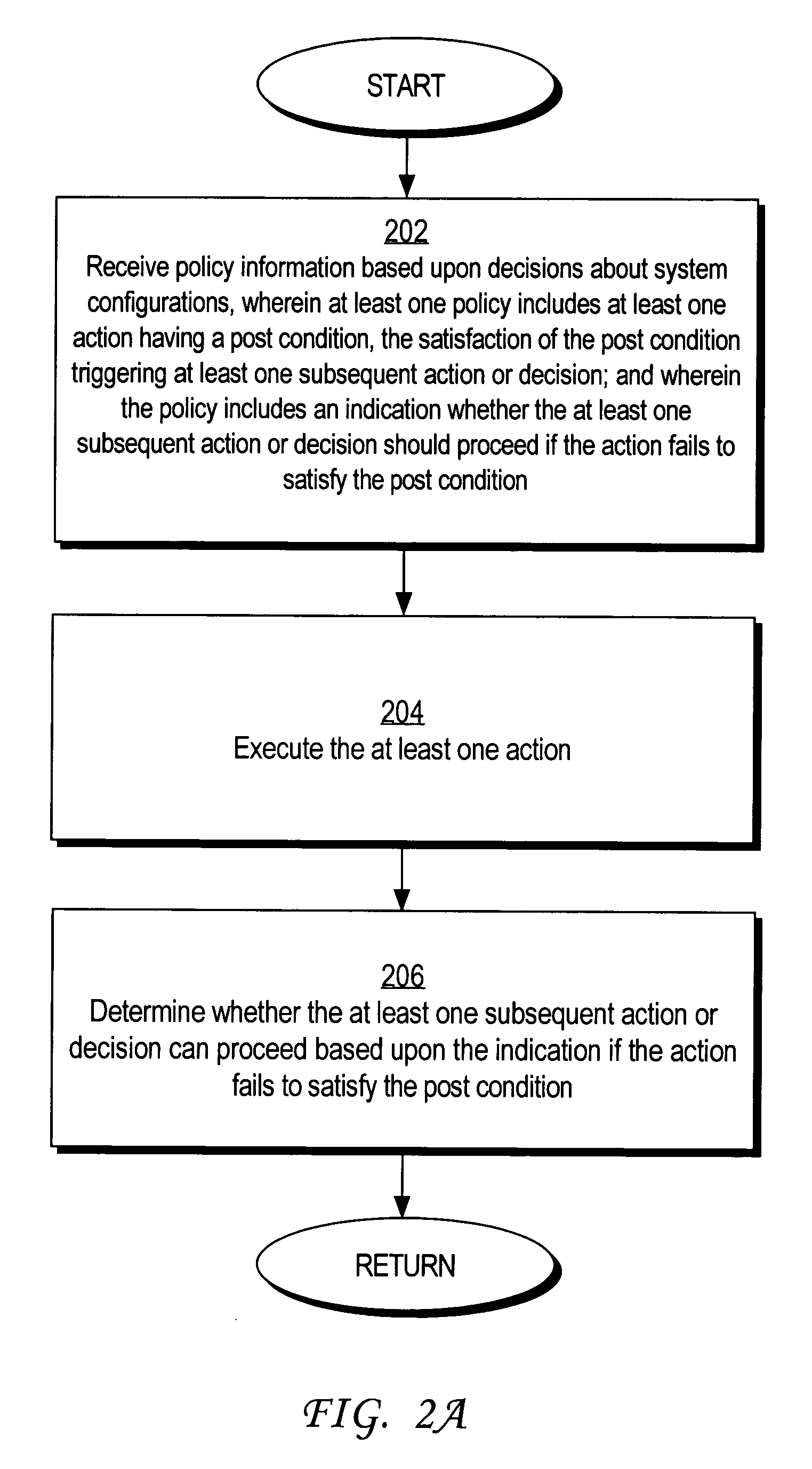
Preventing deadlock in a policy-based computer system
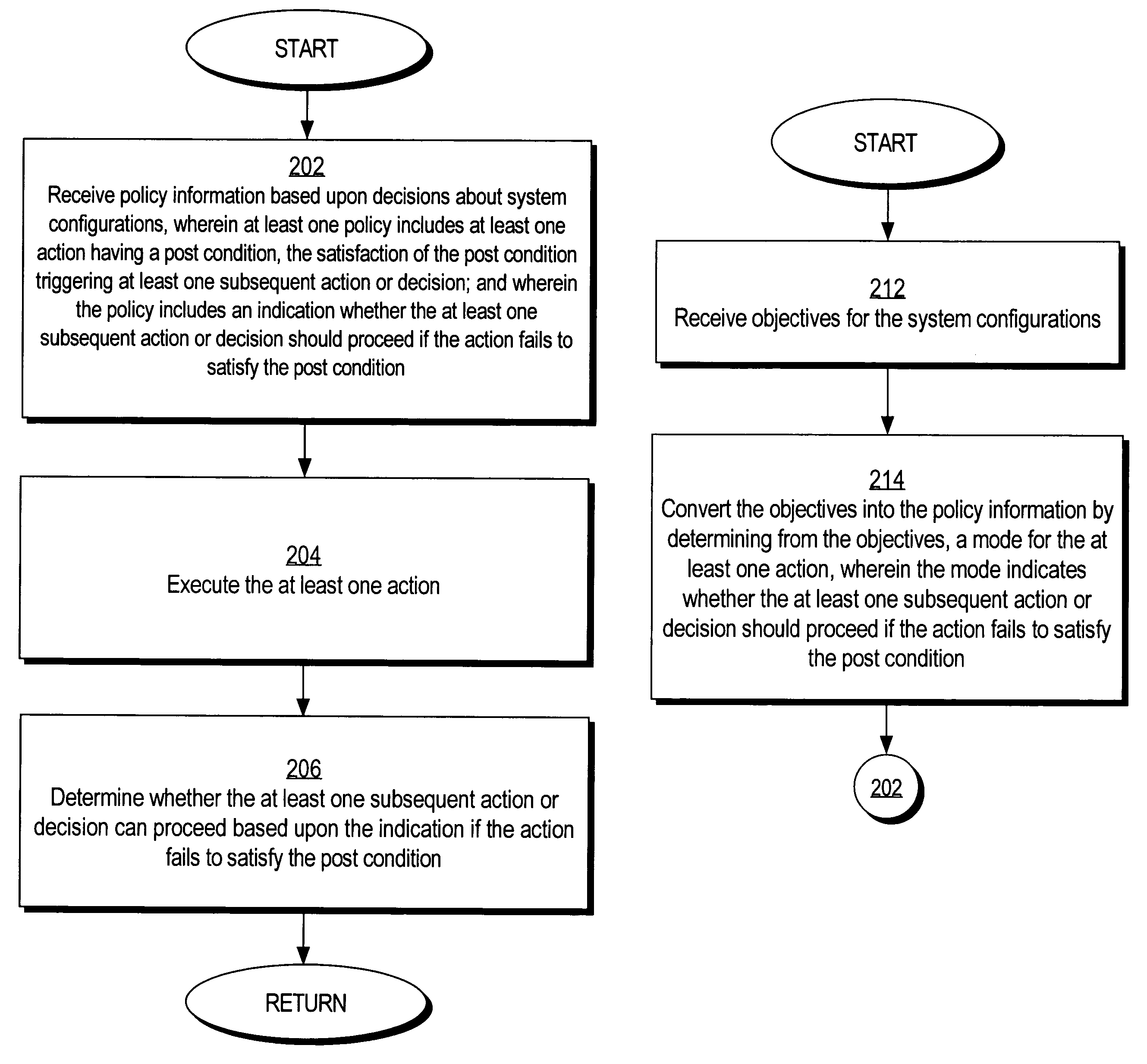
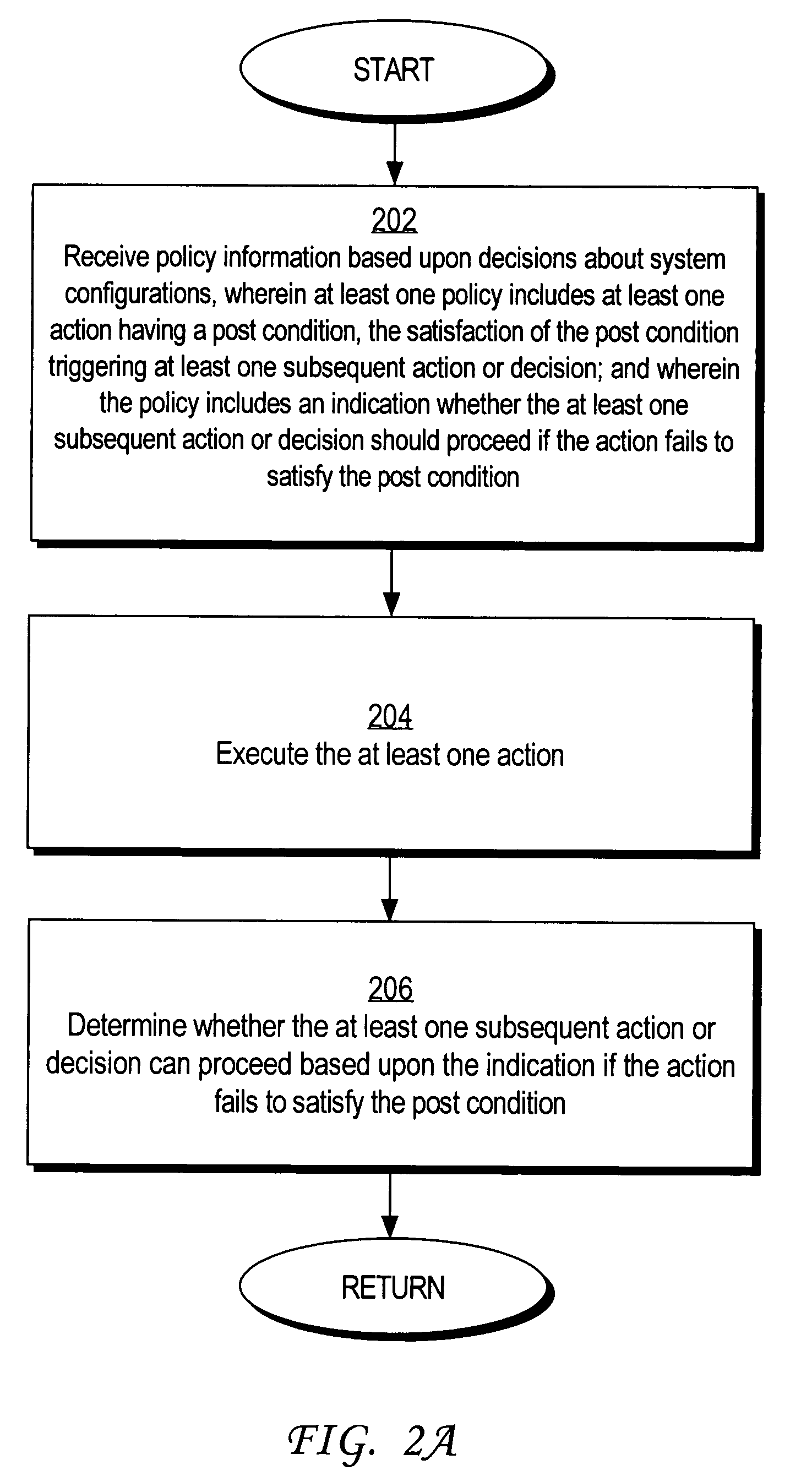
Methods and mechanisms for preventing deadlock in a policy-based computer system are disclosed. In one embodiment, the method includes various machine-implemented steps, such as a step of receiving policy information based upon decisions about system configurations. At least one policy includes at least one action that has a post condition. Satisfaction of the post condition triggers at least one subsequent action or decision. The policy includes an indication whether the at least one subsequent action or decision should proceed if the action fails to satisfy the post condition. The at least one action is executed. Then, if the action fails to satisfy the post condition, a determination is made whether the at least one subsequent action or decision can proceed based upon the indication.
Owner:CISCO TECH INC
Communication method and device, and system
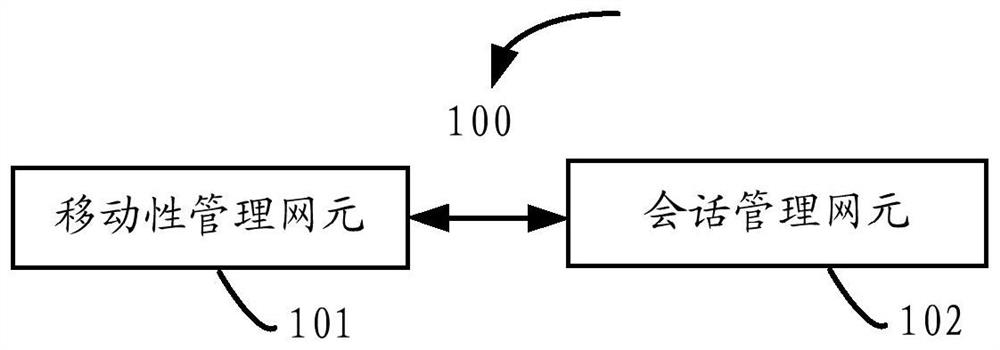
The invention provides a communication method and device, and a system, which can improve the admission control capability of a network side to terminal behaviors. The method comprises the following steps: a mobility management network element receives a first session request message from a terminal; wherein the first session request message carries user routing selection strategy URSP identification information. Then, the mobility management network element acquires URSP policy information based on the URSP identification information. Then, the mobility management network element sends a second session request message to the session management network element. Wherein the second session request message carries URSP policy information, and the URSP policy information is used for making a policy rule for the terminal.
Owner:HUAWEI TECH CO LTD
Conflict detection system and method for computer network defense (CND) policy
InactiveCN103049700AImprove versatilityStrong scalabilityPlatform integrity maintainanceInformation repositoryInternet privacy
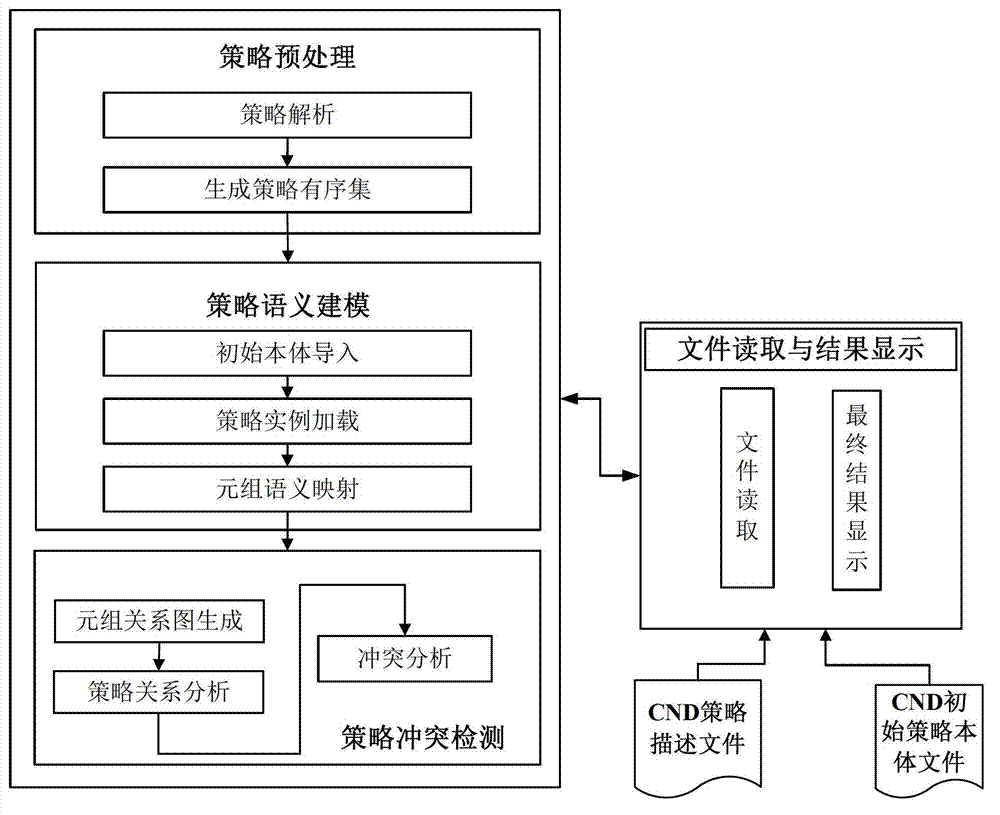
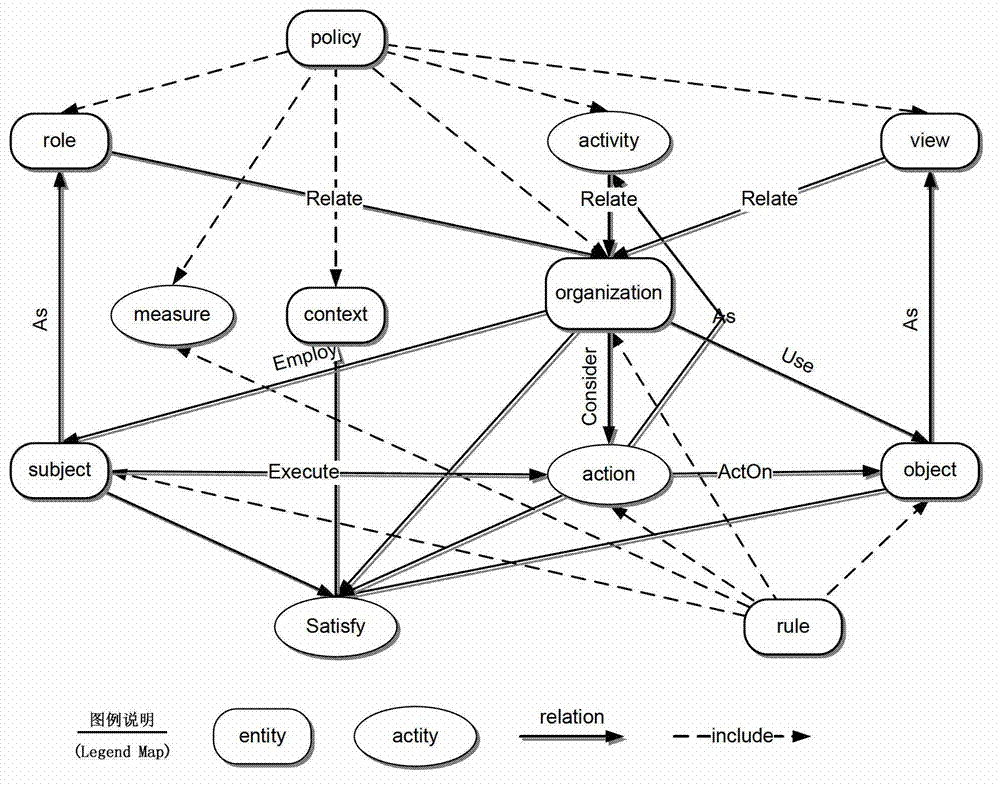
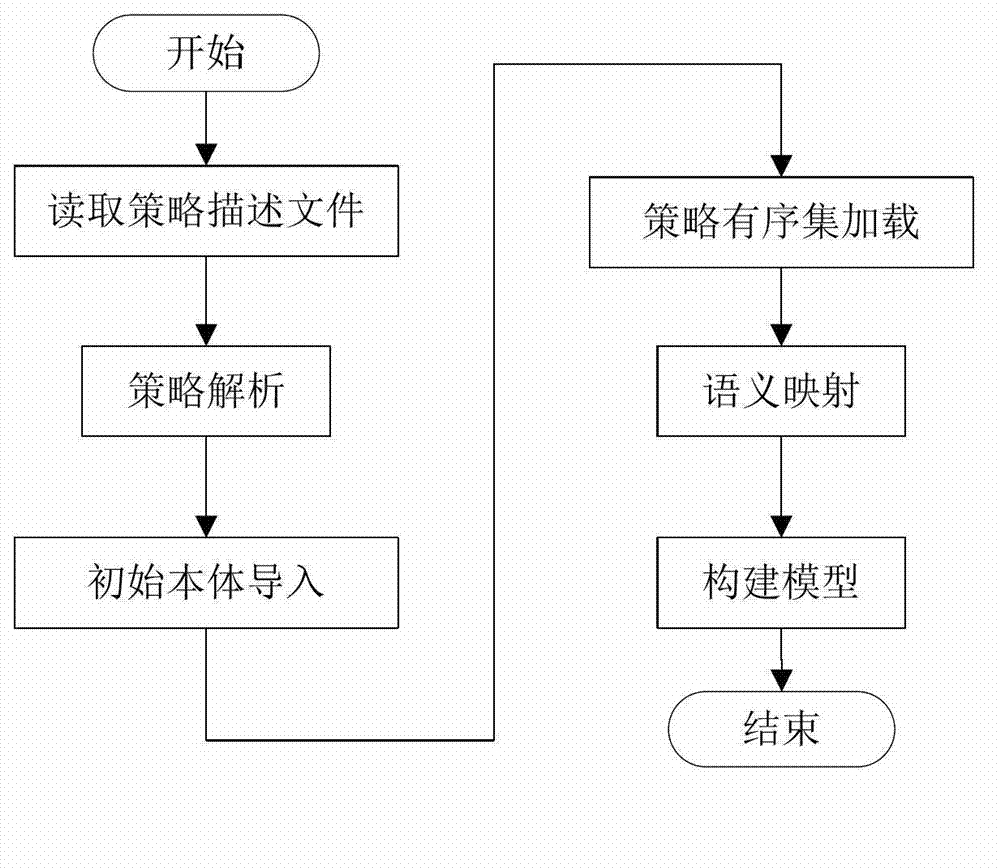
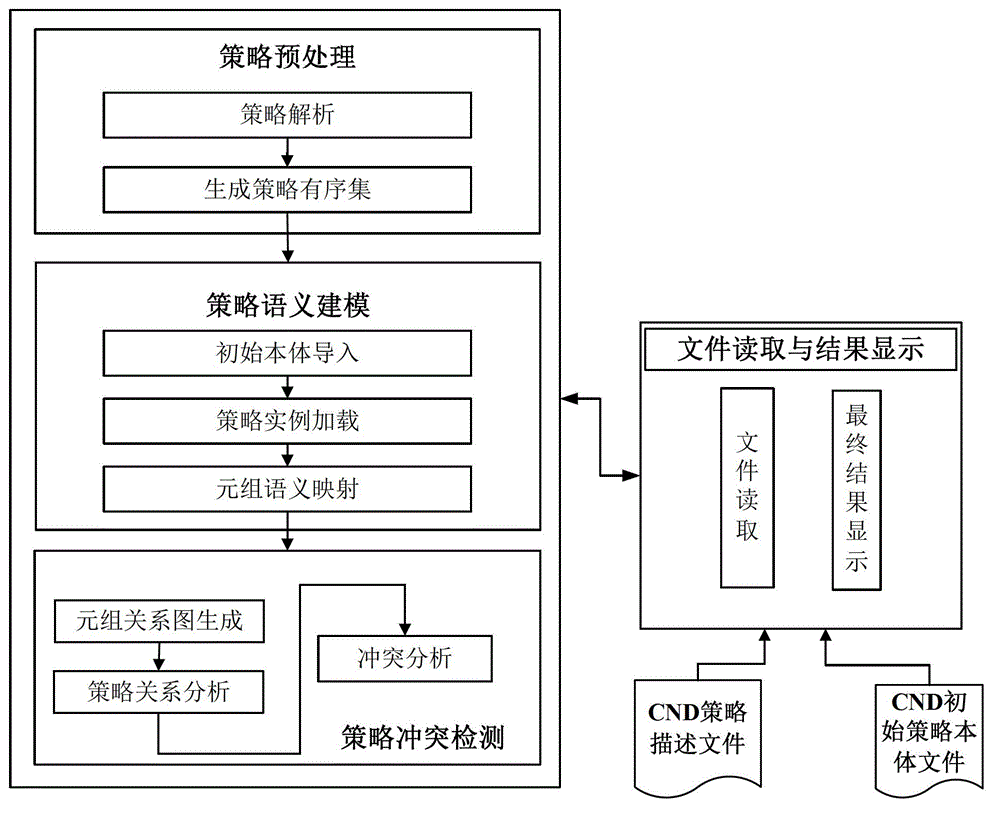
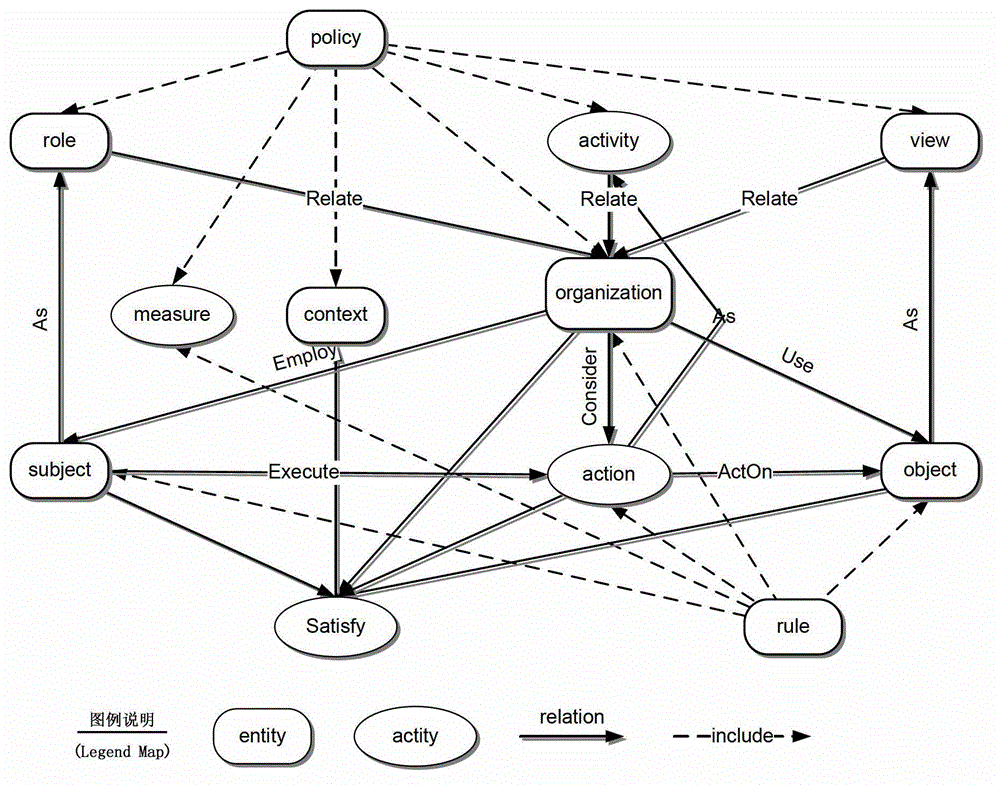
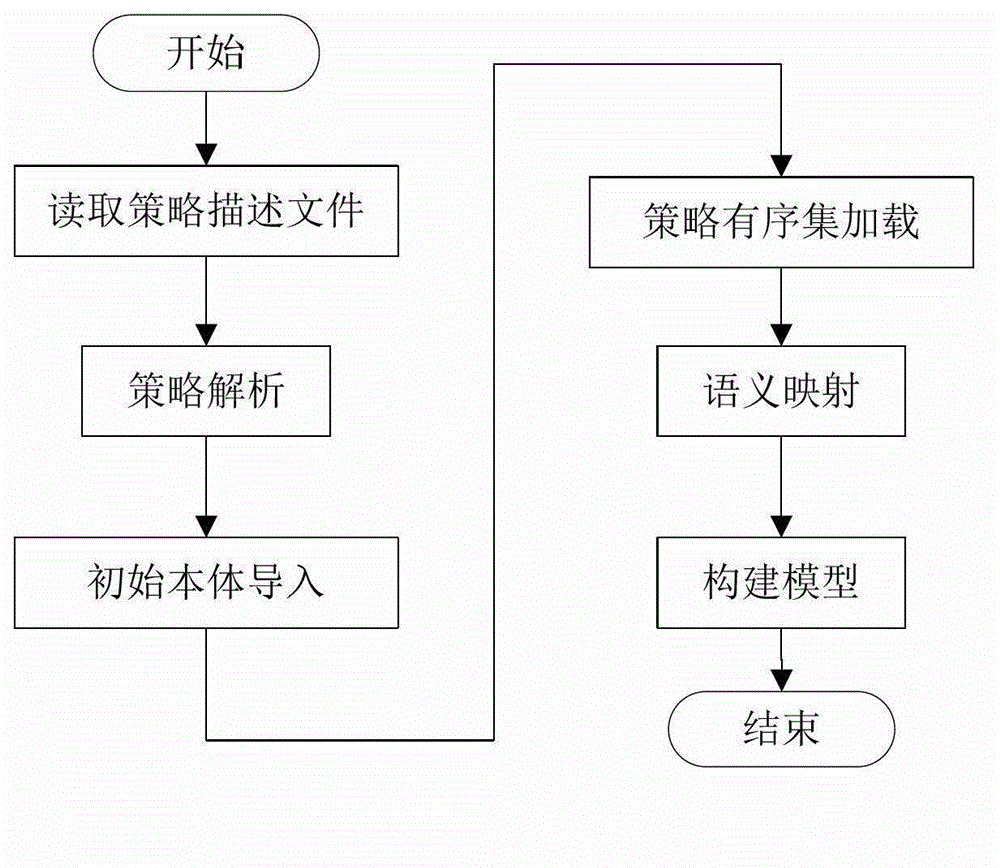
The invention relates to a conflict detection system and method for a computer network defense (CND) policy. According to the method, a CND policy description file is read and parsed by using a morphology parser and a grammar parser; an initial policy body is artificially constructed by using a body modeling tool, only comprises concepts for policy tuples in a CND policy and the relationship among the concepts, and does not include policy examples and the relationship among the policy examples; a local policy body including the policy examples is generated according to the initial policy body and a loaded and parsed policy ordered set, a semantic inclusion relationship among the tuples is then obtained according to the semantic mapping of the policy tuples in a defense policy information base, and a CND policy semantic model is constructed based on the semantic inclusion relationship; a relational diagram for all the tuples of the policy is constructed and traversed, and the relationship among the policy tuples is obtained through analysis; and through the measure of tuple comparison, the policy conflict analysis is completed, and the objects, types and reasons for conflict generation are finally provided by algorithms in the form of conflict reports. According to the system and the method, conflicts can be more effectively detected, security problems, such as unauthorized access and the like, are prevented from easily occurring, and the security of a computer network system is greatly improved.
Owner:BEIHANG UNIV
Application service system based on big data platform
InactiveCN108288244AIncrease awarenessReal-time queryData processing applicationsInformation repositoryData platform
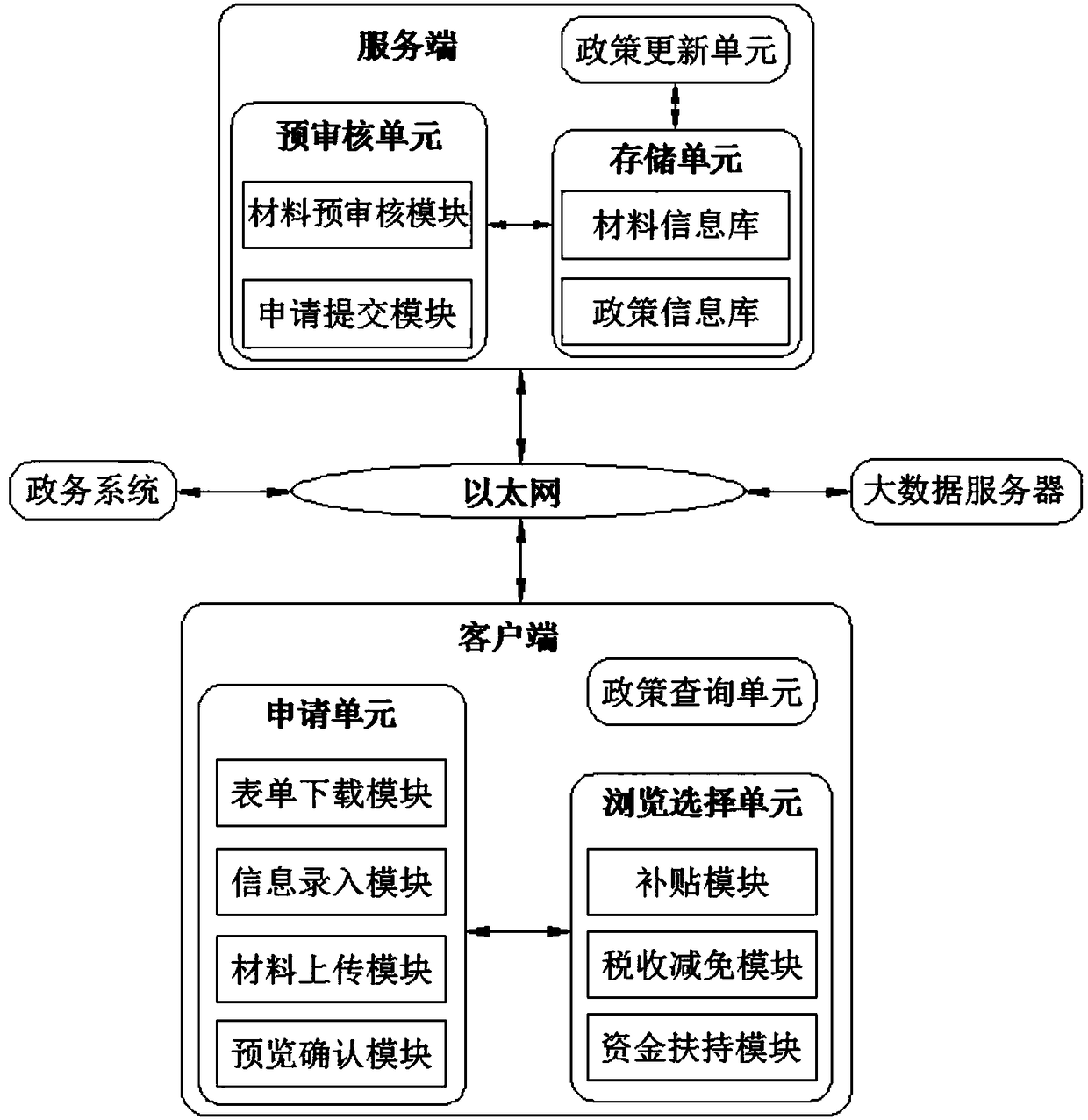
The present invention discloses an application service system based on a big data platform, and relates to the technical field of big data platform application service systems. The application servicesystem comprises a client, a server, a big data server, and a government affair system. The client communicates with the server through Ethernet; the server communicates with the big data server andthe government affair system through Ethernet; the client comprises an application unit, a policy query unit, and a browsing unit; the server comprises a policy updating unit, a storage unit, and a pre-auditing unit; the pre-auditing unit comprises a material pre-auditing module and an application submitting module; and the storage unit comprises a material information database and a policy information database. According to the application service system disclosed by the present invention, by setting an order downloading module, an information input module, a material uploading module, and apreview confirmation module in an application unit on the client, and by setting a material pre-auditing module and an application submitting module in a pre-auditing unit on the server, the failure of the company declaration is avoided, and application efficiency and a declaration success rate are improved.
Owner:合肥和钧正策信息技术有限公司
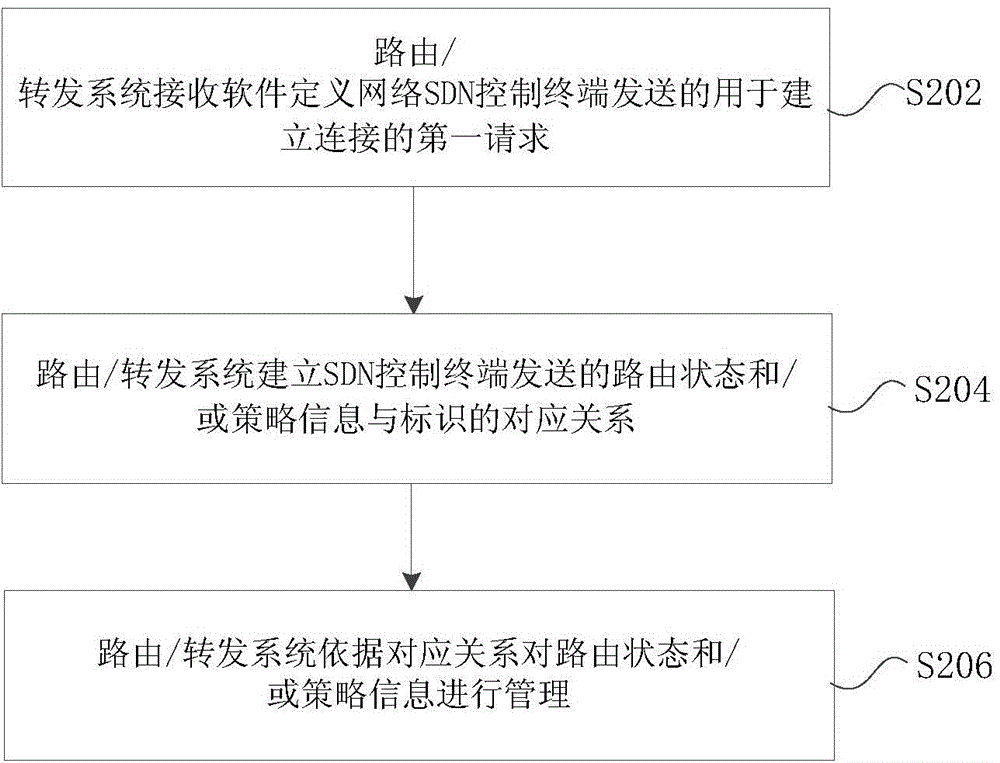
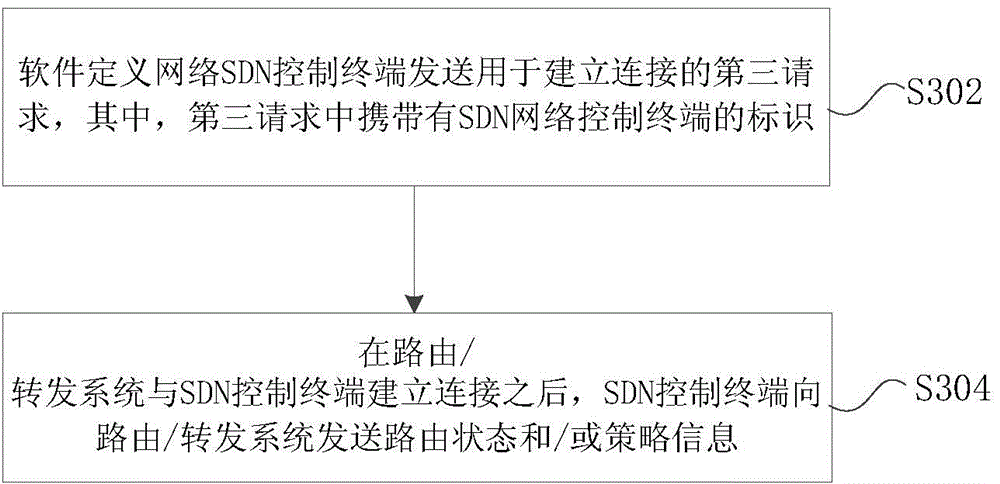
Processing method and apparatus of routing status and/or policy information
ActiveCN105871719APrecise managementResolution statusData switching networksComputer scienceDistributed computing
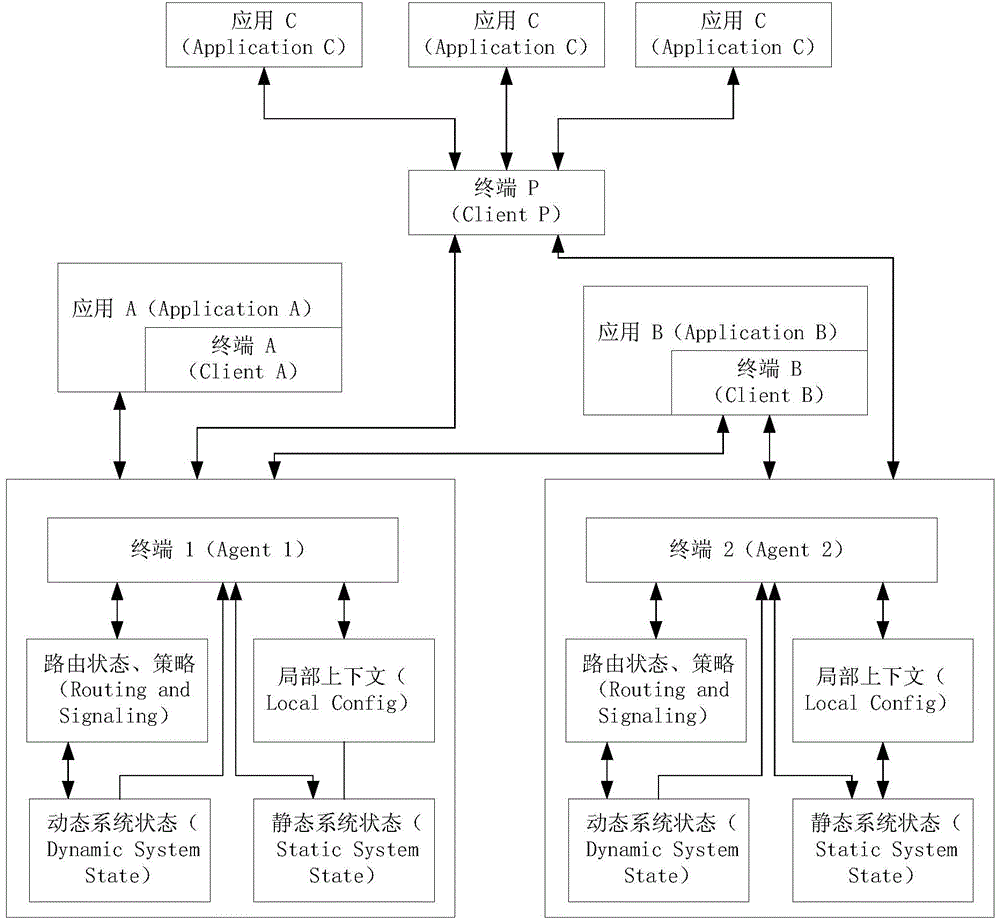
The invention provides a processing method and apparatus of routing status and / or policy information. The method includes the following steps that: a routing / forwarding system receives first requests for establishing connections which are sent by software defined networking (SDN) control terminals, wherein the first requests carries the identifiers of the SDN control terminals; the routing / forwarding system establishes corresponding relationships between routing status and / or policy information sent by the SDN control terminals and the identifiers of the SDN control terminals; and the routing / forwarding system manages the routing status and / or policy information based on the corresponding relationships. With the processing method and apparatus of the invention adopted, the problem that attribution control terminals of the routing status and / or policy information are not distinguished in the prior art can be solved, and accurate management of the routing status and / or policy information can be realized.
Owner:ZTE CORP
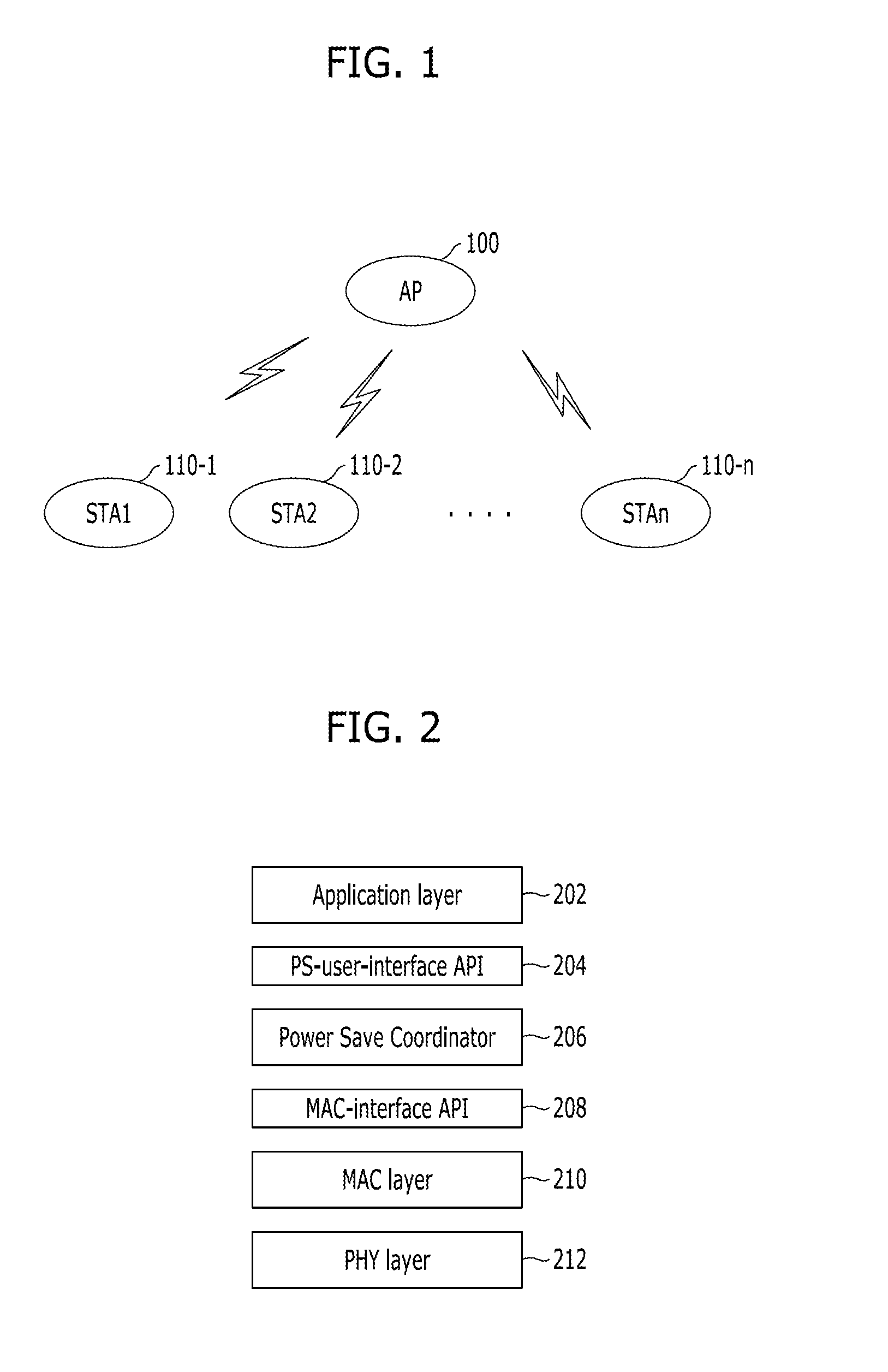
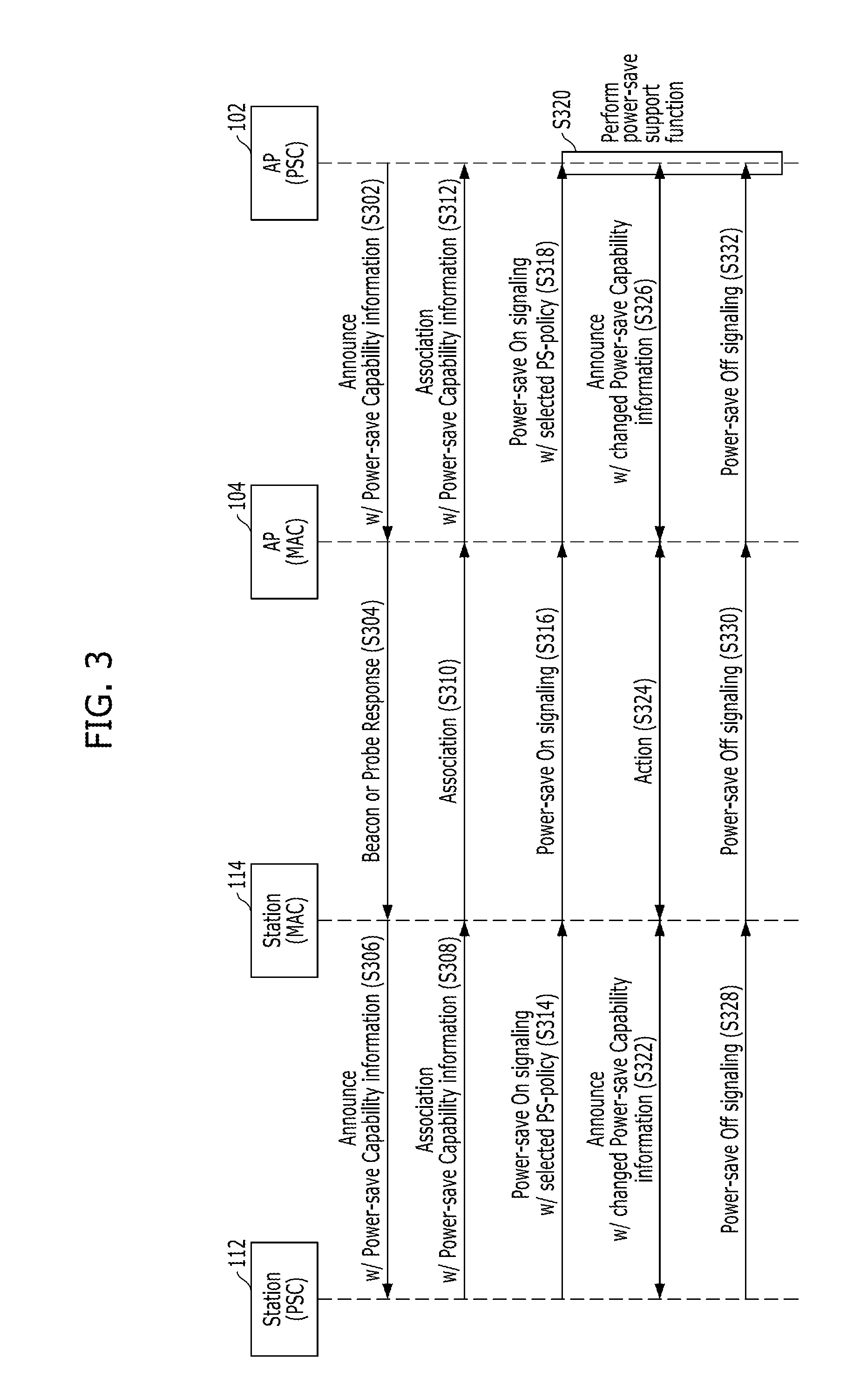
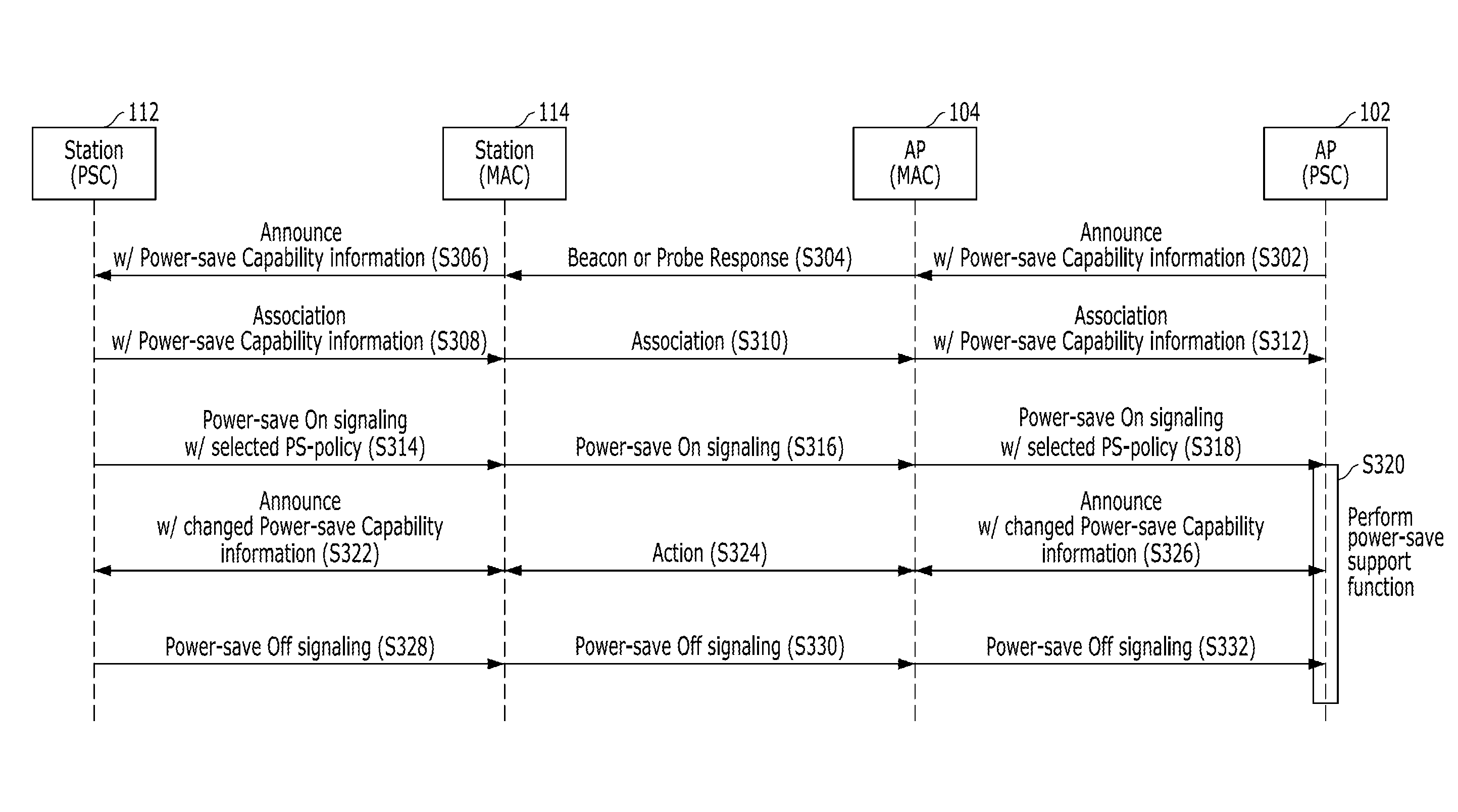
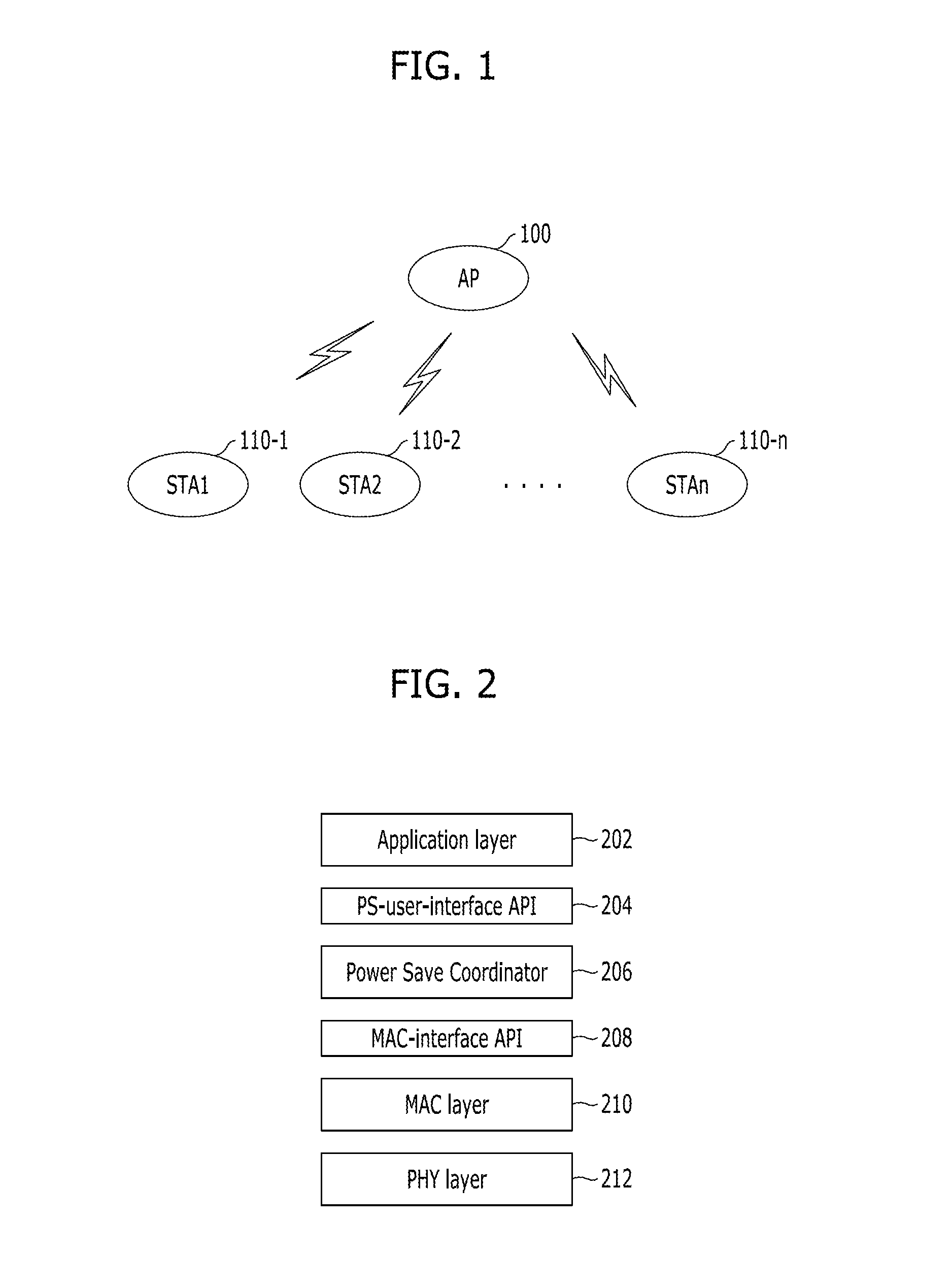
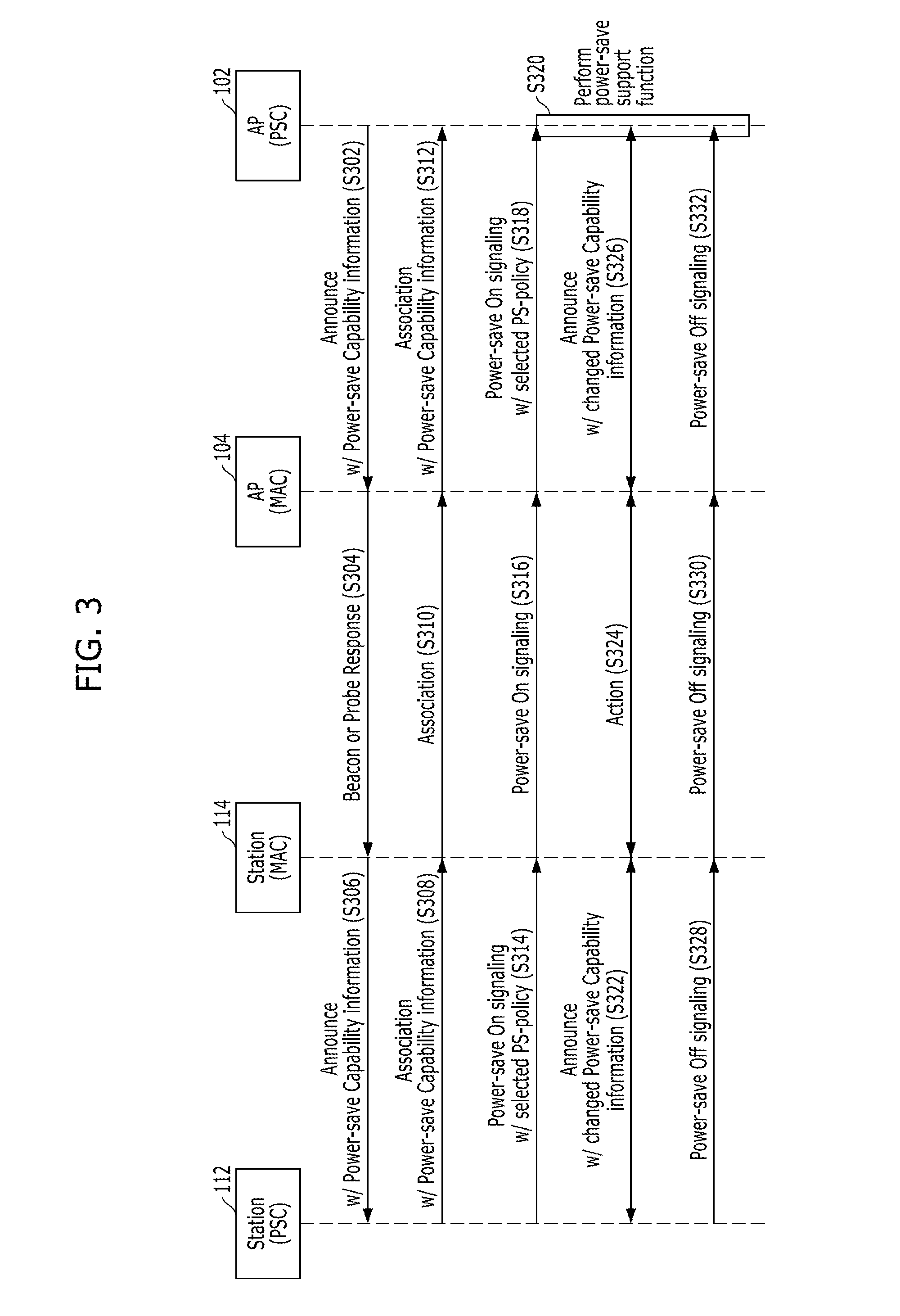
Adaptive power-saving/power-saving support method in wireless communication system and apparatus using the same
A method for adaptively performing power saving in a station of a wireless communication system includes: receiving first power-save capability information from an AP, the first power-save capability information containing information on power-save schemes supported by a MAC layer of the AP; transmitting second power-save capability information to the AP in response to the first power-save capability information, the second power-save capability information containing information on power-save schemes supported by a MAC layer of the station; transmitting power-save policy information, into which properties of traffics used in the station are reflected, to the AP; and performing a power-save function while interworking with the MAC layer of the station, according to the power-save policy information based on a predetermined power-save scheme.
Owner:ELECTRONICS & TELECOMM RES INST
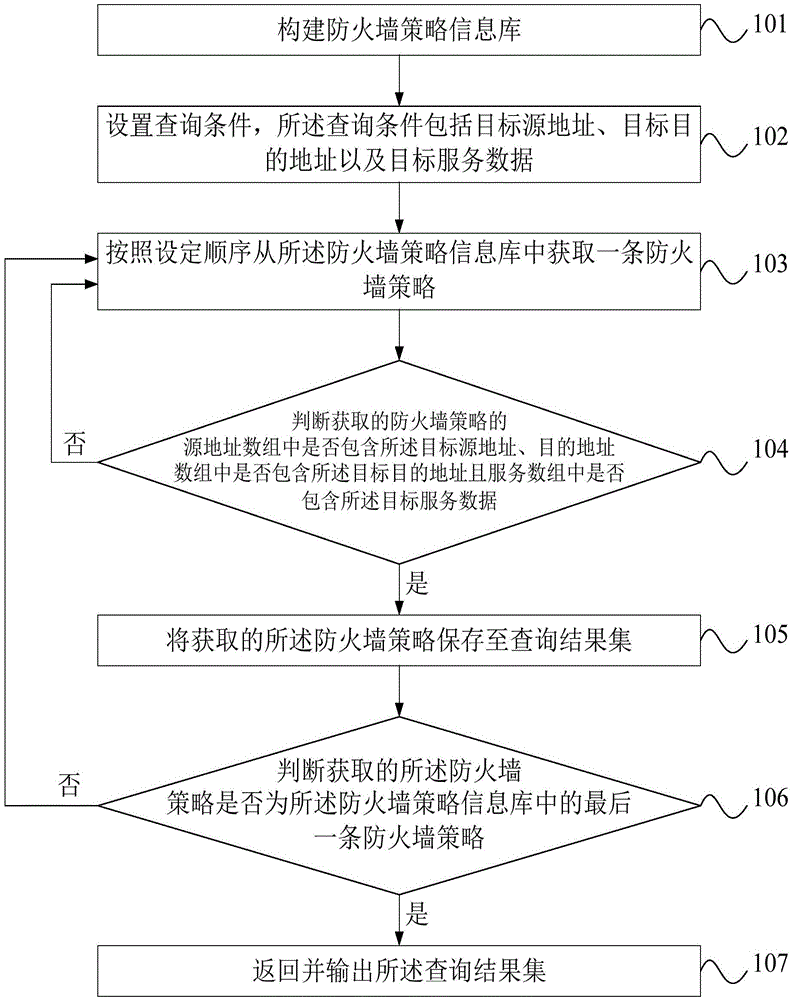
Automatic query method and system for firewall policy
ActiveCN105681327AImprove management efficiencyReduce workloadTransmissionInformation repositoryArray data structure
The invention discloses an automatic query method and system for a firewall policy. The method comprises the following steps: step S1, constructing a firewall policy information base; step S2, setting query conditions, including a target source address, a target destination address and target service data; step S3, acquiring one firewall policy from the firewall policy information base; step S4, judging whether a source address array, a target address array and a service array of the acquired firewall policy respectively include the target source address, the target destination address and the target service data, if so, then executing step S5, and if not, then returning to step S3; step S5, conserving the acquired firewall policy to a query result set; step S6, judging whether the acquired firewall policy is the last one in the firewall policy information base, if so, then executing step S7, and if not, then returning to step S3; and step S7, outputting the query result set. The automatic query method and system for the firewall policy provided by the invention can realize the concentrated and unified management of the firewall policy, and improve the efficiency of firewall policy query.
Owner:SHANGHAI CTRIP COMMERCE CO LTD
Dynamic service activation using cops-pr to support outsourcing and configuration models for policy control
ActiveUS20100205288A1Service provisioningMultiple digital computer combinationsInformation repositoryCommon Open Policy Service
A device may include a service activation engine (SAE) including: a policy information base (PIB) file that defines a plurality of attachments that correspond to a plurality of network policies; and a server. The server may receive a request, using common open policy service for policy provisioning (COPS-PR), for a network service related to an interface handle associated with a subscriber device; determine which ones of the network policies correspond to the network service; and send, using COPS-PR, a provisioning instance (PRI) including a first of the attachments to implement the ones of the network policies to the interface handle based on the attachments.
Owner:JUMIPER NETWORKS INC
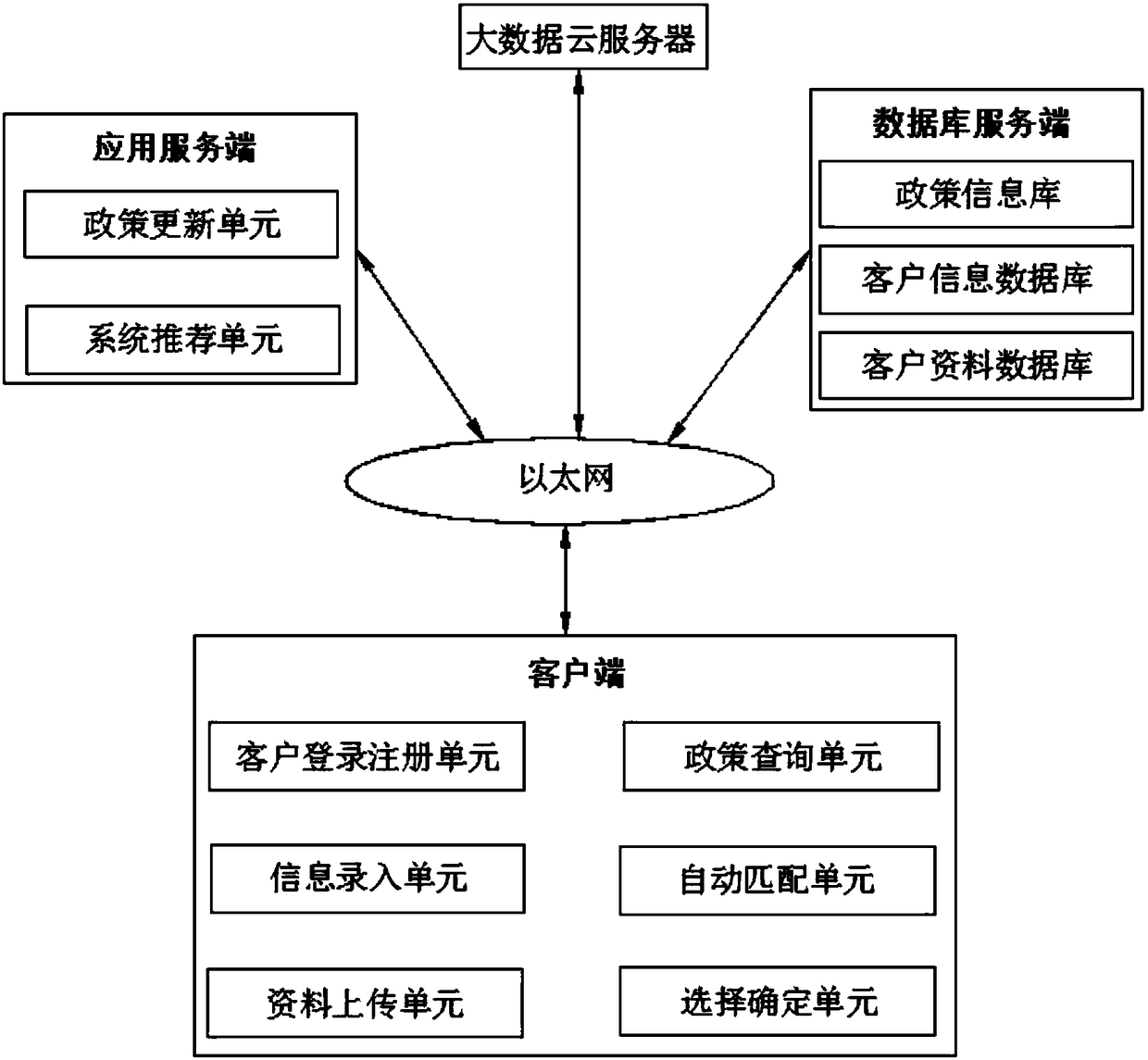
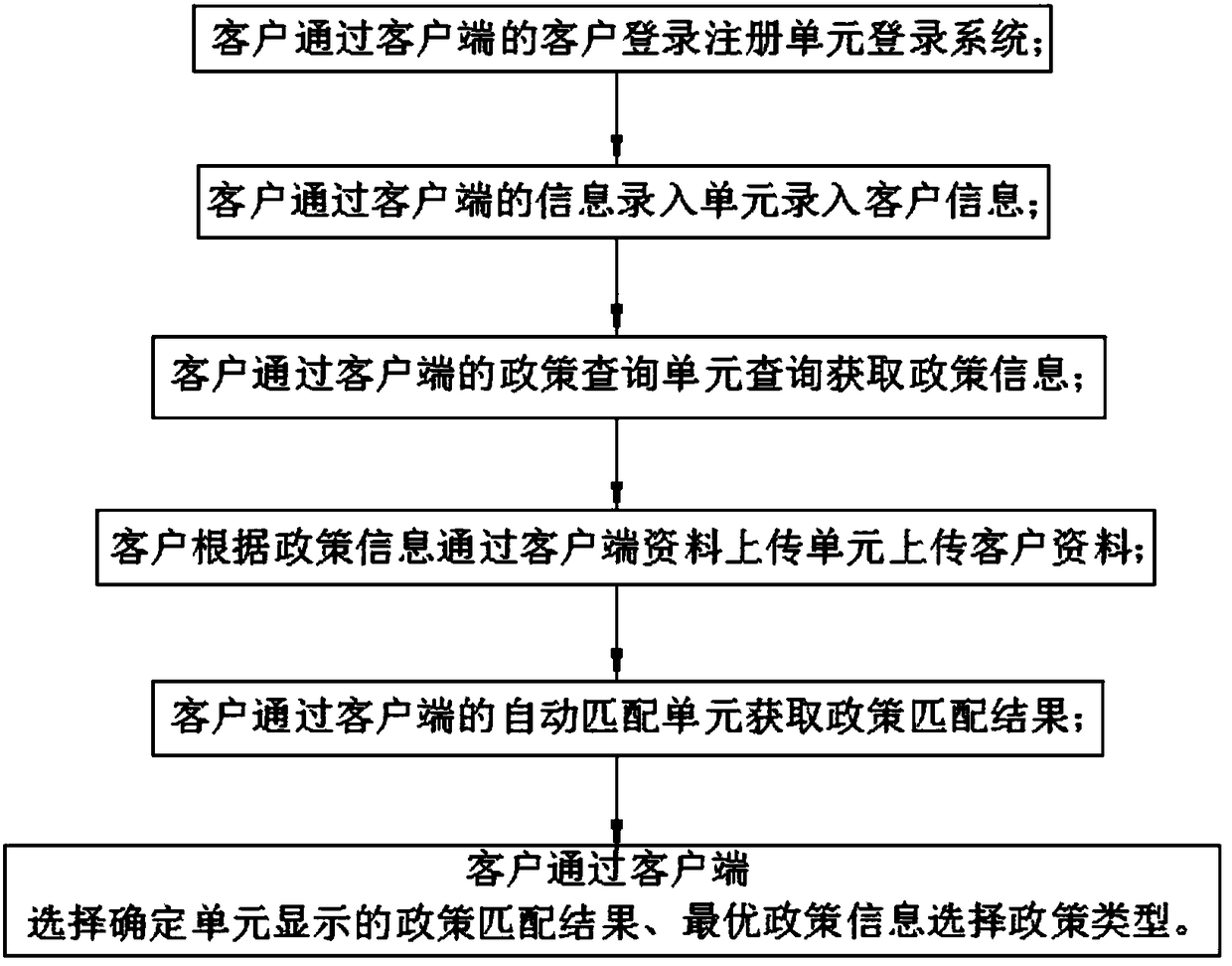
Big data-based enterprise service system and method
InactiveCN108399495ARealize real-time queryEasy to understandWeb data indexingResourcesInformation repositoryInformatization
The invention discloses a big data-based enterprise service system and method, and relates to the technical field of big data-based enterprise service systems. The system comprises a client, an application server, a database server and a big data cloud server, wherein the application server comprises a policy updating unit and a system recommendation unit; the database server stores a policy information library, a client information library and a client data database; the client comprises a client login registration unit, an information input unit, a data uploading unit, a policy query unit, an automatic matching unit and a selection confirmation unit; and the client is in communication connection with the application server, the database server and the big data cloud server. Through the system recommendation module, the automatic matching module and the policy information library, the problems of indirect benefit loss and enterprise information communication reduction due to policy update non-synchronicity or policy application process incomprehension of companies and enterprises are avoided, so that company benefits and informatization are improved.
Owner:合肥和钧正策信息技术有限公司
Preventing deadlock in a policy-based computer system
Methods and mechanisms for preventing deadlock in a policy-based computer system are disclosed. In one embodiment, the method includes various machine-implemented steps, such as a step of receiving policy information based upon decisions about system configurations. At least one policy includes at least one action that has a post condition. Satisfaction of the post condition triggers at least one subsequent action or decision. The policy includes an indication whether the at least one subsequent action or decision should proceed if the action fails to satisfy the post condition. The at least one action is executed. Then, if the action fails to satisfy the post condition, a determination is made whether the at least one subsequent action or decision can proceed based upon the indication.
Owner:CISCO TECH INC
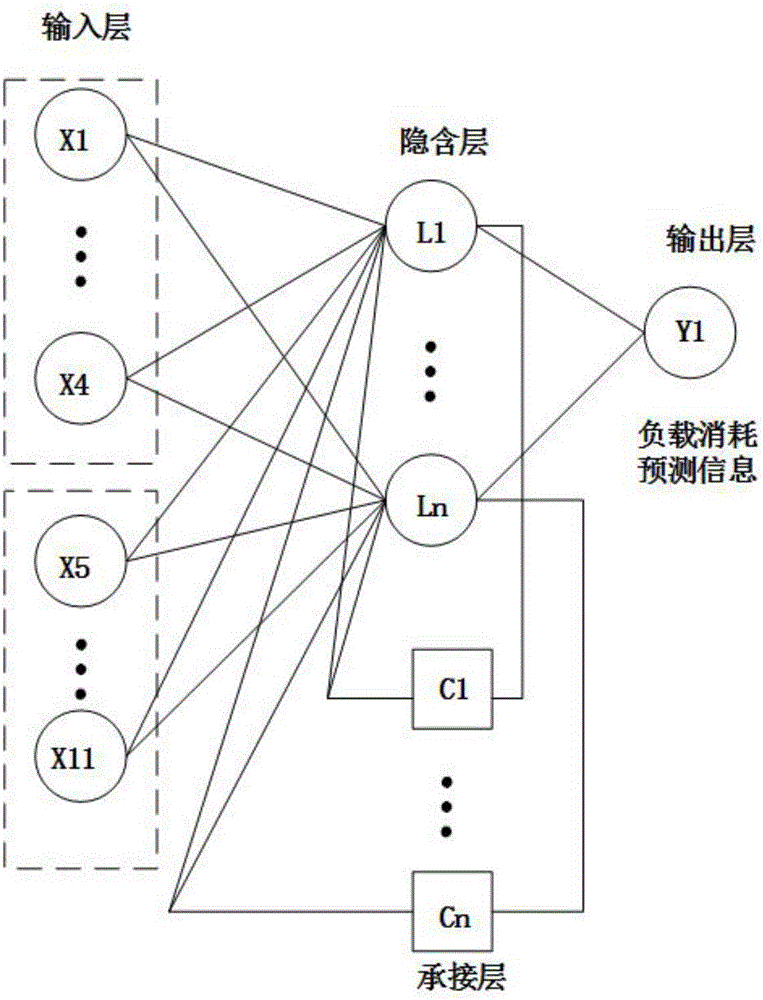
Energy storage management system based on neural network
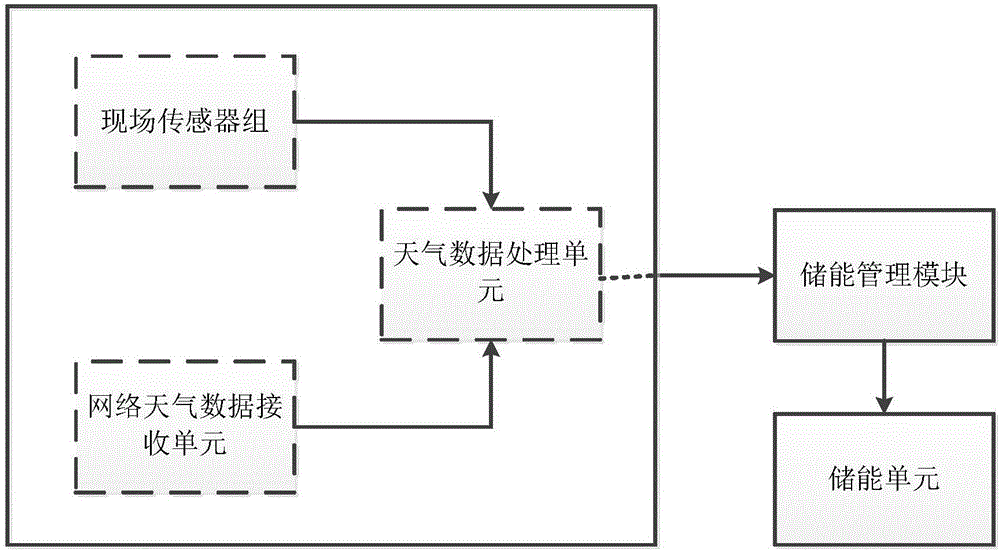
InactiveCN106845770AReduce charge costLow costNeural architecturesResourcesComputer moduleData acquisition
The present invention discloses an energy storage management system based on a neural network. The system comprises a weather data acquisition module, an energy storage unit and an energy storage management module. The weather data acquisition module comprises a field sensor group, a network weather data receiving unit and a weather data processing unit, wherein the weather data processing unit processes data output by the field sensor group and the network weather data receiving unit and marks the data as weather data; the energy storage unit is used for marking and recording energy consumption information of an energy consumption unit; and the energy storage management module receives the weather data and the energy consumption information and processing the weather data and the energy consumption information based on a neural network to output expected energy consumption information Q, and outputs regulation policy information based on the expected energy consumption information Q. According to the system provided by the present invention, energy consumption and weather and data are processed based on the neural network to output the expected energy consumption information; the periods of energy charging and energy discharging of the energy storage unit are adjusted based on the energy consumption information; and by adjusting the period of energy charging, the cost of energy charging is reduced, so that cost reduction is facilitated and benefits are increased.
Owner:深圳市麦澜创新科技有限公司
Adaptive power-saving/power-saving support method in wireless communication system and apparatus using the same
A method for adaptively performing power saving in a station of a wireless communication system includes: receiving first power-save capability information from an AP, the first power-save capability information containing information on power-save schemes supported by a MAC layer of the AP; transmitting second power-save capability information to the AP in response to the first power-save capability information, the second power-save capability information containing information on power-save schemes supported by a MAC layer of the station; transmitting power-save policy information, into which properties of traffics used in the station are reflected, to the AP; and performing a power-save function while interworking with the MAC layer of the station, according to the power-save policy information based on a predetermined power-save scheme.
Owner:ELECTRONICS & TELECOMM RES INST
Method for obtaining user identifier and system therefor
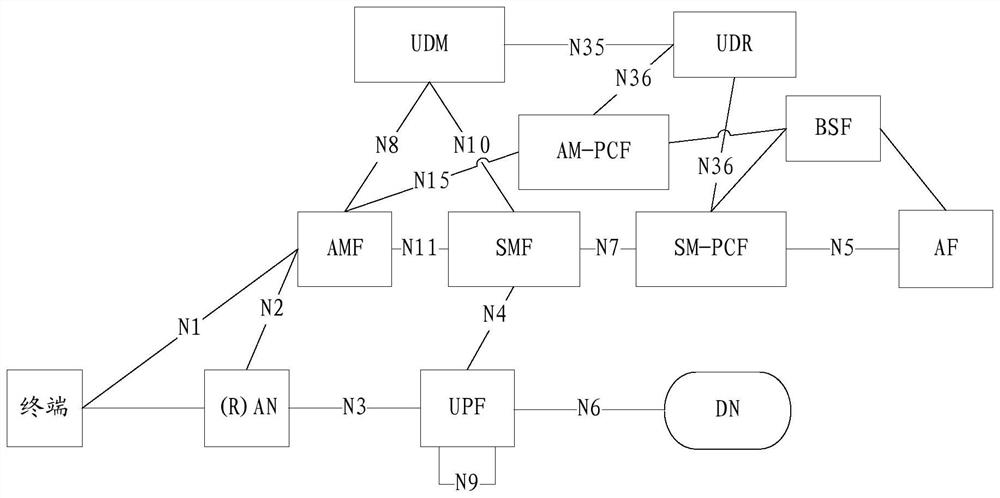
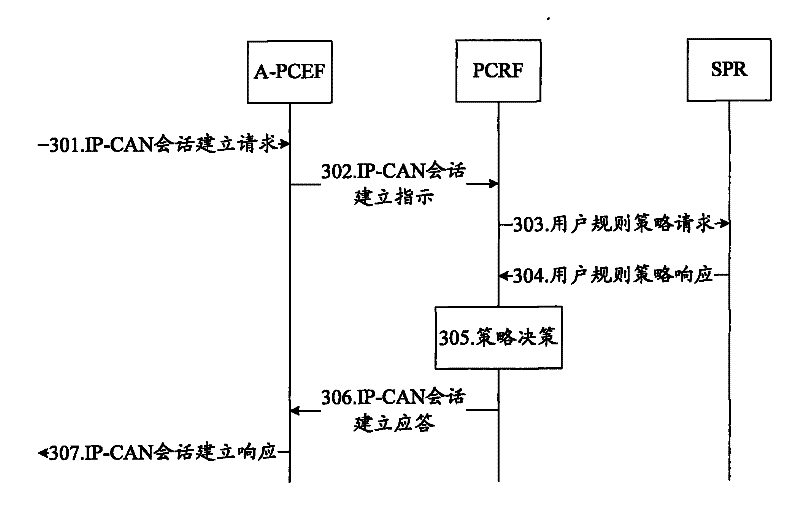
The invention discloses a method for obtaining a user identifier and a system for obtaining the user identifier under a policy and charging control (PCC) frame in a worldwide interoperability for microwave access (WiMAX) network. The method comprises the following steps: when an internet protocol-connectivity access network (IP-CAN) conversation is built, a policy and charging rules function (PCRF) entity requests a real identifier of a user from an authentication authorization accounting (AAA) server, and the AAA server returns the real identifier of the user back to the PCRF; or when the IP-CAN conversation is built, a subscription profile repository (SPR) requests a real identifier of the user from the AAA server, and the AAA server returns the real identifier of the user back to the SPR. User policy information based on the real user identifier is realized under the condition that the SPR is separated from the AAA server in the PCC frame of the WiMAX network.
Owner:ZTE CORP
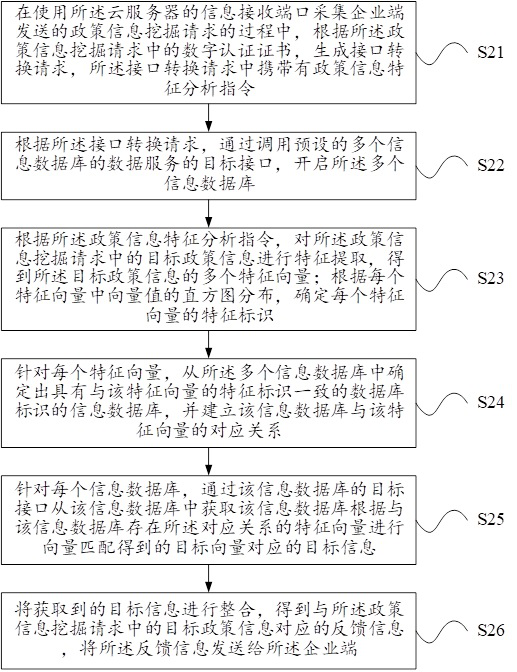
Policy information mining method and device, and cloud server
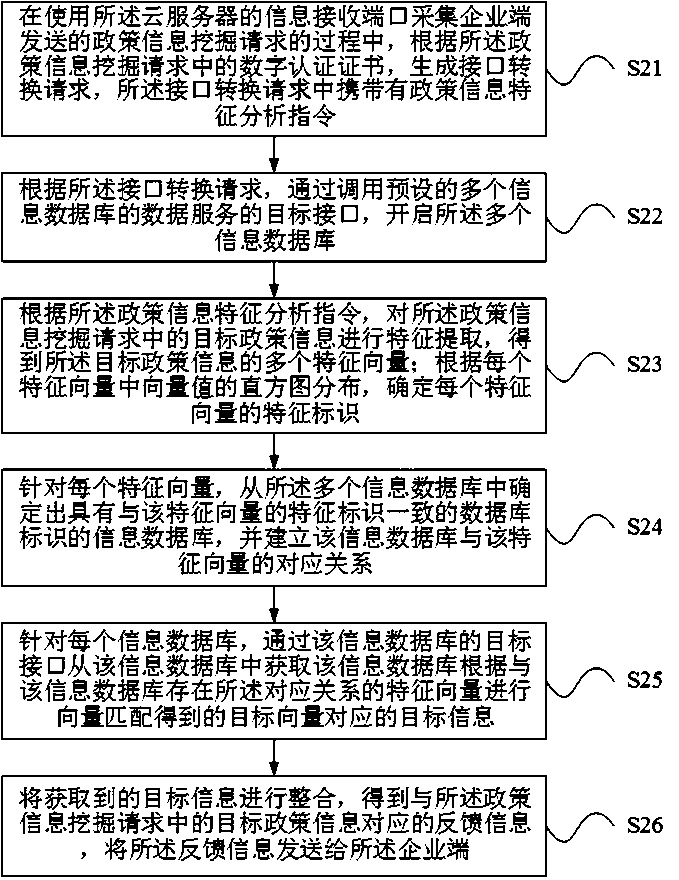
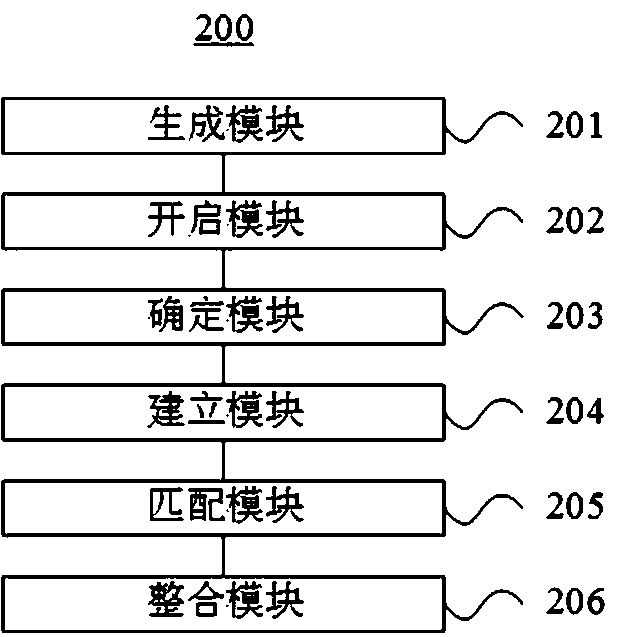
ActiveCN111241152ADatabase management systemsDigital data protectionFeature extractionInformation mining
The invention relates to the technical field of data processing, in particular to a policy information mining method, a policy information mining device and a cloud server. The policy information mining method comprises the steps of generating a policy information feature analysis instruction according to a digital authentication certificate, performing feature extraction on target policy information in a policy information mining request according to the policy information feature analysis instruction to obtain a plurality of feature vectors, establishing a corresponding relationship betweenthe feature vectors and a plurality of information databases opened based on an interface conversion request according to a feature identifier of each feature vector, acquiring target information corresponding to a target vector obtained by performing vector matching on the information database based on the feature vectors having the corresponding relationship with the information database by means of an interface of each information database, and finally sending feedback information obtained by integrating the target information to an enterprise terminal. According to the policy information mining method, the policy information mining device and the cloud server, multi-dimensional feature extraction can be carried out on the target policy information sent by the enterprise terminal, and then comprehensive and deep mining and interpretation are carried out on the target policy information based on the information databases of different dimensions.
Owner:广州高企云信息科技有限公司
Insurance policy generation method and electronic equipment
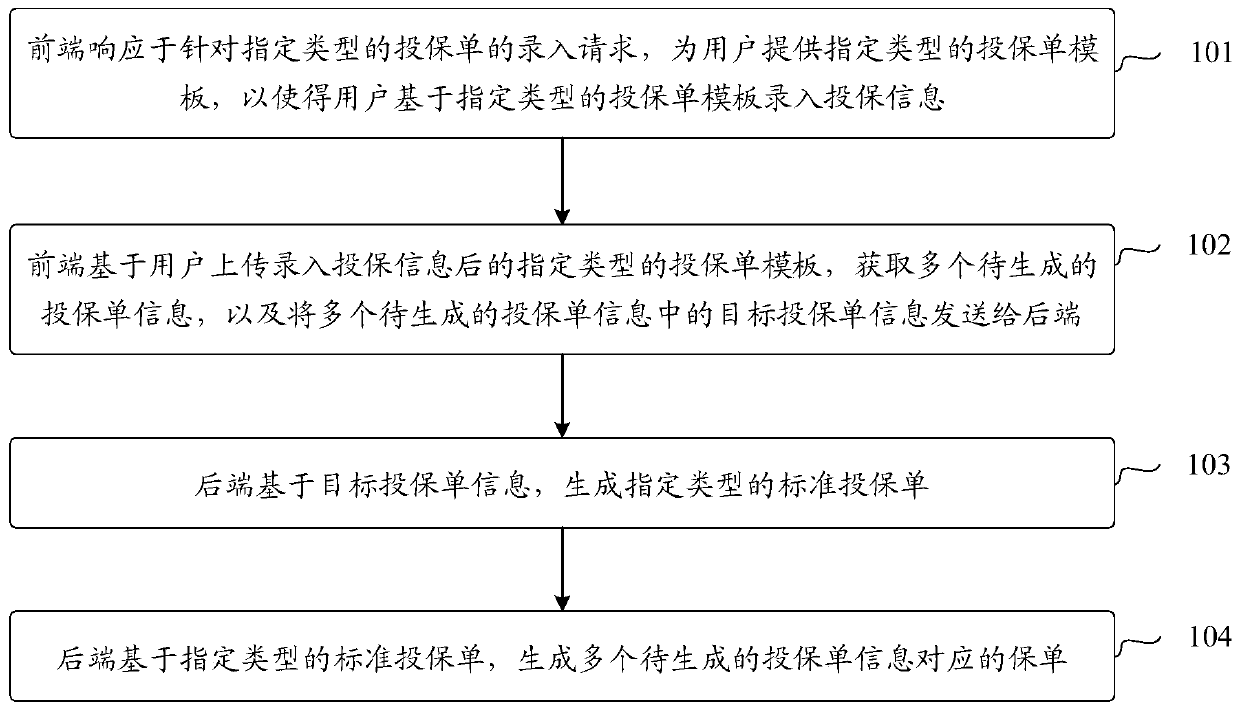
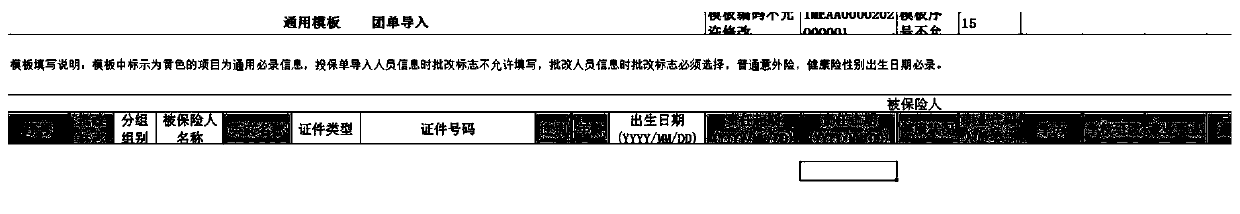
ActiveCN111598525AReduce workloadFinanceNatural language data processingBusiness PersonnelPolicy information base
The invention discloses an insurance policy generation method and electronic equipment, which are used for solving the problems of large workload of technicians and business personnel in the insuranceindustry and relatively low insurance policy generation efficiency in the prior art. The method comprises the steps that a front end responds to an input request for an insurance slip of a specifiedtype and provides an insurance slip template of the specified type for a user, so that the user inputs insurance information based on the insurance slip template of the specified type, and the insurance slip of the specified type comprises a group bill and one of multiple insurance slips of the same type; the front end obtains a plurality of pieces of insurance slip information to be generated based on the insurance slip template of the specified type after the insurance slip information is uploaded and input by the user, and sends target insurance slip information in the plurality of pieces of insurance slip information to be generated to the rear end; the rear end generates an insurance slip of a specified type based on the target insurance slip information; and the rear end generates aplurality of insurance policies corresponding to the to-be-generated insurance policy information based on the specified type of insurance policy.
Owner:PEOPLE'S INSURANCE COMPANY OF CHINA
Method for importing and analyzing insurance policy information based on dynamic mapping
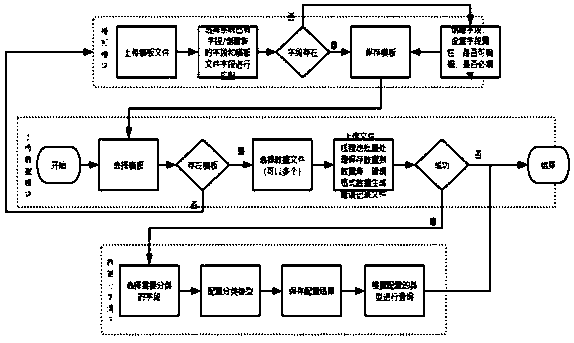
PendingCN111324646ASolve data management problemsImprove service qualityDatabase management systemsRelational databasesData fileChecksum
The invention relates to an insurance policy information data processing method. The method comprises the following steps of 1, creating a dynamic mapping template; 2, uploading data by using a data uploading module; 3, classifying the data by utilizing a data classification module; according to the invention, available data is sorted out in a classified manner according to requirements. Accordingto the technology, different dynamic mapping templates can be set according to insurance policy data from different sources; and the template can be modified to cope with the change of the demand, validity verification and analysis are performed on the input data, and incorrect insurance policy data is sorted to generate an error data file to be fed back to the user.
Owner:北京众信易保科技有限公司
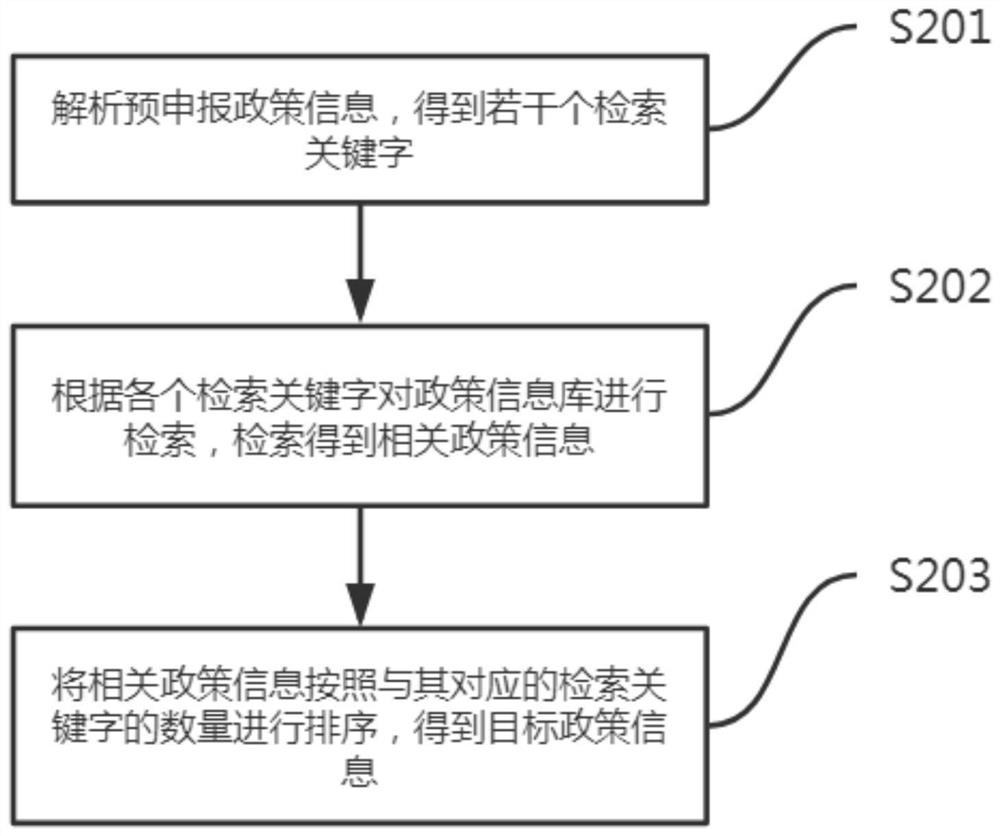
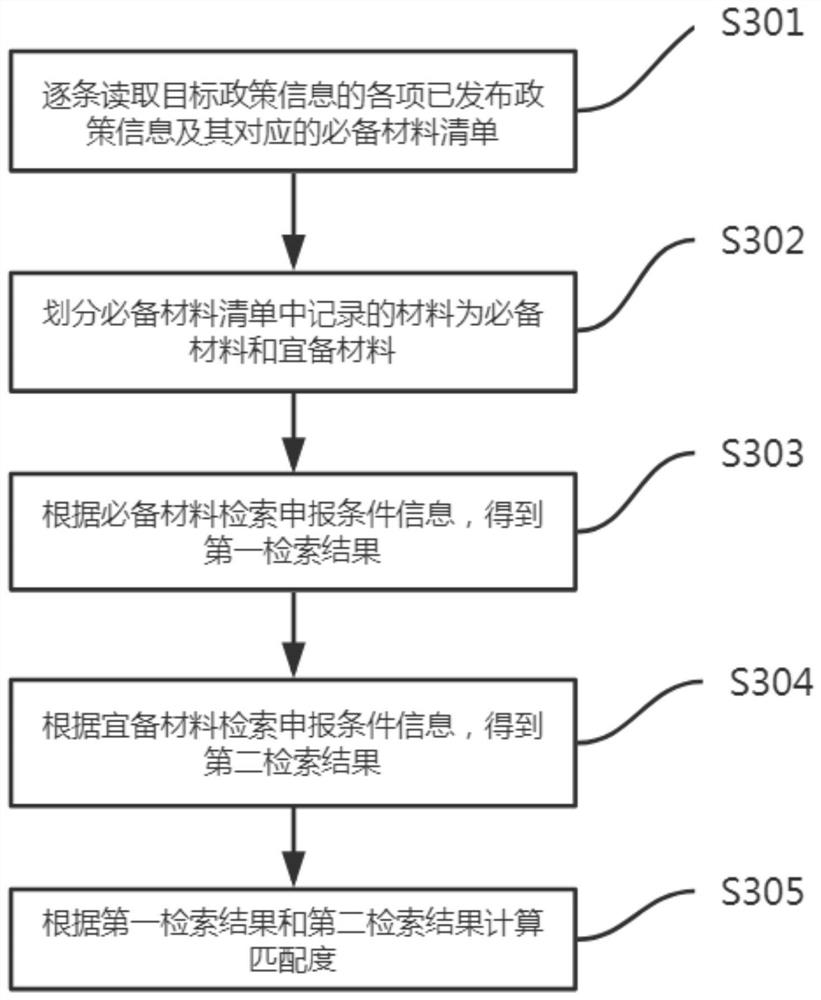
Policy matching degree calculation method and system, computer equipment and storage medium
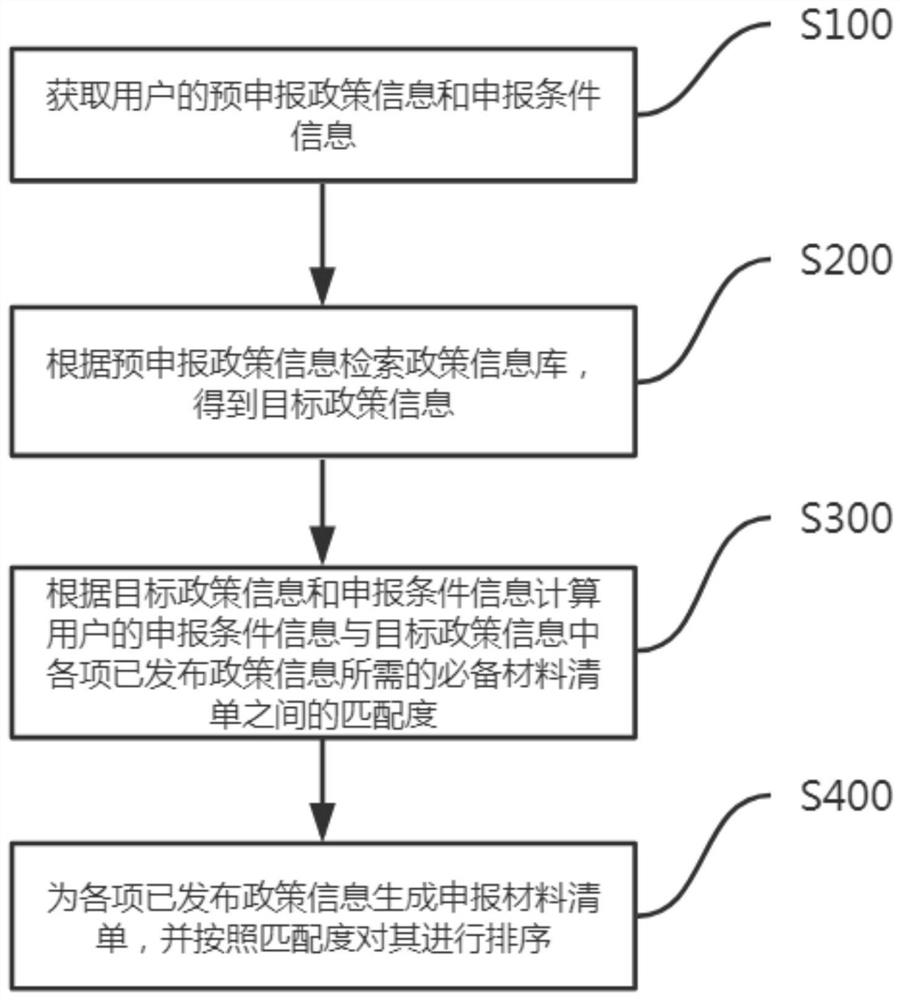
InactiveCN113255742ATroubleshoot Self-Lookup PoliciesKnow quicklyCharacter and pattern recognitionText database queryingInformation repositoryCollation
The invention belongs to the technical field of software management, and particularly relates to a policy matching degree calculation method and system, computer equipment and a storage medium, and the method comprises the steps: obtaining pre-declaration policy information and declaration condition information of a user; retrieving a policy information base according to the pre-declaration policy information to obtain target policy information; calculating a matching degree according to the target policy information and the declaration condition information; and generating a declaration material list for each published policy information, and sorting the declaration material list according to the matching degree. According to the method and system, the type of the policy to be declared by the current user is judged according to the policy information to be declared of the user, so that the related policy is determined, the matching degree is calculated according to the declared condition information of the user, and the basis for judging the policy declared possibility is provided for the user, so that on one hand, the problem that the user needs to autonomously search the policy is solved; and on the other hand, the user can be helped to quickly know the declarable policy, and a required material list is generated.
Owner:广西东创大数据有限公司
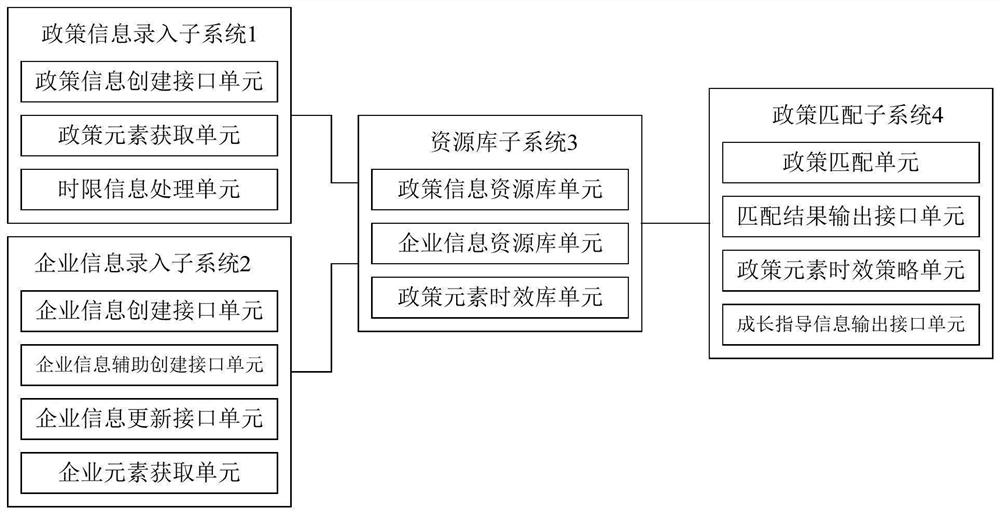
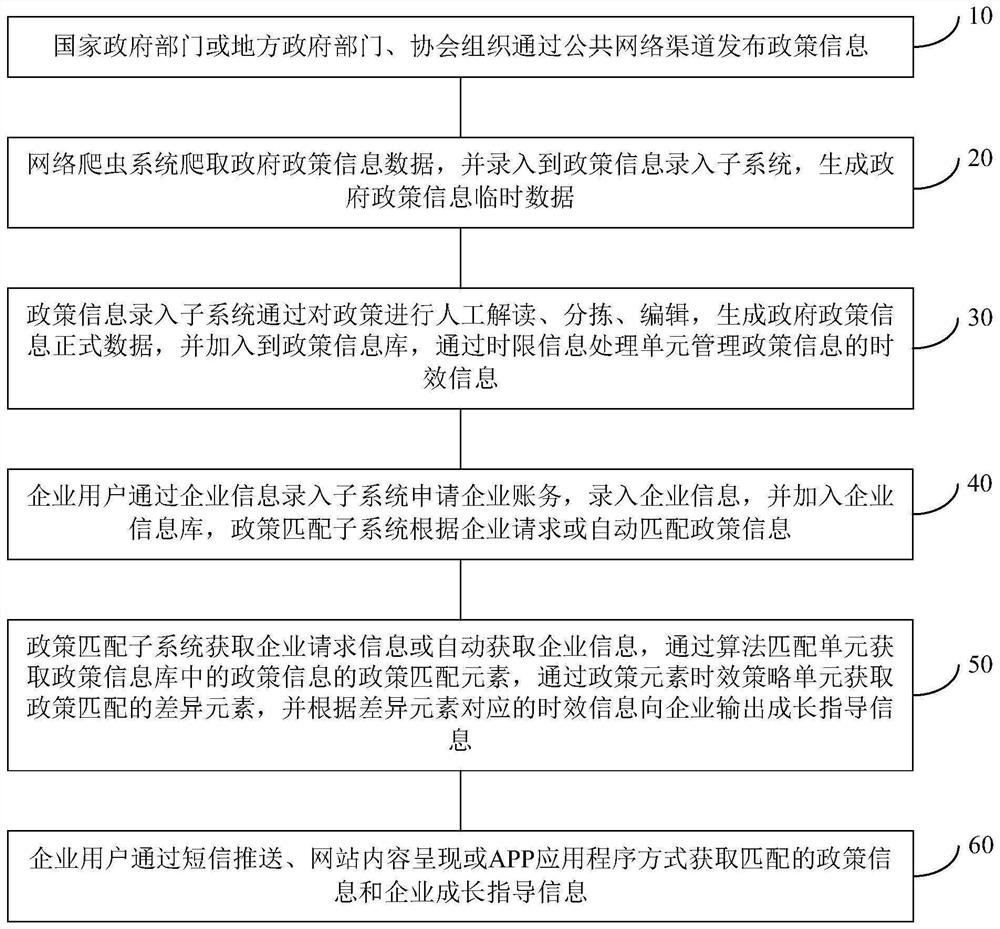
Enterprise policy information matching method and system
PendingCN111784094AImprove convenienceFully understandWeb data indexingResourcesInformation repositoryInformation processing
The invention discloses an enterprise policy information matching method and system. The method comprises the steps that a web crawler system crawls government policy information data, inputs the government policy information data into a policy information input subsystem, and generates government policy information temporary data; government policy information formal data are generated through manual interpretation, sorting and editing of policies and added into a policy information base, and time limit information of policy information is managed through a time limit information processing unit; an enterprise inputs enterprise information; and the policy matching subsystem matches policy matching elements of the policy information and difference elements of policy matching through an algorithm, and outputs growth guidance information to the enterprise according to the time efficiency information corresponding to the difference elements. The policy element information is compared withthe enterprise element information through the policy matching subsystem, policies are quickly matched for enterprises and output to the enterprises, relevant procedure information of policy handlingcan be output, the convenience degree of enterprise handling is increased, and the enterprises can fully understand the policies and enjoy policy bonus.
Owner:成都草根有智创新科技有限公司
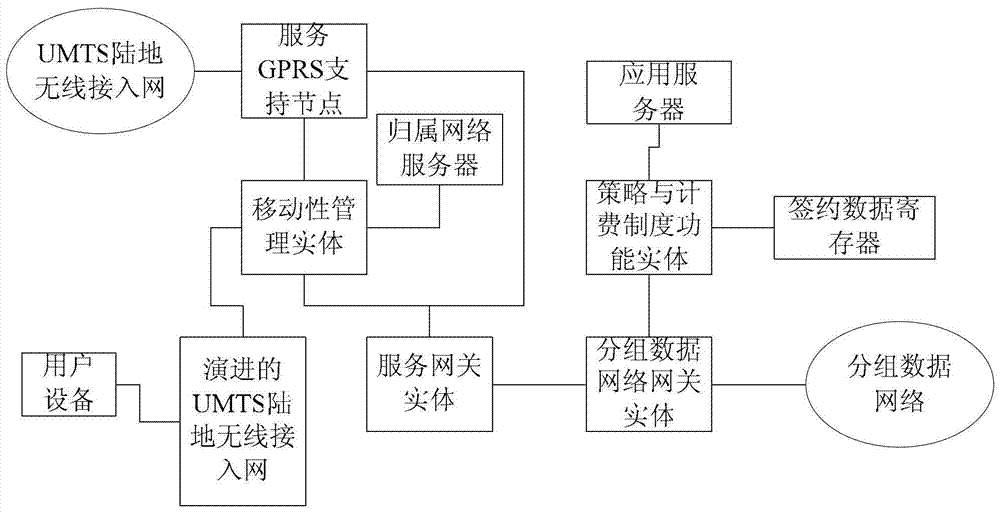
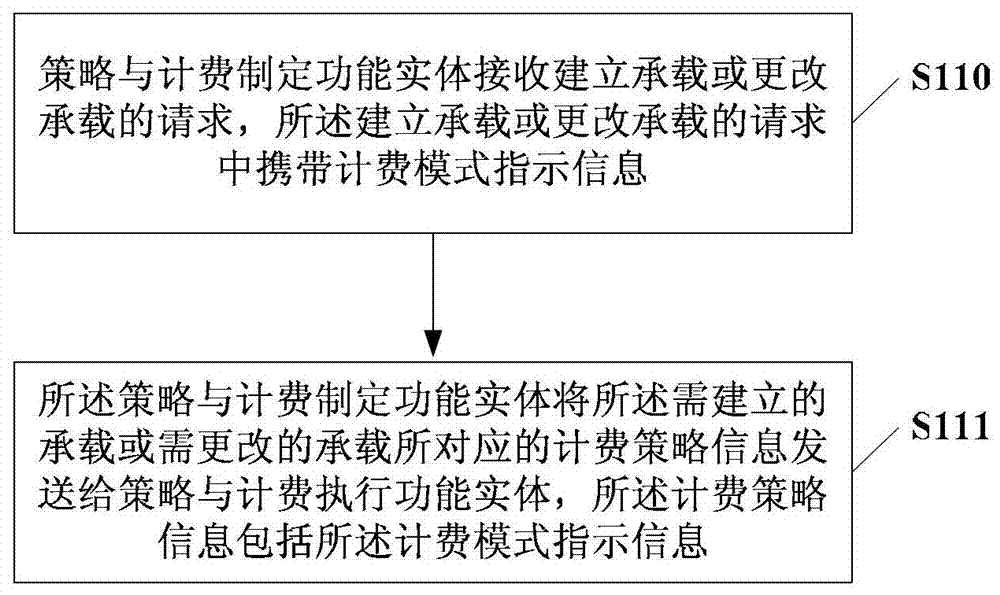
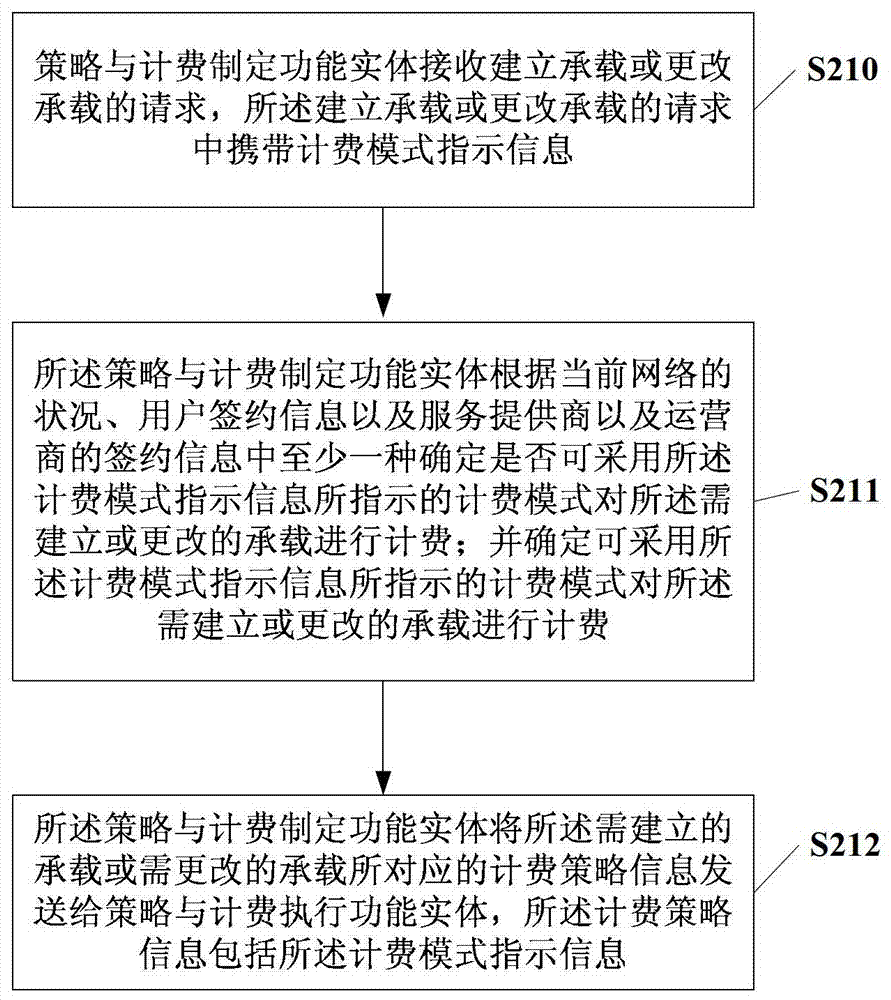
Billing policy information generation method and policy and billing formulation functional entity
The embodiment of the present invention discloses a method for generating charging policy information and a policy and charging formulation functional entity, wherein the method may include: the policy and charging formulation functional entity receives a request for establishing a bearer or changing a bearer, and the establishing or changing a bearer The bearer request carries charging mode indication information, and the charging mode indication information is used to indicate that the charging mode based on the bearer to be established or changed is a traffic-based charging mode or a connection duration-based charging mode, and Any one or a combination of event-based charging modes; the policy and charging formulation function entity sends the charging policy information corresponding to the bearer to be established or the bearer to be changed to the policy and charging execution function entity, where the charging policy information includes the charging mode indication information. In the embodiment of the present invention, charging policy information based on different charging modes is generated for different application scenarios, so as to satisfy user experience to the greatest extent.
Owner:HUAWEI TECH CO LTD
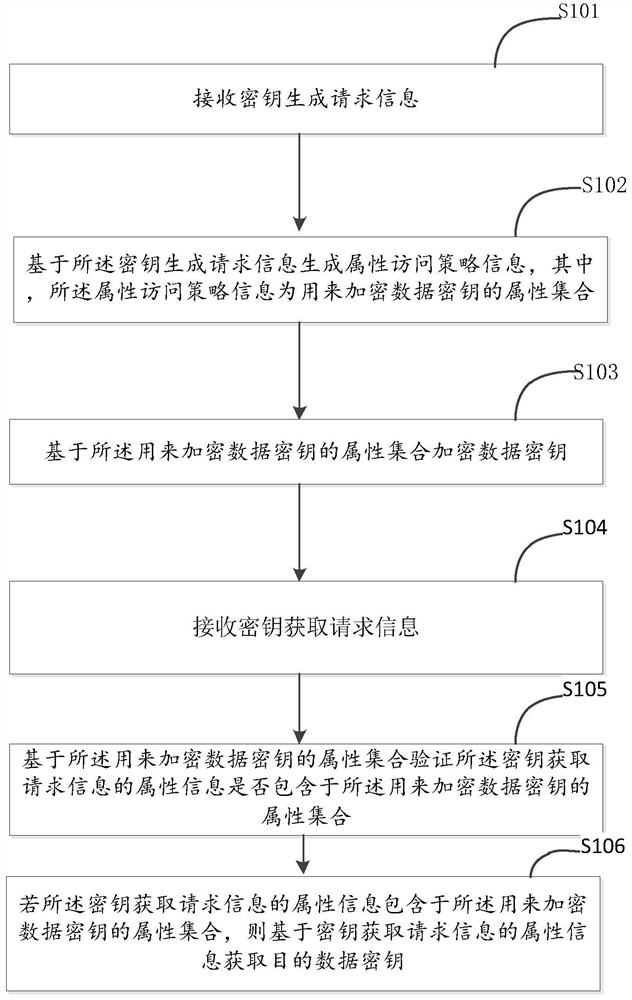
A key management method and related equipment
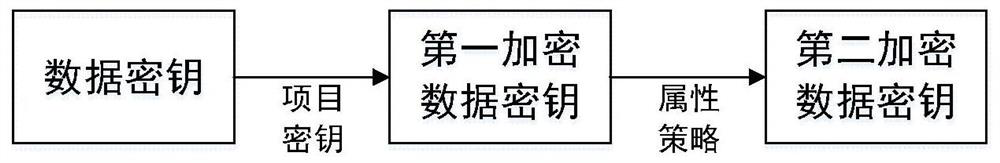
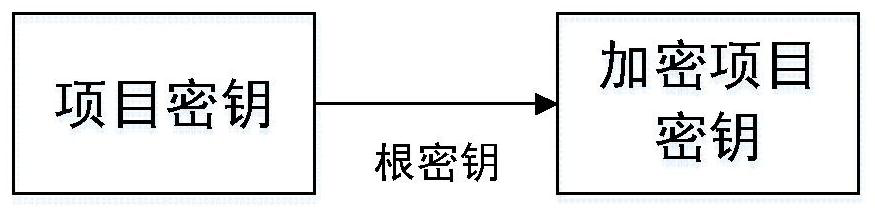
The embodiment of the present application provides a key management method and related equipment, belonging to the field of network security technology, which solves the problem that access control cannot be effectively implemented for each key in the existing solutions, and it is inconvenient for users to manage keys flexibly. The method includes: receiving key generation request information; generating attribute access policy information based on the key generation request information, wherein the attribute access policy information is a set of attributes used to encrypt data keys; Encrypting the attribute set of the data key to encrypt the data key; receiving the key acquisition request information; verifying whether the attribute information of the key acquisition request information is included in the encryption key based on the attribute set used to encrypt the data key An attribute set of the data key; if the attribute information of the key acquisition request information is included in the attribute set used to encrypt the data key, the target data key is acquired based on the attribute information of the key acquisition request information.
Owner:INSPUR SUZHOU INTELLIGENT TECH CO LTD
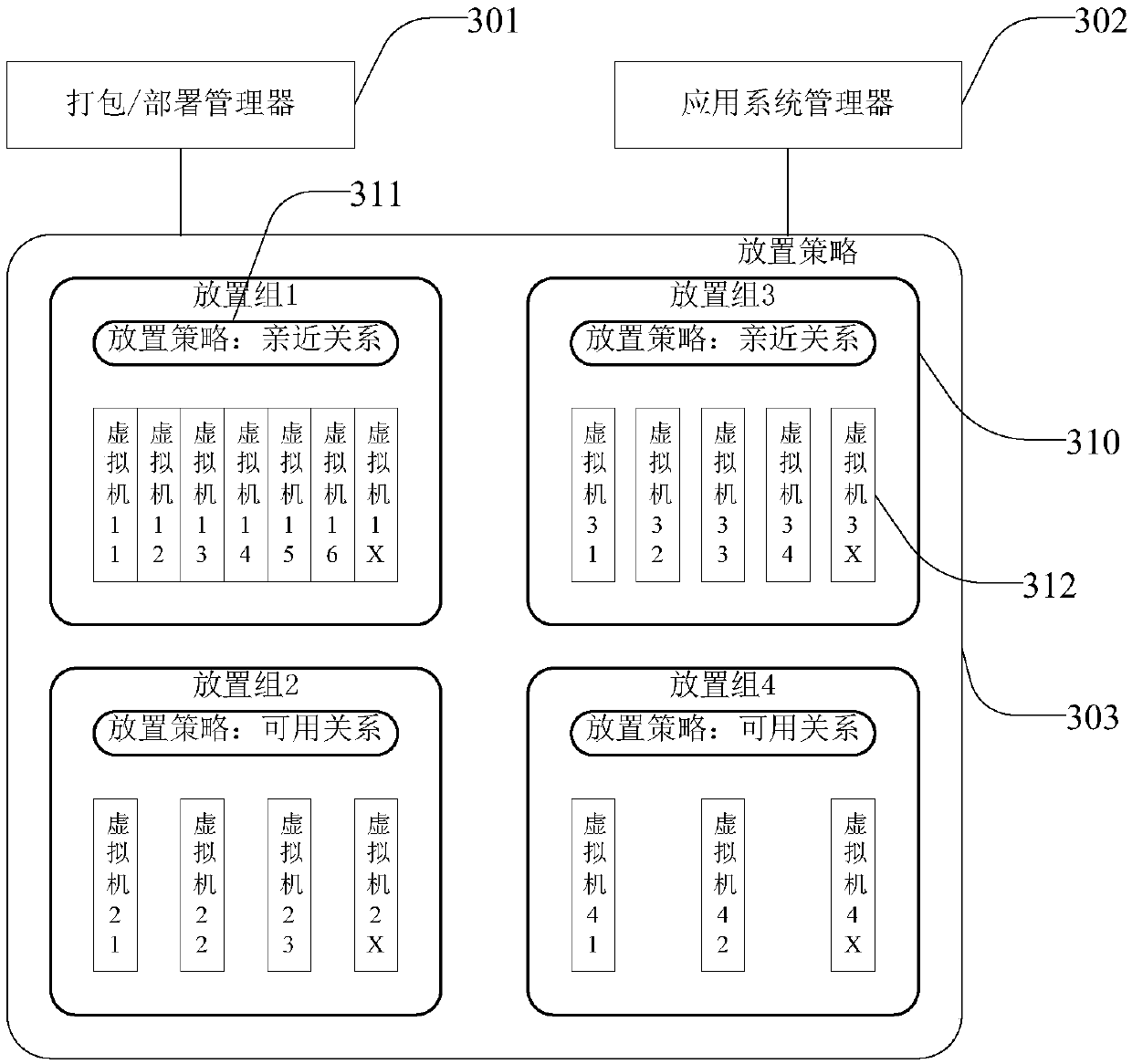
Deployment method and device for a collection of virtual machines
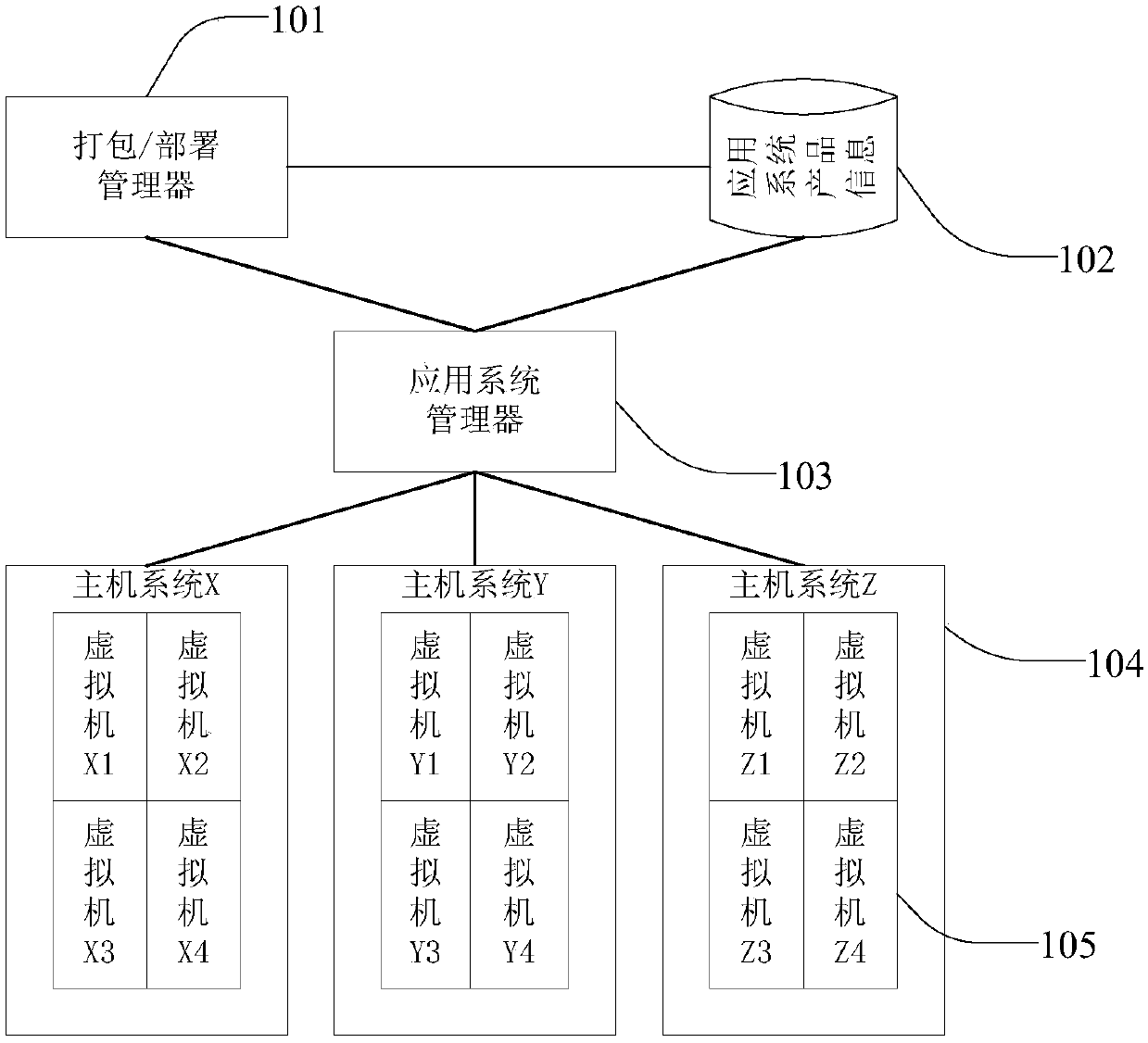
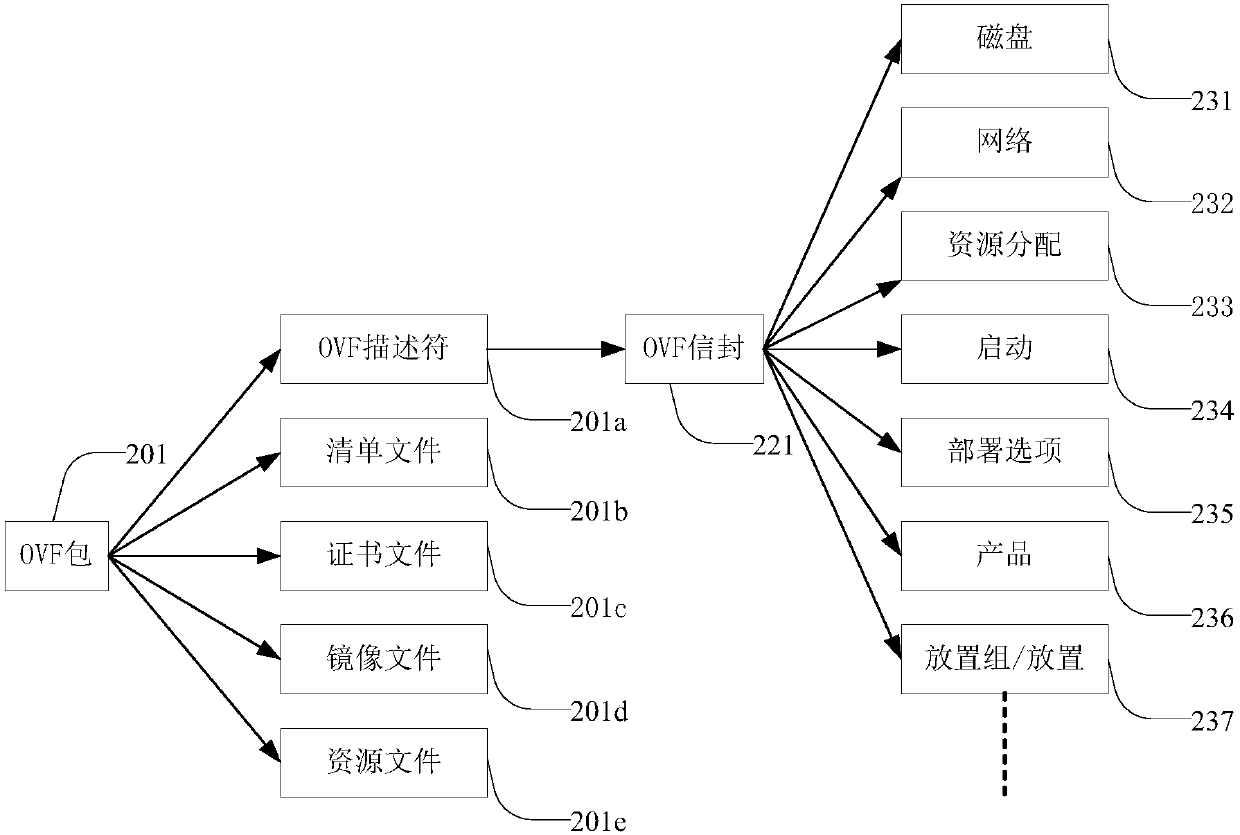
ActiveCN104035808BSolve problems that cannot meet user application deployment needsImprove deployment capabilitiesTransmissionSoftware simulation/interpretation/emulationVirtualizationComputer science
The invention discloses a method and a device for deploying a set of virtual machines. Wherein, the method includes: receiving the placement strategy information of the OVF package; judging whether the placement strategy of the virtual machine collection is a nested placement strategy according to the placement strategy information; if so, deploying the virtual machine collection by adopting the placement strategy depth-first principle, wherein, The virtual machine collection is divided into multiple levels according to the nested placement strategy. Each level contains a virtual machine collection and / or virtual machines. The order satisfies the placement policy of the virtual machine collection. The present invention solves the problem in the related art that the deployment mode of the virtual machine set cannot meet user application deployment requirements, and enhances the deployment capability of the virtualization platform.
Owner:ZTE CORP
Policy information mining method, device and cloud server
The invention relates to the technical field of data processing, and relates to a policy information mining method, device and cloud server. According to the digital authentication certificate, the present invention generates a policy information characteristic analysis instruction, and according to the policy information characteristic analysis instruction, performs feature extraction on the target policy information in the policy information mining request to obtain a plurality of feature vectors, and then according to the feature identification of each feature vector, Establish a corresponding relationship with multiple information databases based on the interface conversion request, so that based on the excuse of each information database, the target information corresponding to the target vector obtained by the vector matching of the information database based on the feature vector that has a corresponding relationship with the information database is obtained, and finally Send the feedback information obtained by integrating the target information to the enterprise. The present invention can perform multi-dimensional feature extraction on the target policy information sent by the enterprise end, and then comprehensively and deeply excavate and interpret the target policy information based on information databases of different dimensions.
Owner:广州高企云信息科技有限公司
Conflict detection system and method for computer network defense (CND) policy
InactiveCN103049700BImprove versatilityImprove scalabilityPlatform integrity maintainanceInformation repositoryInternet privacy
The invention relates to a conflict detection system and method for a computer network defense (CND) policy. According to the method, a CND policy description file is read and parsed by using a morphology parser and a grammar parser; an initial policy body is artificially constructed by using a body modeling tool, only comprises concepts for policy tuples in a CND policy and the relationship among the concepts, and does not include policy examples and the relationship among the policy examples; a local policy body including the policy examples is generated according to the initial policy body and a loaded and parsed policy ordered set, a semantic inclusion relationship among the tuples is then obtained according to the semantic mapping of the policy tuples in a defense policy information base, and a CND policy semantic model is constructed based on the semantic inclusion relationship; a relational diagram for all the tuples of the policy is constructed and traversed, and the relationship among the policy tuples is obtained through analysis; and through the measure of tuple comparison, the policy conflict analysis is completed, and the objects, types and reasons for conflict generation are finally provided by algorithms in the form of conflict reports. According to the system and the method, conflicts can be more effectively detected, security problems, such as unauthorized access and the like, are prevented from easily occurring, and the security of a computer network system is greatly improved.
Owner:BEIHANG UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com