Conflict detection system and method for computer network defense (CND) policy
A computer network and conflict detection technology, applied in the direction of platform integrity maintenance, etc., to achieve the effect of improving versatility and good scalability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
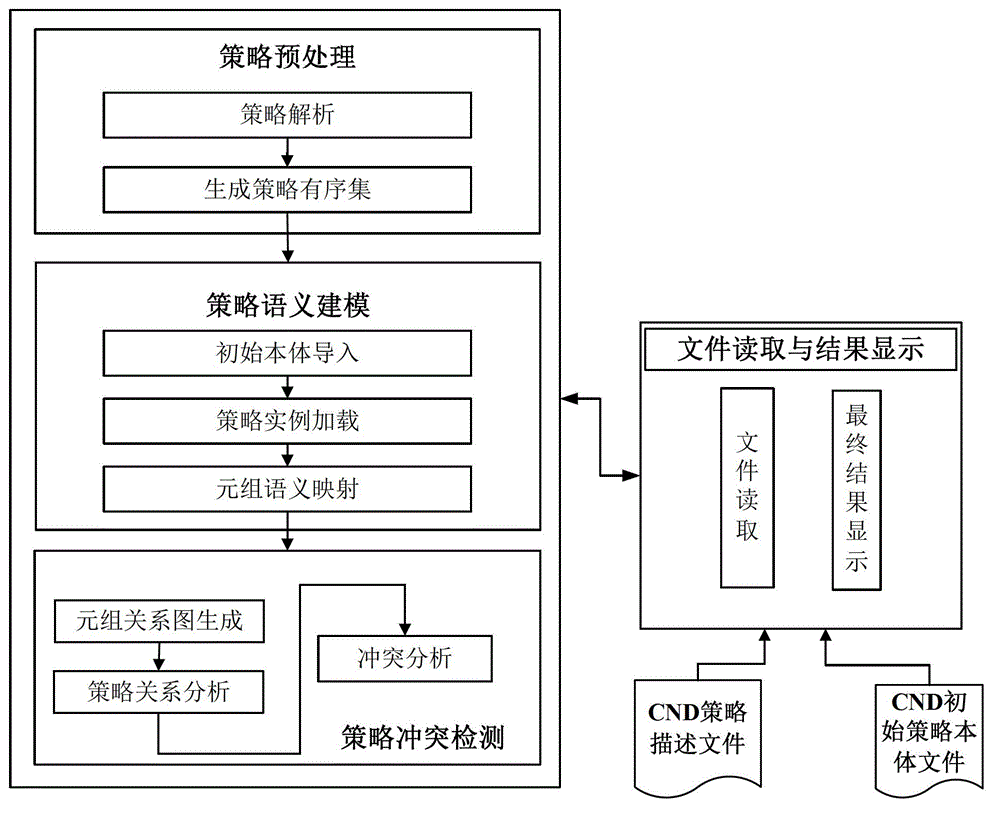
[0029] Such as figure 1 As shown, in the present invention, the computer network defense policy conflict detection system is composed of a file reading and result display module, a policy preprocessing module, a policy semantic modeling module and a policy conflict detection module.
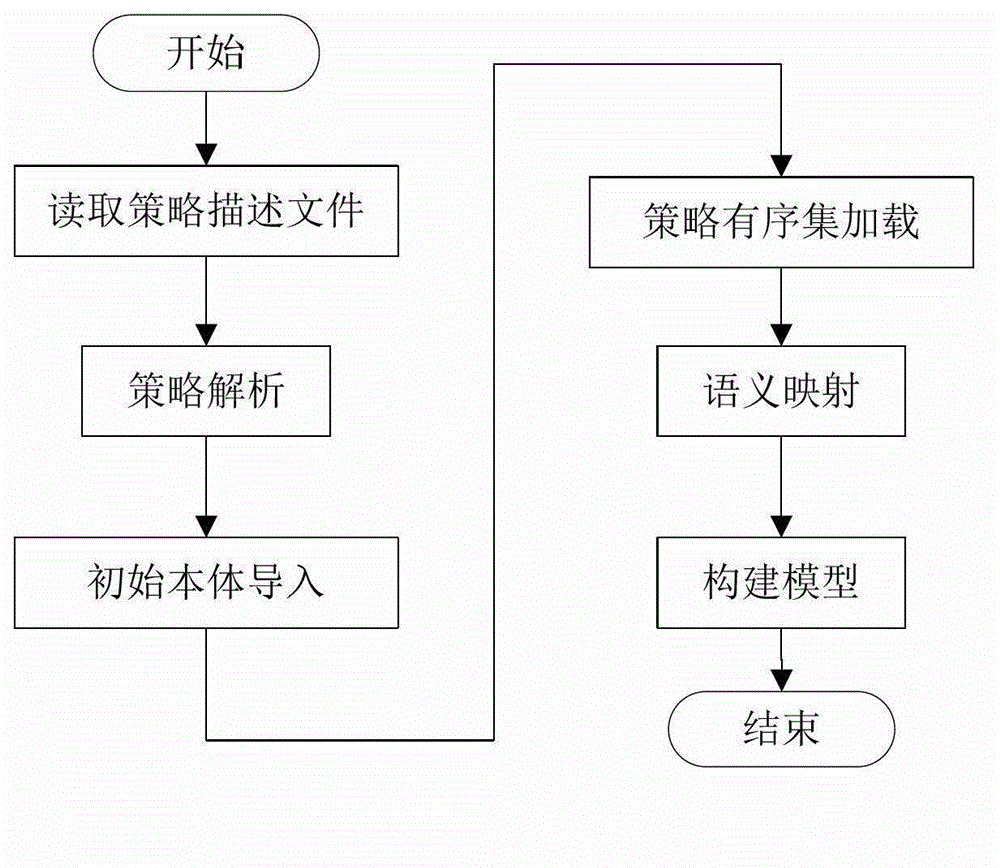
[0030] The whole system implementation process is as follows:
[0031] (1) First give the CNDPSL language model
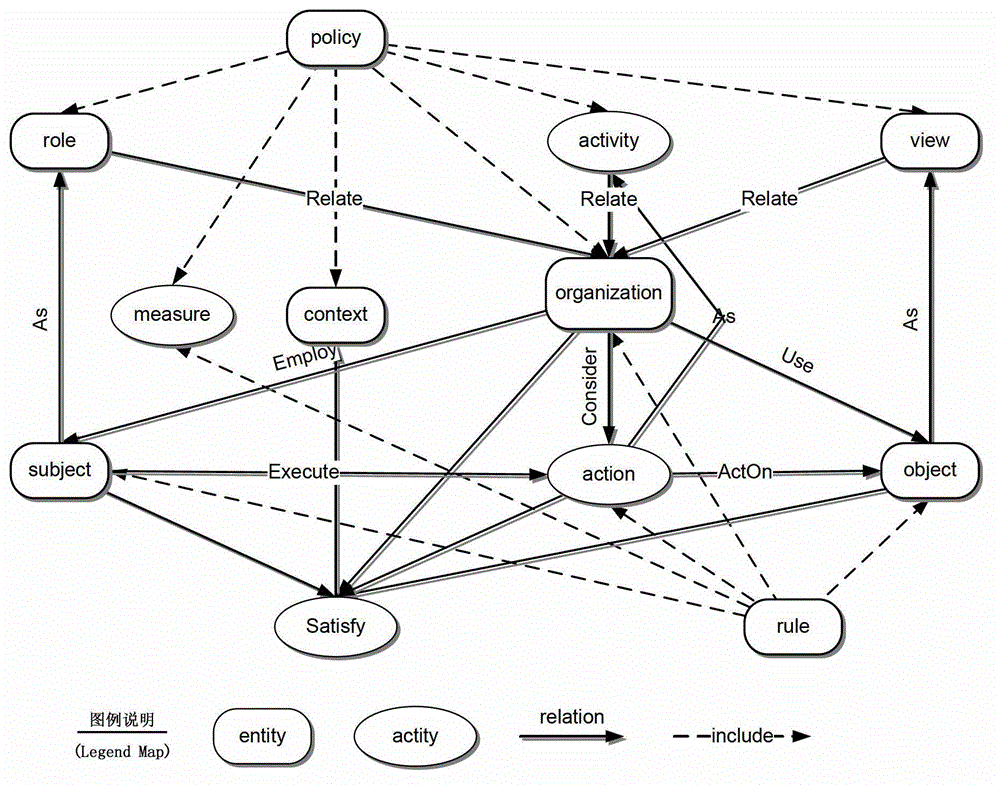
[0032] CNDPSL language is oriented to Computer Network Defense Policy Model (Computer Network Defense Policy Model, CNDPM), figure 2 It is the structural diagram of the model, which can describe the protection, detection and response strategies in a unified way. The CNDPSL language is a declarative language that abstracts the behavior of network defense control, and has good flexibility, scalability and adaptability.
[0033] The defense strategy described by the CNDPSL language is a black box related to organization, role, view and activity. According to the definition of the compo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com