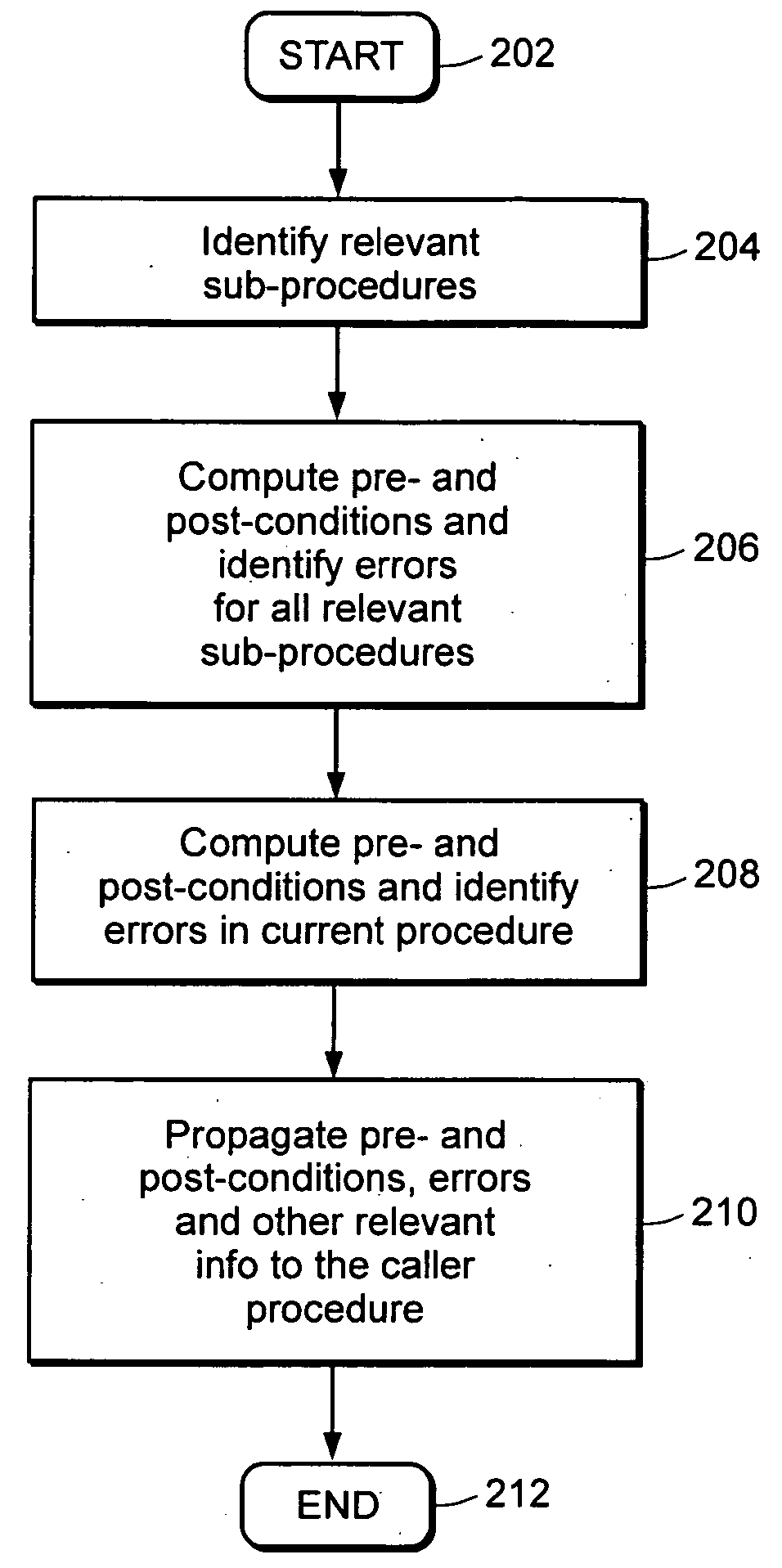
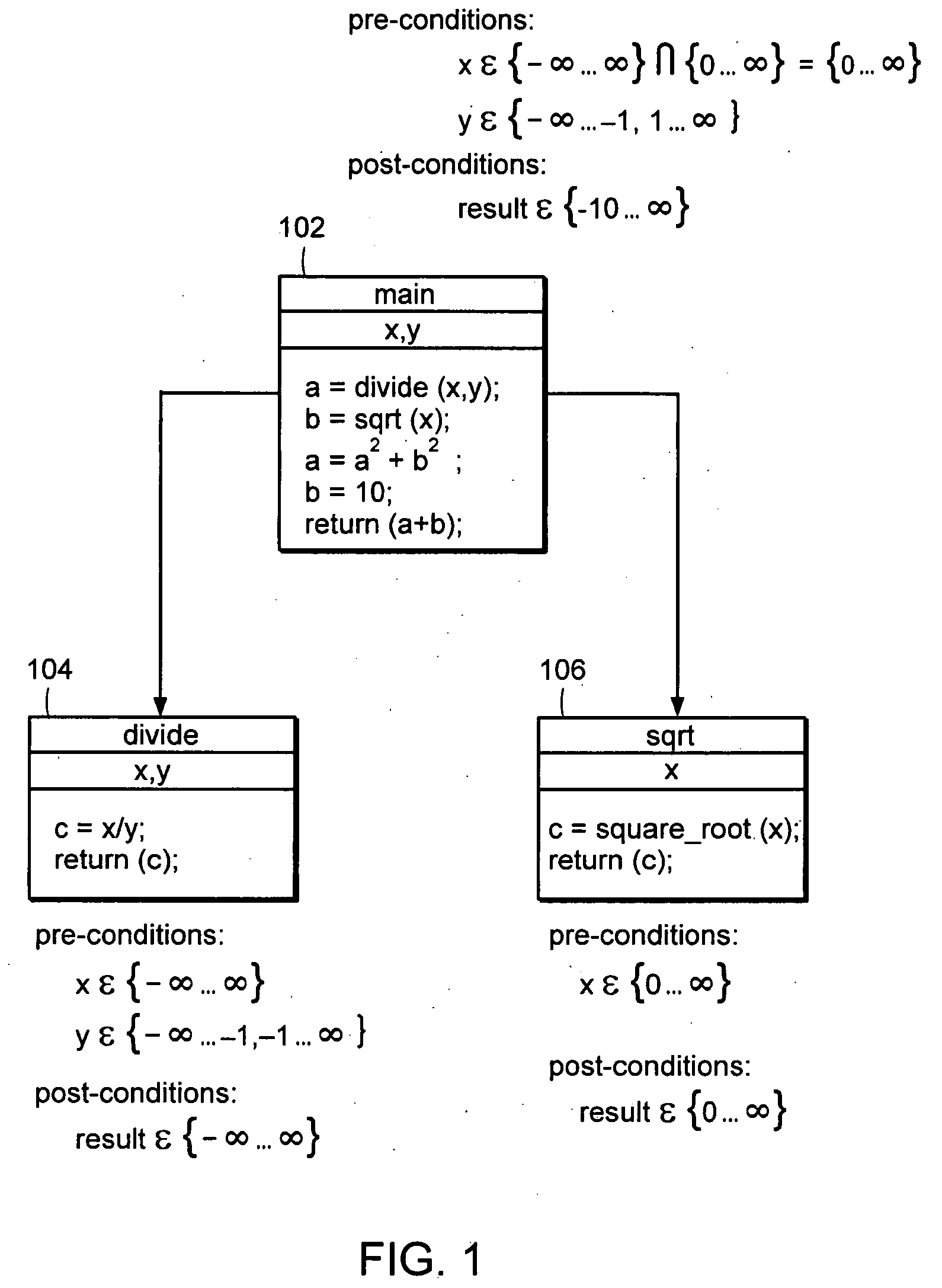
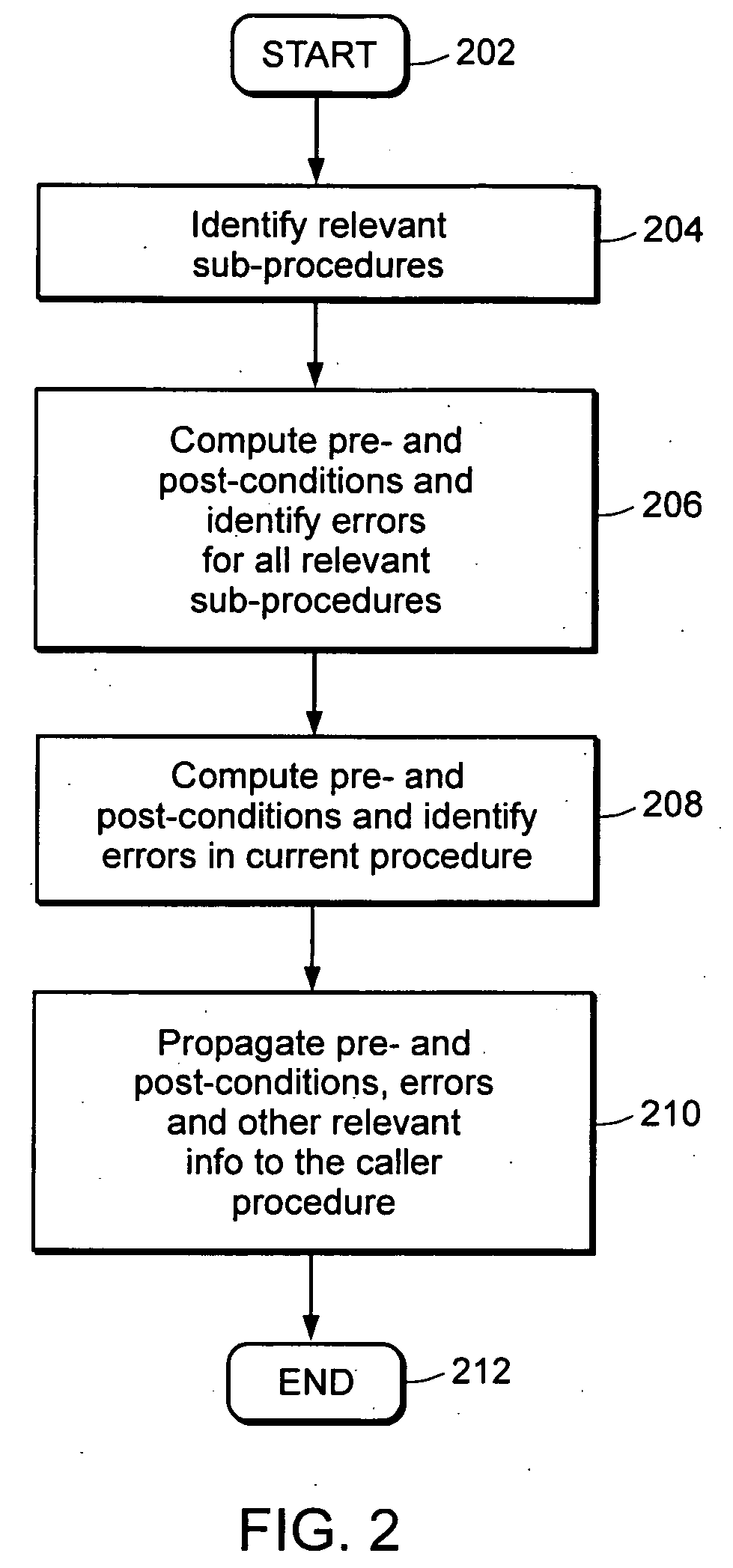
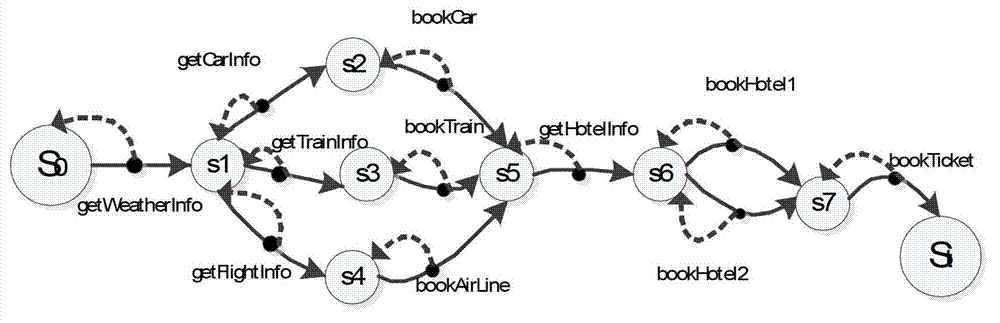
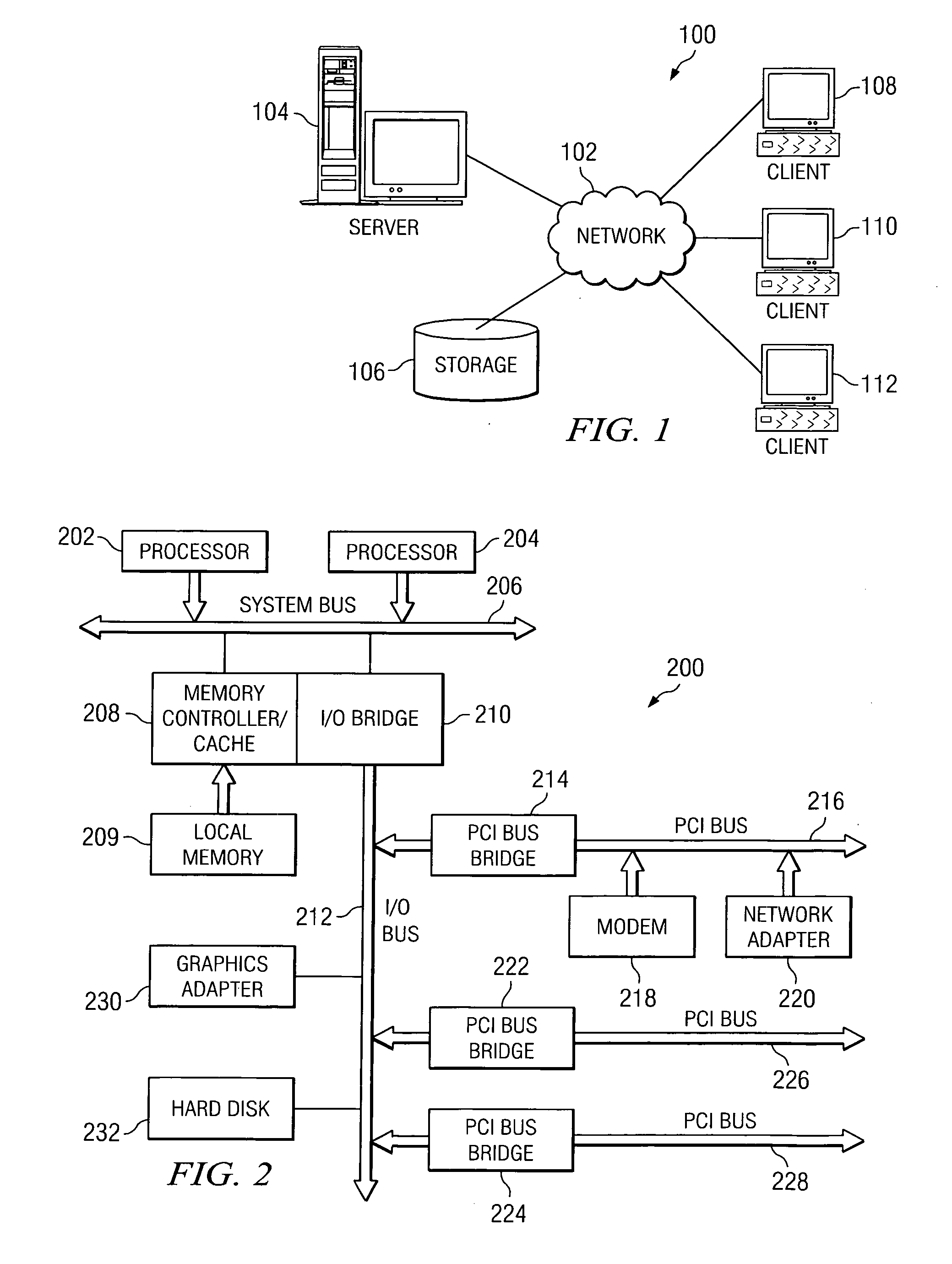
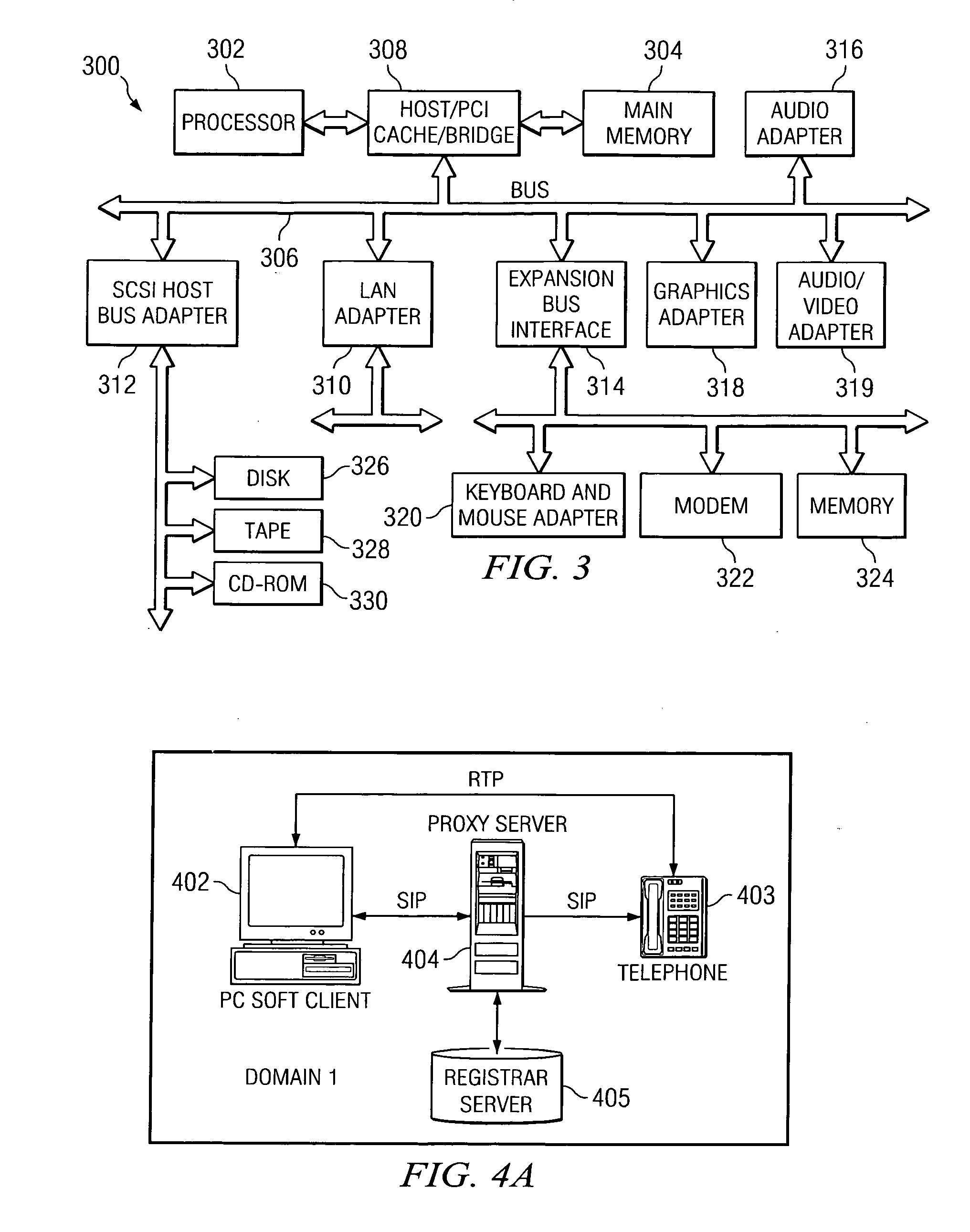
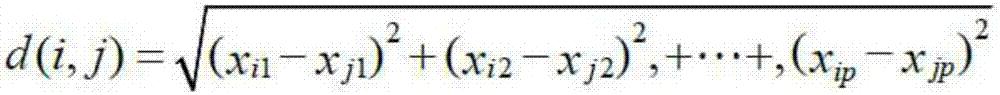Patents
Literature
57 results about "Post-condition" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
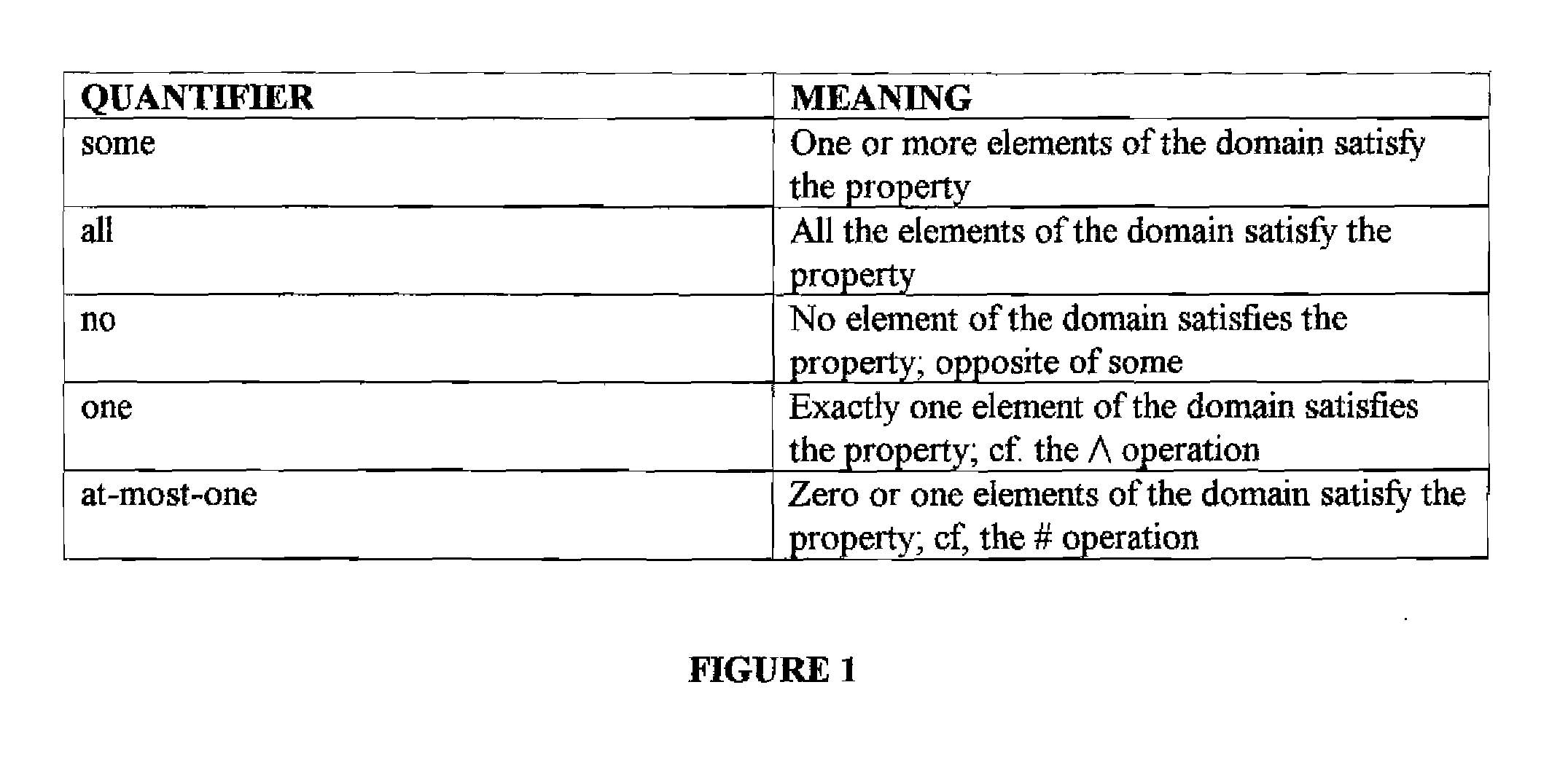
In computer programming, a postcondition is a condition or predicate that must always be true just after the execution of some section of code or after an operation in a formal specification.
Software analyzer
InactiveUS20060150160A1Minimizing chanceHigh precisionError detection/correctionSpecific program execution arrangementsValue setMachine instruction
It is possible to identify pre- and post-conditions on a set of machine instructions by determining and analyzing possible value sets for variables and expressions. Stepping forward and backward through the set of instructions and tracking value sets at all points of reference allows for the value sets to be maximally restricted, which, in turn, gives an indication of allowed domains for different variables. These domains can be used to derive pre- and post-conditions for the set of instructions.
Owner:SOFCHECK
Large-scale self-adaptive composite service optimization method based on multi-agent reinforced learning
InactiveCN103248693AAdd coordinatorMeet individual needsTransmissionComposite servicesCombinatorial optimization
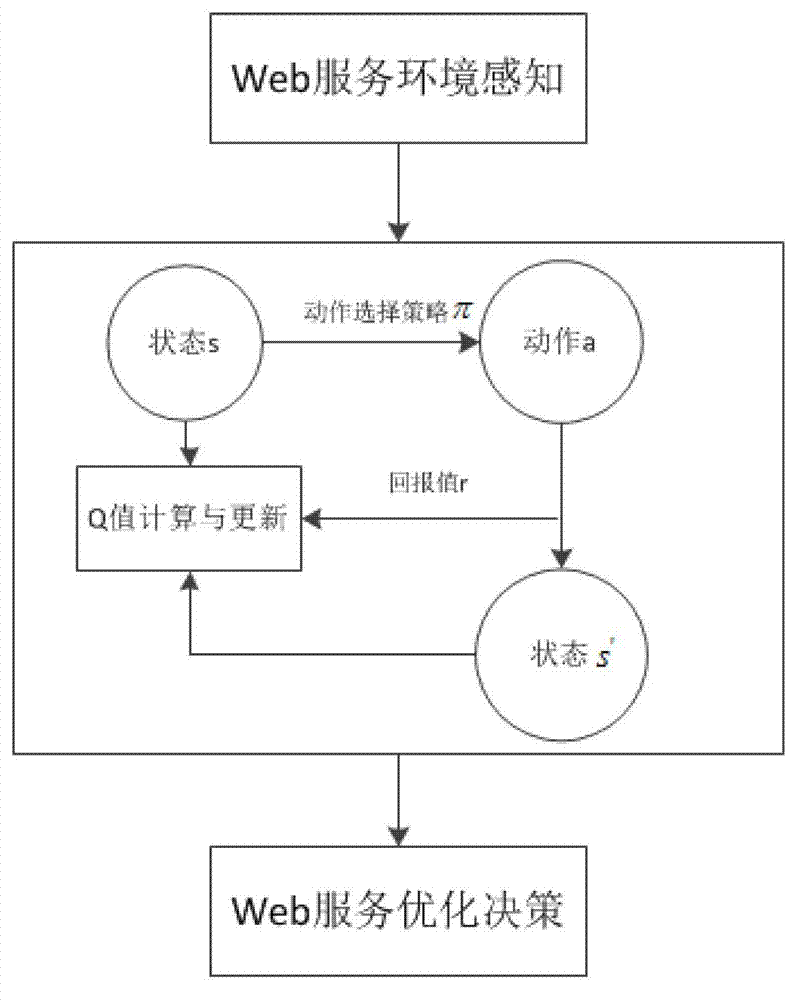
The invention discloses a self-adaptive composite service optimization method based on multi-agent reinforced learning. The method combines conceptions of the reinforced learning and agents, and defines the state set of reinforced learning to be the precondition and postcondition of the service, and the action set to be the Web service; parameters for Q learning including the learning rate, discount factors and Q value in reinforced learning are initialized; each agent is used for performing one composite optimizing task, and can perceive the current state, and select the optimal action under the current state as per the action selection strategy; the Q value is calculated and updated as per the Q learning algorithm; before the Q value is converged, the next round learning is performed after one learning round is finished, and finally the optimal strategy is obtained. According to the method, the corresponding self-adaptive action strategy is worked out on line as per the environment change at the time, so that higher flexibility, self-adaptability and practical value are realized.
Owner:SOUTHEAST UNIV
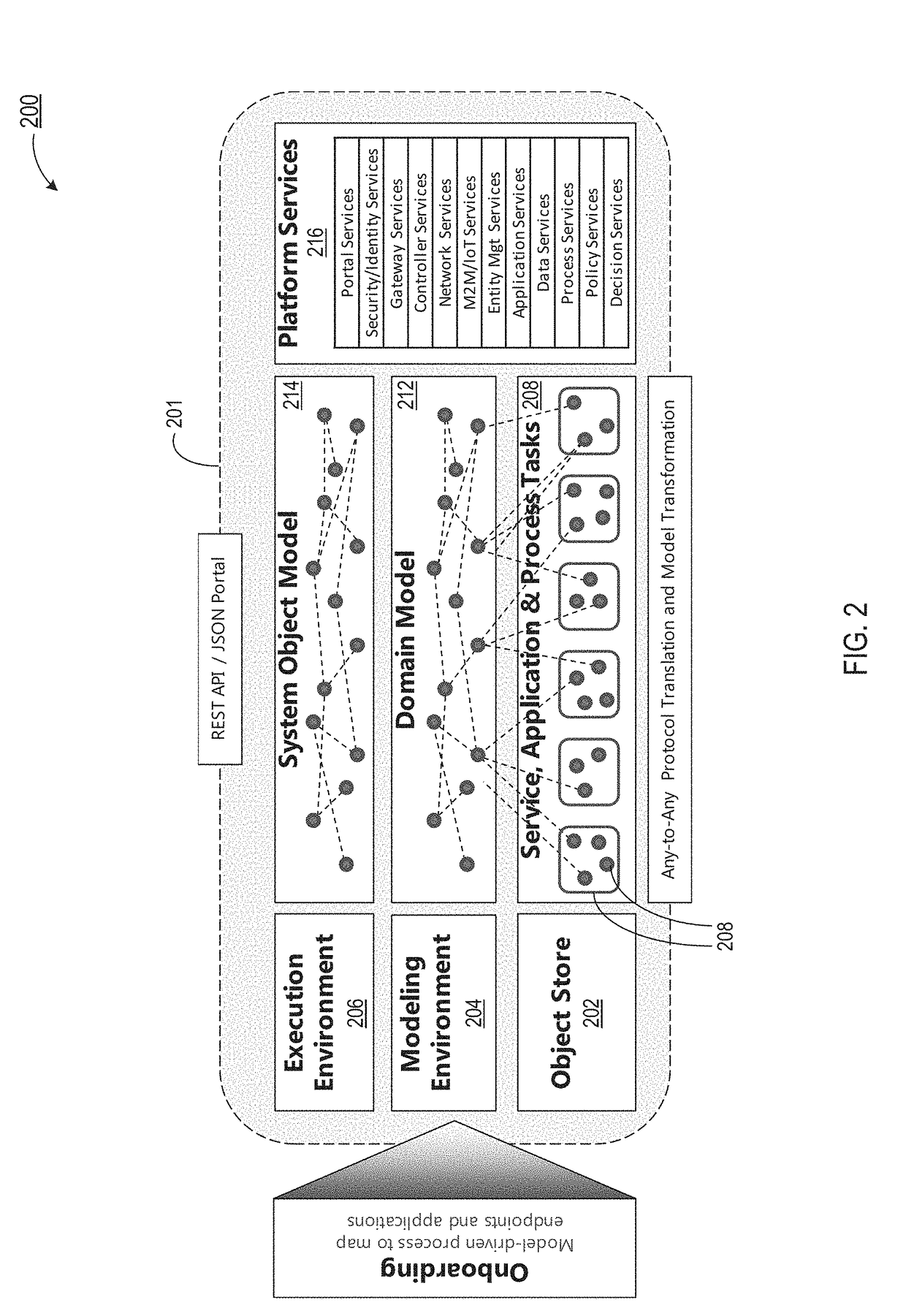
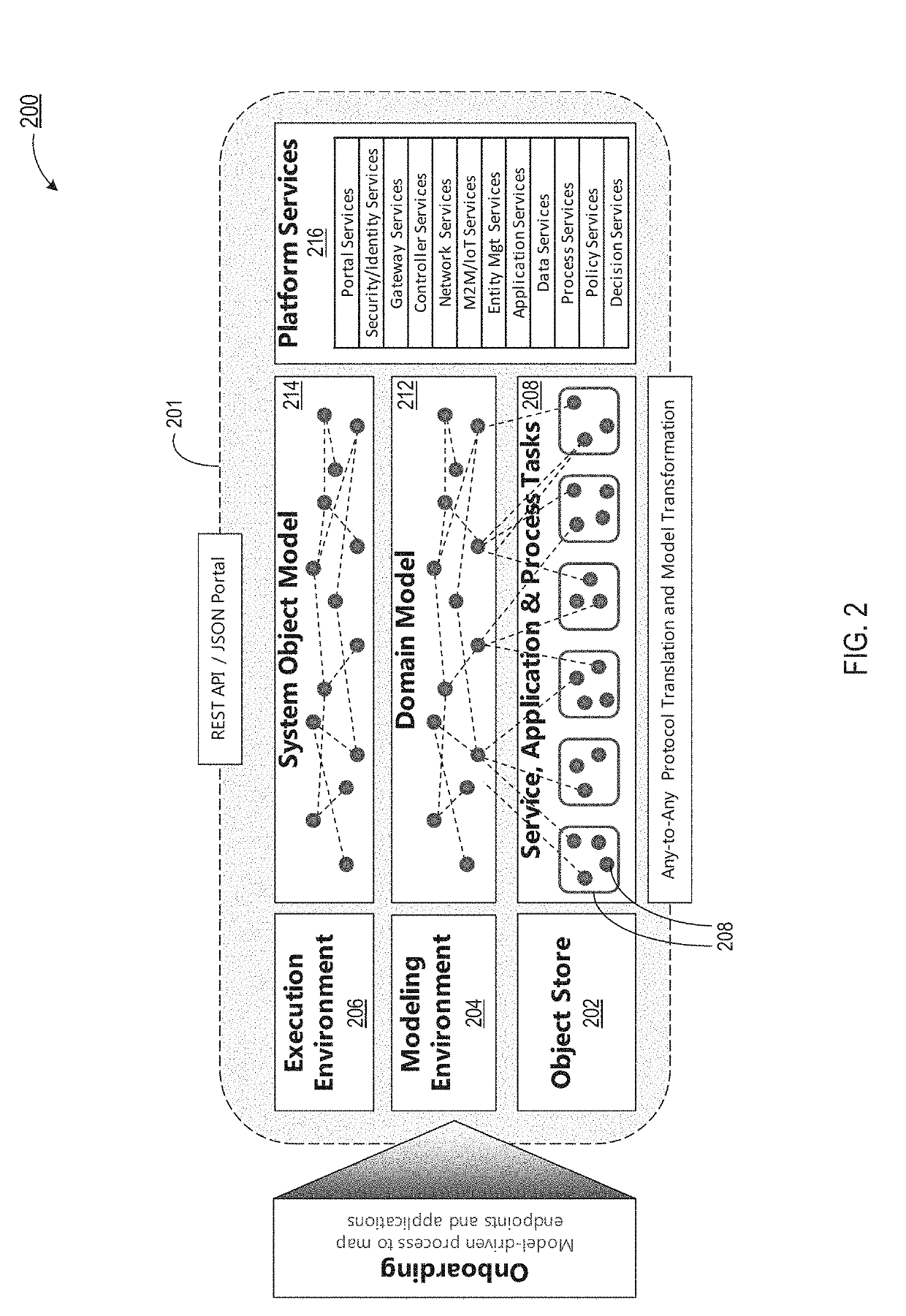
Systems and methods for domain-driven design and execution of modular and dynamic services, applications and processes
ActiveUS20170323089A1Object oriented databasesSoftware maintainance/managementObject basedModularity
A context of one or more interactions is determined. Base objects are transformed into interpreted objects by interpreting the base objects based on evaluation of the context, and by resolving references of the base objects relative to domain model types and concepts, each of the base objects modeled using a same declarative modeling language, the same declarative modeling language enabling transitions between the interpreted objects, at least one of the interpreted objects including at least one post-condition providing hooks for transition policies which allow the at least one of the interpreted objects to be logically chained in a non-linear process. Transitioning between at least two of the interpreted objects by chaining the at least two interpreted objects based on a particular post-condition of a particular interpreted object to create at least a portion of a particular non-linear process. At least a portion of the particular non-linear process is executed.
Owner:ENTERPRISEWEB
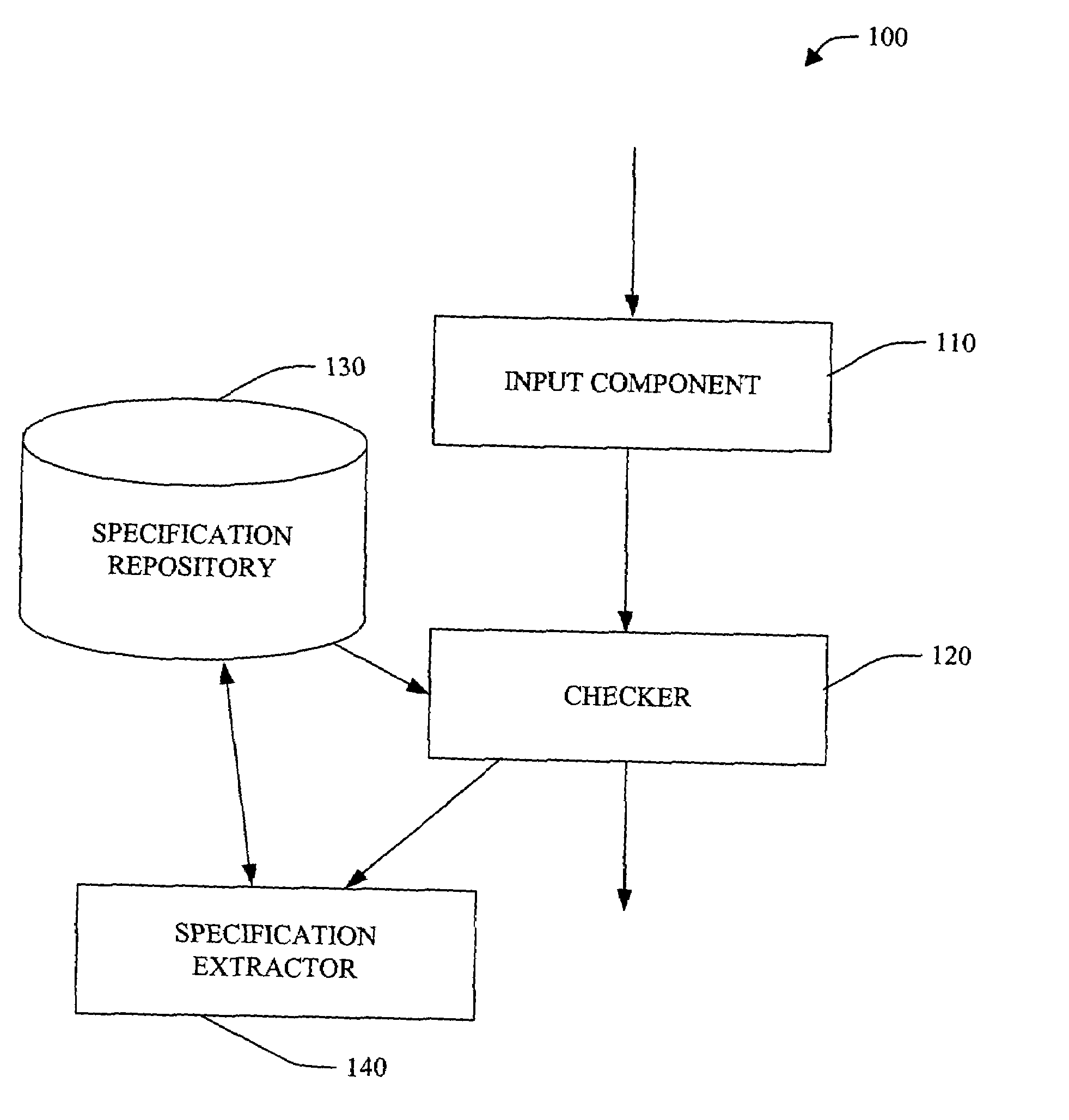
Persisted specifications of method pre-and post-conditions for static checking
ActiveUS20050066319A1Easy to checkFacilitate static checkingSoftware engineeringSpecific program execution arrangementsObject codeFinite-state machine
A system and method employing pre- and / or post-condition(s) specified at a source code level and persisted (e.g., in associated object code and / or a specification repository) facilitating static checking of the object code is provided. The system and method are based, at least in part, upon a framework that employs rules for using an interface to be recorded as declarative specifications in an existing language. The system can employ a range of annotations that allow a developer to specify interface rule(s) with varying precision. At the simplest end of the range, a specifier can mark those methods that allocate and release resource(s). A specifier can also limit the order in which an object's methods may be called to the transitions of a finite state machine. At the more complex end of the range, a specifier can give a method a plug-in pre- and post condition, which is arbitrary code that examines an object's current state and a static approximation of the method's actuals, decides whether the call is legal and returns the object's state after the call.
Owner:MICROSOFT TECH LICENSING LLC
Persisted specifications of method pre-and post-conditions for static checking
ActiveUS7421680B2Easy to checkFacilitate static checkingSoftware engineeringSpecific program execution arrangementsObject codeFinite-state machine
A system and method employing pre- and / or post-condition(s) specified at a source code level and persisted (e.g., in associated object code and / or a specification repository) facilitating static checking of the object code is provided. The system and method are based, at least in part, upon a framework that employs rules for using an interface to be recorded as declarative specifications in an existing language. The system can employ a range of annotations that allow a developer to specify interface rule(s) with varying precision. At the simplest end of the range, a specifier can mark those methods that allocate and release resource(s). A specifier can also limit the order in which an object's methods may be called to the transitions of a finite state machine. At the more complex end of the range, a specifier can give a method a plug-in pre- and post condition, which is arbitrary code that examines an object's current state and a static approximation of the method's actuals, decides whether the call is legal and returns the object's state after the call.
Owner:MICROSOFT TECH LICENSING LLC
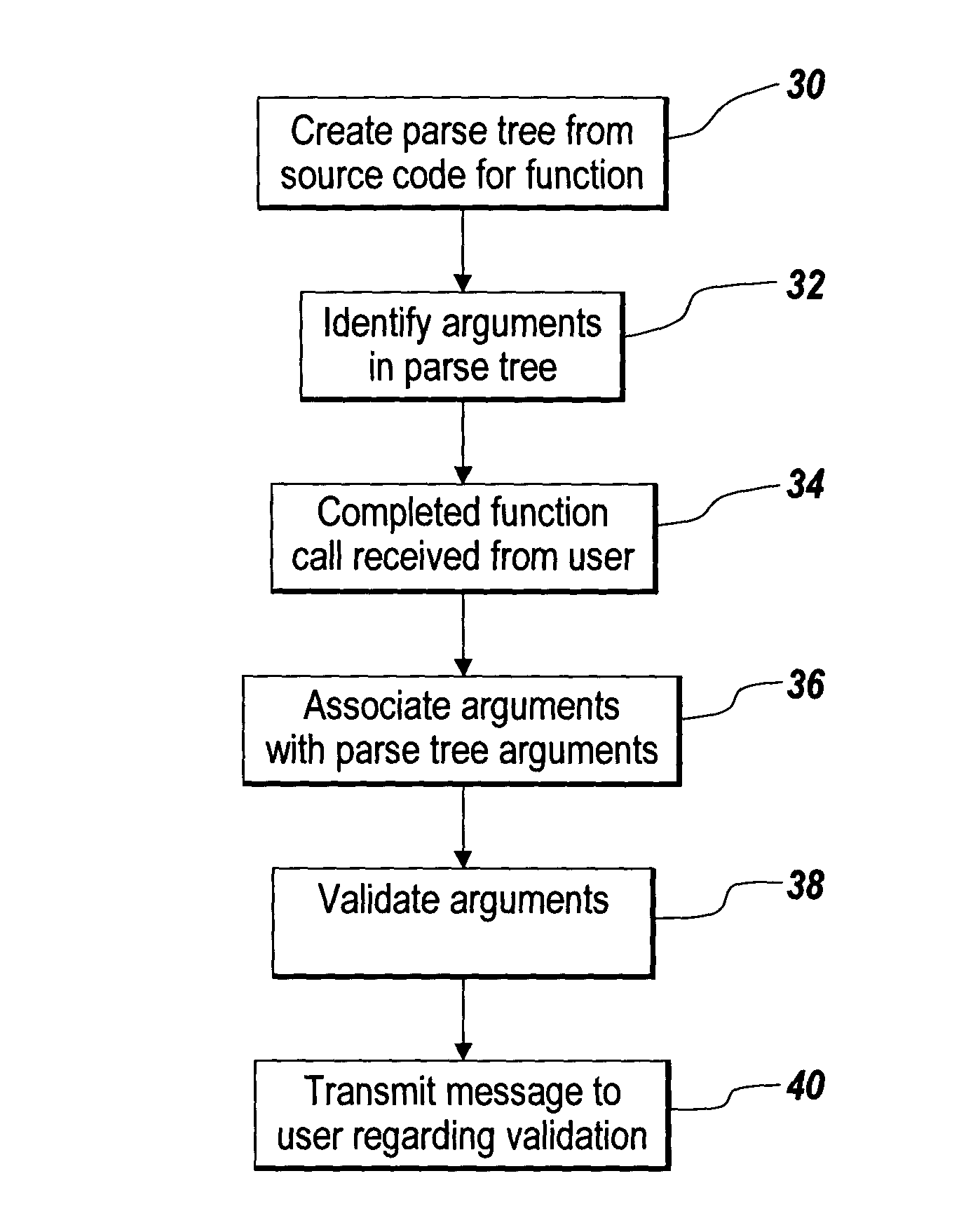
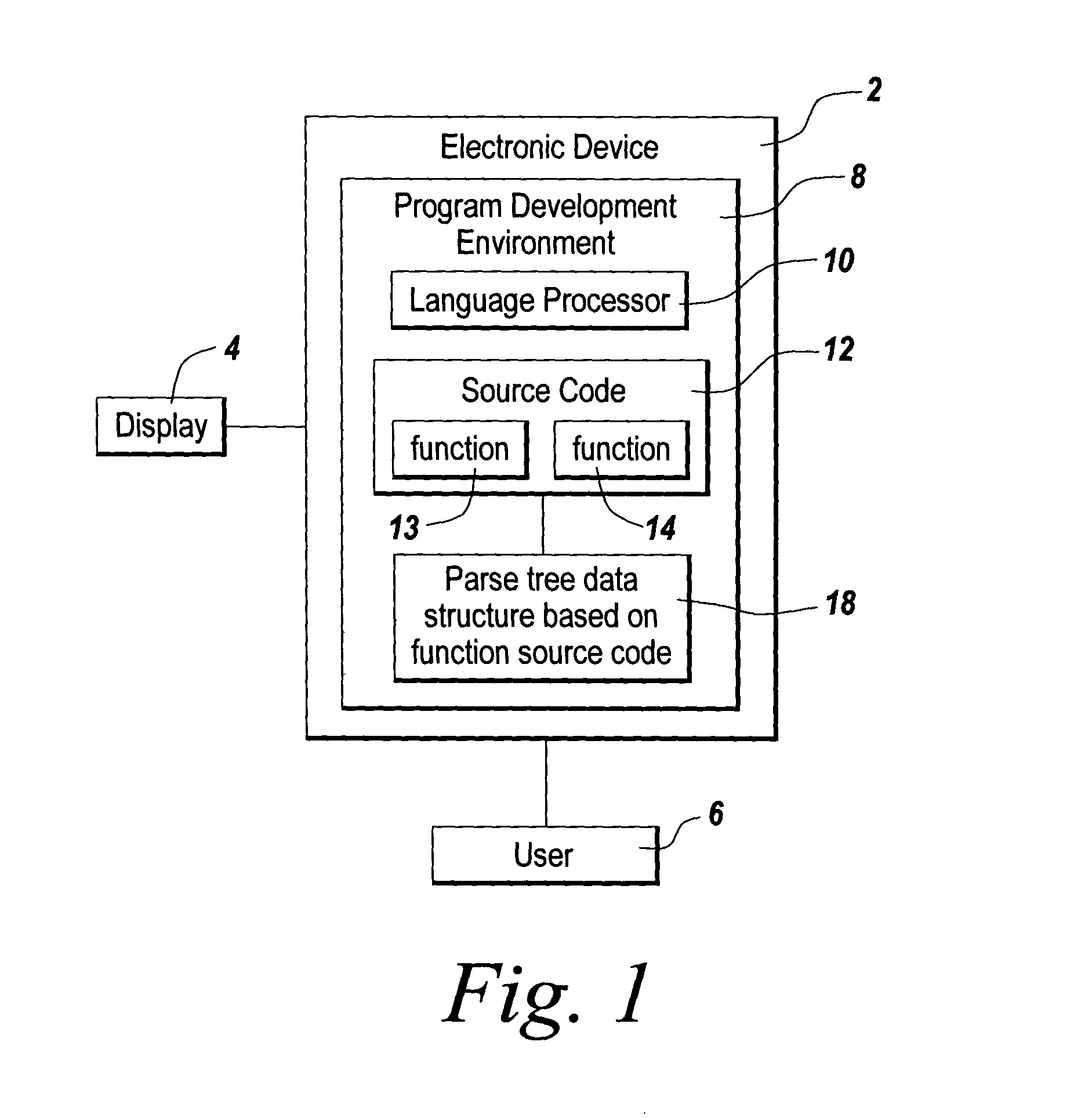
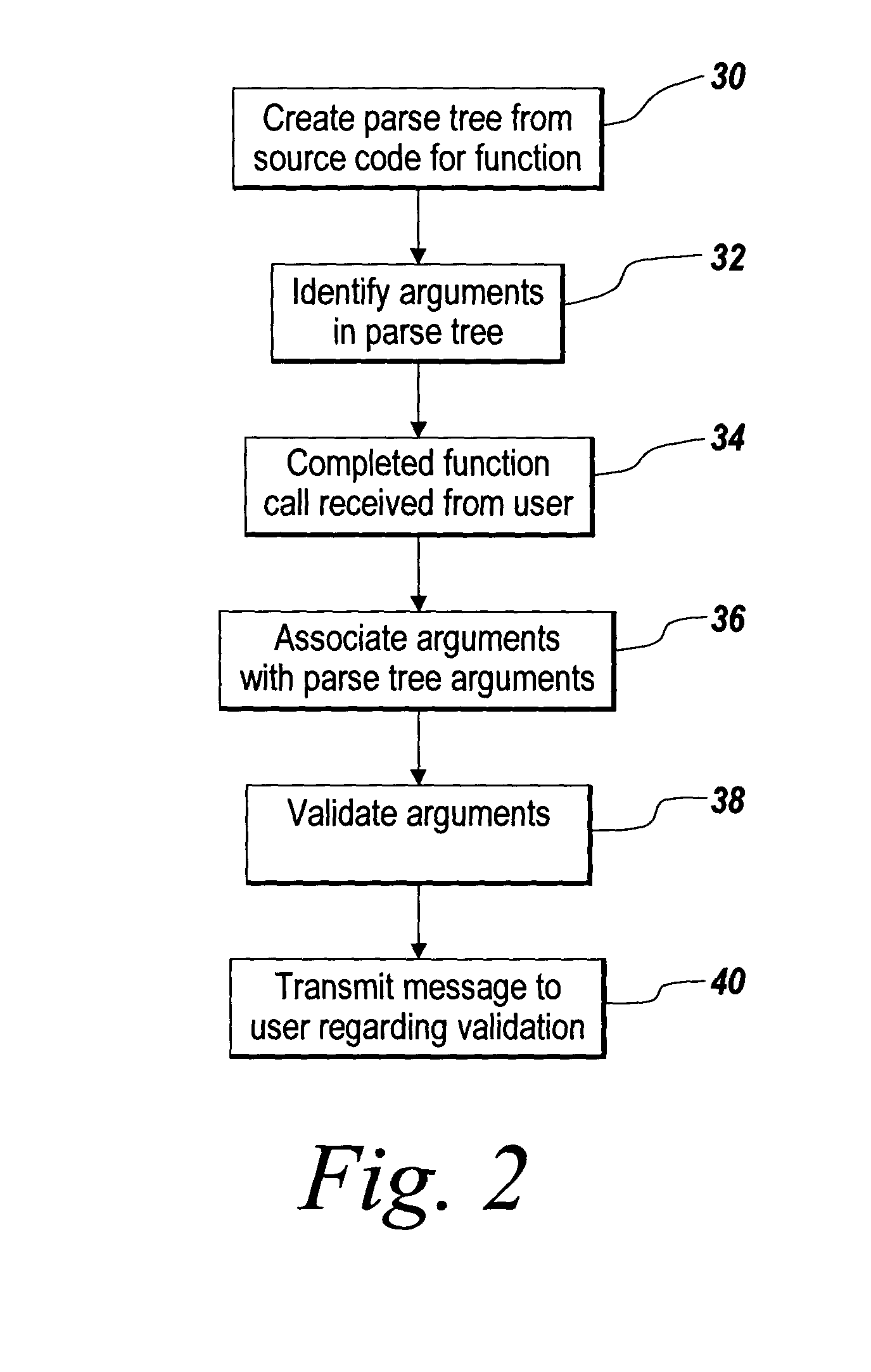
Method of providing interactive usage descriptions based on source code analysis
A method of dynamically analyzing source code to generate usage hints for a user performing program editing is disclosed. The functions in a collection of source code being edited by a user are processed so as to generate a parse tree data structure for each function called. The incoming and outgoing arguments in the parse tree are identified. Subsequently, a user editing code calls the function and either completely or incompletely enters the arguments as part of the function called. Input arguments are identified and associated with the corresponding argument in the parse tree for the function. Relevant preconditions and post-conditions of the surrounding nodes corresponding to the current location are analyzed. Usage hints are provided for the completion of the function call. Arguments for a completed function call argument entered by the user are validated. Error messages are delivered in the event of an invalid call.
Owner:THE MATHWORKS INC
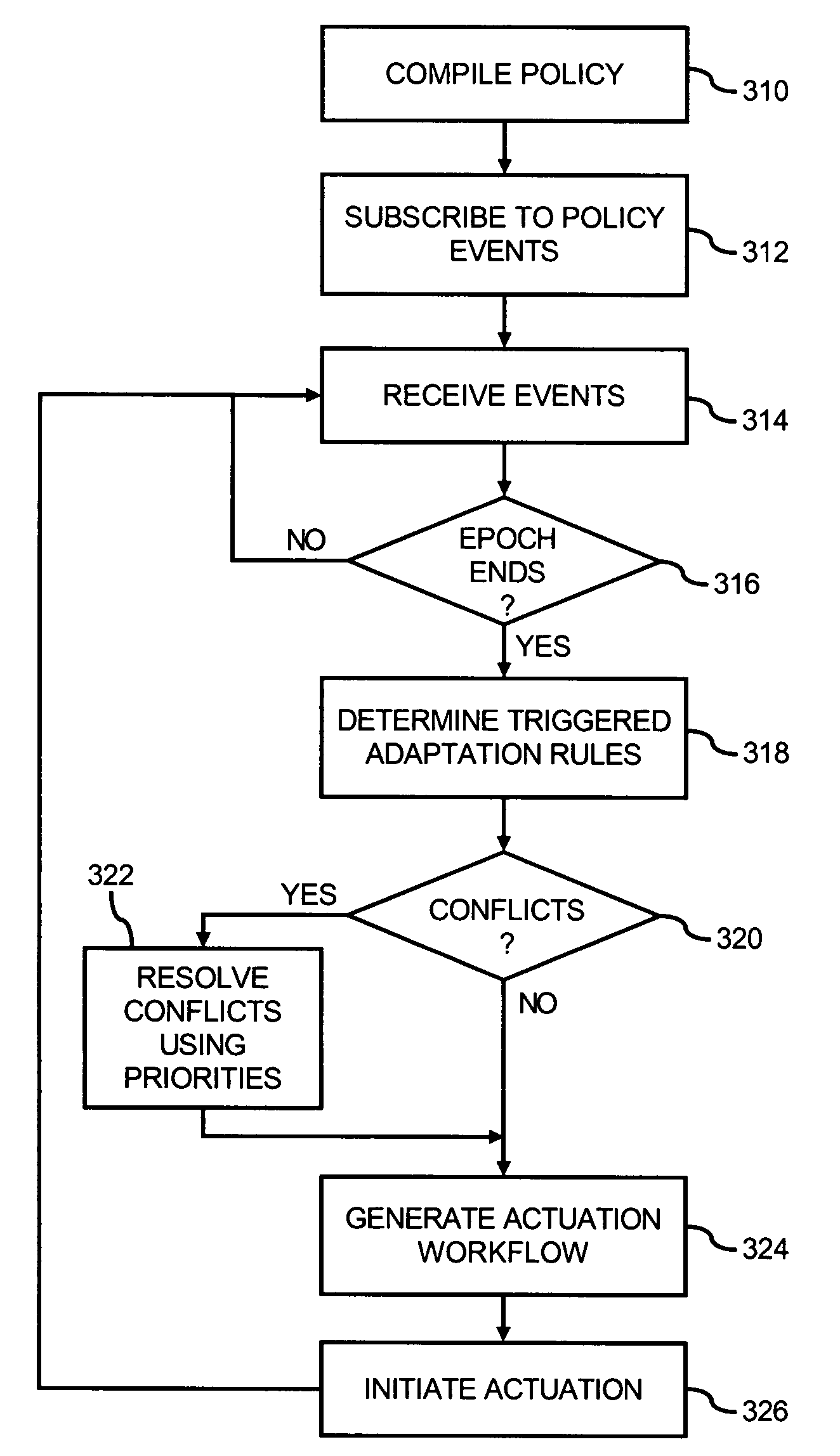
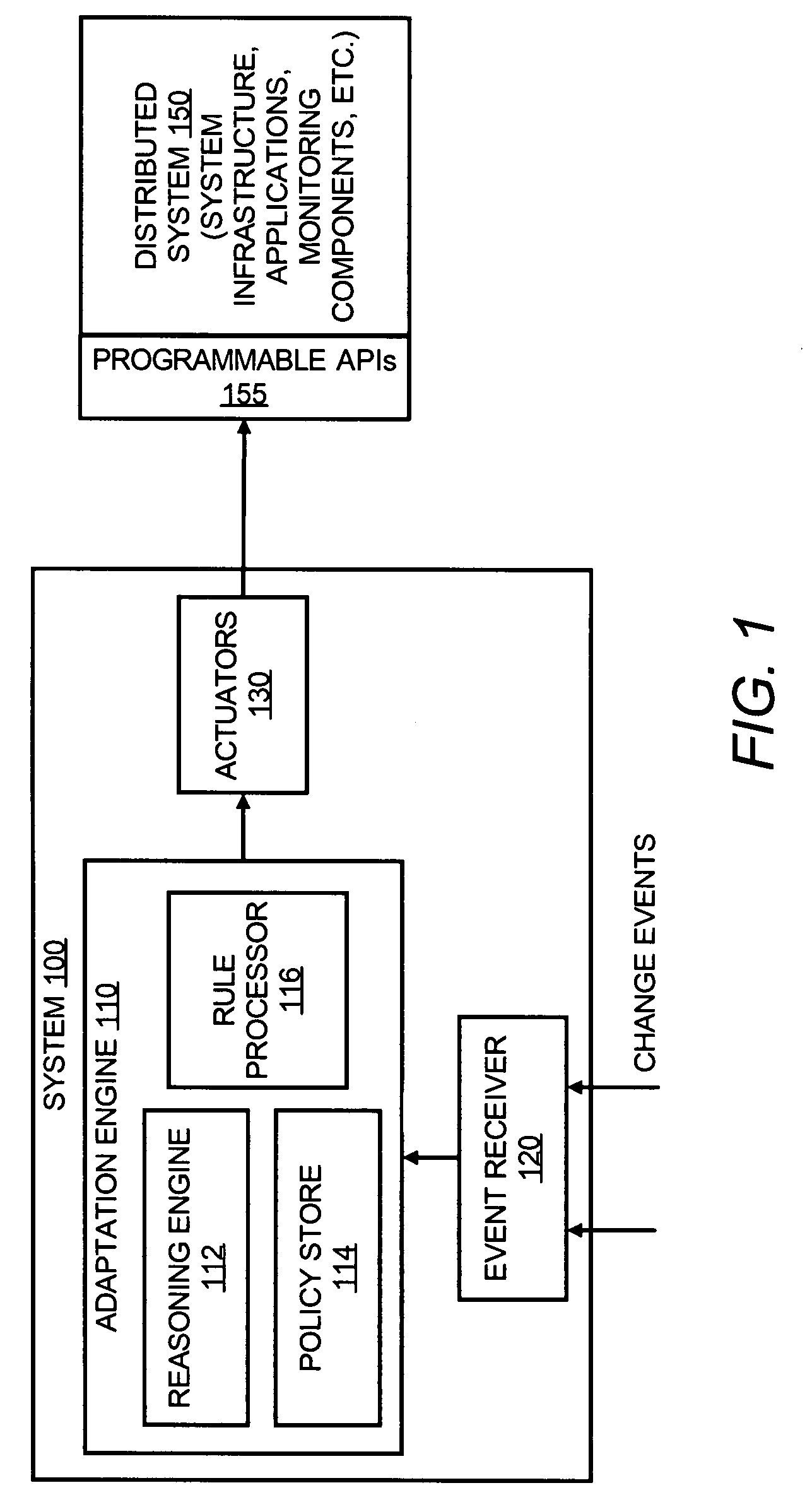
Change management in a distributed system based on triggered policy rules
A method for providing change management in a distributed system is provided. The method includes compiling a policy for change management in the distributed system, the policy includes at least one policy rule based on an event-condition-action (ECA) framework with a pre-condition and a post-condition to an action in the policy rule, wherein the pre-condition is separate from a condition of the policy rule and indicates a prior condition in the distributed system that enables the action, and the post-condition indicates a subsequent condition in the distributed system that results from the action; receiving at least one event indicating a change in the distributed system; determining that the at least one received event triggers the at least one policy rule; generating a workflow to manage the change in the distributed system based on the at least one triggered policy rule; and initiating one or more actuators in the distributed system to dynamically configure or deploy components in the distributed system to execute the workflow.
Owner:HEWLETT PACKARD DEV CO LP
Cryptographically secure financial instruments
InactiveUS20180204284A1Enhance financial instrumentsIncrease computational costFinanceCommunication with homomorphic encryptionPlaintextData set
Systems, methods and financial instruments enhanced with secure computation. A financial instrument management system is implemented with secure computation capabilities, respecting the privacy and secrecy rights during computation of the information contained within financial instruments, external datasets and / or secure computation programs. Automatic conversion and aggregation of conventional financial instruments is also disclosed. Furthermore, secure computation programs can be certified with mathematical proofs about very advantageous and valuable properties such as their correct termination, conformance to a specification, or any other pre-conditions, post-conditions and invariants on their inputs and outputs, encrypted or in plaintext form.
Owner:CEREZO SANCHEZ DAVID
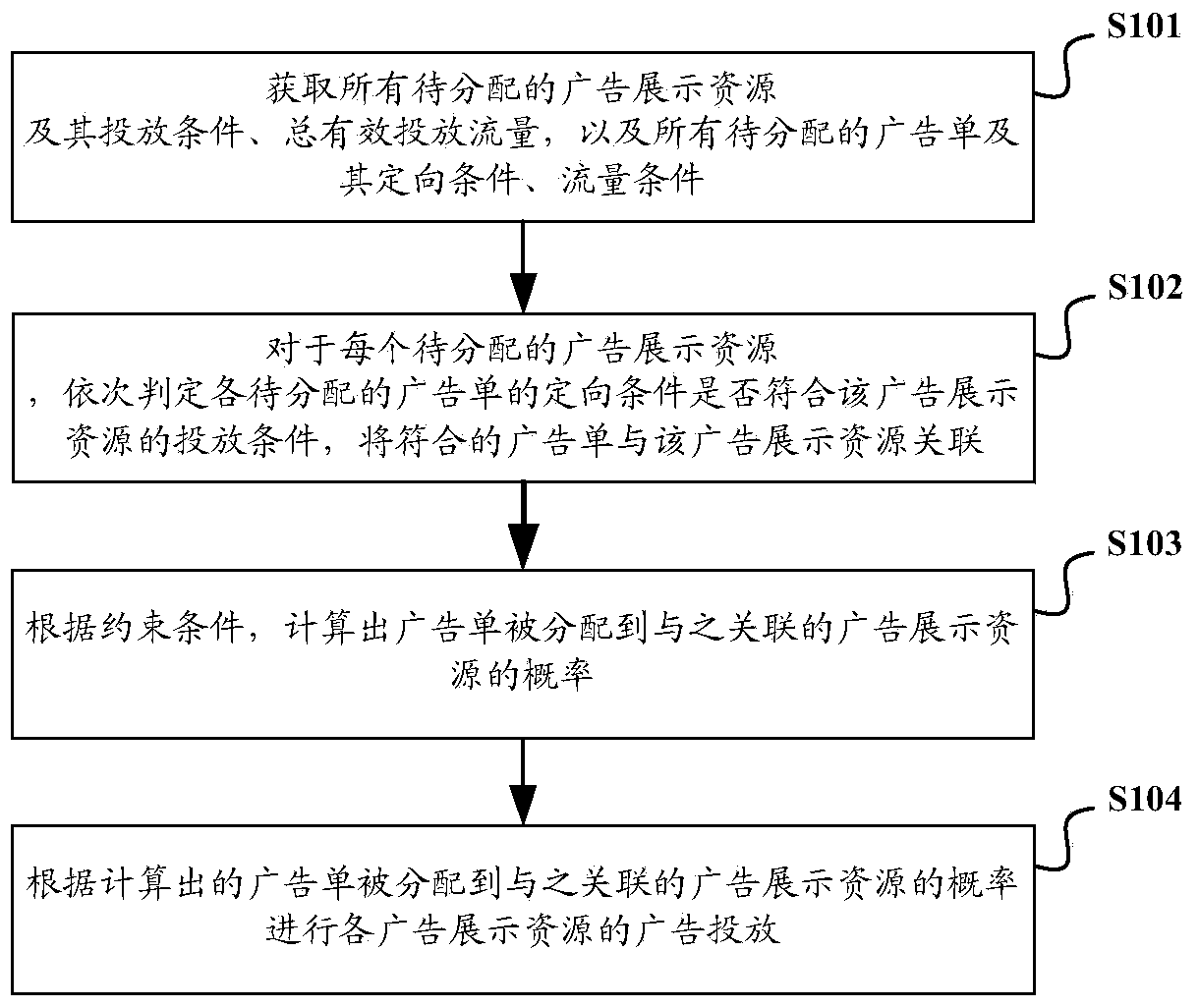
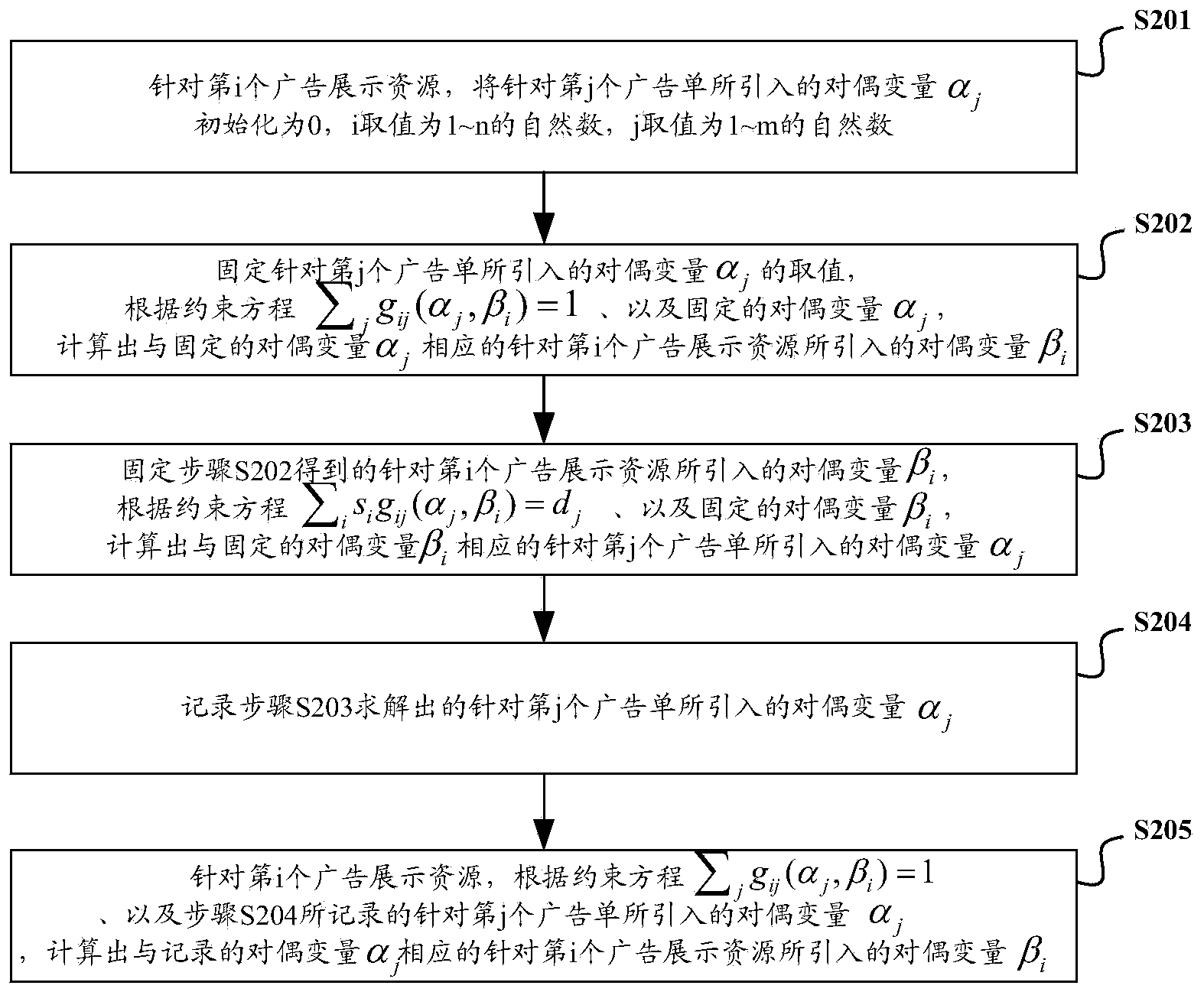
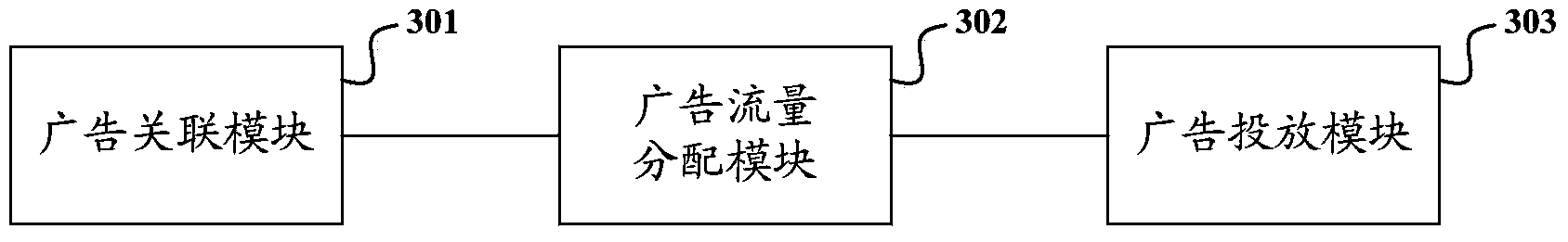
Online advertising flow distribution system and method
ActiveCN104299151AReduce allocation complexityImprove distribution efficiencyMarketingOnline advertisingPost-condition
The invention discloses an online advertising flow distribution system and method. The method includes the steps that for each advertisement display resource to be allocated, and the advertisement leaflets to be allocated and with the orientation condition conforming to the posting condition of the corresponding advertisement display resources are made to be associated with the corresponding advertisement display resources; according to the following constraint conditions, the probability that the advertisement leaflets are allocated to the advertisement display resources associated with the advertisement leaflets is worked out; for all the advertisement display resources, the sum of the posting amount of the advertisement display resources relative to the advertisement leaflets associated with the advertisement display resources is made to be not more than the total valid posting flow of the corresponding advertisement display resources; for all the advertisement leaflets, the sum of the posting amount of the advertisement display resources associated with the advertisement leaflets relative to the advertisement leaflets is made to be not less than the flow condition of the corresponding advertisement leaflets; advertisement posting of all the advertisement display resources is conducted according to the computed probability that the advertisement leaflets are allocated to the advertisement display resources associated with the advertisement leaflets. By the adoption of the online advertising flow distribution system and method, the allocation complexity of online advertising can be reduced, and allocation efficiency can be improved.
Owner:新浪技术(中国)有限公司
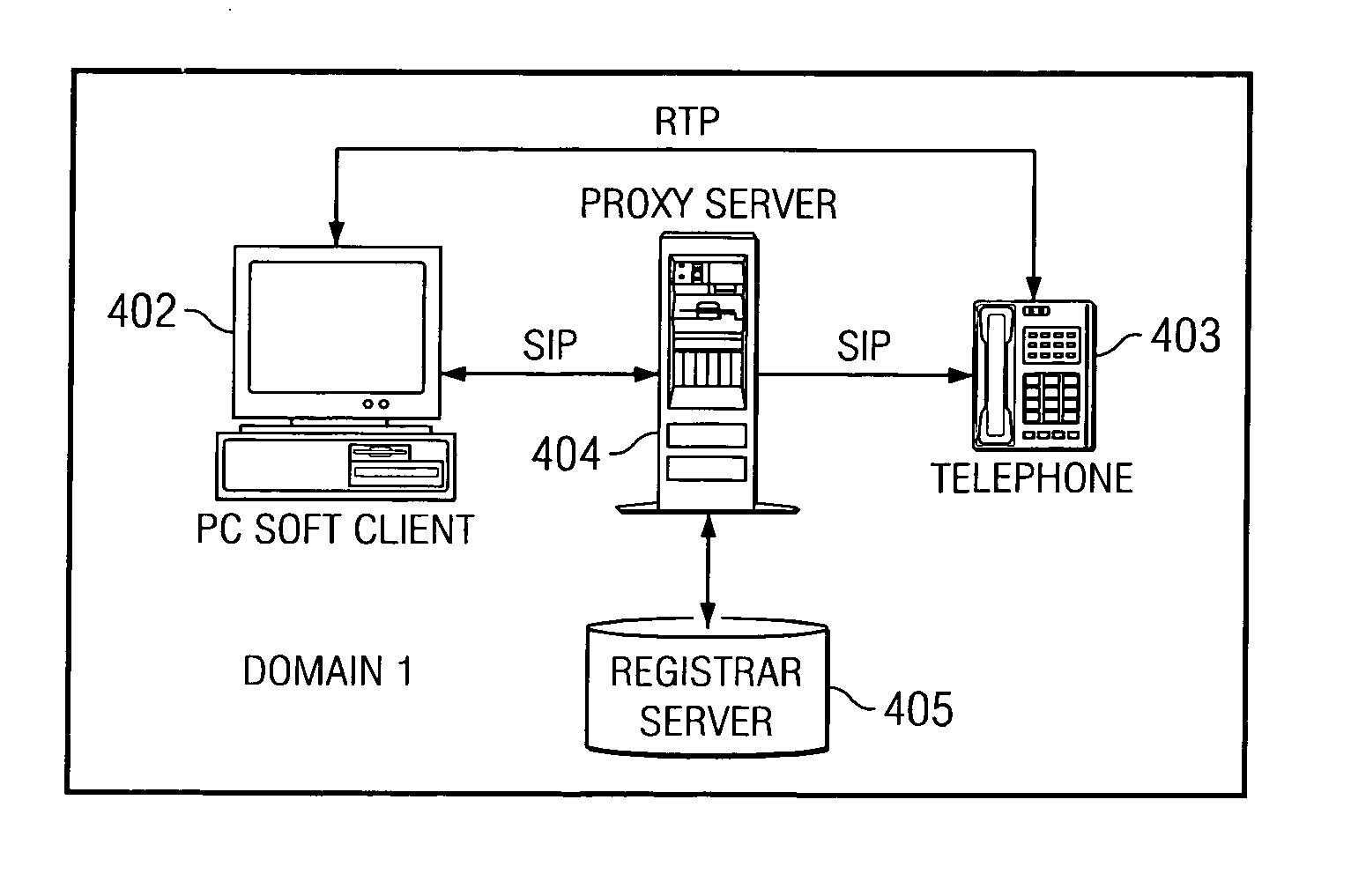
Method and apparatus for session initiation protocol application design, development, execution and integration
InactiveUS20060187902A1Data switching by path configurationNetwork connectionsSession Initiation ProtocolWeb service
A method, apparatus, and computer instructions are provided for a session initiation protocol application design, development, execution, and integration. A framework with a framework controller, an application data object, transition handlers, precondition handlers and post condition handlers is provided. When a message is received in a SIP application, the framework controller determines a state of application and parses the message to update application data by using corresponding handlers. The handlers for each state are specified in an input markup language model defined by a user externally via a Web service accessible component.
Owner:IBM CORP
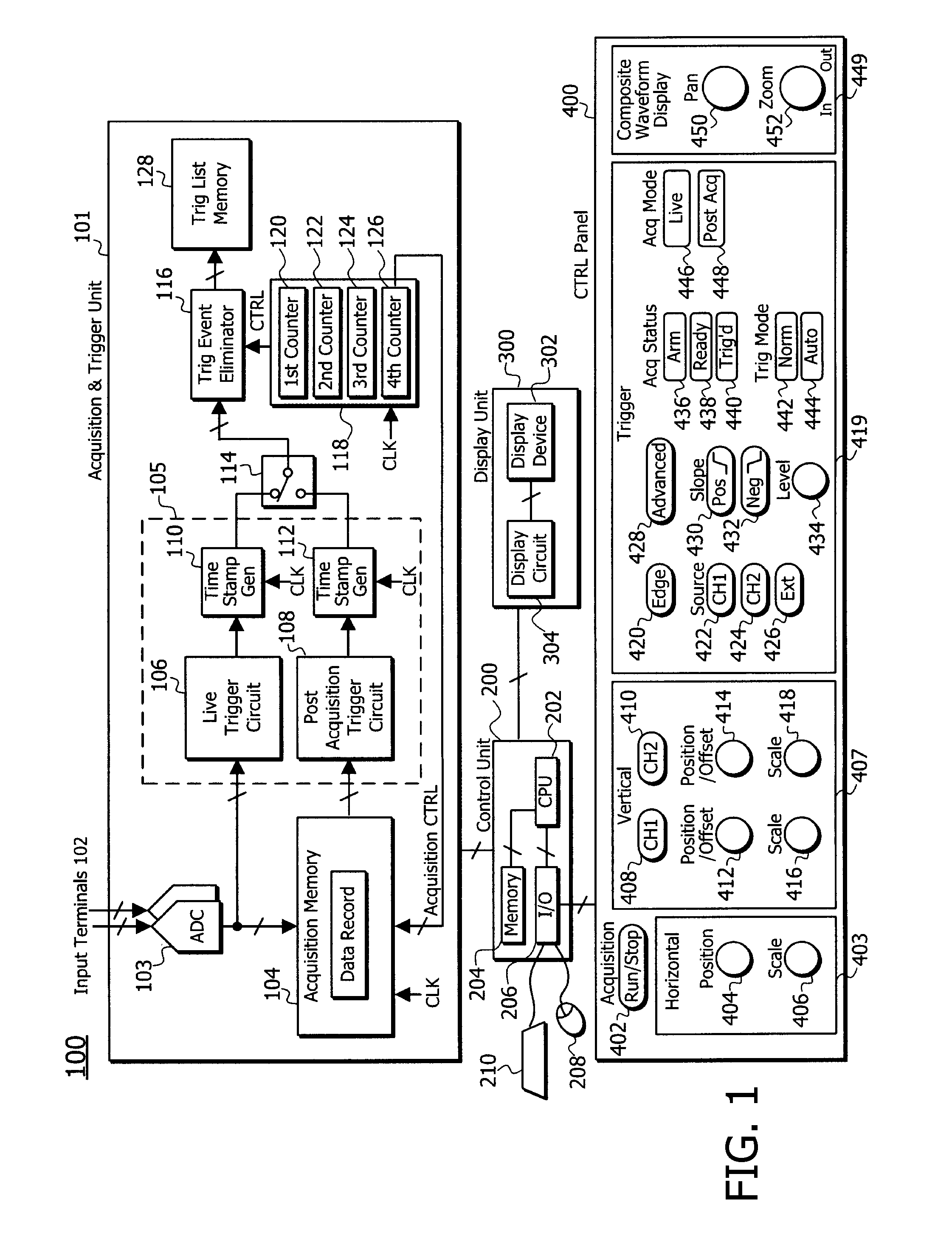
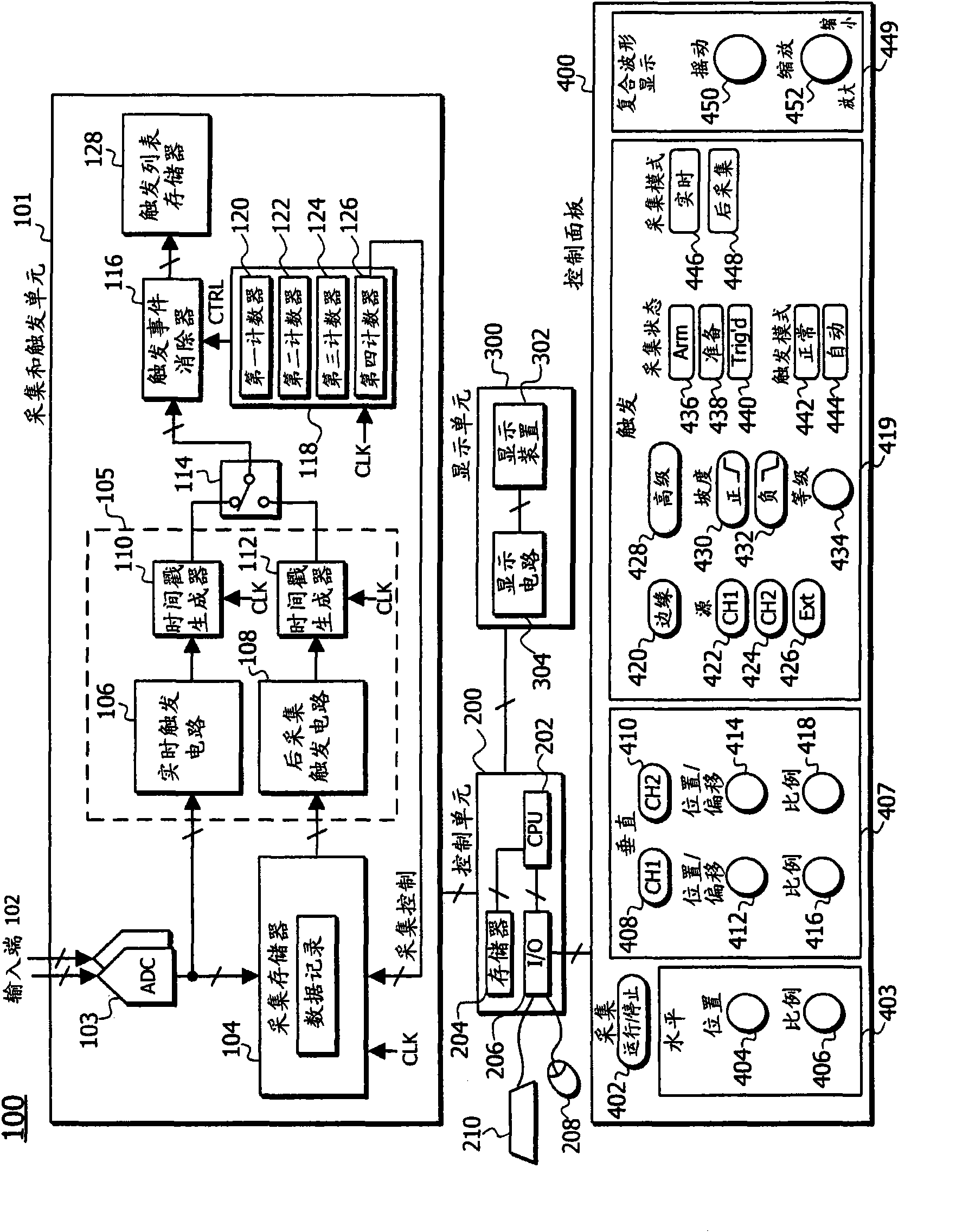
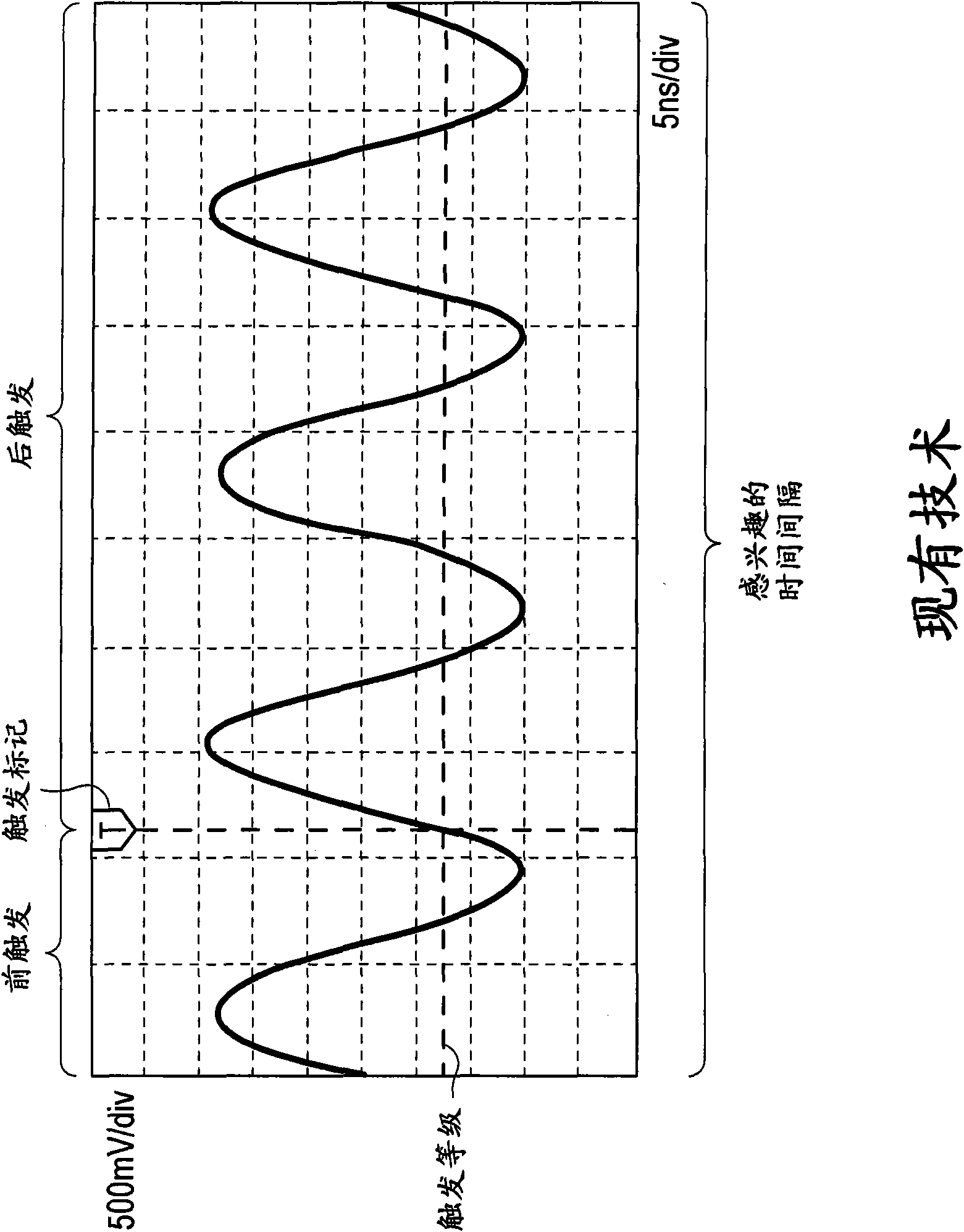
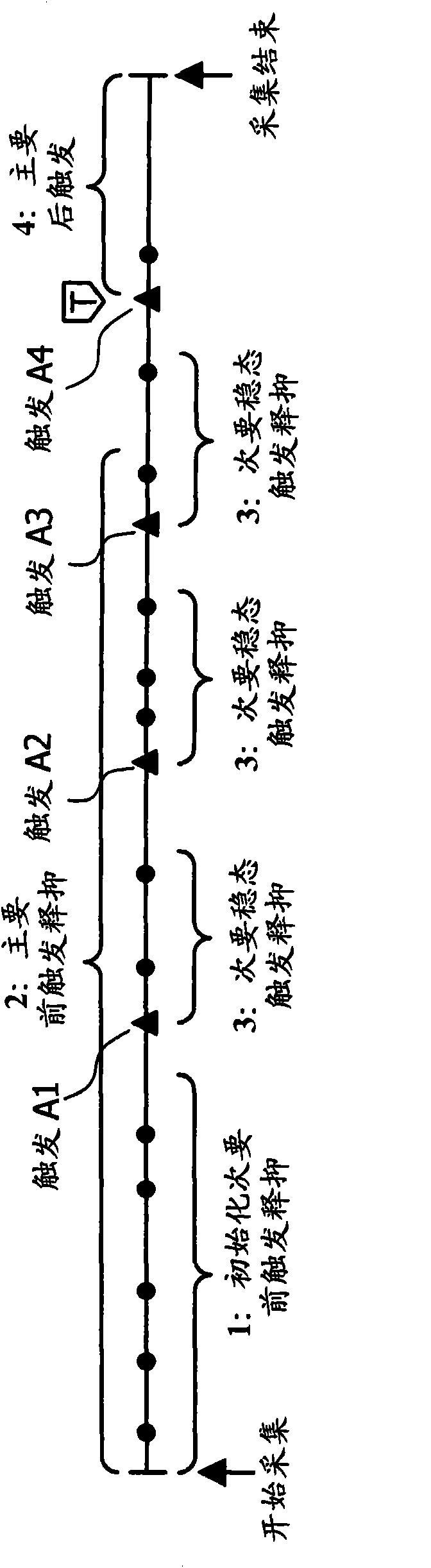
High Waveform Throughput with a Large Acquisition Memory
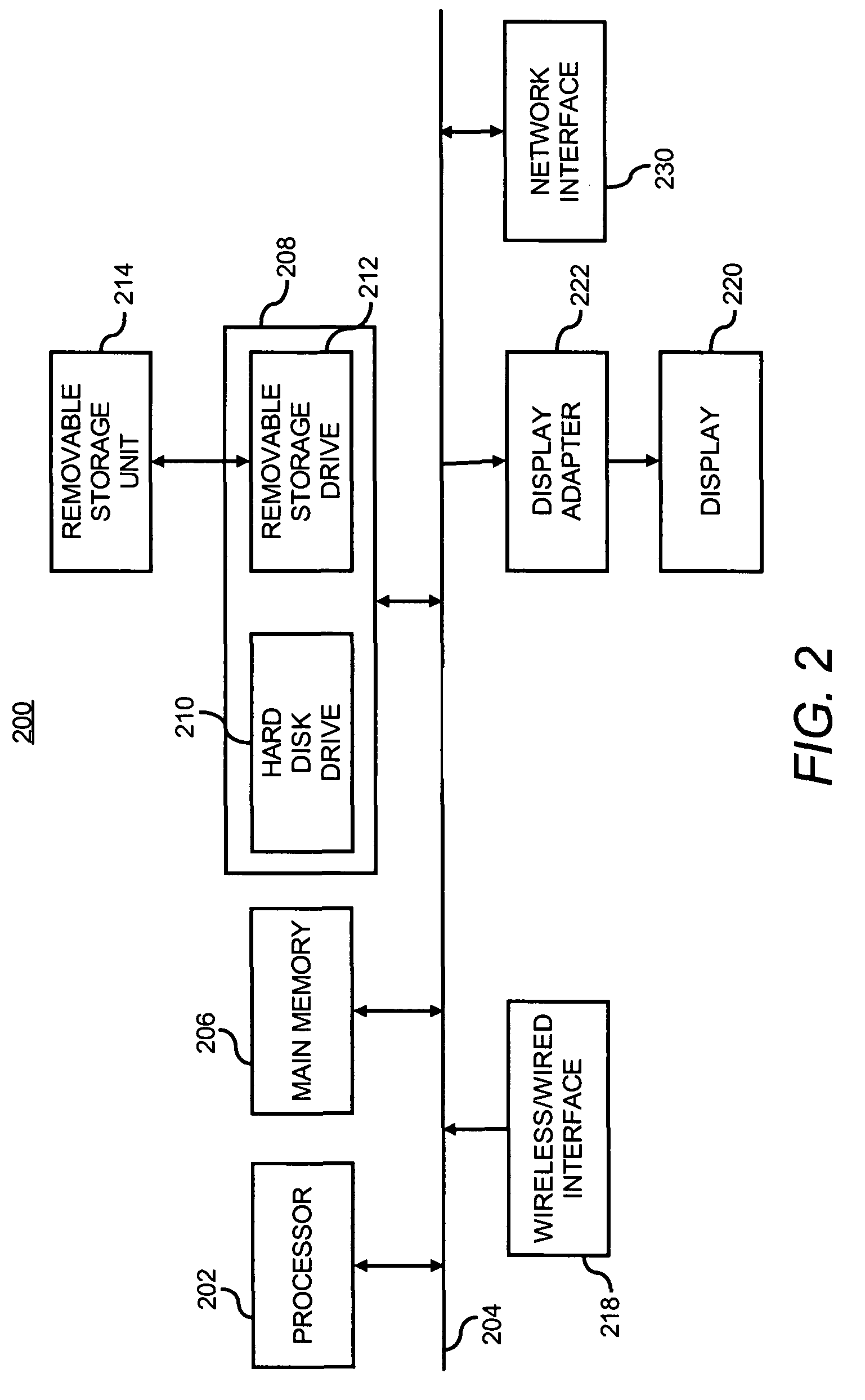
ActiveUS20110137594A1Increase chanceDigital variable displaySpecial data processing applicationsDigital dataDisplay device
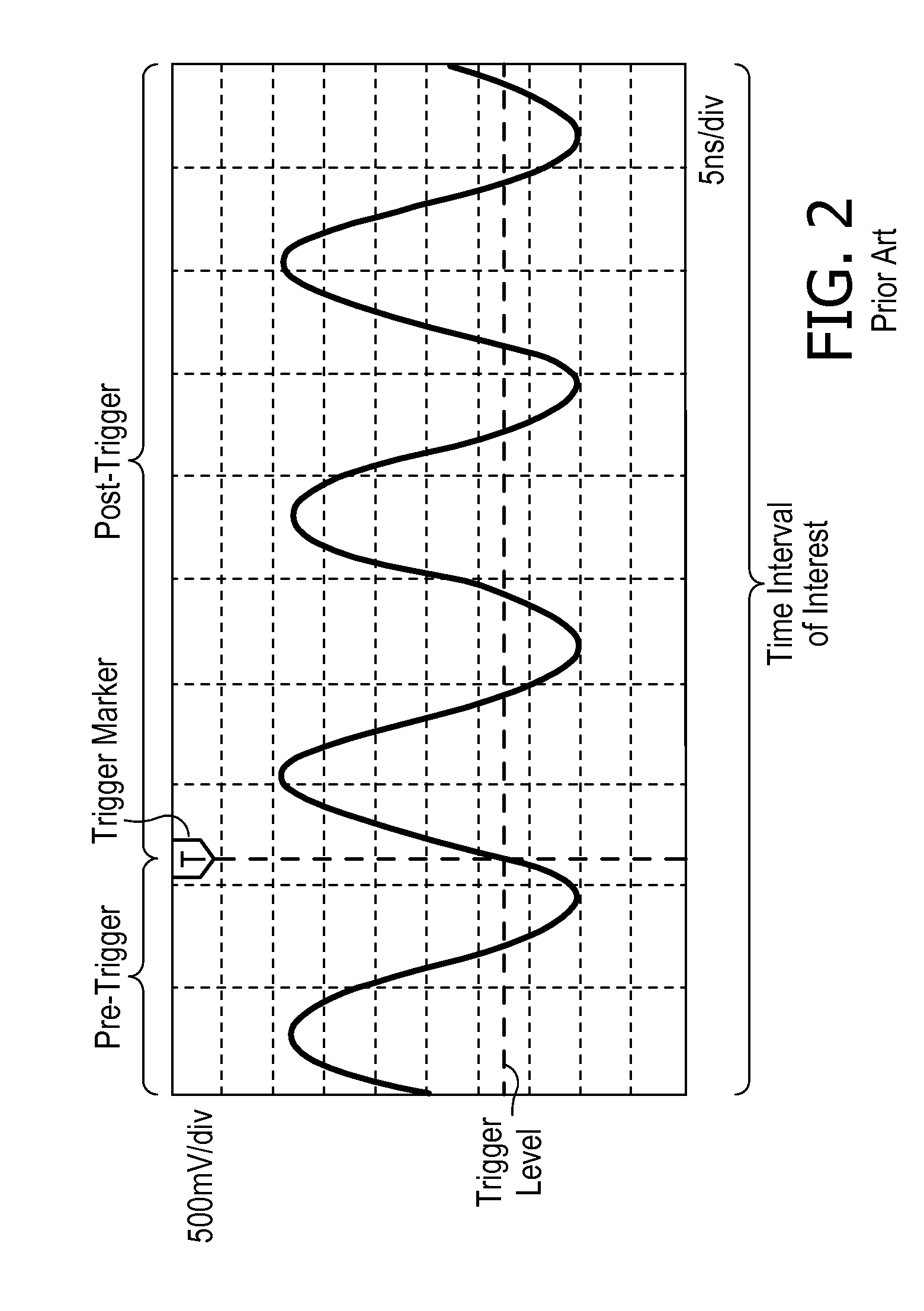
A waveform display apparatus and method displays one or more waveforms of a signal under test at high throughput while acquiring digital data of the signal under test in a large acquisition memory. A user sets a time interval of user's interest when viewing a signal under test and sets trigger criteria through a user interface. An ADC converts the signal under test into digital data that is stored in a large acquisition memory. A trigger unit detects and produces trigger events, based on a trigger, as trigger event information during one acquisition process. A trigger event eliminator may discard some of the trigger events based on pre-trigger and post-conditions set through the interface by a user. The trigger events are recorded in a trigger list as the trigger event information. A control unit locates the digital data in the acquisition memory corresponding to the trigger events in the trigger list and displays a waveform associated with the trigger event for the time interval on a display device.
Owner:TEKTRONIX INC
Preventing deadlock in a policy-based computer system
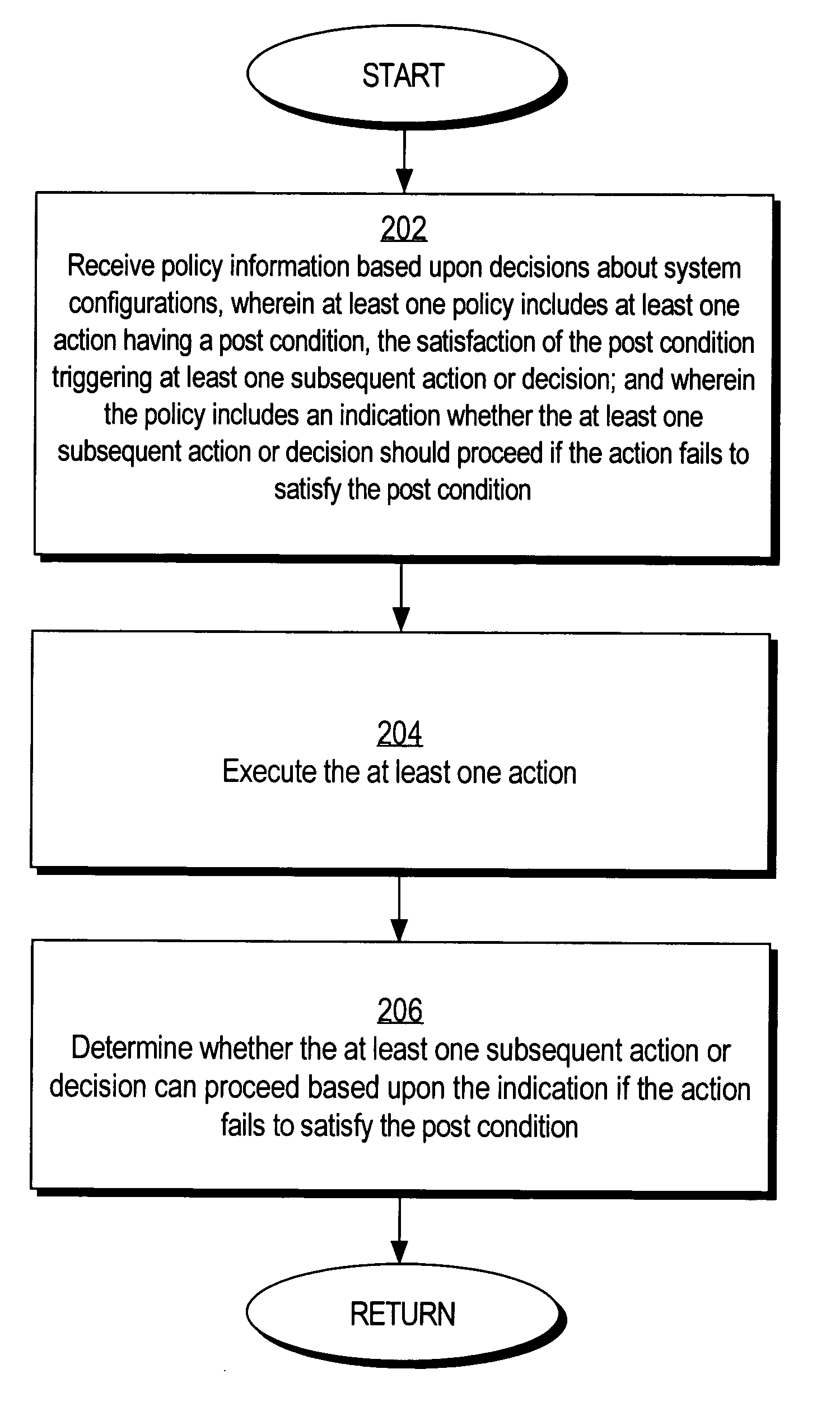
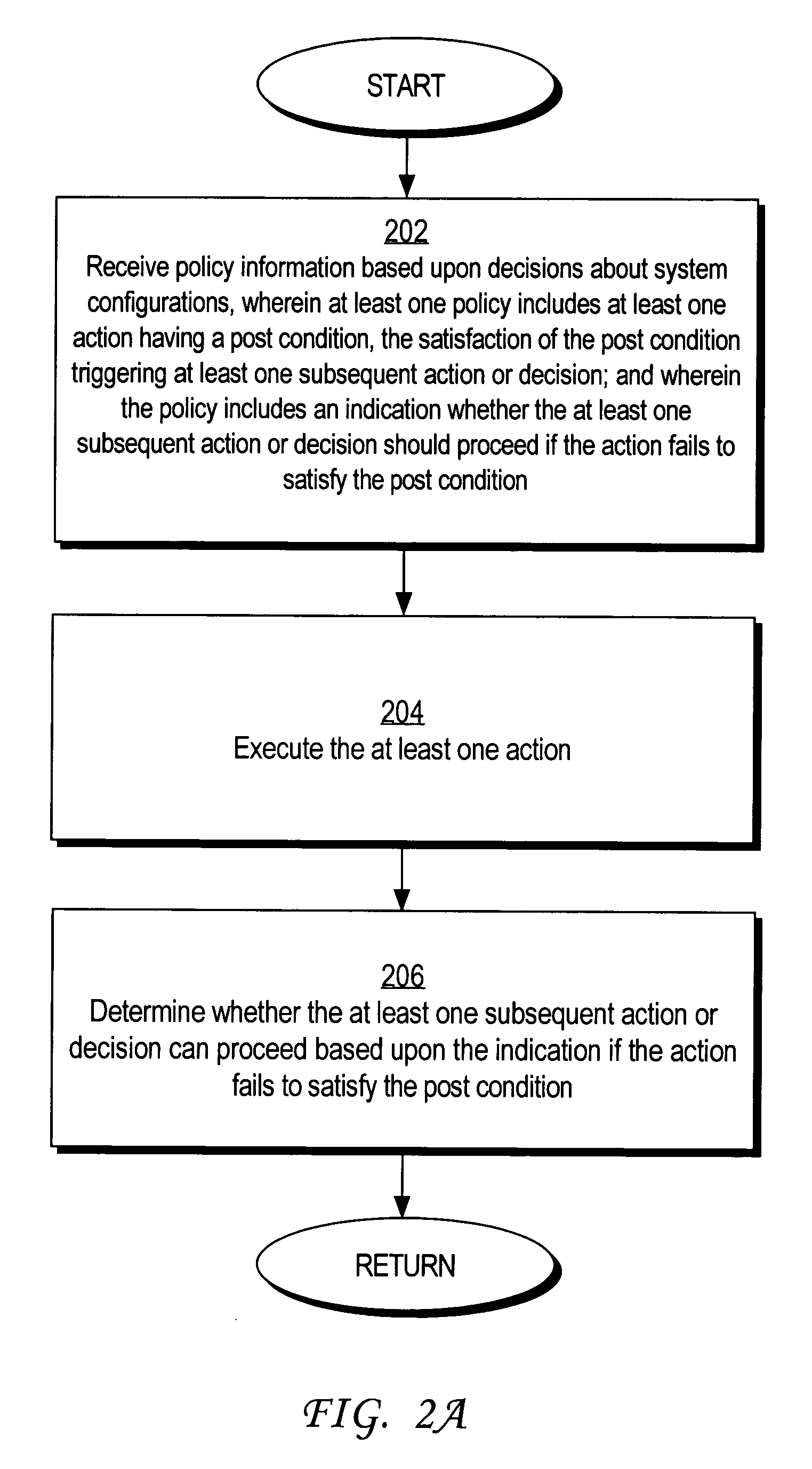
Methods and mechanisms for preventing deadlock in a policy-based computer system are disclosed. In one embodiment, the method includes various machine-implemented steps, such as a step of receiving policy information based upon decisions about system configurations. At least one policy includes at least one action that has a post condition. Satisfaction of the post condition triggers at least one subsequent action or decision. The policy includes an indication whether the at least one subsequent action or decision should proceed if the action fails to satisfy the post condition. The at least one action is executed. Then, if the action fails to satisfy the post condition, a determination is made whether the at least one subsequent action or decision can proceed based upon the indication.
Owner:CISCO TECH INC
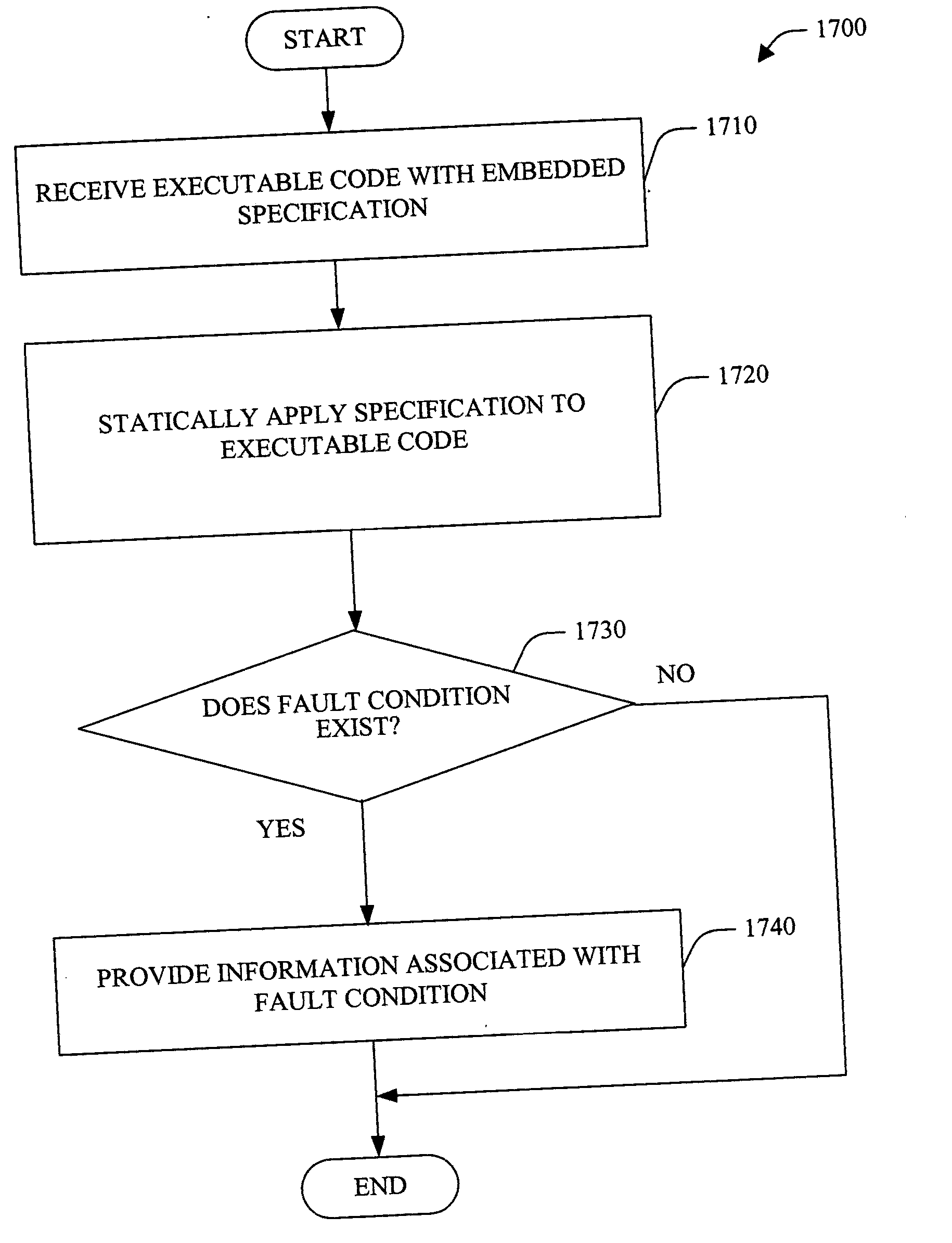
Test postcondition items for automated analysis and test generation
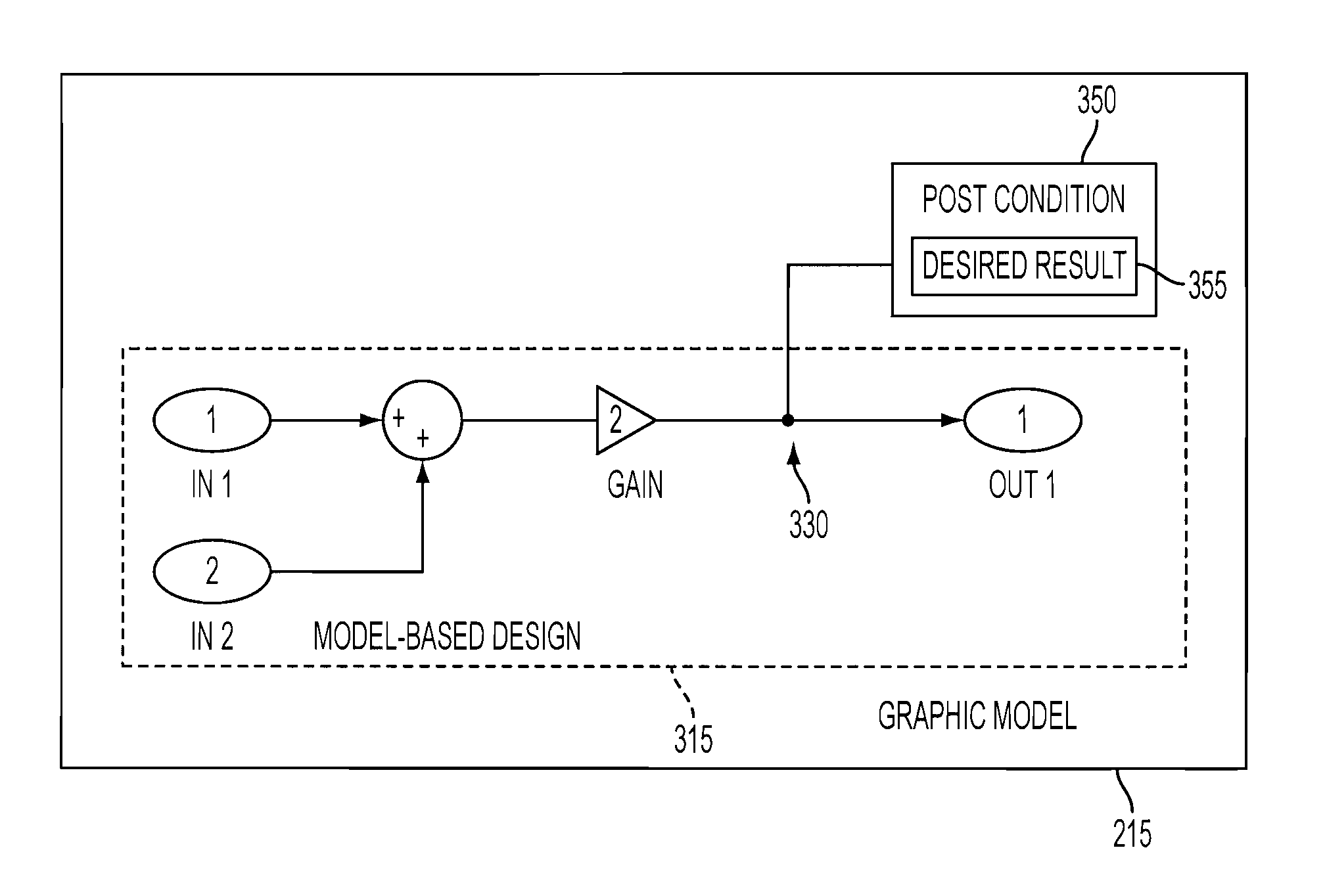
ActiveUS7729894B1Achieve performanceVisual/graphical programmingSoftware simulation/interpretation/emulationGraphicsTheoretical computer science
The present invention provides methods and systems for using a element in a graphical model to represent and identify a postcondition for use by a verification tool in verifying an executable form of the design represented by the graphical model. The postcondition element comprises desired result for verification without affecting the behavior of the design. The desired result is to be achieved or tested for in verifying the design. As such, the postcondition element of the present invention provides a mechanism and formalism in a model-based design approach that is used to direct automatically generated tests or verification of the design represented by the graphical model.
Owner:THE MATHWORKS INC
Third-party component vulnerability test method based on conditions and parameter variations
ActiveCN103617114ADetect securityImprove test efficiencySoftware testing/debuggingThird partyTest efficiency
The invention provides a third-party component vulnerability test method based on conditions and parameter variations. The third-party component vulnerability test method comprises the steps of analyzing a component interface through a third-party type library to obtain type information of a component, obtaining a safety requirement protocol of the component according to the description and IDL of the component, obtaining pre-conditions and post-conditions of the method from the requirement protocol, conducting a condition variation test on a method sequence, extracting parameter value constraints and relation constraints from requirements, conducting a parameter protocol variation test on the method sequence, and obtaining a vulnerability test report according to the testing result of the step 3 and the testing result of the step 4. The third-party component vulnerability test method has a certain effect on explicit expression safety abnormity, the safety of the component can be tested, and the test efficiency is improved.
Owner:JIANGSU UNIV
Systems and methods for domain-driven design and execution of modular and dynamic services, applications and processes
A context of one or more interactions is determined. Base objects are transformed into interpreted objects by interpreting the base objects based on evaluation of the context, and by resolving references of the base objects relative to domain model types and concepts, each of the base objects modeled using a same declarative modeling language, the same declarative modeling language enabling transitions between the interpreted objects, at least one of the interpreted objects including at least one post-condition providing hooks for transition policies which allow the at least one of the interpreted objects to be logically chained in a non-linear process. Transitioning between at least two of the interpreted objects by chaining the at least two interpreted objects based on a particular post-condition of a particular interpreted object to create at least a portion of a particular non-linear process. At least a portion of the particular non-linear process is executed.
Owner:ENTERPRISEWEB
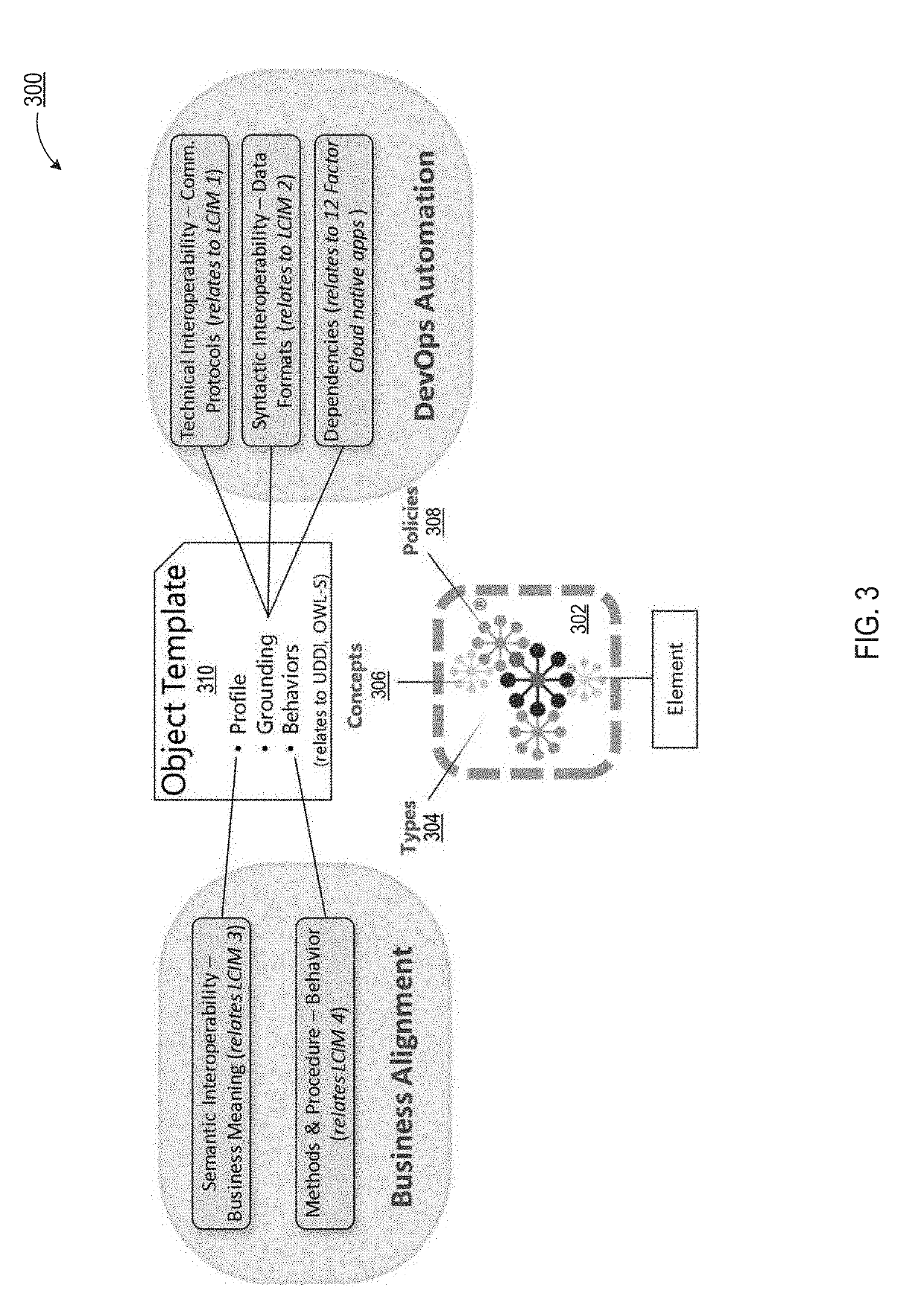
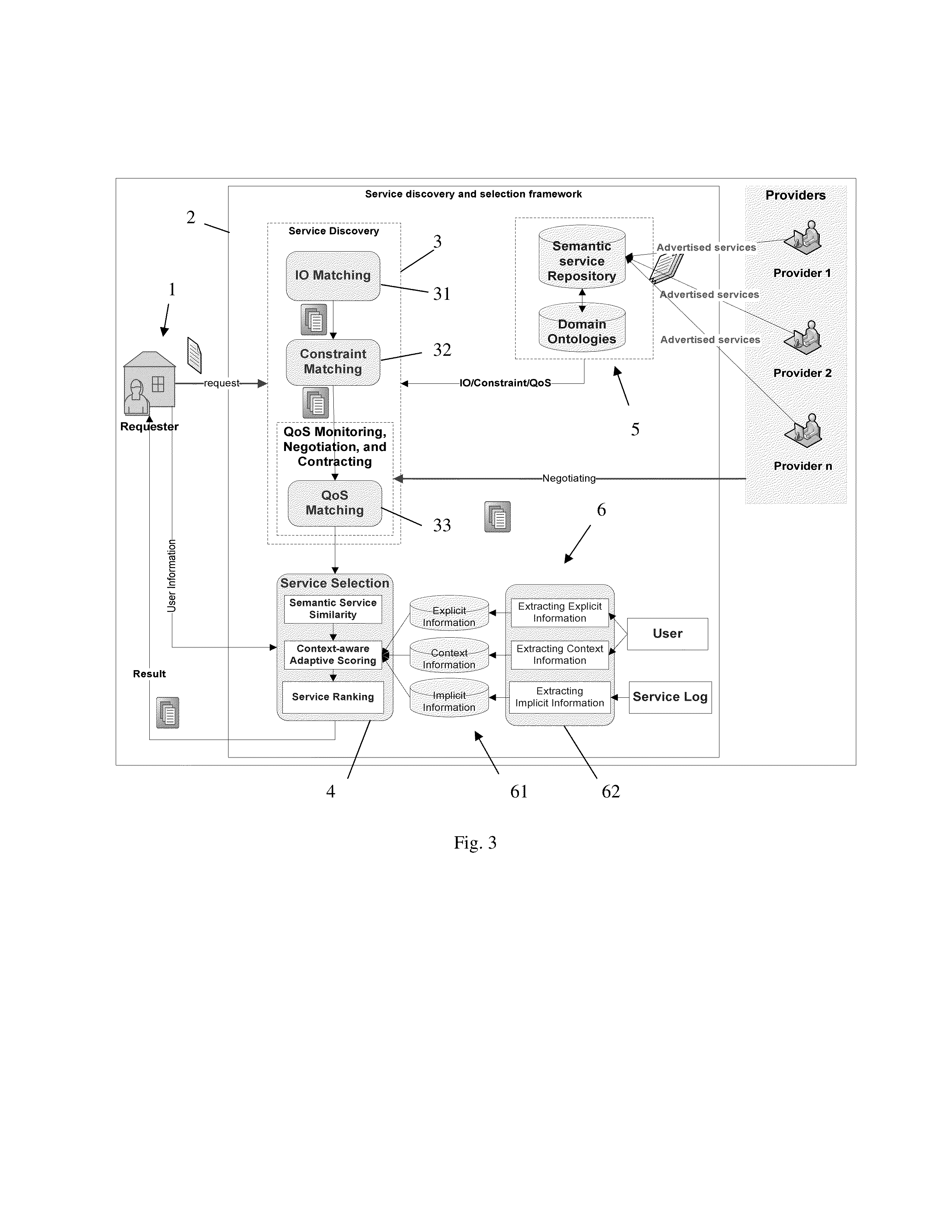
Methods and systems for service discovery and selection
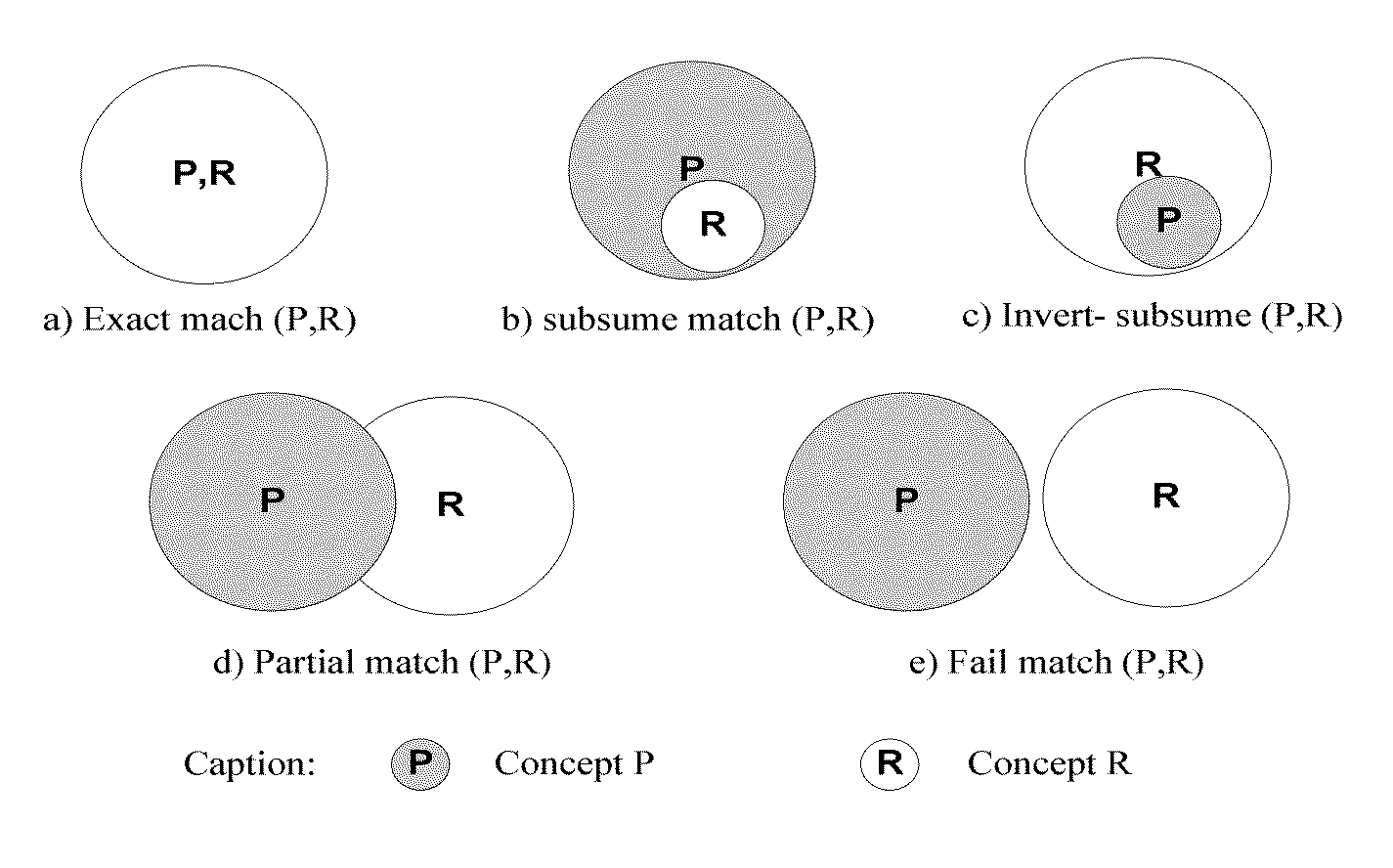
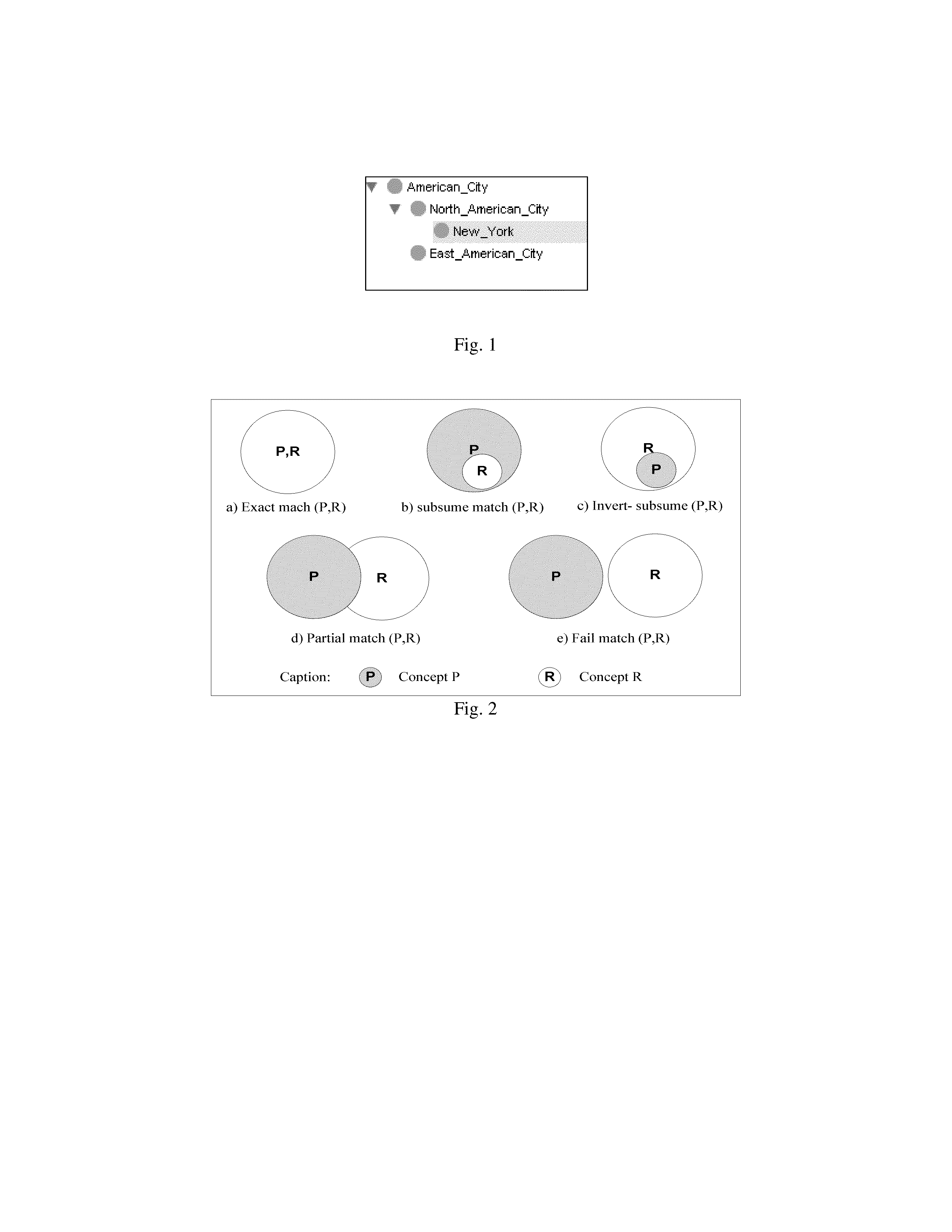
A systems and method are proposed that address the task of locating advertised services satisfying specific requirements described by a service request, and ranking discovered services so as to enable selection of best services among them. Real life scenarios often involve services described with complex pre- and post-conditions, and have Quality of Service (QoS) associated with them. The proposed method and apparatus support a unified matching of functional as well as non-functional service properties: input-output, complex constraints, and QoS. A novel service discovery and selection algorithm can adaptively locate advertised services by performing a flexible matching of the three service properties. The algorithm is capable of returning partially matched services should there be no exact match.
Owner:AGENCY FOR SCI TECH & RES
Third-party component security testing method based on data mining
ActiveCN106294162AImplement automated testingImprove test efficiencySoftware testing/debuggingComputer hardwareThird party
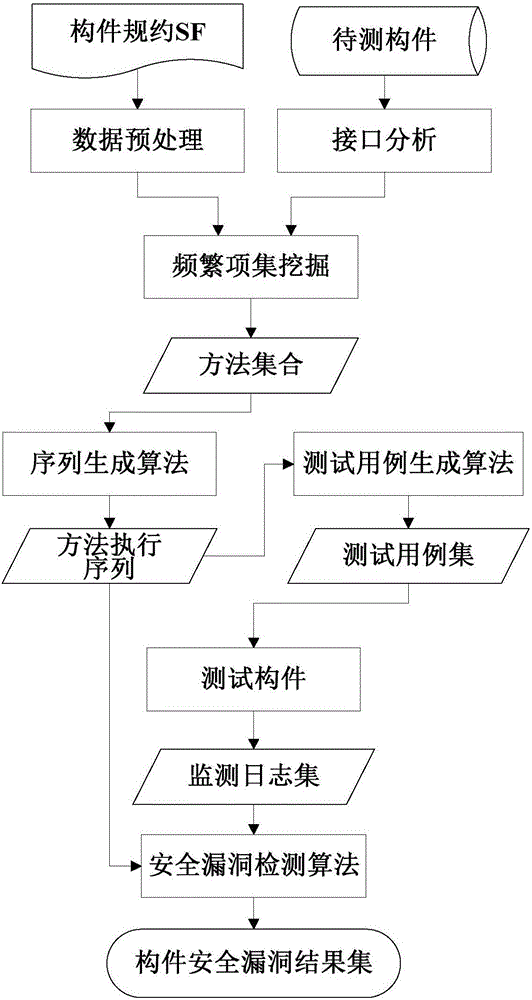
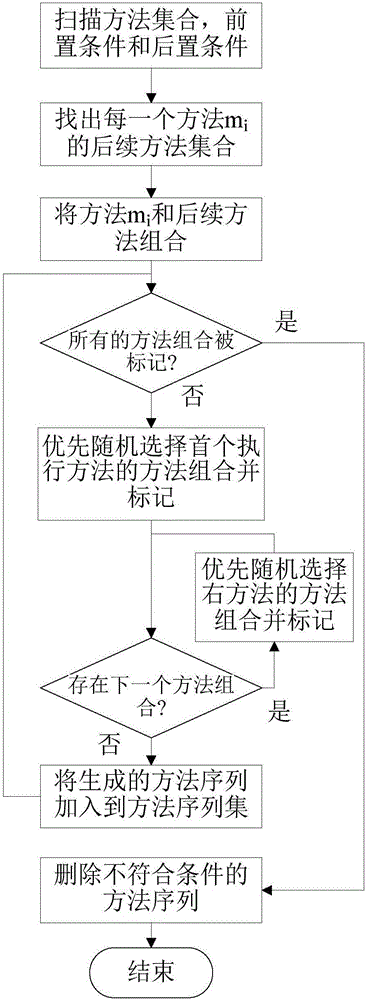
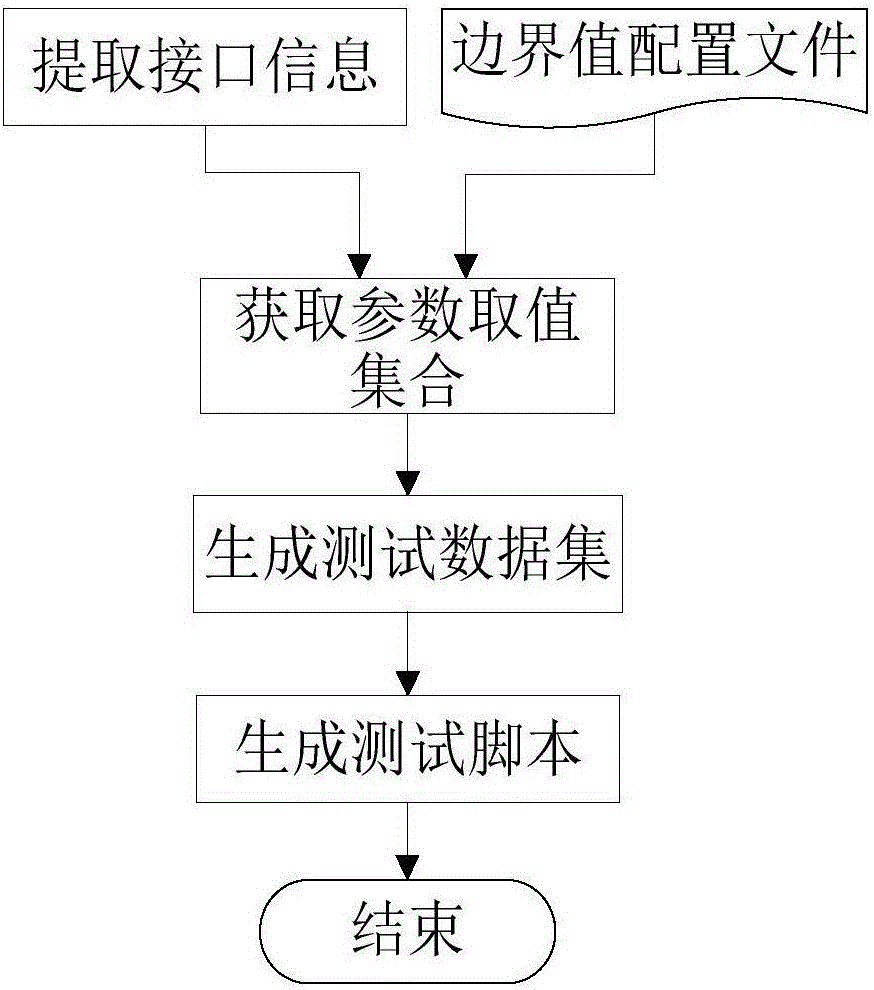
The invention discloses a third-party component security testing method based on data mining. The method comprises steps as follows: 1, generating a method execution sequence set with a sequence generating algorithm according to effective component method names, method pre-conditions and post-conditions; 2, reading parameter boundary value files, assigning parameters of methods in the method execution sequences with a test case generating algorithm, and generating a test case set; 3, testing the components according to the generated test case set, recording state information during component operation, and generating a monitoring log set; 4, analyzing monitoring logs with a security vulnerability detecting algorithm to obtain a final component security vulnerability test result set. The method provides the model basis and the test criterion for the test of component security vulnerability and can be better applied to component security tests; besides, a third-party component security testing system based on data mining is also designed, automatic testing is well realized by the aid of the system, and the testing efficiency is improved.
Owner:JIANGSU UNIV
Method and apparatus for providing symbolic mode checking of business application requirements
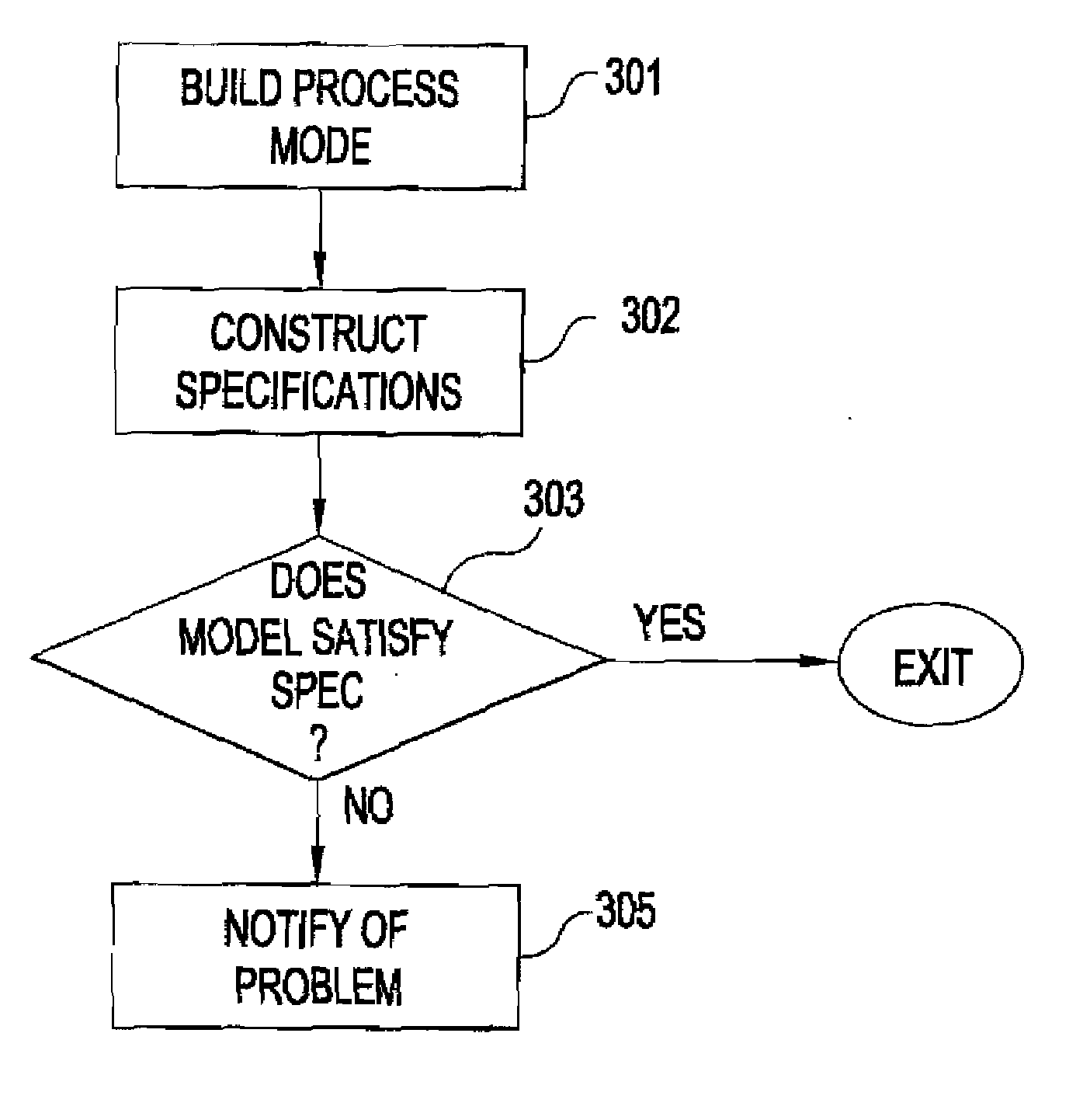
A system and method for providing symbolic mode checking of business application requirements. A language allows for building a model for the business process, the model comprising a plurality of actions, with each action having a precondition and a postcondition or outcome. Specifications are constructed for the properties of the business applications with the specifications describing both the states of the business process and the order in which they may occur. Finally, the model and the specifications are analyzed to determine if the model satisfies the specifications. If the model fails to satisfy the specifications, a problem may be indicated in the business application. The process can be automated to permit the system to make assumptions for conducting a thorough analysis of selected potential problem areas in the application.
Owner:IBM CORP
Establishing method and multiplexing method for multiplex attack mode in software security development
InactiveCN102810137AImprove efficiencyImprove accuracyComputer security arrangementsMultiplexingTest efficiency
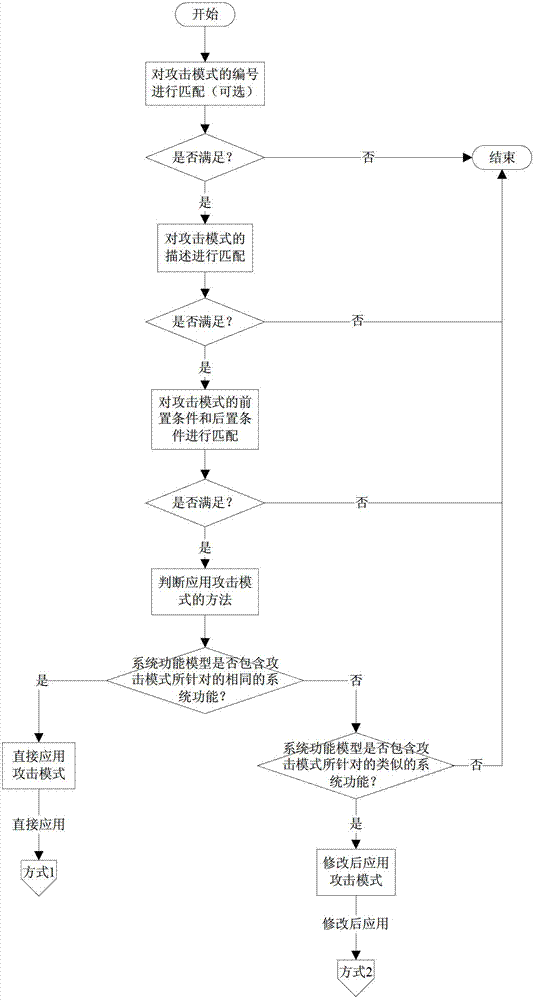
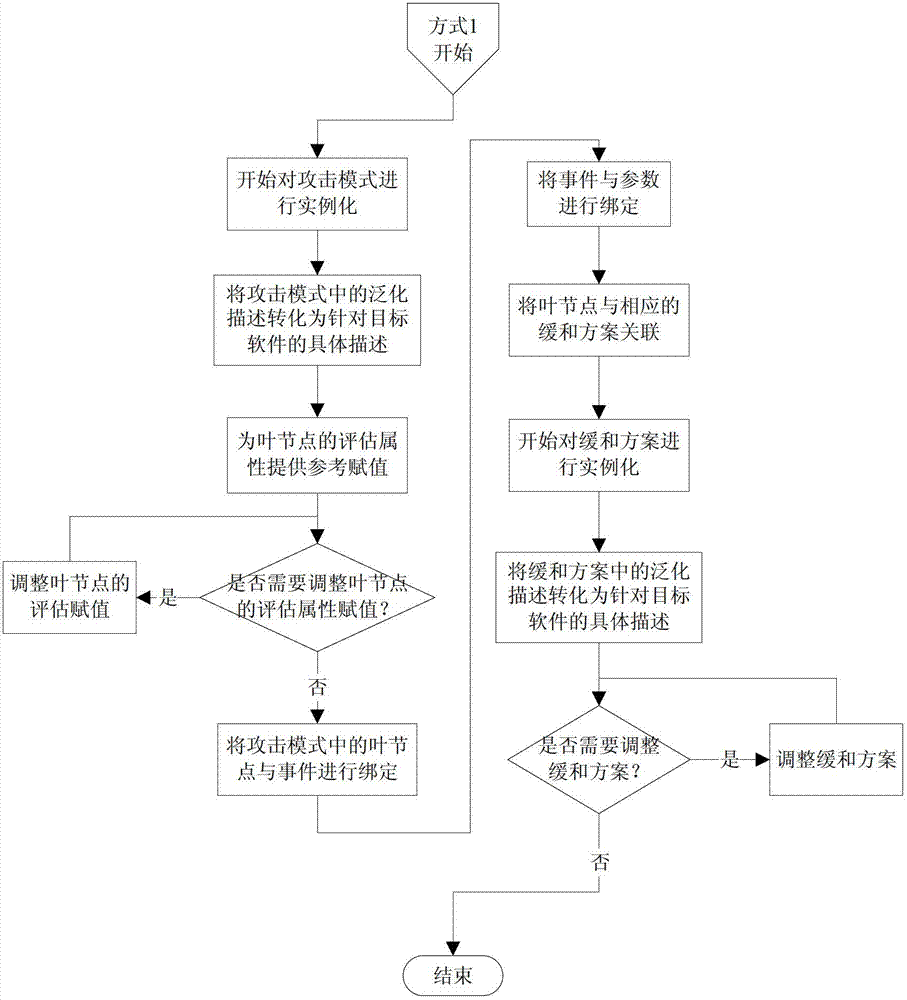
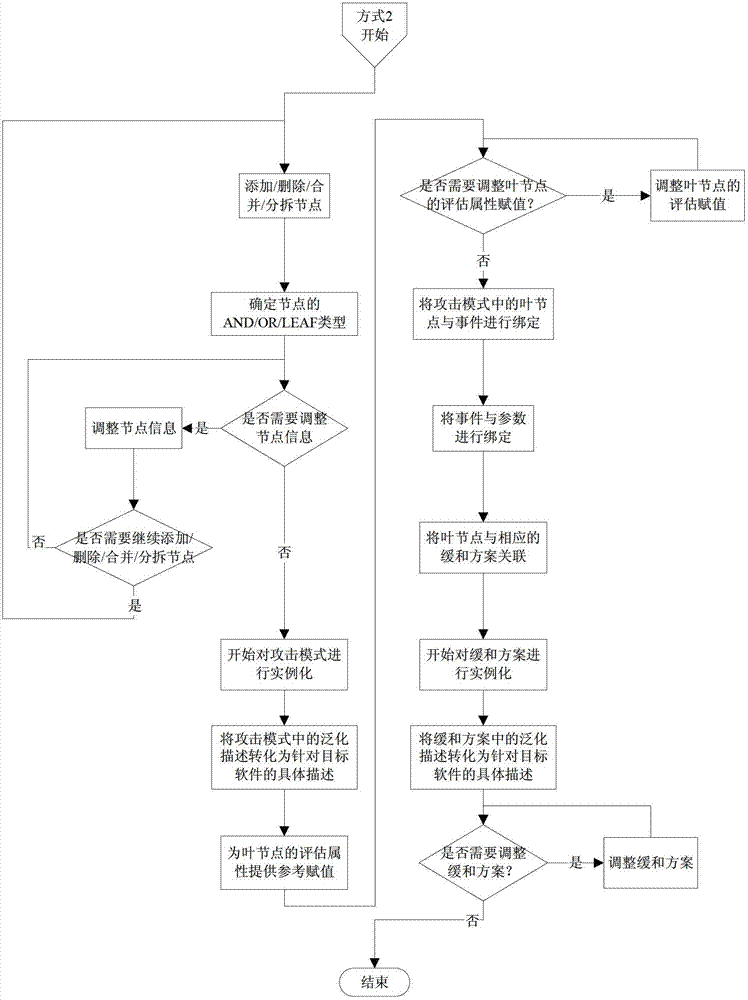
The invention discloses an establishing method and a multiplexing method for a multiplex attack mode in software security development, wherein the establishing method comprises four key steps: abstraction, matching, modification and instantiation. The multiplexing method comprises the following steps: the descriptive information, the precondition and the post condition of the attack mode are matched; a method applying the attack mode is further judged if the conditions are met; the first class of method applying the attack mode--a multiplexing method directly applying the attack mode is adopted if the function model of a system contains the identical system function for the attack mode; and a second class of method applying the attack mode--a multiplexing method applying the modified attack mode is adopted if the function model of the system contains a similar system function for the attack mode. Compared with the prior art, the multiplexing method of the attack mode improves the efficiency and the accuracy of modeling threatening, so that the software security evaluation and test efficiency of threatening model drive is improved, and the security of a software system is enhanced.
Owner:TIANJIN UNIV
Apparatus and method for displaying a waveform at high rate with a large aquisition memory
A waveform display apparatus and method displays one or more waveforms of a signal under test at high throughput while acquiring digital data of the signal under test in a large acquisition memory. A user sets a time interval of user's interest when viewing a signal under test and sets trigger criteria through a user interface. An ADC converts the signal under test into digital data that is stored in a large acquisition memory. A trigger unit detects and produces trigger events, based on a trigger, as trigger event information during one acquisition process. A trigger event eliminator may discard some of the trigger events based on pre-trigger and post-conditions set through the interface by a user. The trigger events are recorded in a trigger list as the trigger event information. A control unit locates the digital data in the acquisition memory corresponding to the trigger events in the trigger list and displays a waveform associated with the trigger event for the time interval on a display device.
Owner:TEKTRONIX INC
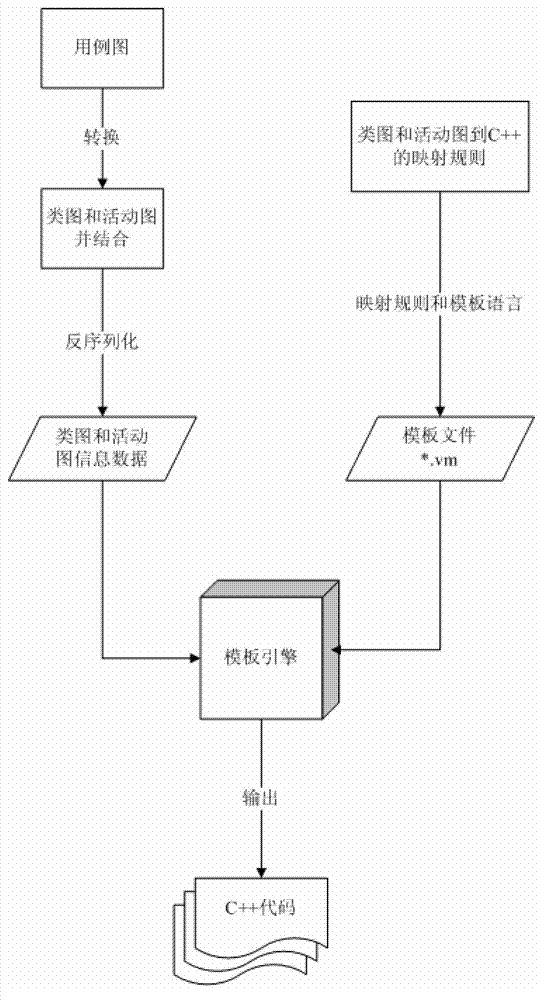
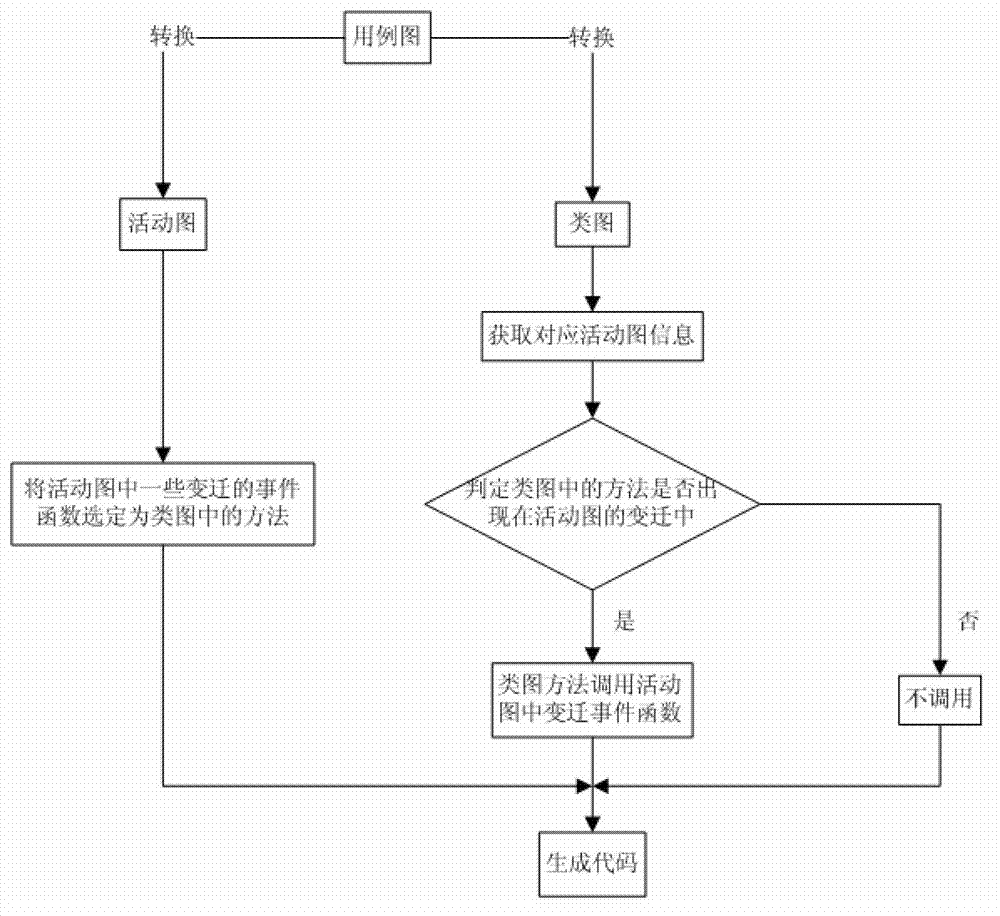
Method for generating C++code based on combination of class diagram and activity diagram
InactiveCN103176830AEasy accessImprove operational efficiencyProgram controlMemory systemsControl flowActivity diagram
The invention discloses a method for generating a C++code based on combination of a class diagram and an activity diagram. The generation method comprises the following steps of: converting a use case diagram into the class diagram and the activity diagram, wherein each use case is taken as the basis, and generating the class diagram and the activity diagram according to the information in the use case diagram, i.e. the use case description, the precondition, the post condition, the control flow and the like; building a mapping rule of the class diagram and the activity diagram to the C++code, wherein in order to improve the practical applicability and the effectiveness of the code, the class diagram and the activity diagram need to be combined with each other to generate the code; and after a template-based technology is taken as a frame, enabling input information of a template engine to be selected from the class diagram and the activity diagram based on a model technology, and generating the code by a template code generating technology based on the class diagram and the activity diagram.
Owner:XIDIAN UNIV
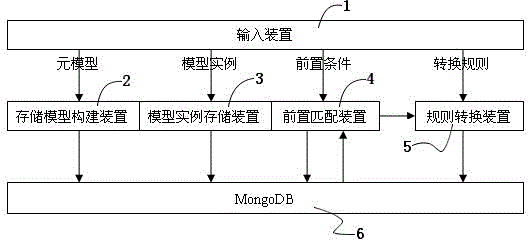
Method and device for realizing graph conversion based on MongoDB
ActiveCN104794244AReduce memory requirementsNo size limitSpecial data processing applicationsPre-conditionPre conditioning
Owner:NANJING UNIV
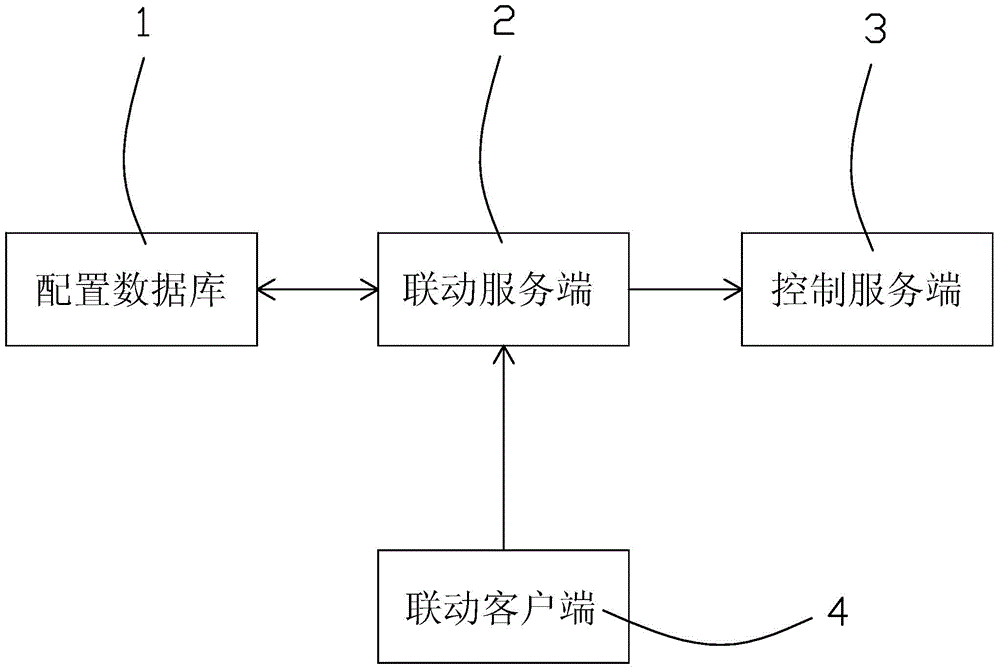
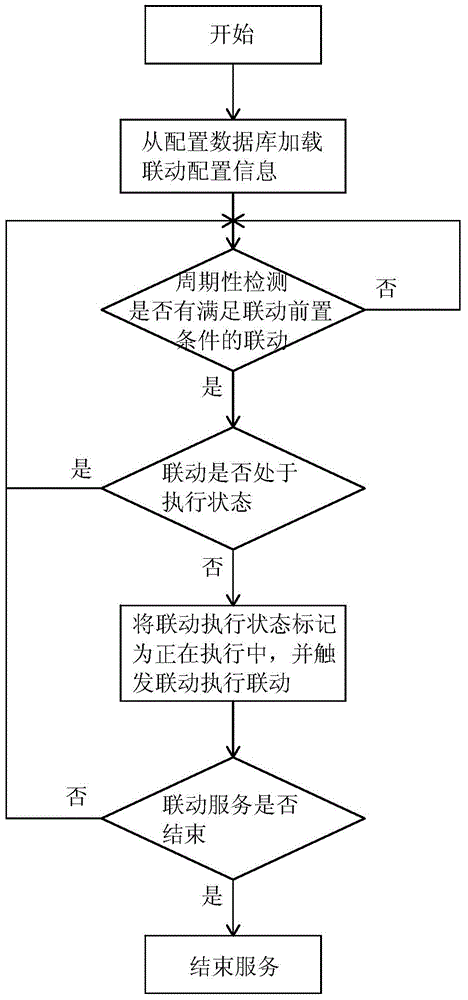
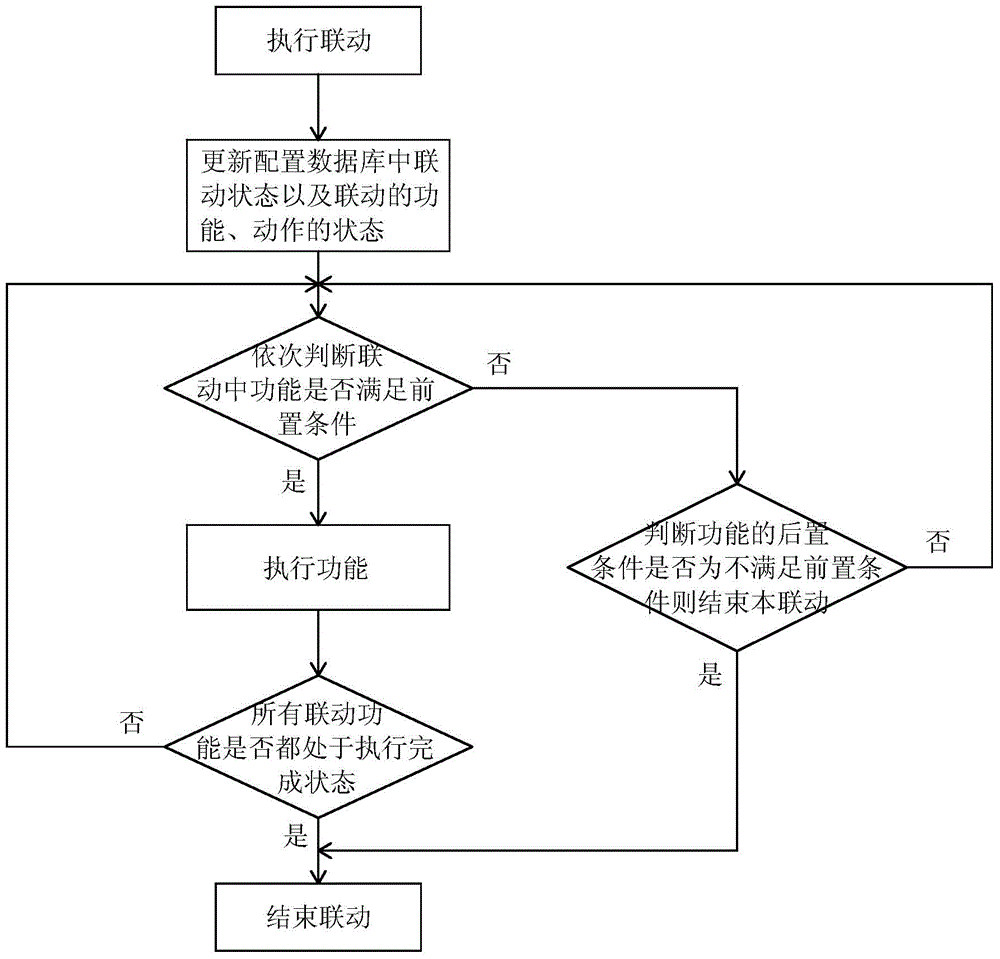
Linkage service system and linkage service method applied in integrated rail transit supervisory control system
ActiveCN104683443AGuaranteed preservationFlexible configurationTransmissionSoftware engineeringClient-side
The invention relates to a linkage service system and a linkage service method applied in an integrated rail transit supervisory control system, aiming at solving the problem that the linkage of the existing integrated rail transit supervisory control system is fixed, so that monitoring software needs to be replaced during modification. The system comprises a configuration database, a linkage client-side, a linkage server-side and a control server-side, wherein the configuration database and the linkage client-side are respectively connected with the linkage server-side; the linkage server-side is connected with the control server-side. The linkage service method comprises the steps of triggering linkage, function and action according to whether a precondition and a post-condition are met or not. The system and the method have the advantages that the linkage scheme can be flexibly collocated, and sustainable storage of the database is realized, so that linkage execution results can be stored under the special conditions that the linkage service collapses, restarts and the like, and an operator can conveniently master the linkage execution condition and prejudge the execution of the next step action; the linkage service system is capable of updating in an online way.
Owner:ZHEJIANG SUPCON INFORMATION TECH CO LTD
Exercise machine For Use with Lower Body Negative Pressure Box
InactiveUS20140235412A1Improve understandingSpeed up recoverySpace saving gamesMovement coordination devicesNervous systemLeg press
A compact, portable, lightweight, easily transportable leg press exercise apparatus to simulate both exercise and the daily activity of sitting in a microgravity environment. The exercise portion of the apparatus creates stress on the lower extremities by supplying a variable resistance to a reciprocating foot pedal by way of a coil spring and damper system acting through a four-bar linkage. The leg press exercise apparatus is paired with an existing Lower Body Negative Pressure (LBNP) box to add an evenly distributed pressure-induced stress to the lower extremities. By combining resistance exercise and lower body negative pressure with the LBNP leg press exercise apparatus, the users experience one or more times body weight (BW) in stress on their musculoskeletal, cardiovascular and nervous systems. By achieving one times BW or greater (artificial gravity) during exercise and two-thirds BW during sitting, the gap between the precondition and post condition syndrome will become smaller.
Owner:UNITED STATES OF AMERICA
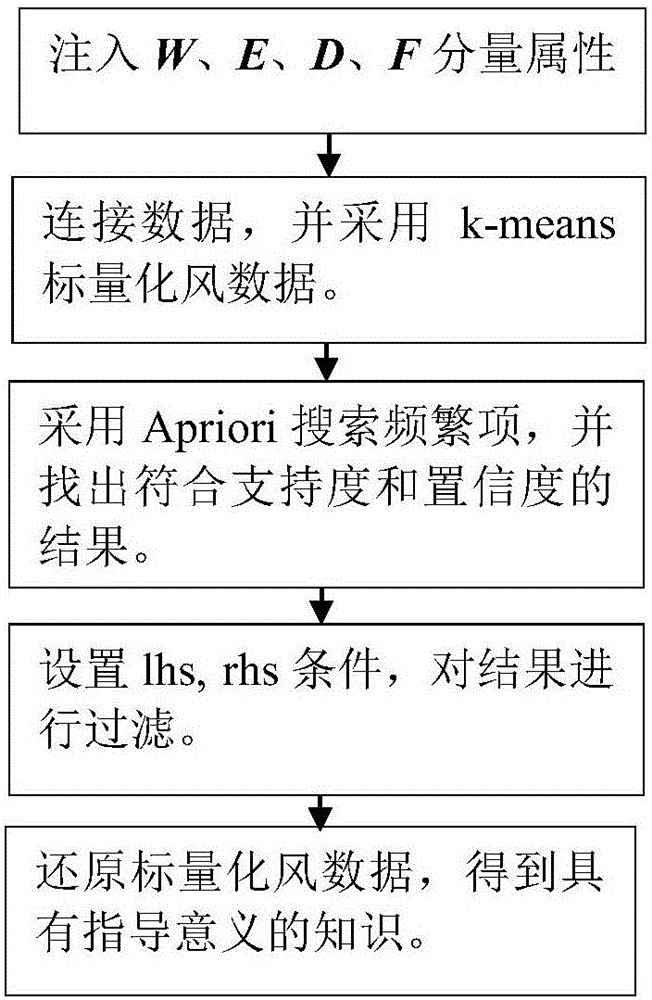
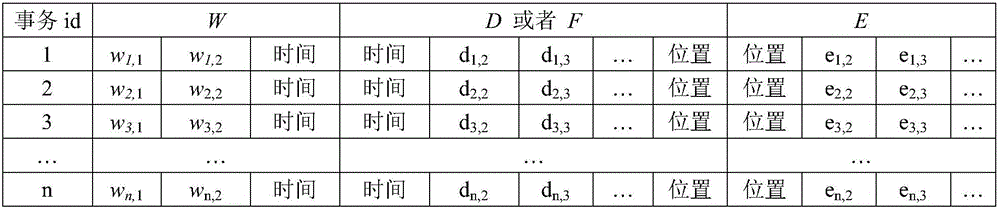
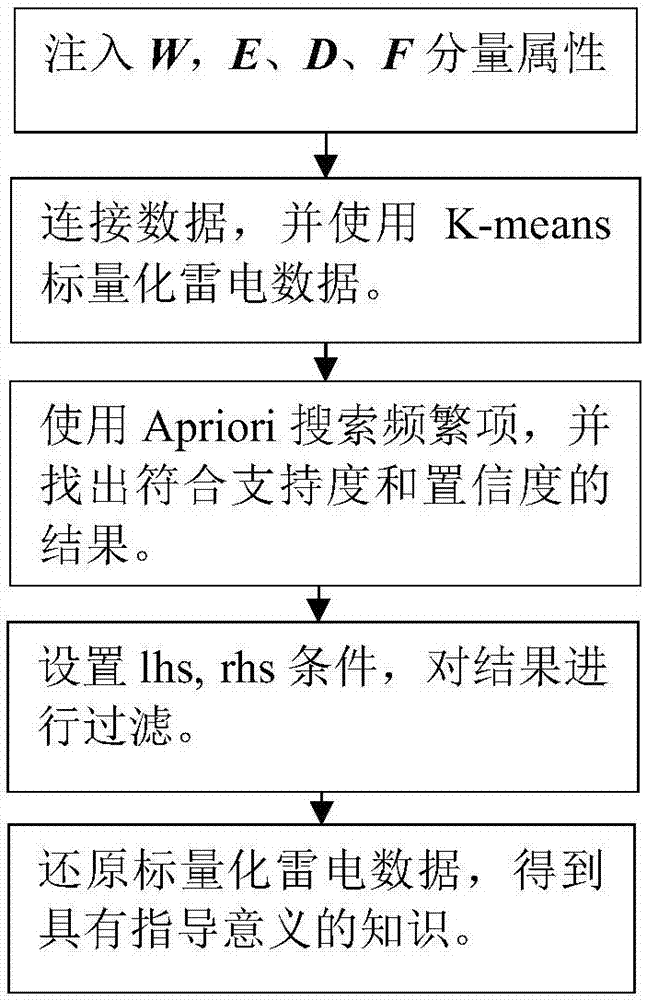
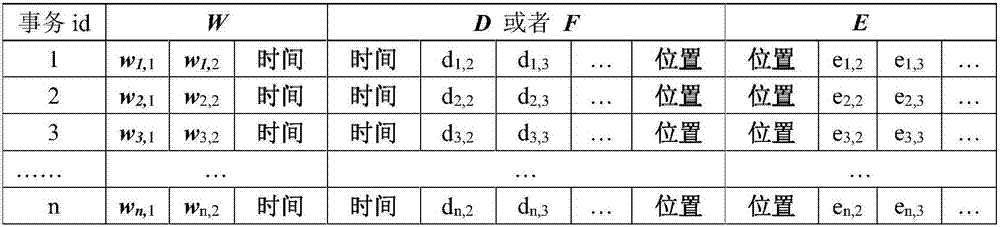
Association method of wind data and transmission line body operation data
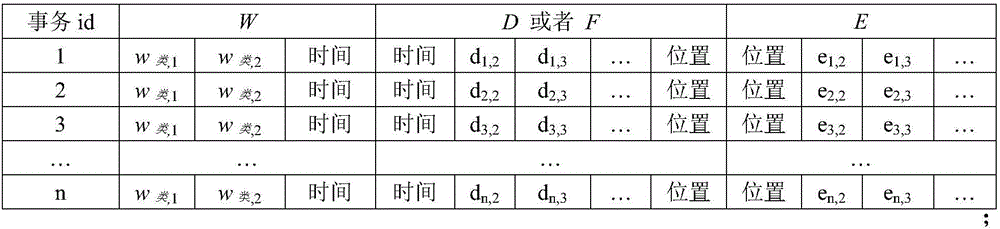
The invention discloses an association method of wind data and transmission line body operation data. The method comprises the steps of S010 setting W as a wind external force set, E as a transmission line equipment set, D as a defect set and F as a fault set, and setting the attributes of W, E, D and F, S020 connecting data, S030 using a k-means algorithm to carry out the scalarization of wind data, S040 using Apriori to search a frequent item, and finding a result which is in accordance with support and confidence, S050 setting a pre-condition lhs and a post-condition rhs, and filtering the result, and S060 restoring scalar wind data. According to the method, a reference basis is provided for the targeted maintenance of a transmission line and the reduction of the occurrence of fault defects.
Owner:ELECTRIC POWER SCI RES INST OF STATE GRID XINJIANG ELECTRIC POWER +2
Apparatus and method for providing digital content
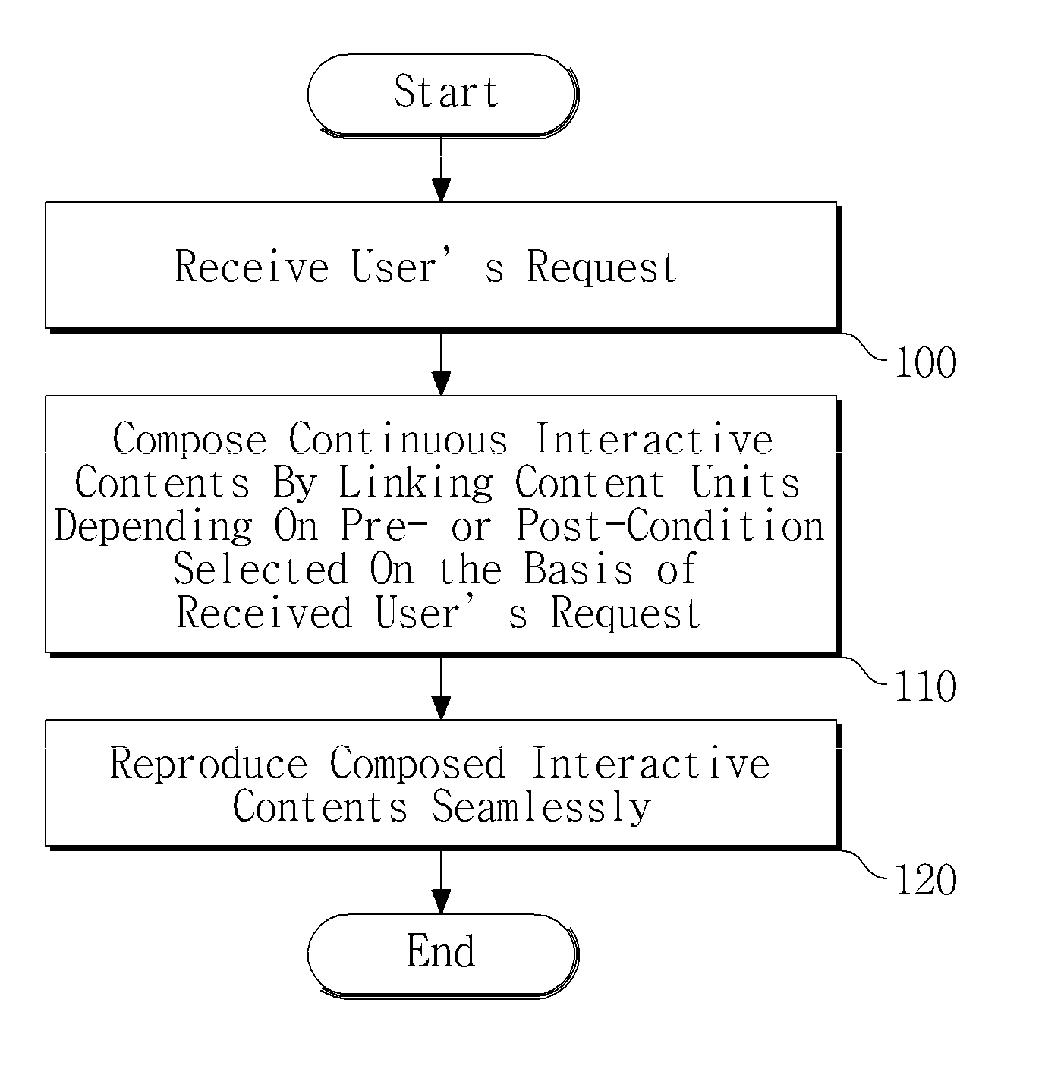
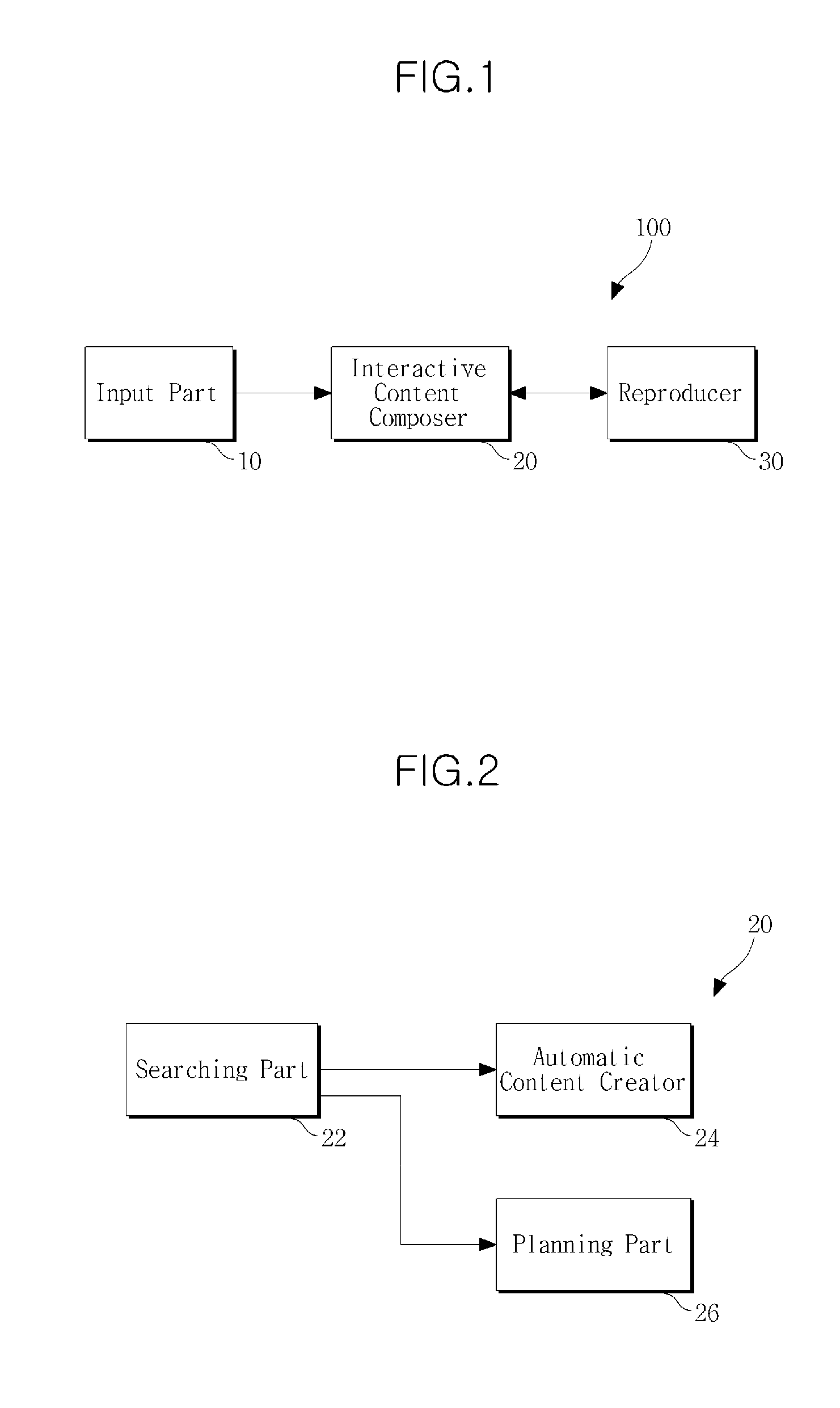
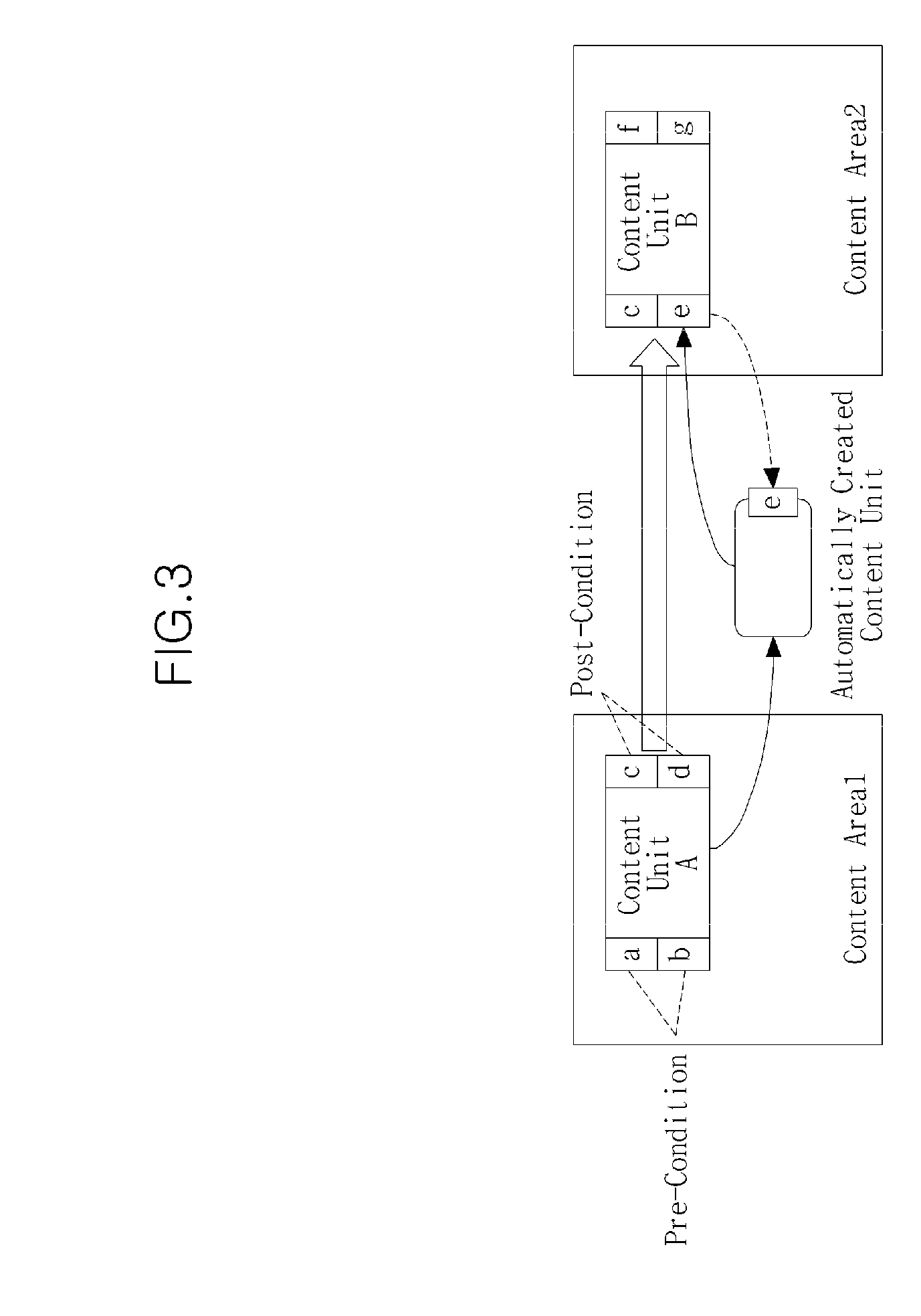
ActiveUS20100031191A1Digital data information retrievalData processing applicationsInteractive contentPre-condition
A digital content providing apparatus including an interactive content composer to compose continuous interactive contents by linking at least two content units depending on at least one pre-condition or post-condition selected determined on the basis of a user's request and a reproducer to seamlessly reproduce the composed interactive contents.
Owner:SAMSUNG ELECTRONICS CO LTD
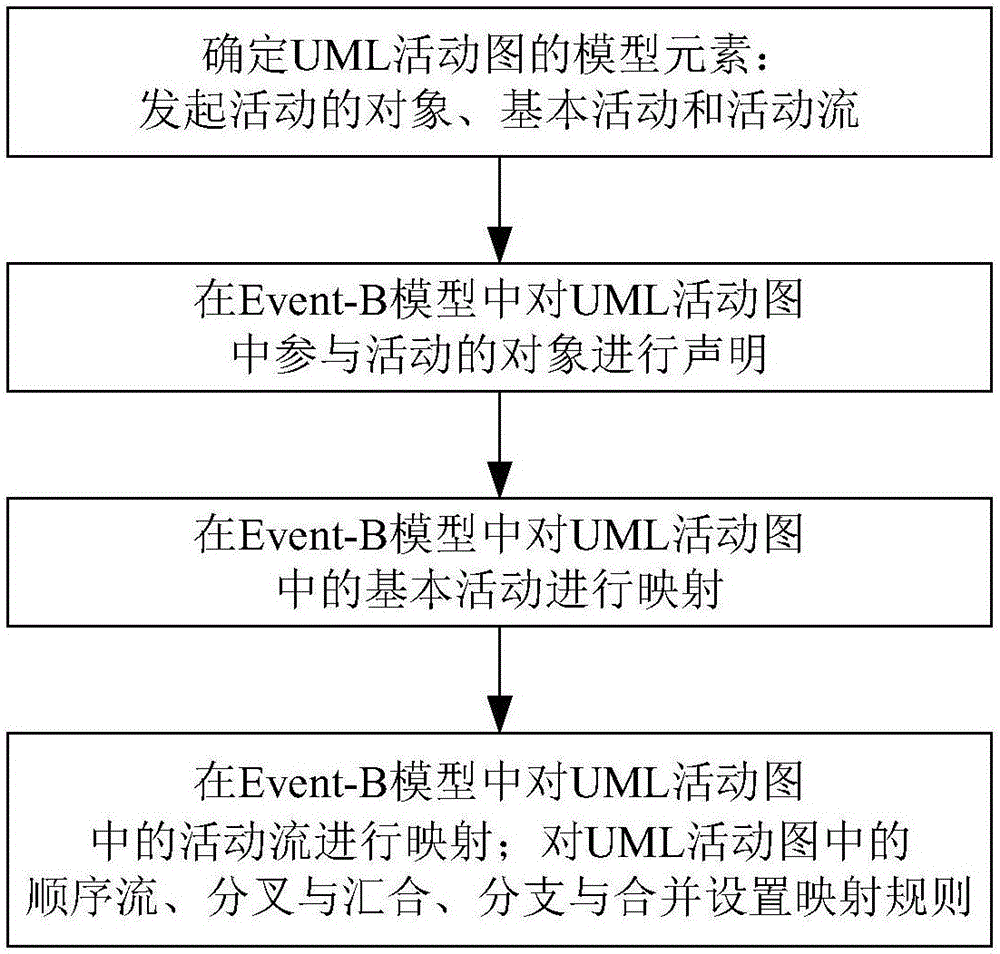
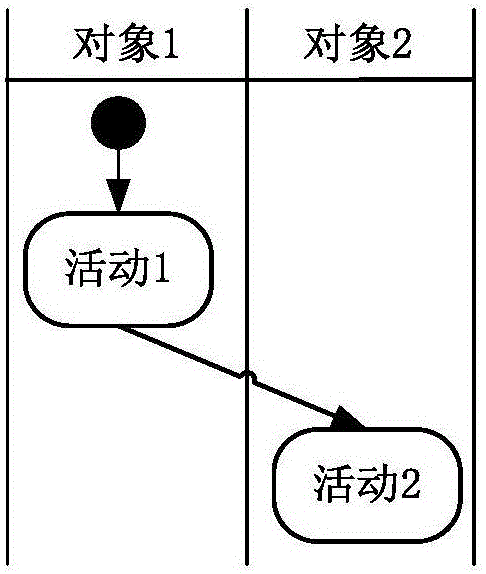
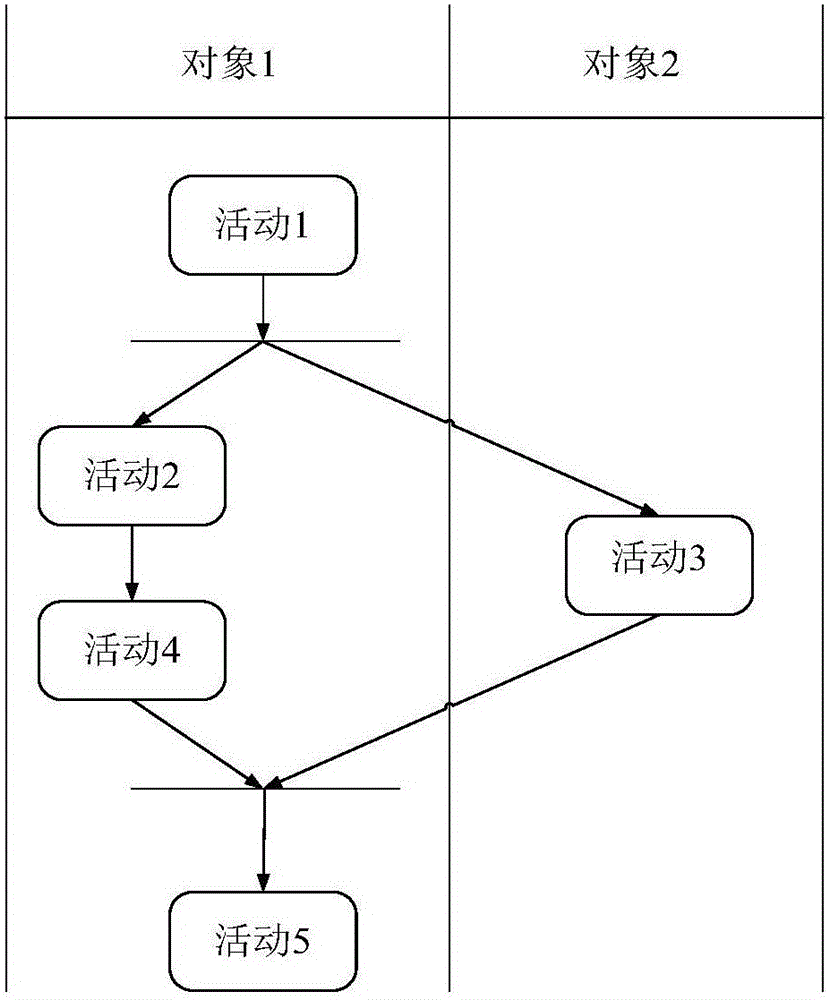
Conversion method from UML activity graph to Event-B model
InactiveCN105787198AImplement methods to aid in its modelingSpecial data processing applicationsComputer Software EngineeringEvent trigger
The invention relates to a conversion method from a UML activity graph to an Event-B model, and belongs to the field of computer software engineering.The method comprises the steps that a model element of the UML activity graph is determined, wherein active objects, basic activities and activity flows are initiated; an object collection and an activity collection are established, invariant is established to ensure that each activity only belongs to one object, preconditions and post conditions of the activities are stated in event trigger conditions guards and actions respectively, and mapping is conducted on the activity flows which comprise a sequence flow, bifurcation and joint and branch and combination.According to the method, the UML active graph is converted into the Event-B model, formalized validation is conducted on a converted model through a modeling platform of an Event-B, and problems existing in a UML model can be found; meanwhile, for the problem that modeling is inconvenient for the Event-B serving as a formalized language, the method for assisting the Event-B in modeling by means of the ULML active graph is achieved.
Owner:BEIHANG UNIV
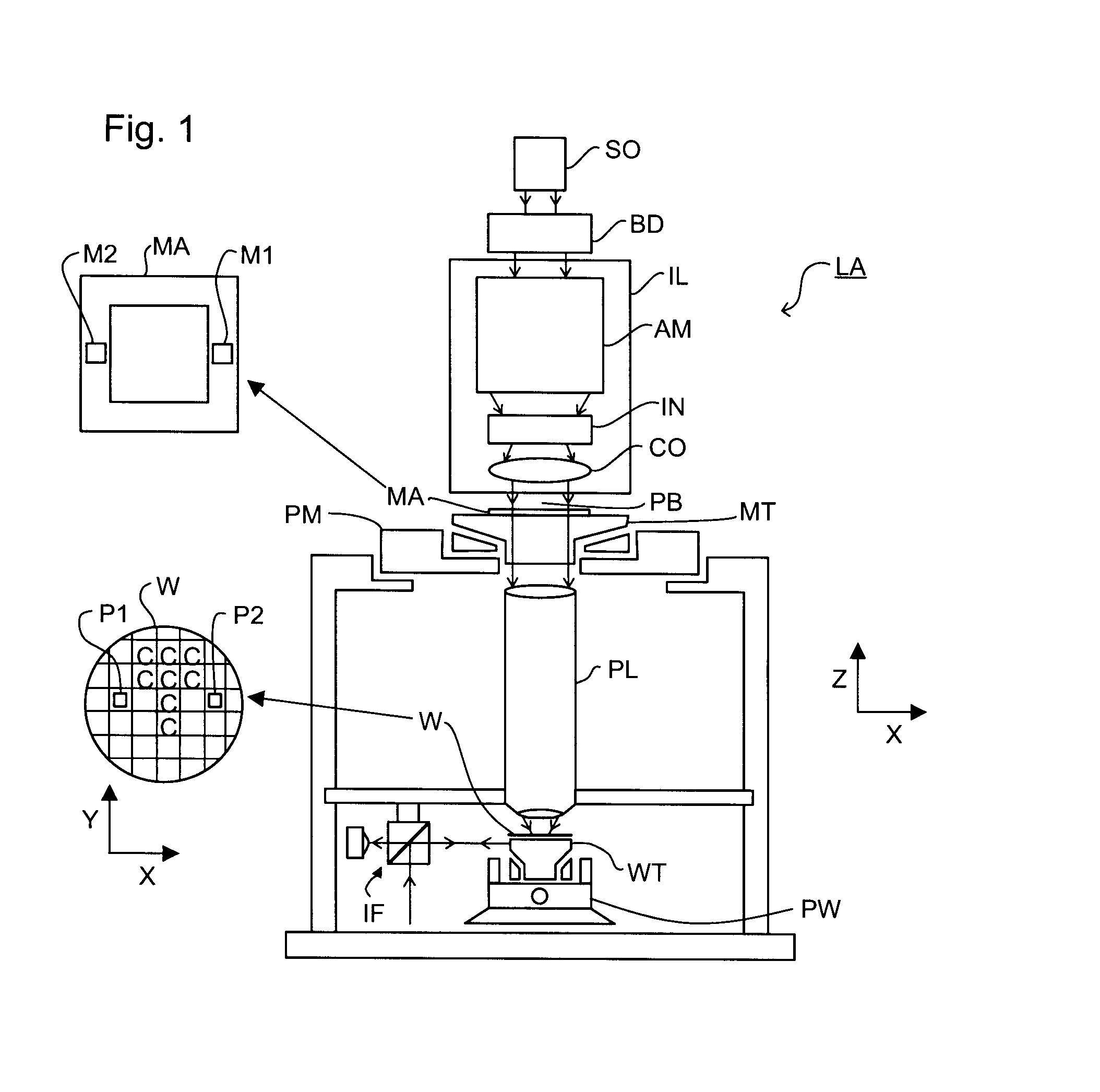
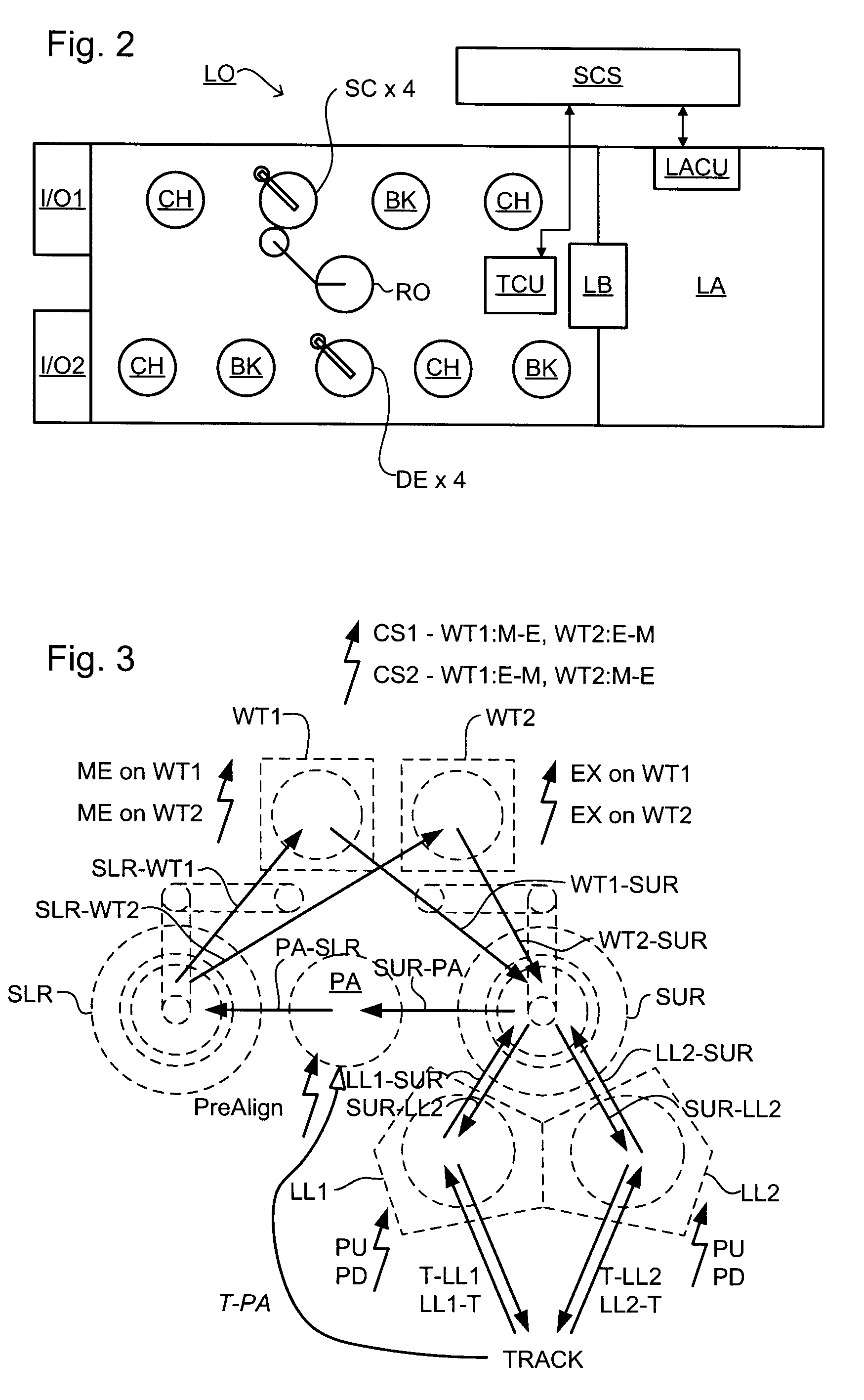
Method of operating a lithographic processing machine, control system, lithographic apparatus, lithographic processing cell, and computer program
InactiveUS7756597B2Semiconductor/solid-state device manufacturingTotal factory controlControl systemProcessing element
Owner:ASML NETHERLANDS BV
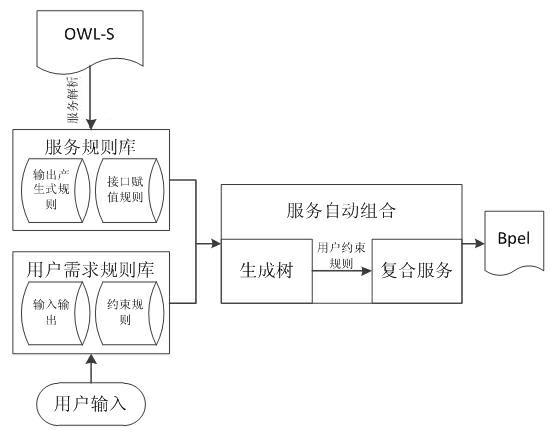
Method for interactively combining Web services based on precondition and post-condition
ActiveCN102135998AImprove acceleration performanceHigh degree of automationSpecial data processing applicationsComposite servicesUser needs
The invention discloses a method for interactively combining Web services based on a precondition and a post-condition. The method comprises the following steps: 1, a user requirement rule base establishing module expresses input, output and constraint conditions of a user into a user requirement rule to establish a user requirement rule base; 2, a service rule base establishing module generates service rules corresponding to all services to establish a service rule base; and 3, an automatic service combining module establishes a corresponding spanning tree for each target output object required by the user by using the user requirement rule base and the service rule base and combines the spanning trees by using a constraint rule in the user requirement rule base to obtain the flow of a composite service. By adopting the method, the variability, the openness and the dynamics of the Internet can be adapted, Web service resources on the Internet can be fully integrated and utilized, various data are compared, acquired and computed, and the expandability and the automatic degree of a Web service combination of a computer system are enhanced.
Owner:ZHEJIANG UNIV
Method of associating lightning data with operation data of power transmission line
InactiveCN107392790AReduce failure defectsData processing applicationsCharacter and pattern recognitionData connectionComputer science
Owner:WUHAN NARI LIABILITY OF STATE GRID ELECTRIC POWER RES INST +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com