Establishing method and multiplexing method for multiplex attack mode in software security development
A technology for software security and establishment methods, applied in computer security devices, instruments, electrical digital data processing, etc., to achieve the effects of improving efficiency and accuracy, improving software security evaluation and testing efficiency, and improving efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example
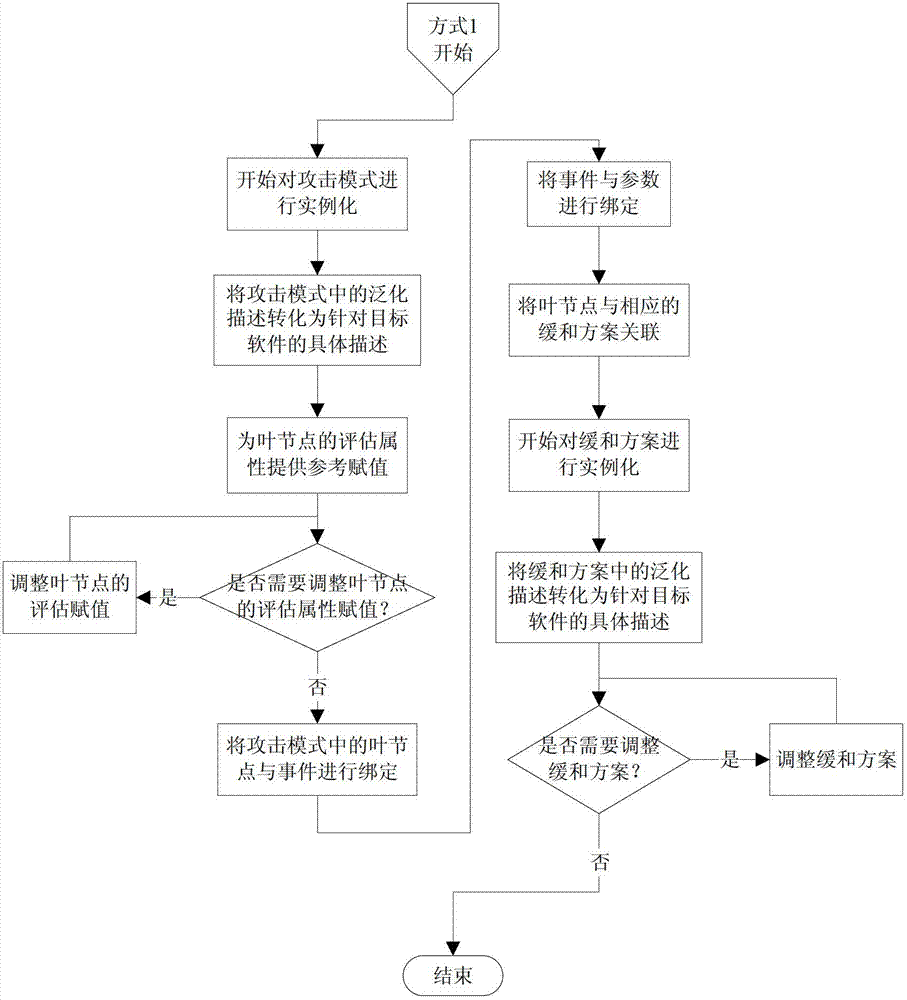
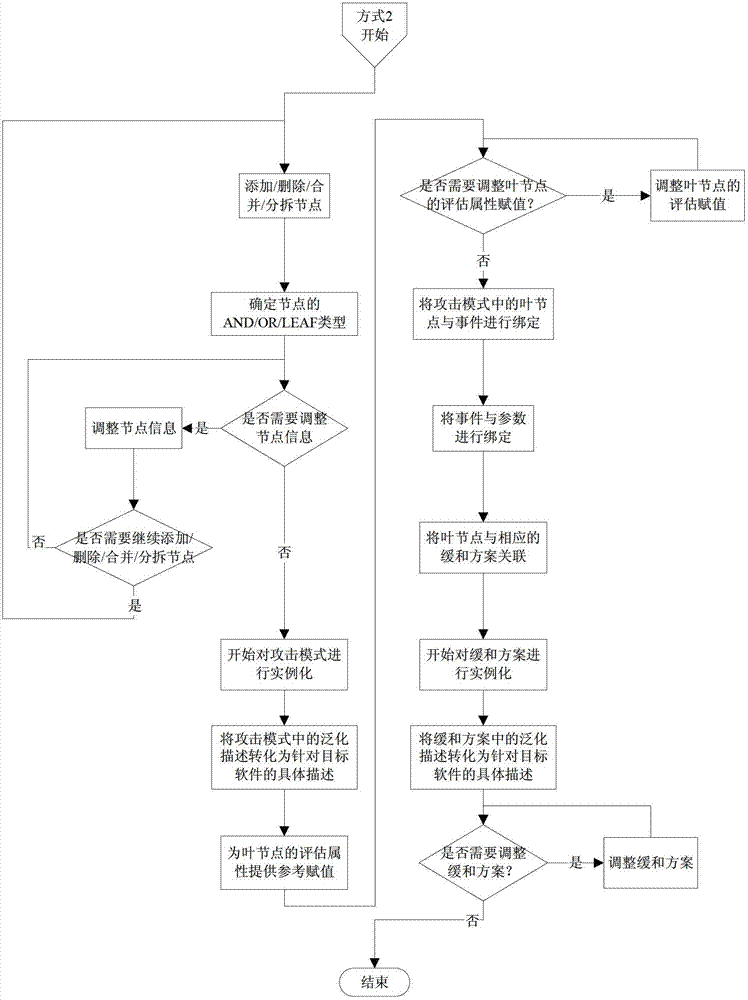
[0025] Instantiation: This step instantiates the abstract attack methods and their corresponding mitigation solutions, and applies them to the threat modeling process for specific systems to complete the reuse of attack patterns.
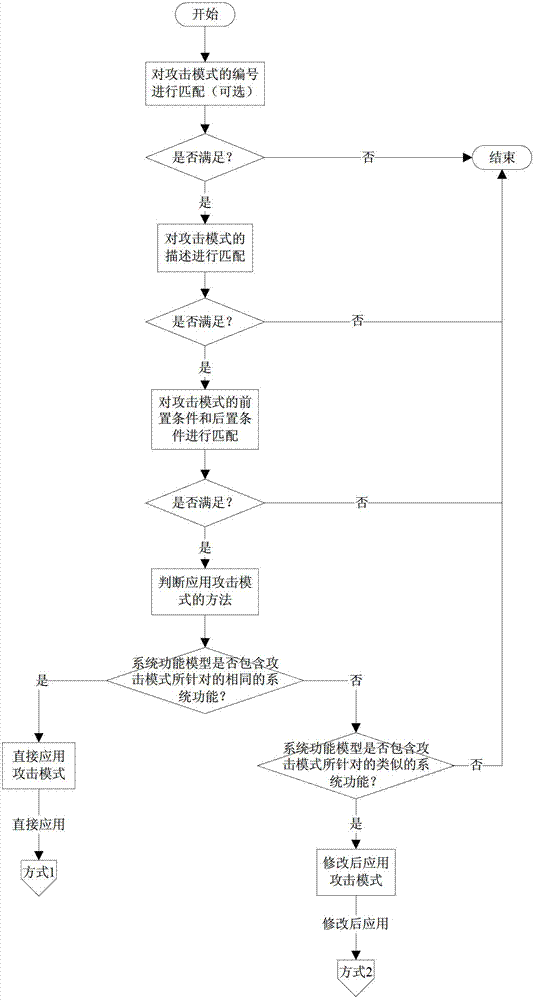
[0026] When applying the attack pattern to the threat modeling process for a specific system, it is necessary to perform the matching, modification and instantiation steps of the attack pattern reuse technology. The overall process is as follows: figure 1 shown. First, match the attack pattern number, this step is optional; then, match the description information, preconditions and postconditions of the attack pattern; if the above conditions are met, then further judge the method of applying the attack pattern ; If the functional model of the system contains the same system function targeted by the attack pattern, the method of applying the attack pattern of the first type - the method of directly applying the attack pattern is adopted; if the func...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com