Third-party component security testing method based on data mining
A technology of security testing and data mining, applied in software testing/debugging, electrical digital data processing, error detection/correction, etc., can solve problems such as untestable security issues, failure to achieve results, and inapplicability of third-party components. Achieve the effect of realizing automated testing and improving testing efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0046] The present invention will be further described below in conjunction with the accompanying drawings and examples. It should be noted that the described examples are only intended to facilitate the understanding of the present invention, and have no limiting effect on it.
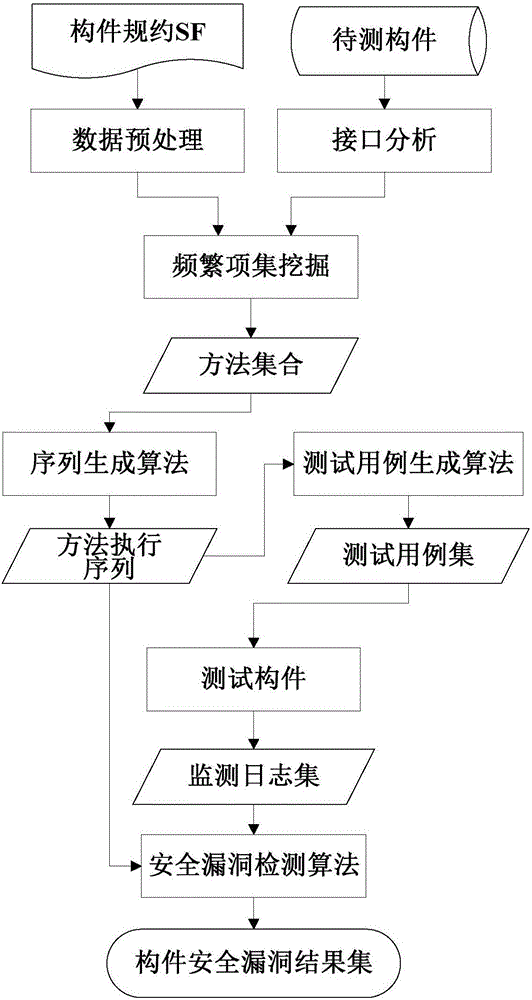
[0047] The present invention aims to solve the problem of third-party component security testing, provides a third-party component security testing method based on data mining, effectively detects the implicit security loopholes and explicit security loopholes of third-party components, and provides a comprehensive The framework and algorithm are tested, and sufficient experiments are carried out to prove the feasibility and effectiveness of the method.
[0048] First, several concepts involved in the definition of the present invention are defined as follows.
[0049] Definition 1 Precondition: A series of constraints that must be met before the method is invoked. The constraints are composed of relati...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com