Block chain technology-based network digital identity authentication method
A technology of digital identity and authentication method, applied in the field of computer network, to achieve the effect of ensuring security, solving information leakage, and shortening confirmation time
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0038] In order to make the objectives, technical solutions and advantages of the present invention clearer, the following further describes the present invention in detail with reference to the drawings and specific embodiments.
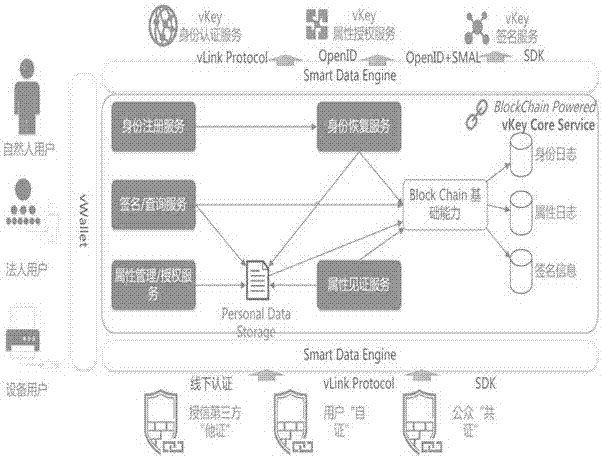
[0039] figure 1 It is the main architecture of digital identity authentication based on blockchain technology, as shown in the figure. Digital identity authentication based on blockchain technology is mainly for natural person users, legal person users, and device users. All user information is recorded on our distributed network. Currently, it mainly provides identity authentication services, attribute authorization services, and signature services. , "Other certificates" for third-party credit, users "self-certification", public "co-certification", etc. The certification center also integrates the blockchain's identity log, attribute log, signature information and other functions.
[0040] Identity authentication service: The vLink protocol is used fo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com