Secure Electronic Payment
a technology of electronic payment and security, applied in the field of secure electronic payment, can solve the problems of increasing problems and increasing opportunities for payment fraud, and achieve the effect of secure and efficient mechanisms
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
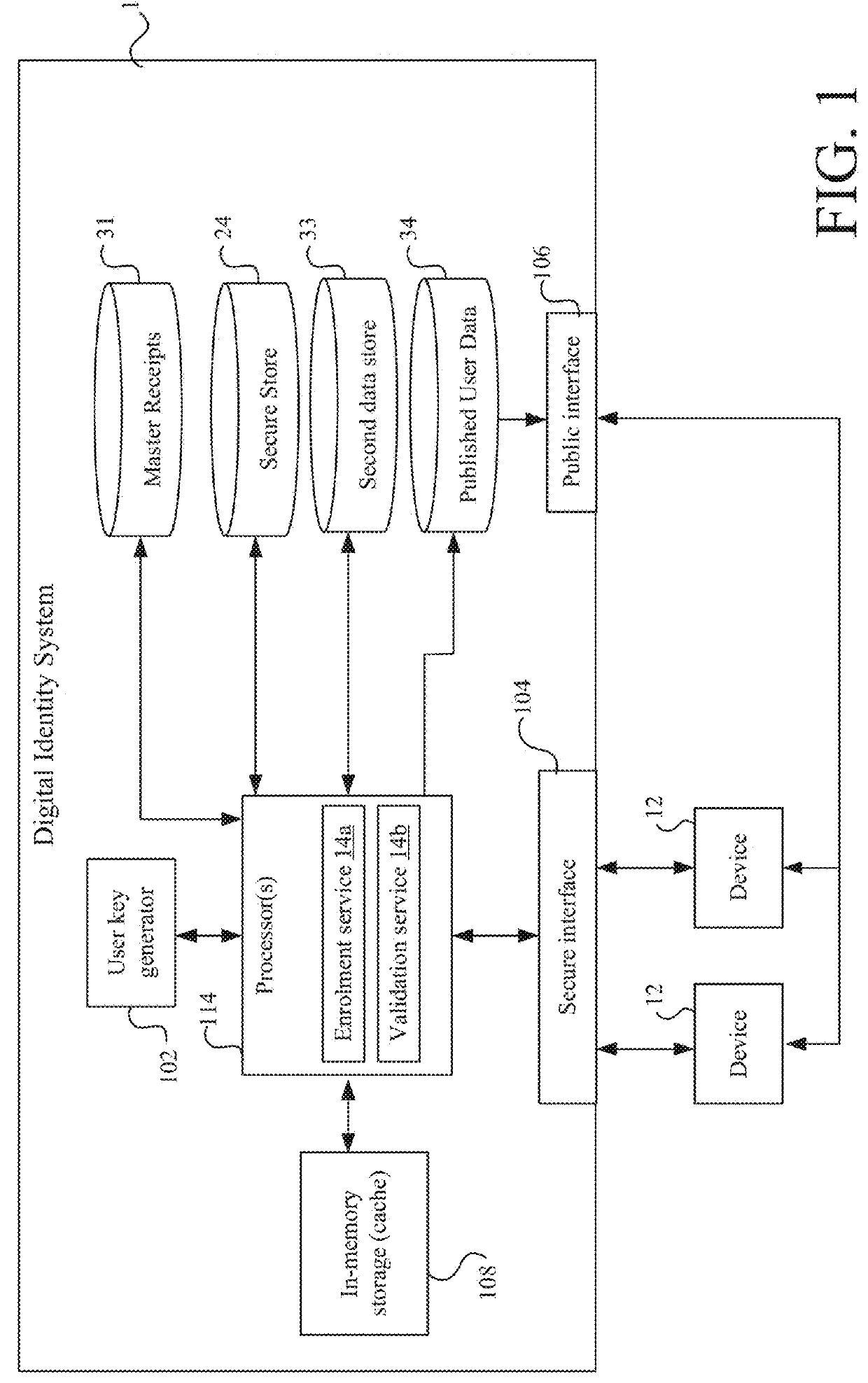
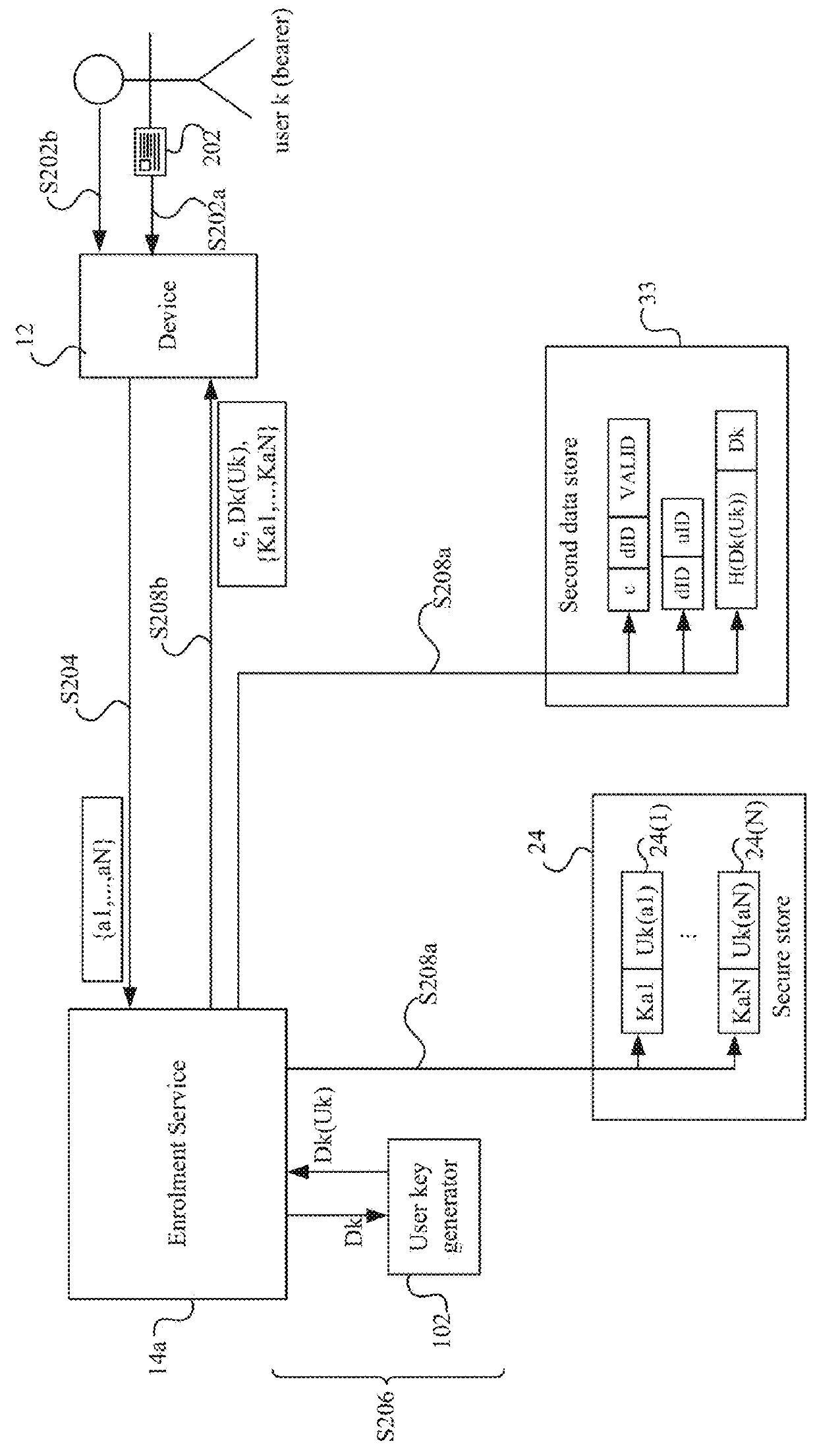
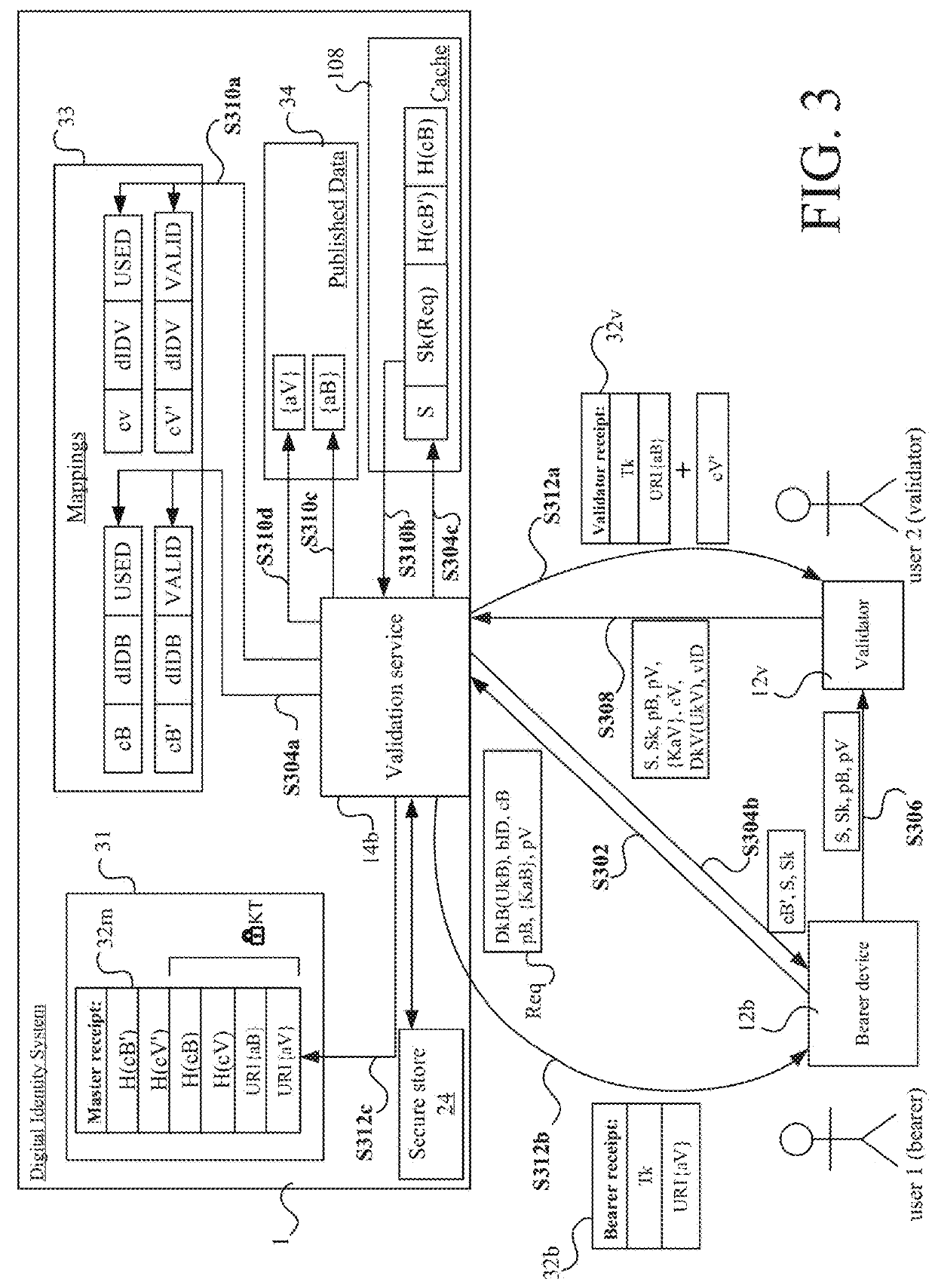
[0131]FIG. 1 shows a block diagram of a digital identity system 1, which comprises at least one processor 114. The at least one processor 114 is configured to execute digital identity management code so as to implement various services, including an enrolment service 14a and a validation service 14b. The processor 4 has access to in-memory storage (“cache”) 108, which may for example be implemented, at the hardware level, in volatile electronic storage.
[0132]The services 14a, 14b implemented by the processor 114 are accessed, by external devices 12, via a secure interface 104, such as a secure API. The secure interface 104 provides a secure (i.e. encrypted) channel(s) by which an external device 12 can communicate with the services 14a, 14b securely. The external device 12 can be any device desiring to make use of the services 14a, 14b, and in the examples below is a user device operated by a user. Examples of such user devices include smartphones and other smart devices, tablets, l...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com