Computer permission control method based on mobile dynamic password
A dynamic password and authority control technology, applied in the field of information processing, can solve the problems of low system security, invalid password, and inability to guarantee the time synchronization between the mobile phone and the PC, so as to improve security, reduce requirements, and improve anti-attack capabilities. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
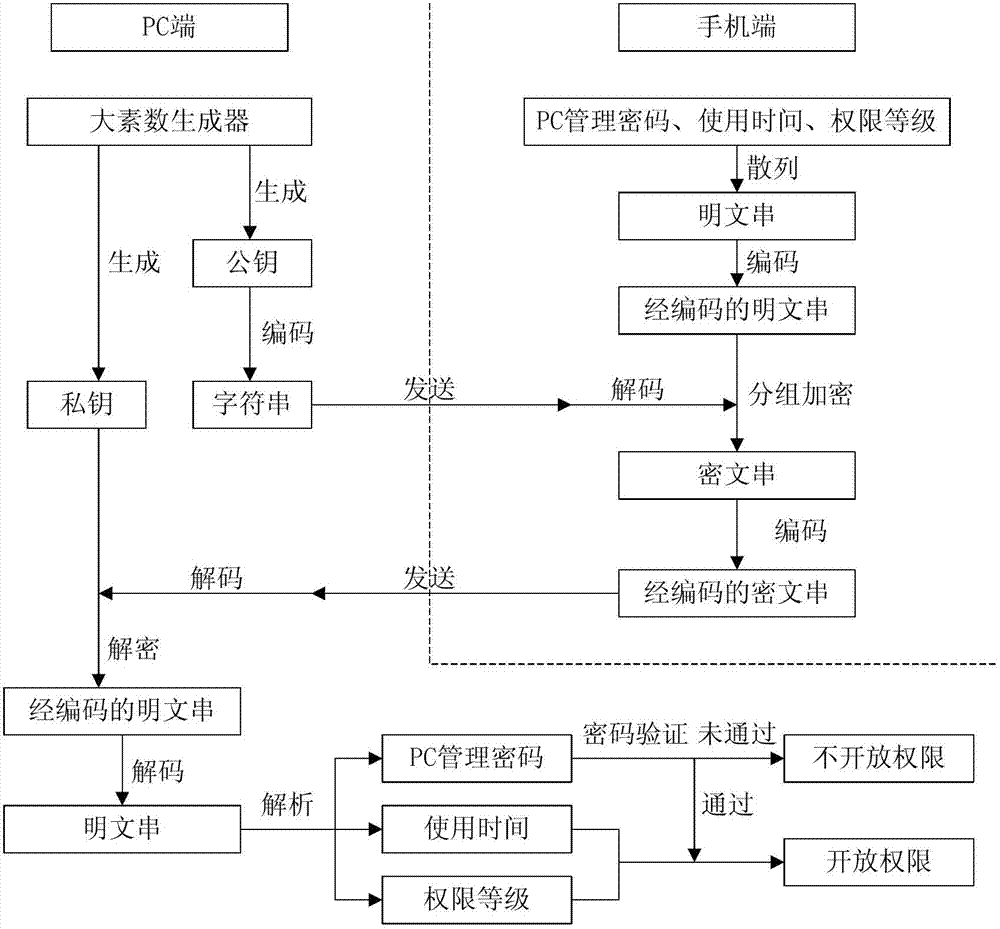
[0032] A computer use authority control method based on a mobile phone dynamic password, the method is realized through a system composed of a PC terminal connected to a network, a mobile terminal and a server terminal, and the server terminal is used to transmit information between the PC terminal and the mobile terminal. In order to ensure the reliability of data transmission, the TCP protocol is used for data transmission between PC, mobile and server. The specific steps of the method are as follows figure 1 Shown:
[0033] Step 1: The PC uses the RSA encryption algorithm, and a large prime number generator dynamically generates a private key and a public key. The private key is kept on the PC for subsequent decryption, and the public key is encoded into a string and sent to the mobile phone.
[0034] Step 2: After the mobile terminal receives the string, it first decodes it, and obtains the public key used for encryption to encrypt the PC management password, usage time a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com