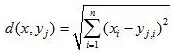Operation authority control method based on APT attack intention
A control method and a technology of operating authority, applied in the field of network security in the computer field, to achieve the effects of security and convenience, high controllability, and accurate identification
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0056] Such as figure 1 As shown, the operation authority control method based on the APT attack intention of this implementation includes the following steps:
[0057] Step 1. Obtain network and system logs to identify APT attack behavior;
[0058] In this embodiment, the specific process of obtaining the network and system logs described in step 1 and identifying the APT attack behavior is as follows:
[0059] Step 1A1, collect network and system logs, obtain network link log records through network logs, obtain the domain name of relevant information data from network and system logs through dns logs, and then query its source IP address, for the visit of a specific IP address, dns The log parses its source IP address, including access parameters, access content and return data from the dns server;
[0060] Step 1A2, log mining based on DBSCAN cluster analysis, find out abnormal operation logs, and identify them as APT attack behaviors.
[0061] In this embodiment, the l...
Embodiment 2
[0099] The difference between this embodiment and Embodiment 1 is: the specific process of obtaining the network and system logs described in step 1 and identifying the APT attack behavior is as follows:
[0100] Step 1B1, acquiring user behavior characteristics;
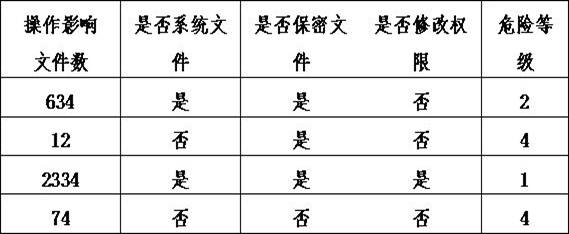
[0101] During specific implementation, the acquisition of user behavior features described in step 1B1 is to perform one-hot word vector feature extraction on user behavior operations affecting the number of files, whether they are system files, whether they are confidential files, and whether they modify permissions. The one-hot word vector uses a 128-dimensional word vector for feature extraction. The user's behavior characteristics carry the security level information of the operation behavior. The security level information of the operation behavior includes the number of files affected by the operation, whether it is a system file, whether it is a confidential file, and whether it has modification authority. Ba...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com