Extraction and analysis method for heterogeneous security log information under complex network system
A complex network and analysis method technology, applied in the field of extraction and analysis of heterogeneous security log information, can solve the problems of high error probability of manual writing, poor adaptability of SYSLOG information, high project implementation cost, etc., to achieve high error probability and high implementation cost Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
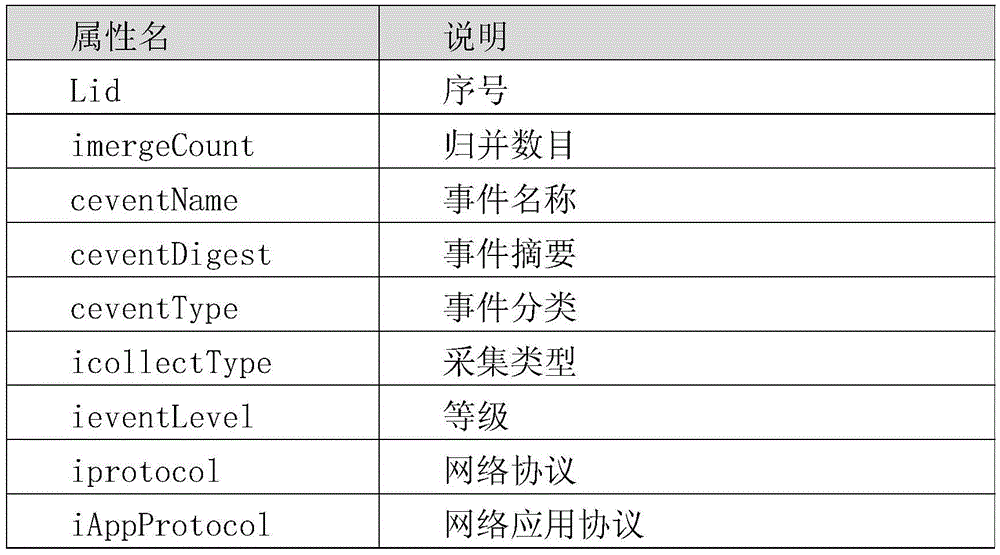
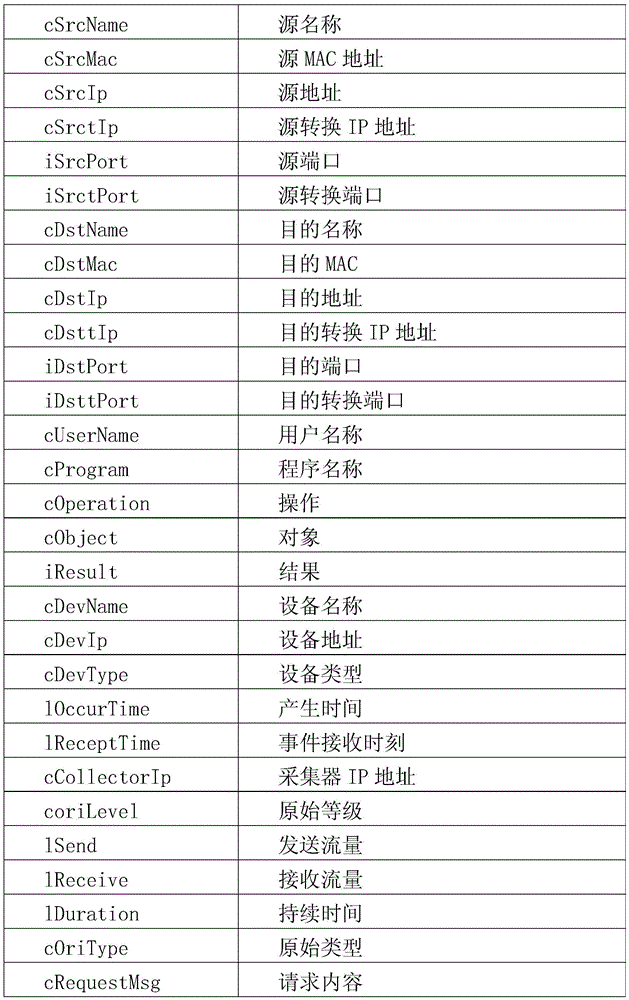
[0037] A method for extracting and analyzing heterogeneous security log information under a complex network system, which includes:
[0038] Step A. Learning phase: Continuously collect heterogeneous security log data, use word segmentation tools to split the log data structure, define the content attributes of the field data at the specified location in the log according to regular matching, and dynamically construct the log information extraction decision tree. LIDT tree, the decision tree information is constantly updated with the addition of new log structures;
[0039] Step B. Cache stage: extract the decision tree information from the log information constructed by learning and cache it in the computer memory, the cache is updated in real time according to the dynamic learning process of the decision tree; it is stored in the hard disk in text form, and the stored information is updated periodically;
[0040] Step C. Parsing stage: Newly collect log data, extract the decision t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com