Voice over internet protocol data overload detection and mitigation system and method
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
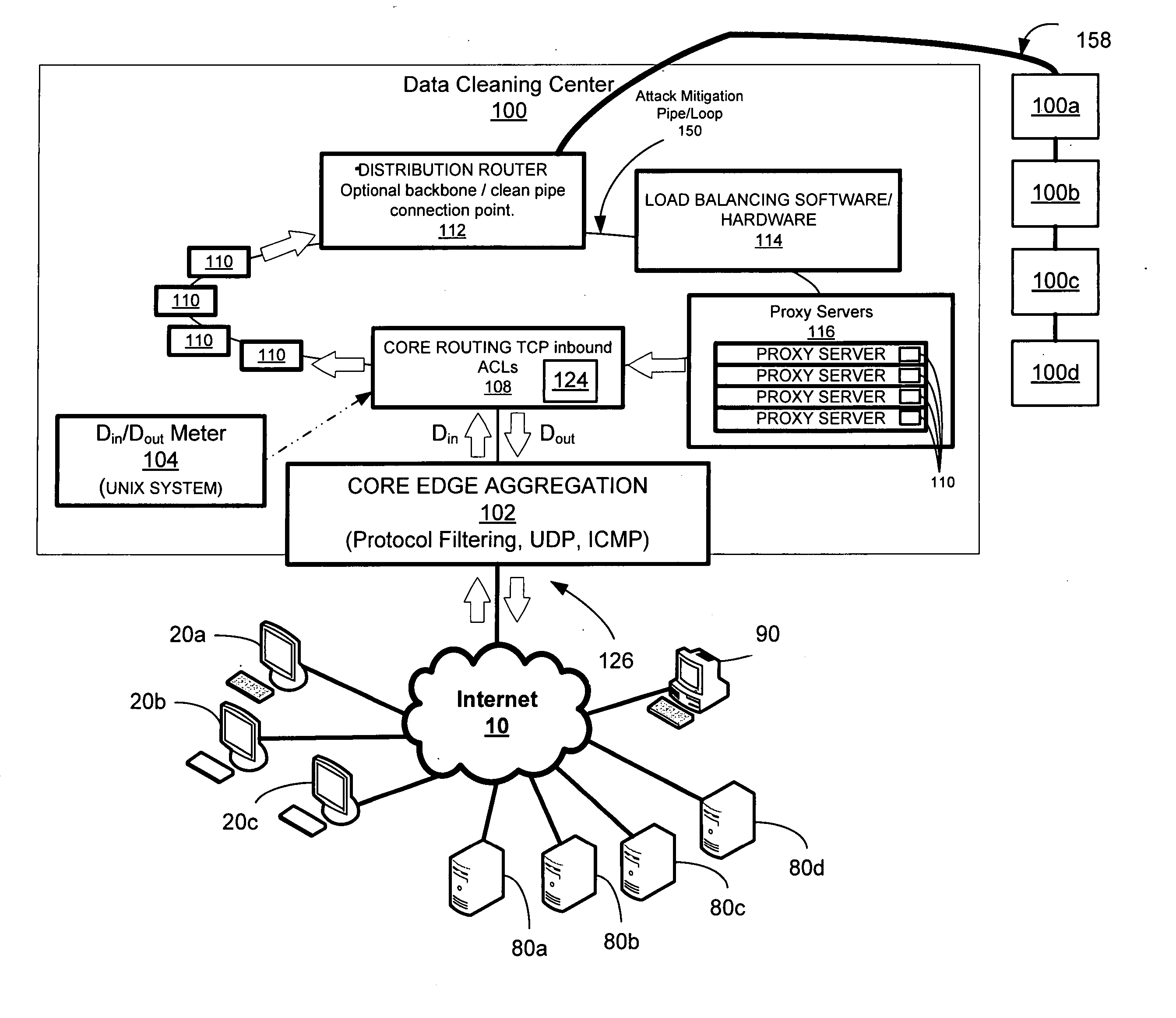
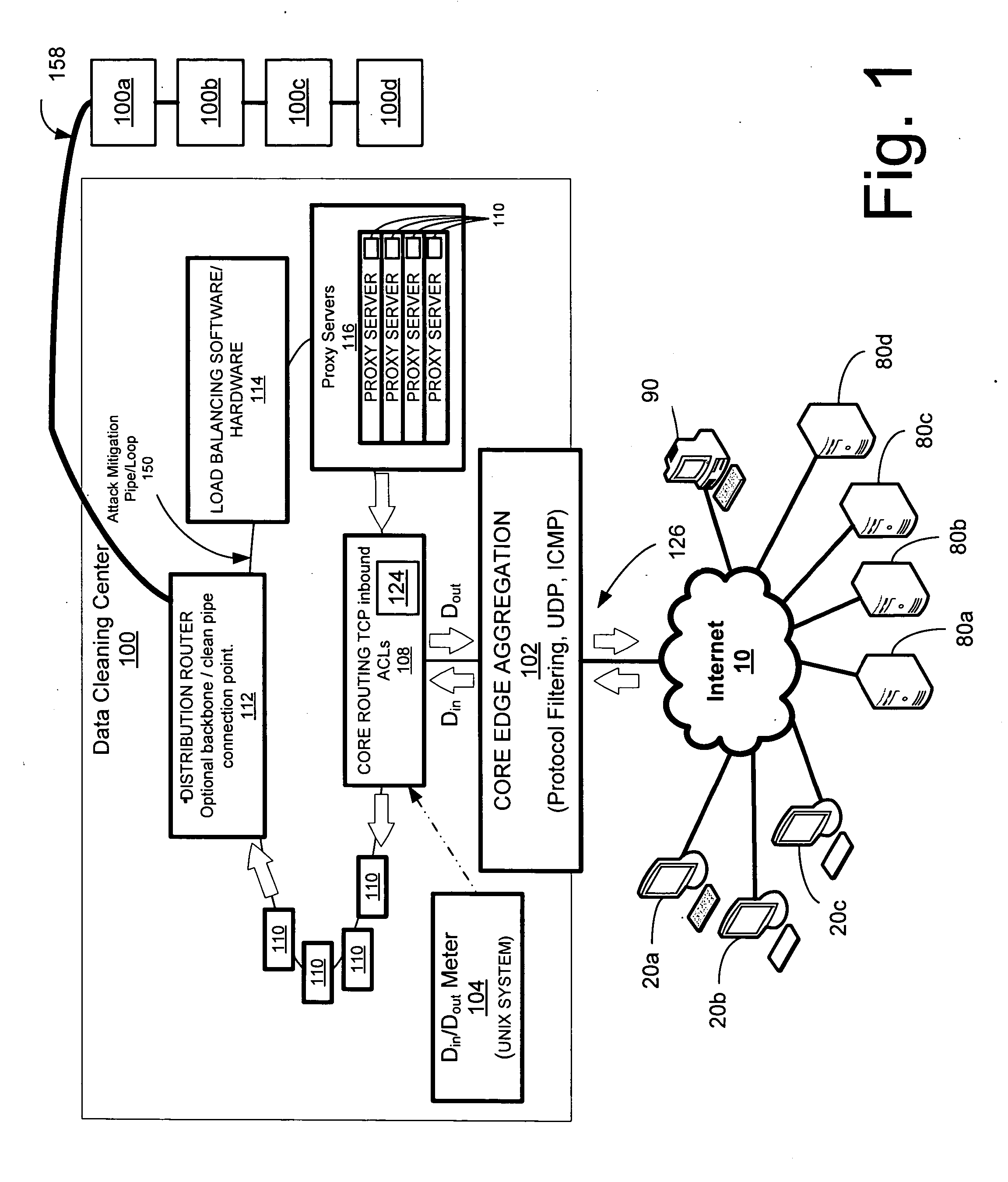
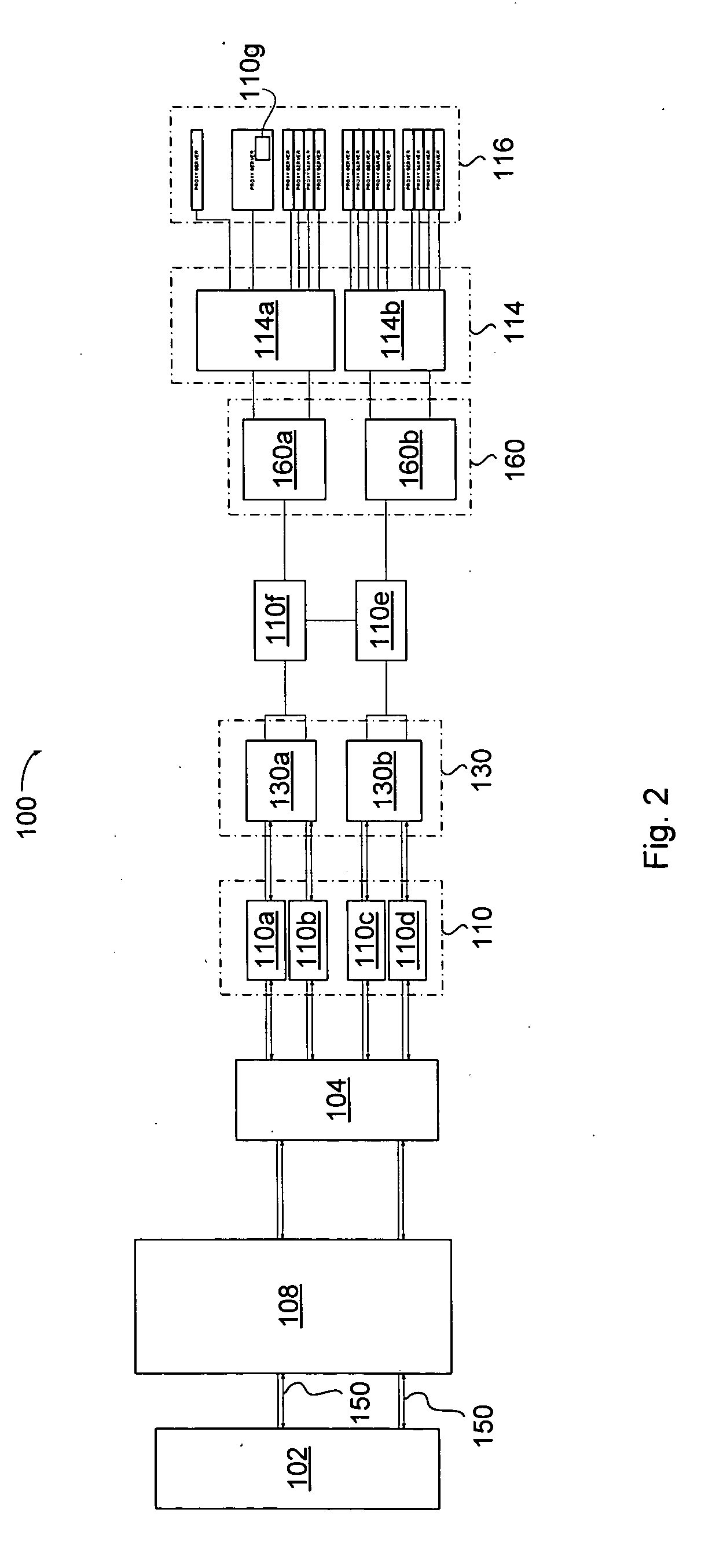
[0050] A preferred embodiment of a system and method for detecting and / or mitigating an overload condition, constructed in accordance with the claimed invention, provides detection and / or mitigation of an overload condition style attack from one or more first computers that target one or more of a plurality of second computers located on a network. Such attack includes, by way of example only, and not by way of limitation a distributed denial of service (DDoS) attack, viral attack or the like. The network may comprise any type of public or private network, such as the Internet, intranet, virtual private network (VPN) or the like.
[0051] Referring now to the drawings, like reference numerals denote like or corresponding parts throughout the drawing figures.
[0052] Referring now to the drawings, like reference numerals denote like or corresponding parts throughout the drawing figures. Shown in FIG. 1 is a preferred data cleaning center 100 according to an exemplary embodiment of the s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com