Security And Isolation Models In UCIe Chiplet Interconnect
SEP 1, 20259 MIN READ
Generate Your Research Report Instantly with AI Agent
Patsnap Eureka helps you evaluate technical feasibility & market potential.
UCIe Security Evolution and Objectives
The evolution of security in UCIe (Universal Chiplet Interconnect Express) has been driven by the increasing complexity of heterogeneous integration and the growing threat landscape in modern computing systems. Initially, when chiplets were primarily used within controlled environments by single manufacturers, security considerations were limited to basic integrity checks and rudimentary authentication mechanisms. As the chiplet ecosystem expanded to include multi-vendor scenarios, security requirements evolved dramatically.
The first generation of UCIe specifications introduced fundamental security concepts, focusing primarily on die-to-die communication integrity. These early implementations addressed basic concerns such as transmission errors and simple authentication protocols but lacked comprehensive security frameworks for advanced threat models.
The current UCIe security architecture has matured significantly, incorporating lessons from other interconnect technologies like PCIe and CXL. Modern implementations now include robust encryption capabilities, hardware-based root-of-trust mechanisms, and secure boot processes that establish a chain of trust from power-on through the entire system initialization.
A key objective of UCIe security evolution is establishing standardized isolation models that enable secure multi-tenancy within chiplet-based systems. This is particularly critical as chiplet architectures increasingly support cloud computing environments where multiple customers may share physical hardware resources while requiring strict security boundaries.
Another central goal is maintaining security without compromising the performance advantages that make chiplet architectures attractive. The ultra-low latency requirements of die-to-die interfaces present unique challenges for implementing cryptographic protocols and security verification mechanisms without introducing unacceptable overhead.
The UCIe consortium has established several specific security objectives, including standardized authentication protocols for chiplet-to-chiplet communication, hardware-based security enclaves within the interconnect fabric, and comprehensive key management frameworks that support both manufacturing-time and runtime security operations.
Looking forward, UCIe security evolution aims to address emerging threats such as side-channel attacks specific to closely-integrated heterogeneous systems, post-quantum cryptographic requirements, and security implications of AI-accelerated chiplets that may process sensitive data. The roadmap also includes enhanced telemetry capabilities for security monitoring and anomaly detection at the interconnect level.
The ultimate objective remains creating a security architecture that balances robust protection with the flexibility needed to support diverse implementation scenarios across different market segments, from high-performance computing to embedded systems with varying security requirements and resource constraints.
The first generation of UCIe specifications introduced fundamental security concepts, focusing primarily on die-to-die communication integrity. These early implementations addressed basic concerns such as transmission errors and simple authentication protocols but lacked comprehensive security frameworks for advanced threat models.
The current UCIe security architecture has matured significantly, incorporating lessons from other interconnect technologies like PCIe and CXL. Modern implementations now include robust encryption capabilities, hardware-based root-of-trust mechanisms, and secure boot processes that establish a chain of trust from power-on through the entire system initialization.
A key objective of UCIe security evolution is establishing standardized isolation models that enable secure multi-tenancy within chiplet-based systems. This is particularly critical as chiplet architectures increasingly support cloud computing environments where multiple customers may share physical hardware resources while requiring strict security boundaries.
Another central goal is maintaining security without compromising the performance advantages that make chiplet architectures attractive. The ultra-low latency requirements of die-to-die interfaces present unique challenges for implementing cryptographic protocols and security verification mechanisms without introducing unacceptable overhead.
The UCIe consortium has established several specific security objectives, including standardized authentication protocols for chiplet-to-chiplet communication, hardware-based security enclaves within the interconnect fabric, and comprehensive key management frameworks that support both manufacturing-time and runtime security operations.
Looking forward, UCIe security evolution aims to address emerging threats such as side-channel attacks specific to closely-integrated heterogeneous systems, post-quantum cryptographic requirements, and security implications of AI-accelerated chiplets that may process sensitive data. The roadmap also includes enhanced telemetry capabilities for security monitoring and anomaly detection at the interconnect level.
The ultimate objective remains creating a security architecture that balances robust protection with the flexibility needed to support diverse implementation scenarios across different market segments, from high-performance computing to embedded systems with varying security requirements and resource constraints.
Market Demand for Secure Chiplet Interconnects
The market demand for secure chiplet interconnects has experienced significant growth in recent years, driven primarily by the increasing complexity of modern computing systems and the evolving threat landscape. As chiplet-based designs become more prevalent across various industries, the need for robust security mechanisms within the Universal Chiplet Interconnect Express (UCIe) framework has become paramount.
Enterprise data centers represent one of the largest market segments demanding secure chiplet interconnects. These facilities process vast amounts of sensitive information and require hardware-level security guarantees to protect against sophisticated attacks. Financial institutions, healthcare providers, and government agencies are particularly concerned about data breaches that could compromise confidential information, making them willing to invest in advanced security features for their computing infrastructure.
Cloud service providers constitute another major market driver, as they must ensure isolation between different customers' workloads running on shared hardware. The multi-tenant nature of cloud computing creates unique security challenges that can be addressed through hardware-based isolation mechanisms in chiplet interconnects. Major cloud providers are actively seeking solutions that can provide verifiable security guarantees to their customers.
The telecommunications sector has also emerged as a significant market for secure chiplet interconnects, especially with the ongoing deployment of 5G networks and the anticipated transition to 6G. These networks require high-performance, secure processing capabilities at the edge, where physical security cannot always be guaranteed. Secure chiplet designs offer a promising solution for these distributed computing environments.
Market research indicates that the semiconductor industry is responding to these demands by incorporating security features directly into chiplet designs. The trend toward disaggregated chip architectures has created new attack surfaces that traditional security approaches cannot adequately address, necessitating innovation in interconnect security.
Consumer electronics manufacturers are increasingly concerned about supply chain security and the potential for hardware-based attacks. As devices become more interconnected and handle more sensitive personal data, the demand for secure components has extended beyond enterprise applications to consumer products. This broadening market base has accelerated investment in secure chiplet technologies.
Automotive and industrial IoT applications represent emerging markets with stringent security requirements. As vehicles and industrial systems become more connected and autonomous, the consequences of security breaches become more severe, potentially affecting physical safety. These sectors demand chiplet interconnects with robust security features to protect against remote attacks and ensure operational integrity.
Enterprise data centers represent one of the largest market segments demanding secure chiplet interconnects. These facilities process vast amounts of sensitive information and require hardware-level security guarantees to protect against sophisticated attacks. Financial institutions, healthcare providers, and government agencies are particularly concerned about data breaches that could compromise confidential information, making them willing to invest in advanced security features for their computing infrastructure.
Cloud service providers constitute another major market driver, as they must ensure isolation between different customers' workloads running on shared hardware. The multi-tenant nature of cloud computing creates unique security challenges that can be addressed through hardware-based isolation mechanisms in chiplet interconnects. Major cloud providers are actively seeking solutions that can provide verifiable security guarantees to their customers.
The telecommunications sector has also emerged as a significant market for secure chiplet interconnects, especially with the ongoing deployment of 5G networks and the anticipated transition to 6G. These networks require high-performance, secure processing capabilities at the edge, where physical security cannot always be guaranteed. Secure chiplet designs offer a promising solution for these distributed computing environments.
Market research indicates that the semiconductor industry is responding to these demands by incorporating security features directly into chiplet designs. The trend toward disaggregated chip architectures has created new attack surfaces that traditional security approaches cannot adequately address, necessitating innovation in interconnect security.
Consumer electronics manufacturers are increasingly concerned about supply chain security and the potential for hardware-based attacks. As devices become more interconnected and handle more sensitive personal data, the demand for secure components has extended beyond enterprise applications to consumer products. This broadening market base has accelerated investment in secure chiplet technologies.
Automotive and industrial IoT applications represent emerging markets with stringent security requirements. As vehicles and industrial systems become more connected and autonomous, the consequences of security breaches become more severe, potentially affecting physical safety. These sectors demand chiplet interconnects with robust security features to protect against remote attacks and ensure operational integrity.
Current Security Challenges in UCIe Implementation
The implementation of UCIe (Universal Chiplet Interconnect Express) faces significant security challenges that must be addressed to ensure the integrity and confidentiality of data across chiplet boundaries. As chiplets from different vendors are integrated into a single package, the traditional security perimeter expands, creating new attack surfaces and vulnerabilities.
One primary challenge is establishing trust between heterogeneous chiplets. Unlike traditional SoCs where all components are designed and manufactured by a single vendor, UCIe-based systems may incorporate chiplets from multiple sources with varying security standards and implementations. This multi-vendor ecosystem complicates the establishment of a root of trust and secure boot sequences across the entire package.
Data protection during transit between chiplets presents another critical challenge. The high-speed die-to-die interfaces in UCIe must implement robust encryption and authentication mechanisms to prevent data interception or tampering. However, implementing cryptographic operations at UCIe's high data rates (up to 32 GT/s) without introducing significant latency remains technically challenging, creating a performance-security tradeoff.
Side-channel attacks pose a particular threat in the chiplet architecture. The physical proximity of chiplets from different security domains increases the risk of power analysis, electromagnetic emanation, and timing attacks. These side-channel vulnerabilities could potentially allow malicious chiplets to extract sensitive information from neighboring components.
Resource isolation represents another significant challenge. UCIe must provide mechanisms to enforce strict boundaries between chiplets with different security classifications or trust levels. This includes memory protection, access control for shared resources, and prevention of unauthorized DMA (Direct Memory Access) operations across chiplet boundaries.
The verification and certification of security properties in UCIe implementations is exceptionally difficult. Current security certification methodologies are not well-adapted to heterogeneous chiplet architectures, making it challenging to provide comprehensive security assurances for the integrated system.
Supply chain security concerns are amplified in the chiplet ecosystem. The increased number of components and manufacturers involved in a single package raises the risk of hardware trojans, counterfeits, or compromised components entering the supply chain. Detecting such security breaches becomes more complex as responsibility is distributed across multiple vendors.
Finally, the UCIe specification itself is still evolving in terms of security features. While the standard provides a foundation for physical and protocol layers, comprehensive security models and requirements are still under development. This creates uncertainty for implementers and potential inconsistencies in security approaches across the ecosystem.
One primary challenge is establishing trust between heterogeneous chiplets. Unlike traditional SoCs where all components are designed and manufactured by a single vendor, UCIe-based systems may incorporate chiplets from multiple sources with varying security standards and implementations. This multi-vendor ecosystem complicates the establishment of a root of trust and secure boot sequences across the entire package.
Data protection during transit between chiplets presents another critical challenge. The high-speed die-to-die interfaces in UCIe must implement robust encryption and authentication mechanisms to prevent data interception or tampering. However, implementing cryptographic operations at UCIe's high data rates (up to 32 GT/s) without introducing significant latency remains technically challenging, creating a performance-security tradeoff.
Side-channel attacks pose a particular threat in the chiplet architecture. The physical proximity of chiplets from different security domains increases the risk of power analysis, electromagnetic emanation, and timing attacks. These side-channel vulnerabilities could potentially allow malicious chiplets to extract sensitive information from neighboring components.
Resource isolation represents another significant challenge. UCIe must provide mechanisms to enforce strict boundaries between chiplets with different security classifications or trust levels. This includes memory protection, access control for shared resources, and prevention of unauthorized DMA (Direct Memory Access) operations across chiplet boundaries.
The verification and certification of security properties in UCIe implementations is exceptionally difficult. Current security certification methodologies are not well-adapted to heterogeneous chiplet architectures, making it challenging to provide comprehensive security assurances for the integrated system.
Supply chain security concerns are amplified in the chiplet ecosystem. The increased number of components and manufacturers involved in a single package raises the risk of hardware trojans, counterfeits, or compromised components entering the supply chain. Detecting such security breaches becomes more complex as responsibility is distributed across multiple vendors.
Finally, the UCIe specification itself is still evolving in terms of security features. While the standard provides a foundation for physical and protocol layers, comprehensive security models and requirements are still under development. This creates uncertainty for implementers and potential inconsistencies in security approaches across the ecosystem.
Existing UCIe Isolation and Security Mechanisms
01 Security mechanisms for UCIe chiplet interconnects
Various security mechanisms can be implemented in UCIe chiplet interconnects to protect against unauthorized access and data breaches. These include encryption protocols, secure boot processes, and authentication systems that verify the identity of connected chiplets. Such security features help maintain data integrity across the interconnect while preventing malicious attacks or tampering with the communication between chiplets.- Security mechanisms for UCIe chiplet interconnects: Various security mechanisms can be implemented in UCIe chiplet interconnects to protect against unauthorized access and data breaches. These include encryption protocols, secure boot processes, and authentication systems that verify the identity of connected chiplets. Such security features help maintain data integrity across the interconnect while preventing malicious attacks or tampering attempts in multi-chiplet systems.
- Isolation techniques for chiplet domains: Isolation techniques are essential for maintaining separation between different functional domains in chiplet-based systems. These techniques include physical isolation barriers, logical partitioning, and dedicated security zones that prevent unauthorized data flow between chiplets. By implementing robust isolation mechanisms, designers can ensure that sensitive operations remain protected even when multiple chiplets from different vendors are integrated into a single package.
- Secure communication protocols for inter-chiplet data transfer: Secure communication protocols are implemented to protect data as it travels between chiplets via UCIe interfaces. These protocols include encrypted channels, secure handshaking mechanisms, and integrity verification methods that ensure data remains protected during transit. By establishing trusted communication pathways, chiplet-based systems can maintain confidentiality and integrity of sensitive information across the interconnect fabric.
- Hardware-based security features for UCIe implementations: Hardware-based security features provide robust protection for UCIe chiplet interconnects through physical security mechanisms. These include secure enclaves, hardware root of trust, tamper-resistant modules, and physical unclonable functions (PUFs) that create unique chiplet identities. By embedding security directly into the hardware, these features offer stronger protection against sophisticated attacks compared to software-only solutions, ensuring the integrity of the entire chiplet ecosystem.
- Security monitoring and threat detection in chiplet systems: Security monitoring and threat detection systems are crucial for maintaining the integrity of UCIe chiplet interconnects. These systems include real-time monitoring of data traffic patterns, anomaly detection algorithms, and intrusion prevention mechanisms that can identify and respond to potential security breaches. By continuously monitoring the interconnect activity, these systems can detect unauthorized access attempts or suspicious behavior, allowing for rapid response to security threats in chiplet-based architectures.
02 Isolation techniques for chiplet interconnects
Isolation techniques are crucial for maintaining separation between different functional domains in chiplet-based systems. These techniques include physical isolation barriers, logical isolation through dedicated channels, and power domain isolation. By implementing robust isolation methods, chiplet designs can prevent interference between components, contain faults within specific domains, and enhance overall system reliability while maintaining the performance benefits of integrated chiplet architectures.Expand Specific Solutions03 Secure communication protocols for UCIe
Secure communication protocols specifically designed for UCIe implementations ensure protected data transfer between chiplets. These protocols include encrypted data channels, secure handshaking mechanisms, and integrity verification methods that detect tampering or data corruption. Advanced protocols may also incorporate features like secure key exchange and session management to establish trusted communication paths between chiplets, even when integrated into complex systems-on-package designs.Expand Specific Solutions04 Hardware-based security features for chiplet architectures
Hardware-based security features embedded directly into chiplet designs provide robust protection against various threats. These include physical unclonable functions (PUFs) for unique identification, hardware root of trust implementations, secure enclaves for sensitive operations, and tamper-resistant circuitry. Such hardware security elements create a foundation for establishing trusted execution environments within chiplet-based systems while minimizing performance overhead compared to software-only security solutions.Expand Specific Solutions05 Security monitoring and management for UCIe implementations
Security monitoring and management systems for UCIe implementations provide continuous oversight of chiplet interconnect activities. These systems include real-time threat detection mechanisms, anomaly detection algorithms that identify unusual behavior patterns, and management interfaces for security policy enforcement. Advanced implementations may incorporate machine learning techniques to adapt to emerging threats and provide comprehensive security analytics for system administrators to maintain the integrity of chiplet-based architectures.Expand Specific Solutions
Key Industry Players in Chiplet Security Ecosystem
The UCIe chiplet interconnect security landscape is evolving rapidly, currently in its early growth phase with increasing market adoption. The technology is approaching maturity with key players developing robust security and isolation models. Intel, AMD (through Xilinx acquisition), and NVIDIA lead with advanced implementations, while TSMC, GlobalFoundries, and Samsung provide essential manufacturing support. Qualcomm and IBM contribute significant innovations in secure chiplet communications. Chinese entities like Huawei and Ziguang Qingteng are emerging competitors, focusing on sovereign security solutions. The market is characterized by collaborative standardization efforts alongside competitive proprietary implementations, with security becoming a critical differentiator as chiplet adoption accelerates across data centers, AI systems, and high-performance computing.
Intel Corp.
Technical Solution: Intel has developed a comprehensive security architecture for UCIe (Universal Chiplet Interconnect Express) that implements a multi-layered approach to chiplet security. Their solution incorporates hardware-based security features including a Root of Trust (RoT) within each chiplet that establishes secure boot processes and runtime attestation. Intel's UCIe implementation utilizes a secure enclave architecture where sensitive operations are isolated in protected execution environments with dedicated memory regions. For inter-chiplet communication security, Intel employs end-to-end encryption with AES-GCM protocols and implements a zero-trust security model requiring mutual authentication between chiplets before establishing secure channels. Their security framework also includes hardware-based key management systems that generate, store, and manage cryptographic keys within secure elements, preventing exposure to software vulnerabilities. Intel has further enhanced their UCIe security with advanced memory protection mechanisms that enforce strict access controls and prevent unauthorized data access between chiplets.
Strengths: Intel's extensive experience in x86 architecture security provides robust protection mechanisms with minimal performance overhead. Their established ecosystem allows for comprehensive security validation across multiple chiplet vendors. Weaknesses: The complexity of Intel's security model may increase integration challenges for third-party chiplet manufacturers and potentially impact time-to-market for heterogeneous chiplet designs.
International Business Machines Corp.
Technical Solution: IBM has pioneered a security framework for UCIe chiplet interconnects centered around their Secure Service Container (SSC) technology adapted for chiplet architectures. This approach creates isolated security domains within the chiplet ecosystem, with each domain having strictly controlled communication channels. IBM's implementation features hardware-enforced memory isolation that prevents unauthorized access across chiplet boundaries through memory address translation and permission checking at the hardware level. Their solution incorporates a hierarchical trust model where a primary secure chiplet manages the security policies and authentication for subordinate chiplets in the package. For data protection, IBM employs inline encryption/decryption engines at UCIe interfaces that secure data in transit between chiplets without significant latency penalties. The company has also developed specialized secure elements within their chiplet designs that handle cryptographic operations, key storage, and security policy enforcement isolated from general processing elements. IBM's approach includes continuous integrity monitoring that detects and responds to potential security violations in real-time across the chiplet interconnect.
Strengths: IBM's solution offers enterprise-grade security features with particular strength in cryptographic acceleration and hardware-based isolation. Their approach excels in high-security environments like financial services and government applications. Weaknesses: The implementation may require additional silicon area dedicated to security functions, potentially increasing manufacturing costs and power consumption compared to less secure alternatives.
Critical Patents in Chiplet Security Technologies
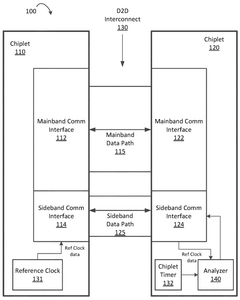
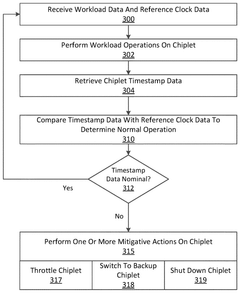
Chiplet timestamp verification
PatentWO2025082629A1
Innovation
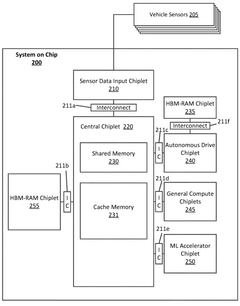
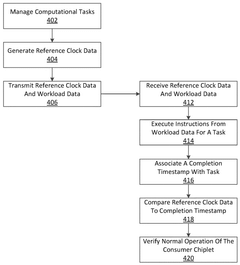
- A multi-chiplet computing apparatus is implemented, comprising a primary chiplet and a consumer chiplet connected via a UCIe interconnect, which includes a mainband data path for performance-based communications and a sideband data path for reporting and scheduling data. The consumer chiplet receives reference clock data and power consumption data from the primary chiplet, uses this data to verify its own operation, and can initiate mitigative actions if anomalies are detected.
Functional safety for system-on-chip arrangements
PatentPendingUS20240430125A1
Innovation
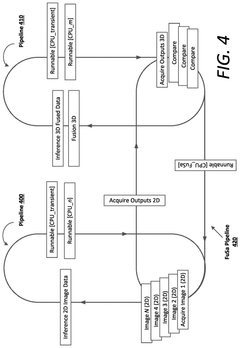
- A computing system with multiple System-on-Chip (SoC) arrangements, including a primary and backup SoC, executes a Functional Safety (FuSa) program to monitor shared memory, compare and verify independent pipeline outputs, and generate error correction codes, ensuring robust hardware components and reliable communication between chiplets, thereby enhancing ASIL ratings.
Standardization Efforts in Chiplet Security
The standardization of chiplet security has become a critical focus area as the industry moves toward disaggregated chip designs. The Universal Chiplet Interconnect Express (UCIe) consortium, formed in 2022, has established a dedicated security working group to address the unique challenges posed by multi-die architectures. This group is developing comprehensive specifications for secure communication between chiplets, focusing on authentication protocols, encryption standards, and secure boot mechanisms.
Beyond UCIe, other industry bodies are making significant contributions to chiplet security standardization. The CHIPS Alliance has proposed open-source security frameworks specifically designed for chiplet interfaces, emphasizing transparency and community-driven security solutions. Similarly, the Open Compute Project (OCP) has established guidelines for secure chiplet integration in data center applications, recognizing the heightened security requirements in these environments.
The Trusted Computing Group (TCG) has extended its hardware security standards to encompass chiplet architectures, adapting established concepts like the Trusted Platform Module (TPM) to function effectively in disaggregated designs. These efforts aim to ensure that security primitives remain robust even when distributed across multiple dies.
Standardization efforts are also addressing the unique supply chain security concerns inherent to chiplet-based designs. The Common Criteria for Information Technology Security Evaluation has begun developing evaluation methodologies specifically for multi-die packages, helping establish trust in components sourced from different vendors. This work is complemented by NIST's efforts to create security assessment frameworks for heterogeneous integration technologies.
Industry-academia partnerships are playing a crucial role in advancing chiplet security standards. Research consortia like DARPA's CHIPS program and the European Processor Initiative have established security requirements that are informing formal standardization processes. These collaborative efforts are helping bridge the gap between theoretical security models and practical implementation guidelines.
The emerging standards are increasingly focusing on hardware-based security features, including physically unclonable functions (PUFs) for die authentication and secure enclaves for protecting sensitive operations across chiplet boundaries. These hardware-centric approaches are being codified into formal specifications that vendors can implement consistently across different product lines.
Beyond UCIe, other industry bodies are making significant contributions to chiplet security standardization. The CHIPS Alliance has proposed open-source security frameworks specifically designed for chiplet interfaces, emphasizing transparency and community-driven security solutions. Similarly, the Open Compute Project (OCP) has established guidelines for secure chiplet integration in data center applications, recognizing the heightened security requirements in these environments.
The Trusted Computing Group (TCG) has extended its hardware security standards to encompass chiplet architectures, adapting established concepts like the Trusted Platform Module (TPM) to function effectively in disaggregated designs. These efforts aim to ensure that security primitives remain robust even when distributed across multiple dies.
Standardization efforts are also addressing the unique supply chain security concerns inherent to chiplet-based designs. The Common Criteria for Information Technology Security Evaluation has begun developing evaluation methodologies specifically for multi-die packages, helping establish trust in components sourced from different vendors. This work is complemented by NIST's efforts to create security assessment frameworks for heterogeneous integration technologies.
Industry-academia partnerships are playing a crucial role in advancing chiplet security standards. Research consortia like DARPA's CHIPS program and the European Processor Initiative have established security requirements that are informing formal standardization processes. These collaborative efforts are helping bridge the gap between theoretical security models and practical implementation guidelines.
The emerging standards are increasingly focusing on hardware-based security features, including physically unclonable functions (PUFs) for die authentication and secure enclaves for protecting sensitive operations across chiplet boundaries. These hardware-centric approaches are being codified into formal specifications that vendors can implement consistently across different product lines.
Supply Chain Security Considerations for UCIe
The UCIe (Universal Chiplet Interconnect Express) ecosystem introduces unique supply chain security challenges that must be addressed to ensure the integrity of multi-vendor chiplet-based systems. As chiplets from different manufacturers are integrated into a single package, the attack surface expands significantly, creating potential vulnerabilities at each stage of the supply chain.
Manufacturing security represents a critical concern, as chiplets may be produced by various foundries with different security protocols and quality control standards. Without robust verification mechanisms, malicious modifications or hardware trojans could be introduced during fabrication. The UCIe standard must therefore incorporate manufacturing certificates and secure provenance tracking to validate chiplet origins and production integrity.
Integration security poses another significant challenge, as the assembly process brings together components from multiple vendors. This creates opportunities for tampering or substitution of chiplets before final packaging. Implementing secure assembly facilities with comprehensive monitoring and authentication protocols becomes essential to mitigate these risks. Additionally, the UCIe specification should include mechanisms for post-integration verification to confirm that no unauthorized modifications occurred during the assembly process.
Distribution channels represent a third vulnerability point, where intercepted chiplet packages could be compromised before reaching end users. Secure packaging with tamper-evident seals and cryptographic verification methods can help address this concern. The UCIe ecosystem would benefit from implementing a secure chain-of-custody documentation system that tracks components from manufacturing through distribution.
Trust models within the UCIe ecosystem must evolve to accommodate multi-vendor scenarios. Traditional single-vendor systems benefit from unified security protocols, but chiplet-based designs require new frameworks for establishing trust between components from different sources. This necessitates the development of standardized security interfaces and protocols that enable secure communication between chiplets regardless of their origin.
Long-term supply chain resilience for UCIe technology depends on establishing industry-wide security standards and certification processes. These should include requirements for chiplet authentication, secure boot sequences, and runtime verification mechanisms. Creating a collaborative security framework among UCIe consortium members would strengthen the entire ecosystem against supply chain attacks while maintaining the benefits of modular chiplet design.
Manufacturing security represents a critical concern, as chiplets may be produced by various foundries with different security protocols and quality control standards. Without robust verification mechanisms, malicious modifications or hardware trojans could be introduced during fabrication. The UCIe standard must therefore incorporate manufacturing certificates and secure provenance tracking to validate chiplet origins and production integrity.
Integration security poses another significant challenge, as the assembly process brings together components from multiple vendors. This creates opportunities for tampering or substitution of chiplets before final packaging. Implementing secure assembly facilities with comprehensive monitoring and authentication protocols becomes essential to mitigate these risks. Additionally, the UCIe specification should include mechanisms for post-integration verification to confirm that no unauthorized modifications occurred during the assembly process.
Distribution channels represent a third vulnerability point, where intercepted chiplet packages could be compromised before reaching end users. Secure packaging with tamper-evident seals and cryptographic verification methods can help address this concern. The UCIe ecosystem would benefit from implementing a secure chain-of-custody documentation system that tracks components from manufacturing through distribution.
Trust models within the UCIe ecosystem must evolve to accommodate multi-vendor scenarios. Traditional single-vendor systems benefit from unified security protocols, but chiplet-based designs require new frameworks for establishing trust between components from different sources. This necessitates the development of standardized security interfaces and protocols that enable secure communication between chiplets regardless of their origin.
Long-term supply chain resilience for UCIe technology depends on establishing industry-wide security standards and certification processes. These should include requirements for chiplet authentication, secure boot sequences, and runtime verification mechanisms. Creating a collaborative security framework among UCIe consortium members would strengthen the entire ecosystem against supply chain attacks while maintaining the benefits of modular chiplet design.
Unlock deeper insights with Patsnap Eureka Quick Research — get a full tech report to explore trends and direct your research. Try now!
Generate Your Research Report Instantly with AI Agent
Supercharge your innovation with Patsnap Eureka AI Agent Platform!