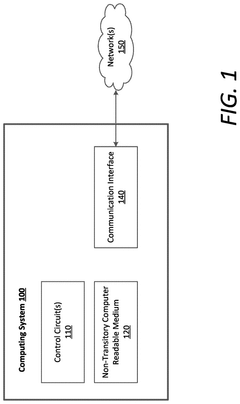
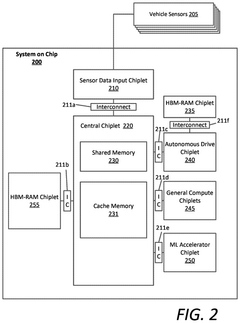
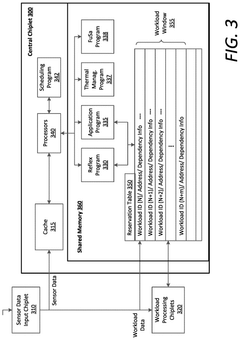
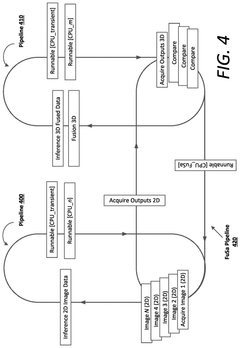
UCIe Chiplet Interconnect Chiplet Security Threat Modeling
SEP 1, 20259 MIN READ
Generate Your Research Report Instantly with AI Agent
Patsnap Eureka helps you evaluate technical feasibility & market potential.
UCIe Chiplet Interconnect Security Background and Objectives
Universal Chiplet Interconnect Express (UCIe) represents a significant advancement in semiconductor integration technology, enabling heterogeneous chiplet-based designs that overcome the limitations of traditional monolithic chip architectures. The evolution of chiplet technology has been driven by the slowing of Moore's Law and the increasing demand for specialized computing capabilities across diverse applications including high-performance computing, artificial intelligence, and edge devices.
The development of UCIe began as an industry response to the fragmentation of chiplet interconnect standards. Prior to UCIe, various proprietary solutions such as Intel's EMIB, AMD's Infinity Fabric, and TSMC's CoWoS created a complex ecosystem that hindered interoperability and broad adoption. The UCIe consortium, formed in 2022 with founding members including Intel, AMD, Arm, TSMC, and Samsung, aimed to establish a unified open standard for die-to-die interconnection.
As chiplet adoption accelerates, security considerations have emerged as a critical concern. The disaggregation of traditionally monolithic systems into multiple chiplets introduces new attack surfaces and security challenges that were previously contained within a single silicon die. These include potential vulnerabilities at physical interconnect boundaries, side-channel attacks leveraging proximity of heterogeneous components, and supply chain security risks due to multi-vendor integration scenarios.
The primary objective of UCIe chiplet security threat modeling is to systematically identify, categorize, and mitigate potential security vulnerabilities specific to chiplet-based architectures. This includes developing comprehensive security frameworks that address both hardware and protocol-level threats across the entire chiplet ecosystem, from design and manufacturing to deployment and operation.
Key technical goals include establishing robust authentication mechanisms between chiplets, implementing secure boot sequences for multi-die systems, developing effective isolation between chiplets with different trust levels, and creating standardized security protocols that maintain the performance advantages of UCIe while providing necessary protection against emerging threats.
The evolution of UCIe security standards must balance competing requirements: maintaining the performance benefits that make chiplet architectures attractive while implementing sufficient security measures; ensuring backward compatibility with existing designs; and creating scalable solutions that can adapt to increasingly complex chiplet configurations and emerging attack vectors.
As the industry transitions toward greater reliance on chiplet-based designs, establishing a thorough understanding of the security landscape becomes essential for maintaining trust in these systems across critical applications in data centers, telecommunications infrastructure, automotive systems, and other domains where both performance and security are non-negotiable requirements.
The development of UCIe began as an industry response to the fragmentation of chiplet interconnect standards. Prior to UCIe, various proprietary solutions such as Intel's EMIB, AMD's Infinity Fabric, and TSMC's CoWoS created a complex ecosystem that hindered interoperability and broad adoption. The UCIe consortium, formed in 2022 with founding members including Intel, AMD, Arm, TSMC, and Samsung, aimed to establish a unified open standard for die-to-die interconnection.
As chiplet adoption accelerates, security considerations have emerged as a critical concern. The disaggregation of traditionally monolithic systems into multiple chiplets introduces new attack surfaces and security challenges that were previously contained within a single silicon die. These include potential vulnerabilities at physical interconnect boundaries, side-channel attacks leveraging proximity of heterogeneous components, and supply chain security risks due to multi-vendor integration scenarios.
The primary objective of UCIe chiplet security threat modeling is to systematically identify, categorize, and mitigate potential security vulnerabilities specific to chiplet-based architectures. This includes developing comprehensive security frameworks that address both hardware and protocol-level threats across the entire chiplet ecosystem, from design and manufacturing to deployment and operation.
Key technical goals include establishing robust authentication mechanisms between chiplets, implementing secure boot sequences for multi-die systems, developing effective isolation between chiplets with different trust levels, and creating standardized security protocols that maintain the performance advantages of UCIe while providing necessary protection against emerging threats.
The evolution of UCIe security standards must balance competing requirements: maintaining the performance benefits that make chiplet architectures attractive while implementing sufficient security measures; ensuring backward compatibility with existing designs; and creating scalable solutions that can adapt to increasingly complex chiplet configurations and emerging attack vectors.
As the industry transitions toward greater reliance on chiplet-based designs, establishing a thorough understanding of the security landscape becomes essential for maintaining trust in these systems across critical applications in data centers, telecommunications infrastructure, automotive systems, and other domains where both performance and security are non-negotiable requirements.
Market Demand Analysis for Secure Chiplet Interconnects
The global market for secure chiplet interconnects is experiencing robust growth, driven by the increasing adoption of heterogeneous integration in semiconductor design. As traditional monolithic chip scaling faces physical and economic limitations, the chiplet approach has emerged as a viable alternative, allowing different functional blocks to be manufactured separately and then integrated. This market is projected to reach significant value by 2028, with a compound annual growth rate exceeding 35% from 2023 to 2028.
Security concerns have become paramount as chiplet-based designs gain traction across multiple industries. The financial services sector demands secure chiplet interconnects to protect sensitive transaction data and prevent financial fraud. Healthcare organizations require robust security measures to safeguard patient information and ensure the integrity of medical devices. Defense and aerospace industries prioritize secure chiplet solutions to protect classified information and maintain operational security in mission-critical systems.
Market research indicates that approximately 78% of semiconductor companies are actively investing in chiplet technology, with security considerations being a top priority for over 65% of these investments. The UCIe (Universal Chiplet Interconnect Express) standard has emerged as a critical enabler for the secure chiplet ecosystem, with adoption rates accelerating across the industry.
Consumer electronics represents the largest market segment for secure chiplet interconnects, followed by data centers and telecommunications infrastructure. The proliferation of edge computing and IoT devices is creating new demand vectors, as these distributed systems require robust security measures to protect against increasingly sophisticated cyber threats.
Regional analysis shows North America leading the market for secure chiplet interconnects, followed by Asia-Pacific and Europe. China's significant investments in semiconductor self-sufficiency are accelerating demand for secure chiplet technologies in the Asia-Pacific region, while Europe's focus on data privacy regulations is driving adoption in various industrial applications.
The market is witnessing a shift from proprietary interconnect solutions toward standardized approaches like UCIe, which promises to reduce integration challenges while maintaining security requirements. This standardization is expected to lower barriers to entry and expand the ecosystem of chiplet providers, potentially accelerating market growth.
Customer surveys reveal that data integrity, authentication mechanisms, and protection against side-channel attacks are the most valued security features in chiplet interconnect solutions. The ability to implement hardware-based security measures without significant performance penalties is consistently rated as a critical market requirement.
Security concerns have become paramount as chiplet-based designs gain traction across multiple industries. The financial services sector demands secure chiplet interconnects to protect sensitive transaction data and prevent financial fraud. Healthcare organizations require robust security measures to safeguard patient information and ensure the integrity of medical devices. Defense and aerospace industries prioritize secure chiplet solutions to protect classified information and maintain operational security in mission-critical systems.
Market research indicates that approximately 78% of semiconductor companies are actively investing in chiplet technology, with security considerations being a top priority for over 65% of these investments. The UCIe (Universal Chiplet Interconnect Express) standard has emerged as a critical enabler for the secure chiplet ecosystem, with adoption rates accelerating across the industry.
Consumer electronics represents the largest market segment for secure chiplet interconnects, followed by data centers and telecommunications infrastructure. The proliferation of edge computing and IoT devices is creating new demand vectors, as these distributed systems require robust security measures to protect against increasingly sophisticated cyber threats.
Regional analysis shows North America leading the market for secure chiplet interconnects, followed by Asia-Pacific and Europe. China's significant investments in semiconductor self-sufficiency are accelerating demand for secure chiplet technologies in the Asia-Pacific region, while Europe's focus on data privacy regulations is driving adoption in various industrial applications.
The market is witnessing a shift from proprietary interconnect solutions toward standardized approaches like UCIe, which promises to reduce integration challenges while maintaining security requirements. This standardization is expected to lower barriers to entry and expand the ecosystem of chiplet providers, potentially accelerating market growth.
Customer surveys reveal that data integrity, authentication mechanisms, and protection against side-channel attacks are the most valued security features in chiplet interconnect solutions. The ability to implement hardware-based security measures without significant performance penalties is consistently rated as a critical market requirement.
Current Security Challenges in UCIe Chiplet Technology
UCIe (Universal Chiplet Interconnect Express) technology faces several critical security challenges as the industry moves toward disaggregated chip designs. The integration of multiple chiplets from different vendors introduces unprecedented security vulnerabilities across the physical, protocol, and system levels.
At the physical layer, side-channel attacks represent a significant threat. The close proximity of chiplets from different security domains enables power analysis, electromagnetic emanation monitoring, and thermal analysis attacks. These physical vulnerabilities are particularly concerning because traditional isolation mechanisms used in monolithic designs are not applicable in the multi-chiplet architecture. Additionally, the die-to-die interfaces present potential probing points that sophisticated attackers could exploit to extract sensitive information.
Protocol-level vulnerabilities constitute another major challenge. The UCIe standard defines communication protocols between chiplets, but these protocols may contain exploitable flaws. Potential attacks include replay attacks, where legitimate transactions are captured and maliciously replayed; man-in-the-middle attacks that intercept and potentially modify communications between chiplets; and denial-of-service attacks that could disrupt the entire system by targeting inter-chiplet communications.
Trust establishment between chiplets from different vendors presents a fundamental security challenge. Without robust authentication mechanisms, malicious chiplets could be introduced into the package, potentially compromising the entire system. The industry currently lacks standardized methods for chiplet authentication and secure boot processes in multi-vendor environments.
Data protection across chiplet boundaries remains problematic. While data may be encrypted during transmission between chiplets, key management across multiple vendor components introduces significant complexity. Furthermore, the encryption/decryption processes themselves may create performance bottlenecks that designers might be tempted to bypass for performance reasons.
Supply chain security represents another critical vulnerability. The multi-vendor nature of chiplet-based designs increases the risk of hardware Trojans or backdoors being introduced during manufacturing. Current verification techniques are insufficient to detect sophisticated hardware-level threats across chiplet boundaries.
Finally, the heterogeneous nature of chiplet designs complicates security monitoring and threat detection. Traditional security monitoring approaches designed for monolithic chips are inadequate for detecting cross-chiplet attack patterns. The industry lacks comprehensive security monitoring frameworks specifically designed for UCIe-based systems that can detect anomalous behaviors across chiplet boundaries.
At the physical layer, side-channel attacks represent a significant threat. The close proximity of chiplets from different security domains enables power analysis, electromagnetic emanation monitoring, and thermal analysis attacks. These physical vulnerabilities are particularly concerning because traditional isolation mechanisms used in monolithic designs are not applicable in the multi-chiplet architecture. Additionally, the die-to-die interfaces present potential probing points that sophisticated attackers could exploit to extract sensitive information.
Protocol-level vulnerabilities constitute another major challenge. The UCIe standard defines communication protocols between chiplets, but these protocols may contain exploitable flaws. Potential attacks include replay attacks, where legitimate transactions are captured and maliciously replayed; man-in-the-middle attacks that intercept and potentially modify communications between chiplets; and denial-of-service attacks that could disrupt the entire system by targeting inter-chiplet communications.
Trust establishment between chiplets from different vendors presents a fundamental security challenge. Without robust authentication mechanisms, malicious chiplets could be introduced into the package, potentially compromising the entire system. The industry currently lacks standardized methods for chiplet authentication and secure boot processes in multi-vendor environments.
Data protection across chiplet boundaries remains problematic. While data may be encrypted during transmission between chiplets, key management across multiple vendor components introduces significant complexity. Furthermore, the encryption/decryption processes themselves may create performance bottlenecks that designers might be tempted to bypass for performance reasons.
Supply chain security represents another critical vulnerability. The multi-vendor nature of chiplet-based designs increases the risk of hardware Trojans or backdoors being introduced during manufacturing. Current verification techniques are insufficient to detect sophisticated hardware-level threats across chiplet boundaries.
Finally, the heterogeneous nature of chiplet designs complicates security monitoring and threat detection. Traditional security monitoring approaches designed for monolithic chips are inadequate for detecting cross-chiplet attack patterns. The industry lacks comprehensive security monitoring frameworks specifically designed for UCIe-based systems that can detect anomalous behaviors across chiplet boundaries.
Existing UCIe Security Architectures and Protocols
01 Security mechanisms for UCIe chiplet interconnects
Various security mechanisms can be implemented in UCIe chiplet interconnects to protect against unauthorized access and attacks. These include encryption protocols, secure boot processes, and authentication methods that verify the identity of connected chiplets. Such security features help maintain data integrity and confidentiality across the interconnect, preventing potential security breaches in multi-chiplet systems.- Authentication and encryption mechanisms for UCIe chiplet interconnects: Security mechanisms including authentication protocols and encryption algorithms are implemented to protect data transmission between chiplets in UCIe interconnects. These mechanisms verify the identity of chiplets before establishing connections and encrypt data to prevent unauthorized access or tampering during transmission. Advanced cryptographic techniques ensure secure communication channels between chiplets, protecting sensitive information from potential attacks.
- Hardware-based security features for chiplet protection: Hardware security modules and physical unclonable functions (PUFs) are integrated into chiplet designs to provide robust protection against hardware attacks. These features include tamper-resistant circuits, secure boot mechanisms, and hardware-level encryption engines that operate independently of software layers. The hardware-based approach offers stronger security guarantees by establishing a root of trust directly at the silicon level for UCIe interconnects.
- Secure key management and distribution for chiplet ecosystems: Specialized key management systems are implemented to securely generate, store, and distribute cryptographic keys across multiple chiplets in a UCIe environment. These systems include secure key rotation mechanisms, compartmentalized key storage, and hierarchical key structures that limit exposure in case of compromise. The secure management of cryptographic material ensures that even if one chiplet is compromised, the security of the entire system remains intact.
- Runtime security monitoring and threat detection for UCIe interfaces: Advanced monitoring systems continuously analyze data traffic across UCIe interfaces to detect anomalies and potential security threats in real-time. These systems employ machine learning algorithms to establish baseline behavior patterns and identify deviations that might indicate attacks. Integrated threat detection mechanisms can trigger automatic responses such as isolating compromised chiplets or revoking access privileges to maintain system integrity during operation.
- Secure chiplet initialization and attestation protocols: Specialized protocols ensure that chiplets are securely initialized and can prove their authenticity and integrity before joining a UCIe interconnect system. These protocols include remote attestation mechanisms that verify chiplet firmware hasn't been tampered with, secure boot sequences that validate each stage of initialization, and trust establishment procedures that create verifiable identity chains. The secure initialization process prevents malicious or counterfeit chiplets from being integrated into sensitive systems.
02 Hardware-based security features for chiplet communications
Hardware-based security features provide robust protection for chiplet communications in UCIe implementations. These include physical unclonable functions (PUFs), secure enclaves, hardware root of trust, and dedicated security processors. Such hardware mechanisms establish a secure foundation for chiplet-to-chiplet communications, protecting against side-channel attacks and physical tampering attempts.Expand Specific Solutions03 Secure key management for UCIe interconnects
Effective key management systems are essential for maintaining security in UCIe chiplet interconnects. These systems handle the generation, distribution, storage, and rotation of cryptographic keys used for securing communications between chiplets. Secure key management protocols ensure that encryption remains effective and that compromised keys can be quickly replaced, maintaining the overall security posture of the interconnect.Expand Specific Solutions04 Secure protocol implementations for chiplet communications
Secure protocol implementations for UCIe chiplet communications establish standardized methods for protecting data as it travels between chiplets. These protocols define encryption standards, authentication procedures, and integrity verification mechanisms. By implementing secure communication protocols specifically designed for the high-speed, low-latency requirements of UCIe interconnects, chiplet-based systems can maintain both performance and security.Expand Specific Solutions05 Security monitoring and threat detection in UCIe systems
Security monitoring and threat detection mechanisms are crucial for identifying and responding to potential security breaches in UCIe chiplet interconnects. These systems continuously monitor communication patterns, power consumption, and timing characteristics to detect anomalies that might indicate an attack. Real-time monitoring allows for rapid response to security threats, including the ability to isolate compromised chiplets or activate countermeasures to mitigate attacks.Expand Specific Solutions
Key Industry Players in Chiplet Security Ecosystem
The UCIe Chiplet Interconnect Security landscape is currently in an early growth phase, with the market expanding as chiplet technology gains traction in high-performance computing. Major semiconductor players like Intel, AMD (formerly ATI), Qualcomm, and Samsung are leading technical innovation, while specialized security firms such as Qi An Xin and Infineon are addressing emerging security challenges. The technology is approaching maturity for basic implementations but security threat modeling remains nascent. Research institutions including University of Florida, Zhejiang University, and NUDT are contributing significantly to security frameworks, collaborating with industry leaders to establish standards. As chiplet adoption accelerates in data centers and edge computing, the security ecosystem is expected to evolve rapidly with increased focus on hardware-level threat protection.
QUALCOMM, Inc.
Technical Solution: Qualcomm has developed a specialized security framework for UCIe implementations focusing on mobile and edge computing scenarios. Their approach centers on a "Security Island" architecture where dedicated security processing elements are integrated within the chiplet ecosystem to monitor and protect die-to-die communications. Qualcomm's implementation includes hardware-based cryptographic accelerators optimized for the low-latency requirements of chiplet interconnects, enabling real-time encryption without performance penalties. Their threat modeling specifically addresses power analysis attacks and fault injection vulnerabilities in the UCIe physical layer. Qualcomm has also pioneered dynamic security policy enforcement that adapts protection mechanisms based on workload characteristics and threat intelligence, allowing for optimized security-performance tradeoffs in resource-constrained environments.
Strengths: Qualcomm excels in power-efficient security implementations suitable for mobile devices, with strong expertise in RF and wireless security that extends to chiplet communications. Weaknesses: Their solutions may be overly optimized for mobile use cases, potentially limiting applicability in high-performance computing environments.
Intel Corp.
Technical Solution: Intel as a founding member of the UCIe consortium has developed comprehensive security architecture for chiplet interconnects. Their approach includes a multi-layered security framework that implements hardware root-of-trust, secure boot mechanisms, and runtime attestation specifically designed for die-to-die communications. Intel's UCIe security implementation features encrypted channels between chiplets with dedicated security engines that manage key exchange and authentication protocols. They've pioneered the concept of "security domains" within multi-chiplet packages, where each chiplet operates with different trust levels and security requirements. Intel has also developed specific threat models addressing side-channel attacks unique to the proximity of chiplets in advanced packaging, implementing countermeasures such as constant-time operations and power/thermal isolation techniques.
Strengths: As UCIe consortium founder, Intel has extensive expertise in chiplet integration and security architecture design. Their solutions benefit from vertical integration across hardware and software. Weaknesses: Their security implementations may prioritize compatibility with their own ecosystem, potentially limiting interoperability with third-party chiplets.
Critical Security Patents and Research in Chiplet Interconnects
Functional safety for system-on-chip arrangements
PatentWO2024260605A1
Innovation
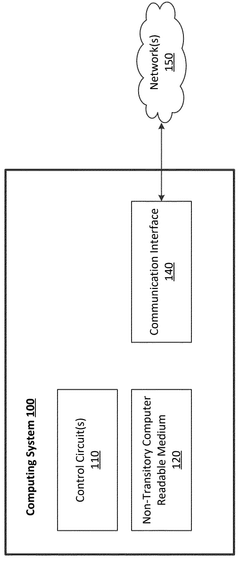
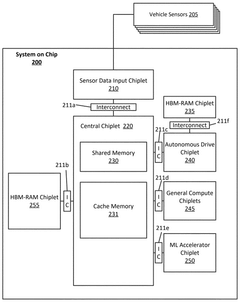
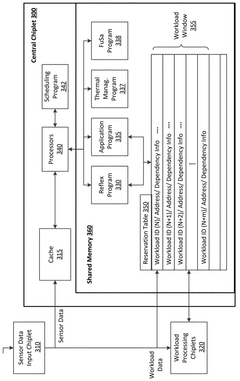
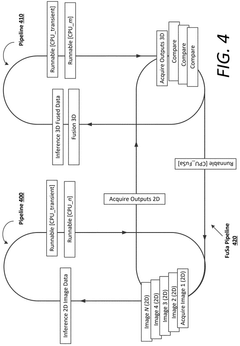
- The implementation of a computing system with a primary and backup System-on-Chip (SoC) arrangement, where each SoC executes a Functional Safety (FuSa) program to monitor shared memory, compare and verify independent pipeline outputs, and generate error correction codes for enhanced reliability and redundancy.
Functional safety for system-on-chip arrangements
PatentPendingUS20240430125A1
Innovation
- A computing system with multiple System-on-Chip (SoC) arrangements, including a primary and backup SoC, executes a Functional Safety (FuSa) program to monitor shared memory, compare and verify independent pipeline outputs, and generate error correction codes, ensuring robust hardware components and reliable communication between chiplets, thereby enhancing ASIL ratings.
Supply Chain Security Considerations for Chiplets
The security of the chiplet supply chain represents a critical concern in the UCIe (Universal Chiplet Interconnect Express) ecosystem. As chiplet-based designs involve multiple components potentially sourced from different vendors, they introduce unique security vulnerabilities across the manufacturing and integration process. The disaggregation of system-on-chip (SoC) designs into separate chiplets creates multiple entry points for malicious actors to compromise system integrity.
Supply chain attacks targeting chiplets can occur at various stages, from design and fabrication to packaging and integration. Adversaries may insert hardware trojans, backdoors, or counterfeit components that are difficult to detect once integrated. The UCIe standard, while providing a common interconnect protocol, must address these security challenges through comprehensive supply chain validation mechanisms.
Verification of chiplet provenance becomes paramount in this context. Organizations must implement robust chain-of-custody documentation and authentication protocols to ensure chiplets originate from trusted sources. This includes cryptographic signing of chiplet designs and secure manufacturing processes with tamper-evident packaging. The industry needs standardized methods to verify chiplet authenticity before integration into multi-die packages.
Testing methodologies for chiplet security present significant challenges due to the complex nature of die-to-die interfaces. Traditional boundary scan techniques may be insufficient for detecting sophisticated hardware implants or modifications at the chiplet level. Advanced testing frameworks specifically designed for chiplet architectures must be developed to validate security properties across die boundaries and interconnects.
The UCIe ecosystem requires secure provisioning mechanisms to establish trust between chiplets from different vendors. This includes secure boot sequences, attestation protocols, and runtime verification methods that can detect unauthorized modifications or substitutions. Implementing hardware root-of-trust within the chiplet architecture provides a foundation for establishing secure communication channels between dies.
Regulatory frameworks and industry standards for chiplet supply chain security are still evolving. Organizations like NIST, ISO, and industry consortia are working to establish guidelines specific to disaggregated computing architectures. These frameworks must address the unique challenges of multi-vendor chiplet ecosystems while providing practical implementation guidance for manufacturers and integrators.
Ultimately, a defense-in-depth approach is essential for chiplet supply chain security. This combines technical measures like physical unclonable functions (PUFs) and side-channel analysis with procedural controls such as vendor qualification and secure logistics. As the UCIe standard matures, incorporating these security considerations will be crucial for widespread adoption in sensitive applications.
Supply chain attacks targeting chiplets can occur at various stages, from design and fabrication to packaging and integration. Adversaries may insert hardware trojans, backdoors, or counterfeit components that are difficult to detect once integrated. The UCIe standard, while providing a common interconnect protocol, must address these security challenges through comprehensive supply chain validation mechanisms.
Verification of chiplet provenance becomes paramount in this context. Organizations must implement robust chain-of-custody documentation and authentication protocols to ensure chiplets originate from trusted sources. This includes cryptographic signing of chiplet designs and secure manufacturing processes with tamper-evident packaging. The industry needs standardized methods to verify chiplet authenticity before integration into multi-die packages.
Testing methodologies for chiplet security present significant challenges due to the complex nature of die-to-die interfaces. Traditional boundary scan techniques may be insufficient for detecting sophisticated hardware implants or modifications at the chiplet level. Advanced testing frameworks specifically designed for chiplet architectures must be developed to validate security properties across die boundaries and interconnects.
The UCIe ecosystem requires secure provisioning mechanisms to establish trust between chiplets from different vendors. This includes secure boot sequences, attestation protocols, and runtime verification methods that can detect unauthorized modifications or substitutions. Implementing hardware root-of-trust within the chiplet architecture provides a foundation for establishing secure communication channels between dies.
Regulatory frameworks and industry standards for chiplet supply chain security are still evolving. Organizations like NIST, ISO, and industry consortia are working to establish guidelines specific to disaggregated computing architectures. These frameworks must address the unique challenges of multi-vendor chiplet ecosystems while providing practical implementation guidance for manufacturers and integrators.
Ultimately, a defense-in-depth approach is essential for chiplet supply chain security. This combines technical measures like physical unclonable functions (PUFs) and side-channel analysis with procedural controls such as vendor qualification and secure logistics. As the UCIe standard matures, incorporating these security considerations will be crucial for widespread adoption in sensitive applications.
Standardization Efforts in Chiplet Security
The standardization of chiplet security has become a critical focus area as the industry moves toward disaggregated chip designs using the Universal Chiplet Interconnect Express (UCIe) standard. Several industry consortia and standards bodies are actively working to establish comprehensive security frameworks specifically addressing the unique challenges posed by chiplet architectures.
The UCIe Consortium, formed in 2022, has established a dedicated security working group focused on developing specifications for secure chiplet-to-chiplet communications. This group is currently developing authentication protocols, encryption standards, and secure boot mechanisms specifically tailored to the multi-die environment. Their work emphasizes maintaining security without compromising the performance benefits that make chiplets attractive.
JEDEC and IEEE have also launched specialized task forces addressing chiplet security standardization. JEDEC's JC-70 committee is developing standards for secure memory interfaces in chiplet designs, while IEEE P3186 is creating a framework for hardware security verification in heterogeneous integrated circuits.
The Trusted Computing Group (TCG) has extended its Trusted Platform Module (TPM) specifications to accommodate chiplet-based architectures, recognizing the need for hardware root-of-trust mechanisms that can function across multiple dies. Their work includes specifications for distributed TPM functionality across chiplets while maintaining security guarantees.
Industry-academic partnerships are also contributing significantly to standardization efforts. The DARPA CHIPS program has fostered collaboration between semiconductor companies and research institutions to develop open security standards for modular chip designs. These efforts have resulted in proposed standards for secure die-to-die interfaces that are currently under consideration by larger standards bodies.
The RISC-V International security committee has developed extensions specifically addressing secure communication between RISC-V cores implemented across different chiplets. Their specifications include secure enclave implementations that can span multiple dies while maintaining isolation guarantees.
Notably, the Common Criteria Recognition Arrangement (CCRA) is working to update its evaluation methodology to address chiplet-specific security concerns, providing a framework for security certification of chiplet-based products. This will enable consistent security evaluation across different chiplet implementations.
These standardization efforts collectively aim to establish a comprehensive security framework that addresses the unique threat landscape of chiplet architectures while enabling the industry to fully realize the benefits of this emerging technology paradigm.
The UCIe Consortium, formed in 2022, has established a dedicated security working group focused on developing specifications for secure chiplet-to-chiplet communications. This group is currently developing authentication protocols, encryption standards, and secure boot mechanisms specifically tailored to the multi-die environment. Their work emphasizes maintaining security without compromising the performance benefits that make chiplets attractive.
JEDEC and IEEE have also launched specialized task forces addressing chiplet security standardization. JEDEC's JC-70 committee is developing standards for secure memory interfaces in chiplet designs, while IEEE P3186 is creating a framework for hardware security verification in heterogeneous integrated circuits.
The Trusted Computing Group (TCG) has extended its Trusted Platform Module (TPM) specifications to accommodate chiplet-based architectures, recognizing the need for hardware root-of-trust mechanisms that can function across multiple dies. Their work includes specifications for distributed TPM functionality across chiplets while maintaining security guarantees.
Industry-academic partnerships are also contributing significantly to standardization efforts. The DARPA CHIPS program has fostered collaboration between semiconductor companies and research institutions to develop open security standards for modular chip designs. These efforts have resulted in proposed standards for secure die-to-die interfaces that are currently under consideration by larger standards bodies.
The RISC-V International security committee has developed extensions specifically addressing secure communication between RISC-V cores implemented across different chiplets. Their specifications include secure enclave implementations that can span multiple dies while maintaining isolation guarantees.
Notably, the Common Criteria Recognition Arrangement (CCRA) is working to update its evaluation methodology to address chiplet-specific security concerns, providing a framework for security certification of chiplet-based products. This will enable consistent security evaluation across different chiplet implementations.
These standardization efforts collectively aim to establish a comprehensive security framework that addresses the unique threat landscape of chiplet architectures while enabling the industry to fully realize the benefits of this emerging technology paradigm.
Unlock deeper insights with Patsnap Eureka Quick Research — get a full tech report to explore trends and direct your research. Try now!
Generate Your Research Report Instantly with AI Agent
Supercharge your innovation with Patsnap Eureka AI Agent Platform!