A Monitoring Method for Static Object Tampering in Mixed Environment
一种混合环境、静态的技术,应用在计算机安全领域,能够解决静态文件被篡改、无法看到被篡改页面、不能统计被篡改频次等问题
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0044] The present invention will be described in further detail below in conjunction with the accompanying drawings and specific embodiments, and the implementation scope of the present invention is not limited thereto.
[0045] The invention provides a monitoring method for static object tampering in a mixed environment. The terminology involved in the present invention is described as follows:
[0046] Hybrid environment: Data center IT infrastructure where the cloud computing environment and the traditional IT architecture-based physical computing environment exist side by side.
[0047] Static objects: refer to electronic files stored in computers such as documents, design drawings, videos, and images that are not changing.
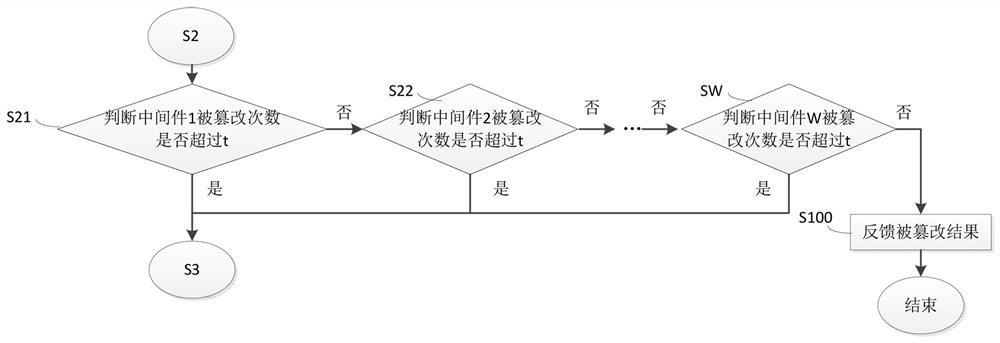
[0048] Seed file: For the storage method in the cloud computing environment, all local data usage and systems are retrieved from the cloud platform. We call the storage content of static objects, middleware, and operating systems on the cloud platfo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com