Implementation method of a secure network disk system in a cloud storage environment
An implementation method and cloud storage technology, applied in transmission systems, electrical components, etc., can solve problems such as destroying data security and reducing system efficiency.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach
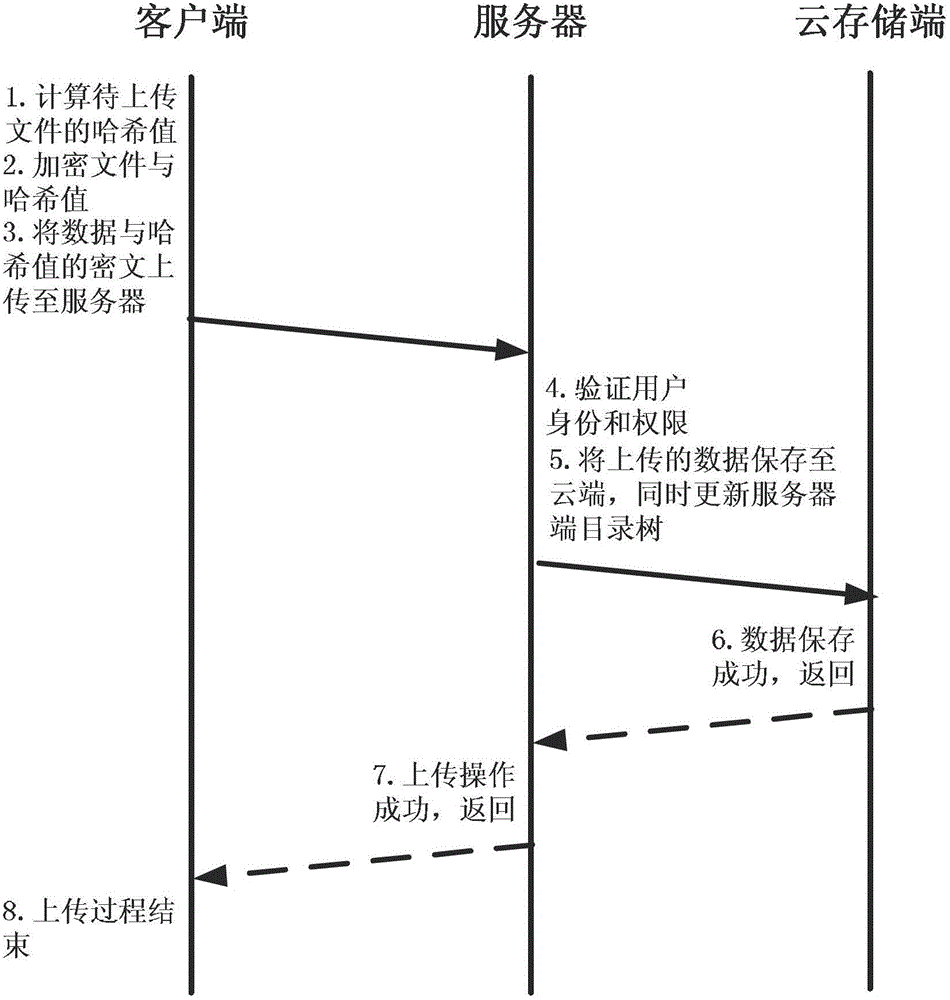
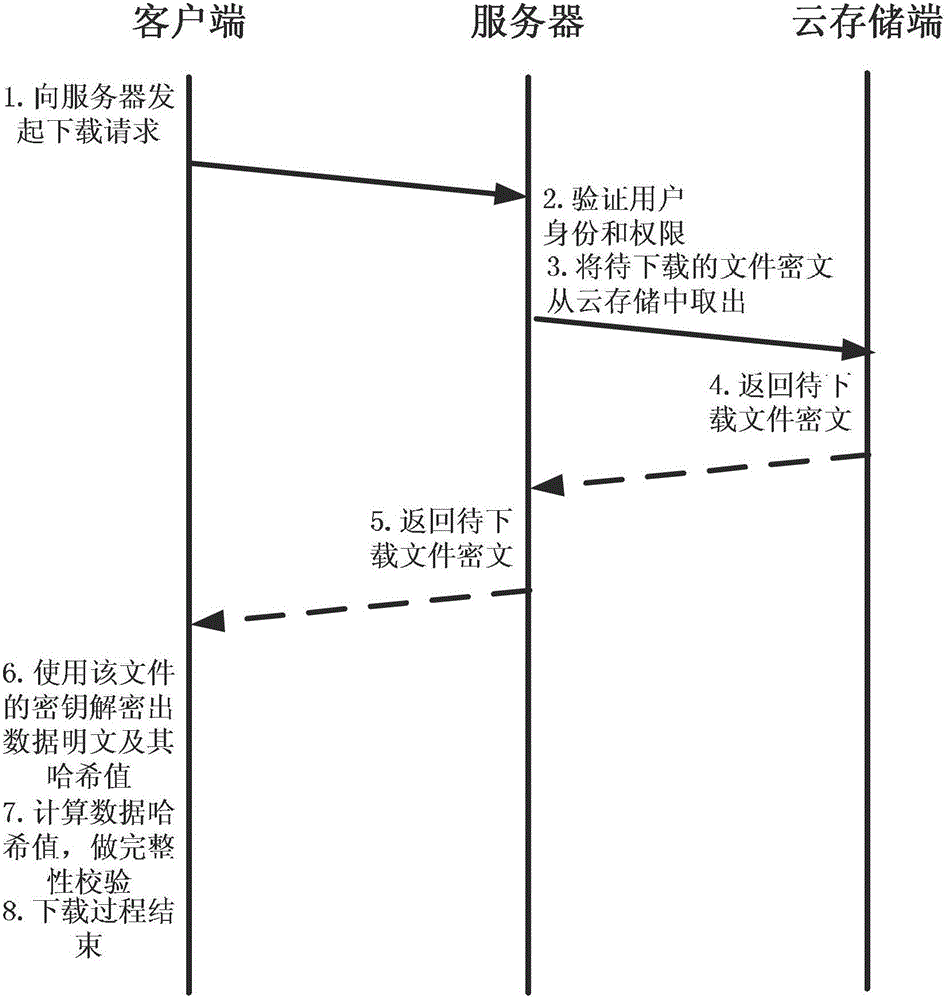
[0104] Step 1: System initialization.
[0105] The client computer, hereinafter referred to as the client, is equipped with a data encryption and decryption module, a data integrity verification module, a local monitoring module, a folder sharing module and a protocol communication module;
[0106] The server is equipped with: identity verification module, storage control module, access control module, version control module and directory metadata management module, among which:
[0107] The directory metadata management module is used to query and update directory metadata, including: directory type, owner username, absolute path, access control list, number of authorized users, and key generation way, wherein the access control list includes: user names and corresponding key ciphertexts, the key ciphertexts are encrypted using the corresponding user's public key, and the corresponding user can use their own private key to decrypt;
[0108] The cloud storage server is here...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com