User resource authorization method
A technology of user resources and resources, which is applied in the field of user resource authorization, and can solve the problem that there is no corresponding technical solution for user resource authorization
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
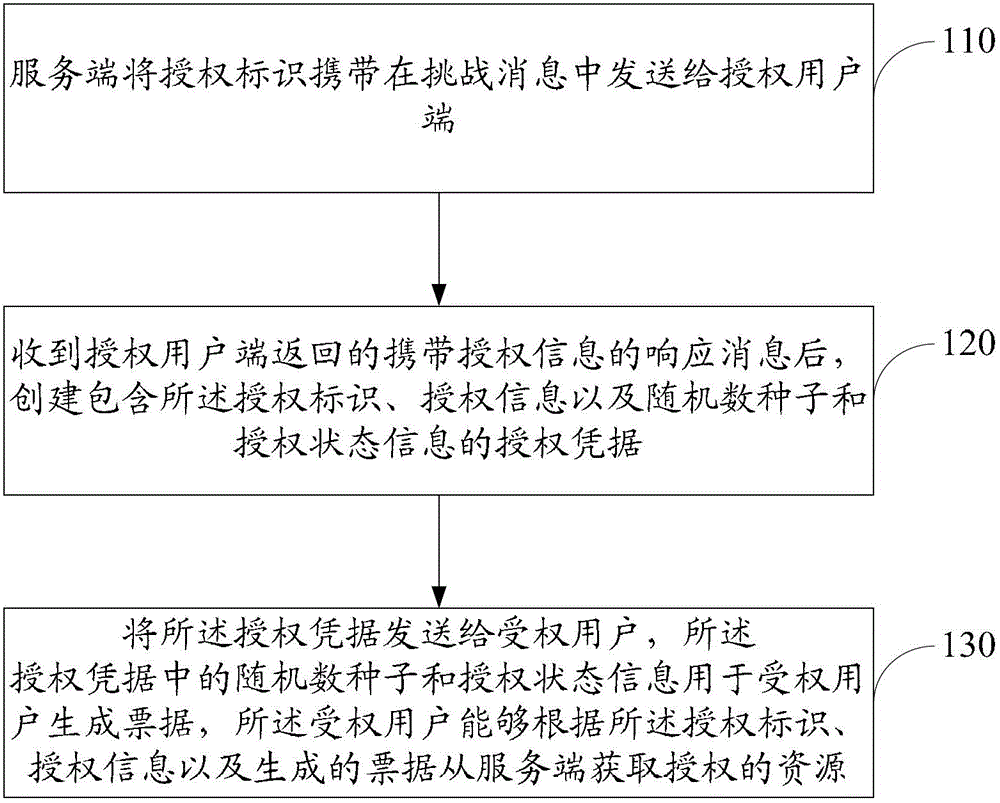
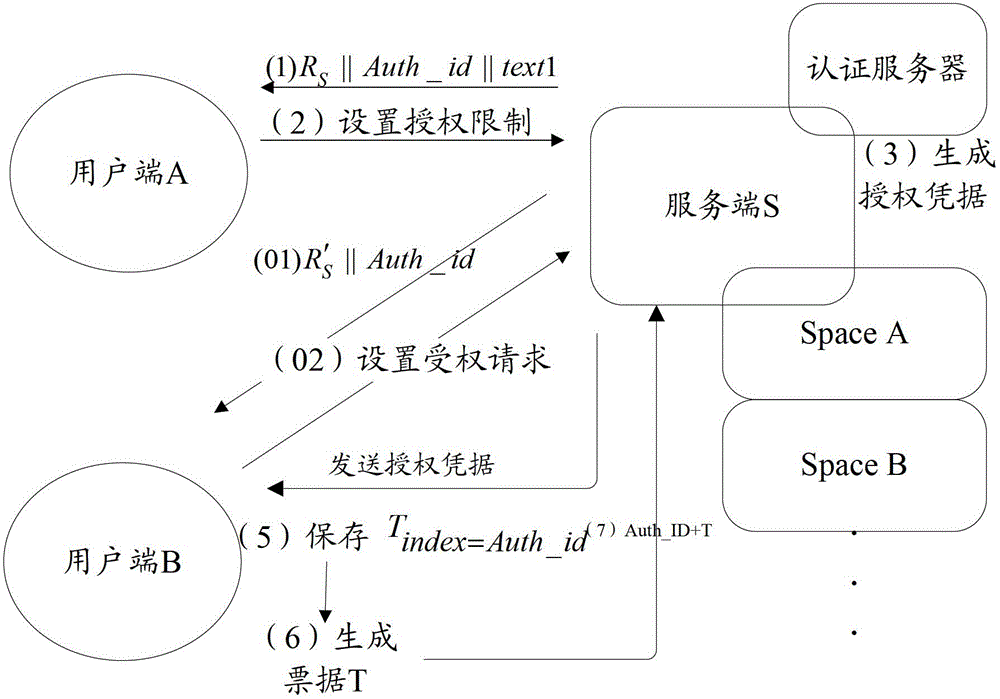
[0026] Please refer to figure 1 with figure 2 , the embodiment of the present invention provides a user resource authorization method. The equipment involved in the method includes a server S and at least two user terminals. In the following, two clients A and B are taken as an example.
[0027] Among them, the server S is a public operating platform, including an authentication server; both client A and B are connected to the server S, and are legal users of the server S, and the resources owned by the client A and B are provided by the server provision and management. Server S can authenticate client A or B, but direct authentication between client A and client B is not supported. Client A and Client B respectively apply for a section of storage space on server S, namely Space A and Space B, which store their respective resources. In the prior art, client B cannot access the resources of Space A applied by client A, and client A cannot access the resources of Space B a...
Embodiment 2
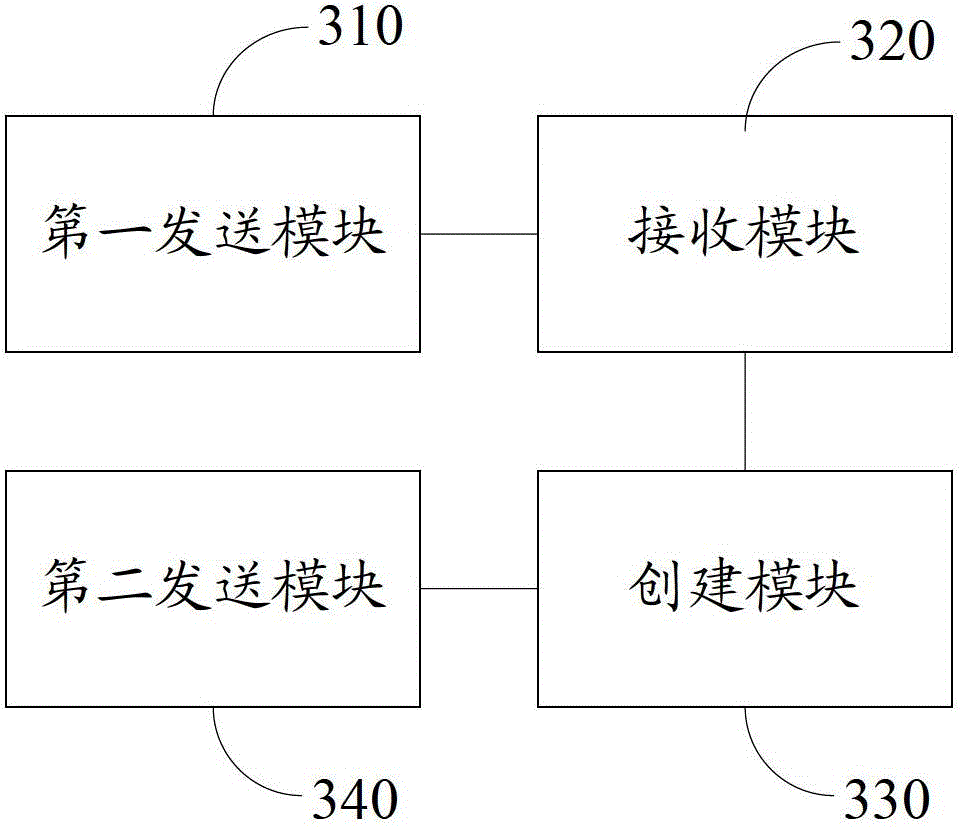
[0062] Please refer to image 3 , an embodiment of the present invention provides a user resource authorization device, including:
[0063] The first sending module 310 is configured to carry the authorization identifier in the challenge message and send it to the authorized client;
[0064] A receiving module 320, configured to receive a response message carrying authorization information returned by the authorized client;
[0065] Creating module 330, configured to create an authorization credential that includes the authorization ID, authorization information, random number seed, and authorization state information;
[0066] The second sending module 340 is configured to send the authorization credential to the authorized user end, the random number seed and authorization state information in the authorization credential are used for the authorized user end to generate a ticket, and the authorized user end can The identity, authorization information, and generated ticket ...
Embodiment 3
[0076] Please refer to figure 2 , an embodiment of the present invention provides a user resource authorization system, including:
[0077] Server S, authorized client A and authorized client B;
[0078] The server S is configured to carry the authorization identifier in the challenge message and send it to the authorized client, and after receiving the response message carrying the authorization information returned by the authorized client, create an and the authorization credential of the authorization status information, sending the authorization credential to the authorized client, and providing the authorized resource to the authorized client;
[0079] The authorized client A is configured to receive a challenge message carrying an authorization identifier sent by the server, and carry the authorization information in a response message and send it to the server;
[0080] The authorized client B is used to receive the authorization certificate sent by the server, gene...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap