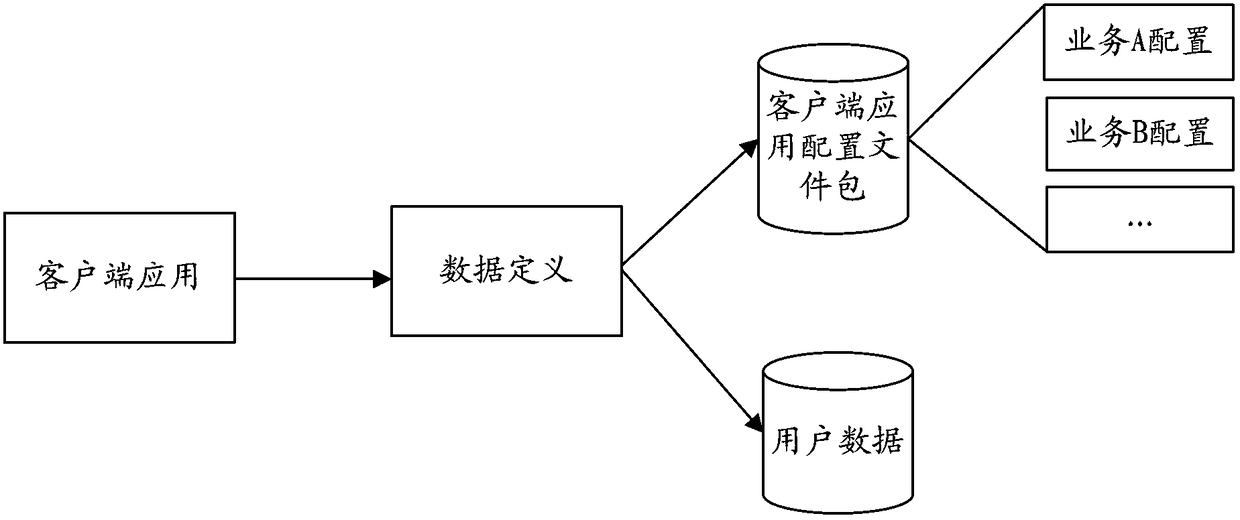
Data access method and device
A data access and database technology, applied in the client application field, can solve the problems of low efficiency of data processing scheme, inability to manage data clearly and efficiently, and achieve the effect of simple and clear data access and management, simple and flexible editing operation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
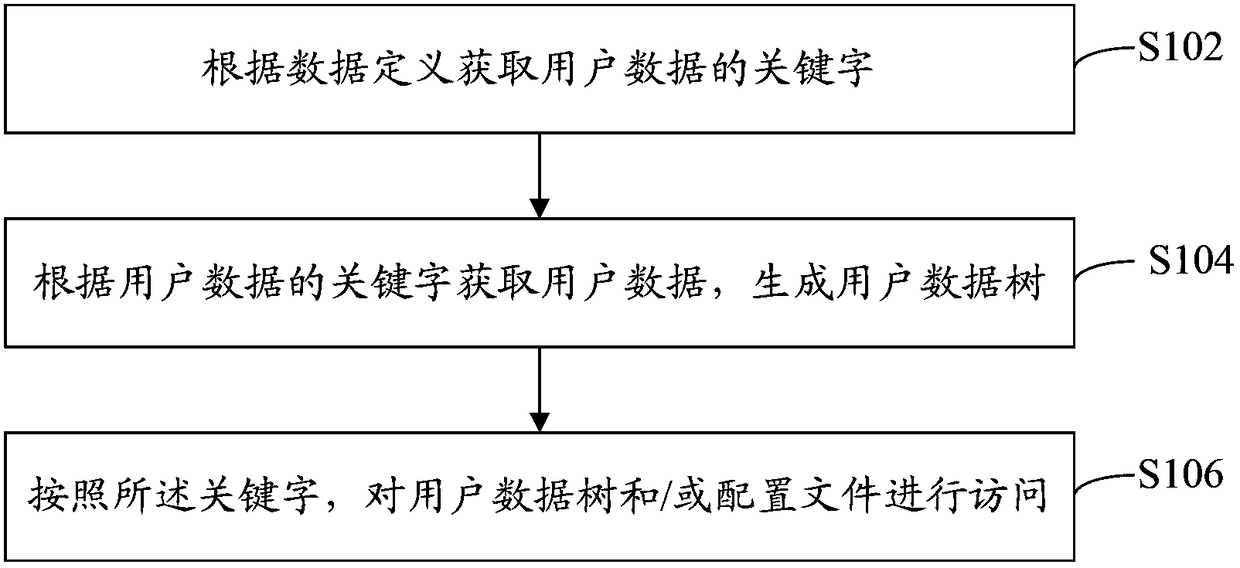
[0033] refer to figure 2 , shows a flow chart of steps of a data access method according to Embodiment 1 of the present invention.
[0034] The data access method of the present embodiment includes the following steps:
[0035] Step S102: Obtain keywords of user data according to the data definition.
[0036] Among them, the data definition defines (also can be understood as setting) the keywords corresponding to the user data of a certain service and the keywords corresponding to the configuration file of the service, wherein the keywords corresponding to the user data of the same service are the same as the keywords of the service The corresponding keywords in the configuration file are the same.
[0037] Business usually refers to each specific function of the software, such as: automatic reply function in instant messaging software, security domain name checking function, interface skin changing function; user data of a business may include the automatic reply content e...
Embodiment 2
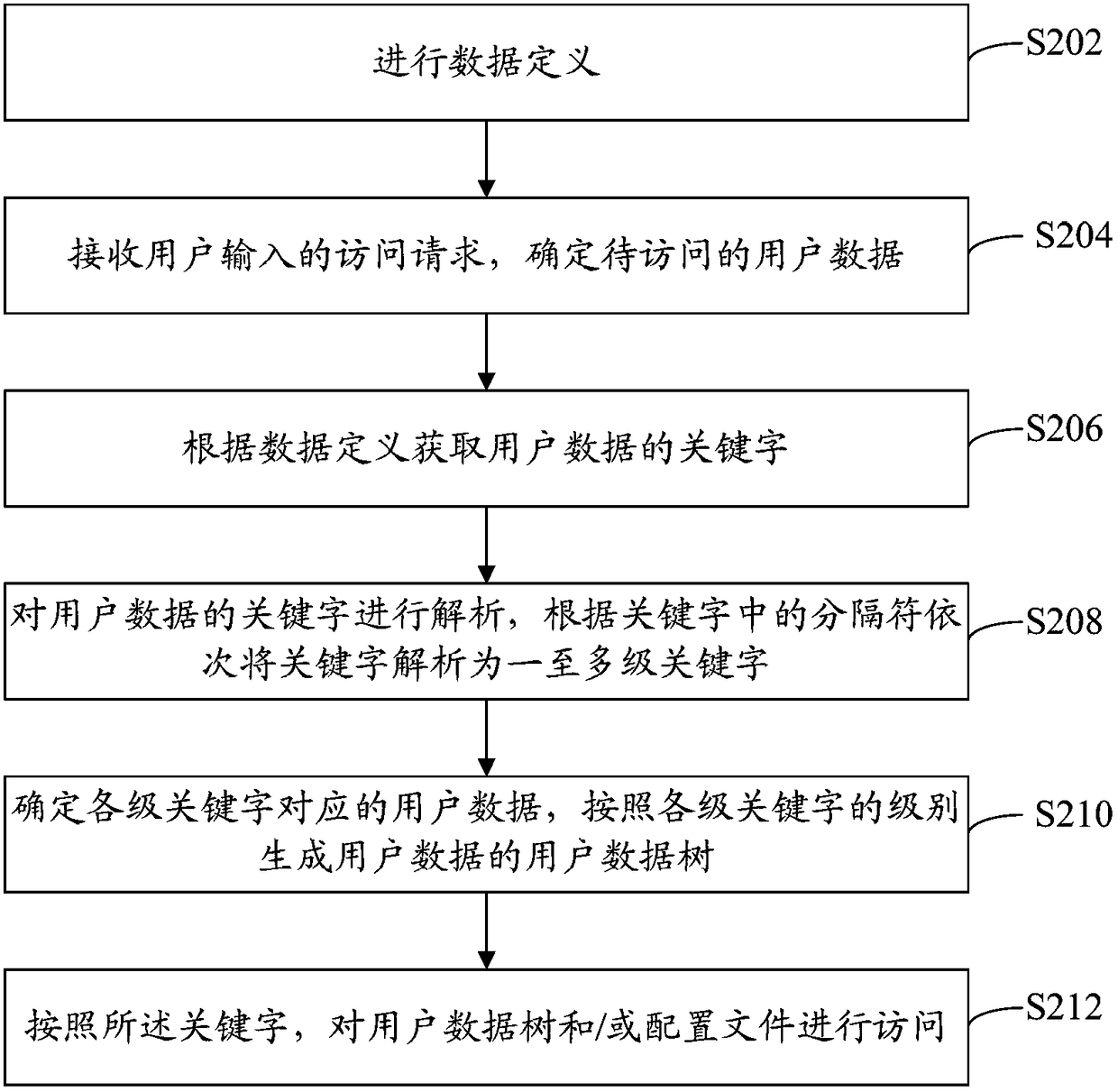
[0043] refer to image 3 , shows a flow chart of steps of a data access method according to Embodiment 2 of the present invention.
[0044] The data access method of the present embodiment includes the following steps:
[0045] Step S202: Perform data definition.
[0046] In this step, the data definition defines the keywords corresponding to the user data of each service and the keywords corresponding to the configuration files of each service, wherein the keywords corresponding to the user data of the same service are the same as the keywords corresponding to the configuration files of this service . The keywords corresponding to the user data of a certain business defined by the data definition and the keywords corresponding to the configuration file of the business are as follows:
[0047]
[0048] Among them, DefinedConfigSources defines the location and format of the data, and DefinedConfigFileKeys defines the KEY for the configuration file.
[0049] When defining...
Embodiment 3
[0076] refer to Figure 4 , shows a flow chart of steps of a data reading method according to Embodiment 3 of the present invention.
[0077] This embodiment describes the data access scheme of the present invention from the aspect of data reading, and the data reading method of this embodiment includes the following steps:
[0078] Step S302: Obtain the KEY (keyword) corresponding to the user data to be accessed and the configuration file according to the data definition.
[0079] Step S304: Obtain all user data according to the KEY of the user data.
[0080] Step S306: parse the KEY of the user data into a parent KEY and multiple child KEYs according to separators such as "|".
[0081] This embodiment takes a multi-level KEY as an example, but those skilled in the art should understand that in some cases, there may be only a parent KEY.
[0082] Step S308: Generate a user data tree from the user data according to the parsed parent KEY and multiple child KEYs.
[0083] St...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com