Method and system for anti-theft security authentication
A security certification and consistent technology, applied in the field of vehicle security, can solve the problem of low security level of anti-theft
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
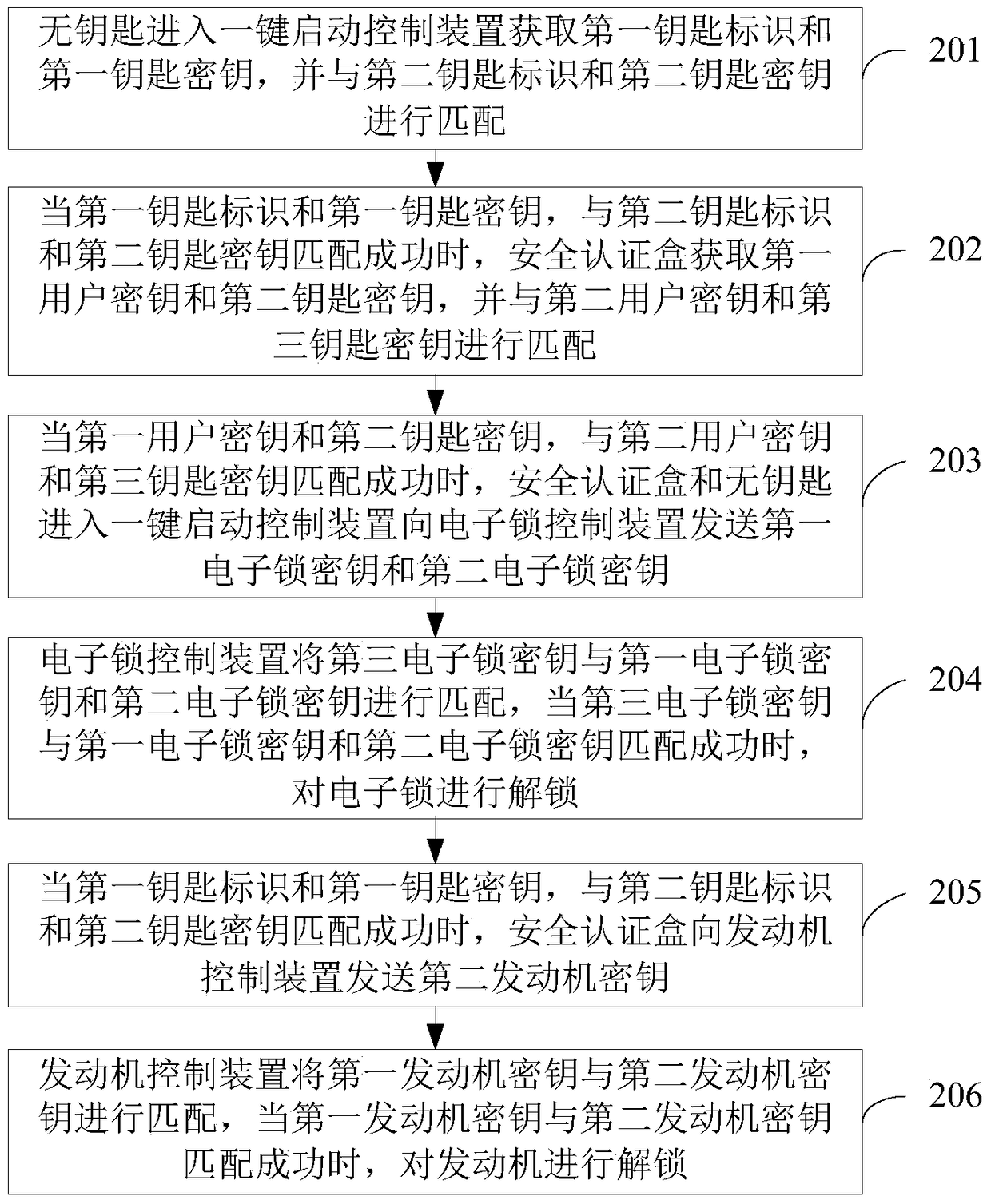
[0072] see figure 2 , an embodiment of the present invention provides a method for anti-theft security authentication, the method for anti-theft security authentication includes:
[0073] Step 201, the keyless entry one-button start control device 12 acquires the first key ID and the first key key, and matches them with the second key ID and the second key key; wherein, the keyless entry one-button start control device 12 After starting, the smart key 11 can be searched in the vehicle to obtain the first key identification and the first key key stored in the smart key 11, and the obtained first key identification and keyless entry into the one-button start control device 12 The stored second key identifier is matched, and the obtained first key key is matched with the second key key stored in the keyless entry one-key start control device 12 . Step 201 is the authentication and matching process between the smart key 11 and the keyless entry one-button start control device 12...
Embodiment 2
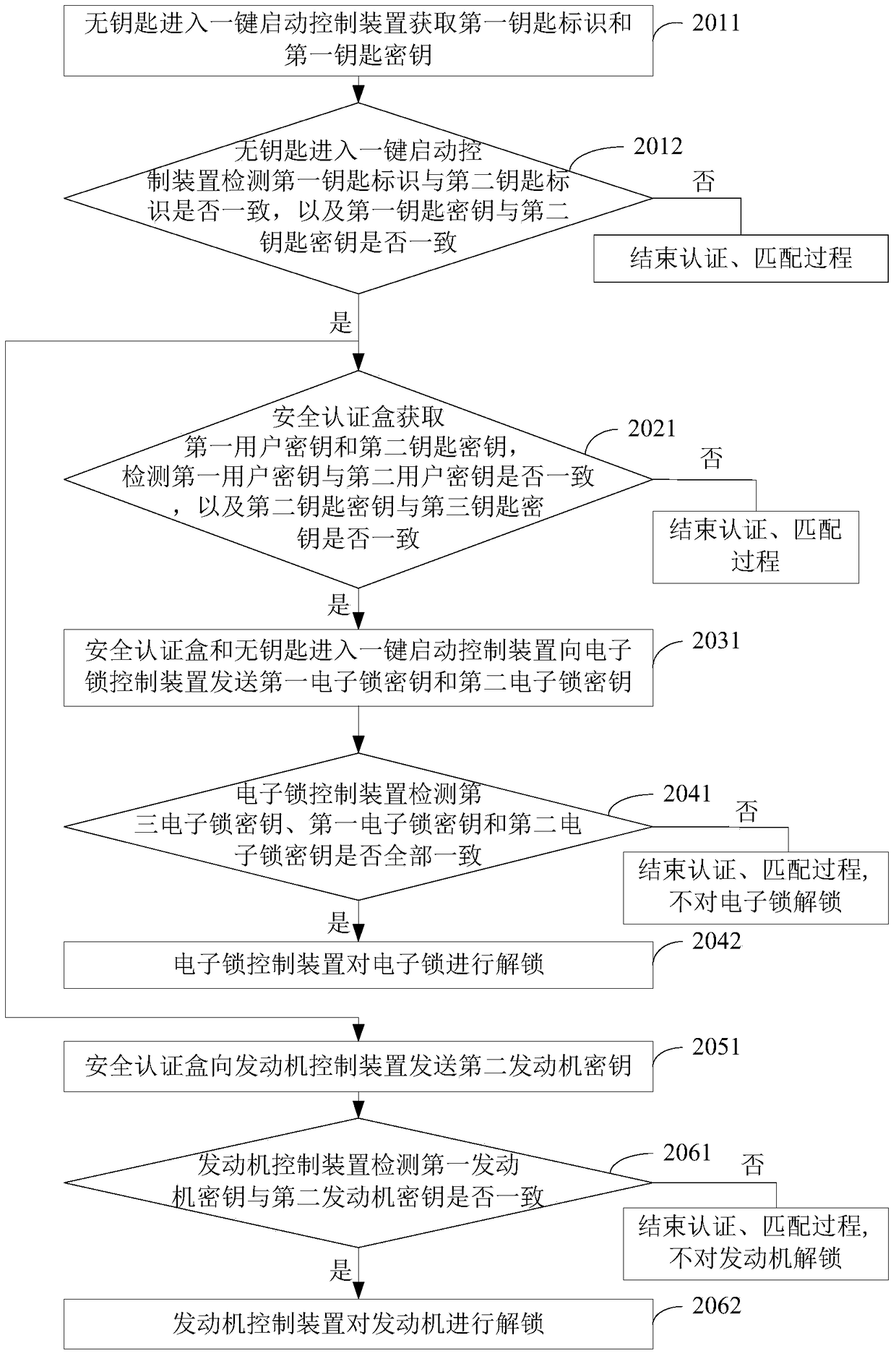
[0082] see image 3 , in order to further illustrate the process of mutual authentication and matching between the smart key 11 , the keyless entry one-button start control device 12 , the engine control device 13 , the security authentication box 14 and the electronic lock control device 15 , step 201 can be subdivided into step 2011 - step 2012, step 202 can be refined into step 2021, step 203 can be refined into step 2031, step 204 can be refined into step 2041-step 2042, step 205 can be refined into step 2051, and step 206 can be refined into step 2061-step 2062, the specific content is as follows:
[0083] Step 2011, the keyless entry one-key start control device 12 obtains the first key identification and the first key key; the specific process of obtaining the first key indication and the first key key is described in Embodiment 1, and will not be repeated here.
[0084] Step 2012, the keyless entry one-key start control device 12 detects whether the first key identifi...
Embodiment 3
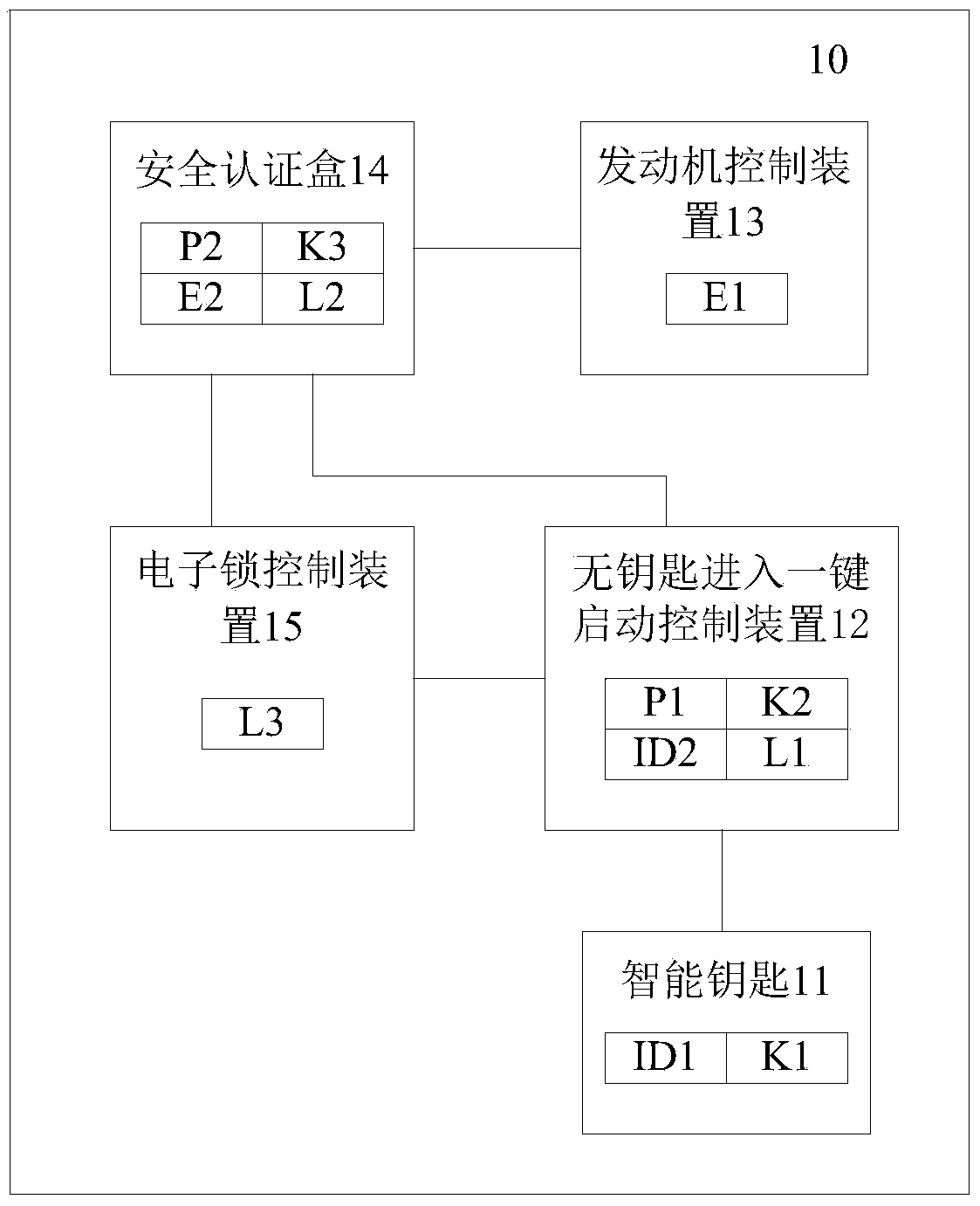
[0093] see Figure 4 , the system 10 of anti-theft security authentication can also include a power relay 16, the power relay 16 can communicate with the keyless entry one-button start control device 12, the engine control power supply, the security authentication box 14 and the electronic lock control device 15, specifically, the power supply The relay 16 can communicate with the keyless entry one-button start control device 12 and the security authentication box 14 through a diagnostic bus (K line).
[0094] see Figure 5 , on the basis of Embodiment 2, step 207 can also be added, using the security authentication box 14 and the keyless entry one-button start control device 12 to control the power supply to perform dual control on the power relay 16, the specific content is as follows:
[0095] Step 207, when the first user key is consistent with the second user key, and the second key key is consistent with the third key key, the security authentication box 14 and / or the k...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com