Device and method for resisting attacks in avalanche transition zone
A technology of transition area and multiplexer, which is applied in the countermeasures of attacking encryption mechanism, secure communication device, digital transmission system, etc., and can solve problems such as QKD error code or code rate change
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
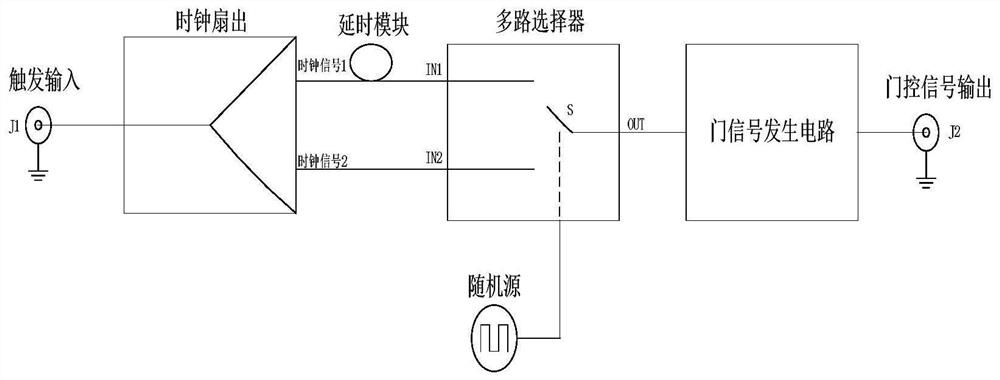
[0036] Such as figure 1 , the device for resisting the attack of the avalanche transition zone includes a clock fan-out device, a delay module, a multiplexer device, a random source device and a gate signal generation circuit device; the clock fan-out device detector is used to pass through the detector The starting input signal is divided into two independent clock signals T1 and clock signal T2; the output terminal of the delay module is connected with the input terminal IN1 of the multiplexer, and the delay module is used to delay the clock signal T1 After inputting the multiplexer, the delay amount of the delay module is Δt, and the delay amount Δt is greater than or equal to half of the edge time of the gating signal; the clock signal T2 is connected with the input terminal IN2 of the multiplexer device, and multiple The selection switch S of the selector device is connected with the random source module; the random source module is used to randomly select the input clock...
Embodiment 2
[0046] see figure 1 , the method for resisting the attack of the avalanche transition zone is implemented by means of a device for resisting the attack of the avalanche transition zone, including the following steps:
[0047] The trigger input signal passing through the detector is divided into two independent clock signals T1 and clock signal T2 through the clock fan-out device detector;
[0048] The clock signal T1 is delayed by the delay module and then input to the multiplexer, the delay amount of the delay module is Δt, and the delay amount Δt is greater than or equal to half of the edge time of the gate control signal;
[0049] The clock signal T2 is input to the multiplexer through the input terminal IN2 of the multiplexer device, and the selection switch S of the multiplexer device is connected to the random source module;
[0050] The input clock T1 of the input terminal IN1 or the input clock T2 of the input terminal IN2 is randomly selected by the random source mod...
Embodiment 3
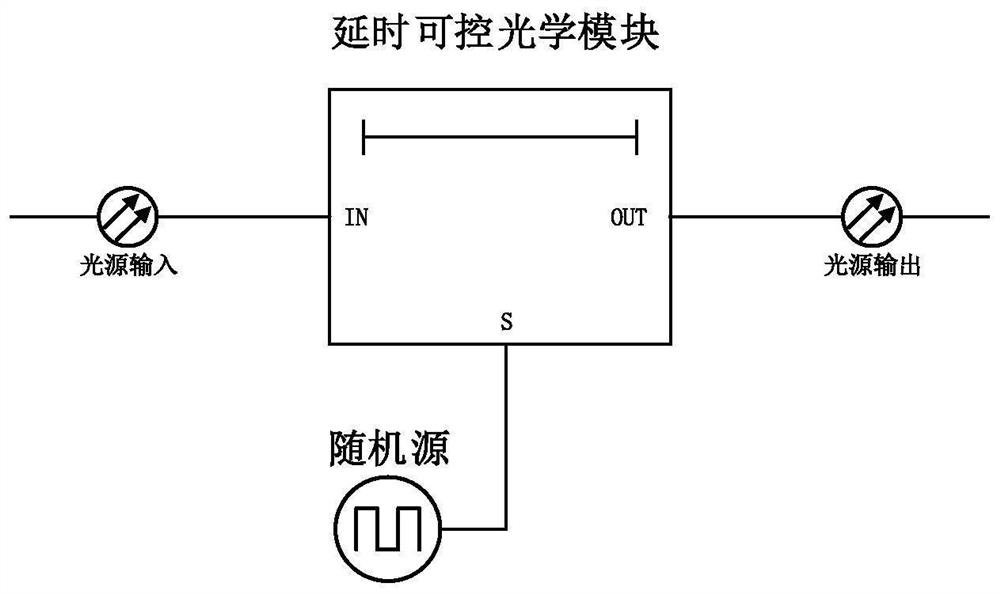
[0052] see figure 2 , the device for resisting the attack of the avalanche transition zone includes a light source input module, a delay controllable optical module, a random source module and a light source output module; the light source input module is connected to the input terminal IN of the delay controllable optical module for Input the light source into the delay controllable optical module; the delay controllable optical module is used to modulate the input light source, so that after the light source is modulated by the delay controllable optical module, it is divided into two different delay times of t or t+Δt Output: The output interface of the random source module is connected to the control terminal S of the delay controllable optical module, and the random source module is used to randomly select the delayed output of t or t+Δt as the final light source output through the light source output module. The delay controllable optical module is an optical controllab...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com