A malicious identification defense method and system based on handle system
An identification and malicious technology, applied in the field of malicious identification defense, can solve problems such as unable to respond to user requests normally, achieve the effect of defending against malicious identification attacks and improving the quality of analysis services
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
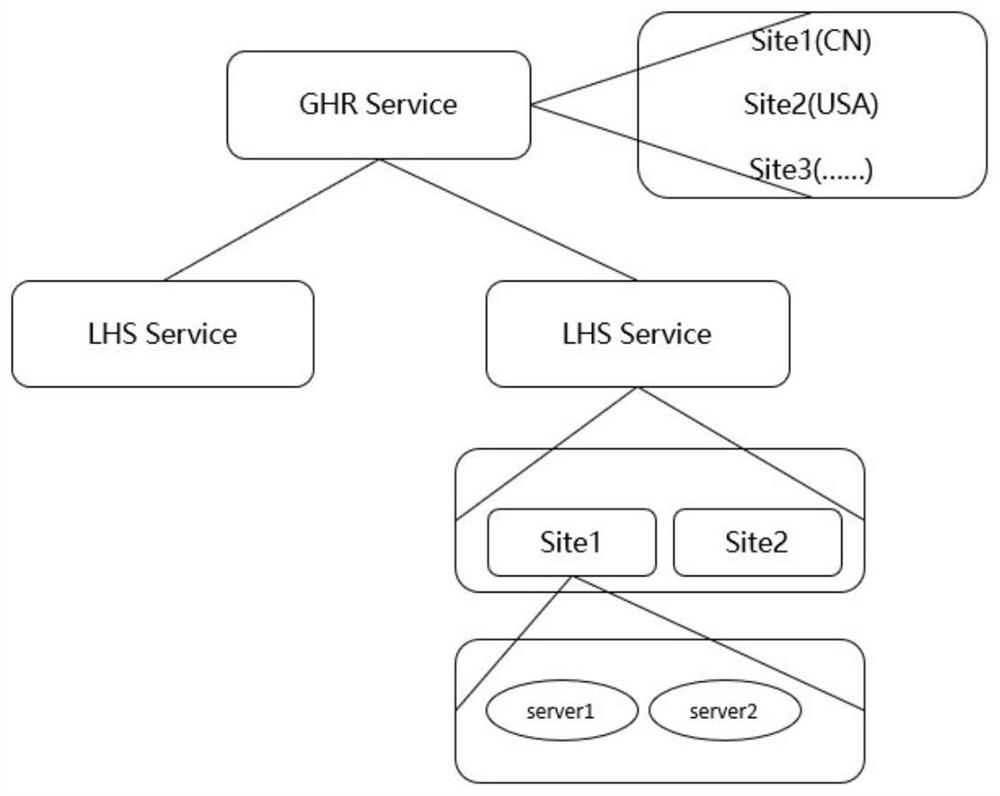
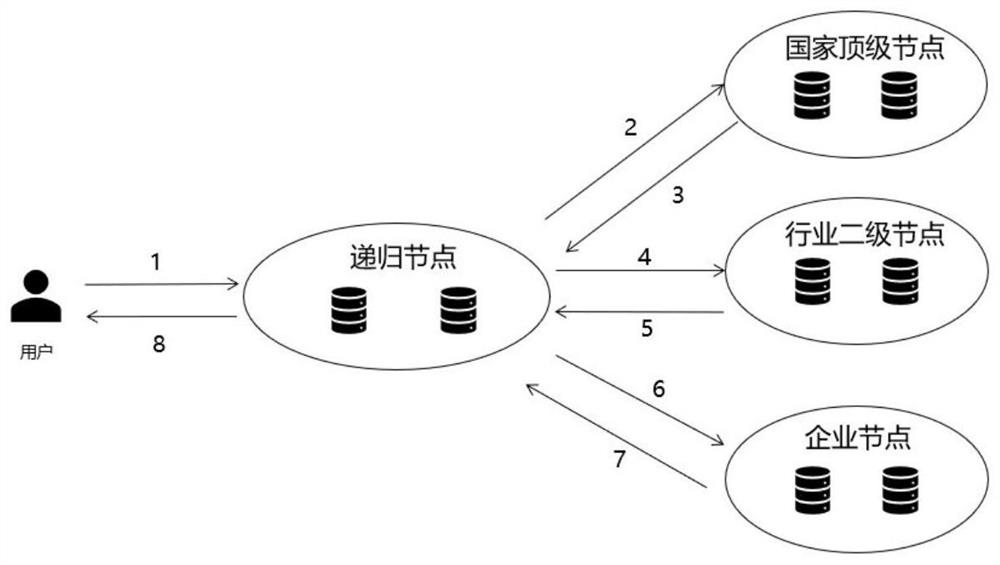
[0029] The invention proposes a malicious identification defense method based on the Handle system, which aims at improving the problem that the recursive node cannot normally respond to user requests under the condition that the existing Handle system is facing a denial of service attack by large-scale sub-deployment.
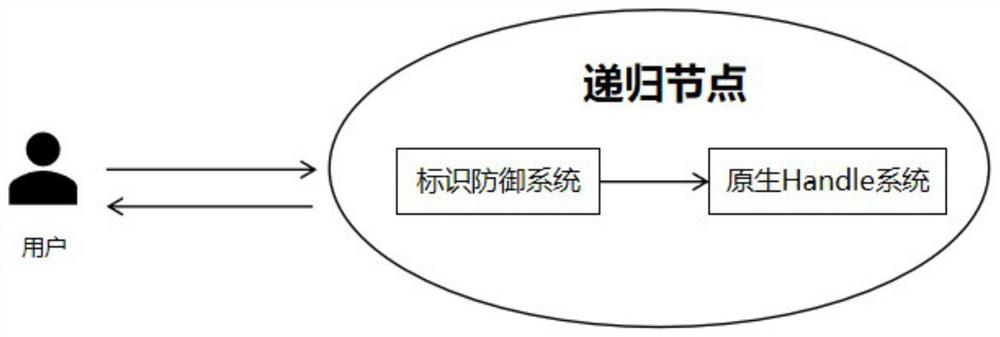
[0030] image 3 Add the schematic diagram of the identification defense system for the embodiment of the present invention, add the identification defense system on the basis of the original Handle system module, and all the identification analysis requests initiated by the original users (including normal users and malicious attack users) first need to go through the identification defense system, and the identification defense system Through modules such as logo extraction, logo detection, and logo cleaning, the system directly discards or limits the speed of malicious attack logo requests, and sends normal user request message queries to the Handle system, w...
Embodiment 2
[0089]The above defense method adds an identification defense system at the entrance of the native Handle system to identify and filter malicious access identifications in advance, so that the recursive node server can respond to normal user requests and improve the resolution quality.
[0090] This embodiment provides the overall architecture of the logo defense system, which includes: a logo extraction module, a logo detection module, a logo cleaning module, and a logo sample library module.
[0091] The identification extraction is used to extract the source IP address, destination IP address, source port number, destination port number, and handle query identification prefix encoding of the IP segment, transmission segment, and identification field respectively from the request message of the ingress query. The extracted key information is stored and passed to the identification detection module and the identification cleaning module respectively;
[0092] The identificati...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com