Protection method and system for multi-point fiber cut in communication network
A communication network and protection system technology, applied in the protection field of multi-point fiber breakage, can solve the problems of high consumption of main control CPU resources, long service switching time, service interruption, etc., and achieve the effect of saving resources and speeding up service switching time.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] Terminology Explanation:
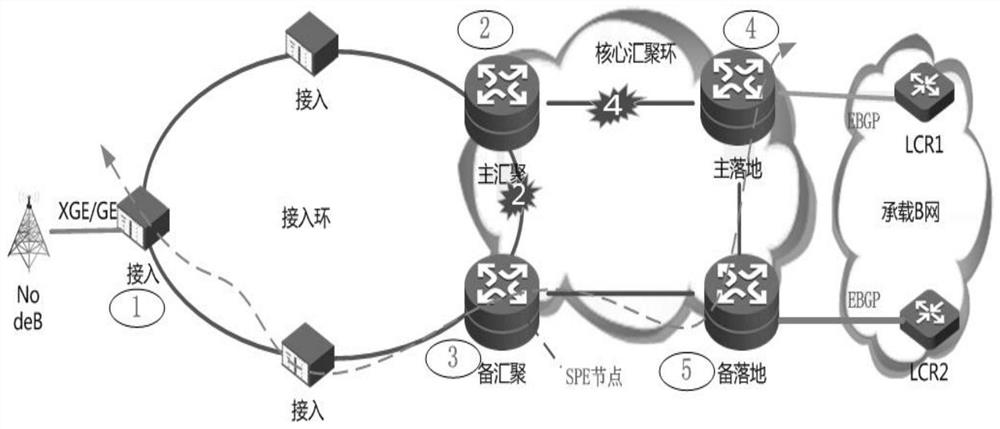
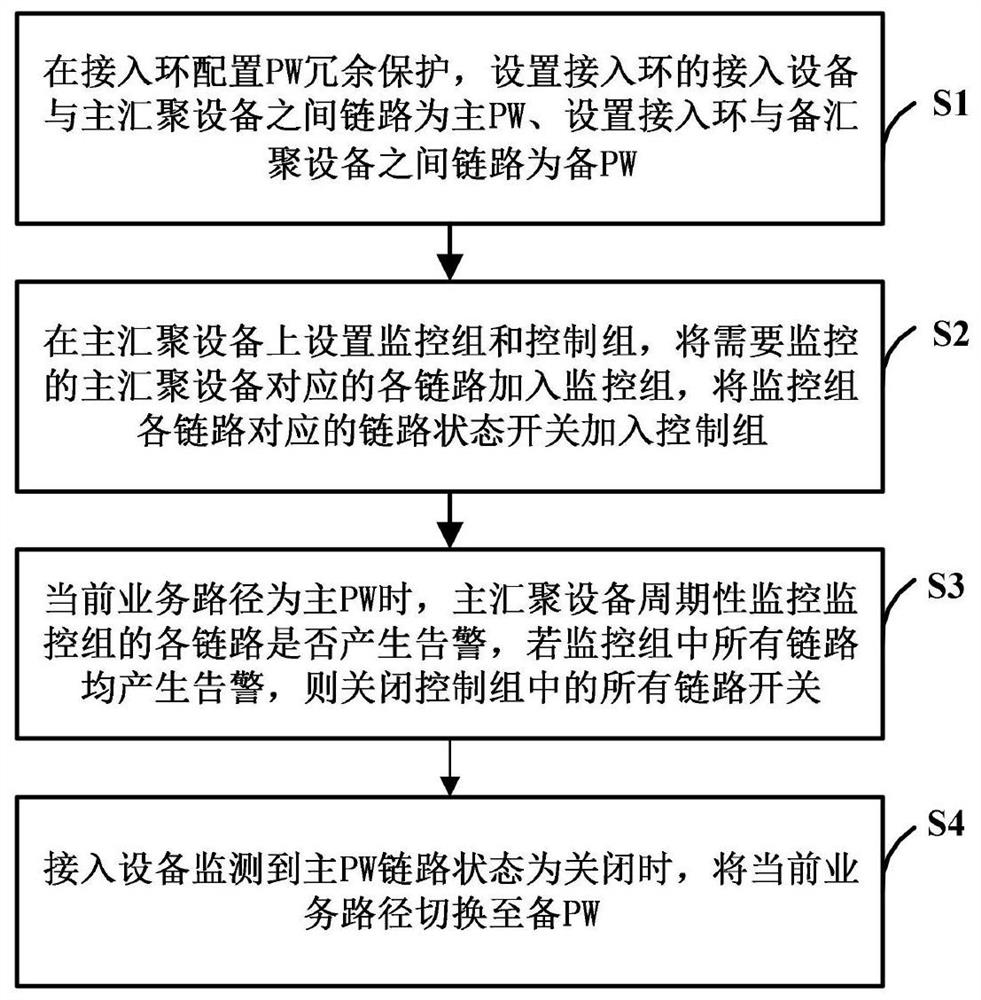
[0030] PW redundancy: It belongs to the business protection method. In the VPWS business model, when the main PW is established, a backup PW is established. When the main PW fails, the service is switched to the backup PW. At the same time, a variety of detection methods can be used to realize fast fault detection.
[0031] BFD: It is the abbreviation of Bidirectional Forwarding Detection. It is a network protocol used to detect failures between two forwarding points. It is described in detail in RFC 5880. BFD is a bidirectional forwarding detection mechanism that can provide millisecond-level detection and fast detection of links. By cooperating with upper-layer routing protocols, BFD can realize fast route convergence and ensure service continuity.
[0032] TP-OAM: MPLS-TP OAM, MPLS-TP (Multi-Protocol Label SwitchingTransport Profile, Multi-Protocol Label Switching Transport Application) performs hierarchical management and control on the o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com