Method for restraining clone card service key from updating
A key update and key technology, applied in the direction of analog security/charging system, TV, electrical components, etc., can solve the problem of unable to prevent illegal users from watching programs, affecting users to watch programs, and the speed is not infinite.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0026] The present invention will be further described below in conjunction with the accompanying drawings and specific embodiments, but the present invention is not limited to the following embodiments.
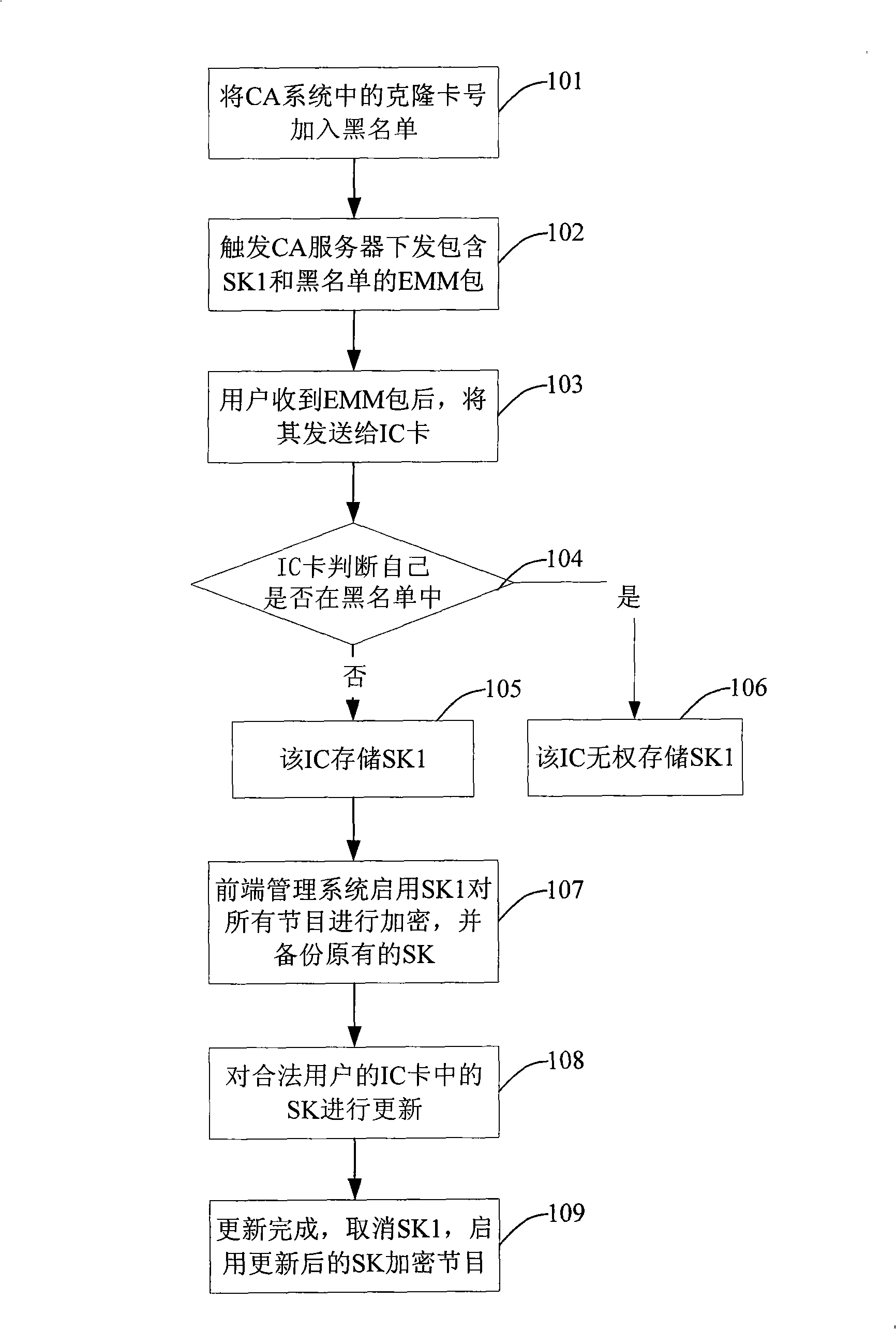
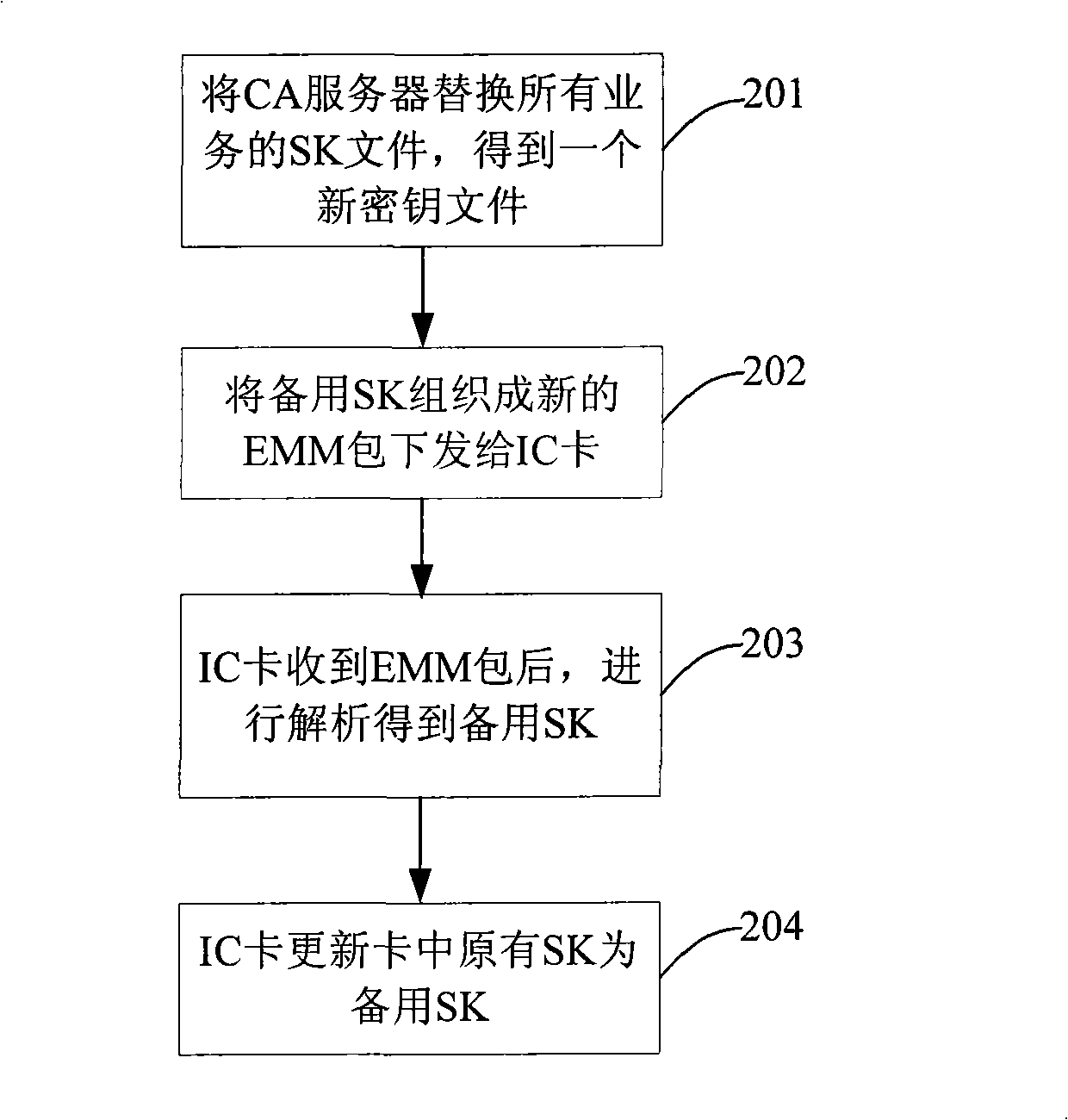
[0027] The invention first invalidates the authorization of the cloning card, and then updates it according to the SK update mechanism in the prior art. At the same time, it ensures that the IC card can receive a complete blacklist and temporary service key SK1 by adding a data protocol. The card compares whether it exists in the blacklist to determine whether it can store the temporary service key SK1, which ensures that legitimate users watch programs while preventing the cloned card from renewing the SK and taking effect.
[0028] see figure 1 , the embodiment of the present invention provides a method for suppressing the key update of the clone card service, the specific steps are as follows:
[0029] Step 101: Add the card numbers of the cloned cards in the CA system t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com