Anti-attack method and device in electronic component using Rivest-Shamir-Adleman (RSA) public-key encryption algorithm
An encryption algorithm and electronic component technology, applied in the field of attack prevention, can solve the problems of leaking the secret parameters of the decryption algorithm and the insecurity of the encryption system, and achieve the effect of defending against DPA attacks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0055] The present invention will be further described below in conjunction with the accompanying drawings and specific embodiments.
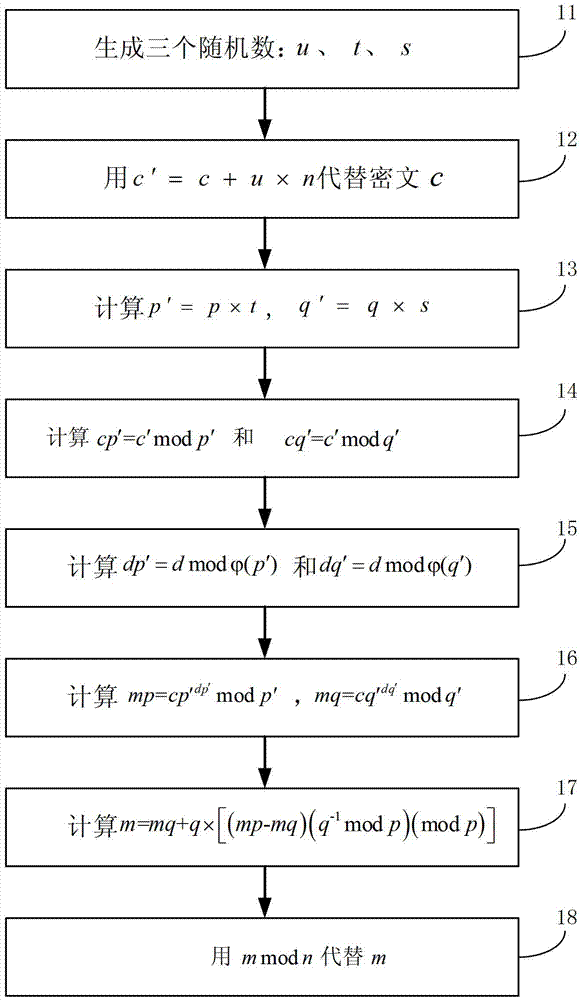
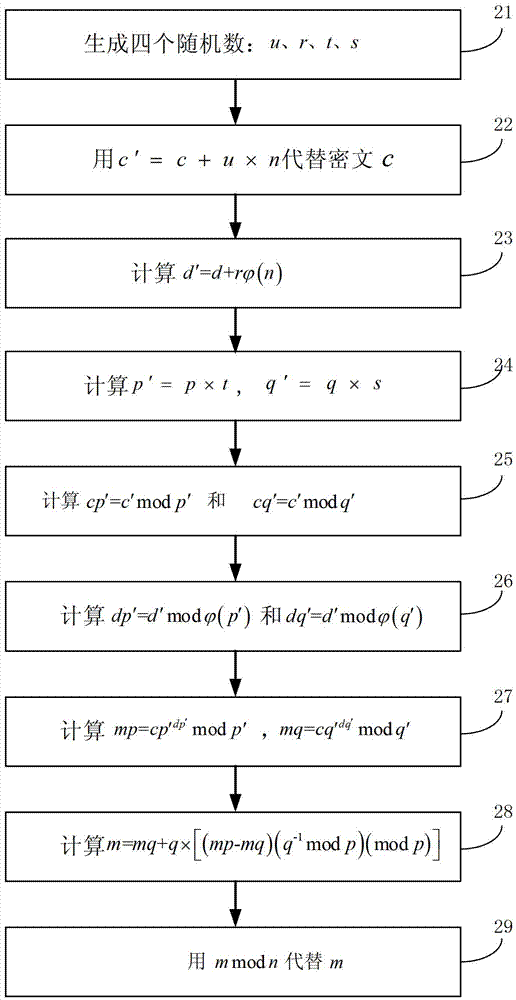
[0056] Such as figure 1 As shown, it is a schematic flow chart of the first embodiment of the anti-attack method in the electronic component using the RSA public key encryption algorithm of the present invention. This method is adopted when the RSA decryption algorithm using the CRT is executed each time. The method converts the ciphertext c, Keys d, n, p, q are used as input, the method includes the following 8 steps:
[0057] Step 11, generate three random numbers: u, t, s;
[0058] Step 12, replace the ciphertext c with c'=c+u×n;
[0059] Step 13, calculate p'=p×t, q'=q×s;
[0060] Step 14, calculate cp'=c'modp' and cq'=c'modq';
[0061] Step 15. Calculate with
[0062] Step 16, calculate mp=cp' dp′ modp',mq=cq' dq′ modq';
[0063] Step 17, calculate m=mq+q×[(mp-mq)(q -1 modp)(modp)];
[0064] Step 18, replace m with mmodn;
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com