A key management method for an internet of things sensor system
A sensor system and key management technology, applied in the field of Internet of Things security, can solve the problems of large losses, lack of key management system, frequent key replacement, etc., and achieve the effect of effective key security protection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0026] The present invention will be further described below in conjunction with drawings and embodiments. It should be understood that the specific embodiments described here are only used to explain the present invention, but not to limit the present invention. In addition, it should be noted that, for the convenience of description, only parts related to the present invention are shown in the drawings but not all content.
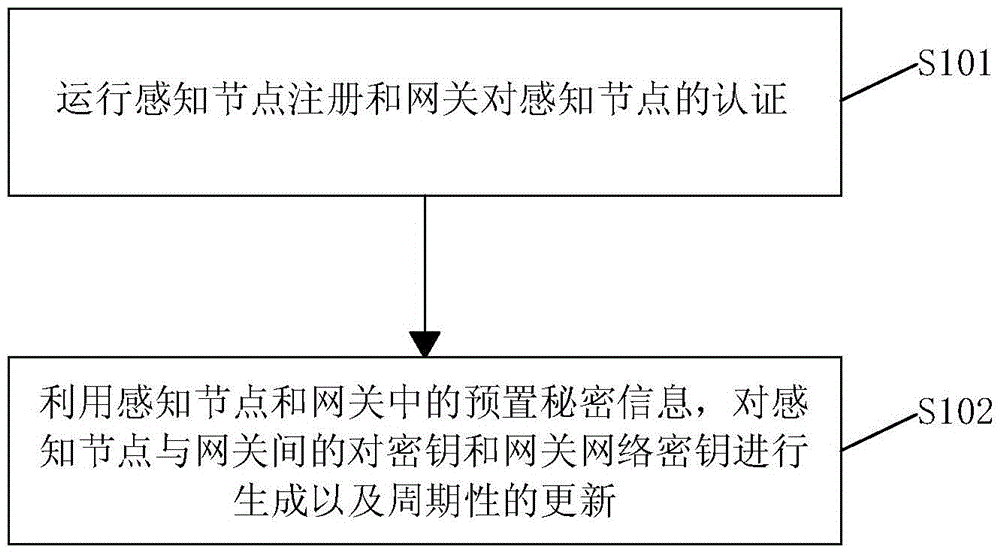
[0027] Please refer to figure 1 as shown, figure 1 It is a flow chart of the key management method of the IoT sensor system provided by the embodiment of the present invention.
[0028] The key management method flow of the IoT sensor system in this embodiment specifically includes the following steps:
[0029] Step S101 , after the security-aware node is powered on, it first runs the registration of the sensory node and the authentication of the sensory node by the gateway.
[0030] Step S102, start the key management module, use the preset secret i...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap