A detection method for android application packing
An application and detection method technology, applied in software testing/debugging and other directions, can solve problems such as difficulty in detection, and achieve great commercial value, APK reinforcement, and risk assessment market promotion and mobile application security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
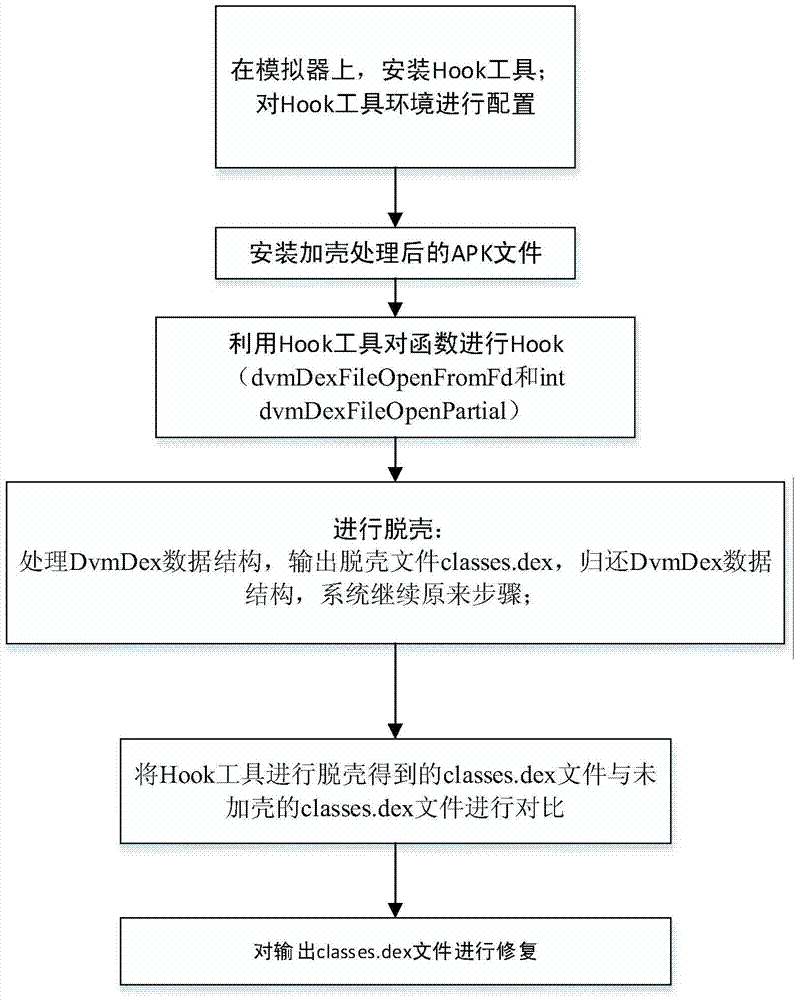
[0086] Assume that in an Android application detection system written in Java language, the scheme of the present invention is used to detect packed APK applications to detect whether the packed APK applications are effective.
[0087] Set the name of the packed application as MyApplication. The name of the Android application detection system is AnproAss. The specific steps of the detection are as follows (such as image 3 ):
[0088] 1) Install the application detection system AnproAss in the simulator MyTest;
[0089] 2) AnproAss hooks the int dvmDexFileOpenFromFd(intfd,DvmDex**ppDvmDex) function in the system / system / lib / libdvm.so;
[0090] 3) Simulator MyTest installs MyApplication;
[0091] 4) Run the unpacking processing program (unpacking tool), mainly processing the DvmDex data structure parameter that Hook function imports. At this time, the unpacking program added by the packing software has unpacked the packed classes.dex file, so the DvmDex data structure pass...
Embodiment 2
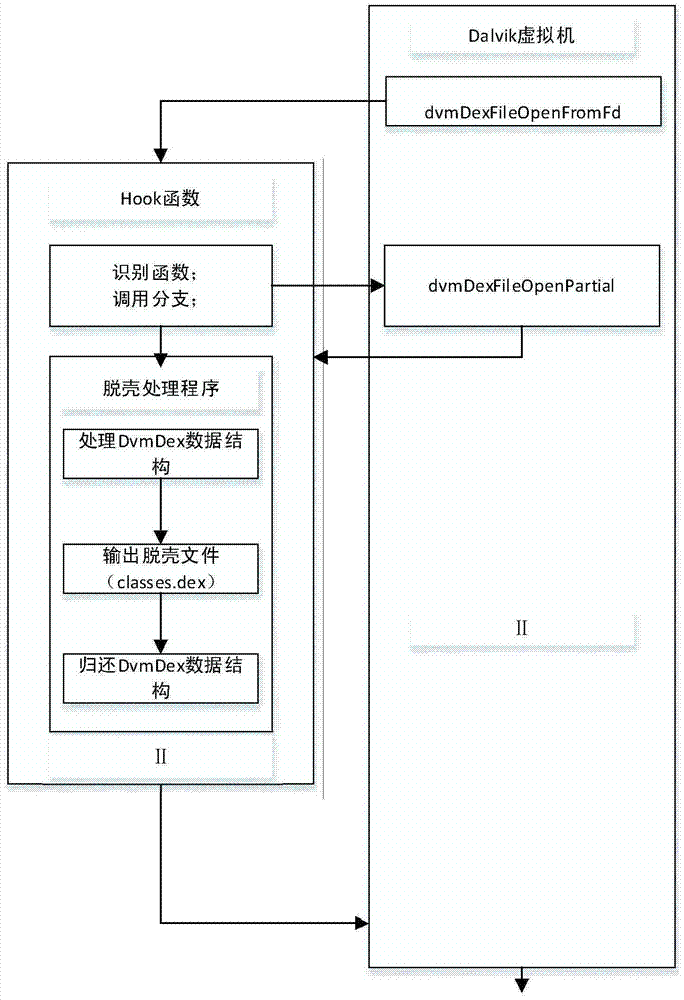
[0096]Assume that in an Android application detection system written in Java language, the invention is used to detect the packed APK application to detect whether the packed APK application is effective, and the name of the packed application is set to MyApplication. The name of the Android application detection system is AnproAss. The specific steps are as follows (such as Figure 4 ):
[0097] 1) Install the application detection system AnproAss in the simulator MyTest;
[0098] 2) AnproAss hooks the int dvmDexFileOpenPartial(const void*addr,int len,DvmDex**ppDvmDex) function in the system / system / lib / libdvm.so;
[0099] 3) Simulator MyTest installs MyApplication;
[0100] 4) Run the unpacking processing program (unpacking tool), mainly processing the DvmDex data structure parameter that Hook function imports. At this time, the unpacking program added by the packing software has unpacked the packed classes.dex file, so the DvmDex data structure passed in at this time con...
Embodiment 3
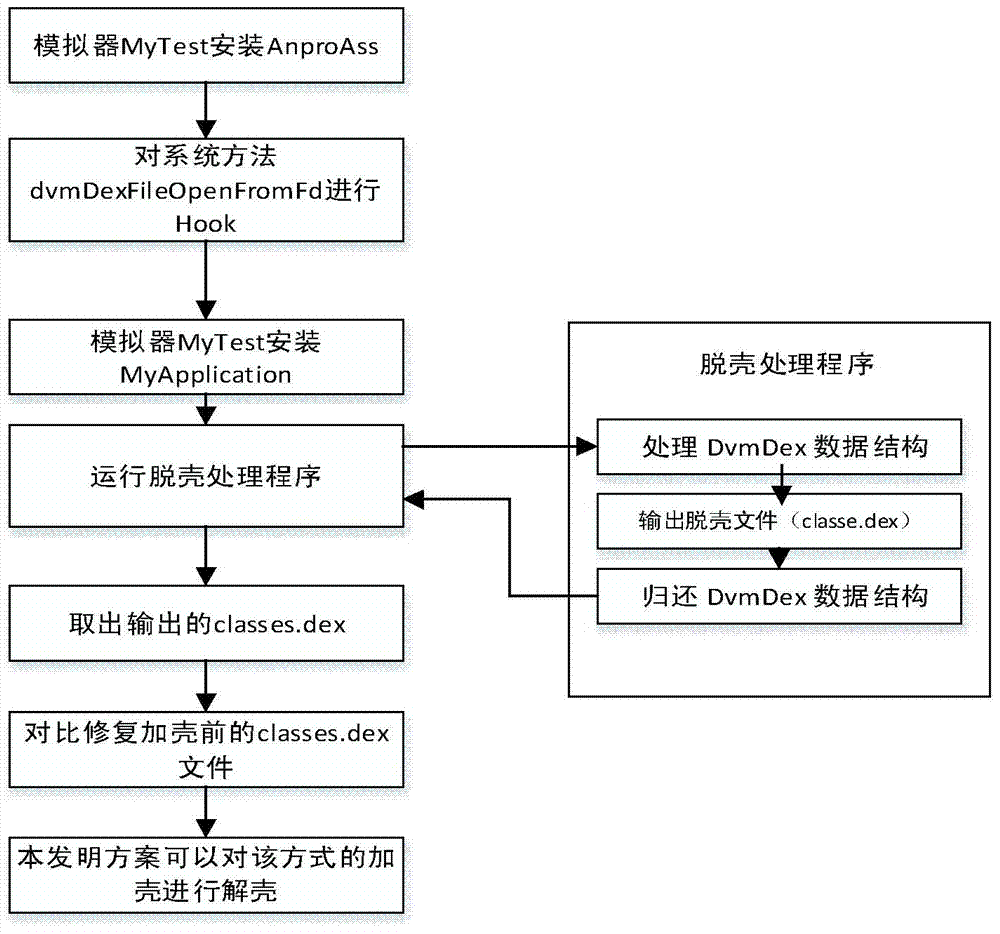
[0107] Assume that in an Android application detection system written in Java language, the invention is used to detect the packed APK application to detect whether the packed APK application is effective, and the name of the packed application is set to MyApplication. The name of the Android application detection system is AnproAss. The specific steps are as follows (such as Figure 5 ):
[0108] 1) Install the application detection system AnproAss in the simulator MyTest;
[0109] 2) Install the packed Android application MyApplication;
[0110] 3) Dalvik loads the classes.dex file of the packed MyApplication;
[0111] 4) Dalvik did not reload the dex or odex file;
[0112] 5) The classes.dex file is not obtained;
[0113] 6) The scheme of the present invention cannot deshell the shell of this method.
[0114] After packing through the corresponding packing tool, the unpacking method of the present invention can be used to obtain the source code and further analyze the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com