A call connection method and a call connection device
A technology of call connection and call party, applied in the field of information security, can solve the problems of fraudsters causing property damage to users, misleading voice confirmation of call users, etc., and achieve the effect of avoiding property and other losses.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
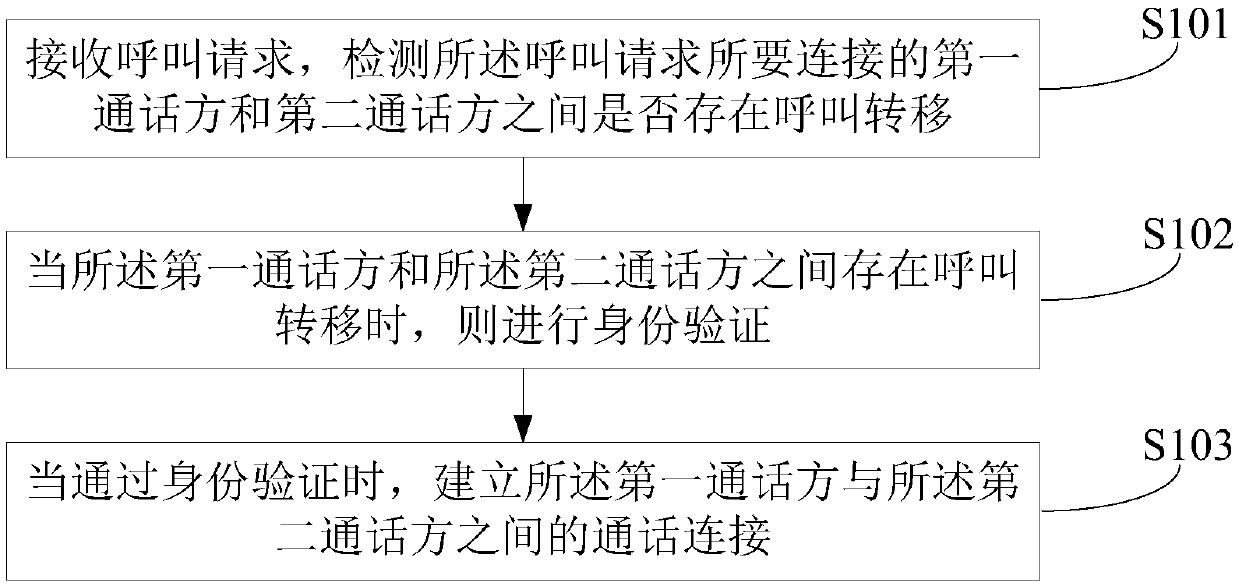
[0052] figure 1 The implementation flow of the call connection method provided by the first embodiment of the present invention is shown, and the details are as follows:
[0053] In step S101, a call request is received, and it is detected whether there is a call transfer between the first call party and the second call party to be connected by the call request.
[0054] Specifically, the call connection establishment request is usually initiated by the first call party who may be defrauded. For example, when a user receives a text message for remittance or phone charge, for security reasons, the user usually initiates a call confirmation request to the text message sender.
[0055] Fraudsters usually gain the trust of the SMS sender in advance, and change the contact name corresponding to the fraudulent call to the fraudulent contact name. For example, fraudsters may use a fake base station to impersonate the mobile phone number B of the second caller to send a number change ...
Embodiment 2
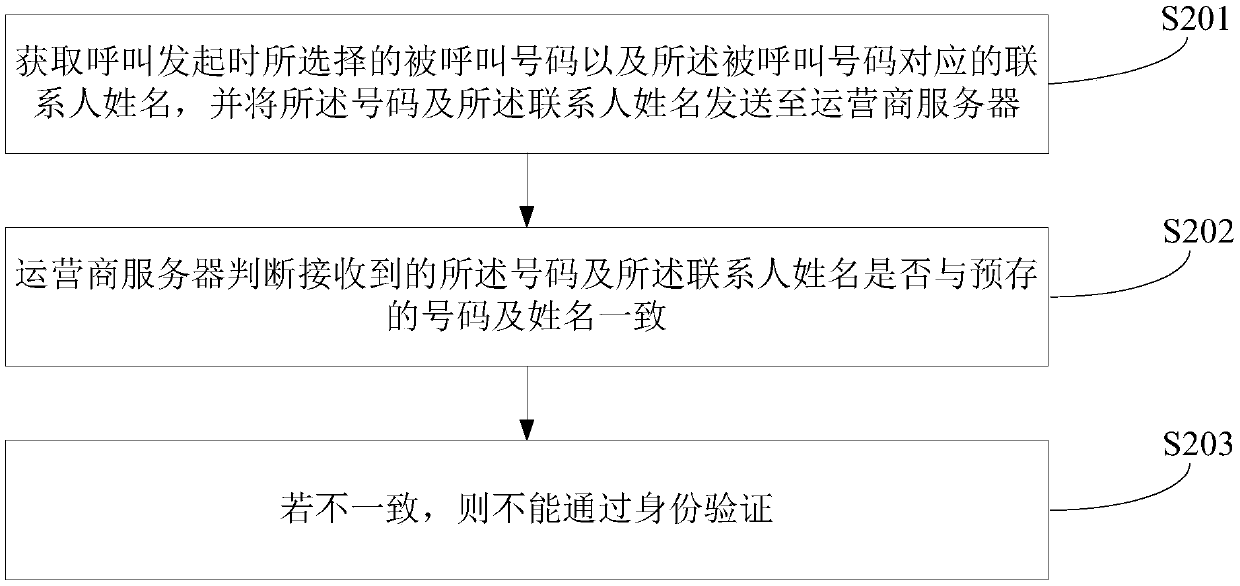
[0084] figure 2 Provided for the second embodiment of the present invention, based on the implementation process of a specific identity verification method in step S102 in the first embodiment, the details are as follows:
[0085] In step S201, the called number selected when the call is initiated and the contact name corresponding to the called number are obtained, and the number and the contact name are sent to the operator server.
[0086] When the trigger mode of the called number is a fraudulent request triggered by the user in the contact list, the name of the contact corresponding to the called may be obtained directly from the contact list.
[0087] When the called number is the number after the user modifies the contact, the name of the contact corresponding to the called can be obtained from the modified contact item.
[0088] When the called number is a number change text message (for example, when a specific number change keyword is included), the name of the con...
Embodiment 3
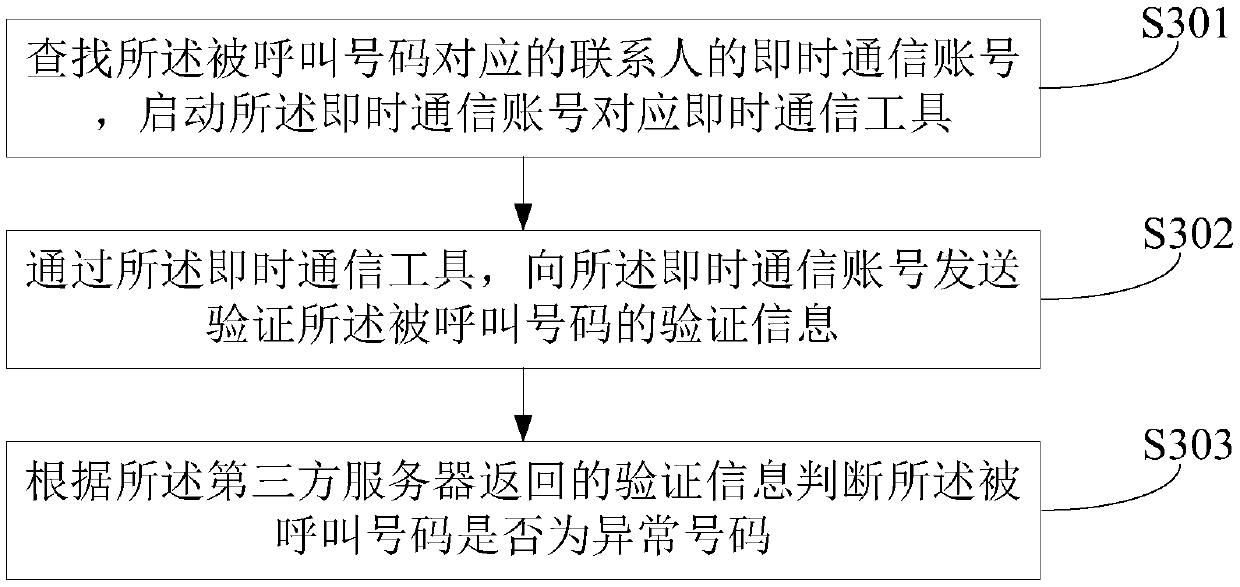
[0097] image 3 The implementation process of the identity verification method based on the first embodiment provided by the third embodiment of the present invention is described in detail as follows:
[0098] In step S301, the instant messaging account of the contact person corresponding to the called number is searched, and the instant messaging tool corresponding to the instant messaging account is activated.
[0099] Specifically, the instant messaging account of the contact person corresponding to the called number may be QQ, WeChat, Weibo or the like. Or, as an optional implementation manner of the present invention, other communication tools of the contact person, such as telephone number and email address, etc. may also be obtained.
[0100] The instant messaging account of the contact may be pre-set by the user in the contact information in the address book. When determining the contact corresponding to the called number, if the called number is a number in the con...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com