Android reinforcement method based on DEX byte code extraction and mapping confusion
A bytecode and mapping table technology, which is applied in the field of Android application reinforcement based on DEX bytecode extraction and mapping confusion, to achieve the effects of ensuring independence and versatility, realizing security reinforcement protection, and effective obfuscation protection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
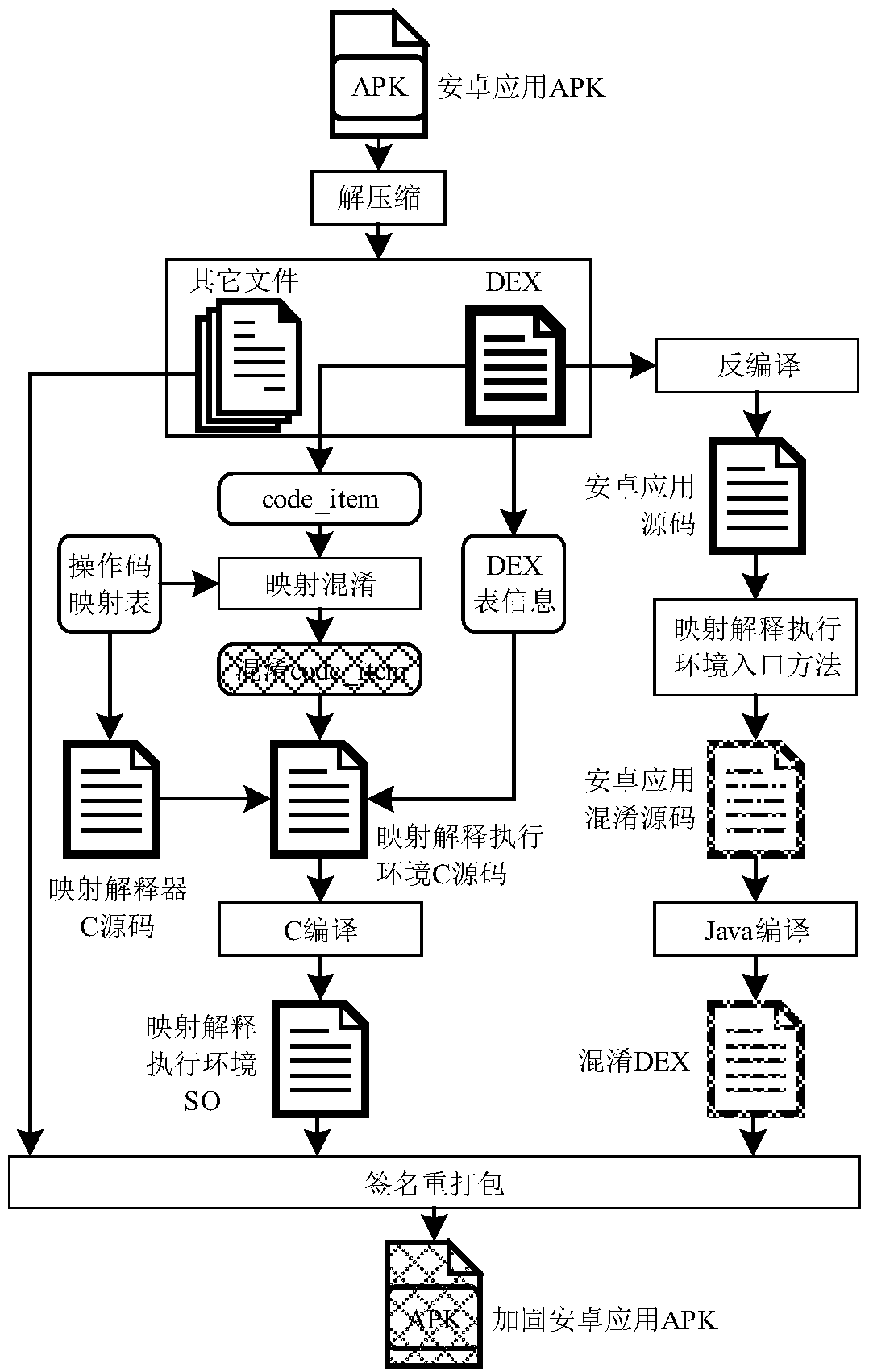
[0031] Such as figure 1 As shown, an Android application reinforcement method based on DEX bytecode detachment mapping obfuscation, the method includes DEX detachment mapping obfuscation and mapping interpretation execution, specifically includes the following steps:
[0032] S01: Decompress the APK program of the Android application to obtain the original DEX file;
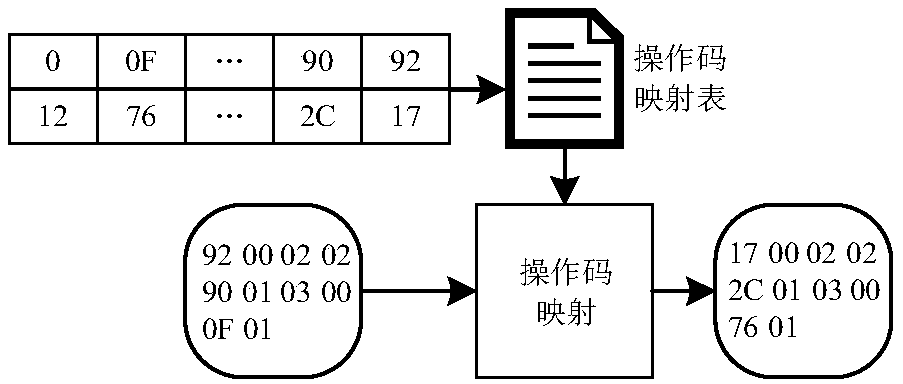
[0033] S02: Extract the code_item code to be obfuscated from the original DEX file, and map and obfuscate the code_item according to the opcode mapping table; Code_item is the content in the Android dex file format.
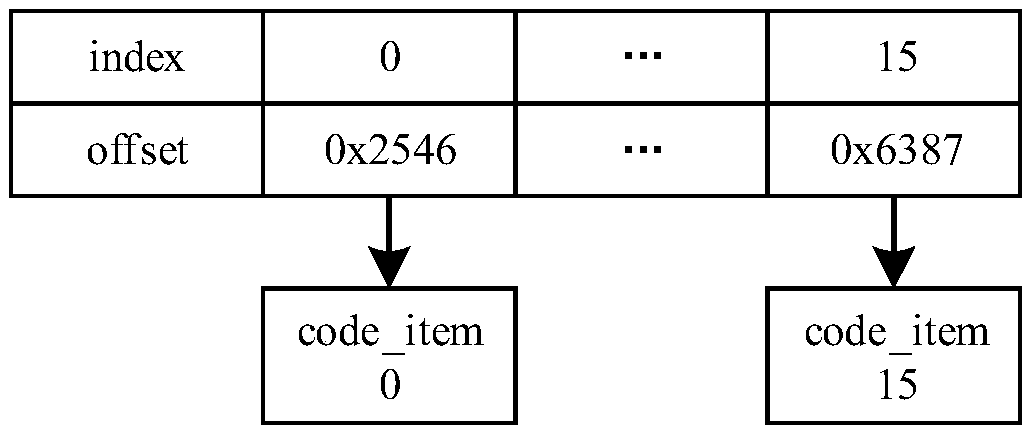
[0034] S03: Extract the table information in the original DEX file, place the obfuscated code_item code and the source code of the mapping interpreter in the source code of the mapping interpretation execution environment, compile the source code of the mapping interpretation execution environment to obtain the shared object of the mapping interpretation execution environment Library (Shared Object...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com