Identity protection method, devices and corresponding computer programme product
A technology of computer and identity, applied in the field of identification
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0108] Review of the principles of the invention
[0109] Therefore, the present invention proposes to protect the identity of the client during the authentication process. This protection is even more important, because the identity of users has become a real challenge for operators and access providers, and even for customers themselves who do not want their personal lives to be monitored.
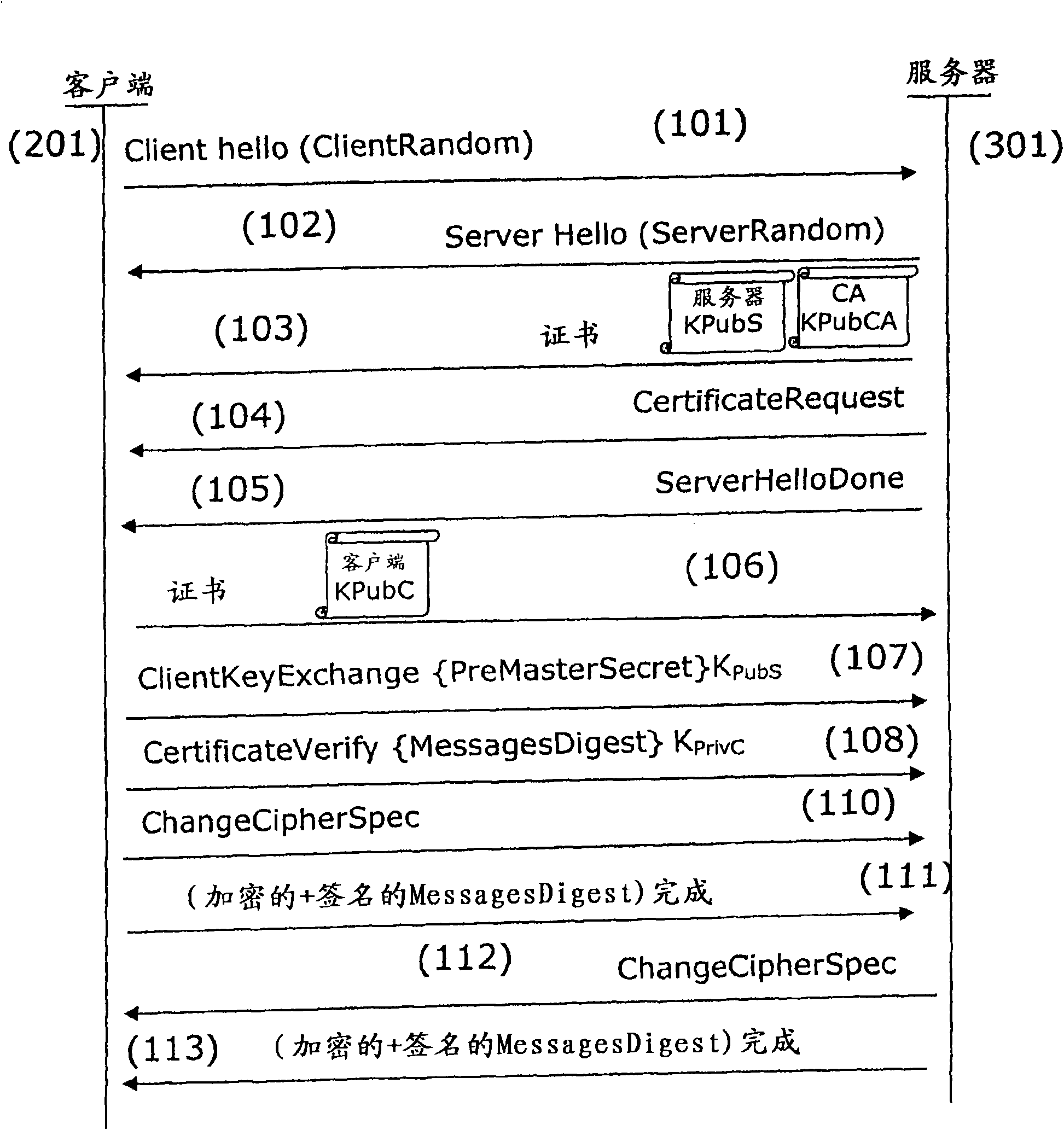
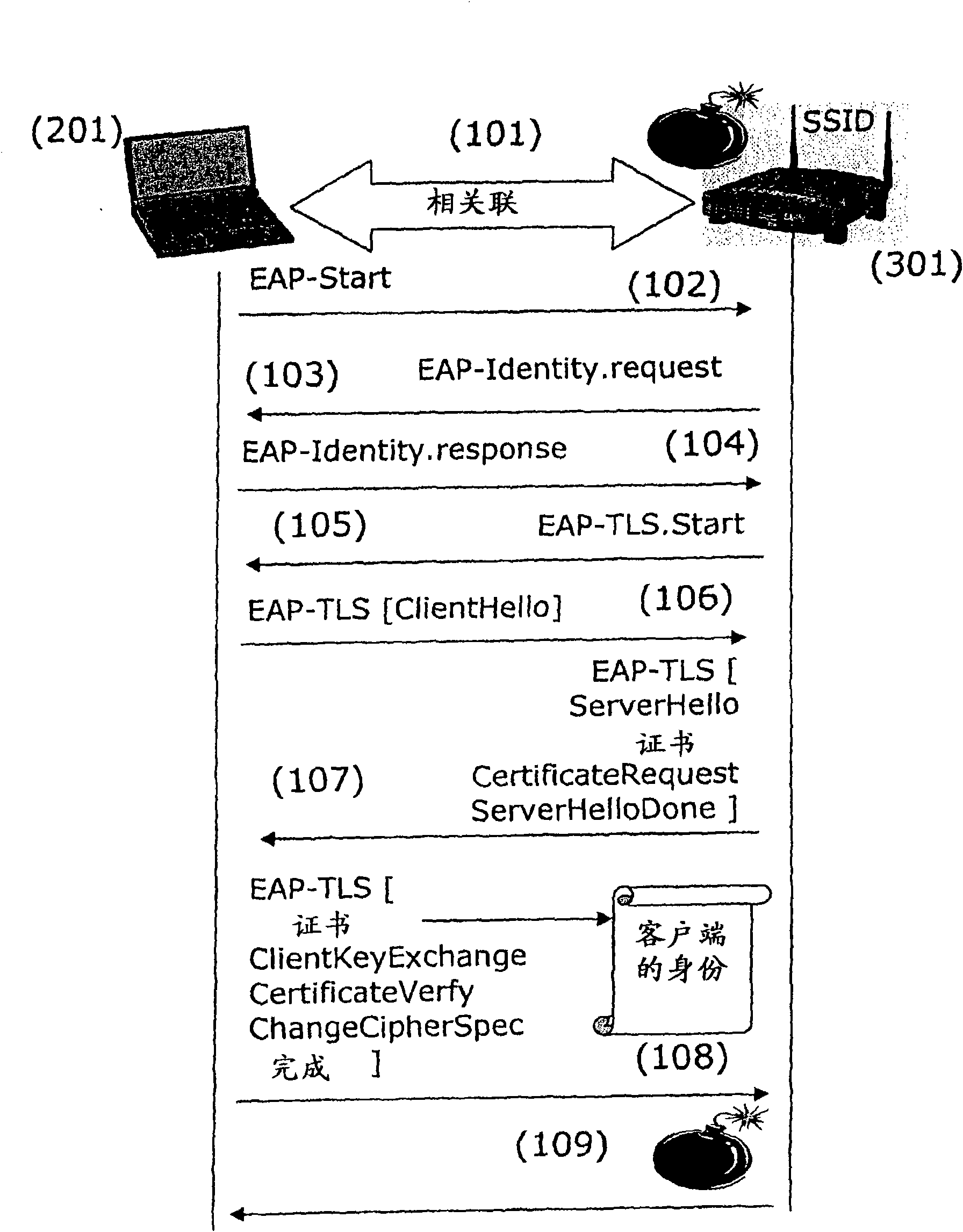
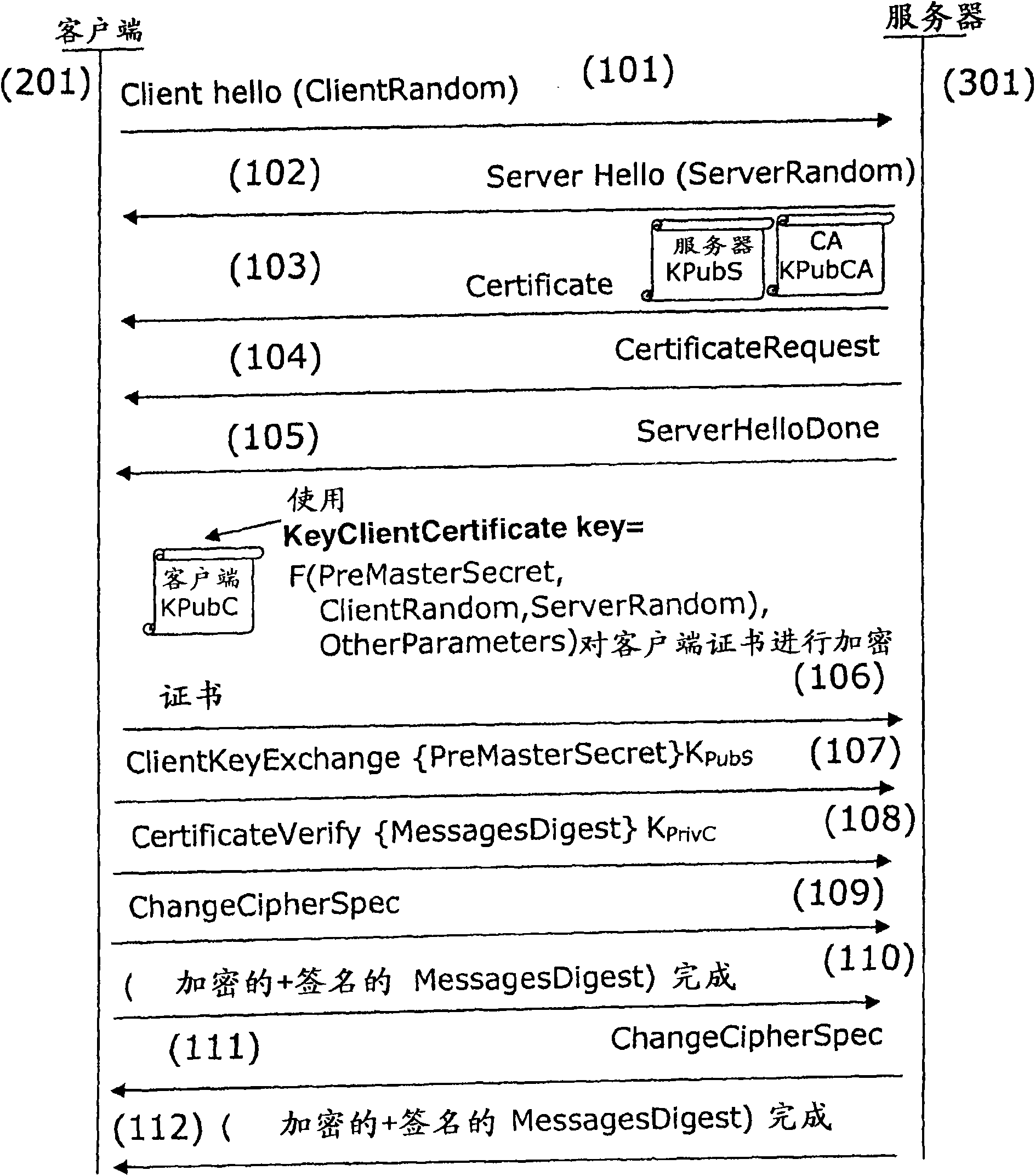
[0110] The main principle of the present invention is based on the encryption of the identity through the security module. on image 3 , Describes an embodiment of the present invention applied to the EAP-TLS protocol. However, the authentication method according to the present invention can be used in any authentication method in which the client sends its identity to the server.
[0111] In the EAP-TLS authentication process, messages are exchanged according to the TLS protocol. During the client authentication handshake session, the client (201) initiates the session through a ClientHello...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap