A single-system multi-platform authentication method
An identity verification method and multi-platform technology, which is applied in the field of single-system multi-platform identity verification, can solve problems such as failure to identify user login failure behavior, session failure process, failure to synchronize system content, etc., to improve efficiency and security, and reduce risks Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0079] The technical solution of the present invention will be further described below in conjunction with the accompanying drawings.
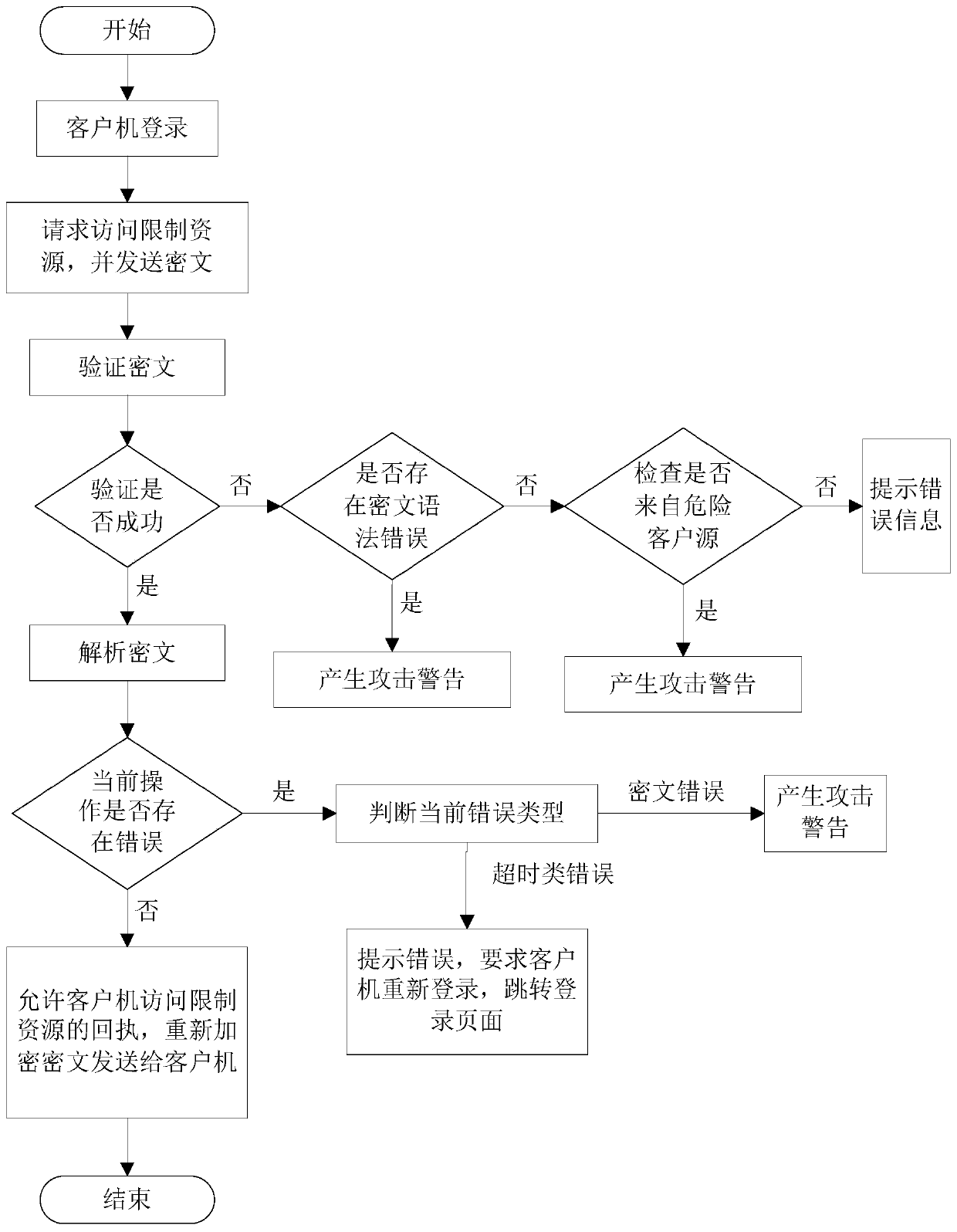
[0080] like figure 1 As shown, a single-system multi-platform authentication method includes the following steps:
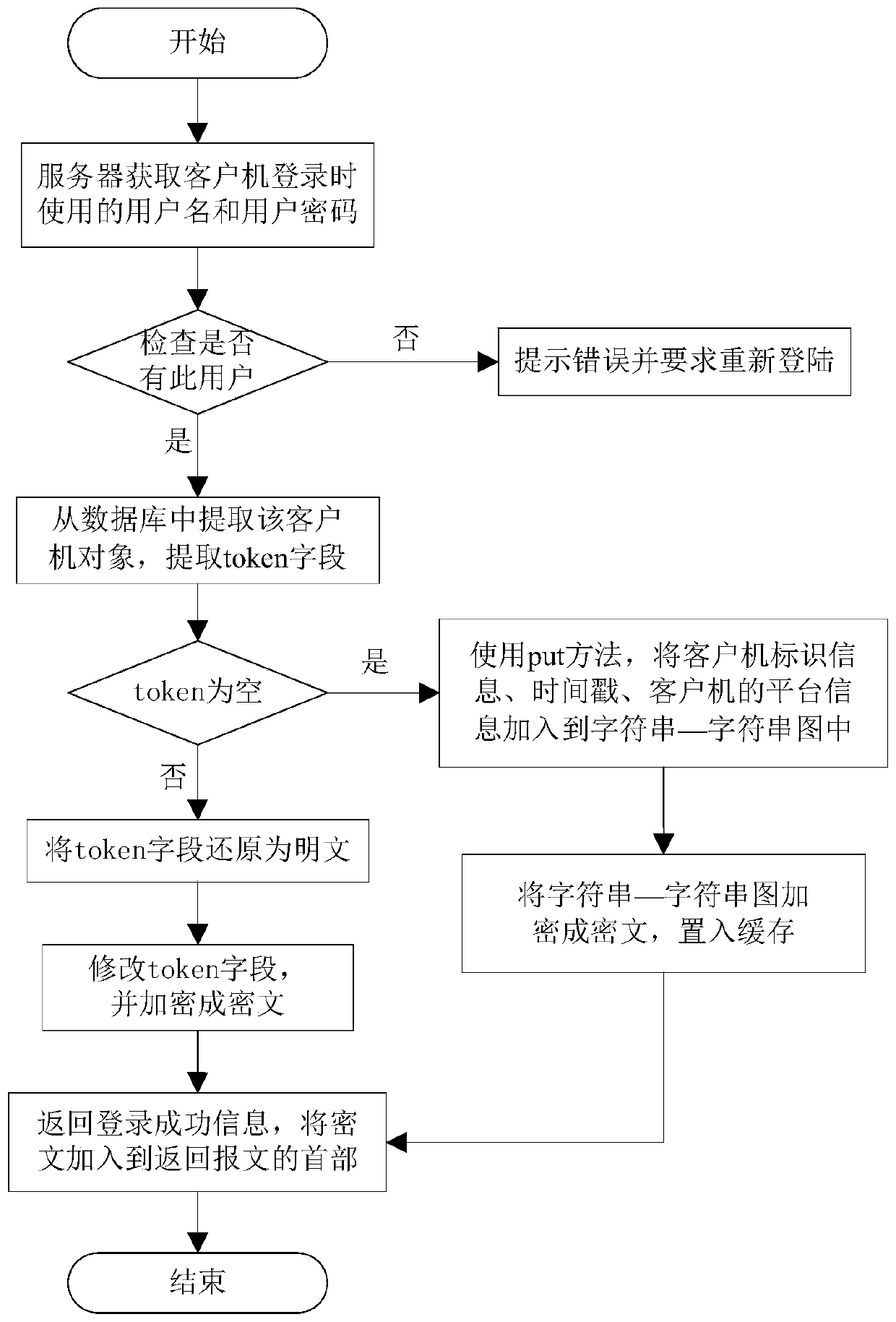
[0081] S1. The server obtains the user name and user password used by the client computer to log in, and then accesses the database to find out whether the user exists. If it exists, it provides the user with a ciphertext, otherwise it prompts an error and requires the client computer to log in again; figure 2 As shown, it specifically includes the following sub-steps:
[0082] S11, the server obtains the user name and user password used when the client logs in, accesses the database to find out whether the user exists, if it exists, executes step S12, otherwise prompts an error and requires the client to log in again;
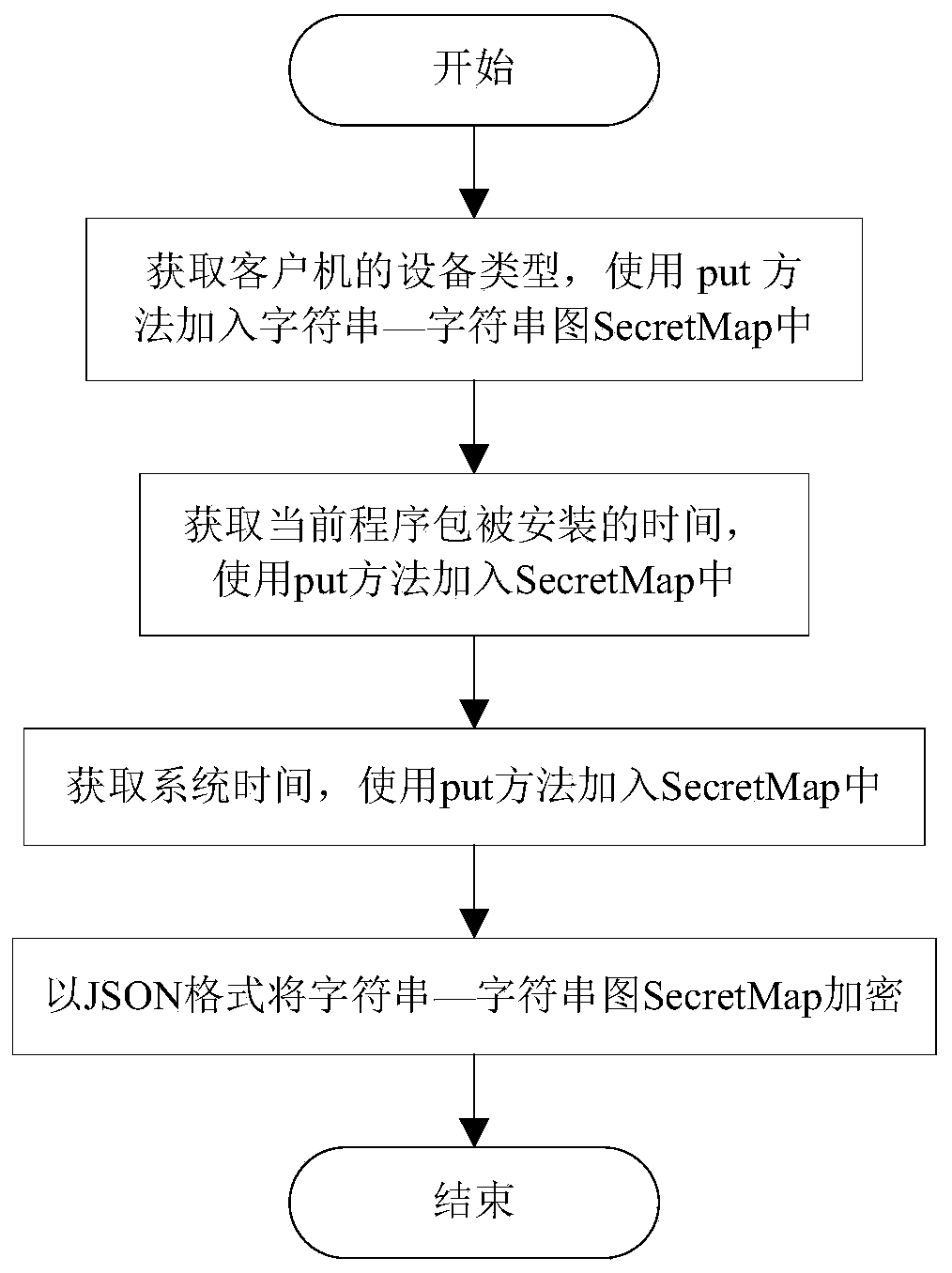
[0083] S12, extracting the client object from the database, extracting the token field, if the token field ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com