Method and system for assessing risk of information security attack in industrial control system
An industrial control system and information security technology, which is applied in the field of risk assessment of industrial control system information security attacks, can solve the problems of lack of risk assessment model risk warning level, lack of risk assessment, etc., to improve defense capabilities, reduce disaster losses, improve The effect of accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
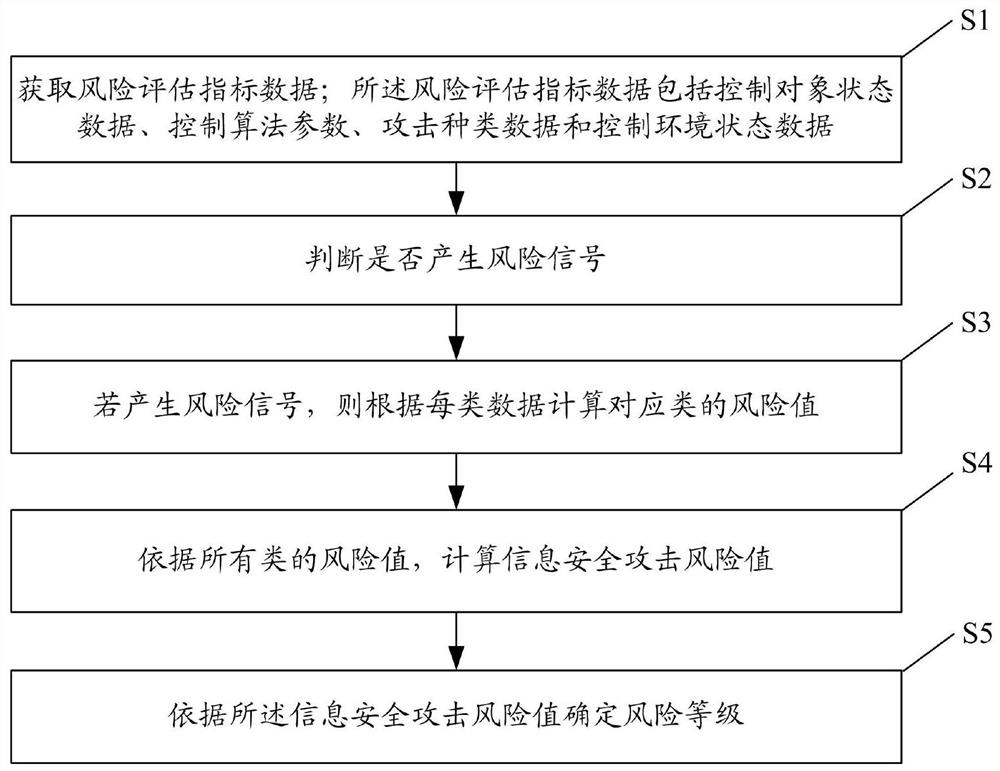
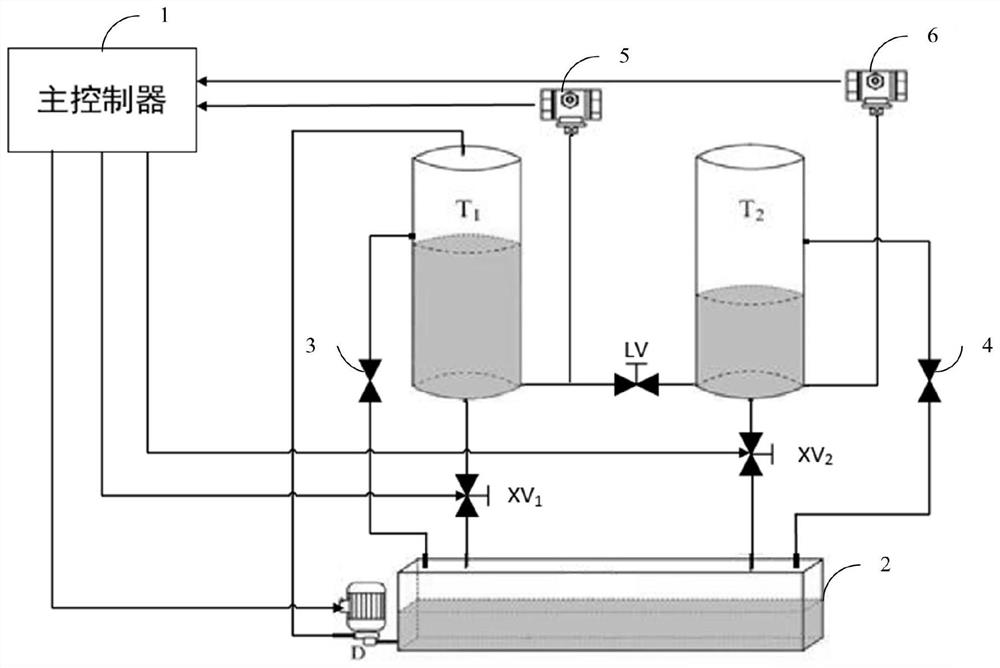
[0051] figure 1 It is a flowchart of an industrial control system information security attack risk assessment method according to an embodiment of the present invention, figure 2 It is a structural diagram of an industrial control system information security attack risk simulation device according to an embodiment of the present invention.
[0052] see figure 1 and figure 2 , the method for assessing the risk of an attack on an industrial control system information security in this embodiment is applied to a simulation device for simulating the risk of an attack on an industrial control system information security.
[0053] Industrial control system information security attack risk simulation environment is an important part of the industrial control system information security laboratory. The simulation environment is the liquid level control system, among which the liquid level control system is a highly versatile industrial control system, which can easily realize the ...
Embodiment 2
[0072] This embodiment provides a more detailed implementation manner.
[0073] The risk assessment method for information security attacks on industrial control systems provided in this example divides industrial systems into five risk warning levels: red, orange, yellow, blue, and green, extracts four categories and eighteen risk assessment indicators, and establishes a risk assessment Model. This method is applied to the information security attack risk simulation device of industrial control system. The simulation device also takes the water tank liquid level control system as the object, and helps the research by simulating information security attack, industrial control system damage evolution and damage risk level early warning. Researchers have a comprehensive understanding of the situation of information security attacks on industrial control systems, and formulate appropriate countermeasures. The invention can effectively reduce disaster loss and improve the securit...
Embodiment 3
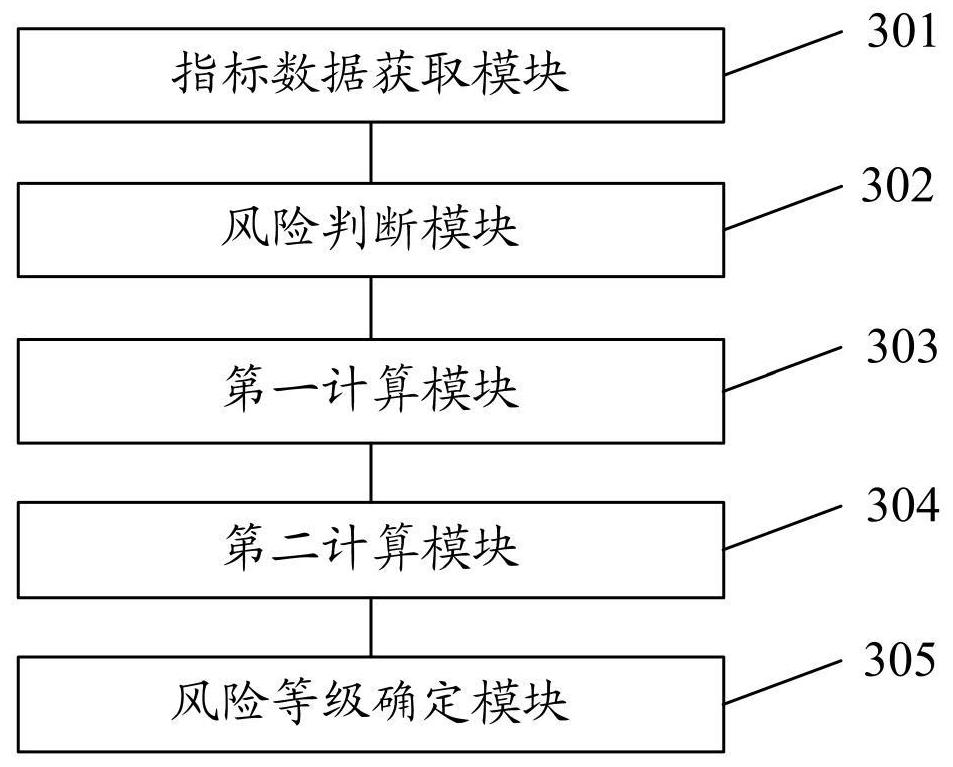
[0112] This embodiment provides an industrial control system information security attack risk assessment system, image 3 It is a structural diagram of an industrial control system information security attack risk assessment system according to Embodiment 3 of the present invention. see image 3 , the system includes:
[0113] The indicator data acquisition module 301 is used to acquire risk assessment indicator data; the risk assessment indicator data includes four types of data, which are respectively control object state data, control algorithm parameters, attack type data and control environment state data; each type of data includes A plurality of parameter values; the control object state data includes six parameter values, which are respectively the liquid level of the first water tank, the liquid level of the second water tank, the opening degree of the first overflow valve, and the opening degree of the second overflow valve , the opening degree of the communication...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com